What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2022-06-22 13:00:00 | RSA 2022: Cyber Attacks Continue to Come in Ever-Shifting Waves (lien direct) | Supply chains, trust, and the Internet itself remain prime targets. When Russia launched wide-ranging cyber-attacks while its army invaded Ukraine, it also deployed waves of wiper malware to destroy data. The first wave targeted the data on the disks. As Ukraine fortified its defenses in that area, the second wave left the data on the disks alone and went after the metadata. The third wave bypassed the two previous targets and attacked the file systems. As depicted in global news and during sessions of the RSA conference, this was a very methodical and effective approach designed to inflict maximum amounts of damage, and it reflects the methodical, often relentless, attack approaches shaping the threat landscape. In particular, as organizations fortify their defenses, adversaries will continue to focus on trust to gain access, using your partners, your vendors, and your employees against you. What does this mean for enterprise users? As we discussed in our previous post on cyber threats, organizations must find new and novel defenses against adversaries who increasingly shift tactics. As adversaries become more nuanced, we must understand their moves and motivations to try to get one step ahead of them. Let’s Recap: Several high-profile security incidents in the recent past altogether grimly encapsulate the myriad challenges companies now face. NotPetya, the most expensive cyber incident in history, demonstrated how attackers are masquerading their efforts. NotPetya targeted a tax software company in Ukraine in 2017. At first, the effort appeared to be ransomware. However, its intent was purely destructive as it was designed to inflict damage as quickly and effectively as possible. The C Cleaner attack, a few months later, demonstrated how complex and patient actors who were focused on IP level threats had become. The targets were system administrative tools that, if compromised, already had an increased level of access. C Cleaner showed that all software supply chain attacks aren’t created equal. It’s dependent on the level of access of the systems and the users that you’re compromising. Some 3 million versions of the compromised C Cleaner software were downloaded. However, only 50 of the downloaded software received additional payloads. This was an adversary that was willing to compromise more than 3 million systems to just get a foothold into 50. This gives you a clear idea of the challenges that we face as enterprises from these types of sophisticated actors. Attackers are also being more flagrant and doing a better job of covering their tracks. In the past, nation states focused on covert activities. Olympic Destroyer, which targeted the 2018 Olympics in South Korea, showed how attacks are now being brought to the public eye. False flags, tactics applied to deceive or misguide attribution attempts, were also put into Olympic Destroyer. Six months after the attack, it was attributed to multiple different nations, because such care had been put into throwing off attribution. More recently, VPN Filter/Cyber Blink demonstrated how adversaries are targeting different types of equipment. While attacks have historically focused on office equipment, these incidents shifted to home routers, in tandem with the increase in remote work. At home, people often use combination modem routers. These devices challenge detection capabilities. A foothold into home routers also allows actors to analyze all traffic moving in and out of the network. It’s incredibly difficult to detect an attack. You have to treat a home Wi-Fi like a public Wi-Fi at a coffee shop. Threat actors are targeting the foundational infrastructure of the internet as well. Sea T | Malware Tool Threat | NotPetya NotPetya | ||
| 2022-06-22 11:07:27 | Symbiote Backdoor in Linux (lien direct) | Interesting: What makes Symbiote different from other Linux malware that we usually come across, is that it needs to infect other running processes to inflict damage on infected machines. Instead of being a standalone executable file that is run to infect a machine, it is a shared object (SO) library that is loaded into all running processes using LD_PRELOAD (T1574.006), and parasitically infects the machine. Once it has infected all the running processes, it provides the threat actor with rootkit functionality, the ability to harvest credentials, and remote access capability... | Malware Threat | |||
| 2022-06-22 10:31:08 | (Déjà vu) New Phishing Attack Infects Devices With Cobalt Strike (lien direct) | Security researchers have discovered a new malicious spam campaign that delivers the ‘Matanbuchus’ malware to drop Cobalt Strike beacons on compromised machines. Cobalt Strike is a penetration testing suite that is frequently used by threat actors for lateral movement and to drop additional payloads. First spotted in February 2021 in advertisements on the dark web, […] | Spam Malware Threat | |||
| 2022-06-21 21:41:58 | RIG Exploit Kit Now Infects Victims\' PCs With Dridex Instead of Raccoon Stealer (lien direct) | The operators behind the Rig Exploit Kit have swapped the Raccoon Stealer malware for the Dridex financial trojan as part of an ongoing campaign that commenced in January 2022. The switch in modus operandi, spotted by Romanian company Bitdefender, comes in the wake of Raccoon Stealer temporarily closing the project after one of its team members responsible for critical operations passed away in | Malware | |||
| 2022-06-21 21:00:00 | BrandPost: What Every Enterprise Can Learn from Russia\'s Cyber Assault on Ukraine (lien direct) | In January, the Microsoft Threat Intelligence Center (MSTIC) discovered wiper malware in more than a dozen networks in Ukraine. Designed to look like ransomware but lacking a ransom recovery mechanism, we believe this malware was intended to be destructive and designed to render targeted devices inoperable rather than obtain a ransom. We alerted the Ukrainian government and published our findings.To read this article in full, please click here | Ransomware Malware Threat | |||
| 2022-06-21 18:58:20 | Rise of LNK (Shortcut files) Malware (lien direct) | > Authored by Lakshya Mathur An LNK file is a Windows Shortcut that serves as a pointer to open a file,...
