What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-04-20 12:22:15 | Plus d'entreprises avec cyber-assurance sont touchées par des ransomwares que ceux sans More Companies with Cyber Insurance Are Hit by Ransomware Than Those Without (lien direct) |

|
Ransomware | ★★★★ | ||
| 2023-04-11 13:16:54 | Cyberheistnews Vol 13 # 15 [Le nouveau visage de la fraude] FTC fait la lumière sur les escroqueries d'urgence familiale améliorées AI-AI CyberheistNews Vol 13 #15 [The New Face of Fraud] FTC Sheds Light on AI-Enhanced Family Emergency Scams (lien direct) |
 CyberheistNews Vol 13 #15 | April 11th, 2023
[The New Face of Fraud] FTC Sheds Light on AI-Enhanced Family Emergency Scams
The Federal Trade Commission is alerting consumers about a next-level, more sophisticated family emergency scam that uses AI which imitates the voice of a "family member in distress."
They started out with: "You get a call. There\'s a panicked voice on the line. It\'s your grandson. He says he\'s in deep trouble - he wrecked the car and landed in jail. But you can help by sending money. You take a deep breath and think. You\'ve heard about grandparent scams. But darn, it sounds just like him. How could it be a scam? Voice cloning, that\'s how."
"Don\'t Trust The Voice"
The FTC explains: "Artificial intelligence is no longer a far-fetched idea out of a sci-fi movie. We\'re living with it, here and now. A scammer could use AI to clone the voice of your loved one. All he needs is a short audio clip of your family member\'s voice - which he could get from content posted online - and a voice-cloning program. When the scammer calls you, he\'ll sound just like your loved one.
"So how can you tell if a family member is in trouble or if it\'s a scammer using a cloned voice? Don\'t trust the voice. Call the person who supposedly contacted you and verify the story. Use a phone number you know is theirs. If you can\'t reach your loved one, try to get in touch with them through another family member or their friends."
Full text of the alert is at the FTC website. Share with friends, family and co-workers:https://blog.knowbe4.com/the-new-face-of-fraud-ftc-sheds-light-on-ai-enhanced-family-emergency-scams
A Master Class on IT Security: Roger A. Grimes Teaches Ransomware Mitigation
Cybercriminals have become thoughtful about ransomware attacks; taking time to maximize your organization\'s potential damage and their payoff. Protecting your network from this growing threat is more important than ever. And nobody knows this more than Roger A. Grimes, Data-Driven Defense Evangelist at KnowBe4.
With 30+ years of experience as a computer security consultant, instructor, and award-winning author, Roger has dedicated his life to making
CyberheistNews Vol 13 #15 | April 11th, 2023
[The New Face of Fraud] FTC Sheds Light on AI-Enhanced Family Emergency Scams
The Federal Trade Commission is alerting consumers about a next-level, more sophisticated family emergency scam that uses AI which imitates the voice of a "family member in distress."
They started out with: "You get a call. There\'s a panicked voice on the line. It\'s your grandson. He says he\'s in deep trouble - he wrecked the car and landed in jail. But you can help by sending money. You take a deep breath and think. You\'ve heard about grandparent scams. But darn, it sounds just like him. How could it be a scam? Voice cloning, that\'s how."
"Don\'t Trust The Voice"
The FTC explains: "Artificial intelligence is no longer a far-fetched idea out of a sci-fi movie. We\'re living with it, here and now. A scammer could use AI to clone the voice of your loved one. All he needs is a short audio clip of your family member\'s voice - which he could get from content posted online - and a voice-cloning program. When the scammer calls you, he\'ll sound just like your loved one.
"So how can you tell if a family member is in trouble or if it\'s a scammer using a cloned voice? Don\'t trust the voice. Call the person who supposedly contacted you and verify the story. Use a phone number you know is theirs. If you can\'t reach your loved one, try to get in touch with them through another family member or their friends."
Full text of the alert is at the FTC website. Share with friends, family and co-workers:https://blog.knowbe4.com/the-new-face-of-fraud-ftc-sheds-light-on-ai-enhanced-family-emergency-scams
A Master Class on IT Security: Roger A. Grimes Teaches Ransomware Mitigation
Cybercriminals have become thoughtful about ransomware attacks; taking time to maximize your organization\'s potential damage and their payoff. Protecting your network from this growing threat is more important than ever. And nobody knows this more than Roger A. Grimes, Data-Driven Defense Evangelist at KnowBe4.
With 30+ years of experience as a computer security consultant, instructor, and award-winning author, Roger has dedicated his life to making |
Ransomware Data Breach Spam Malware Hack Tool Threat | ChatGPT ChatGPT | ★★ | |
| 2023-04-11 12:20:01 | Top à emporter, vous pourriez manquer ma prochaine classe de maître de ransomware Top Takeaways You Could be Missing Out on my Upcoming Ransomware Master Class (lien direct) |

|
Ransomware | ★★ | ||
| 2023-04-04 13:50:02 | Scareware d'un groupe de ransomwares bidon Scareware From a Phony Ransomware Group (lien direct) |

