What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2018-09-14 17:23:01 | China-linked APT10 Hackers Update Attack Techniques (lien direct) | Recently attacks launched by the China-linked threat actor APT10 against the Japanese media sector revealed the use of updated tactics, techniques and procedures (TTPs), FireEye says. | Threat | APT 10 | ||
| 2018-09-13 11:00:00 | APT10 ciblant les sociétés japonaises à l'aide de TTPS mis à jour APT10 Targeting Japanese Corporations Using Updated TTPs (lien direct) |
Introduction
En juillet 2018, les appareils FireEye ont détecté et bloqué ce qui semble être une activité APT10 (Menupass) ciblant le secteur des médias japonais.APT10 est un groupe de cyber-espionnage chinois que Fireeye a suivi depuis 2009, et ils ont une histoire de ciblant les entités japonaises .
Dans cette campagne, le groupe a envoyé des e-mails de phishing de lance contenant des documents malveillants qui ont conduit à l'installation de la porte dérobée Uppercut.Cette porte dérobée est bien connue dans la communauté de la sécurité comme Anel , et il venait en bêta ou en RC (candidat à la libération) jusqu'à récemment.Une partie de cet article de blog discutera du
Introduction In July 2018, FireEye devices detected and blocked what appears to be APT10 (Menupass) activity targeting the Japanese media sector. APT10 is a Chinese cyber espionage group that FireEye has tracked since 2009, and they have a history of targeting Japanese entities. In this campaign, the group sent spear phishing emails containing malicious documents that led to the installation of the UPPERCUT backdoor. This backdoor is well-known in the security community as ANEL, and it used to come in beta or RC (release candidate) until recently. Part of this blog post will discuss the |
Technical | APT 10 APT 10 | ★★★★ | |
| 2018-09-03 12:49:03 | APT10 Under Close Scrutiny as Potentially Linked to Chinese Ministry of State Security (lien direct) | An advanced threat actor has been associated with China's Ministry of State Security via two individuals and a Chinese firm. | Threat | APT 10 | ||
| 2018-01-30 13:40:00 | OTX Trends Part 3 - Threat Actors (lien direct) |
By Javvad Malik and Chris Doman
This is the third of a three part series on trends identified by AlienVault in 2017.
Part 1 focused on exploits and part 2 addressed malware. This part will discuss threat actors and patterns we have detected with OTX.
Which threat actors should I be most concerned about?
Which threat actors your organization should be most concerned about will vary greatly. A flower shop will have a very different threat profile from a defense contractor. Therefore below we’ve limited ourselves to some very high level trends of particular threat actors below- many of which may not be relevant to your organisation.
Which threat actors are most active?
The following graph describes the number of vendor reports for each threat actor over the past two years by quarter:
 For clarity, we have limited the graph to the five threat actors reported on most in OTX. This is useful as a very rough indication of which actors are particularly busy.
Caveats
There are a number of caveats to consider here. One news-worthy event against a single target may be reported in multiple vendor reports. Whereas a campaign against thousands of targets may be only represented by one report.
Vendors are also more inclined to report on something that is “commercially interesting”. For example activity targeting banks in the United States is more likely to be reported than attacks targeting the Uyghur population in China. It’s also likely we missed some reports, particularly in the earlier days of OTX which may explain some of the increase in reports between 2016 and 2017.
The global targeted threat landscape
There are a number of suggested methods to classify the capability of different threat actors. Each have their problems however. For example – if a threat actor never deploys 0-day exploits do they lack the resources to develop them, or are they mature enough to avoid wasting resources unnecessarily?
Below we have plotted out a graph of the threat actors most reported on in the last two years. We have excluded threat actors whose motivation is thought to be criminal, as that wouldn’t be an apples to apples comparison.
Both the measure of their activity (the number of vendor reports) and the measure of their capability (a rough rule of thumb) are not scientific, but can provide some rough insights:
For clarity, we have limited the graph to the five threat actors reported on most in OTX. This is useful as a very rough indication of which actors are particularly busy.
Caveats
There are a number of caveats to consider here. One news-worthy event against a single target may be reported in multiple vendor reports. Whereas a campaign against thousands of targets may be only represented by one report.
Vendors are also more inclined to report on something that is “commercially interesting”. For example activity targeting banks in the United States is more likely to be reported than attacks targeting the Uyghur population in China. It’s also likely we missed some reports, particularly in the earlier days of OTX which may explain some of the increase in reports between 2016 and 2017.