Authored by Lakshya Mathur An LNK file is a Windows Shortcut that serves as a pointer to open a file,...
|
Malware | |||
| 2022-06-21 18:28:00 | Cyber Threats Are as Bad as You Imagine, But Different Than You May Think (lien direct) | The Global Threat Landscape is Novel and Requires a Novel Response From Russia to China to South Korea, the global threat landscape continues to mature, often confounding the assumptions of those who must defend against the attacks. Novel techniques are the norm, such as criminals posing as job seekers to infiltrate networks or attacking non-obvious networks. This results in attacks that are harder to predict, adversaries that are harder to detect, and breaches that are harder to address. Harder, but not impossible. While we are certainly living in a more dangerous cyber age, we also find ourselves at a point of inflection. XDR is a significant evolution, and we believe that adversary detection and response (ADR) is not far behind, particularly with more collaboration between the public and private sectors. Perhaps most importantly, we are getting closer and closer to realizing the full promise of Big Data in a cybersecurity context. At Anomali, much of our energy is put towards closing that gap. We believe it is the key to unlocking adversary defense as a truly viable and scalable approach to securing companies and people. At the RSA Conference 2022, cyber threat experts gave attendees a virtual trip around the world during a panel presentation examining threat actor activity from both nation-states and criminal groups. The panelists revealed the latest global threat activity, as well as the best strategies to thwart increasingly sophisticated attacks. They detailed adversary behavior that should both concern and energize us, and we share it here in the hopes of generating energy amongst our community, our partners, our customers, and all those who see an understanding of adversary behavior as a critical mission. Attacks Go Beyond Traditional Platforms China, while not as flashy and flamboyant as Russia, is reshaping the cyber threat landscape as well. Its attacks are moving beyond traditional platforms such as Microsoft and Linux malware to esoteric systems, like Huawei routers and Solaris implants. As panelists noted, the attack surface is shifting, widening, and morphing in many different ways. For example, China exploited a vulnerability in software that tracks diseases in cattle to gain a foothold into 18 state and local governments in the U.S. that use the software. Often, threat actors can exploit vulnerabilities within hours. The implication, according to the panel? Defenders must look beyond traditional assets and accelerate the patching of critical systems. It’s no longer a matter of simply matching every so often. Instead, it’s imperative to have hard conversations with the business about downtime and schedule patching regularly. Ransomware as Harassment Iran has become an innovator in government-backed ransomware. Iranian attackers are becoming more patient, sometimes having 10 interactions with a victim before doing anything malicious. The panelists referred to them as “big-game hunters at scale,” and I couldn’t agree more. We’re not talking about just targeting one system within the network to lock it up. This is a network-wide ransomware endeavor to get as much ransom as possible. Add to this the practice of leaking data to harass organizations. Cyber Criminals are Posing as Job Seekers North Korea, whose cyber activities have been mostly on hold during the pandemic, is returning in a vengeful – and creative way. Among the newest developments: A focus on cryptocurrency schemes. Panelists recounted examples of stolen crypto wallets. If one doesn’t store cryptocurrency offline, they will likely lose al | Ransomware Malware Vulnerability Threat Patching | |||
| 2022-06-21 15:34:44 | Russian govt hackers hit Ukraine with Cobalt Strike, CredoMap malware (lien direct) | The Ukrainian Computer Emergency Response Team (CERT) is warning that Russian hacking groups are exploiting the Follina code execution vulnerability in new phishing campaigns to install the CredoMap malware and Cobalt Strike beacons. [...] | Malware Vulnerability | |||
| 2022-06-21 15:25:09 | Russia\'s APT28 uses fear of nuclear war to spread Follina docs in Ukraine (lien direct) | Threat actors associated with Russian intelligence are using the fear or nuclear war to spread data-stealing malware in Ukraine. | Malware | APT 28 | ||
| 2022-06-21 15:03:00 | Anomali Cyber Watch: GALLIUM Expands Targeting Across Telecommunications, Government and Finance Sectors With New PingPull Tool, DragonForce Malaysia OpsPatuk / OpsIndia and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT35, CrescentImp, Follina, Gallium, Phosphorous, and Sandworm. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Update: The Phish Goes On - 5 Million Stolen Credentials and Counting
(published: June 16, 2022)
PIXM researchers describe an ongoing, large-scale Facebook phishing campaign. Its primary targets are Facebook Messenger mobile users and an estimated five million users lost their login credentials. The campaign evades Facebook anti-phishing protection by redirecting to a new page at a legitimate service such as amaze.co, famous.co, funnel-preview.com, or glitch.me. In June 2022, the campaign also employed the tactic of displaying legitimate shopping cart content at the final page for about two seconds before displaying the phishing content. The campaign is attributed to Colombian actor BenderCrack (Hackerasueldo) who monetizes displaying affiliate ads.
