What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2018-07-23 11:23:05 | Sign-language hack lets Amazon Alexa respond to gestures (lien direct) | A prototype uses an artificial intelligence system that can interpret hand movements. | Hack | |||
| 2018-07-23 08:00:02 | Hack the FourAndSix:1 (CTF Challenge) (lien direct) | FourAndSix is a CTF challenge uploaded by Fred on vulnhub. You can download it from here. The aim of this lab is to capture a flag in the root directory. This lab was very confusing to even begin with due to the lack of description by author. So, on the basis of our experience, we... Continue reading → | Hack | |||
| 2018-07-23 07:22:04 | Experts believe US Cyber Command it the only entity that can carry out \'hack backs\' (lien direct) | The U.S. government should opt to carry out hack backs as retaliation against the massive attacks against organizations in the US private sector. The U.S. government should opt to carry out hack backs as retaliation against the massive attacks against organizations in the US private sector, and when appropriate, the military's hacking unit should hit […] | Hack | |||
| 2018-07-22 07:32:00 | Hack the Blacklight: 1 (CTF Challenge) (lien direct) | Hello everyone. In this article we'll be hacking a new lab Blacklight. The motto of the lab is to capture 2 flags. It is made by Carter B (downloadable from here) and after a lot of brainstorming, we are presenting before you a really efficient method to get root and capture the flags. Steps involved:... Continue reading → | Hack | |||
| 2018-07-22 07:10:01 | (Déjà vu) Hack the Box Challenge: Ariekei Walkthrough (lien direct) | Hello friends! Today we are going to solve another CTF challenge “Ariekei” which is available online for those who want to increase their skill in penetration testing and black box testing. Ariekei is retired vulnerable lab presented by Hack the Box for making online penetration practices according to your experience level; they have the collection of vulnerable... Continue reading → | Hack | |||
| 2018-07-20 14:27:04 | Hackers Breach Russian Bank and Steal $1 Million Due to Outdated Router (lien direct) | A notorious hacker group known as MoneyTaker has stolen roughly $1 million from a Russian bank after breaching its network via an outdated router. The victim of the hack is PIR Bank, which lost at least $920,000 in money it had stored in a corresponding account at the Bank of Russia. View Full Story ORIGINAL ... | Hack | |||
| 2018-07-20 12:08:00 | Singapore personal data hack hits 1.5m, health authority says (lien direct) | The attack by hackers on a health database has affected about a quarter of the population. | Hack | |||
| 2018-07-20 09:39:00 | Hack the Violator (CTF Challenge) (lien direct) | Welcome to another boot2root / CTF this one is called Violator. The VM is set to grab a DHCP lease on boot. As, there is a theme, and you will need to snag the flag in order to complete the challenge. for downloading open this link: https://www.vulnhub.com/entry/violator-1,153/ Some hints for you: Vince Clarke can help... Continue reading → | Hack | |||
| 2018-07-20 07:01:02 | Microsoft uncovered and stopped attempts to launch spear-phishing attacks on three 2018 congressional candidates (lien direct) | Microsoft helped the US Government is protecting at least three 2018 midterm election candidates from attacks of Russian cyberspies. Microsoft revealed that Russian cyberspies attempted to hack at least three 2018 midterm election candidates and it has helped the US government to repeal their attacks. A Microsoft executive speaking at the Aspen Security Forum revealed the hacking attempts against […] | Hack | ★★★★★ | ||
| 2018-07-19 14:35:01 | Industry Reactions to U.S. Indicting 12 Russians for DNC Hack (lien direct) | The U.S. last week indicted 12 Russian intelligence officers over their alleged role in a hacking operation targeting the Democratic National Committee (DNC) and Hillary Clinton's 2016 presidential campaign. | Hack | |||
| 2018-07-19 13:35:00 | Microsoft Says Russia Tried to Hack Three 2018 Midterm Election Candidates (lien direct) | Microsoft said it detected and helped the US government to block Russian hacking attempts against at least three congressional candidates this year, a Microsoft executive revealed speaking at the Aspen Security Forum today.
