What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2024-02-28 06:00:52 | Briser la chaîne d'attaque: développer la position pour détecter les attaques de mouvement latérales Break the Attack Chain: Developing the Position to Detect Lateral Movement Attacks (lien direct) |
In this three-part “Break the Attack Chain” blog series, we look at how threat actors compromise our defenses and move laterally within our networks to escalate privileges and prepare for their final endgame. If one phrase could sum up the current state of the threat landscape, it is this: Threat actors don\'t break in. They log in. Rather than spend time trying to circumnavigate or brute force their way through our defenses, today\'s cybercriminals set their sights firmly on our users. Or to be more accurate, their highly prized credentials and identities. This remains true at almost every stage of the attack chain. Identities are not just an incredibly efficient way into our organizations, they also stand in the way of the most valuable and sensitive data. As a result, the cat-and-mouse game of cybersecurity is becoming increasingly like chess, with the traditional smash-and-grab approach making way for a more methodical M.O. Cybercriminals are now adept at moving laterally through our networks, compromising additional users to escalate privileges and lay the necessary groundwork for the endgame. While this more tactical gambit has the potential to do significant damage, it also gives security teams many more opportunities to spot and thwart attacks. If we understand the threat actor\'s playbook from the initial compromise to impact, we can follow suit and place protections along the length of the attack chain. Understanding the opening repertoire To continue our chess analogy, the more we understand our adversary\'s opening repertoire, the better equipped we are to counter it. When it comes to lateral movement, we can be sure that the vast majority of threat actors will follow the line of least resistance. Why attempt to break through defenses and risk detection when it is much easier to search for credentials that are stored on the compromised endpoint? This could be a search for password.txt files, stored Remote Desktop Protocol (RDP) credentials, and anything of value that could be sitting in the recycle bin. If it sounds scarily simple, that\'s because it is. This approach does not require admin privileges. It is unlikely to trigger any alarms. And unfortunately, it\'s successful time and time again. Proofpoint has found through our research that one in six endpoints contain an exploitable identity risk that allows threat actors to escalate privileges and move laterally using this data. (Learn more in our Analyzing Identity Risks report.) When it comes to large-scale attacks, DCSync is also now the norm. Nation-states and many hacking groups use it. It is so ubiquitous that if it were a zero-day, security leaders would be crying out for a patch. However, as there is general acceptance that Active Directory is so difficult to secure, there is also an acceptance that vulnerabilities like this will continue to exist. In simple terms, a DCSync attack allows a threat actor to simulate the behavior of a domain controller and retrieve password data on privileged users from Active Directory. And, once again, it is incredibly easy to execute. With a simple PowerShell command, threat actors can find users with the permissions they require. Add an off-the-shelf tool like Mimikatz into the mix, and within seconds, they can access every hash and every Active Directory privilege on the network. Mastering our defense With threat actors inside our organizations, it is too late for traditional perimeter protections. Instead, we must take steps to limit attackers\' access to further privileges and encourage them to reveal their movements. This starts with an assessment of our environment. Proofpoint Identity Threat Defense offers complete transparency, allowing security teams to see where they are most vulnerable. With this information, we can shrink the potential attack surface by increasing protections around privileged users and cleaning up endpoints to make it harder for cybercriminals to access valuable identities. With Proofpoin | Tool Vulnerability Threat | ★★★ | ||
| 2024-02-27 21:30:00 | Cutting avant, partie 3: Enquête sur Ivanti Connect Secure Secure VPN Exploitation et Tentatives de persistance Cutting Edge, Part 3: Investigating Ivanti Connect Secure VPN Exploitation and Persistence Attempts (lien direct) |
Les enquêtes de mandiant et ivanti \\ sur les larges et nbsp; Ivanti Exploitation zéro-jour se sont poursuivis à travers une variété de verticales de l'industrie, y compris le secteur de la base industrielle de la défense américaine.Après la publication initiale du 10 janvier 2024, Mandiant a observé des tentatives de masse pour exploiter ces vulnérabilités par un petit nombre d'acteurs de la menace de Chine-Nexus, et le développement d'un byligation d'exploitation de ciblage & nbsp; CVE-2024-21893 utilisé par & nbsp; unc5325 , que nous avons introduit dans notre & nbsp; " Cutting Edge, partie 2 "Blog Article . & nbsp; notamment, Mandiant a identifié unc5325 en utilisant une combinaison de vie-the-land (LOTL)
Mandiant and Ivanti\'s investigations into widespread Ivanti zero-day exploitation have continued across a variety of industry verticals, including the U.S. defense industrial base sector. Following the initial publication on Jan. 10, 2024, Mandiant observed mass attempts to exploit these vulnerabilities by a small number of China-nexus threat actors, and development of a mitigation bypass exploit targeting CVE-2024-21893 used by UNC5325, which we introduced in our "Cutting Edge, Part 2" blog post. Notably, Mandiant has identified UNC5325 using a combination of living-off-the-land (LotL) |
Vulnerability Threat Industrial | ★★ | ||
| 2024-02-27 20:13:00 | La vulnérabilité du plugin WordPress Litespeed met 5 millions de sites en danger WordPress LiteSpeed Plugin Vulnerability Puts 5 Million Sites at Risk (lien direct) |
Une vulnérabilité de sécurité a été divulguée dans le plugin de cache LiteSpeed pour WordPress qui pourrait permettre aux utilisateurs non authentifiés de dégénérer leurs privilèges.
Suivi en AS & NBSP; CVE-2023-40000, la vulnérabilité a été abordée en octobre 2023 dans la version 5.7.0.1.
"Ce plugin souffre d'une vulnérabilité non authentifiée à l'échelle du site [scripting inter-site] et pourrait permettre à tout utilisateur non authentifié
A security vulnerability has been disclosed in the LiteSpeed Cache plugin for WordPress that could enable unauthenticated users to escalate their privileges. Tracked as CVE-2023-40000, the vulnerability was addressed in October 2023 in version 5.7.0.1. "This plugin suffers from unauthenticated site-wide stored [cross-site scripting] vulnerability and could allow any unauthenticated user |
Vulnerability | ★★ | ||
| 2024-02-27 18:34:03 | Le nouveau sondage de Viokoo trouve que moins de la moitié des leaders informatiques sont confiants dans leurs plans de sécurité IoT New Viakoo Survey Finds Less Than Half of IT Leaders are Confident in their IoT Security Plans (lien direct) |
La nouvelle enquête de Viokoo trouve que moins de la moitié des leaders informatiques sont confiants dans leurs plans de sécurité IoT
71% des dirigeants informatiques souhaitent qu'ils commencent leurs plans de sécurité IoT différemment afin qu'ils puissent corriger les vulnérabilités plus rapidement
-
rapports spéciaux
New Viakoo Survey Finds Less Than Half of IT Leaders are Confident in their IoT Security Plans 71% of IT leaders wish they started their IoT security plans differently so they could remediate vulnerabilities faster - Special Reports |
Vulnerability Studies Industrial | ★★ | ||
| 2024-02-27 18:00:00 | 4 façons dont les organisations peuvent stimuler la demande de formation de sécurité des logiciels 4 Ways Organizations Can Drive Demand for Software Security Training (lien direct) |
Les programmes de sécurité axés sur les développeurs placent l'équipe de développement au centre de la réduction des vulnérabilités.
Developer-driven security programs place the development team at the center of reducing vulnerabilities. |
Vulnerability | ★★ | ||
| 2024-02-27 15:48:00 | La nouvelle vulnérabilité du visage étreint expose les modèles d'IA aux attaques de chaîne d'approvisionnement New Hugging Face Vulnerability Exposes AI Models to Supply Chain Attacks (lien direct) |
Les chercheurs en cybersécurité ont constaté qu'il était possible de compromettre le service de conversion de sauvegarde Face Sectetensors pour détourner les modèles soumis par les utilisateurs et entraîner des attaques de chaîne d'approvisionnement.
"Il est possible d'envoyer des demandes de traction malveillantes avec des données contrôlées par l'attaquant du service de visage étreint à n'importe quel référentiel sur la plate-forme, ainsi que de détourner tous les modèles soumis
Cybersecurity researchers have found that it\'s possible to compromise the Hugging Face Safetensors conversion service to ultimately hijack the models submitted by users and result in supply chain attacks. "It\'s possible to send malicious pull requests with attacker-controlled data from the Hugging Face service to any repository on the platform, as well as hijack any models that are submitted |
Vulnerability | ★★ | ||
| 2024-02-27 15:00:33 | Une recherche de sécurité des robots éducatifs An educational robot security research (lien direct) |
Les recherches en matière de sécurité sur un robot d'IA pour les enfants ont révélé plusieurs vulnérabilités permettant à un cybercriminal de prendre le contrôle des appareils et de bavarder avec l'enfant.