Analyst Comment: Users should check what domain is asking for login credentials before providing those. Organizations can consider monitoring their employees using Facebook as a Single Sign-On (SSO) Provider.
MITRE ATT&CK: [MITRE ATT&CK] Phishing - T1566 | [MITRE ATT&CK] User Execution - T1204
Tags: Facebook, Phishing, Facebook Messenger, Social networks, Mobile, Android, iOS, Redirect, Colombia, source-country:CO, BenderCrack, Hackerasueldo
F5 Labs Investigates MaliBot
(published: June 15, 2022)
F5 Labs researchers describe a novel Android trojan, dubbed MaliBot. Based on re-written SOVA malware code, MaliBot is maintaining its Background Service by setting itself as a launcher. Its code has some unused evasion portions for emulation environment detection and setting the malware as a hidden app. MaliBot spreads via smishing, takes control of the device and monetizes using overlays for certain Italian and Spanish banks, stealing cryptocurrency, and sometimes sending Premium SMS to paid services.
Analyst Comment: Users should be wary of following links in unexpected SMS messages. Try to avoid downloading apps from third-party websites. Be cautious with enabling accessibility options.
MITRE ATT&CK: [MITRE ATT&CK] System Network Configuration Discovery - T1016 | [MITRE ATT&CK] User Execution - T1204
Tags: MaliBot, Android, MFA bypass, SMS theft, Premium SMS, Smishing, Binance, Trust wallet, VNC, SOVA, Sality, Cryptocurrency, Financial, Italy, target-country:IT, Spain, target-country:ES
Extortion Gang Ransoms Shoprite, Largest Supermarket Chain in Africa
(published: June 15, 2022)
On June 10, 2022, the African largest supermarket chain operating in twelve countries, Shoprite Holdings, announced a possible cybersecurity incident. The company notified customers in E
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Update: The Phish Goes On - 5 Million Stolen Credentials and Counting
(published: June 16, 2022)
PIXM researchers describe an ongoing, large-scale Facebook phishing campaign. Its primary targets are Facebook Messenger mobile users and an estimated five million users lost their login credentials. The campaign evades Facebook anti-phishing protection by redirecting to a new page at a legitimate service such as amaze.co, famous.co, funnel-preview.com, or glitch.me. In June 2022, the campaign also employed the tactic of displaying legitimate shopping cart content at the final page for about two seconds before displaying the phishing content. The campaign is attributed to Colombian actor BenderCrack (Hackerasueldo) who monetizes displaying affiliate ads.
Analyst Comment: Users should check what domain is asking for login credentials before providing those. Organizations can consider monitoring their employees using Facebook as a Single Sign-On (SSO) Provider.
MITRE ATT&CK: [MITRE ATT&CK] Phishing - T1566 | [MITRE ATT&CK] User Execution - T1204
Tags: Facebook, Phishing, Facebook Messenger, Social networks, Mobile, Android, iOS, Redirect, Colombia, source-country:CO, BenderCrack, Hackerasueldo
F5 Labs Investigates MaliBot
(published: June 15, 2022)
F5 Labs researchers describe a novel Android trojan, dubbed MaliBot. Based on re-written SOVA malware code, MaliBot is maintaining its Background Service by setting itself as a launcher. Its code has some unused evasion portions for emulation environment detection and setting the malware as a hidden app. MaliBot spreads via smishing, takes control of the device and monetizes using overlays for certain Italian and Spanish banks, stealing cryptocurrency, and sometimes sending Premium SMS to paid services.
Analyst Comment: Users should be wary of following links in unexpected SMS messages. Try to avoid downloading apps from third-party websites. Be cautious with enabling accessibility options.
MITRE ATT&CK: [MITRE ATT&CK] System Network Configuration Discovery - T1016 | [MITRE ATT&CK] User Execution - T1204
Tags: MaliBot, Android, MFA bypass, SMS theft, Premium SMS, Smishing, Binance, Trust wallet, VNC, SOVA, Sality, Cryptocurrency, Financial, Italy, target-country:IT, Spain, target-country:ES
Extortion Gang Ransoms Shoprite, Largest Supermarket Chain in Africa
(published: June 15, 2022)
On June 10, 2022, the African largest supermarket chain operating in twelve countries, Shoprite Holdings, announced a possible cybersecurity incident. The company notified customers in E |
Ransomware Malware Tool Vulnerability Threat Guideline Conference | Yahoo APT 35 | ||
| 2022-06-21 14:30:40 | BRATA Android Malware Evolves Into an APT (lien direct) | The BRATA Android banking Trojan is evolving into a persistent threat with a new phishing technique and event-logging capabilities. | Malware Threat | |||
| 2022-06-21 13:50:02 | Android : le malware Brata est de retour, il est encore plus dangereux (lien direct) |  Le malware Brata repart à l'offensive des smartphones Android. De plus en plus dangereux, le virus est désormais capable de lire les SMS de ses victimes.