Although the company refused to name the targets but said, the three candidates were "people who, because of their positions, might have been interesting targets from an
|
Hack | |||
| 2018-07-19 04:00:00 | IDG Contributor Network: Hack like a CISO (lien direct) | I have written several times over the last couple of years about how the role of today's CISOs have changed and are now more tuned to support business activities and the management of enterprise risk. Serving an organization as their most senior security executive requires one to be creative and flexible on how to approach issues. Part of this creativity that many CISOs develop over time is specific processes or “hacks” that they have found useful to grow their security programs and use resources efficiently.A hack has multiple definitions; it can be defined as a piece of computer code providing a quick or inelegant technique to solve a particular problem. It also can be what I believe is a more appropriate definition for CISOs – a process, strategy or technique for managing one's time, resources, teams or program more efficiently. | Hack | |||
| 2018-07-17 09:29:04 | (Déjà vu) Hack the Teuchter VM (CTF Challenge) (lien direct) | Hello friends!! Today we are going to solve latest CTF challenge “Teuchter” presented by vulnhub for penetration practice and design by knightmare. This virtual machine is having intermediate to medium difficulty level. One need to break into VM using web application and from there escalate privileges to gain root access. Download it from here: https://www.vulnhub.com/entry/teuchter-03,163/... Continue reading → | Hack | |||
| 2018-07-17 07:35:00 | (Déjà vu) Hack the Box Challenge: Enterprises Walkthrough (lien direct) | Hello friends!! Today we are going to solve another CTF challenge “Enterprise” which is available online for those who want to increase their skill in penetration testing and black box testing. Enterprise is retired vulnerable lab presented by Hack the Box for making online penetration practices according to your experience level; they have the collection of vulnerable... Continue reading → | Hack | |||
| 2018-07-16 15:54:01 | IoT search engine exposes passwords of over 30,000 vulnerable DVRs (lien direct) |  A researcher has discovered that it's easier than ever before to hack at least one brand of internet-enabled DVR, as an IoT search engine has cached their passwords within search results.
Read more in my article on the Bitdefender BOX blog. A researcher has discovered that it's easier than ever before to hack at least one brand of internet-enabled DVR, as an IoT search engine has cached their passwords within search results.
Read more in my article on the Bitdefender BOX blog.
|
Hack | |||
| 2018-07-16 02:58:00 | 5 ways to hack blockchain in the enterprise (lien direct) | One of the hottest topics in cybersecurity circles is the enterprise blockchain. This is the same technology that underpins cryptocurrencies like Bitcoin. Simply defined, blockchain is a list of transactions or contracts shared with peers and locked down by some clever cryptography. Beyond Bitcoin, it can ensure the integrity of supply chains, manage contracts, or even as serve as a platform for financial transactions. | Hack | |||
| 2018-07-15 18:30:04 | Hack the Billu Box2 VM (Boot to Root) (lien direct) | Hello freinds!! Today we are going to solve latest CTF challenge “Billu Box2” presented by vulnhub for penetration practice and design by Manish Kishan Tanwar. This virtual machine is having intermediate to medium difficulty level. One need to break into VM using web application and from there escalate privileges to gain root access. You can... Continue reading → | Hack | |||
| 2018-07-15 13:35:05 | Hack the Lin.Security VM (Boot to Root) (lien direct) | Hello Guy's!! In our previous article “Linux Privilege Escalation using Sudo Rights” we had described how some weak misconfiguration sudo rights can lead to root privilege escalation and today I am going to solve the CTF “Lin.Security – Vulnhub” which is design on weak sudo right permissions for beginners to test their skillset through this... Continue reading → | Hack Guideline | |||
| 2018-07-15 00:49:00 | 12 Russian Intelligence Agents Indicted For Hacking DNC Emails (lien direct) | The US Justice Department has announced criminal indictments against 12 Russian intelligence officers tied to the hack of the Democratic National Committee (DNC) during the 2016 US presidential election campaign.