The global targeted threat landscape
There are a number of suggested methods to classify the capability of different threat actors. Each have their problems however. For example – if a threat actor never deploys 0-day exploits do they lack the resources to develop them, or are they mature enough to avoid wasting resources unnecessarily?
Below we have plotted out a graph of the threat actors most reported on in the last two years. We have excluded threat actors whose motivation is thought to be criminal, as that wouldn’t be an apples to apples comparison.
Both the measure of their activity (the number of vendor reports) and the measure of their capability (a rough rule of thumb) are not scientific, but can provide some rough insights:
 A rough chart of the activity and capability of notable threat actors in the last year
Perhaps most notable here is which threat actors are not listed here. Some, such as APT1 and Equation Group, seem to have disappeared under their existing formation following from very public reporting. It seems unlikely groups which likely employ thousands of people such as those have disappeared completely. The lack of such reporting is more likely a result of significantly changed tactics and identification following their outing. Others remain visibly active, but not enough to make our chart of “worst offenders”.
A review of the most reported on threat actors
The threat actor referenced i
A rough chart of the activity and capability of notable threat actors in the last year
Perhaps most notable here is which threat actors are not listed here. Some, such as APT1 and Equation Group, seem to have disappeared under their existing formation following from very public reporting. It seems unlikely groups which likely employ thousands of people such as those have disappeared completely. The lack of such reporting is more likely a result of significantly changed tactics and identification following their outing. Others remain visibly active, but not enough to make our chart of “worst offenders”.
A review of the most reported on threat actors
The threat actor referenced i |
APT 38 APT 28 APT 10 APT 3 APT 1 APT 34 | |||
| 2017-07-27 11:30:10 | ChessMaster Makes its Move: A Look into the Campaign\'s Cyberespionage Arsenal (lien direct) | From gathering intelligence, using the right social engineering lures, and exploiting vulnerabilities to laterally moving within the network, targeted attacks have multifarious tools at their disposal. And like in a game of chess, they are the set pieces that make up their modus operandi. Take for instance the self-named ChessMaster, a campaign targeting Japanese academe, technology enterprises, media outfits, managed service providers, and government agencies. It employs various poisoned pawns: malware-laden spear-phishing emails with decoy documents purporting to be legitimate. And beyond ChessMaster's endgame and pawns, we also found red flags that allude to its links to APT 10, a.k.a. menuPass, POTASSIUM, Stone Panda, Red Apollo, and CVNX. ChessMaster's name is from pieces of chess/checkers/draughts we found in the resource section of the main backdoor they use against their targets: ChChes, which Trend Micro detects as BKDR_CHCHES. Post from: Trendlabs Security Intelligence Blog - by Trend Micro ChessMaster Makes its Move: A Look into the Campaign's Cyberespionage Arsenal | APT 10 | |||
| 2017-05-10 08:54:57 | (Déjà vu) Anti-virus defences are leaving global businesses vulnerable to the China syndrome (lien direct) | The news that the China-based APT10 hackers have so devastatingly penetrated the cyber defences of some of the world's biggest commercial and governmental organisations reveals a sickening reality. Described in a new report from PwC UK and BAE Systems as a sustained, “global operation of unprecedented size and scaleâ€, APT10's Operation Cloud Hopper has stolen ... | APT 10 | |||
| 2017-04-06 19:15:00 | China-Based Threat Actor APT10 Ramps Up Cyber Espionage Activity (lien direct) | Customers of managed security service providers, website of U.S. trade lobby group targeted in separate campaigns | APT 10 | |||
| 2017-04-06 14:00:00 | APT10 (Menupass Group): Nouveaux outils, la dernière campagne de la campagne mondiale de la menace de longue date APT10 (MenuPass Group): New Tools, Global Campaign Latest Manifestation of Longstanding Threat (lien direct) |
APT10 Background
APT10 (Menupass Group) est un groupe de cyber-espionnage chinois que Fireeye a suivi depuis 2009. Ils ont historiquement ciblé la construction et l'ingénierie, l'aérospatiale et les sociétés de télécommunications et les gouvernements aux États-Unis, en Europe et au Japon.Nous pensons que le ciblage de ces industries a soutenu les objectifs de sécurité nationale chinoise, notamment l'acquisition de précieuses informations militaires et de renseignement ainsi que le vol de données commerciales confidentielles pour soutenir les sociétés chinoises.Pwc et Bae ont récemment publié un blog conjoint >
APT10 Background APT10 (MenuPass Group) is a Chinese cyber espionage group that FireEye has tracked since 2009. They have historically targeted construction and engineering, aerospace, and telecom firms, and governments in the United States, Europe, and Japan. We believe that the targeting of these industries has been in support of Chinese national security goals, including acquiring valuable military and intelligence information as well as the theft of confidential business data to support Chinese corporations. PwC and BAE recently issued a joint blog detailing extensive APT10 activity. |
Threat Technical | APT 10 APT 10 | ★★★★ | |
| 2017-04-06 11:03:37 | U.S. Trade Group Hacked by Chinese Hackers ahead of Trump-Xi Trade Summit (lien direct) | Researchers have uncovered a Chinese cyber-espionage against the United States ahead of the trade summit on Thursday between US President Donald Trump and China's President Xi Jinping.
