What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2018-09-11 11:36:02 | Microsoft Issues Software Updates for 17 Critical Vulnerabilities (lien direct) | Times to gear up your systems and software.
Just a few minutes ago Microsoft released its latest monthly Patch Tuesday update for September 2018, patching a total of 61 security vulnerabilities, 17 of which are rated as critical, 43 are rated Important, and one Moderate in severity.
This month's security updates patch vulnerabilities in Microsoft Windows, Edge, Internet Explorer, MS Office,
|
Patching | |||
| 2018-09-10 17:33:17 | California\'s bad IoT law (lien direct) | California has passed an IoT security bill, awaiting the government's signature/veto. It's a typically bad bill based on a superficial understanding of cybersecurity/hacking that will do little improve security, while doing a lot to impose costs and harm innovation.It's based on the misconception of adding security features. It's like dieting, where people insist you should eat more kale, which does little to address the problem you are pigging out on potato chips. The key to dieting is not eating more but eating less. The same is true of cybersecurity, where the point is not to add “security features” but to remove “insecure features”. For IoT devices, that means removing listening ports and cross-site/injection issues in web management. Adding features is typical “magic pill” or “silver bullet” thinking that we spend much of our time in infosec fighting against.We don't want arbitrary features like firewall and anti-virus added to these products. It'll just increase the attack surface making things worse. The one possible exception to this is “patchability”: some IoT devices can't be patched, and that is a problem. But even here, it's complicated. Even if IoT devices are patchable in theory there is no guarantee vendors will supply such patches, or worse, that users will apply them. Users overwhelmingly forget about devices once they are installed. These devices aren't like phones/laptops which notify users about patching.You might think a good solution to this is automated patching, but only if you ignore history. Many rate “NotPetya” as the worst, most costly, cyberattack ever. That was launched by subverting an automated patch. Most IoT devices exist behind firewalls, and are thus very difficult to hack. Automated patching gets beyond firewalls; it makes it much more likely mass infections will result from hackers targeting the vendor. The Mirai worm infected fewer than 200,000 devices. A hack of a tiny IoT vendor can gain control of more devices than that in one fell swoop.The bill does target one insecure feature that should be removed: hardcoded passwords. But they get the language wrong. A device doesn't have a single password, but many things that may or may not be called passwords. A typical IoT device has one system for creating accounts on the web management interface, a wholly separate authentication system for services like Telnet (based on /etc/passwd), and yet a wholly separate system for things like debugging interfaces. Just because a device does the proscribed thing of using a unique or user generated password in the user interface doesn't mean it doesn't also have a bug in Telnet.That was the problem with devices infected by Mirai. The description that these were hardcoded passwords is only a superficial understanding of the problem. The real problem was that there were different authentication systems in the web interface and in other services like Telnet. Most of the devices vulnerable to Mirai did the right thing on the web interfaces (meeting the language of this law) requiring the user to create new passwords before operating. They just did the wrong thing elsewhere.People aren't really paying attention to what happened with Mirai. They look at the 20 billion new IoT devices that are going to be connected to the Internet by 2020 and believe Mirai is just the tip of the iceberg. But it isn't. The IPv4 Internet has only 4 billion addresses, which are pretty much already used up. This means those 20 billion won't be exposed to the public Internet like Mirai devices, but hidden behind firewalls that translate addresses. Thus, rather than Mirai presaging the future, it represents the last gasp of the past that is unlikely to come again.This law is backwards looking rather than forward looking. Forward looking, by far the most important t | Hack Threat Patching Guideline | NotPetya Tesla | ||
| 2018-08-28 03:06:03 | Podcast Episode 110: Why Patching Struts isn\'t Enough and Hacking Electricity Demand with IoT? (lien direct) | In this week's episode (#110): the second major flaw in Apache Struts 2 in as many years and has put the information security community on alert. But is this vulnerability as serious as the last, which resulted in the hack of the firm Equifax? We talk with an expert from the firm Synopsys. And: we've heard a lot about the risk of cyber...Read the whole entry... _!fbztxtlnk!_ https://feeds.feedblitz.com/~/566525656/0/thesecurityledger -->» |
Hack Vulnerability Patching | Equifax | ||
| 2018-08-23 20:22:03 | Experts Urge Rapid Patching of \'Struts\' Bug (lien direct) | In September 2017, Equifax disclosed that a failure to patch one of its Internet servers against a pervasive software flaw -- in a Web component known as Apache Struts -- led to a breach that exposed personal data on 147 million Americans. Now security experts are warning that blueprints showing malicious hackers how to exploit a newly-discovered Apache Struts bug are available online, leaving countless organizations in a rush to apply new updates and plug the security hole before attackers can use it to wriggle inside. | Patching | Equifax | ||
| 2018-08-14 11:36:00 | Microsoft Releases Patches for 60 Flaws-Two Under Active Attack (lien direct) | Get your update caps on.