Security research into an AI robot for kids revealed several vulnerabilities enabling a cybercriminal to take over device control and to video-chat with the kid. |
Vulnerability | ★★ | ||
| 2024-02-27 13:00:37 | Avantages de l'ingestion de données d'Amazon Inspecteur dans la gestion de la vulnérabilité Cisco Benefits of Ingesting Data from Amazon Inspector into Cisco Vulnerability Management (lien direct) |
Découvrez comment vous pouvez ingérer vos résultats de vulnérabilité spécifiques au cloud d'Amazon Inspector dans la gestion de la vulnérabilité Cisco pour une hiérarchisation efficace.
Learn how you can ingest your cloud-specific vulnerability findings from Amazon Inspector into Cisco Vulnerability Management for effective prioritization. |
Vulnerability | ★★ | ||
| 2024-02-27 11:13:00 | Alerte du plugin WordPress - La vulnérabilité critique SQLI menace 200k + sites Web WordPress Plugin Alert - Critical SQLi Vulnerability Threatens 200K+ Websites (lien direct) |
Un défaut de sécurité critique a été divulgué dans un plugin WordPress populaire appelé & nbsp; Ultimate Member & NBSP; qui a plus de 200 000 installations actives.
La vulnérabilité, suivie comme CVE-2024-1071, a un score CVSS de 9,8 sur un maximum de 10. Le chercheur en sécurité Christiaan Swiers a été crédité de la découverte et de la signalement du défaut.
Dans un avis publié la semaine dernière, WordPress
A critical security flaw has been disclosed in a popular WordPress plugin called Ultimate Member that has more than 200,000 active installations. The vulnerability, tracked as CVE-2024-1071, carries a CVSS score of 9.8 out of a maximum of 10. Security researcher Christiaan Swiers has been credited with discovering and reporting the flaw. In an advisory published last week, WordPress |
Vulnerability | ★★★ | ||
| 2024-02-27 11:00:00 | L'évolution du point de terminaison - passant des critères de terminaison traditionnels aux charges de travail cloud ou conteneurisées et les solutions de sécurité pour les protéger The endpoint evolution - Evolving from traditional endpoints to cloud or containerized workloads and the security solutions to protect them (lien direct) |
As organizations grow and more endpoints are added across the enterprise, they create an increasingly broad attack surface sophisticated attackers are looking to compromise. According to the 2019 Endpoint Security Trends Report 70% of breaches originate at the endpoint¹. That is likely because endpoints typically represent the Intersection between humans and machines creating vulnerable points of entry for cybercriminals. This is why it is increasingly important to secure your endpoints.
Growth in endpoints
An endpoint is defined as any computing device that communicates back and forth with a network to which it is connected. Some end user devices serve as an interface with human users while others are servers that communicate with other endpoints on the network. Traditional endpoints began as physical devices including servers, workstations, desktops, and laptops, all connected to a corporate network. When smartphones and tablets became handheld computing devices with access to corporate email, document sharing and collaboration tools the number of endpoints at least doubled.
Then came the rise of the Internet of Things (IoT) including devices like printers, webcams, smartwatches, and thermostats, all of which are connected to the network. Industries like healthcare and manufacturing are using millions of IoT sensors to collect and exchange data. This continued growth in IoT only increases the number of endpoints that need to be protected.
Another contribution to the growth in endpoints is the migration to the cloud. It is estimated that 67% of enterprise infrastructure is cloud-based². This cloud transformation is the evolution from physical devices to virtualization and containerization.
Endpoint virtualization
The cloud is a multi-tenant environment where multiple users run services on the same server hardware. Virtualization and containerization are both virtualization technologies that separate the host operating system from the programs that run in them.
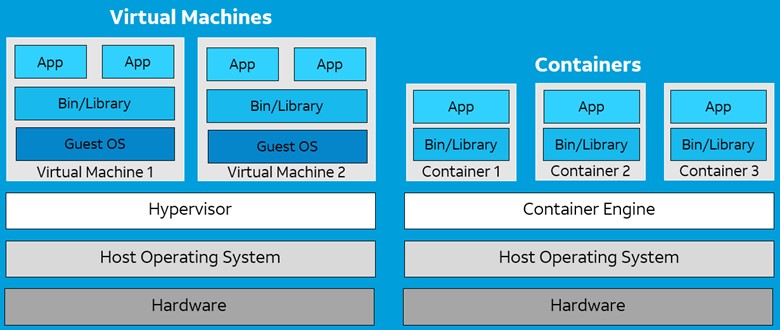 Virtualization is achieved using a hypervisor, which splits CPU, RAM, and storage resources between multiple virtual machines (VMs). Each VM behaves like a separate computer that gets a guest operating system and each VM is independent of each other. This allows organizations to run multiple OS instances on a single server.
Containerization, on the other hand, runs a single host OS instance and uses a container engine to help package applications into container images that can be easily deployed and re-used. By splitting each individual application function or microservice into containers they can operate independently to improve enterprise resilience and scalability. Kubernetes then manages the orchestration of multiple containers. VMs and containers present very different security challenges so let’s look at the evolution of endpoint security and the solutions that meet the needs of complex customer environments.
Securing endpoints
For decades, organizations have heavily relied on antivirus (AV) software to secure endpoints. However, traditional antivirus worked by matching known malicious signatures in a database and can no longer protect against today’s sophisticated threats. Modern endpoint security solutions are less signature-based and much more behavior-based. Endpoint protection platforms (EPP) offer cloud native architectures that provide a layered defense against fileless attacks using machine learning and behavioral AI to protect against malicious activity. Endpoint detection and response (EDR) solutions went beyond protection by recording and storing endpoint-system level behaviors to detect malicious threats.
EDR solutions use data analytics combined with threat intelligence feeds to provide incident responders with the forensic data for completing investigations and threat hunting. In addi
Virtualization is achieved using a hypervisor, which splits CPU, RAM, and storage resources between multiple virtual machines (VMs). Each VM behaves like a separate computer that gets a guest operating system and each VM is independent of each other. This allows organizations to run multiple OS instances on a single server.
Containerization, on the other hand, runs a single host OS instance and uses a container engine to help package applications into container images that can be easily deployed and re-used. By splitting each individual application function or microservice into containers they can operate independently to improve enterprise resilience and scalability. Kubernetes then manages the orchestration of multiple containers. VMs and containers present very different security challenges so let’s look at the evolution of endpoint security and the solutions that meet the needs of complex customer environments.
Securing endpoints
For decades, organizations have heavily relied on antivirus (AV) software to secure endpoints. However, traditional antivirus worked by matching known malicious signatures in a database and can no longer protect against today’s sophisticated threats. Modern endpoint security solutions are less signature-based and much more behavior-based. Endpoint protection platforms (EPP) offer cloud native architectures that provide a layered defense against fileless attacks using machine learning and behavioral AI to protect against malicious activity. Endpoint detection and response (EDR) solutions went beyond protection by recording and storing endpoint-system level behaviors to detect malicious threats.
