What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2018-06-27 07:41:00 | (Déjà vu) Hack The Box : Nineveh Walkthrough (lien direct) | Hello friends!! Today we are going to solve another CTF challenge “Nineveh” which is categories as retired lab presented by Hack the Box for making online penetration practices. Level: Intermidate Task: find user.txt and root.txt file on victim's machine. Since these labs are online accessible therefore they have static IP. The IP of Nineveh is 10.10.10.43 so let's initiate with nmap port enumeration. [crayon-5b334375bea26466936564/]... Continue reading → | Hack | |||
| 2018-06-26 06:20:01 | Hack The Gemini Inc (CTF Challenge) (lien direct) | Gemini Inc has contacted you to perform a penetration testing on one of their internal systems. This system has a web application that is meant for employees to export their profile to a PDF. Identify any vulnerabilities possible with the goal of complete system compromise with root privilege. To demonstrate the level of access obtained,... Continue reading → | Hack | |||
| 2018-06-26 04:44:00 | Lazarus APT hackers leverages HWP Documents in a recent string of attacks (lien direct) | Security researchers at AlienVault uncovered a series of cyber attacks on cryptocurrency exchanges leveraging weaponized Hangul Word Processor HWP documents (Hangul Word Processor documents). The string of attacks involving the HWP documents has been attributed to the North Korea-linked Lazarus APT group, and includes the hack of the South Korean virtual currency exchange Bithumb. The hackers […] | Hack Threat | Bithumb APT 38 | ||
| 2018-06-26 03:40:00 | 4 scams that illustrate the one-way authentication problem (lien direct) | My 11 ways to hack 2FA column a few weeks ago continues to be a popular discussion topic with readers. Most people are shocked about how easy it is to hack around two-factor (2FA) and multi-factor authentication (MFA). It isn't hard. Sometimes it's as easy as a regular phishing email. [ Learn about alternatives to the password. | Get the latest from CSO by signing up for our newsletters. ] | Hack | |||
| 2018-06-25 15:03:20 | Bejtlich on the APT1 Report: No Hack Back (lien direct) |  Before reading the rest of this post, I suggest reading Mandiant/FireEye's statement Doing Our Part -- Without Hacking Back.I would like to add my own color to this situation.First, at no time when I worked for Mandiant or FireEye, or afterwards, was there ever a notion that we would hack into adversary systems. During my six year tenure, we were publicly and privately a "no hack back" company. I never heard anyone talk about hack back operations. No one ever intimated we had imagery of APT1 actors taken with their own laptop cameras. No one even said that would be a good idea.Second, I would never have testified or written, repeatedly, about our company's stance on not hacking back if I knew we secretly did otherwise. I have quit jobs because I had fundamental disagreements with company policy or practice. I worked for Mandiant from 2011 through the end of 2013, when FireEye acquired Mandiant, and stayed until last year (2017). I never considered quitting Mandiant or FireEye due to a disconnect between public statements and private conduct.Third, I was personally involved with briefings to the press, in public and in private, concerning the APT1 report. I provided the voiceover for a 5 minute YouTube video called APT1: Exposing One of China's Cyber Espionage Units. That video was one of the most sensitive, if not the most sensitive, aspects of releasing the report. We showed the world how we could intercept adversary communications and reconstruct it. There was internal debate about whether we should do that. We decided to cover the practice it in the report, as Christopher Glyer Tweeted: Before reading the rest of this post, I suggest reading Mandiant/FireEye's statement Doing Our Part -- Without Hacking Back.I would like to add my own color to this situation.First, at no time when I worked for Mandiant or FireEye, or afterwards, was there ever a notion that we would hack into adversary systems. During my six year tenure, we were publicly and privately a "no hack back" company. I never heard anyone talk about hack back operations. No one ever intimated we had imagery of APT1 actors taken with their own laptop cameras. No one even said that would be a good idea.Second, I would never have testified or written, repeatedly, about our company's stance on not hacking back if I knew we secretly did otherwise. I have quit jobs because I had fundamental disagreements with company policy or practice. I worked for Mandiant from 2011 through the end of 2013, when FireEye acquired Mandiant, and stayed until last year (2017). I never considered quitting Mandiant or FireEye due to a disconnect between public statements and private conduct.Third, I was personally involved with briefings to the press, in public and in private, concerning the APT1 report. I provided the voiceover for a 5 minute YouTube video called APT1: Exposing One of China's Cyber Espionage Units. That video was one