Just a few minutes ago Microsoft released its latest monthly Patch Tuesday update for August 2018, patching a total of 60 vulnerabilities, of which 19 are rated as critical.
The updates patch flaws in Microsoft Windows, Edge Browser, Internet Explorer, Office, ChakraCore, .NET Framework, Exchange Server, Microsoft SQL Server and Visual Studio.
Two of these
|
Patching | ★★★★★ | ||
| 2018-08-08 13:28:00 | Chip maker TSMC will lose millions for not patching its computers (lien direct) | Taiwanese chip-making giant Taiwan Semiconductor Manufacturing Co. (TSMC), whose customers include Apple, Nvidia, AMD, Qualcomm, and Broadcom, was hit with a WannaCry infection last weekend that knocked out production for a few days and will cost the firm millions of dollars.Most chip companies are fabless, meaning they don't make their own chips. It's a massively expensive process, as Intel has learned. Most, like the aforementioned firms, simply design the chips and farm out the manufacturing process, and TSMC is by far the biggest player in that field.CEO C.C. Wei told Bloomberg that TSMC wasn't targeted by a hacker; it was an infected production tool provided by an unidentified vendor that was brought into the company. The company is overhauling its procedures after encountering a virus more complex than initially thought, he said. | Tool Patching | Wannacry | ||
| 2018-08-07 23:18:45 | What the Caesars (@DefCon) WiFi situation looks like (lien direct) | So I took a survey of WiFi at Caesar's Palace and thought I'd write up some results.When we go to DEF CON in Vegas, hundreds of us bring our WiFi tools to look at the world. Actually, no special hardware is necessary, as modern laptops/phones have WiFi built-in, while the operating system (Windows, macOS, Linux) enables “monitor mode”. Software is widely available and free. We still love our specialized WiFi dongles and directional antennas, but they aren't really needed anymore.It's also legal, as long as you are just grabbing header information and broadcasts. Which is about all that's useful anymore as encryption has become the norm -- we can pretty much only see what we are allowed to see. The days of grabbing somebody's session-cookie and hijacking their web email are long gone (though the was a fun period). There are still a few targets around if you want to WiFi hack, but most are gone.So naturally I wanted to do a survey of what Caesar's Palace has for WiFi during the DEF CON hacker conference located there.Here is a list of access-points (on channel 1 only) sorted by popularity, the number of stations using them. These have mind-blowing high numbers in the ~3000 range for “CAESARS”. I think something is wrong with the data.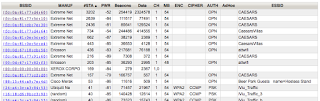 I click on the first one to drill down, and I find a source of the problem. I'm seeing only “Data Out” packets from these devices, not “Data In”. I click on the first one to drill down, and I find a source of the problem. I'm seeing only “Data Out” packets from these devices, not “Data In”.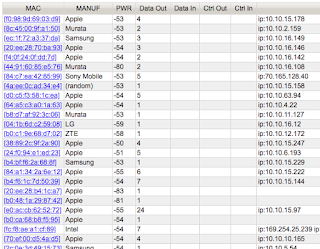 These are almost entirely ARP packets from devices, associated with other access-points, not actually associated with this access-point. The hotel has bridged (via Ethernet) all the access-points together. We can see this in the raw ARP packets, such as the one shown below: These are almost entirely ARP packets from devices, associated with other access-points, not actually associated with this access-point. The hotel has bridged (via Ethernet) all the access-points together. We can see this in the raw ARP packets, such as the one shown below: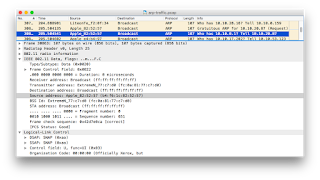 WiFi packets have three MAC addresses, the source and destination (as expected) and also the address of the access-point involved. The access point is the actual transmitter, but it's bridging the packet from some other location on the local Ethernet network.Apparently, CAESARS dumps all the guests into the address range 10.10.x.x, all going out through the router 10.10.0.1. We can see this from the ARP traffic, as everyone seems to be ARPing that router.I'm probably seeing all the devices on the CAESARS WiFi. In ot WiFi packets have three MAC addresses, the source and destination (as expected) and also the address of the access-point involved. The access point is the actual transmitter, but it's bridging the packet from some other location on the local Ethernet network.Apparently, CAESARS dumps all the guests into the address range 10.10.x.x, all going out through the router 10.10.0.1. We can see this from the ARP traffic, as everyone seems to be ARPing that router.I'm probably seeing all the devices on the CAESARS WiFi. In ot |
Patching | |||