|
Ransomware | ★★ | ||
| 2023-04-04 13:00:00 | CyberheistNews Vol 13 # 14 [Eyes sur le prix] Comment les inconvénients croissants ont tenté un courteur par e-mail de 36 millions de vendeurs CyberheistNews Vol 13 #14 [Eyes on the Prize] How Crafty Cons Attempted a 36 Million Vendor Email Heist (lien direct) |
 CyberheistNews Vol 13 #14 | April 4th, 2023
[Eyes on the Prize] How Crafty Cons Attempted a 36 Million Vendor Email Heist
The details in this thwarted VEC attack demonstrate how the use of just a few key details can both establish credibility and indicate the entire thing is a scam.
It\'s not every day you hear about a purely social engineering-based scam taking place that is looking to run away with tens of millions of dollars. But, according to security researchers at Abnormal Security, cybercriminals are becoming brazen and are taking their shots at very large prizes.
This attack begins with a case of VEC – where a domain is impersonated. In the case of this attack, the impersonated vendor\'s domain (which had a .com top level domain) was replaced with a matching .cam domain (.cam domains are supposedly used for photography enthusiasts, but there\'s the now-obvious problem with it looking very much like .com to the cursory glance).
The email attaches a legitimate-looking payoff letter complete with loan details. According to Abnormal Security, nearly every aspect of the request looked legitimate. The telltale signs primarily revolved around the use of the lookalike domain, but there were other grammatical mistakes (that can easily be addressed by using an online grammar service or ChatGPT).
This attack was identified well before it caused any damage, but the social engineering tactics leveraged were nearly enough to make this attack successful. Security solutions will help stop most attacks, but for those that make it past scanners, your users need to play a role in spotting and stopping BEC, VEC and phishing attacks themselves – something taught through security awareness training combined with frequent simulated phishing and other social engineering tests.
Blog post with screenshots and links:https://blog.knowbe4.com/36-mil-vendor-email-compromise-attack
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human firewall as your last line of defense.
Join us TOMORROW, Wednesday, April 5, @ 2:00 PM (ET), for a live demo of how KnowBe4 i
CyberheistNews Vol 13 #14 | April 4th, 2023
[Eyes on the Prize] How Crafty Cons Attempted a 36 Million Vendor Email Heist
The details in this thwarted VEC attack demonstrate how the use of just a few key details can both establish credibility and indicate the entire thing is a scam.
It\'s not every day you hear about a purely social engineering-based scam taking place that is looking to run away with tens of millions of dollars. But, according to security researchers at Abnormal Security, cybercriminals are becoming brazen and are taking their shots at very large prizes.
This attack begins with a case of VEC – where a domain is impersonated. In the case of this attack, the impersonated vendor\'s domain (which had a .com top level domain) was replaced with a matching .cam domain (.cam domains are supposedly used for photography enthusiasts, but there\'s the now-obvious problem with it looking very much like .com to the cursory glance).
The email attaches a legitimate-looking payoff letter complete with loan details. According to Abnormal Security, nearly every aspect of the request looked legitimate. The telltale signs primarily revolved around the use of the lookalike domain, but there were other grammatical mistakes (that can easily be addressed by using an online grammar service or ChatGPT).
This attack was identified well before it caused any damage, but the social engineering tactics leveraged were nearly enough to make this attack successful. Security solutions will help stop most attacks, but for those that make it past scanners, your users need to play a role in spotting and stopping BEC, VEC and phishing attacks themselves – something taught through security awareness training combined with frequent simulated phishing and other social engineering tests.
Blog post with screenshots and links:https://blog.knowbe4.com/36-mil-vendor-email-compromise-attack
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human firewall as your last line of defense.
Join us TOMORROW, Wednesday, April 5, @ 2:00 PM (ET), for a live demo of how KnowBe4 i |
Ransomware Malware Hack Threat | ChatGPT ChatGPT APT 43 | ★★ | |
| 2023-03-28 13:00:00 | Cyberheistnews Vol 13 # 13 [Oeil Overner] Comment déjouer les attaques de phishing basées sur l'IA sournoises [CyberheistNews Vol 13 #13 [Eye Opener] How to Outsmart Sneaky AI-Based Phishing Attacks] (lien direct) |
 CyberheistNews Vol 13 #13 | March 28th, 2023
[Eye Opener] How to Outsmart Sneaky AI-Based Phishing Attacks
Users need to adapt to an evolving threat landscape in which attackers can use AI tools like ChatGPT to craft extremely convincing phishing emails, according to Matthew Tyson at CSO.
"A leader tasked with cybersecurity can get ahead of the game by understanding where we are in the story of machine learning (ML) as a hacking tool," Tyson writes. "At present, the most important area of relevance around AI for cybersecurity is content generation.
"This is where machine learning is making its greatest strides and it dovetails nicely for hackers with vectors such as phishing and malicious chatbots. The capacity to craft compelling, well-formed text is in the hands of anyone with access to ChatGPT, and that\'s basically anyone with an internet connection."
Tyson quotes Conal Gallagher, CIO and CISO at Flexera, as saying that since attackers can now write grammatically correct phishing emails, users will need to pay attention to the circumstances of the emails.
"Looking for bad grammar and incorrect spelling is a thing of the past - even pre-ChatGPT phishing emails have been getting more sophisticated," Gallagher said. "We must ask: \'Is the email expected? Is the from address legit? Is the email enticing you to click on a link?\' Security awareness training still has a place to play here."
Tyson explains that technical defenses have become very effective, so attackers focus on targeting humans to bypass these measures.
"Email and other elements of software infrastructure offer built-in fundamental security that largely guarantees we are not in danger until we ourselves take action," Tyson writes. "This is where we can install a tripwire in our mindsets: we should be hyper aware of what it is we are acting upon when we act upon it.
"Not until an employee sends a reply, runs an attachment, or fills in a form is sensitive information at risk. The first ring of defense in our mentality should be: \'Is the content I\'m looking at legit, not just based on its internal aspects, but given the entire context?\' The second ring of defense in our mentality then has to be, \'Wait! I\'m being asked to do something here.\'"
New-school security awareness training with simulated phishing tests enables your employees to recognize increasingly sophisticated phishing attacks and builds a strong security culture.
Remember: Culture eats strategy for breakfast and is always top-down.
Blog post with links:https://blog.knowbe4.com/identifying-ai-enabled-phishing
CyberheistNews Vol 13 #13 | March 28th, 2023
[Eye Opener] How to Outsmart Sneaky AI-Based Phishing Attacks
Users need to adapt to an evolving threat landscape in which attackers can use AI tools like ChatGPT to craft extremely convincing phishing emails, according to Matthew Tyson at CSO.
"A leader tasked with cybersecurity can get ahead of the game by understanding where we are in the story of machine learning (ML) as a hacking tool," Tyson writes. "At present, the most important area of relevance around AI for cybersecurity is content generation.
"This is where machine learning is making its greatest strides and it dovetails nicely for hackers with vectors such as phishing and malicious chatbots. The capacity to craft compelling, well-formed text is in the hands of anyone with access to ChatGPT, and that\'s basically anyone with an internet connection."
Tyson quotes Conal Gallagher, CIO and CISO at Flexera, as saying that since attackers can now write grammatically correct phishing emails, users will need to pay attention to the circumstances of the emails.
"Looking for bad grammar and incorrect spelling is a thing of the past - even pre-ChatGPT phishing emails have been getting more sophisticated," Gallagher said. "We must ask: \'Is the email expected? Is the from address legit? Is the email enticing you to click on a link?\' Security awareness training still has a place to play here."
Tyson explains that technical defenses have become very effective, so attackers focus on targeting humans to bypass these measures.
"Email and other elements of software infrastructure offer built-in fundamental security that largely guarantees we are not in danger until we ourselves take action," Tyson writes. "This is where we can install a tripwire in our mindsets: we should be hyper aware of what it is we are acting upon when we act upon it.
"Not until an employee sends a reply, runs an attachment, or fills in a form is sensitive information at risk. The first ring of defense in our mentality should be: \'Is the content I\'m looking at legit, not just based on its internal aspects, but given the entire context?\' The second ring of defense in our mentality then has to be, \'Wait! I\'m being asked to do something here.\'"
New-school security awareness training with simulated phishing tests enables your employees to recognize increasingly sophisticated phishing attacks and builds a strong security culture.
Remember: Culture eats strategy for breakfast and is always top-down.
Blog post with links:https://blog.knowbe4.com/identifying-ai-enabled-phishing
|
Ransomware Malware Hack Tool Threat Guideline | ChatGPT ChatGPT | ★★★ | |
| 2023-03-24 12:15:00 | Ransomware Data Volt Extorsion augmente de 40% à 70% de \\ '21 à \\' 22 [Ransomware Data Theft Extortion Goes up 40% to 70% From \\'21 to \\'22] (lien direct) |