L'article Android : le malware Brata est de retour, il est encore plus dangereux est à retrouver sur 01net.com.
Le malware Brata repart à l'offensive des smartphones Android. De plus en plus dangereux, le virus est désormais capable de lire les SMS de ses victimes.
L'article Android : le malware Brata est de retour, il est encore plus dangereux est à retrouver sur 01net.com. |
Malware | |||
| 2022-06-21 13:42:37 | New Android banking malware disguises as crypto app to spread (lien direct) | >A new banking Trojan dubbed "Malibot" pretends to be a cryptomining application to spread between Android phones. While only active now in Spain and Italy, it could begin targeting Americans. | Malware | |||
| 2022-06-21 13:28:00 | APT actor ToddyCat hits government and military targets in Europe and Asia (lien direct) | Researchers from Kaspersky Lab have published an analysis of a previously undocumented advanced persistent threat (APT) group that they have dubbed ToddyCat.The threat actor, which has targeted high-profile organizations in Asia and Europe, often breaks into organizations by hacking into internet-facing Microsoft Exchange servers, following up with a multi-stage infection chain that deploys two custom malware programs."We still have little information about this actor, but we know that its main distinctive signs are two formerly unknown tools that we call 'Samurai backdoor' and 'Ninja Trojan'," the researchers said.To read this article in full, please click here | Malware Tool Threat | |||
| 2022-06-21 06:00:00 | Version 2.0 FLOSS Version 2.0 (lien direct) |
Le solveur de chaîne par évasion (Floss) a soutenu les analystes pour extraire des chaînes cachées des échantillons de logiciels malveillants depuis de nombreuses années maintenant.Au cours des derniers mois, nous avons ajouté de nouvelles fonctionnalités et amélioré les performances de l'outil.Dans cet article de blog, nous partagerons de nouvelles fonctionnalités et améliorations passionnantes, notamment une nouvelle technique de déobfuscation de chaîne, une utilisation simplifiée des outils et une sortie de résultats beaucoup plus rapide.Nous avons également mis à jour le logo de soie dentaire:
 Rappel: les chaînes d'extraits de fil de malware
analyse du fil des programmes compilés, identifie les fonctions qui peuvent décoder les données et désobfumate automatiquement Rappel: les chaînes d'extraits de fil de malware
analyse du fil des programmes compilés, identifie les fonctions qui peuvent décoder les données et désobfumate automatiquement
The FLARE Obfuscated String Solver (FLOSS) has been supporting analysts to extract hidden strings from malware samples for many years now. Over the last few months, we\'ve added new functionality and improved the tool\'s performance. In this blog post we will share exciting new features and improvements including a new string deobfuscation technique, simplified tool usage, and much faster result output. We\'ve also updated the FLOSS logo: 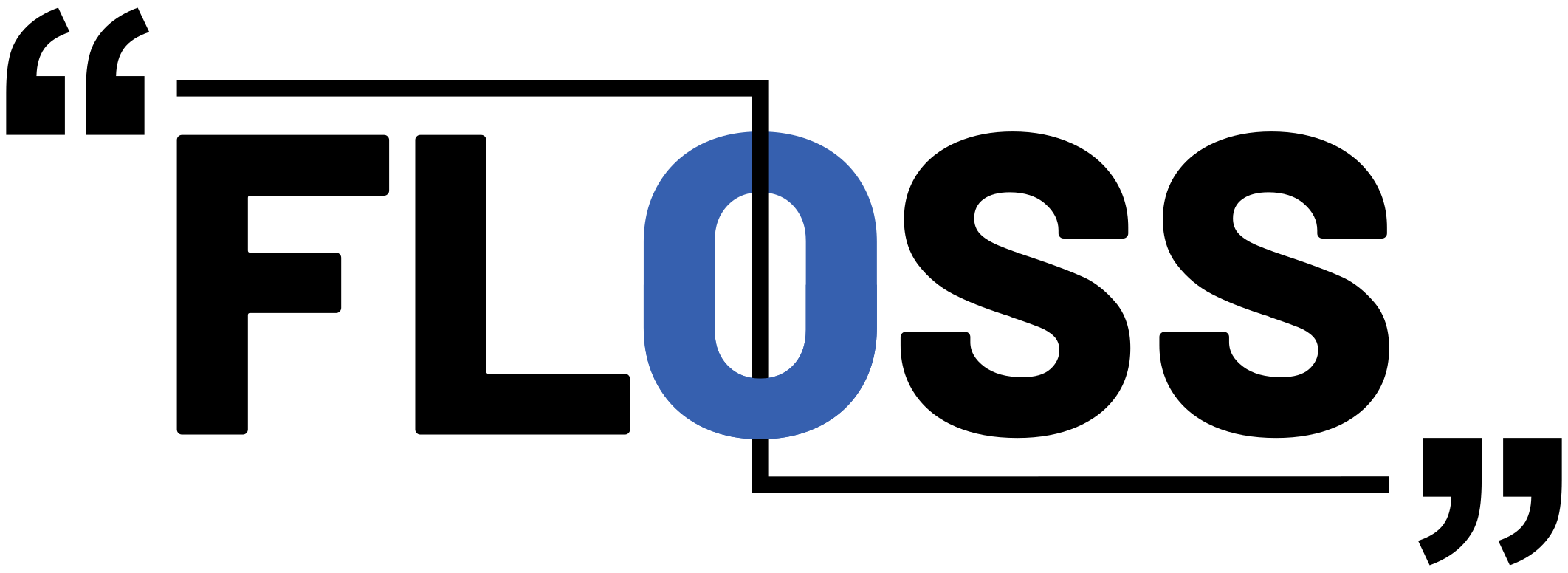 Reminder: FLOSS extracts strings from malware
FLOSS analyzes compiled programs, identifies functions that may decode data, and automatically deobfuscates Reminder: FLOSS extracts strings from malware
FLOSS analyzes compiled programs, identifies functions that may decode data, and automatically deobfuscates |
Malware Tool | ★★★ | ||
| 2022-06-20 15:30:00 | BRATA Android Malware Group Now Classified As Advanced Persistent Threat (lien direct) | BRATA now targeting a specific financial institution at a time | Malware Threat | |||
| 2022-06-20 09:41:01 | BRATA Android Malware evolves and targets the UK, Spain, and Italy (lien direct) | >The developers behind the BRATA Android malware have implemented additional features to avoid detection. The operators behind the BRATA Android malware have implemented more features to make their attacks stealthy. The malware was first spotted in 2019 by security experts at Kaspersky, the name BRAT comes from 'Brazilian RAT Android,' because at the time it was used to […] | Malware | |||
| 2022-06-19 22:18:13 | BRATA Android Malware Gains Advanced Mobile Threat Capabilities (lien direct) | The operators behind BRATA have once again added more capabilities to the Android mobile malware in an attempt to make their attacks against financial apps more stealthy. "In fact, the modus operandi now fits into an Advanced Persistent Threat (APT) activity pattern," Italian cybersecurity firm Cleafy said in a report last week. "This term is used to describe an attack campaign in which | Malware Threat | |||