| 2018-08-01 16:46:02 | An Open Letter to Microsoft About Poor Windows 10 Update Experiences (lien direct) | Susan Bradley, an 18 year Microsoft MVP focused on Windows patching and patch management, has sent an open letter to Microsoft executives Satya Nadella, Carlos Picoto, and Scott Guthrie about the frustration Windows 10 users have when dealing with installing new updates. [...] | Patching | |||
| 2018-07-12 19:54:20 | Your IoT security concerns are stupid (lien direct) | Lots of government people are focused on IoT security, such as this recent effort. They are usually wrong. It's a typical cybersecurity policy effort which knows the answer without paying attention to the question.Patching has little to do with IoT security. For one thing, consumers will not patch vulns, because unlike your phone/laptop computer which is all "in your face", IoT devices, once installed, are quickly forgotten. For another thing, the average lifespan of a device on your network is at least twice the duration of support from the vendor making patches available.Naive solutions to the manual patching problem, like forcing autoupdates from vendors, increase rather than decrease the danger. Manual patches that don't get applied cause a small, but manageable constant hacking problem. Automatic patching causes rarer, but more catastrophic events when hackers hack the vendor and push out a bad patch. People are afraid of Mirai, a comparatively minor event that led to a quick cleansing of vulnerable devices from the Internet. They should be more afraid of notPetya, the most catastrophic event yet on the Internet that was launched by subverting an automated patch of accounting software.Vulns aren't even the problem. Mirai didn't happen because of accidental bugs, but because of conscious design decisions. Security cameras have unique requirements of being exposed to the Internet and needing a remote factory reset, leading to the worm. While notPetya did exploit a Microsoft vuln, it's primary vector of spreading (after the subverted update) was via misconfigured Windows networking, not that vuln. In other words, while Mirai and notPetya are the most important events people cite supporting their vuln/patching policy, neither was really about vuln/patching.Such technical analysis of events like Mirai and notPetya are ignored. Policymakers are only cherrypicking the superficial conclusions supporting their goals. They assiduously ignore in-depth analysis of such things because it inevitably fails to support their positions, or directly contradicts them. IoT security is going to be solved regardless of what government does. All this policy talk is premised on things being static unless government takes action. This is wrong. Government is still waffling on its response to Mirai, but the market quickly adapted. Those off-brand, poorly engineered security cameras you buy for $19 from Amazon.com shipped directly from Shenzen now look very different, having less Internet exposure, than the ones used in Mirai. Major Internet sites like Twitter now use multiple DNS providers so that a DDoS attack on one won't take down their services.In addition, technology is fundamentally changing. Mirai attacked IPv4 addresses outside the firewall. The 100-billion IoT devices going on the network in the next decade will not work this way, cannot work this way, because there are only 4-billion IPv4 addresses. Instead, they'll be behind NATs or accessed via IPv6, both of which prevent Mirai-style worms from functioning. Your fridge and toaster won't connect via your home WiFi anyway, but via a 5G chip unrelated to your home.Lastly, focusing on the ven IoT security is going to be solved regardless of what government does. All this policy talk is premised on things being static unless government takes action. This is wrong. Government is still waffling on its response to Mirai, but the market quickly adapted. Those off-brand, poorly engineered security cameras you buy for $19 from Amazon.com shipped directly from Shenzen now look very different, having less Internet exposure, than the ones used in Mirai. Major Internet sites like Twitter now use multiple DNS providers so that a DDoS attack on one won't take down their services.In addition, technology is fundamentally changing. Mirai attacked IPv4 addresses outside the firewall. The 100-billion IoT devices going on the network in the next decade will not work this way, cannot work this way, because there are only 4-billion IPv4 addresses. Instead, they'll be behind NATs or accessed via IPv6, both of which prevent Mirai-style worms from functioning. Your fridge and toaster won't connect via your home WiFi anyway, but via a 5G chip unrelated to your home.Lastly, focusing on the ven |
Hack Patching Guideline | NotPetya | ||