EDR solutions use data analytics combined with threat intelligence feeds to provide incident responders with the forensic data for completing investigations and threat hunting. In addi |
Malware Tool Vulnerability Threat Mobile Cloud | ★★ | ||
| 2024-02-27 05:00:31 | Risque et ils le savent: 96% des utilisateurs de prise de risque sont conscients des dangers mais le font quand même, 2024 State of the Phish révèle Risky and They Know It: 96% of Risk-Taking Users Aware of the Dangers but Do It Anyway, 2024 State of the Phish Reveals (lien direct) |
We often-and justifiably-associate cyberattacks with technical exploits and ingenious hacks. But the truth is that many breaches occur due to the vulnerabilities of human behavior. That\'s why Proofpoint has gathered new data and expanded the scope of our 2024 State of the Phish report. Traditionally, our annual report covers the threat landscape and the impact of security education. But this time, we\'ve added data on risky user behavior and their attitudes about security. We believe that combining this information will help you to: Advance your cybersecurity strategy Implement a behavior change program Motivate your users to prioritize security This year\'s report compiles data derived from Proofpoint products and research, as well as from additional sources that include: A commissioned survey of 7,500 working adults and 1,050 IT professionals across 15 countries 183 million simulated phishing attacks sent by Proofpoint customers More than 24 million suspicious emails reported by our customers\' end users To get full access to our global findings, you can download your copy of the 2024 State of the Phish report now. Also, be sure to register now for our 2024 State of the Phish webinar on March 5, 2024. Our experts will provide more insights into the key findings and answer your questions in a live session. Meanwhile, let\'s take a sneak peek at some of the data in our new reports. Global findings Here\'s a closer look at a few of the key findings in our tenth annual State of the Phish report. Survey of working adults In our survey of working adults, about 71%, said they engaged in actions that they knew were risky. Worse, 96% were aware of the potential dangers. About 58% of these users acted in ways that exposed them to common social engineering tactics. The motivations behind these risky actions varied. Many users cited convenience, the desire to save time, and a sense of urgency as their main reasons. This suggests that while users are aware of the risks, they choose convenience. The survey also revealed that nearly all participants (94%) said they\'d pay more attention to security if controls were simplified and more user-friendly. This sentiment reveals a clear demand for security tools that are not only effective but that don\'t get in users\' way. Survey of IT and information security professionals The good news is that last year phishing attacks were down. In 2023, 71% of organizations experienced at least one successful phishing attack compared to 84% in 2022. The bad news is that the consequences of successful attacks were more severe. There was a 144% increase in reports of financial penalties. And there was a 50% increase in reports of damage to their reputation. Another major challenge was ransomware. The survey revealed that 69% of organizations were infected by ransomware (vs. 64% in 2022). However, the rate of ransom payments declined to 54% (vs. 64% in 2022). To address these issues, 46% of surveyed security pros are increasing user training to help change risky behaviors. This is their top strategy for improving cybersecurity. Threat landscape and security awareness data Business email compromise (BEC) is on the rise. And it is now spreading among non-English-speaking countries. On average, Proofpoint detected and blocked 66 million BEC attacks per month. Other threats are also increasing. Proofpoint observed over 1 million multifactor authentication (MFA) bypass attacks using EvilProxy per month. What\'s concerning is that 89% of surveyed security pros think MFA is a “silver bullet” that can protect them against account takeover. When it comes to telephone-oriented attack delivery (TOAD), Proofpoint saw 10 million incidents per month, on average. The peak was in August 2023, which saw 13 million incidents. When looking at industry failure rates for simulated phishing campaigns, the finance industry saw the most improvement. Last year the failure rate was only 9% (vs. 16% in 2022). “Resil | Ransomware Tool Vulnerability Threat Studies Technical | ★★★★ | ||
| 2024-02-27 00:12:58 | La Maison Blanche exhorte le passage aux langues sûres de la mémoire White House Urges Switching to Memory Safe Languages (lien direct) |
Le Bureau du Rapport technique du National Cyber Director se concentre sur la réduction des vulnérabilités de sécurité de la mémoire dans les applications et de rendre plus difficile pour les acteurs malveillants de les exploiter.
The Office of the National Cyber Director technical report focuses on reducing memory-safety vulnerabilities in applications and making it harder for malicious actors to exploit them. |
Vulnerability Threat Technical | ★★ | ||
| 2024-02-27 00:00:00 | Microsoft boosts its Microsoft 365 Insider Builds on Windows Bounty Program with higher awards and an expanded scope (lien direct) | À partir d'aujourd'hui, nous doublons la récompense maximale pour le programme de primes de bug d'initié Microsoft 365 à 30 000 USD pour des scénarios à fort impact, tels que l'exécution de code non sandbox non authentifiée sans interaction utilisateur.Nous élargissons également la portée de notre programme de primes pour inclure plus de types et de produits de vulnérabilité.
Starting today, we are doubling the maximum bounty award for the Microsoft 365 Insider Bug Bounty Program to $30,000 USD for high impact scenarios, such as unauthenticated non-sandboxed code execution with no user interaction. We are also expanding the scope of our bounty program to include more vulnerability types and products. |
Vulnerability | ★★★ | ||
| 2024-02-27 00:00:00 | Les groupes d'acteurs de menace, dont Black Basta, exploitent les vulnérabilités récentes de Screenconnect Threat Actor Groups, Including Black Basta, are Exploiting Recent ScreenConnect Vulnerabilities (lien direct) |
Cette entrée de blog donne une analyse détaillée de ces vulnérabilités récentes de ScreenConnect.Nous discutons également de notre découverte de groupes d'acteurs de menace, notamment Black Basta et Bl00dy Ransomware Gangs, qui exploitent activement CVE-2024-1708 et CVE-2024-1709 sur la base de notre télémétrie.
This blog entry gives a detailed analysis of these recent ScreenConnect vulnerabilities. We also discuss our discovery of threat actor groups, including Black Basta and Bl00dy Ransomware gangs, that are actively exploiting CVE-2024-1708 and CVE-2024-1709 based on our telemetry. |
Ransomware Vulnerability Threat | ★★★ | ||
| 2024-02-26 19:43:10 | ONCD publie un rapport sur l'adoption de langues sécurisées ONCD releases report on the adoption of memory-safe languages (lien direct) |
> L'effort vise à réduire l'une des vulnérabilités les plus courantes qui affligent les logiciels.
>The effort is aimed at reducing one of the most common vulnerabilities that plague software. |
Vulnerability | ★★★ | ||
| 2024-02-26 17:45:00 | La Maison Blanche exhorte l'industrie technologique à éliminer les vulnérabilités de la sécurité de la mémoire White House Urges Tech Industry to Eliminate Memory Safety Vulnerabilities (lien direct) |
Un nouveau rapport de la Maison Blanche a exhorté les développeurs de logiciels et de matériel à adopter des langages de programmation en toute sécurité et à éliminer l'une des classes de bogues les plus omniprésents
A new White House report has urged software and hardware developers to adopt memory safe programming languages, and eliminate one of the most pervasive classes of bugs |
Vulnerability | ★★★ | ||
| 2024-02-26 16:34:42 | La Maison Blanche exhorte les développeurs à passer à des langages de programmation sécurisés par la mémoire White House urges devs to switch to memory-safe programming languages (lien direct) |
Le bureau de la Maison Blanche du National Cyber Director (ONCD) a exhorté les entreprises technologiques aujourd'hui à passer aux langages de programmation en matière de mémoire, tels que Rust, pour améliorer la sécurité des logiciels en réduisant le nombre de vulnérabilités de sécurité mémoire.[...]
The White House Office of the National Cyber Director (ONCD) urged tech companies today to switch to memory-safe programming languages, such as Rust, to improve software security by reducing the number of memory safety vulnerabilities. [...] |
Vulnerability | ★★★ | ||
| 2024-02-26 15:17:44 | Étapes pratiques pour prévenir les vulnérabilités d'injection SQL Practical Steps to Prevent SQL Injection Vulnerabilities (lien direct) |
Dans le paysage numérique d'aujourd'hui, les applications Web et les API sont constamment menacées par des acteurs malveillants qui cherchent à exploiter les vulnérabilités.Une attaque commune et dangereuse est une injection SQL.
Dans ce blog, nous explorerons les vulnérabilités et les attaques de l'injection de SQL, comprendrons leur niveau de gravité et fournirons des étapes pratiques pour les empêcher.En mettant en œuvre ces meilleures pratiques, vous pouvez améliorer la sécurité de vos applications Web et API.
Comprendre les vulnérabilités et les attaques de l'injection SQL
Les attaques d'injection SQL se produisent lorsque les pirates manipulent les requêtes SQL d'une application \\ pour obtenir un accès non autorisé, altérer la base de données ou perturber la fonctionnalité de l'application \\.Ces attaques peuvent entraîner une usurpation d'identité, un accès aux données non autorisé et des attaques enchaînées.