of the most sensitive, if not the most sensitive, aspects of releasing the report. We showed the world how we could intercept adversary communications and reconstruct it. There was internal debate about whether we should do that. We decided to cover the practice it in the report, as Christopher Glyer Tweeted:  In none of these briefings to the press did we show pictures or video from adversary laptops. We did show the video that we published to YouTube.Fourth, I privately contacted former Mandiant personnel with whom I worked during the time of the APT1 report creation and distribution. Their reaction to Mr Sanger's allegations ranged from "I've never heard of that" to "completely false." I asked former Mandiant colleagues, like myself, In none of these briefings to the press did we show pictures or video from adversary laptops. We did show the video that we published to YouTube.Fourth, I privately contacted former Mandiant personnel with whom I worked during the time of the APT1 report creation and distribution. Their reaction to Mr Sanger's allegations ranged from "I've never heard of that" to "completely false." I asked former Mandiant colleagues, like myself, |
Hack | APT 1 | ||
| 2018-06-25 12:50:00 | iOS Hack Lets Attackers Brute Force iPhone, iPad Passcodes (lien direct) | A vulnerability in Apple's iOS lets anyone with a Lightning cable bypass the passcode entry restriction designed to protect the company's devices. | Hack Vulnerability | |||
| 2018-06-25 09:32:03 | Hack The Vulnhub Pentester Lab: S2-052 (lien direct) | Hello friend!! Today we are going to exploit another VM lab which is designed by Pentester Lab covers the exploitation of the Struts S2-052 vulnerability. The REST Plugin is using a XStreamHandler with an instance of XStream for deserialization without any type filtering and this can lead to Remote Code Execution when deserializing XML payloads. Source: https://cwiki.apache.org/confluence/display/WW/S2-052 Table... Continue reading → | Hack Guideline | |||
| 2018-06-23 05:15:04 | (Déjà vu) Hack the Box Challenge: Sneaky Walkthrough (lien direct) | Hello friends!! Today we are going to solve another CTF challenge “Sneaky” which is available online for those who want to increase their skill in penetration testing and black box testing. Sneaky is retired vulnerable lab presented by Hack the Box for making online penetration practices according to your experience level; they have the collection of vulnerable... Continue reading → | Hack | |||
| 2018-06-22 13:00:00 | Things I Hearted this Week, 22nd June 2018 (lien direct) |
 The Tesla Insider
Elon Musk sent out an email stating an employee had stabbed the company in the back like Brutus, changing production code, and leaking inside information. I'll admit that like many people who have talked about or written about insider threats in the past, I instinctively punched the air and yelled, "YES! I warned you but you didn't listen."
The incident is also notable for the impact it had on the company's share price which dropped more than 6% in trading.
"I was dismayed to learn this weekend about a Tesla employee who had conducted quite extensive and damaging sabotage to our operations, this included making direct code changes to the Tesla Manufacturing Operating System under false usernames and exporting large amounts of highly sensitive Tesla data to unknown third parties."
Insider threats defined | AlienVault
Tesla hit by insider saboteur who changed code, exfiltrated data | SC Magazine
Tesla sinks after Elon Musk says an employee conducted 'sabotage' and Trump ramps up fears of a trade war (TSLA) | Business Insider
Can't Fix Won't Fix, Don't Fix
Organisations cannot afford to view penetration testing as a tick box exercise. How should they mitigate the fact some vulnerabilities can’t be fixed, won’t be fixed, and in some instances, actually shouldn’t be fixed?
Can’t fix, won’t fix, don’t fix: Is it time for businesses to rethink how they action pen test results?| IT Pro Portal
On the topic of pen tests, check out Adrian Sanabria's presentation slides from RSA earlier this year on killing the pen test.
It's time to kill the pen test (PDF) | RSAconference
To add balance, and to convince you pen testers out there that I'm not a bad person who hates all pen testers, here's an awesome collection of penetration testing resources that include tools, online resources, books, courses, conferences, magazine...
Awesome Penetration Testing | Kinimiwar, GitHub
A Case Study In Bad Disclosure
Imagine you're a researcher and have found a vulnerability, you then disclose it responsibly to a vendor, then that vendor fixes the issue - but instead of sending the chopper over to you with a care package, they pretend like you didn't exist. Akin to Tom Cruise getting disavowed in every single Mission Impossible movie.
Then imagine that vendor submitted the vulnerability details to Google and received a bug bounty award to the tune of $5,000.
Then to top it off, they sat back in a massive reclining chair, threw their head back and laughed as they donated the full $5,000 to a good cause.