| 2022-06-19 10:15:23 | Android-wiping BRATA malware is evolving into a persistent threat (lien direct) | The threat actors operating the BRATA banking trojan have evolved their tactics and incorporated new information-stealing features into their malware. [...] | Malware Threat | ★★★ | ||
| 2022-06-18 10:06:03 | (Déjà vu) New phishing attack infects devices with Cobalt Strike (lien direct) | Security researchers have noticed a new malicious spam campaign that delivers the 'Matanbuchus' malware to drop Cobalt Strike beacons on compromised machines. [...] | Spam Malware | ★★★ | ||
| 2022-06-18 10:06:03 | Wave of \'Matanbuchus\' spam is infecting devices with Cobalt Strike (lien direct) | Security researchers have noticed a new malicious spam campaign that delivers the 'Matanbuchus' malware to drop Cobalt Strike beacons on compromised machines. [...] | Spam Malware | |||
| 2022-06-18 06:47:02 | MaliBot Android Banking Trojan targets Spain and Italy (lien direct) | >Malibot is a new Android malware targeting online banking and cryptocurrency wallet customers in Spain and Italy. F5 Labs researchers spotted a new strain of Android malware, named Malibot, that is targeting online banking and cryptocurrency wallet customers in Spain and Italy. The experts documented attacks against multiple banks, including UniCredit, Santander, CaixaBank, and CartaBCC. […] | Malware | |||
| 2022-06-17 20:40:00 | Ransomware and Phishing Remain IT\'s Biggest Concerns (lien direct) | Security teams - who are already fighting off malware challenges - are also facing renewed attacks on cloud assets and remote systems. | Malware | |||
| 2022-06-17 20:00:33 | Experts link Hermit spyware to Italian surveillance firm RCS Lab and a front company (lien direct) | >Experts uncovered an enterprise-grade surveillance malware dubbed Hermit used to target individuals in Kazakhstan, Syria, and Italy since 2019. Lookout Threat Lab researchers uncovered enterprise-grade Android surveillance spyware, named Hermit, used by the government of Kazakhstan to track individuals within the country. The latest samples of this spyware were detected by the researchers in April 2022, four […] | Malware Threat Cloud | APT 37 | ||
| 2022-06-17 16:02:35 | Panchan Peer-to-Peer Botnet (lien direct) | Akamai security researchers have released discovery on Panchan, a new peer-to-peer botnet and SSH worm that emerged in March and has been actively breaching Linux servers since. Panchan, written in Golang, utilizes its built-in concurrency features to maximize spreadability and execute malware modules. The malware also harvests SSH keys to perform lateral movement. To view […] | Malware | |||
| 2022-06-17 13:00:00 | Tackling 5 Challenges Facing Critical National Infrastructure Today (lien direct) | The stakes are high when protecting CNI from destructive malware and other threats. | Malware | |||
| 2022-06-17 10:20:40 | New MaliBot Android Banking Malware Poses as Cryptocurrency Mining App (lien direct) | A new Android banking malware named MaliBot has been discovered by cybersecurity researchers. The malware poses as a cryptocurrency mining app or the Chrome web browser to target users in Spain and Italy. MaliBot focuses on stealing financial information, like e-banking credentials, crypto wallet passwords, and sensitive personal details. It is also capable of snatching […] | Malware | |||
| 2022-06-17 10:17:19 | Russian RSocks botnet disrupted after hacking millions of devices (lien direct) | The U.S. Department of Justice has announced the disruption of the Russian RSocks malware botnet used to hijack millions of computers, Android smartphones, and IoT (Internet of Things) devices worldwide for use as proxy servers. [...] | Malware | |||
| 2022-06-17 09:23:15 | (Déjà vu) Several Data-Stealing Apps Remain on Google Play Store According to Cybersecurity Researchers (lien direct) | Cybersecurity researchers from Dr. Web claim to have spotted numerous apps on the Google Play Store in May with adware and information-stealing malware built in. According to the report, the most dangerous of these apps features spyware tools capable of stealing information from other apps’ notifications, mainly to capture one-time two-factor authentication (2FA) one-time passwords […] | Malware Tool | |||