|
Ransomware | ★★★ | ||
| 2023-03-14 13:00:00 | CyberheistNews Vol 13 #11 [Heads Up] Employees Are Feeding Sensitive Biz Data to ChatGPT, Raising Security Fears (lien direct) |
 CyberheistNews Vol 13 #11 | March 14th, 2023
[Heads Up] Employees Are Feeding Sensitive Biz Data to ChatGPT, Raising Security Fears
Robert Lemos at DARKReading just reported on a worrying trend. The title said it all, and the news is that more than 4% of employees have put sensitive corporate data into the large language model, raising concerns that its popularity may result in massive leaks of proprietary information. Yikes.
I'm giving you a short extract of the story and the link to the whole article is below.
"Employees are submitting sensitive business data and privacy-protected information to large language models (LLMs) such as ChatGPT, raising concerns that artificial intelligence (AI) services could be incorporating the data into their models, and that information could be retrieved at a later date if proper data security isn't in place for the service.
"In a recent report, data security service Cyberhaven detected and blocked requests to input data into ChatGPT from 4.2% of the 1.6 million workers at its client companies because of the risk of leaking confidential info, client data, source code, or regulated information to the LLM.
"In one case, an executive cut and pasted the firm's 2023 strategy document into ChatGPT and asked it to create a PowerPoint deck. In another case, a doctor input his patient's name and their medical condition and asked ChatGPT to craft a letter to the patient's insurance company.
"And as more employees use ChatGPT and other AI-based services as productivity tools, the risk will grow, says Howard Ting, CEO of Cyberhaven.
"'There was this big migration of data from on-prem to cloud, and the next big shift is going to be the migration of data into these generative apps," he says. "And how that plays out [remains to be seen] - I think, we're in pregame; we're not even in the first inning.'"
Your employees need to be stepped through new-school security awareness training so that they understand the risks of doing things like this.
Blog post with links:https://blog.knowbe4.com/employees-are-feeding-sensitive-biz-data-to-chatgpt-raising-security-fears
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blockl
CyberheistNews Vol 13 #11 | March 14th, 2023
[Heads Up] Employees Are Feeding Sensitive Biz Data to ChatGPT, Raising Security Fears
Robert Lemos at DARKReading just reported on a worrying trend. The title said it all, and the news is that more than 4% of employees have put sensitive corporate data into the large language model, raising concerns that its popularity may result in massive leaks of proprietary information. Yikes.
I'm giving you a short extract of the story and the link to the whole article is below.
"Employees are submitting sensitive business data and privacy-protected information to large language models (LLMs) such as ChatGPT, raising concerns that artificial intelligence (AI) services could be incorporating the data into their models, and that information could be retrieved at a later date if proper data security isn't in place for the service.
"In a recent report, data security service Cyberhaven detected and blocked requests to input data into ChatGPT from 4.2% of the 1.6 million workers at its client companies because of the risk of leaking confidential info, client data, source code, or regulated information to the LLM.
"In one case, an executive cut and pasted the firm's 2023 strategy document into ChatGPT and asked it to create a PowerPoint deck. In another case, a doctor input his patient's name and their medical condition and asked ChatGPT to craft a letter to the patient's insurance company.
"And as more employees use ChatGPT and other AI-based services as productivity tools, the risk will grow, says Howard Ting, CEO of Cyberhaven.
"'There was this big migration of data from on-prem to cloud, and the next big shift is going to be the migration of data into these generative apps," he says. "And how that plays out [remains to be seen] - I think, we're in pregame; we're not even in the first inning.'"
Your employees need to be stepped through new-school security awareness training so that they understand the risks of doing things like this.
Blog post with links:https://blog.knowbe4.com/employees-are-feeding-sensitive-biz-data-to-chatgpt-raising-security-fears
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blockl |
Ransomware Data Breach Spam Malware Threat Guideline Medical | ChatGPT ChatGPT | ★★ | |
| 2023-02-23 16:28:04 | Ransomware Attacks Using Extortion Tactics Reaches Critical Mass at 96% of all Attacks (lien direct) |