According to a new report published today by Fidelis Cybersecurity firm, the Chinese APT10 hacking group implanted a piece of malware on the "Events" page of the US National Foreign Trade Council (NFTC) website
|
APT 10 | |||
| 2017-04-06 10:13:00 | US trade lobbying group attacked by suspected Chinese hackers (lien direct) | A group of what appears to be Chinese hackers infiltrated a U.S. trade-focused lobbying group as the two countries wrestle with how they treat imports of each other's goods and services.The APT10 Chinese hacking group appears to be behind a "strategic web compromise" in late February and early March at the National Foreign Trade Council, according to security vendor Fidelis Cybersecurity.The NFTC lobbies for open and fair trade and has pledged to work with U.S. President Donald Trump to "find ways to address Chinese policies that frustrate access to their market and undermine fair trade, while at the same time encouraging a positive trend in our trade relationship." Trump will meet with China President Xi Jinping in Florida this week.To read this article in full or to leave a comment, please click here | APT 10 | |||
| 2017-04-05 09:15:00 | Chinese APT10 Hacking Group Suspected of Global Campaign Targeting MSPs (lien direct) | 'Operation Cloud Hopper' reveals China-based attackers allegedly targeted IT service providers in 15 countries. | APT 10 | |||
| 2017-04-04 13:39:28 | Chinese hackers go after third-party IT suppliers to steal data (lien direct) | Companies that choose to outsource their IT operations should be careful. Suspected Chinese hackers have been hitting businesses by breaching their third-party IT service providers. Major IT suppliers that specialize in cloud storage, help desk, and application management have become a top target for the hacking group known as APT10, security providers BAE Systems and PwC said in a joint report.That's because these suppliers often have direct access to their client's networks. APT10 has been found stealing intellectual property as part of a global cyberespionage campaign that ramped up last year, PwC said on Monday.To read this article in full or to leave a comment, please click here | APT 10 | |||
| 2017-04-03 18:09:04 | APT10 - Operation Cloud Hopper (lien direct) | Written by Adrian Nish and Tom RowlesBACKGROUNDFor many businesses the network now extends to suppliers who provide management of applications, cloud storage, helpdesk, and other functions. With the right integration and service levels Managed Service Providers (MSPs) can become a key enabler for businesses by allowing them to focus on their core mission while suppliers take care of background tasks. However, the network connectivity which exists between MSPs and their customers also provides a vector for attackers to jump through. Successful global MSPs are even more attractive as they become a hub from which an intruder may access multiple end-victim networks.Since late 2016 we have been investigating a campaign of intrusions against several major MSPs. These attacks can be attributed to the actor known as APT10 (a.k.a. CVNX, Stone Panda, MenuPass, and POTASSIUM). Their activity seems to have increased in mid-2016, and has focused on compromise of MSPs as a stepping stone into victim organisations.