| 2022-06-17 08:06:00 | New in Cybersecurity - Insights, threat trends, & RSA learnings (lien direct) | AT&T Business’ most recently #BizTalks Twitter Chat—What’s New in Cybersecurity—Insights, Threat Trends, & RSA Learnings—explored many emerging concepts in the cybersecurity industry. [Optional sentence: Our very own Tawnya Lancaster, AT&T Cybersecurity’s threat intelligence and trends Research lead, did a takeover of the @ATTBusiness Twitter handle to provide her point of view.] Head to the @ATTBusiness Twitter page—go.att.com/twchat—to see the full chat and learn more. It was an interesting conversation with diverse opinions. Here are some of the highlights. Adversary tactics The top question in terms of engagement was this one, and lots of interesting perspectives: A3: Human weakness remains the Achilles Heel of #cybersecurity. And human stupidity is not going to change any time soon. We are gullible creatures.#cybersecurity #biztalks #ATTinfluencer — Joseph Steinberg (@JosephSteinberg) June 15, 2022 A3.a: Rapidly evolving IoT malware & compromised personal devices as entry points into networks are trends. This shows an accelerated threat of home networks becoming entry points into corporate networks which has been an issue since 2020. #BizTalks #Cybersecurity #ATTInfluencer pic.twitter.com/1xoSZ304j7 — ��Tyler Cohen Wood (@TylerCohenWood) June 15, 2022 Ransomware is not new but is trending again because criminal hackers can easily get paid in crypto currencies. Also, many of those attacks are hybrid in nature, being automated and augmented with machine learning algorithms. #Cybersecurity, #BizTalks, #ATTInfluencer — Chuck Brooks (@ChuckDBrooks) June 15, 2022 A3… This fact has proven especially problematic during the COVID-19 pandemic and will remain so in the post-pandemic era as remote working has made it easier to carry out successful social engineering campaigns... #cybersecurity #biztalks #ATTinfluencer — Joseph Steinberg (@JosephSteinberg) June 15, 2022 | Ransomware Malware Threat Guideline | |||
| 2022-06-17 00:00:00 | Websites Hosting Fake Cracks Spread Updated CopperStealer Malware (lien direct) | We found updated samples of the CopperStealer malware infecting systems via websites hosting fake software.
|
Malware | |||
| 2022-06-16 17:53:41 | \'MaliBot\' Android Malware Steals Financial, Personal Information (lien direct) | Researchers at F5 Labs have nabbed a new Android malware family capable of exfiltrating financial and personal information after taking control of infected devices. | Malware | |||
| 2022-06-16 17:19:09 | Volexity Blames \'DriftingCloud\' APT For Sophos Firewall Zero-Day (lien direct) | Big-game malware hunters at Volexity are shining the spotlight on a sophisticated Chinese APT caught recently exploiting a Sophos firewall zero-day to plant backdoors and launch man-in-the-middle attacks. | Malware | |||
| 2022-06-16 17:07:04 | Microsoft Defender extends malware protection to macOS and Android-for a price (lien direct) | App also provides "security tips," checks the antivirus status of other devices. | Malware | |||
| 2022-06-16 17:00:00 | RSAC Startup Competition Focuses on Post-Cloud IT Infrastructure (lien direct) | A secure Web browser takes the top prize, and for the second year in a row malware detection is an afterthought. | Malware | |||
| 2022-06-16 15:43:57 | New MaliBot Android banking malware spreads as a crypto miner (lien direct) | Threat analysts have discovered a new Android malware strain named MaliBot, which poses as a cryptocurrency mining app or the Chrome web browser to target users in Italy and Spain. [...] | Malware Threat | |||
| 2022-06-16 09:30:53 | How Emotet is changing tactics in response to Microsoft\'s tightening of Office macro security (lien direct) | >Emotet malware is back with ferocious vigor, according to ESET telemetry in the first four months of 2022. Will it survive the ever-tightening controls on macro-enabled documents? | Malware | |||
| 2022-06-16 07:00:36 | Malicious apps continue to spread through the Google Play Store (lien direct) | >Researchers at antivirus firm Dr. Web discovered malware in the Google Play Store that was downloaded two million times. An investigation conducted by the antivirus firm Dr. Web in May resulted in the discovery of multiple adware and information-stealing malware on the official Google Play Store. However, the experts warn that info-stealing Trojans are the […] | Malware | |||
| 2022-06-16 03:05:49 | A Microsoft Office 365 Feature Could Help Ransomware Hackers Hold Cloud Files Hostage (lien direct) | A "dangerous piece of functionality" has been discovered in Microsoft 365 suite that could be potentially abused by a malicious actor to ransom files stored on SharePoint and OneDrive and launch attacks on cloud infrastructure. The cloud ransomware attack makes it possible to launch file-encrypting malware to "encrypt files stored on SharePoint and OneDrive in a way that makes them unrecoverable | Ransomware Malware | |||