L'injection SQL est une technique où les pirates injectent des requêtes SQL malveillantes dans la base de données backend d'une application Web.Cette vulnérabilité survient lorsque l'application accepte la saisie de l'utilisateur comme une instruction SQL que la base de données…
In today\'s digital landscape, web applications and APIs are constantly under threat from malicious actors looking to exploit vulnerabilities. A common and dangerous attack is a SQL injection. In this blog, we will explore SQL injection vulnerabilities and attacks, understand their severity levels, and provide practical steps to prevent them. By implementing these best practices, you can enhance the security of your web applications and APIs. Understanding SQL Injection Vulnerabilities and Attacks SQL injection attacks occur when hackers manipulate an application\'s SQL queries to gain unauthorized access, tamper with the database, or disrupt the application\'s functionality. These attacks can lead to identity spoofing, unauthorized data access, and chained attacks. SQL injection is a technique where hackers inject malicious SQL queries into a web application\'s backend database. This vulnerability arises when the application accepts user input as a SQL statement that the database… |
Vulnerability Threat Guideline Technical | ★★★ | ||
| 2024-02-26 13:56:26 | Russie Cyber Spies derrière Solarwinds Breach adoptant de nouvelles tactiques, avertissez cinq agences Eyes Russia cyber spies behind SolarWinds breach adopting new tactics, warn Five Eyes agencies (lien direct) |
 Les cyber-espions russes derrière la violation de Solarwinds adaptent leurs techniques pour pirater des organisations qui ont déplacé leurs réseaux dans des environnements hébergés dans le cloud, les responsables occidentaux avertissent.L'hébergement cloud a posé un défi pour les pirates, car il a effectivement réduit la surface d'attaque en termes de capacité à exploiter les vulnérabilités logicielles que les organisations
Les cyber-espions russes derrière la violation de Solarwinds adaptent leurs techniques pour pirater des organisations qui ont déplacé leurs réseaux dans des environnements hébergés dans le cloud, les responsables occidentaux avertissent.L'hébergement cloud a posé un défi pour les pirates, car il a effectivement réduit la surface d'attaque en termes de capacité à exploiter les vulnérabilités logicielles que les organisations
 The Russian cyber spies behind the SolarWinds breach are adapting their techniques to hack into organizations that have moved their networks into cloud-hosted environments, Western officials are warning. Cloud hosting has posed a challenge to hackers because it has effectively reduced the attack surface in terms of their ability to exploit software vulnerabilities that organizations
The Russian cyber spies behind the SolarWinds breach are adapting their techniques to hack into organizations that have moved their networks into cloud-hosted environments, Western officials are warning. Cloud hosting has posed a challenge to hackers because it has effectively reduced the attack surface in terms of their ability to exploit software vulnerabilities that organizations |
Hack Vulnerability Threat Cloud | ★★★ | ||
| 2024-02-26 13:55:25 | Tenable classe n ° 1 pour la cinquième année consécutive en partage de marché dans la gestion de la vulnérabilité des appareils Tenable Ranks #1 for Fifth Consecutive Year in Market Share in Device Vulnerability Management (lien direct) |
Tenable Ranks # 1 pour la cinquième année consécutive en partage de marché dans la gestion de la vulnérabilité des appareils
Crédits tenables Croissance des parts de marché à son approche de plate-forme et à l'étendue de la couverture des cyber-risques
-
magic quadrant
Tenable Ranks #1 for Fifth Consecutive Year in Market Share in Device Vulnerability Management Tenable credits market share growth to its platform approach and breadth of cyber risk coverage - MAGIC QUADRANT |
Vulnerability | ★ | ||
| 2024-02-26 11:00:00 | Construire une cyber-résilience contre l'ingénierie sociale alimentée par l'IA Building Cyber resilience against AI-powered social engineering (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Exploring advanced AI tactics in social engineering and effective strategies for cyber defense Long-standing as a significant threat in the business world, social engineering attacks constitute a major portion of global cyberattacks. An average business regularly faces a substantial number of such attacks every year. These attacks manifest in various forms, from intricate phishing emails to complex interactions designed to deceive employees, often leading to grave outcomes. This alarming reality is further underscored by the following statistics: · Social engineering is implicated in 98% of all cyberattacks · Approximately 90% of malicious data breaches occur due to social engineering · The typical organization faces over 700 social engineering attacks each year · The average cost incurred from a social engineering attack is about $130,000 | Malware Tool Vulnerability Threat | ★★ | ||
| 2024-02-24 17:00:00 | (Déjà vu) CVE-2024-0011 PAN-OS: Vulnérabilité des scripts croisés (XSS) réfléchis dans l'authentification portale en captivité (gravité: milieu) CVE-2024-0011 PAN-OS: Reflected Cross-Site Scripting (XSS) Vulnerability in Captive Portal Authentication (Severity: MEDIUM) (lien direct) |
Pas de details / No more details | Vulnerability | |||
| 2024-02-24 00:30:00 | Guide de correction et de durcissement pour ConnectWise Screenconnect Vulnérabilités (CVE-2024-1708 et CVE-2024-1709) Remediation and Hardening Guide for ConnectWise ScreenConnect Vulnerabilities (CVE-2024-1708 and CVE-2024-1709) (lien direct) |
Le 19 février 2024, ConnectWise a annoncé deux vulnérabilités pour leur produit ScreenConnect affectant (sur site) 23.9.7 et plus tôt: CVE-2024-1708 & # 8211;Vulnérabilité de contournement de l'authentification (10.0) CVE-2024-1709 & # 8211;Vulnérabilité de traversée de chemin (8.4) Ces vulnérabilités permettent à un acteur non authentifié de contourner l'authentification et d'accès à des environnements screenconnets qui peuvent êtreDerrière un pare-feu d'entreprise. & nbsp; connectWise a publié un & nbsp; version usée du produit Screenconnect (23.9.8+) qui atténue les vulnérabilités.ConnectWise a supprimé les restrictions de licence, donc Screenconnect aux consommateurs qui
On Feb. 19, 2024, ConnectWise announced two vulnerabilities for their ScreenConnect product affecting (on-premises) versions 23.9.7 and earlier:CVE-2024-1708 – Authentication Bypass Vulnerability (10.0)CVE-2024-1709 – Path Traversal Vulnerability (8.4)These vulnerabilities allow an unauthenticated actor to bypass authentication, and access ScreenConnect environments that may be behind a corporate firewall. ConnectWise released an updated version of the ScreenConnect product (23.9.8+) that mitigates the vulnerabilities. ConnectWise has removed license restrictions so ScreenConnect consumers who |
Vulnerability | ★★★ | ||
| 2024-02-23 16:14:27 | Sites Web de piratage AIS AIs Hacking Websites (lien direct) |
nouveau recherche :
les agents LLM peuvent pirater de manière autonome les sites Web
Résumé: Ces dernières années, les modèles de grandes langues (LLM) sont devenus de plus en plus capables et peuvent désormais interagir avec les outils (c'est-à-dire les fonctions d'appel), lire des documents et s'appeler récursivement.En conséquence, ces LLM peuvent désormais fonctionner de manière autonome en tant qu'agents.Avec l'augmentation des capacités de ces agents, les travaux récents ont spéculé sur la façon dont les agents LLM affecteraient la cybersécurité.Cependant, on ne sait pas grand-chose sur les capacités offensives des agents LLM.
Dans ce travail, nous montrons que les agents LLM peuvent pirater de manière autonome des sites Web, effectuant des tâches aussi complexes que l'extraction de schéma de base de données aveugle et les injections SQL sans rétroaction humaine.Surtout, l'agent n'a pas besoin de connaître au préalable la vulnérabilité.Cette capacité est de manière unique par des modèles frontières qui sont très capables d'utiliser des outils et de tirer parti du contexte étendu.À savoir, nous montrons que le GPT-4 est capable de ces hacks, mais les modèles open-source existants ne le sont pas.Enfin, nous montrons que GPT-4 est capable de trouver de manière autonome des vulnérabilités dans les sites Web à l'état sauvage.Nos résultats soulèvent des questions sur le déploiement généralisé de LLMS ...
New research: LLM Agents can Autonomously Hack Websites Abstract: In recent years, large language models (LLMs) have become increasingly capable and can now interact with tools (i.e., call functions), read documents, and recursively call themselves. As a result, these LLMs can now function autonomously as agents. With the rise in capabilities of these agents, recent work has speculated on how LLM agents would affect cybersecurity. However, not much is known about the offensive capabilities of LLM agents. In this work, we show that LLM agents can autonomously hack websites, performing tasks as complex as blind database schema extraction and SQL injections without human feedback. Importantly, the agent does not need to know the vulnerability beforehand. This capability is uniquely enabled by frontier models that are highly capable of tool use and leveraging extended context. Namely, we show that GPT-4 is capable of such hacks, but existing open-source models are not. Finally, we show that GPT-4 is capable of autonomously finding vulnerabilities in websites in the wild. Our findings raise questions about the widespread deployment of LLMs... |
Hack Tool Vulnerability | ★★ | ||
| 2024-02-23 13:21:51 | La vulnérabilité des raccourcis Apple expose des informations sensibles Apple Shortcuts Vulnerability Exposes Sensitive Information (lien direct) |
> La vulnérabilité de haute sévérité dans les raccourcis Apple pourrait entraîner une fuite d'informations sensibles à la connaissance de l'utilisateur.