|
Ransomware | ★★★ | ||
| 2023-02-14 14:00:00 | CyberheistNews Vol 13 #07 [Scam of the Week] The Turkey-Syria Earthquake (lien direct) |
 CyberheistNews Vol 13 #07 | February 14th, 2023
[Scam of the Week] The Turkey-Syria Earthquake
Just when you think they cannot sink any lower, criminal internet scum is now exploiting the recent earthquake in Turkey and Syria.
Less than 24 hours after two massive earthquakes claimed the lives of tens of thousands of people, cybercrooks are already piggybacking on the horrible humanitarian crisis. You need to alert your employees, friends and family... again.
Just one example are scammers that pose as representatives from a Ukrainian charity foundation that seeks money to help those affected by the natural disasters that struck in the early hours of Monday.
There are going to be a raft of scams varying from blood drives to pleas for charitable contributions for victims and their families. Unfortunately, this type of scam is the worst kind of phishbait, and it is a very good idea to inoculate people before they get suckered into falling for a scam like this.
I suggest you send the following short alert to as many people as you can. As usual, feel free to edit:
[ALERT] "Lowlife internet scum is trying to benefit from the Turkey-Syria earthquake. The first phishing campaigns have already been sent and more will be coming that try to trick you into clicking on a variety of links about blood drives, charitable donations, or "exclusive" videos.
"Don't let them shock you into clicking on anything, or open possibly dangerous attachments you did not ask for! Anything you receive about this recent earthquake, be very suspicious. With this topic, think three times before you click. It is very possible that it is a scam, even though it might look legit or was forwarded to you by a friend -- be especially careful when it seems to come from someone you know through email, a text or social media postings because their account may be hacked.
"In case you want to donate to charity, go to your usual charity by typing their name in the address bar of your browser and do not click on a link in any email. Remember, these precautions are just as important at the house as in the office, so tell your friends and family."
It is unfortunate that we continue to have to warn against the bad actors on the internet that use these tragedies for their own benefit. For KnowBe4 customers, we have a few templates with this topic in the Current Events. It's a good idea to send one to your users this week.
Blog post with links:https://blog.knowbe4.com/scam-of-the-week-the-turkey-syria-earthquake
CyberheistNews Vol 13 #07 | February 14th, 2023
[Scam of the Week] The Turkey-Syria Earthquake
Just when you think they cannot sink any lower, criminal internet scum is now exploiting the recent earthquake in Turkey and Syria.
Less than 24 hours after two massive earthquakes claimed the lives of tens of thousands of people, cybercrooks are already piggybacking on the horrible humanitarian crisis. You need to alert your employees, friends and family... again.
Just one example are scammers that pose as representatives from a Ukrainian charity foundation that seeks money to help those affected by the natural disasters that struck in the early hours of Monday.
There are going to be a raft of scams varying from blood drives to pleas for charitable contributions for victims and their families. Unfortunately, this type of scam is the worst kind of phishbait, and it is a very good idea to inoculate people before they get suckered into falling for a scam like this.
I suggest you send the following short alert to as many people as you can. As usual, feel free to edit:
[ALERT] "Lowlife internet scum is trying to benefit from the Turkey-Syria earthquake. The first phishing campaigns have already been sent and more will be coming that try to trick you into clicking on a variety of links about blood drives, charitable donations, or "exclusive" videos.
"Don't let them shock you into clicking on anything, or open possibly dangerous attachments you did not ask for! Anything you receive about this recent earthquake, be very suspicious. With this topic, think three times before you click. It is very possible that it is a scam, even though it might look legit or was forwarded to you by a friend -- be especially careful when it seems to come from someone you know through email, a text or social media postings because their account may be hacked.
"In case you want to donate to charity, go to your usual charity by typing their name in the address bar of your browser and do not click on a link in any email. Remember, these precautions are just as important at the house as in the office, so tell your friends and family."
It is unfortunate that we continue to have to warn against the bad actors on the internet that use these tragedies for their own benefit. For KnowBe4 customers, we have a few templates with this topic in the Current Events. It's a good idea to send one to your users this week.
Blog post with links:https://blog.knowbe4.com/scam-of-the-week-the-turkey-syria-earthquake
|
Ransomware Spam Threat Guideline | ChatGPT | ★★ | |
| 2023-01-31 20:04:22 | Ransomware Targets are Getting Larger and Paying More as Fewer Victims Are Paying the Ransom (lien direct) |

|
Ransomware | ★★★ | ||
| 2023-01-20 12:03:01 | [Eye Popper] Ransomware Victims Refused To Pay Last Year (lien direct) |
![[Eye Popper] Ransomware Victims Refused To Pay Last Year](https://blog.knowbe4.com/hubfs/Ransomware-payments-graphic-courtesy-chainalysis-1.png)
|
Ransomware | ★ | ||
| 2023-01-06 13:51:44 | Ransomware and Fraudulent Funds Transfer are the Two Main Drivers of Cyber Loss (lien direct) |

|
Ransomware | ★★ | ||
| 2023-01-05 13:32:40 | These grim figures show that the ransomware problem isn\'t going away (lien direct) |

|
Ransomware | ★★ | ||
| 2022-12-28 12:15:35 | [Eye Opener] Insurance policy doesn\'t cover ransomware attack, Ohio Supreme Court says (lien direct) |
![[Eye Opener] Insurance policy doesn't cover ransomware attack, Ohio Supreme Court says](https://blog.knowbe4.com/hubfs/Ransomware-Attack-Warning-2022.jpg)
|
Ransomware | ★★★ | ||
| 2022-12-16 13:15:38 | Hospitals Warned of Royal Ransomware Attacks by U.S. Department of Health (lien direct) |