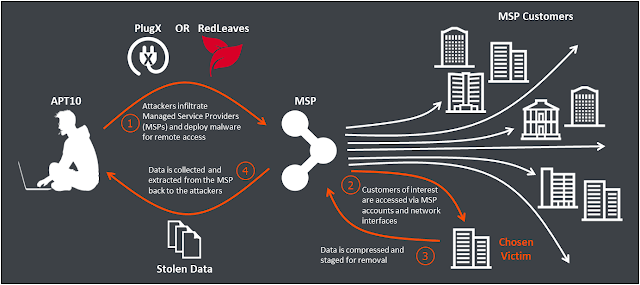 Figure 1 – Attack stages for APT10 in targeting MSP end-customersWe have joined forces with PwC to release our findings from investigations into these on-going attacks and raise awareness. This joint analysis report can be found on PwC's blog at:https://www.pwc.co.uk/issues/cyber-security-data-privacy/insights/operation-cloud-hopper.htmlOVERVIEWThe current campaign linked to APT10 can be split into two sets of activity:1. Attacks targeting MSPs, engineering and other sectors with common as well as custom malware;2. Attacks targeting Japanese organisations with the 'ChChes' malware;The latter campaign has been well covered in the public domain, however the MSP targeting is the focus of our joint analysis report with PwC.The group use a custom dropper for their various implants. This dropper makes use of DLL side-loading to execute the main payload.In our analysis the attackers have used several payloads including:1. PlugX – a well-known espionage tool in use by several threat actors2. RedLeaves – a newly developed, fully-featured backdoor, first used by APT10 in recent monthsINFRASTRUCTUREThe C&C domains chosen by the APT10 actors for their MSP-related campaign are predominantly dynamic-DNS domains.The various domains are highly-interconnected through shared IP address hosting, even linking back historically to the group's much older operations. The graph below depicts infrastructure used by the attackers in late 2016. Figure 1 – Attack stages for APT10 in targeting MSP end-customersWe have joined forces with PwC to release our findings from investigations into these on-going attacks and raise awareness. This joint analysis report can be found on PwC's blog at:https://www.pwc.co.uk/issues/cyber-security-data-privacy/insights/operation-cloud-hopper.htmlOVERVIEWThe current campaign linked to APT10 can be split into two sets of activity:1. Attacks targeting MSPs, engineering and other sectors with common as well as custom malware;2. Attacks targeting Japanese organisations with the 'ChChes' malware;The latter campaign has been well covered in the public domain, however the MSP targeting is the focus of our joint analysis report with PwC.The group use a custom dropper for their various implants. This dropper makes use of DLL side-loading to execute the main payload.In our analysis the attackers have used several payloads including:1. PlugX – a well-known espionage tool in use by several threat actors2. RedLeaves – a newly developed, fully-featured backdoor, first used by APT10 in recent monthsINFRASTRUCTUREThe C&C domains chosen by the APT10 actors for their MSP-related campaign are predominantly dynamic-DNS domains.The various domains are highly-interconnected through shared IP address hosting, even linking back historically to the group's much older operations. The graph below depicts infrastructure used by the attackers in late 2016. Figure 2 – Infrastructure view from late 2016In recent months the infrastructure has expanded significantly. The nodes number into the thousands and cannot be easily visualised.The below graph represents a linkage between one of the PlugX C&Cs used in the group's newer ope Figure 2 – Infrastructure view from late 2016In recent months the infrastructure has expanded significantly. The nodes number into the thousands and cannot be easily visualised.The below graph represents a linkage between one of the PlugX C&Cs used in the group's newer ope |