>High-severity vulnerability in Apple Shortcuts could lead to sensitive information leak without user\'s knowledge. |
Vulnerability | ★★★ | ||
| 2024-02-23 12:53:03 | Groupes de cybercrimins exploitant activement \\ 'Catastrophic \\' Screenconnect Bogue Cybercriminal groups actively exploiting \\'catastrophic\\' ScreenConnect bug (lien direct) |
 Une vulnérabilité de sécurité dans un outil d'accès à distance disponible dans le commerce est exploitée par des criminels de ransomware quelques jours seulement après la première fois.La vulnérabilité spécifique, affectant certaines versions du produit ScreenConnect de ConnectWise \\, a reçu le maximum score CVSS de 10 , indiquantqu'il représente une menace critique pour les organisations qui n'ont pas corrigé leur logiciel.
Une vulnérabilité de sécurité dans un outil d'accès à distance disponible dans le commerce est exploitée par des criminels de ransomware quelques jours seulement après la première fois.La vulnérabilité spécifique, affectant certaines versions du produit ScreenConnect de ConnectWise \\, a reçu le maximum score CVSS de 10 , indiquantqu'il représente une menace critique pour les organisations qui n'ont pas corrigé leur logiciel.
 A security vulnerability in a commercially available remote access tool is being exploited by ransomware criminals just days after first being disclosed. The specific vulnerability, affecting some versions of ConnectWise\'s ScreenConnect product, has been given the maximum CVSS score of 10, indicating that it poses a critical threat to organizations that haven\'t patched their software.
A security vulnerability in a commercially available remote access tool is being exploited by ransomware criminals just days after first being disclosed. The specific vulnerability, affecting some versions of ConnectWise\'s ScreenConnect product, has been given the maximum CVSS score of 10, indicating that it poses a critical threat to organizations that haven\'t patched their software. |
Ransomware Tool Vulnerability Threat | ★★ | ||
| 2024-02-23 12:25:12 | \\ 'slashandgrab \\' Vulnérabilité de déconnexion largement exploitée pour la livraison de logiciels malveillants \\'SlashAndGrab\\' ScreenConnect Vulnerability Widely Exploited for Malware Delivery (lien direct) |
Vulnérabilité ConnectWise Screenconnect suivie sous le nom de CVE-2024-1709 et Slashandgrab exploité pour fournir des ransomwares et autres logiciels malveillants.
ConnectWise ScreenConnect vulnerability tracked as CVE-2024-1709 and SlashAndGrab exploited to deliver ransomware and other malware. |
Ransomware Malware Vulnerability | ★★ | ||
| 2024-02-23 10:35:00 | Les chercheurs détaillent la vulnérabilité des récentes raccourcis zéro cliquez sur Apple \\ Researchers Detail Apple\\'s Recent Zero-Click Shortcuts Vulnerability (lien direct) |
Des détails ont émergé sur une faille de sécurité à haute sévérité maintenant paralysée dans l'application de raccourcis d'Apple \\ qui pourrait permettre à un raccourci d'accès à des informations sensibles sur l'appareil sans le consentement des utilisateurs.
La vulnérabilité, suivie comme & nbsp; CVE-2024-23204 & nbsp; (Score CVSS: 7,5), a été adressée par Apple le 22 janvier 2024, avec la sortie de & nbsp; iOS 17.3, iPados 17.3, & nbsp; macOS Sonoma 14.3 et & nbsp;
Details have emerged about a now-patched high-severity security flaw in Apple\'s Shortcuts app that could permit a shortcut to access sensitive information on the device without users\' consent. The vulnerability, tracked as CVE-2024-23204 (CVSS score: 7.5), was addressed by Apple on January 22, 2024, with the release of iOS 17.3, iPadOS 17.3, macOS Sonoma 14.3, and |
Vulnerability | ★★ | ||
| 2024-02-22 20:39:07 | La vulnérabilité des raccourcis Apple zéro cliquez sur un vol de données silencieux Zero-Click Apple Shortcuts Vulnerability Allows Silent Data Theft (lien direct) |
La vulnérabilité CVE-2024-23204, affectant l'application populaire de raccourcis d'Apple \\, suggère un besoin critique de sensibilisation à la sécurité continue dans l'écosystème macOS et IOS.
Vulnerability CVE-2024-23204, affecting Apple\'s popular Shortcuts app, suggests a critical need for ongoing security awareness in the macOS and iOS ecosystem. |
Vulnerability | ★★ | ||
| 2024-02-22 17:22:37 | La vulnérabilité des raccourcis Apple expose les données sensibles, mettez à jour maintenant! Apple Shortcuts Vulnerability Exposes Sensitive Data, Update Now! (lien direct) |
> Par waqas
Un autre jour, une autre vulnérabilité de sécurité Apple!
Ceci est un article de HackRead.com Lire le post original: La vulnérabilité des raccourcis Apple expose les données sensibles, mise à jour maintenant!
>By Waqas Another day, another Apple Security Vulnerability! This is a post from HackRead.com Read the original post: Apple Shortcuts Vulnerability Exposes Sensitive Data, Update Now! |
Vulnerability | ★★ | ||
| 2024-02-22 13:34:58 | Nouveau Screenconnect RCE Flaw exploité dans les attaques de ransomwares New ScreenConnect RCE flaw exploited in ransomware attacks (lien direct) |
Les attaquants exploitent une vulnérabilité de contournement d'authentification de gravité maximale pour violer les serveurs ScreenConnect non corrigées et déployer des charges utiles de ransomware de verrouillage sur les réseaux compromis.[...]
Attackers are exploiting a maximum severity authentication bypass vulnerability to breach unpatched ScreenConnect servers and deploy LockBit ransomware payloads on compromised networks. [...] |
Ransomware Vulnerability | ★★★ | ||
| 2024-02-22 11:00:00 | L'importance de la cybersécurité dans les services bancaires en ligne The importance of Cybersecurity in online banking (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. In our digitized world, online banking has become an integral part of managing your finances, offering unparalleled convenience. However, with this convenience comes an increasing need for robust cybersecurity measures. As you embrace the ease of handling your financial affairs online, understanding the importance of cybersecurity becomes paramount. This article delves into the critical role of cybersecurity in safeguarding your financial assets and personal information from the evolving risks associated with online banking. Risks associated with online banking Engaging in online banking exposes you to various risks that demand your vigilance. Financial data breaches, where cybercriminals exploit vulnerabilities to gain unauthorized access to sensitive information, pose a significant threat. Phishing attacks, disguised as legitimate communications, aim to trick you into disclosing personal details. Additionally, identity theft, a direct consequence of these breaches, can lead to severe financial implications. Recognizing these risks is the first step in fortifying your online banking experience and ensuring the protection of your valuable information. Beyond individual concerns, these risks reverberate through financial institutions, impacting their reputation. Financial losses and unauthorized activities not only harm individuals but also erode the trust customers place in their banks and reputational damage becomes a looming threat for financial institutions, highlighting the critical need for comprehensive cybersecurity measures. Offshore banking risks Offshore banking, while offering financial privacy and potential tax advantages, poses certain risks that individuals should be aware of. One significant concern is the potential for increased susceptibility to financial fraud and money laundering due to the less stringent regulations in some offshore jurisdictions. Additionally, the lack of transparency in offshore banking systems may create challenges in recovering funds in the event of disputes or legal issues. It\'s crucial for individuals engaging in offshore banking to carefully evaluate the regulatory environment, conduct thorough due diligence on financial institutions, and be aware of the potential risks associated with this financial strategy. The impact of cyber-attacks on individuals and financial institutions The fallout from cyber-attacks extends far beyond individual victims, leaving lasting effects on financial institutions. Instances of financial losses and unauthorized activities not only harm individuals but also erode the trust customers place in their banks. The repercussions of cyber-attacks reverberate through the broader financial landscape, extending well beyond the immediate impact on individual victims. It is sobering to consider that when a financial institution falls victim to a cyber-attack, the consequences are felt on a systemic level. Instances of financial losses and unauthorized activities create a ripple effect, compromising the overall integrity of the affected institution. The fallout includes not only the immediate financial implications | Vulnerability Threat | ★★ | ||
| 2024-02-22 09:45:00 | AVERTISSEMENT RANSOMWARE comme le bug CVSS 10.0 Screenconnect est exploité Ransomware Warning as CVSS 10.0 ScreenConnect Bug is Exploited (lien direct) |
Les chercheurs mettent en garde contre un «ransomware gratuit pour tout» après l'exploitation de la vulnérabilité de Screenconnect
Researchers warn of a “ransomware free-for-all” after ScreenConnect vulnerability is exploited |
Ransomware Vulnerability | ★★ | ||
| 2024-02-22 03:03:14 | Personnalisation de la sécurité avec la gestion de la configuration de la sécurité (SCM) Customizing Security with Security Configuration Management (SCM) (lien direct) |
De nombreuses violations des dix dernières années ont profité des paramètres de sécurité faibles ou inexistants.À l'inverse, par exemple, les entreprises qui ont configuré leur application Docker aux paramètres de sécurité recommandés par CIS pour les utilisateurs de conteneurs et les privilèges n'étaient pas aussi vulnérables aux exploits d'évasion des conteneurs.On peut dire qu'un changement de configuration a empêché de nombreuses violations.La gestion de la configuration de sécurité peut faire une énorme différence dans la réduction de la vulnérabilité d'une organisation.Comme indiqué dans un article précédent: «En tant que sujet à multiples facettes, le durcissement peut submerger les organisations lors de la conception ou de la modification ...