|
Ransomware | ★★ | ||
| 2022-12-06 14:30:00 | CyberheistNews Vol 12 #49 [Keep An Eye Out] Beware of New Holiday Gift Card Scams (lien direct) |
 CyberheistNews Vol 12 #49 | December 6th, 2022
[Keep An Eye Out] Beware of New Holiday Gift Card Scams
By Roger A. Grimes
Every holiday season brings on an increase in gift card scams. Most people love to buy and use gift cards. They are convenient, easy to buy, easy to use, easy to gift, usually allow the receiver to pick just what they want, and are often received as a reward for doing something.
The gift card market is estimated in the many hundreds of BILLIONS of dollars. Who doesn't like to get a free gift card? Unfortunately, scammers often use gift cards as a way to steal value from their victims. There are dozens of ways gift cards can be used by scammers to steal money.
Roger covers these three scams in a short [VIDEO] and in detail on the KnowBe4 blog:
You Need to Pay a Bill Using Gift Cards
Maliciously Modified Gift Cards in Stores
Phish You for Information to Supposedly Get a Gift Card
Blog post with 2:13 [VIDEO] and links you can share with your users and family:https://blog.knowbe4.com/beware-of-holiday-gift-card-scams
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human firewall as your last line of defense.
Join us TOMORROW, Wednesday, December 7 @ 2:00 PM (ET), for a live demo of how KnowBe4 introduces a new-school approach to security awareness training and simulated phishing.
Get a look at THREE NEW FEATURES and see how easy it is to train and phish your users.
NEW! KnowBe4 Mobile Learner App - Users Can Now Train Anytime, Anywhere!
NEW! Security Culture Benchmarking feature lets you compare your organization's security culture with your peers
NEW! AI-Driven phishing and training recommendations for your end users
Did You Know? You can upload your own training video and SCORM modules into your account for home workers
Active Directory or SCIM Integration to easily upload user data, eliminating the need to manually manage user changes
Find out how 50,000+ organizations have mobilized their end-users as their human firewall.
Date/Time: TOMORROW, Wednesday, December 7 @ 2:00 PM (ET)
Save My Spot!https://event.on24.com/wcc/r/3947028/0273119CCBF116DBE42DF81F151FF99F?partnerref=CHN3
CyberheistNews Vol 12 #49 | December 6th, 2022
[Keep An Eye Out] Beware of New Holiday Gift Card Scams
By Roger A. Grimes
Every holiday season brings on an increase in gift card scams. Most people love to buy and use gift cards. They are convenient, easy to buy, easy to use, easy to gift, usually allow the receiver to pick just what they want, and are often received as a reward for doing something.
The gift card market is estimated in the many hundreds of BILLIONS of dollars. Who doesn't like to get a free gift card? Unfortunately, scammers often use gift cards as a way to steal value from their victims. There are dozens of ways gift cards can be used by scammers to steal money.
Roger covers these three scams in a short [VIDEO] and in detail on the KnowBe4 blog:
You Need to Pay a Bill Using Gift Cards
Maliciously Modified Gift Cards in Stores
Phish You for Information to Supposedly Get a Gift Card
Blog post with 2:13 [VIDEO] and links you can share with your users and family:https://blog.knowbe4.com/beware-of-holiday-gift-card-scams
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human firewall as your last line of defense.
Join us TOMORROW, Wednesday, December 7 @ 2:00 PM (ET), for a live demo of how KnowBe4 introduces a new-school approach to security awareness training and simulated phishing.
Get a look at THREE NEW FEATURES and see how easy it is to train and phish your users.
NEW! KnowBe4 Mobile Learner App - Users Can Now Train Anytime, Anywhere!
NEW! Security Culture Benchmarking feature lets you compare your organization's security culture with your peers
NEW! AI-Driven phishing and training recommendations for your end users
Did You Know? You can upload your own training video and SCORM modules into your account for home workers
Active Directory or SCIM Integration to easily upload user data, eliminating the need to manually manage user changes
Find out how 50,000+ organizations have mobilized their end-users as their human firewall.
Date/Time: TOMORROW, Wednesday, December 7 @ 2:00 PM (ET)
Save My Spot!https://event.on24.com/wcc/r/3947028/0273119CCBF116DBE42DF81F151FF99F?partnerref=CHN3
|
Ransomware Data Breach Spam Hack Tool Guideline | ★★★ | ||
| 2022-12-02 17:36:35 | Ransomware Attacks on Holidays and Weekends Increase and Take a Greater Toll on Organizations (lien direct) |

|
Ransomware | ★★ | ||
| 2022-11-21 18:33:41 | 10 Million Health Records from Australian Insurer Medibank are Leaked After Refusing to Pay the Ransom (lien direct) |
|
Ransomware | ★★★ | ||
| 2022-11-09 11:54:55 | [EYES OUT] This Scary Strain of Sleeper Ransomware Is Really a Data Wiper in Disguise (lien direct) |
![[EYES OUT] This Scary Strain of Sleeper Ransomware Is Really a Data Wiper in Disguise](https://blog.knowbe4.com/hubfs/Ransomware-Attack-Warning-2022.jpg)
|
Ransomware | |||
| 2022-10-12 16:00:00 | Encrypted Files are the Overwhelming Way Organizations “Detect” Ransomware Attacks (lien direct) |

|
Ransomware | |||
| 2022-10-04 13:14:56 | One-Fourth of Organizations Have Been Victim to a Ransomware Attack with 59% Starting with Email (lien direct) |
 New analysis highlights just how prevalent ransomware attacks are today, how material the impacts are, whether organizations get their data back, and exactly how these attacks start.
New analysis highlights just how prevalent ransomware attacks are today, how material the impacts are, whether organizations get their data back, and exactly how these attacks start. |
Ransomware | |||
| 2022-08-16 13:34:25 | (Déjà vu) CyberheistNews Vol 12 #33 [Eye Opener] Recent Cisco Hack by Ransomware Group Started Because of a Phishing Attack (lien direct) |

|
Ransomware Hack | |||
| 2022-08-11 13:28:56 | SolidBit Ransomware Targets League of Legends Players (lien direct) |