| 2018-06-27 15:49:15 | Lessons from nPetya one year later (lien direct) | This is the one year anniversary of NotPetya. It was probably the most expensive single hacker attack in history (so far), with FedEx estimating it cost them $300 million. Shipping giant Maersk and drug giant Merck suffered losses on a similar scale. Many are discussing lessons we should learn from this, but they are the wrong lessons.An example is this quote in a recent article:"One year on from NotPetya, it seems lessons still haven't been learned. A lack of regular patching of outdated systems because of the issues of downtime and disruption to organisations was the path through which both NotPetya and WannaCry spread, and this fundamental problem remains." This is an attractive claim. It describes the problem in terms of people being "weak" and that the solution is to be "strong". If only organizations where strong enough, willing to deal with downtime and disruption, then problems like this wouldn't happen.But this is wrong, at least in the case of NotPetya.NotPetya's spread was initiated through the Ukraining company MeDoc, which provided tax accounting software. It had an auto-update process for keeping its software up-to-date. This was subverted in order to deliver the initial NotPetya infection. Patching had nothing to do with this. Other common security controls like firewalls were also bypassed.Auto-updates and cloud-management of software and IoT devices is becoming the norm. This creates a danger for such "supply chain" attacks, where the supplier of the product gets compromised, spreading an infection to all their customers. The lesson organizations need to learn about this is how such infections can be contained. One way is to firewall such products away from the core network. Another solution is port-isolation/microsegmentation, that limits the spread after an initial infection.Once NotPetya got into an organization, it spread laterally. The chief way it did this was through Mimikatz/PsExec, reusing Windows credentials. It stole whatever login information it could get from the infected machine and used it to try to log on to other Windows machines. If it got lucky getting domain administrator credentials, it then spread to the entire Windows domain. This was the primary method of spreading, not the unpatched ETERNALBLUE vulnerability. This is why it was so devastating to companies like Maersk: it wasn't a matter of a few unpatched systems getting infected, it was a matter of losing entire domains, including the backup systems.Such spreading through Windows credentials continues to plague organizations. A good example is the recent ransomware infection of the City of Atlanta that spread much the same way. The limits of the worm were the limits of domain trust relationships. For example, it didn't infect the city airport because that Windows domain is separate from the city's domains.This is the most pressing lesson organizations need to learn, the one they are ignoring. They need to do more to prevent desktops from infecting each other, such as through port-isolation/microsegmentation. They need to control the spread of administrative credentials within the organization. A lot of organizations put the same local admin account on every workstation which makes the spread of NotPetya style worms trivial. They need to reevaluate trust relationships between domains, so that the admin of one can't infect the others.These solutions are difficult, which is why news articles don't mention them. You don't have to know anything about security to proclaim "the problem is lack of patches". It's moral authority, chastising the weak, rather than a proscription of what to do. Solving supply chain hacks and Windows credential sharing, though, is hard. I don't know any universal solution to this -- I'd have to thoroughly analyze your network and business in order to | Ransomware Malware Patching | FedEx NotPetya Wannacry | ||
| 2018-03-07 18:41:05 | Technique Discovered That Can Mitigate Memcached DDoS Attacks (lien direct) | A mitigation mechanism is available for all victims who are under a DDoS attack carried out via Memcached servers. [...] | Patching | ★★★ | ||
| 2018-03-07 18:00:00 | Here\'s how Android P promises to protect your privacy (lien direct) | Android P could give even the most ardent iPhone fans a run for their money. | Patching | ★★★ | ||
| 2018-03-07 17:00:03 | Building an incident response program: creating the framework (lien direct) |
 An incident response plan does not need to be overly complicated. However, having a solid and tested framework for the program is key in the ability of an organization to respond to and survive a security incident.
Categories:
101
Business
Tags: gdprGeneral Data Protection RegulationIncident Responseincident response frameworkincident response program
(Read more...)
An incident response plan does not need to be overly complicated. However, having a solid and tested framework for the program is key in the ability of an organization to respond to and survive a security incident.