The charges were drawn up as part of the investigation of Russian interference in the 2016 US presidential election by Robert Mueller, the Special Counsel, and former FBI director.
|
Hack | |||
| 2018-07-14 18:09:05 | Hack The Toppo:1 VM (CTF Challenge) (lien direct) | Hello friends!! Today we are going to solve latest CTF challenge presented by vulnhub for penetration practice and design by Mr. Hadi Mene. This lab is proposal for beginners and mode of difficulty level is easy. You can download it from this Link: https://www.vulnhub.com/entry/toppo-1,245/ Penetration Methodologies Network scaning Directory brute-force attack Abusing HTTP web directories... Continue reading → | Hack | |||
| 2018-07-14 11:11:02 | Hack the Basic Pentesting:2 VM (CTF Challenge) (lien direct) | Basic pentesting 2 is a boot2root VM and is a continuation of the Basic Pentesting series by Josiah Pierce. This series is designed to help newcomers to penetration testing develop pentesting skills and have fun exploring part of the offensive side of security. VirtualBox is the recommended platform for this challenge (though it should also... Continue reading → | Hack | |||
| 2018-07-14 06:33:05 | (Déjà vu) Hack the Box Challenge: Falafel Walkthrough (lien direct) | Hello friends!! Today we are going to solve another CTF challenge “falafel” which is available online for those who want to increase their skill in penetration testing and black box testing. Falafel is a retired vulnerable lab presented by hack the box for making online penetration practices according to your experience level; they have the... Continue reading → | Hack | |||
| 2018-07-14 01:59:03 | Indictment of Russian Intelligence Operatives Should Quell Harebrained Conspiracy Theories on DNC Hack (lien direct) | Longtime Donald Trump associate Roger Stone pauses while speaking to members of the media after testifying before the House Intelligence Committee on Sept. 26, 2017. | Hack | |||
| 2018-07-13 16:58:00 | Russians indicted over US election hack (lien direct) | Twelve Russian intelligence officers are indicted for hacking Democrat emails during 2016 election. | Hack | |||
| 2018-07-13 16:06:00 | Justice Dept. indicts 12 Russian spies over 2016 DNC hack (lien direct) | The 12 indictments were sought by US special counsel Robert Mueller. | Hack | |||
| 2018-07-13 11:42:04 | (Déjà vu) Hack the Box Challenge: Charon Walkthrough (lien direct) | Hello friends!! Today we are going to solve another CTF challenge “Charon” which is available online for those who want to increase their skill in penetration testing and black box testing. Charon is retired vulnerable lab presented by Hack the Box for making online penetration practices according to your experience level; they have the collection of vulnerable... Continue reading → | Hack | |||
| 2018-07-13 10:14:04 | The Types of Hackers & Why They Hack (lien direct) | In current times, the term may describe a person who attempts to gain unauthorized access to computers, with less than honorable intentions, or the person who counters the bad intentioned one. But, there is a pretty broad spectrum of hackers and a variety of motivations for hacking. [...] | Hack | |||
| 2018-07-12 23:27:00 | The Most Common Hack Is Also the Most Successful. Here\'s How to Fight It. (lien direct) | Despite what movies might show, most hacks don't involve frantic typing or brute-force attacks. In fact, Verizon’s “2017 Data Breach Investigations” report revealed that 90 percent of successful hacks aren't hacks at all: They’re social engineering. Simply put, social engineering is about manipulating people rather than computers. Modern hackers have discovered that it is easier … The ISBuzz Post: This Post The Most Common Hack Is Also the Most Successful. Here’s How to Fight It. | Data Breach Hack | |||
| 2018-07-12 19:54:20 | Your IoT security concerns are stupid (lien direct) | Lots of government people are focused on IoT security, such as this recent effort. They are usually wrong. It's a typical cybersecurity policy effort which knows the answer without paying attention to the question.Patching has little to do with IoT security. For one thing, consumers will not patch vulns, because unlike your phone/laptop computer which is all "in your face", IoT devices, once installed, are quickly forgotten. For another thing, the average lifespan of a device on your network is at least twice the duration of support from the vendor making patches available.Naive solutions to the manual patching problem, like forcing autoupdates from vendors, increase rather than decrease the danger. Manual patches that don't get applied cause a small, but manageable constant hacking problem. Automatic patching causes rarer, but more catastrophic events when hackers hack the vendor and push out a bad patch. People are afraid of Mirai, a comparatively minor event that led to a quick cleansing of vulnerable devices from the Internet. They should be more afraid of notPetya, the most catastrophic event yet on the Internet that