|
Ransomware | |||
| 2022-08-11 12:59:06 | Recent Cisco Hack by Ransomware Group Started Because of a Phishing Attack (lien direct) |

|
Ransomware Hack | |||
| 2022-08-02 13:07:39 | Cyber Insurance Expected to Continue to Rise as Sophistication and Cost of Ransomware Attacks Increase (lien direct) |

|
Ransomware | |||
| 2022-07-27 12:49:48 | New Report Reveals that Ransomware and Business Email Compromise Attacks Cause Nearly 70% of Cyber Incidents (lien direct) |
 Do you know your organizations true security risk and where to prioritize your resources? A new report from Palo Alto Networks sheds some light on these questions and shows multiple insights on incident response work from security teams.
Do you know your organizations true security risk and where to prioritize your resources? A new report from Palo Alto Networks sheds some light on these questions and shows multiple insights on incident response work from security teams. |
Ransomware | |||
| 2022-07-25 13:12:21 | Ransomware Groups Get Smaller and More Social (lien direct) |
 The Colonial Pipeline ransomware attack of 2021 put infrastructure operators on notice that they were directly in the crosshairs of big ransomware gangs. The reaction of law enforcement seems, however, to have also put the gangs on notice that their ability to operate with impunity isn't what it used to be. The big criminal operations seem to be breaking up. That's not because they've gone straight. It's because they've realized that they're more vulnerable than they used to be.
The Colonial Pipeline ransomware attack of 2021 put infrastructure operators on notice that they were directly in the crosshairs of big ransomware gangs. The reaction of law enforcement seems, however, to have also put the gangs on notice that their ability to operate with impunity isn't what it used to be. The big criminal operations seem to be breaking up. That's not because they've gone straight. It's because they've realized that they're more vulnerable than they used to be. |
Ransomware | |||
| 2022-07-19 12:16:00 | Copyright Claim Email is a LockBit Ransomware Phishing Attack in Disguise (lien direct) |

|
Ransomware | |||
| 2022-07-06 13:06:58 | (Déjà vu) CyberheistNews Vol 12 #27 [New FBI and CISA Alert] This Ransomware Strain Uses RDP Flaws to Hack Into Your Network (lien direct) |

|
Ransomware Hack | |||
| 2022-07-06 12:03:07 | Phishing Emails Top the List as the Initial Attack Vector for Ransomware Attacks (lien direct) |
|
Ransomware | |||
| 2022-07-01 10:47:10 | [New FBI and CISA Alert] This ransomware strain uses RDP flaws to hack into your network (lien direct) |
![[New FBI and CISA Alert] This ransomware strain uses RDP flaws to hack into your network](https://blog.knowbe4.com/hubfs/CSA-MEDUSA.jpg)
|
Ransomware Hack | |||
| 2022-06-20 14:10:51 | Less Than 40% of Asia-Pacific Organizations Are Confident to Stop Cyber Threats as 83% Experience At Least One Ransomware Attack a Year (lien direct) |
|
Ransomware Threat | |||
| 2022-06-09 16:02:12 | Approaching Ransomware Victims Privately (lien direct) |
 Researchers at KELA warn that ransomware gangs are increasingly refraining from mentioning their victims' names after the initial attack, giving the victims a chance to pay up before the attack is publicized. This puts an additional layer of pressure on the victim to pay quickly, because it may allow them to avoid the reputational damage that's among the biggest threats a victim faces. If the victim refuses to pay, the attackers can then publish their name and threaten to release the stolen data.
Researchers at KELA warn that ransomware gangs are increasingly refraining from mentioning their victims' names after the initial attack, giving the victims a chance to pay up before the attack is publicized. This puts an additional layer of pressure on the victim to pay quickly, because it may allow them to avoid the reputational damage that's among the biggest threats a victim faces. If the victim refuses to pay, the attackers can then publish their name and threaten to release the stolen data. |
Ransomware Threat | |||
| 2022-06-07 13:11:51 | CyberheistNews Vol 12 #23 [Heads Up] Our Global Ransomware Damage Will Be More Than 265 Billion by 2031 (lien direct) |
![CyberheistNews Vol 12 #23 [Heads Up] Our Global Ransomware Damage Will Be More Than 265 Billion by 2031](https://blog.knowbe4.com/hubfs/CHN-Social.jpg)
|
Ransomware | |||
| 2022-06-01 22:08:53 | The Business (and Success) of Ransomware Explained as a Simple Funnel (lien direct) |

|
Ransomware | |||
| 2022-06-01 12:59:33 | CyberheistNews Vol 12 #22 [Heads Up] The New Verizon 2022 Data Breach Investigation Report Shows Sharp Rise in Ransomware (lien direct) |