Categories:
101
Business
Tags: gdprGeneral Data Protection RegulationIncident Responseincident response frameworkincident response program
(Read more...)
|
Patching | ★★★ | ||
| 2018-02-28 14:59:00 | Intel Releases Updated Spectre Fixes For Broadwell and Haswell Chips (lien direct) | Intel has issued stable microcode to help protect its Broadwell and Haswell chips from the Spectre Variant 2 security exploits. | Patching | |||
| 2014-07-16 23:41:20 | Foxit PDF Reader Stored XSS (lien direct) | A friend of mine was performing an external pentest recently and he started to complain that his traditional Java exploits were not being effective. He was able to map a few applications and defenses in place protecting the client's network but he still needed an initial access to start pivoting.Basic protections like AV, application white-listing as well as more advanced ones like EMET are used to make the life of criminals (and pentesters) harder, but they're often bypassed. While discussing alternatives with my friend, he told me that the company replaced Adobe Reader after seeing lots of Security Advisories for the product. And what was the replacement? Foxit Reader: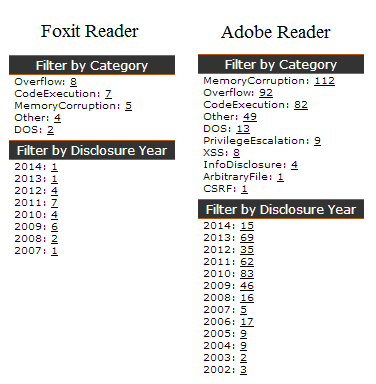 Advisories for Adobe Reader and Foxit Reader listed on OSVDB (May/2014)Less advisories means that the product is more secure, right? Marc Ruef's talk about VDB management summarizes this point: Advisories for Adobe Reader and Foxit Reader listed on OSVDB (May/2014)Less advisories means that the product is more secure, right? Marc Ruef's talk about VDB management summarizes this point: |
Malware Vulnerability Patching Guideline | ★★★★ | ||
| 2014-02-18 09:43:31 | Analyzing Malware for Embedded Devices: TheMoon Worm (lien direct) | All the media outlets are reporting that Embedded Malware is becoming mainstream. This is something totally new and we never heard of this before, right? The high number of Linux SOHO routers with Internet-facing administrative interfaces, the lack of firmware updates and the ease to craft exploits make them a perfect target for online criminals. The Internet of Threats is wildly insecure, but definitely not unpatchable.To all infosec people out there, it's important to understand these threats and report it properly to the media. Some top-notch researchers recently uncovered "Massive Botnets" infecting refrigerators, microwaves, gaming consoles, soda machines and tamagotchis. The problem is that they never provided any sort of evidence, no malware samples, no IOC's and did not write a Hakin9 article describing it. Refrigerator Botnet? Revd. Pastor Laphroaig says Show the PoC || GTFOThe aim for this post is to provide more information to identify/execute embedded binaries, describing how to set your own virtual lab. In case you missed it, head to the first post from the "Analyzing and Running binaries from Firmware Images" series.TheMoon WormJohannes from SANS provided me a sample from "TheMoon" malware and posted some interesting information on their handler's diary. Their honeypots captured the scanning activity and linked the exploit to a vulnerable CGI script running on specific firmwares from the following Linksys routers: E4200, E3200, E3000, E2500, E2100L, E2000, E1550, E1500, E1200, E1000,E900.SANS handlers classified TheMoon as a Worm because of the self-replicating nature of the malware. The worm searches for a "HNAP1" URL to fingerprint and identify potentially vulnerable routers. If you check your FW and Server logs you may find lot's of different IP's probing this URL.The worm was named like this because it contains images from the movie "The Moon". It's possible to carve a few PNG's inside the ELF binary: Refrigerator Botnet? Revd. Pastor Laphroaig says Show the PoC || GTFOThe aim for this post is to provide more information to identify/execute embedded binaries, describing how to set your own virtual lab. In case you missed it, head to the first post from the "Analyzing and Running binaries from Firmware Images" series.TheMoon WormJohannes from SANS provided me a sample from "TheMoon" malware and posted some interesting information on their handler's diary. Their honeypots captured the scanning activity and linked the exploit to a vulnerable CGI script running on specific firmwares from the following Linksys routers: E4200, E3200, E3000, E2500, E2100L, E2000, E1550, E1500, E1200, E1000,E900.SANS handlers classified TheMoon as a Worm because of the self-replicating nature of the malware. The worm searches for a "HNAP1" URL to fingerprint and identify potentially vulnerable routers. If you check your FW and Server logs you may find lot's of different IP's probing this URL.The worm was named like this because it contains images from the movie "The Moon". It's possible to carve a few PNG's inside the ELF binary: |