The Tesla Insider
Elon Musk sent out an email stating an employee had stabbed the company in the back like Brutus, changing production code, and leaking inside information. I'll admit that like many people who have talked about or written about insider threats in the past, I instinctively punched the air and yelled, "YES! I warned you but you didn't listen."
The incident is also notable for the impact it had on the company's share price which dropped more than 6% in trading.
"I was dismayed to learn this weekend about a Tesla employee who had conducted quite extensive and damaging sabotage to our operations, this included making direct code changes to the Tesla Manufacturing Operating System under false usernames and exporting large amounts of highly sensitive Tesla data to unknown third parties."
Insider threats defined | AlienVault
Tesla hit by insider saboteur who changed code, exfiltrated data | SC Magazine
Tesla sinks after Elon Musk says an employee conducted 'sabotage' and Trump ramps up fears of a trade war (TSLA) | Business Insider
Can't Fix Won't Fix, Don't Fix
Organisations cannot afford to view penetration testing as a tick box exercise. How should they mitigate the fact some vulnerabilities can’t be fixed, won’t be fixed, and in some instances, actually shouldn’t be fixed?
Can’t fix, won’t fix, don’t fix: Is it time for businesses to rethink how they action pen test results?| IT Pro Portal
On the topic of pen tests, check out Adrian Sanabria's presentation slides from RSA earlier this year on killing the pen test.
It's time to kill the pen test (PDF) | RSAconference
To add balance, and to convince you pen testers out there that I'm not a bad person who hates all pen testers, here's an awesome collection of penetration testing resources that include tools, online resources, books, courses, conferences, magazine...
Awesome Penetration Testing | Kinimiwar, GitHub
A Case Study In Bad Disclosure
Imagine you're a researcher and have found a vulnerability, you then disclose it responsibly to a vendor, then that vendor fixes the issue - but instead of sending the chopper over to you with a care package, they pretend like you didn't exist. Akin to Tom Cruise getting disavowed in every single Mission Impossible movie.
Then imagine that vendor submitted the vulnerability details to Google and received a bug bounty award to the tune of $5,000.
Then to top it off, they sat back in a massive reclining chair, threw their head back and laughed as they donated the full $5,000 to a good cause.
|
Hack Vulnerability Guideline | Bithumb Tesla Tesla | ||
| 2018-04-23 16:10:10 | Abusing MySQL LOCAL INFILE to read client files (lien direct) | Recently, I was playing the VolgaCTF 2018 CTF with my teammates from TheGoonies and we came across an interesting Web challenge that we didn't manage to solve during the competition. The following day, I read the write-up and learned a cool technique to attack the MySQL client directly via the LOAD DATA INFILE statement.The "Corp Monitoring" task consisted of a Corporate Monitoring API that would test the healthcheck of a given server by connecting and verifying if the FTP, Web and MySQL servers were up. The MySQL user for the connection was restricted and the healthcheck validation was based on a few queries including the "SHOW DATABASE" command.The key to solve the challenge was to identify the "Can Use LOAD DATA LOCAL" client capability and point the API to a Rogue MySQL server that would read arbitrary files from the client via LOAD DATA INFILE statements.After reading about the technique, I decided to check how several libraries, clients and Web Frameworks could be exploited. I also ended up writing a a Bettercap module to abuse this feature in combination with MITM attacks. Previous Research Before I start I would like to point that this technique is not new: it's a known and documented feature from the MySQL clients. I gathered prior posts, tools and presentations and they're all written by Russians - it looks like these techniques are not very widespread outside there.