|
Ransomware Data Breach | |||
| 2022-05-25 16:30:10 | Verizon: Ransomware Involved in 25% of Data Breaches as Credentials and Phishing are Seen as “Key Paths” for Attack Success (lien direct) |
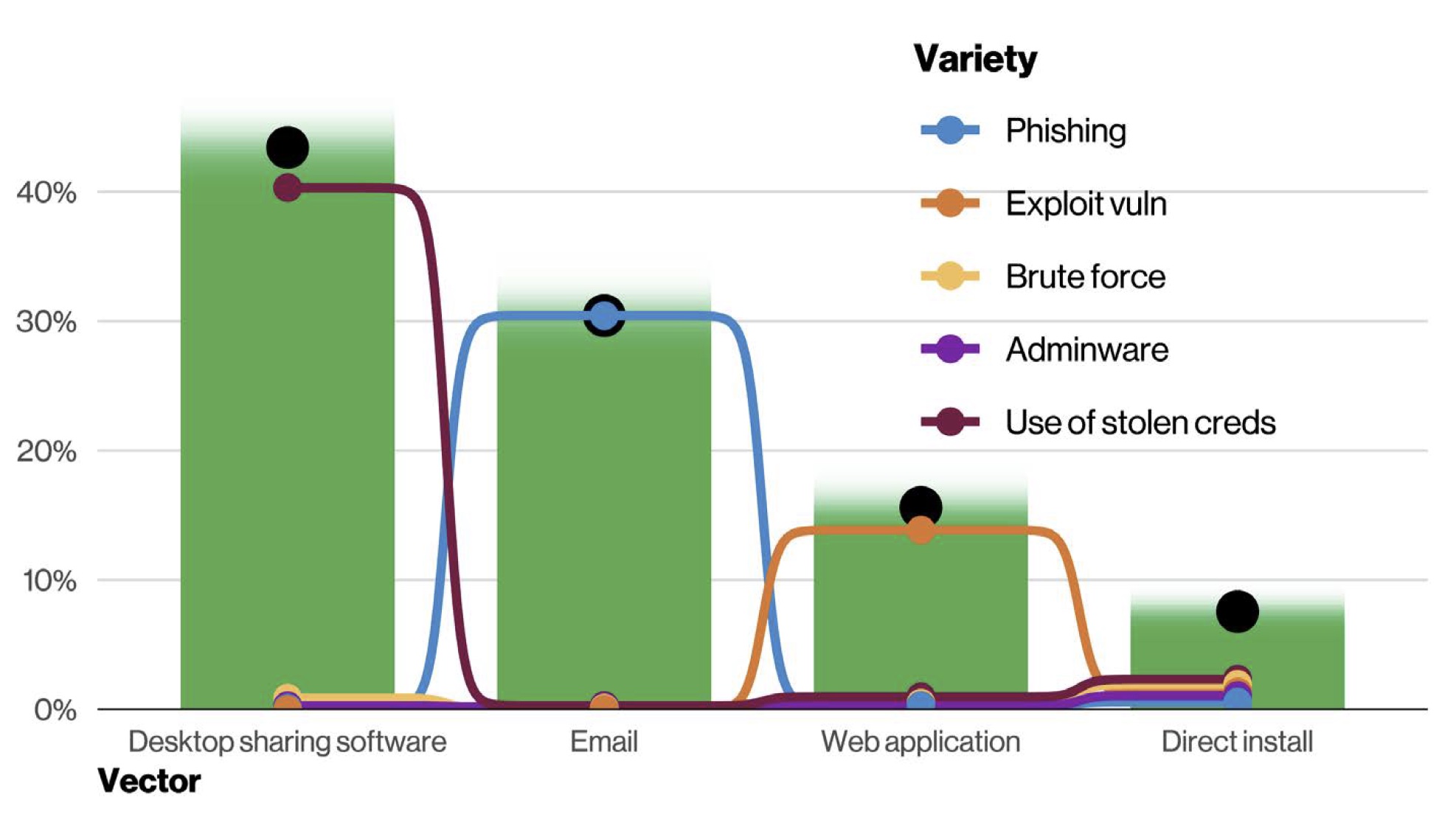
|
Ransomware | |||
| 2022-05-13 12:04:41 | Homeland Security: U.S. Ransomware Attacks Have Doubled in the Last Year (lien direct) |
 A March 2022 report from the Senate Committee on Homeland Security and Governmental Affairs zeros in on the growing problem of ransomware and lessons learned so far.
A March 2022 report from the Senate Committee on Homeland Security and Governmental Affairs zeros in on the growing problem of ransomware and lessons learned so far. |
Ransomware | |||
| 2022-05-04 13:28:52 | FIN12 Threat Group Speeds Up Ransomware Attacks to Just Two Days After Initial Access (lien direct) |
 As detection times are reducing across the board, threat groups are improving their craft and are prioritizing speed as the key ingredient in ransomware attacks.
As detection times are reducing across the board, threat groups are improving their craft and are prioritizing speed as the key ingredient in ransomware attacks. |
Ransomware Threat | |||
| 2022-04-28 22:05:02 | 75% of SMBs Would Only Survive Seven Days or less from a Ransomware Attack (lien direct) |
 With ransomware attacks on the increase, new data shows a material portion of small and medium business organizations are completely ill-equipped to address an attack.
With ransomware attacks on the increase, new data shows a material portion of small and medium business organizations are completely ill-equipped to address an attack. |
Ransomware | |||
| 2022-04-28 19:25:08 | [EYE OPENER] The Ransom Payment is Only 15% of The Total Cost of Ransomware Attacks (lien direct) |
![[EYE OPENER] The Ransom Payment is Only 15% of The Total Cost of Ransomware Attacks](https://blog.knowbe4.com/hubfs/Cyber%20Attacks%20Up%20125%25%20Ransomware%20Tops%20List.jpg) As the number of ransomware attacks has increased 24% over the previous year, security researchers estimate the total associated attack costs to be just over 7 times higher.
As the number of ransomware attacks has increased 24% over the previous year, security researchers estimate the total associated attack costs to be just over 7 times higher. |
Ransomware | |||
| 2022-04-13 20:44:27 | Small and Medium Businesses Account for Nearly Half of all Ransomware Victim Organizations (lien direct) |
 As ransomware costs increase, along with the effectiveness and use of extortions, smaller businesses are paying the price, according to new data from Webroot.
As ransomware costs increase, along with the effectiveness and use of extortions, smaller businesses are paying the price, according to new data from Webroot. |
Ransomware | |||
| 2022-04-08 12:30:51 | The Ransomware Hostage Rescue Checklist: Your Step-by-Step Guide to Preventing and Surviving an Ransomware Attack (lien direct) |
 Skyrocketing attack rates, double and triple extortion, increasing ransom demands… cybercriminals are inflicting pain in every way imaginable when it comes to today's ransomware attacks. And you need to be prepared to protect your network, NOW.
Skyrocketing attack rates, double and triple extortion, increasing ransom demands… cybercriminals are inflicting pain in every way imaginable when it comes to today's ransomware attacks. And you need to be prepared to protect your network, NOW. |
Ransomware | |||
| 2022-03-29 13:59:07 | (Déjà vu) CyberheistNews Vol 12 #13 [Heads Up] Published Zelenskyy Deepfake Video Demonstrates the Modern War is Online (lien direct) |
![CyberheistNews Vol 12 #13 [Heads Up] Published Zelenskyy Deepfake Video Demonstrates the Modern War is Online](https://blog.knowbe4.com/hubfs/CHN-Social.jpg) [Heads Up] Published Zelenskyy Deepfake Video Demonstrates the Modern War is Online
Email not displaying? |
CyberheistNews Vol 12 #13 | Mar. 29th., 2022
[Heads Up] Published Zelenskyy Deepfake Video Demonstrates the Modern War is Online
The video uploaded to a hacked Ukrainian news website shows how far the technology has come, how it can be used in social engineering, and how the tech still needs to improve.
While much of the headlines today around the Russian invasion of Ukraine focus on the war on the ground and in the air, a cyberwar is being waged behind the scenes. It began with wiper ransomware attacks on Ukrainian businesses and government agencies and has culminated so far with a newly released deepfake video of Ukrainian president Zelenskyy asking his troops to lay down their weapons and surrender.
[Heads Up] Published Zelenskyy Deepfake Video Demonstrates the Modern War is Online
Email not displaying? |
