What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2019-09-05 13:00:43 | (Déjà vu) Check Point, VMware and Silver Peak Transform Branch Office SD-WAN with Cloud Security Services (lien direct) | By Russ Schafer, Head of Product Marketing, Security Platforms Enterprise security solutions enable branch offices to connect safely and reliably to the data center, the Internet and cloud applications. In the past, branches relied on centralized security gateways at their data center to protect the entire enterprise. Enterprises sent branch traffic to the data center… | Prediction | APT 39 | ||
| 2019-09-05 13:00:04 | Transforming Branch Security with Top-Rated Threat Prevention Cloud Services Integrated with VMware and Silver Peak SD-WAN (lien direct) | By Russ Schafer, Head of Product Marketing, Security Platforms Enterprise security solutions enable branch offices to connect safely and reliably to the data center, the Internet and cloud applications. In the past, branches relied on centralized security gateways at their data center to protect the entire enterprise. Enterprises sent branch traffic to the data center… | Threat Prediction | APT 39 | ||
| 2019-04-12 13:00:00 | Things I hearted this week 12th April 2019 (lien direct) |
Hello again to another weekly security roundup. This week, I have a slightly different spin on the roundup in that the net has been slightly widened to include broader technology topics from more than just this last week. However, all of the articles were written by ladies. With that, let’s dive straight in.
A beginner's guide to test automation
If you’re new to automated testing, you’re probably starting off with a lot of questions: How do I know which tests to automate? Why is automated testing useful for me and my team? How do I choose a tool or framework? The options for automated testing are wide open, and you may feel overwhelmed.
If so, this is a great article on how to get started.
A Beginner's Guide to Test Automation | Sticky Minds
_500_353.jpg) All roads lead to exploratory testing
When I’m faced with something to test – be it a feature in a software application or a collection of features in a release, my general preference is weighted strongly towards exploratory testing. When someone who doesn’t know a great deal about testing wants me or my team to do testing for them, I would love to educate them on why exploratory testing could be a strong part of the test strategy.
All roads lead to exploratory testing | Womentesters
While on the topic of testing
Testing Behaviours — Writing A Good Gherkin Script | Medium, Jo Mahadevan
Single-page, server-side, static… say what?
An emoji-filled learning journey about the trade-offs of different website architectures, complete with gifs, diagrams, and demo apps.
If you’ve been hanging around the internet, trying to build websites and apps, you may have heard some words in conversation like static site or server-side rendered (SSR) or single-page app (SPA).
But what do all of these words mean? How does each type of application architecture differ? What are the tradeoffs of each approach and which one should you use when building your website?
Single-Page, Server-Side, Static… say what? | Marie Chatfield
If, like me you enjoyed this post by Marie, check out some of her other posts which are great. Quick plug to Protocol-andia: Welcome to the Networking Neighborhood. A whimsical introduction to how computers talk to each other, and what exactly your requests are up to.
Strengthen your security posture: start with a cybersecurity framework
The 2017 Equifax data breach is expected to break all previous records for data breach costs, with Larry Ponemon, chairman of the Ponemon Institute, estimating the final cost to be more than $600 million.
Even non-enterprise-level organizations suffer severe consequences for data breaches. According to the National Cyber Security Alliance, mid-market companies pay more than $1 million in post-attack mitigation, and the average cost of a data breach to an SMB is $117,000 per incident. While estimates vary, approximately 60% of businesses who suffer a breach are forced to shut down business within 6 months.
It is mor
All roads lead to exploratory testing
When I’m faced with something to test – be it a feature in a software application or a collection of features in a release, my general preference is weighted strongly towards exploratory testing. When someone who doesn’t know a great deal about testing wants me or my team to do testing for them, I would love to educate them on why exploratory testing could be a strong part of the test strategy.
All roads lead to exploratory testing | Womentesters
While on the topic of testing
Testing Behaviours — Writing A Good Gherkin Script | Medium, Jo Mahadevan
Single-page, server-side, static… say what?
An emoji-filled learning journey about the trade-offs of different website architectures, complete with gifs, diagrams, and demo apps.
If you’ve been hanging around the internet, trying to build websites and apps, you may have heard some words in conversation like static site or server-side rendered (SSR) or single-page app (SPA).
But what do all of these words mean? How does each type of application architecture differ? What are the tradeoffs of each approach and which one should you use when building your website?
Single-Page, Server-Side, Static… say what? | Marie Chatfield
If, like me you enjoyed this post by Marie, check out some of her other posts which are great. Quick plug to Protocol-andia: Welcome to the Networking Neighborhood. A whimsical introduction to how computers talk to each other, and what exactly your requests are up to.