- Database Honeypot by design - Presentation from Yuri Goltsev (August 2013)- Rogue-MySql-Server Tool: MySQL fake server to read files of connected clients (September 2013)- MySQL connect file read - Post from the Russian Security (April 2016)Revisiting MySQL LOAD DATA INFILEAccording to the MySQL documentation, the handshake connection phase performs the following tasks:- Exchange the capabilities of client and server- Setup SSL communication channel if requested- Authenticate the client against the serverAfter the successful authentication, the client sends the query and waits for the server response before actually doing something. The "Client Capabilities" packet includes an entry called "Can Use LOAD DATA LOCAL". Previous Research Before I start I would like to point that this technique is not new: it's a known and documented feature from the MySQL clients. I gathered prior posts, tools and presentations and they're all written by Russians - it looks like these techniques are not very widespread outside there.- Database Honeypot by design - Presentation from Yuri Goltsev (August 2013)- Rogue-MySql-Server Tool: MySQL fake server to read files of connected clients (September 2013)- MySQL connect file read - Post from the Russian Security (April 2016)Revisiting MySQL LOAD DATA INFILEAccording to the MySQL documentation, the handshake connection phase performs the following tasks:- Exchange the capabilities of client and server- Setup SSL communication channel if requested- Authenticate the client against the serverAfter the successful authentication, the client sends the query and waits for the server response before actually doing something. The "Client Capabilities" packet includes an entry called "Can Use LOAD DATA LOCAL". |
Hack Tool Vulnerability | ★★★★ | ||
| 2016-03-15 19:09:18 | 0CTF 2016 Write Up: Monkey (Web 4) (lien direct) | The Chinese 0CTF took place on March 12-13 and it was yet another fun CTF. I played with my teammates from TheGoonies and we were ranked #48.I found the Web task "Monkey" particularly interesting: I solved it with the help from my friend @danilonc, but it took way longer than it should because of some **Spoiler Alert** DNS glitches. According to the scoreboard status, approximately 35 teams were able to solve it.Task: Monkey (Web - 4pts)What is Same Origin Policy?you can test this problem on your local machinehttp://202.120.7.200The running application receives a Proof-of-Work string and an arbitrary URL, instructing a "monkey" to browse the inputted URL for 2 minutes.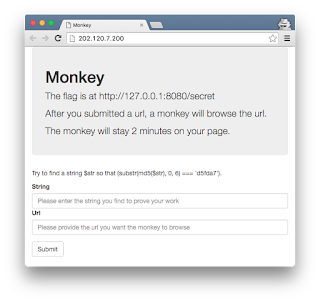 Proof-of-WorkSolving the proof-of-work is pretty straightforward. We had to generate random strings and compare the first 6 chars from its MD5 against the challenge. The POW challenge was more cpu-intensive than normal, so the traditional bash/python one-liner ctf scripts would require some performance improvements.@danilonc had written a quick hack using Go to bruteforce and solve POW from older CTF challs, so we just slightly modified it: Solving the Proof-of-Work: Proof-of-WorkSolving the proof-of-work is pretty straightforward. We had to generate random strings and compare the first 6 chars from its MD5 against the challenge. The POW challenge was more cpu-intensive than normal, so the traditional bash/python one-liner ctf scripts would require some performance improvements.@danilonc had written a quick hack using Go to bruteforce and solve POW from older CTF challs, so we just slightly modified it: Solving the Proof-of-Work: Same-Origin-Policy and CORSThe Same-Origin-Policy (SOP) deems pages having the same URI scheme, hostname and port as residing at the same-origin. If any of these three attributes varies, the resource is in a different origin. Hence, if provided resources come from the same hostname, scheme and port, they can interact without restriction.If you try to use an XMLHttpRequest to send a request to a different origin, you can't read the response. However, the request will still arrive at its destination. This policy prevents a malicious script on one page from obtaining access to sensitive data (both the header and the body) on another web page, on a different origin.For this particular CTF challenge, if the secret internal webpage had had an insecure CORS header like "Access-Control-Allow-Origin: *", we would be able to retrieve its data with no effort. This, of course, was not the case.Bypassing the Same-OriginThe flag was accessible on an internal webserver hosted at http://127.0.0.1:8080/secret. The first thing we did was hooking the monkey's browser using BeEF, so we could fingerprint his device, platform, plugins and components. Same-Origin-Policy and CORSThe Same-Origin-Policy (SOP) deems pages having the same URI