was launched by subverting an automated patch of accounting software.Vulns aren't even the problem. Mirai didn't happen because of accidental bugs, but because of conscious design decisions. Security cameras have unique requirements of being exposed to the Internet and needing a remote factory reset, leading to the worm. While notPetya did exploit a Microsoft vuln, it's primary vector of spreading (after the subverted update) was via misconfigured Windows networking, not that vuln. In other words, while Mirai and notPetya are the most important events people cite supporting their vuln/patching policy, neither was really about vuln/patching.Such technical analysis of events like Mirai and notPetya are ignored. Policymakers are only cherrypicking the superficial conclusions supporting their goals. They assiduously ignore in-depth analysis of such things because it inevitably fails to support their positions, or directly contradicts them.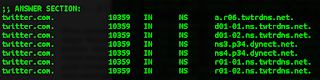 IoT security is going to be solved regardless of what government does. All this policy talk is premised on things being static unless government takes action. This is wrong. Government is still waffling on its response to Mirai, but the market quickly adapted. Those off-brand, poorly engineered security cameras you buy for $19 from Amazon.com shipped directly from Shenzen now look very different, having less Internet exposure, than the ones used in Mirai. Major Internet sites like Twitter now use multiple DNS providers so that a DDoS attack on one won't take down their services.In addition, technology is fundamentally changing. Mirai attacked IPv4 addresses outside the firewall. The 100-billion IoT devices going on the network in the next decade will not work this way, cannot work this way, because there are only 4-billion IPv4 addresses. Instead, they'll be behind NATs or accessed via IPv6, both of which prevent Mirai-style worms from functioning. Your fridge and toaster won't connect via your home WiFi anyway, but via a 5G chip unrelated to your home.Lastly, focusing on the ven IoT security is going to be solved regardless of what government does. All this policy talk is premised on things being static unless government takes action. This is wrong. Government is still waffling on its response to Mirai, but the market quickly adapted. Those off-brand, poorly engineered security cameras you buy for $19 from Amazon.com shipped directly from Shenzen now look very different, having less Internet exposure, than the ones used in Mirai. Major Internet sites like Twitter now use multiple DNS providers so that a DDoS attack on one won't take down their services.In addition, technology is fundamentally changing. Mirai attacked IPv4 addresses outside the firewall. The 100-billion IoT devices going on the network in the next decade will not work this way, cannot work this way, because there are only 4-billion IPv4 addresses. Instead, they'll be behind NATs or accessed via IPv6, both of which prevent Mirai-style worms from functioning. Your fridge and toaster won't connect via your home WiFi anyway, but via a 5G chip unrelated to your home.Lastly, focusing on the ven |
Hack Patching Guideline | NotPetya | ||
| 2018-07-12 09:54:03 | Another hack rocks cryptocurrency trading: Bancor loses $13.5 million (lien direct) | The alleged hack has raised questions over the validity of the start-up's "decentralized" system. | Hack | |||
| 2018-07-12 04:50:00 | Three Arrests Made in Largest Hack in Lebanon\'s History (lien direct) | Beirut officials have arrested three suspects believed to be behind what local authorities are calling the biggest hack in Lebanon's history. [...] | Hack | |||
| 2018-07-10 07:23:00 | The aftermath of the Gentoo GitHub hack (lien direct) | Gentoo GitHub hack: What happened? Late last month (June 28), the Gentoo GitHub repository was attacked after someone gained control of an admin account. All access to the repositories was soon removed from Gentoo developers. Repository and page content were altered. But within 10 minutes of the attacker gaining access, someone noticed something was going on, 7 minutes later a report was sent, and within 70 minutes the attack was over. Legitimate Gentoo developers were shut out for 5 days while the dust settled and repairs and analysis were completed.The attackers also attempted to add "rm -rf" commands to some repositories to cause user data to be recursively removed. As it turns out, this code was unlikely to be run because of technical precautions that were in place, but this wouldn't have been obvious to the attacker. | Hack | |||
| 2018-07-09 15:40:04 | (Déjà vu) Hack the PinkyPalace VM (CTF Challenge) (lien direct) | Hello friends! Today we are going to take another boot2root challenge known as PinkyPalace. The credit for making this vm machine goes to “Pink_panther” and it is another boot to root challenge in which our goal is to gain root access to complete the challenge. You can download this VM here. Let's Breach!!! Let's do an... Continue reading → | Hack | |||