Strengthen your security posture: start with a cybersecurity framework
The 2017 Equifax data breach is expected to break all previous records for data breach costs, with Larry Ponemon, chairman of the Ponemon Institute, estimating the final cost to be more than $600 million.
Even non-enterprise-level organizations suffer severe consequences for data breaches. According to the National Cyber Security Alliance, mid-market companies pay more than $1 million in post-attack mitigation, and the average cost of a data breach to an SMB is $117,000 per incident. While estimates vary, approximately 60% of businesses who suffer a breach are forced to shut down business within 6 months.
It is mor |
Guideline Prediction | Equifax APT 39 | ||
| 2019-04-11 13:00:03 | Protect Your Business by Managing Network Security from the Palm of Your Hand (lien direct) | by Russ Schafer, Head of Product Marketing, Security Platforms, published April 11th 2019 Next generation cyber security attacks can happen at any time to any size business, so you need to be prepared to react immediately. Based on the 2018 Verizon Data Breach report, 58% of security breach victims are categorized as small… | Data Breach Prediction | APT 39 | ||
| 2019-03-05 21:23:03 | Iran-Linked Chafer APT recently used python-based backdoor (lien direct) | The Iran-linked Chafer APT group used a new Python-based backdoor in recent attacks aimed at a Turkish government entity. The Iran-linked Chafer APT group used a new Python-based backdoor in attacks carried out in November 2018 that targeted a Turkish government entity. The Chafer APT group has distributed data stealer malware since at least mid-2014, […] | Malware Prediction | APT 39 | ||
| 2019-03-05 15:30:05 | Iran-Linked Hackers Use Python-Based Backdoor in Recent Attacks (lien direct) | The Iran-linked Chafer threat group has used a new Python-based backdoor in November 2018 attacks targeting a Turkish government entity, Palo Alto Networks reveals. | Threat Prediction | APT 39 | ||
| 2019-01-30 08:58:00 | Iran-Linked APT39 group use off-the-shelf tools to steal data (lien direct) | An Iran-linked cyber-espionage group tracked as APT39 is carrying out a widespread campaign using a broad range of custom and off-the-shelf tools. The APT39 cyberespionage group is carrying out a widespread campaign using a broad range of custom and off-the-shelf tools. The group has been active at least since November 2014, its operations are aligned […] | Prediction | APT 39 | ||
| 2018-03-08 21:11:01 | Chafer : un groupe de cyber attaquants basé en Iran (lien direct) | Un groupe de pirates informatiques, baptisé Chafer s’attaquerait aux entreprises du monde entier. Des amateurs du blackmarket... L'article Chafer : un groupe de cyber attaquants basé en Iran est apparu en premier sur Data Security Breach. | Prediction | APT 39 | ||
| 2018-03-01 19:06:00 | Iran-Linked Chafer Group Expands Toolset, Targets List (lien direct) | The Iran-based targeted attack group known as "Chafer" has been expanding its target list in the Middle East and beyond and adding new tools to its cyberweapon arsenal, Symantec warns. | Prediction | APT 39 | ||
| 2018-03-01 15:32:02 | Iran Taps Chafer APT Group amid Civil Aviation Crisis (lien direct) | Iran’s Chafer hacking group is targeting aviation repair and maintenance firms in an apparent effort to obtain information needed to shore up the safety of that country’s fleet of domestic aircraft, according to research by the firm Symantec. When an Aseman Airlines flight crashed in bad weather in a mountainous region of southern Iran...Read the whole entry... _!fbztxtlnk!_ https://feeds.feedblitz.com/~/529622610/0/thesecurityledger -->» | Prediction | APT 39 | ||
| 2017-10-19 09:00:00 | Magnber Ransomware veut infecter uniquement les bonnes personnes Magniber Ransomware Wants to Infect Only the Right People (lien direct) |
L'utilisation du kit d'exploitation (EK) est en baisse depuis la fin de 2016;Cependant, une certaine activité reste cohérente.Le kit d'exploitation de magnitude est un tel exemple qui continue d'affecter les utilisateurs, en particulier dans la région de l'APAC.
Dans la figure 1, qui est basée sur les données recueillies en mars 2017, nous pouvons voir les régions affectées par l'activité EK de magnitude au cours des trois derniers mois de 2016 et les trois premiers mois de 2017.