Malware Vulnerability Patching | ★★★★ | ||
| 2013-12-10 17:36:29 | Binwally: Directory tree diff tool using Fuzzy Hashing (lien direct) | For this post, I'll discuss about the concept of directory tree and binary diffing and how it could be used to find potential vulnerabilities and security issues that were (silently) patched on firmware images.Silent patching is a big deal as we don't have many security researchers like Spender around. This is a common practice among companies that create software and firmwares for embedded devices. Changelogs from new firmwares often contains few information about security issues, outlining the changes as "bugfixes" or "enhancements": we get no CVE's and we don't know how critical the flaws are.In addition to that, you may occasionally find some reference for the string 'Ac1db1tch3z' on your code (which means that you got a free vulnerability assessment) or your employee Joel might forget to remove a backdoor from the firmware. Diffing the content from previous firmwares may be useful to find out when these backdoors were first installed, modified and/or removed.I introduce you to Binwally: a simple script to perform directory tree diffing using the concept of Fuzzy Hashing (ssdeep) to define a matching score between binaries. Binwally says "no" to Silent PatchingFuzzy HashingFuzzy Hashing, also know as context triggered piecewise hashes (CTPH), can match inputs that have homologies. Such inputs have sequences of identical bytes in the same order, although bytes in between these sequences may be different in both content and length. The concept was introduced by Andrew Tridgell and the most well-known tool is ssdeep, created by Jesse Kornblum.The usage example outlined on ssdeep's homepage summarizes it well:$ ls -l foo.txt-rw-r--r-- 1 jessekor jessekor 240 Oct 25 08:01 foo.txt$ cp foo.txt bar.txt$ echo 1 >> bar.txtA cryptographic hashing algorithm like MD5 can't be used to match these files; they have wildly different hashes.$ md5deep foo.txt bar.txt7b3e9e08ecc391f2da684dd784c5af7c /Users/jessekornblum/foo.txt32436c952f0f4c53bea1dc955a081de4 /Users/jessekornblum/bar.txtBut fuzzy hashing can! We compute the fuzzy hash of one file and use the matching mode to match the other one.$ ssdeep -b foo.txt > hashes.txt$ ssdeep -bm hashes.txt bar.txtbar.txt matches foo.txt (64)The number at the end of the line is a match score, or a weighted measure of how similar these files are. The higher the number, the more similar the files.BinwallyBinwally is a simple Python script that uses this concept to diff directory trees in order to find different, unique and matching files, displaying an overall score of the results. It was based on diffall.py from the book Programming Python (4th Ed Binwally says "no" to Silent PatchingFuzzy HashingFuzzy Hashing, also know as context triggered piecewise hashes (CTPH), can match inputs that have homologies. Such inputs have sequences of identical bytes in the same order, although bytes in between these sequences may be different in both content and length. The concept was introduced by Andrew Tridgell and the most well-known tool is ssdeep, created by Jesse Kornblum.The usage example outlined on ssdeep's homepage summarizes it well:$ ls -l foo.txt-rw-r--r-- 1 jessekor jessekor 240 Oct 25 08:01 foo.txt$ cp foo.txt bar.txt$ echo 1 >> bar.txtA cryptographic hashing algorithm like MD5 can't be used to match these files; they have wildly different hashes.$ md5deep foo.txt bar.txt7b3e9e08ecc391f2da684dd784c5af7c /Users/jessekornblum/foo.txt32436c952f0f4c53bea1dc955a081de4 /Users/jessekornblum/bar.txtBut fuzzy hashing can! We compute the fuzzy hash of one file and use the matching mode to match the other one.$ ssdeep -b foo.txt > hashes.txt$ ssdeep -bm hashes.txt bar.txtbar.txt matches foo.txt (64)The number at the end of the line is a match score, or a weighted measure of how similar these files are. The higher the number, the more similar the files.BinwallyBinwally is a simple Python script that uses this concept to diff directory trees in order to find different, unique and matching files, displaying an overall score of the results. It was based on diffall.py from the book Programming Python (4th Ed |
Tool Vulnerability Patching | ★★★★ |
To see everything:
Our RSS (filtrered)