scheme, hostname and port as residing at the same-origin. If any of these three attributes varies, the resource is in a different origin. Hence, if provided resources come from the same hostname, scheme and port, they can interact without restriction.If you try to use an XMLHttpRequest to send a request to a different origin, you can't read the response. However, the request will still arrive at its destination. This policy prevents a malicious script on one page from obtaining access to sensitive data (both the header and the body) on another web page, on a different origin.For this particular CTF challenge, if the secret internal webpage had had an insecure CORS header like "Access-Control-Allow-Origin: *", we would be able to retrieve its data with no effort. This, of course, was not the case.Bypassing the Same-OriginThe flag was accessible on an internal webserver hosted at http://127.0.0.1:8080/secret. The first thing we did was hooking the monkey's browser using BeEF, so we could fingerprint his device, platform, plugins and components. |
Hack | ★★★★ | ||
| 2015-12-09 01:03:30 | Hack.lu 2015 CTF Write Up: Dr. Bob (Forensic 150) (lien direct) | Hack.lu 2015 CTF was organised by fluxfingers during October 20-22. It's one of the coolest CTFs around, the only drawback is that it runs during week days (hey guys patch this for the next years). My team TheGoonies ranked #59th, which is not bad considering we only played part-time.The task Dr. Bob was the one I found most interesting as it included disk forensics, memory forensics and basic crypto tasks.Task: Dr. Bob (Forensic 150)There are elections at the moment for the representative of the students and the winner will be announced tomorrow by the head of elections Dr. Bob. The local schoolyard gang is gambling on the winner and you could really use that extra cash. Luckily, you are able to hack into the mainframe of the school and get a copy of the virtual machine that is used by Dr. Bob to store the results. The desired information is in the file /home/bob/flag.txt, easy as that.Download: dr_bob_e22538fa166acecc68fa17ac148dcbe2.tar.gzThe file provided is a VirtualBox image in a saved state. According to the challenge instructions, we have to retrieve the flag from the user home folder. The VM starts on a login terminal of what seems to be a Linux distro.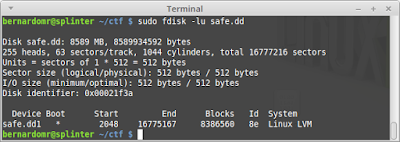 sudo losetup -o 1048576 /dev/loop0 safe.ddsudo lvmdiskscan sudo losetup -o 1048576 /dev/loop0 safe.ddsudo lvmdiskscan There are two interesting devices: /dev/vg/root and /dev/vg/home, let's 1 - mount the home folder, 2 - grab the flag and 3 - PROFIT!!! There are two interesting devices: /dev/vg/root and /dev/vg/home, let's 1 - mount the home folder, 2 - grab the flag and 3 - PROFIT!!! |
Hack Tool | ★★★★ | ||
| 2015-05-04 23:57:38 | Firmware Forensics: Diffs, Timelines, ELFs and Backdoors (lien direct) | This post covers some common techniques that I use to analyze and reverse firmware images. These techniques are particularly useful to dissect malicious firmwares, spot backdoors and detect unwanted modifications.Backdooring and re-flashing firmware images is becoming mainstream: malicious guys are infecting embedded devices and inserting trojans in order to achieve persistence. Recent articles covered the increasing number of trojanized android firmwares and routers that are being permanently modified.Attackers with a privileged network position may MITM your requests and forge fake updates containing malicious firmwares. Writing Evilgrade modules for this is really simple, as most vendors keep failing to deliver updates securely, right ASUS? Valid signature -> nvram_set("rsasign_check", "1")NoConName 2014 CTF Finals: VodkaI'll keep my tradition of writing posts based on CTF challenges because everybody upvotes CTF posts on reddit it's cool.The challenge "Vodka", from NoConName 2014 CTF Finals was created by @MarioVilas, who kindly provided the files here (thanks dude!).I did not participate on the CTF finals, but I found the challenge really interesting because there were many different ways to solve it, summarizing the actions needed to audit a compromised f Valid signature -> nvram_set("rsasign_check", "1")NoConName 2014 CTF Finals: VodkaI'll keep my tradition of writing posts based on CTF challenges because everybody upvotes CTF posts on reddit it's cool.The challenge "Vodka", from NoConName 2014 CTF Finals was created by @MarioVilas, who kindly provided the files here (thanks dude!).I did not participate on the CTF finals, but I found the challenge really interesting because there were many different ways to solve it, summarizing the actions needed to audit a compromised f |