Many of the breaches of the past ten years have taken advantage of weak or nonexistent security settings. Conversely, for example, companies that configured their Docker application to the CIS recommended security settings for container users and privileges were not as vulnerable to container escape exploits. Arguably, a configuration change prevented many breaches. Security configuration management can make a huge difference in reducing an organization\'s vulnerability. As stated in a previous post : “As a multi-faceted topic, hardening may overwhelm organizations when designing or amending... |
Vulnerability | ★★ | ||
| 2024-02-22 02:00:00 | PAN-SA-2024-0002 Impact des vulnérabilités des navires qui fuites (CVE-2024-21626, CVE-2024-23651, CVE-2024-23652 et CVE-2024-23653) (gravité: aucun) PAN-SA-2024-0002 Impact of Leaky Vessels Vulnerabilities (CVE-2024-21626, CVE-2024-23651, CVE-2024-23652, and CVE-2024-23653) (Severity: NONE) (lien direct) |
Pas de details / No more details | Vulnerability | |||
| 2024-02-21 21:46:00 | Les nouvelles vulnérabilités Wi-Fi exposent les appareils Android et Linux aux pirates New Wi-Fi Vulnerabilities Expose Android and Linux Devices to Hackers (lien direct) |
Les chercheurs en cybersécurité ont identifié deux défauts de contournement d'authentification dans le logiciel Wi-Fi open source trouvé dans les appareils Android, Linux et Chromeos qui pourraient inciter les utilisateurs à rejoindre un clone malveillant d'un réseau légitime ou permettre à un attaquant de rejoindre un réseau de confiance sans un mot de passe.
Les vulnérabilités, suivies sous le nom de CVE-2023-52160 et CVE-2023-52161, ont été découvertes à la suite d'un
Cybersecurity researchers have identified two authentication bypass flaws in open-source Wi-Fi software found in Android, Linux, and ChromeOS devices that could trick users into joining a malicious clone of a legitimate network or allow an attacker to join a trusted network without a password. The vulnerabilities, tracked as CVE-2023-52160 and CVE-2023-52161, have been discovered following a |
Vulnerability Mobile | ★★ | ||
| 2024-02-21 15:22:14 | La vulnérabilité critique dans le plug-in VMware vSphere permet un détournement de session Critical Vulnerability in VMware vSphere Plug-in Allows Session Hijacking (lien direct) |
Les administrateurs sont invités à supprimer le plug-in d'authentification amélioré vulnérable de VSphere \\, qui a été abandonné il y a près de trois ans mais est toujours largement utilisé.
Admins are urged to remove vSphere\'s vulnerable Enhanced Authentication Plug-in, which was discontinued nearly three years ago but is still widely in use. |
Vulnerability | ★★★ | ||
| 2024-02-21 13:46:06 | Comprendre la loi UE AI: implications pour les agents de conformité des communications Understanding the EU AI Act: Implications for Communications Compliance Officers (lien direct) |
The European Union\'s Artificial Intelligence Act (EU AI Act) is set to reshape the landscape of AI regulation in Europe-with profound implications. The European Council and Parliament recently agreed on a deal to harmonize AI rules and will soon bring forward the final text. The parliament will then pass the EU AI Act into law. After that, the law is expected to become fully effective in 2026. The EU AI Act is part of the EU\'s digital strategy. When the act goes into effect, it will be the first legislation of its kind. And it is destined to become the “gold standard” for other countries in the same way that the EU\'s General Data Protection Regulation (GDPR) became the gold standard for privacy legislation. Compliance and IT executives will be responsible for the AI models that their firms develop and deploy. And they will need to be very clear about the risks these models present as well as the governance and the oversight that they will apply to these models when they are operated. In this blog post, we\'ll provide an overview of the EU AI Act and how it may impact your communications practices in the future. The scope and purpose of the EU AI Act The EU AI Act establishes a harmonized framework for the development, deployment and oversight of AI systems across the EU. Any AI that is in use in the EU falls under the scope of the act. The phrase “in use in the EU” does not limit the law to models that are physically executed within the EU. The model and the servers that it operates on could be located anywhere. What matters is where the human who interacts with the AI is located. The EU AI Act\'s primary goal is to ensure that AI used in the EU market is safe and respects the fundamental rights and values of the EU and its citizens. That includes privacy, transparency and ethical considerations. The legislation will use a “risk-based” approach to regulate AI, which considers a given AI system\'s ability to cause harm. The higher the risk, the stricter the legislation. For example, certain AI activities, such as profiling, are prohibited. The act also lays out governance expectations, particularly for high-risk or systemic-risk systems. As all machine learning (ML) is a subset of AI, any ML activity will need to be evaluated from a risk perspective as well. The EU AI Act also aims to foster AI investment and innovation in the EU by providing unified operational guidance across the EU. There are exemptions for: Research and innovation purposes Those using AI for non-professional reasons Systems whose purpose is linked to national security, military, defense and policing The EU AI Act places a strong emphasis on ethical AI development. Companies must consider the societal impacts of their AI systems, including potential discrimination and bias. And their compliance officers will need to satisfy regulators (and themselves) that the AI models have been produced and operate within the Act\'s guidelines. To achieve this, businesses will need to engage with their technology partners and understand the models those partners have produced. They will also need to confirm that they are satisfied with how those models are created and how they operate. What\'s more, compliance officers should collaborate with data scientists and developers to implement ethical guidelines in AI development projects within their company. Requirements of the EU AI Act The EU AI Act categorizes AI systems into four risk levels: Unacceptable risk High risk Limited risk Minimal risk Particular attention must be paid to AI systems that fall into the “high-risk” category. These systems are subject to the most stringent requirements and scrutiny. Some will need to be registered in the EU database for high-risk AI systems as well. Systems that fall into the “unacceptable risk” category will be prohibited. In the case of general AI and foundation models, the regulations focus on the transparency of models and the data used and avoiding the introduction of system | Vulnerability Threat Legislation | ★★ | ||
| 2024-02-21 12:18:14 | Screenconnect Critical Bug maintenant attaqué à mesure que le code d'exploit émerge ScreenConnect critical bug now under attack as exploit code emerges (lien direct) |
Les détails techniques et les exploits de preuve de concept sont disponibles pour les deux vulnérabilités que Connectwise a divulguées plus tôt cette semaine pour Screenconnect, son bureau à distance et son logiciel d'accès.[...]
Both technical details and proof-of-concept exploits are available for the two vulnerabilities ConnectWise disclosed earlier this week for ScreenConnect, its remote desktop and access software. [...] |
Vulnerability Threat Technical | ★★★ | ||
| 2024-02-21 11:04:00 | Alerte VMware: désinstaller EAP Now - Critical Flaw met Active Directory en danger VMware Alert: Uninstall EAP Now - Critical Flaw Puts Active Directory at Risk (lien direct) |
VMware exhorte les utilisateurs à désinstaller le plugin d'authentification amélioré décrété (EAP) après la découverte d'un défaut de sécurité critique.
Suivi en AS & NBSP; CVE-2024-22245 & NBSP; (CVSS Score: 9.6), la vulnérabilité a été décrite comme un bogue de relais d'authentification arbitraire.