CyberheistNews Vol 12 #13 | Mar. 29th., 2022
[Heads Up] Published Zelenskyy Deepfake Video Demonstrates the Modern War is Online
The video uploaded to a hacked Ukrainian news website shows how far the technology has come, how it can be used in social engineering, and how the tech still needs to improve.
While much of the headlines today around the Russian invasion of Ukraine focus on the war on the ground and in the air, a cyberwar is being waged behind the scenes. It began with wiper ransomware attacks on Ukrainian businesses and government agencies and has culminated so far with a newly released deepfake video of Ukrainian president Zelenskyy asking his troops to lay down their weapons and surrender.
|
Ransomware | |||
| 2022-03-24 14:20:53 | Initial Access Broker Group Relies on Social Engineering (lien direct) |
 Google's Threat Analysis Group (TAG) describes a cybercriminal group it calls “EXOTIC LILY” that acts as an initial access broker for numerous financially motivated threat actors, including FIN12 and the Conti ransomware gang. EXOTIC LILY uses phishing attacks to gain access to organizations' networks, then sells this access to other gangs for further exploitation.
Google's Threat Analysis Group (TAG) describes a cybercriminal group it calls “EXOTIC LILY” that acts as an initial access broker for numerous financially motivated threat actors, including FIN12 and the Conti ransomware gang. EXOTIC LILY uses phishing attacks to gain access to organizations' networks, then sells this access to other gangs for further exploitation. |
Ransomware Threat | |||
| 2022-03-17 12:43:59 | [Heads Up] New Evil Ransomware Feature: Disk Wiper if You Don\'t Pay (lien direct) |
 There is a new ransomware-as-a-service (RaaS) strain called LokiLocker, researchers at Blackberry warn. The malware uses rare code obfuscation and includes a file wiper component that attackers can deploy if their victims don't pay. "It shouldn't be confused with an older ransomware family called Locky, which was notorious in 2016, or LokiBot, which is an infostealer.
There is a new ransomware-as-a-service (RaaS) strain called LokiLocker, researchers at Blackberry warn. The malware uses rare code obfuscation and includes a file wiper component that attackers can deploy if their victims don't pay. "It shouldn't be confused with an older ransomware family called Locky, which was notorious in 2016, or LokiBot, which is an infostealer. |
Ransomware Malware | |||
| 2022-03-16 14:25:21 | Backups Become the Focus as Three-Fourths of Organizations Experienced Ransomware Attacks (lien direct) |
 New data puts the spotlight on how most organizations unable to completely recover their data after a ransomware attack, making the case for better data protection for improved incident response.
New data puts the spotlight on how most organizations unable to completely recover their data after a ransomware attack, making the case for better data protection for improved incident response. |
Ransomware | |||
| 2022-03-15 13:41:15 | (Déjà vu) CyberheistNews Vol 12 #11 [Heads Up] FBI: Ransomware Gang Breached 52 U.S. Critical Infrastructure Orgs (lien direct) |
![CyberheistNews Vol 12 #11 [Heads Up] FBI: Ransomware Gang Breached 52 U.S. Critical Infrastructure Orgs](https://blog.knowbe4.com/hubfs/CHN-Social.jpg) [Heads Up] FBI: Ransomware Gang Breached 52 US Critical Infrastructure Orgs
Email not displaying? |
CyberheistNews Vol 12 #11 | Mar. 15th., 2022
[Heads Up] FBI: Ransomware Gang Breached 52 U.S. Critical Infrastructure Orgs
The U.S. Federal Bureau of Investigation (FBI) says the Ragnar Locker ransomware gang has breached the networks of at least 52 organizations from multiple U.S. critical infrastructure sectors.
[Heads Up] FBI: Ransomware Gang Breached 52 US Critical Infrastructure Orgs
Email not displaying? |
CyberheistNews Vol 12 #11 | Mar. 15th., 2022
[Heads Up] FBI: Ransomware Gang Breached 52 U.S. Critical Infrastructure Orgs
The U.S. Federal Bureau of Investigation (FBI) says the Ragnar Locker ransomware gang has breached the networks of at least 52 organizations from multiple U.S. critical infrastructure sectors.
|
Ransomware | |||
| 2022-03-15 12:43:58 | Cybercrime-as-a-Service: Its Evolution and What You Can Do to Fight Back (lien direct) |
 The cybercrime market has skyrocketed in a frightening way. With threats such as ransomware to Business Email Compromise (BEC), the stakes are higher than ever for organizations across all industries.
The cybercrime market has skyrocketed in a frightening way. With threats such as ransomware to Business Email Compromise (BEC), the stakes are higher than ever for organizations across all industries. |
Ransomware |
To see everything:
Our RSS (filtrered)