| 2022-06-15 20:00:55 | MaliBot: A New Android Banking Trojan Spotted in the Wild (lien direct) | A new strain of Android malware has been spotted in the wild targeting online banking and cryptocurrency wallet customers in Spain and Italy, just weeks after a coordinated law enforcement operation dismantled FluBot. The information stealing trojan, codenamed MaliBot by F5 Labs, is as feature-rich as its counterparts, allowing it to steal credentials and cookies, bypass multi-factor | Malware | |||
| 2022-06-15 15:48:24 | Stealthy Symbiote Linux malware is after financial institutions (lien direct) | >Symbiote, the latest malware to hit Linux users, is a parasite more than anything. Protect against this banking credential stealer now! | Malware | |||
| 2022-06-15 15:02:30 | Désinstallez rapidement ces applications Android avant qu\'il ne soit trop tard (lien direct) | > Des chercheurs en sécurité ont découvert plusieurs applications Android intégrant des malwares. Toujours disponibles sur le Google Play Store, elles ont été téléchargées plus de deux millions de fois. Méfiance.
L'article Désinstallez rapidement ces applications Android avant qu'il ne soit trop tard est à retrouver sur 01net.com.
Des chercheurs en sécurité ont découvert plusieurs applications Android intégrant des malwares. Toujours disponibles sur le Google Play Store, elles ont été téléchargées plus de deux millions de fois. Méfiance.
L'article Désinstallez rapidement ces applications Android avant qu'il ne soit trop tard est à retrouver sur 01net.com. |
Malware | |||
| 2022-06-15 11:00:00 | New IceXLoader 3.0 – Developers Warm Up to Nim (lien direct) | FortiGuard Labs discovered version 3.0 of IceXLoader, a new malware loader. Read our blog for the technical details of how it behaves and the potential malware that it can deliver in an infected system.
|
Malware | |||
| 2022-06-15 08:58:24 | De plus en plus d\'attaques par ransomware, phishing et malware : comment y faire face ? (lien direct) | En 2021, les réseaux d'entreprise ont été attaqués 50% plus fréquemment qu'en 2020. En fin d'année, on comptabilisait plus de 900 attaques par organisation chaque semaine – un nombre très élevé qui ne devrait pas faiblir en 2022. La transformation digitale était déjà bien engagée avant la pandémie mais celle-ci a accéléré le mouvement, forçant les entreprises à fournir à leurs salariés un accès réseau où qu'ils soient, pour leur permettre d'utiliser les applications cloud internes avec l'Internet public et leur (...) - Points de Vue | Malware | |||
| 2022-06-15 08:43:00 | New peer-to-peer botnet Panchan hijacks Linux servers (lien direct) | Researchers warn of a new worm that's infecting Linux servers by brute-forcing and stealing SSH credentials. The hijacked servers are joined in a botnet and are used to mine cryptocurrency by loading mining programs directly in memory with no files on disk.Dubbed Panchan by researchers from Akamai, the malware is written in the Go programming language, which allows it to be platform independent. It first appeared in late March and has infected servers in all regions of the world since then, though Asia does seem to have a bigger concentration. The most impacted vertical seems to be education."This might be due to poor password hygiene, or it could be related to the malware's unique lateral movement capability with stolen SSH keys," the Akamai team said in a blog post. "Researchers in different academic institutions might collaborate more frequently, and require credentials to authenticate to machines that are outside of their organization/network, than employees in the business sector. To strengthen that hypothesis, we saw that some of the universities involved were from the same country - Spain, or others from the same region, like Taiwan and Hong Kong."To read this article in full, please click here | Malware | |||
| 2022-06-15 05:05:43 | Panchan: A New Golang-based Peer-To-Peer Botnet Targeting Linux Servers (lien direct) | A new Golang-based peer-to-peer (P2P) botnet has been spotted actively targeting Linux servers in the education sector since its emergence in March 2022. Dubbed Panchan by Akamai Security Research, the malware "utilizes its built-in concurrency features to maximize spreadability and execute malware modules" and "harvests SSH keys to perform lateral movement." The feature-packed | Malware | |||