"Un acteur malveillant pourrait tromper un utilisateur de domaine cible avec EAP installé dans son navigateur Web pour demander et relayer
VMware is urging users to uninstall the deprecated Enhanced Authentication Plugin (EAP) following the discovery of a critical security flaw. Tracked as CVE-2024-22245 (CVSS score: 9.6), the vulnerability has been described as an arbitrary authentication relay bug. "A malicious actor could trick a target domain user with EAP installed in their web browser into requesting and relaying |
Vulnerability | ★★ | ||
| 2024-02-21 11:00:00 | Le SoC moderne de Next Gen propulsé par l'IA The modern next gen SOC powered by AI (lien direct) |
AI is among the most disruptive technologies of our time. While AI/ML has been around for decades, it has become a hot topic with continued innovations in generative AI (GenAI) from start-up OpenAI to tech giants like Microsoft, Google, and Meta. When large language models (LLMs) combined with big data and behavior analytics, AI/ML can supercharge productivity and scale operations across every sector from healthcare to manufacturing, transportation, retail, finance, government & defense, telecommunications, media, entertainment, and more. Within the cybersecurity industry, SentinelOne, Palo Alto Networks, Cisco, Fortinet and others are pioneering AI in Cybersecurity. In a research report of the global markets by Allied Market Research, AI in Cybersecurity is estimated to surge to $154.8 billion in 2032 from $19.2 billion in 2022, rising at a CAGR of 23.6%. Challenges of the traditional SOC SIEM One of the challenges with the traditional Security Operations Center (SOC) is SOC analysts are overwhelmed by the sheer number of alerts that come from Security Information Event Management (SIEM). Security teams are bombarded with low fidelity alerts and spend considerable time separating them from high fidelity alerts. The alerts come from almost any sources across the enterprise and is further compounded with too many point solutions and with multi-vendor environment. The numerous tools and lack of integration across multiple vendor product solutions often require a great deal of manual investigation and analysis. The pressure that comes with having to keep up with vendor training and correlate data and logs into meaningful insights becomes burdensome. While multi-vendor, multi-source, and multi-layered security solutions provides a lot of data, without ML and security analytics, it also creates a lot of noise and a disparate view of the threat landscape with insufficient context. SOAR Traditional Security Orchestration and Automation Response (SOAR) platforms used by mature security operations teams to develop run playbooks that automate action responses from a library of APIs for an ecosystem of security solution is complex and expensive to implement, manage, and maintain. Often SOCs are playing catch up on coding and funding development cost for run playbooks making it challenging to maintain and scale the operations to respond to new attacks quickly and efficiently. XDR Extended Detection and Response (XDR) solves a lot of these challenges with siloed security solutions by providing a unified view with more visibility and better context from a single holistic data lake across the entire ecosystem. XDR provides prevention as well as detection and response with integration and automation capabilities across endpoint, cloud, and network. Its automation capabilities can incorporate basic common SOAR like functions to API connected security tools. It collects enriched data from multiple sources and applies big data and ML based analysis to enable response of policy enforcement using security controls throughout the infrastructure. AI in the modern next gen SOC The use of AI and ML are increasingly essential to cyber operations to proactively identify anomalies and defend against cyber threats in a hyperconnected digital world. Canalys research estimates suggest that more than 7 | Ransomware Malware Tool Vulnerability Threat Prediction Cloud | ★★ | ||
| 2024-02-21 07:52:27 | (Déjà vu) 2024 \\'s Cyber Battleground Fouileled: Escalating Ransomware Epidemic, The Evolution of Cyber Warfare Tactics and Strategic Use of IA in Defense & # 8211;Insignes du dernier rapport de sécurité de Check Point \\ 2024\\'s Cyber Battleground Unveiled: Escalating Ransomware Epidemic, the Evolution of Cyber Warfare Tactics and strategic use of AI in defense – Insights from Check Point\\'s Latest Security Report (lien direct) |
 clés à emporter: & middot;Menaces croissantes: le paysage de la cybersécurité fait face à une augmentation sans précédent des attaques de ransomwares, avec 1 organisations sur 10 visées à l'échelle mondiale en 2023. & Middot;Évolution des tactiques: les adversaires exploitent les vulnérabilités de jour zéro, utilisent des essuie-glaces perturbateurs, des tactiques RAAS (ransomwares en tant que service) et des dispositifs de bord cible, amplifiant la complexité des cybermenaces.& Middot;Défense alimentée par l'IA: l'intelligence artificielle apparaît comme un formidable défenseur, remodelant la façon dont nous empêchons, détectons et répondons aux cyberattaques.Obtenez le rapport de cybersécurité en 2024 dans le paysage tumultueux de la cybersécurité, où les menaces sont importantes et les adversaires deviennent de plus en plus sophistiqués, garder une longueur d'avance sur la courbe est primordial.Comme [& # 8230;] clés à emporter: & middot;Menaces croissantes: le paysage de la cybersécurité fait face à une augmentation sans précédent des attaques de ransomwares, avec 1 organisations sur 10 visées à l'échelle mondiale en 2023. & Middot;Évolution des tactiques: les adversaires exploitent les vulnérabilités de jour zéro, utilisent des essuie-glaces perturbateurs, des tactiques RAAS (ransomwares en tant que service) et des dispositifs de bord cible, amplifiant la complexité des cybermenaces.& Middot;Défense alimentée par l'IA: l'intelligence artificielle apparaît comme un formidable défenseur, remodelant la façon dont nous empêchons, détectons et répondons aux cyberattaques.Obtenez le rapport de cybersécurité en 2024 dans le paysage tumultueux de la cybersécurité, où les menaces sont importantes et les adversaires deviennent de plus en plus sophistiqués, garder une longueur d'avance sur la courbe est primordial.Comme [& # 8230;]
 Key Takeaways: · Rising Threats: Cybersecurity landscape faces an unprecedented surge in ransomware attacks, with 1 in every 10 organizations globally being targeted in 2023. · Evolution of Tactics: Adversaries exploit zero-day vulnerabilities, employ disruptive wipers, utlise emerging RaaS (Ransomware-as-a-Service) tactics and target edge devices, amplifying the complexity of cyber threats. · AI-Powered Defense: Artificial intelligence emerges as a formidable defender, reshaping how we prevent, detect, and respond to cyber attacks. Get the 2024 Cyber Security Report In the tumultuous landscape of cybersecurity, where threats loom large and adversaries grow increasingly sophisticated, staying ahead of the curve is paramount. As […] Key Takeaways: · Rising Threats: Cybersecurity landscape faces an unprecedented surge in ransomware attacks, with 1 in every 10 organizations globally being targeted in 2023. · Evolution of Tactics: Adversaries exploit zero-day vulnerabilities, employ disruptive wipers, utlise emerging RaaS (Ransomware-as-a-Service) tactics and target edge devices, amplifying the complexity of cyber threats. · AI-Powered Defense: Artificial intelligence emerges as a formidable defender, reshaping how we prevent, detect, and respond to cyber attacks. Get the 2024 Cyber Security Report In the tumultuous landscape of cybersecurity, where threats loom large and adversaries grow increasingly sophisticated, staying ahead of the curve is paramount. As […]
|
Ransomware Vulnerability Threat | ★ | ||
| 2024-02-21 07:49:18 | 2024\'s Cyber Battleground Unveiled: Escalating Ransomware Epidemic, the Evolution of Cyber Warfare Tactics and strategic use of AI in defense – Insights from Check Point\'s Latest Security Report (lien direct) | Takeaways clés: & middot; & # 160; & # 160; & # 160; & # 160; & # 160; & # 160; & # 160;Rising Menaces: Cybersecurity Landscape fait face à une augmentation sans précédent des attaques de ransomwares, avec 1 organisations sur 10 étant ciblées dans le monde en 2023. & Middot; & # 160; & # 160; & # 160; & # 160; & # 160; & # 160;; & # 160;Évolution des tactiques: les adversaires exploitent les vulnérabilités de jour zéro, utilisent des essuie-glaces perturbateurs, des tactiques RAAS (ransomwares en tant que service) et des dispositifs de bord cible, amplifiant la complexité des cybermenaces.& middot; & # 160; & # 160; & # 160; & # 160; & # 160; & # 160; & # 160;Défense alimentée par AI: artificiel [& # 8230;]
Key Takeaways: · Rising Threats: Cybersecurity landscape faces an unprecedented surge in ransomware attacks, with 1 in every 10 organizations globally being targeted in 2023. · Evolution of Tactics: Adversaries exploit zero-day vulnerabilities, employ disruptive wipers, utlise emerging RaaS (Ransomware-as-a-Service) tactics and target edge devices, amplifying the complexity of cyber threats. · AI-Powered Defense: Artificial […] |
Ransomware Vulnerability Threat Studies | ★★★★ | ||
| 2024-02-20 18:16:24 | \\ 'keytrap \\' dns bogue menace des pannes Internet généralisées \\'KeyTrap\\' DNS Bug Threatens Widespread Internet Outages (lien direct) |
Grâce à une vulnérabilité de sécurité de 24 ans suivie sous le nom de CVE-2023-50387, les attaquants pourraient bloquer les serveurs DNS avec un seul paquet malveillant, éliminant efficacement de larges étendues d'Internet.