APT 10 APT 1 | |||
| 2017-02-16 19:00:11 | menuPass Returns with New Malware and New Attacks Against Japanese Academics and Organizations (lien direct) | In 2016, from September through November, an APT campaign known as “menuPassâ€Â targeted Japanese academics working in several areas of science, along with Japanese pharmaceutical and a US-based subsidiary of a Japanese manufacturing organizations. In addition to using PlugX and Poison Ivy (PIVY), both known to be used the group, they also used a new Trojan called “ChChes†by the Japan Computer Emergency Response Team Coordination Center (JPCERT). In contrast to PlugX and PIVY, which are used by multiple campaigns, ChChes appears to be unique to this group. An analysis … | APT 10 | |||
| 2016-12-02 14:35:57 | Protecting Powershell Credentials (NOT), (Fri, Dec 2nd) (lien direct) | If youre like me, youve worked through at least one Powershell tutorial, class or even a how-to blog. And youve likely been advised to use the PSCredential construct to store credentials. The discussion usually covers that this a secure way to collect credentials, then store them in a variable for later use. You can even store them in a file and read them back later. Awesome - this solves a real problem you thought - or does it? For instance, to collect credentials for a VMware vSphere infrastructure (Im wrapping up a number of audit scripts this week), youbase64,iVBORw0KGgoAAAANSUhEUgAAAYMAAAFKCAIAAABw4aQ5AAAgAElEQVR4nOy9Z1TbaX73ffEiu5vkyUxy57k3s0l23GdcxgUbd4zBFWzTQfSOChJCqCIJkJCEJBBIAvXeERICdSEJUW3PeJrt8ZSdmW3JJjuZna2Z3b3P5jnnOSfPi+uvAvbMbMqT5MX+z+f4qEuA9dH397uKAPjvOP51O/9Djv+Zr+oPxx+OPxx/OP5w/OH4w/HfcfzpX+3/xv/69tf//K+//uff+trzL/z7+PpTfOP5F77x/At//PwLf/L8C3/6/At/9vwLzz3/wvPPv/Dnz7/w/PMvPPf8C889/8KfPf/C//X8C3/y/At/nL79N571UP9xvvbUa8t9VfCFQXa8pMzdv/yH/Z/Pv/XP95/1yP///br+W570fxT/7nfrfyd//q2v/8XffON/793moG/85a6hscnl1XuffPrTf/71b/7517/5+S//+T+dX3wp6Zv96ue/+NXPf/Grn/0e/PQXv/zpz/+T+Nkvf7adnyL84qc/+8VnX8VPfvaLn/z0aX6ey6c7+CzDzyD/lMtPtvHJT36a5dOd/BjhM4R/+uzH//TZPz6bn/zjJz/5h6/g0x998umPfvz78vf/iPCjH3/69z/+9O+/6vb/8ONPv+oF/OQfIc/6EX6c4dPPfpz92Z/6tSC/rp998pOdv8zML/nTLD/fRs6fKf3ne9bf92cIz/wv8bvf/Utbe8f/+19yaAfQ/zVP9J91tNy8+rt/+Zcf/sMn3lCCzZ9CNHSm+JZ9IfL2kw819qUxmZEmUNDHlbkwhF/GjhunUeTCGFcwBIohgYIpULAECjaEP8vmz7L4s0z+7BB/lsGfpfFnqPwZKm+Gwpuh8GbIPPngmGyQKyNxZSSudIAzTRydJo5M9Y9MEYYlePZkH2uijzWBY07gmBPYITF2SIxliDEMEZouQtOFkF76OKSHloYqyNBLFaCpAgxFgIWQ+RnQZH7PIK97kNdJGusgjbUPcNsHuG0D3NYBbks/B9LcP9rcP9qEH2nCjzTiRxr6hhv6hlE4NgrHrsey6rGsOgyzFs2sRTOrexk1vUPVvYyqbnplN62ii1bRRSvvpN7poNxuJ99uJ99qGyxrJZW2kG62DNxoJl5vIl5rJFxrJFxtIFxB4Uvq+4rr+i7X4opqsJeqsYXVmItVmIuV6PMVvecres5X9Jwr7z5zu+v07c7TtzoLyjpOlbafLG3Lv9l24kbriRutx661HL/Wcuxq09GrTa9caXylpPFIScPh4obDl1GHLqMOFtUfLKp7+VLdS4W1BwprD1ys2X+hZt+F6n3nq/eer9p7vmrP+co95yr3nKvcfa5i19