| 2018-07-09 07:55:00 | Thieves hack Marathon gas station, steal $1,800 of gas (lien direct) | An hour past high noon, hackers allegedly used a “remote device” to control a prepaid gas pump at a Marathon gas station in Detroit, allowing 10 vehicles to steal $1,800 of gas over a 90-minute period.How many gallons of gas can your vehicle hold? Surely not 60? Yet the Detroit gas “hack” reportedly included a “convoy” of 10 vehicles, pulling in and pumping one after another for an hour and a half, managing to steal 600 gallons of gas. That implies each vehicle stole 60 gallons. There is no mention of people in those vehicles also filling up gas cans, barrels or other storage, so the total of 10 vehicles filling up for free to make off with 600 gallons doesn't seem quite right. | Hack | |||
| 2018-07-06 17:36:04 | Typing \'A\' key 29 times lets you hack HPE iLO 4 servers (lien direct) | Utilizing a cURL request and the string of letters, researcher obtained a cleartext password. | Hack | |||
| 2018-07-06 13:00:00 | Things I Hearted this Week, 6th July 2018 (lien direct) | Here's an idea. Have convicts in prison manually mine cryptocurrencies. Call it, the blockchain gang! Thank you very much, I'll be here all week. Now on to the serious stuff. 10 THINGS TO KNOW BEFORE GETTING INTO CYBERSECURITY You may know Kevin Beaumont as @GossiTheDog on twitter. He won the 2018 EU blogger awards for best tweeter. But apparently, he's a man of more talents than just twits, he also blogs, and has put together a good list of 10 things you should know if you're considering getting into cybersecurity. 10 things to know before getting into cyber security| Double Pulsar Related, if you're looking to break into security, then you'll want to know which locations offer the best salaries (US-based). Cybersecurity spotlight 2018: Where are the highest paying jobs? | Indeed Blog HACKERS WILL GET HACKED Of course we trust the Government to maintain backdoors and hacking tools... they're the Government. I, for one, am shocked that gambling takes place in this casino. From Cellebrite, to Shadow Brokers, to the CIA dump, so many recent data breaches have shown there is a real risk of exposure to government hacking tools. Your Government's Hacking Tools Are Not Safe | Motherboard In related news, NSO sells its potent iPhone malware to governments, including Mexico and the United Arabs Emirates. But according to a newly released indictment, a disgruntled employee stole the company's code and tried to sell it for $50 million worth of cryptocurrency. NSO Group Employee Allegedly Stole Company’s Powerful Spyware for Personal Profit | Motherboard IT IS COMING HOME While the tide of outsourcing seems to be on the rise, does BP represent an undercurrent of some companies wanting to get their arms around exactly what they have, why they have it, and who manages it? BP is looking to bring the majority of its IT back in-house as part of a wider modernisation programme across the entire energy group, which comprises of a massive 74,000 employees. Speaking at the London leg of AppDynamic’s World Tour, Andy Sturrock, head of modernise IT transformation at BP, admitted that the energy company had been too reliant on outsourcing in the past. “We looked at ourselves and realised that we had become an IT organisation which didn’t really do IT, we facilitated other companies doing IT to us," he said. "So we wanted to get back to us being an IT organisation and developing our own capability again." BP removes reliance on third-party providers by bringing IT in-house | Channel Asia DECENTRALISING THE INTERNET No, this isn't a story plot out of the show Silicon Valley - Fixing the internet can look like mission impossible, even in the West. A Jeffersonian reform in the form of Web 3.0 appears a long way off, and its regulatory equivalent, a vigorous antitrust policy, does not look much more promising. Online, humanity seems bound to sink ever deeper into a Hamiltonian hole. But such an outcome is not inevitable. | Malware Hack Threat Guideline | |||
| 2018-07-05 13:47:02 | Gentoo hack caused by three rookie mistakes (lien direct) | The developers of Gentoo Linux have revealed how it was possible for its GitHub repository to be hacked: someone deduced an admin's password and perhaps that admin ought not to have had access to the repos anyway. View full story ORIGINAL SOURCE: The Register | Hack | |||
| 2018-07-05 06:14:05 | Gentoo Publishes Incident Report After GitHub Hack (lien direct) | 
|
Hack | |||
| 2018-07-05 03:28:00 | Password-Guessing Was Used to Hack Gentoo Linux Github Account (lien direct) | Maintainers of the Gentoo Linux distribution have now revealed the impact and "root cause" of the attack that saw unknown hackers taking control of its GitHub account last week and modifying the content of its repositories and pages.
The hackers not only managed to change the content in compromised repositories but also locked out Gentoo developers from their GitHub organisation.