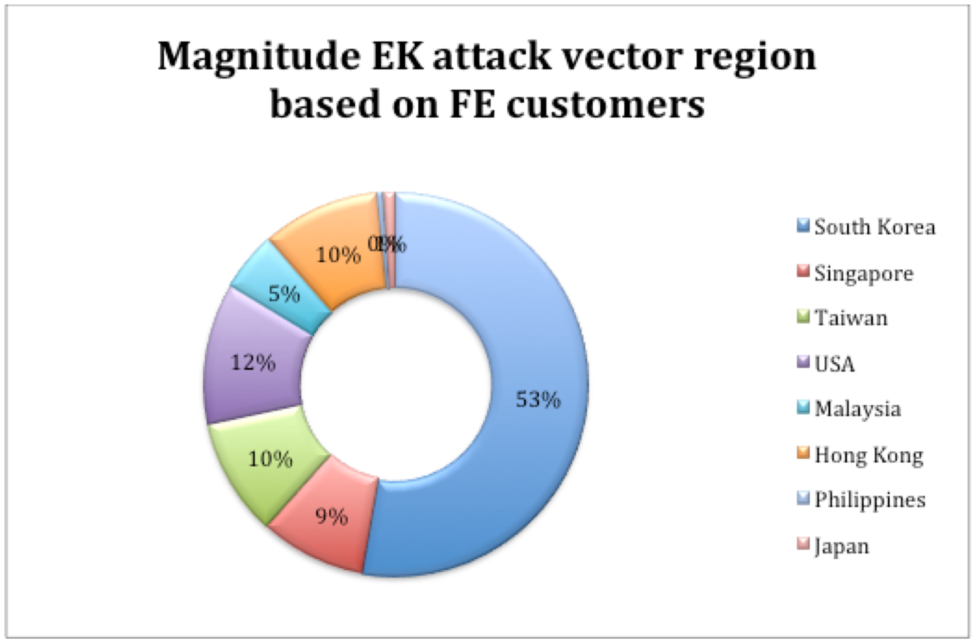 Figure 1: Distribution de l'amplitude EK comme le montre en mars 2017 Cette tendance s'est poursuivie jusqu'à la fin de septembre 2017, lorsque nous avons vu la magnitude EK se concentrer principalement sur la région de l'APAC, avec une grande partie ciblant la Corée du Sud.Activité EK de l'amplitude est ensuite tombée Figure 1: Distribution de l'amplitude EK comme le montre en mars 2017 Cette tendance s'est poursuivie jusqu'à la fin de septembre 2017, lorsque nous avons vu la magnitude EK se concentrer principalement sur la région de l'APAC, avec une grande partie ciblant la Corée du Sud.Activité EK de l'amplitude est ensuite tombée
Exploit kit (EK) use has been on the decline since late 2016; however, certain activity remains consistent. The Magnitude Exploit Kit is one such example that continues to affect users, particularly in the APAC region. In Figure 1, which is based on data gathered in March 2017, we can see the regions affected by Magnitude EK activity during the last three months of 2016 and the first three months of 2017.  Figure 1: Magnitude EK distribution as seen in March 2017This trend continued until late September 2017, when we saw Magnitude EK focus primarily on the APAC region, with a large chunk targeting South Korea. Magnitude EK activity then fell off Figure 1: Magnitude EK distribution as seen in March 2017This trend continued until late September 2017, when we saw Magnitude EK focus primarily on the APAC region, with a large chunk targeting South Korea. Magnitude EK activity then fell off |
Ransomware Prediction | ★★★ | ||
| 2016-08-22 07:00:00 | Piratage matériel intégré 101 & # 8211;Le lien Belkin Wemo Embedded Hardware Hacking 101 – The Belkin WeMo Link (lien direct) |
Pourquoi le piratage intégré?
Les appareils connectés à Internet ou exécutent un système d'exploitation complet deviennent de plus en plus répandus dans la société d'aujourd'hui.Des appareils pour les locomotives aux commutateurs d'éclairage sans fil, la tendance de l'Internet des objets (IoT) est en augmentation et ici pour rester.Cela a le potentiel de nous faciliter la vie;Cependant, la sensibilité croissante des appareils analogiques une fois permet également aux adversaires de les cibler et de les utiliser potentiellement.
Avec l'omniprésence de ces appareils connectés à Internet, il y a un excédent de «choses» à exploiter.L'intention principale de cet article de blog est
Why Embedded Hacking? Devices that are connected to the Internet or run a full operating system are becoming more and more prevalent in today\'s society. From devices for locomotives to wireless light switches, the Internet of Things (IoT) trend is on the rise and here to stay. This has the potential to make our lives much easier; however, the increasing sentience of once analog devices also enables adversaries to target them and potentially misuse them. With the ubiquity of these Internet-connected devices, there is a surplus of “Things” to exploit. The main intent of this blog post is |
Prediction Technical | ★★★★ |
To see everything:
Our RSS (filtrered)