Thanks to a 24-year-old security vulnerability tracked as CVE-2023-50387, attackers could stall DNS servers with just a single malicious packet, effectively taking out wide swaths of the Internet. |
Vulnerability | ★★★ | ||
| 2024-02-20 17:15:31 | Dragos rapporte une augmentation sans précédent des vulnérabilités OT, les signaux ont besoin d'améliorer les mesures de cybersécurité Dragos reports unprecedented surge in OT vulnerabilities, signals need for improved cybersecurity measures (lien direct) |
> De nouvelles données de recherche de la société de cybersécurité industrielle Dragos ont révélé que les vulnérabilités OT (technologie opérationnelle) se sont accumulées à un ...
>New research data from industrial cybersecurity firm Dragos disclosed that OT (operational technology) vulnerabilities have accumulated at an... |
Vulnerability Industrial | ★★★★ | ||
| 2024-02-20 16:08:00 | Flaws critiques trouvés dans ConnectWise ScreenConnect Software - Patch maintenant Critical Flaws Found in ConnectWise ScreenConnect Software - Patch Now (lien direct) |
ConnectWise a publié des mises à jour logicielles pour aborder deux défauts de sécurité dans son logiciel de bureau à distance Screenconnect et d'accès, y compris un bogue critique qui pourrait permettre l'exécution de code distant sur les systèmes affectés.
Les vulnérabilités & nbsp; qui manquent actuellement d'identifiants CVE, sont répertoriés ci-dessous -
Contournement d'authentification à l'aide d'un chemin ou d'un canal alternatif (score CVSS: 10.0)
Limitation inappropriée de
ConnectWise has released software updates to address two security flaws in its ScreenConnect remote desktop and access software, including a critical bug that could enable remote code execution on affected systems. The vulnerabilities, which currently lack CVE identifiers, are listed below - Authentication bypass using an alternate path or channel (CVSS score: 10.0) Improper limitation of |
Vulnerability | ★★ | ||
| 2024-02-20 16:00:00 | Joomla: plusieurs vulnérabilités XSS Joomla: Multiple XSS Vulnerabilities (lien direct) |
Notre solution de code propre, SonarCloud, nous a conduits à un problème de sécurité sévère dans le système populaire de gestion de contenu Joomla.
Our Clean Code solution, SonarCloud, led us to a severe security issue in the popular Content Management System Joomla. |
Vulnerability | ★★ | ||
| 2024-02-20 14:00:00 | Les applications Salesforce personnalisées à tort erronées exposent les données de l'entreprise Misconfigured Custom Salesforce Apps Expose Corporate Data (lien direct) |
Les entreprises utilisent généralement le langage de programmation de type Java pour personnaliser leurs instances Salesforce, mais les attaquants recherchent des vulnérabilités dans les applications.
Enterprises typically use the Java-like programming language to customize their Salesforce instances, but attackers are hunting for vulnerabilities in the apps. |
Vulnerability Threat | ★★ | ||
| 2024-02-20 13:10:33 | Sites Web piratés via la vulnérabilité dans Bricks Builder WordPress Plugin Websites Hacked via Vulnerability in Bricks Builder WordPress Plugin (lien direct) |
> Les attaquants exploitent un défaut d'exécution de code à distance récent dans le plugin WordPress du constructeur de briques pour déployer des logiciels malveillants.
>Attackers are exploiting a recent remote code execution flaw in the Bricks Builder WordPress plugin to deploy malware. |
Malware Vulnerability | ★★ | ||
| 2024-02-20 11:00:00 | Un guide fondamental pour la sécurité des points finaux A fundamental guide to endpoint security (lien direct) |
 Anyone that utilizes technology in their daily lives understands that it is ever-changing, and the sentiment is especially true within the cybersecurity industry. Adversaries continue to evolve with new tactics to bypass defenses, so it is necessary that the methods of detecting and preventing these threats do so at an even more rapid pace.
However, keeping up with all the changes can be quite difficult, even for the most seasoned cybersecurity professional. The way in which we work has changed not just in where but also in how. Today employees conduct business from multiple devices, with some being company-issued and others being privately owned. Sensitive data is being stored across many locations including on these devices, within corporate data centers, and in the cloud. This means that organizations likely need more than one technology to defend their endpoints against security breach or data loss. With cybersecurity vendors marketing a wide range of branded product names for their offers, it may be challenging to determine which are ideal for your particular environment. This article aims to help demystify the various endpoint security technologies you may come across during your research, highlight the primary differences, and explain how they can complement each other. This is not intended to be an exhaustive list and it should be noted that there are some technologies that may fall into more than one category, for example, endpoint and cloud security.
Four key endpoint security technologies
To begin, let’s define exactly what an endpoint is. At the most fundamental level, an endpoint is any device that connects and exchanges data on a network. That could include traditional desktop and laptop computers, tablets, smartphones, printers, and servers. Endpoints also encompass network appliances like routers, switches, or firewalls, and a wide range of IoT devices such as wearables, security cameras, sensors, and connected medical or manufacturing equipment. But we must also think beyond the physical devices and consider virtual machines that host applications and data in public or private clouds.
Although this may seem trivial, it is important to note because they all represent entry points into the network that can be exploited and opportunities for sensitive data loss. As such, they must all be accounted for when building an endpoint security strategy. The following are some of the more common endpoint security technologies you are likely to encounter:
Unified endpoint management (UEM) or mobile device management (MDM): There is a widely accepted concept within the cybersecurity industry that you cannot effectively protect what you can’t see. Therefore, the first step in building a comprehensive endpoint security policy is to inventory all the devices accessing your network, and this can be accomplished with UEM or MDM technologies. The primary difference between the two is that MDM is for iOS and Android operating systems (OS), while UEM includes those OS plus Windows and Mac operating systems--even productivity devices and wearables in some cases. Once the devices are discovered and profiled, administrators will be able to apply consistent security policies across them, regardless of where the endpoint is located.
A key feature of both UEM and MDM is that they allow an organization to set standards regarding the security posture of devices accessing the network. For example, rules can be created that a device cannot be jailbroken and must be running on the latest O
Anyone that utilizes technology in their daily lives understands that it is ever-changing, and the sentiment is especially true within the cybersecurity industry. Adversaries continue to evolve with new tactics to bypass defenses, so it is necessary that the methods of detecting and preventing these threats do so at an even more rapid pace.
However, keeping up with all the changes can be quite difficult, even for the most seasoned cybersecurity professional. The way in which we work has changed not just in where but also in how. Today employees conduct business from multiple devices, with some being company-issued and others being privately owned. Sensitive data is being stored across many locations including on these devices, within corporate data centers, and in the cloud. This means that organizations likely need more than one technology to defend their endpoints against security breach or data loss. With cybersecurity vendors marketing a wide range of branded product names for their offers, it may be challenging to determine which are ideal for your particular environment. This article aims to help demystify the various endpoint security technologies you may come across during your research, highlight the primary differences, and explain how they can complement each other. This is not intended to be an exhaustive list and it should be noted that there are some technologies that may fall into more than one category, for example, endpoint and cloud security.
Four key endpoint security technologies
To begin, let’s define exactly what an endpoint is. At the most fundamental level, an endpoint is any device that connects and exchanges data on a network. That could include traditional desktop and laptop computers, tablets, smartphones, printers, and servers. Endpoints also encompass network appliances like routers, switches, or firewalls, and a wide range of IoT devices such as wearables, security cameras, sensors, and connected medical or manufacturing equipment. But we must also think beyond the physical devices and consider virtual machines that host applications and data in public or private clouds.
Although this may seem trivial, it is important to note because they all represent entry points into the network that can be exploited and opportunities for sensitive data loss. As such, they must all be accounted for when building an endpoint security strategy. The following are some of the more common endpoint security technologies you are likely to encounter:
Unified endpoint management (UEM) or mobile device management (MDM): There is a widely accepted concept within the cybersecurity industry that you cannot effectively protect what you can’t see. Therefore, the first step in building a comprehensive endpoint security policy is to inventory all the devices accessing your network, and this can be accomplished with UEM or MDM technologies. The primary difference between the two is that MDM is for iOS and Android operating systems (OS), while UEM includes those OS plus Windows and Mac operating systems--even productivity devices and wearables in some cases. Once the devices are discovered and profiled, administrators will be able to apply consistent security policies across them, regardless of where the endpoint is located.
A key feature of both UEM and MDM is that they allow an organization to set standards regarding the security posture of devices accessing the network. For example, rules can be created that a device cannot be jailbroken and must be running on the latest O |
Ransomware Malware Tool Vulnerability Threat Mobile Medical Cloud | ★★ |
To see everything:
Our RSS (filtrered)