As a result
|
Hack | |||
| 2018-07-03 10:00:03 | (Déjà vu) Hack the Box Challenge: Jail Walkthrough (lien direct) | Hello friends!! Today we are going to solve another CTF challenge “Jail” which is available online for those who want to increase their skill in penetration testing and black box testing. Jail is retired vulnerable lab presented by Hack the Box for making online penetration practices according to your experience level; they have the collection of vulnerable... Continue reading → | Hack | |||
| 2018-07-02 06:18:05 | (Déjà vu) Hack the Box Challenge: Nibble Walkthrough (lien direct) | Hello friends!! Today we are going to solve another CTF challenge “Nibble” which is categories as retired lab presented by Hack the Box for making online penetration practices. Level: Easy Task: find user.txt and root.txt file on victim's machine. Since these labs are online accessible therefore they have static IP. The IP of Nibble is 10.10.10.75 so let's initiate with nmap port enumeration. [crayon-5b3df99b98178917722383/] As... Continue reading → | Hack | |||
| 2018-06-30 07:32:04 | Hack The Blackmarket VM (CTF Challenge) (lien direct) | BlackMarket VM presented at Brisbane SecTalks BNE0x1B (28th Session) which is focused on students and other InfoSec Professional. This VM has total 6 flags and one r00t flag. Each Flag leads to another Flag and flag format is flag {blahblah}. Download it from here. VM Difficulty Level: Beginner/Intermediate Penetrating Methodology Network Scanning (Nmap, netdiscover) Information gathering:... Continue reading → | Hack Guideline | |||
| 2018-06-29 08:17:05 | (Déjà vu) Hack the Box: October Walkthrough (lien direct) | Hello friends!! Today we are going to solve another CTF challenge “October” which is available online for those who want to increase their skill in penetration testing and black box testing. October is retired vulnerable lab presented by Hack the Box for making online penetration practices according to your experience level; they have the collection of vulnerable... Continue reading → | Hack | |||
| 2018-06-29 03:50:01 | File-Wiping Malware Placed Inside Gentoo Linux Code After GitHub Account Hack (lien direct) | An unknown hacker has temporarily taken control over the GitHub account of the Gentoo Linux organization and embedded malicious code inside the operating system's distributions that would delete user files. [...] | Malware Hack | |||
| 2018-06-28 21:15:02 | Hacking Container Ships To Access The Serial Ports And Networks (lien direct) | Ethical hacking firm, Pen Test Partners, published a blog earlier this week detailing how simple it is to hack container ships to access the serial ports and networks. The blog discusses three different ways to intercept and modify serial data on ship networks – the serial data that controls steering, engine control and much more. Adam Brown, Manager … The ISBuzz Post: This Post Hacking Container Ships To Access The Serial Ports And Networks | Hack | |||
| 2018-06-28 17:38:00 | Rewards Points Targeted by Teens in Hack of 500K Accounts (lien direct) | The two teens used the rewards points built up in the accounts to make purchases, before selling the account credentials on the Dark Web. | Hack | |||
| 2018-06-28 17:00:05 | Ticketmaster Data Breach (lien direct) | Ticketmaster suffered a security breach believe to affect up to 40,000 UK customers. In tweet, firm confirmed that third-party customer support product Inbenta Technologies caused the hack and all affected customers have been contacted. IT security experts commented below. Pravin Kothari, CEO at CipherCloud: “Fool me once, shame on you. Fool me twice, shame on me. Ticketmaster's website … The ISBuzz Post: This Post Ticketmaster Data Breach | Data Breach Hack | |||
| 2018-06-28 11:30:03 | Ticketmaster \'warned of hack attack in April by Monzo\' (lien direct) | Digital bank Monzo claims it warned Ticketmaster that data had been compromised three months ago. | Hack | |||
| 2018-06-27 17:08:01 | Ticketmaster admits personal data stolen in hack attack (lien direct) | Up to 40,000 UK customers may have had data stolen, the BBC understands. | Hack | |||
| 2018-06-27 16:10:02 | Fastbooking Hack Leaves Japan Hotel Red-Faced (lien direct) | A Japanese hotel chain has apologised after more than 120,000 items of customer information were stolen in hacks of its reservations handled by French company Fastbooking. | Hack |
To see everything:
Our RSS (filtrered)