| 2022-06-14 19:12:22 | Syslogk: Linux Rootkit with Hidden Backdoor Payload (lien direct) | FortiGuard Labs is aware of a report that a new rootkit for Linux that appears to be still in development was discovered. Namaed "Syslogk", the rootkit is based on Adore-Ng, an old open-source kernel rootkit for Linux. Syslogk is hides directories containing malicious files and does not load the hidden Rekoobe backdoor malware until specifically-crafted magic packets are received.Why is this Significant?This is significant because "Syslogk" is a Linux rootkit that is in development as such it may be used in real attacks in near future. The rootkit contains a new variant of Rekoobe backdoor that will be launched only upon receiving specifically crafted magic packets from the threat actor.What is Syslogk?Syslogk is a Linux rootkit that is reportedly based on an old open-source Linux kernel rootkit called "Adore-Ng".Syslogk rootkit is installed as kernel modules in the affected system and intercepts legitimate Linux commands in order to hide its files, folders, or processes. It can hide directories containing the malicious files dropped on the compromised machine, hides processes and network traffic, and remotely starts or stop payloads on demand. The rootkit is also capable of inspecting all TCP traffic. The rootkit also loads hidden Rekoobe backdoor only when it receives specifically-crafted magic packets from the threat actor.What is Rekoobe?Rekoobe is a Linux backdoor that is reportedly based on TinySHell, an open-source Unix backdoor. Rekoobe refers to its Command-and Control (C2) server and performs malicious activities based on remote commands it receives.What is the Status of Coverage?FortiGuard Labs provides the following coverage against Syslogk rootkit:Linux/Rootkit_Agent.BY!trFortiGuard Labs provides the following coverage against Rekoobe backdoor:Linux/Rekoobe.BLinux/Rekoobe.B!trLinux/Rekoobe.B!tr.bdrLinux/Rekoobe.D!trLinux/Rekoobe.F!trLinux/Rekoobe.N!trLinux/Agnt.A!trLinux/Agent.B!trLinux/Agent.BX!tr.bdrLinux/Agent.DL!trLinux/Agent.JO!trLinux/Agent.LF!trW32/Rekoobe.F!trW32/Multi.MIBSUN!tr.bdrELF/Rosta.487B.fam!tr.bdrAdware/AgentAdware/RekoobePossibleThreat | Malware Threat | |||
| 2022-06-14 19:07:50 | Active Exploitation of Confluence vulnerability (CVE-2022-26134) (lien direct) | FortiGuard Labs is aware that an unauthenticated remote code execution vulnerability in Confluence (CVE-2022-26134) continues to be exploited to deploy malware in the field. Deployed malware reportedly includes Cerber2021 ransomware, Hezb, coinminers and Dark.IoT. The vulnerability was patched on June 3rd, 2022. Why is this Significant?This is significant because CVE-2022-26134 is a newly patched Confluence vulnerability that continues to be exploited in the field and various malware were deployed to the affected systems upon successful exploitation.What is CVE-2022-26134?CVE-2022-26134 is a critical vulnerability affects Confluence Server and Data Center which the latest patch has not yet been applied. The vulnerability relates to an Object-Graph Navigation Language (OGNL) injection that could allow an unauthenticated user to execute arbitrary code on the compromised system.Atlassian released a fix on June 3rd, 2022.FortiGuard Labs previously published a Threat Signal on the subject. See the Appendix for a link to "New Confluence Vulnerability (CVE-2022-26134) Exploited in the Wild".What Malware were Deployed to the Compromised Servers?Malware such as Cerber2021 ransomware, Dark.IoT and coinminers such as Kinsing and XMRig miner are known to be deployed to the affected servers.What is the Status of Coverage?FortiGuard Labs detects the malicious samples that were known to be deployed through CVE-2022-21634 with the following AV signatures:W32/Filecoder.1104!tr.ransomELF/BitCoinMiner.HF!trELF/Mirai.A!trLinux/Agent.PZ!trLinux/CVE_2021_4034.G!trRiskware/CoinMinerAdware/MinerFortiGuard Labs released the following IPS signature against CVE-2022-26134 in version 21.331:Atlassian.Confluence.OGNL.Remote.Code.ExecutionInitially, the signature's default action was set to "pass", however the action was changed to "drop" from version 21.333. | Malware Vulnerability Threat | |||
| 2022-06-14 16:45:00 | New Syslogk Linux Kernel Rootkit Uses "Magic Packets" to Trigger Remote Backdoor Access (lien direct) | The malware can cloak a malicious payload that could be remotely controlled by an adversary | Malware | |||
| 2022-06-14 15:36:10 | Android malware on the Google Play Store gets 2 million downloads (lien direct) | Cybersecurity researchers have discovered adware and information-stealing malware on the Google Play Store last month, with at least five still available and having amassed over two million downloads. [...] | Malware |
To see everything:
Our RSS (filtrered)