Malware Hack Tool | ★★★★ | ||
| 2015-02-27 00:56:54 | Extracting RAW pictures from memory dumps (lien direct) | IntroductionEarlier today, while reading my Twitter timeline, I saw some Infosec folks discussing about scripts/tools to identify RAW pictures in memory dumps. I decided, then, to write this blog post and share a small hack that I use to visualize data (including memory dumps). Memory DumpsThe first thing you will want to do is to narrow the analysis to the process containing interesting images/pictures. I'm going to use three different memory dumps here:Remote Desktop Client - Windows 7 x64 (mstsc.exe)Let's use the Windows built-in RDP client to connect to an external server and dump the processmemory using procdump: Memory DumpsThe first thing you will want to do is to narrow the analysis to the process containing interesting images/pictures. I'm going to use three different memory dumps here:Remote Desktop Client - Windows 7 x64 (mstsc.exe)Let's use the Windows built-in RDP client to connect to an external server and dump the processmemory using procdump: |
Hack Tool | ★★★★ | ||
| 2013-09-01 10:52:31 | Analyzing and Running binaries from Firmware Images - Part 1 (lien direct) | During the first part of SIMET Box Firmware analysis, we downloaded the firmware Image, extracted its contents, compared/analyzed its base and found a couple of interesting files (SSH keys, binary files, init scripts, firewall rules and so on).For this part we'll focus on identifying binaries, comparing and executing them to find interesting data. Whenever you're analyzing binaries from different architectures, there are a couple of nice tools that aid debugging, reversing and emulating their behavior, like objdump, readelf and QEMU.Embedded Debian Project provides pre-built binary toolchains for mips, mipsel, arm, armel, powerpc, and a couple of other architectures. In order to download and install it on Debian based Linux distros, you have to apt-get its archive signing key:sudo apt-get install emdebian-archive-keyringNow you you need to include their repository on your /etc/apt/sources.list: deb http://www.emdebian.org/debian/ squeeze mainAfter the apt-get update you can install binutils for you target archs:sudo apt-get install binutils-mips-linux-gnu binutils-mipsel-linux-gnu binutils-arm-linux-gnueabiFor this little exercise I'll analyze three busybox binaries, from three different firmwares: busybox-simet (from SIMET Box), busybox-asuswrt (from AsusWRT-Merlin firmware) and busybox-sb6120 (from Motorolla's SB6120 Surfboard Cable Modem).Architecture, Big-Endian or Little Endian?When analyzing SIMET Box we already knew that the device was based on ar71xx platform, which is MIPS based and big endian as stated on OpenWRT's official page. If you want to find it by your own you can use the file utility: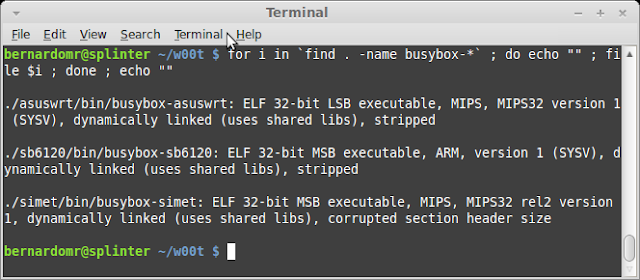 Emdebian binutils also provide useful tools to identify further info from unknown binaries. A nice hack that I commonly use is to display information from object files using different toolchains in order to find out which one understands the file structure properly. For example, objdump -f displays contents of the overall file header.SIMET Box tl-wr740n-v4 (architecture: mips:isa32r2, file format elf32-tradbigmips) Emdebian binutils also provide useful tools to identify further info from unknown binaries. A nice hack that I commonly use is to display information from object files using different toolchains in order to find out which one understands the file structure properly. For example, objdump -f displays contents of the overall file header.SIMET Box tl-wr740n-v4 (architecture: mips:isa32r2, file format elf32-tradbigmips)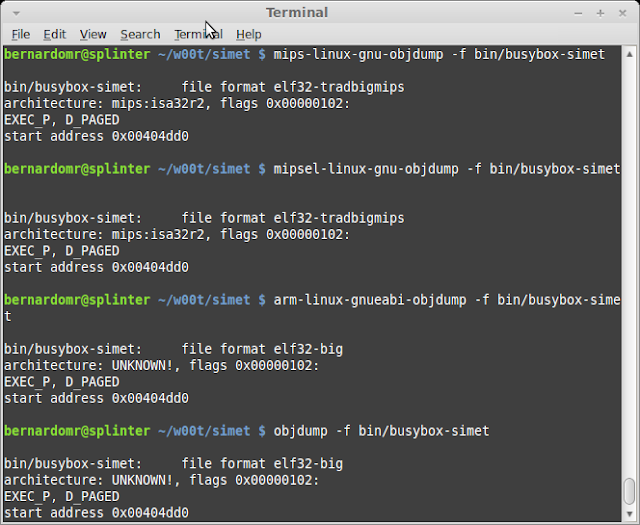 AsusWRT-Merlin v3.0.0.4.374.32 (architecture: mips:isa32 file format elf32-tradlittlemips) AsusWRT-Merlin v3.0.0.4.374.32 (architecture: mips:isa32 file format elf32-tradlittlemips) SB6120 v1.0.2.4-SCM01 (architecture: arm, file format elf32-bigarm) SB6120 v1.0.2.4-SCM01 (architecture: arm, file format elf32-bigarm) |
Malware Hack | ★★★★ |
To see everything:
Our RSS (filtrered)