mKXWcrXjxTDvn26Tt/m+bbp+9kLoc3232ucs+5qj3nqvacr9p7vnrv+ep952v2XajZf6H2wMXaA4V1LxXWvXyp/mBR/cEi1KHLqMOXGw4XNx4paXylpOmVK01HrzYfu9p8/FrL8Wst+Tfa8m+0nbzZfqq0/VRpx+myzjO3Os/c7jp7u+tcec/5it7zFb0XKtGFVZjCasylGmxRDa6oFldc11dcj7+CIlxtIFxr7L/eSLzeSLzRPHCzmVTaOljWOnirjXy7nXKnA0Kt6KJVdtMru+lV3YzqbnpND6O2d6i6h1GLZtb2DtWhmRAUllWPZcE/dEPfcGPfcGPfMPxv0ExAePD2uwdeOfnkO9+NpO5Gs9yLZVjdwX2EtfvLuazfj6+/miGx/lpi/bXExmuJjQeQx+9/rMC0f3j37lsm/Vsm/SOz/rFV/9iqf9eqf8+qf9+q+8iq+8iq+65V932r7vtWzQ+tmr+zav7+y9DuxLaTH23n723av7Npf2DT/sCm/75N/z2b/mOb/iOb/gOb/gOb4T2b4YnN8MRmeMdqeGgxfLi60ni16PH7H4/JTXpX4K0n3wEAgD/+v3fbFyL+5fUc6aiGRBD1kEjNFKtZYg1LrGFNPAPmhIYpfhr1TkRqpkjNEqlZIjUbIlRBWEIVS6hiClVDuYIbV9LGFbRxBU2goPJnKfxZCm+GMjZDHpOTx2RkrozEkZJGpQOj08SR6f7hKcLwFGFYQmBL8KzJPtZkH3OyjzmJY4ozIJ4aEmMZop3QhTi6CEcT4mjCPpoQnsBSxzHUcTR1vIci6KEIuin8bgq/i8LvGORB2gfH2gfH2tJuah3gthA5LcTR5v7RJsJIE2GkCT/chB9u7BtuwLEbcGwUjlWPZdZjmHWYodpeRk0vo7qHXt1Dr+qmVXXTKrqo5fDN0E653U6+1Zq2UvPAjSZopf6rjf1XUIQSFL64Hl9c13e5Dne5FltUg71UjSmsQl+sQl+o6j1f0XOuovtsedeZO12nb3eevt1ZcKvjVFn7ydK2/NK2/Jut+TdaT9xoOX695fi15mPXmo9ebXrlStORksYjJY2HixsOFzccutxw8DIK8vLl+peK6l66VPfSpdqXLtUeKKw9UFi7/2INZN+F6r2Q81UIF6r3Xqjed6E6c5sDhXUHCuEj1L10qf6lovqXL6MOXm6AHLrceLi48XBx45GSpiMZ9VxrPn6t5fj11hM3WvNvtOXfbDtZ2n6qtL2grOP0rc4zt7vO3O46e6f7XHn3+YqeCxW9F6vQhVXoS9WYSzXYy7W4y7W44vq+knp8CQp/pYFwtaH/WiPxehPxRtPAzWZSaQuprHXwViv5VhvlTjvlTgelvJNa0Umt7KLBP0d1D6Omd6gGPVSDZtahmbXooVoMsw7NrMew6tDMOgyrHsOqx7DgCRSW1YBFZNTQx97ho9fefnf/EcREO2QU/T1kFPtyGW1kePD4/Y9ne9o+3Nx4S6eCPNSpHhtUjw2Kdw2K9wyKDwyKj4yKj4yK7xkV3zcqvm9U/PCrUe7g70xfwQ/SfN+k/Nik/Mik/NCo/MCofM+ofGJUvmNQPzaoHxrUDw3qDxLxupKix+9/TBUoqAIFTaAAAIARoezhux8yhKohoWoI+kKsYU9ohie1w5PaEYludEo/OqXnTBu+kKlc9M9A8jS6XEYlulGJbkSiG5FoRyTaYYmWPZkDlJ1IPSRSDwnVDKGKDj0lUND4CmgoCjQURzbIkQ5ypCSOlMSZJnGmBzjTxNEphBEJpD9zYljSPywhDkv62RIiW0JkS/rZkn62hMCaJLAm+5gTENyQGDckxtBF6bQlQtOFaJqwlzreSx3voY73UMehqjrJPEjH4FhH2lNtiKQ42fSU/hRtgNEJg/ynr0EzqnvoVT20SuimTkp5B6Uchqa2QURPzaQbTQM3mojXGvuvNfZfbSBAPZXU9xXX44rrcJfrsJdqMJdqMIXV6ItV6AuVvecre89X9Jwr7zlb3n2mvDstqY7TtzsKbnUUlLWfKms/Vdp28iaiqrStmo9faz5+rfnYtaajSJjKautISePhksbDJQ2HSxoOFSPAs4fTNzhS0gjvcvRqc1Yx11qOX29BLANFA2NOWUdBWUfBrU4o0NO3u87c6Tpb3nOuvOd | APT 10 | |||
| 2016-12-01 04:01:02 | Amplify IT Security by Integrating Solutions (lien direct) | The lowly banana. It's a great source of potassium. As a stand-alone food source, it's rather boring. Mono-flavored (like a banana). It's sometimes squishy or bruised or otherwise imperfect. And it's often part of a dull breakfast routine (mine). But pair banana slices with bran cereal or as the basis for a smoothie, and your […]… Read More | APT 10 | |||
| 2016-06-29 08:21:43 | États-Unis – Le FBI libre de pirater n\'importe quel PC légalement ? (lien direct) |  Au cours des turbulences liées à l'affaire de pédophilie Playpen, un juge américain a déclaré que le FBI n'avait pas besoin de mandat pour obtenir s'introduire et fouiller un ordinateur à distance. Dérive ? Au cours des turbulences liées à l'affaire de pédophilie Playpen, un juge américain a déclaré que le FBI n'avait pas besoin de mandat pour obtenir s'introduire et fouiller un ordinateur à distance. Dérive ? |
APT 10 |
To see everything:
Our RSS (filtrered)
