What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-06-06 19:15:12 | CVE-2023-33957 (lien direct) | La notation est un outil CLI pour signer et vérifier les artefacts OCI et les images de conteneurs.Un attaquant qui a compromis un registre et ajouté un nombre élevé de signatures à un artefact peut provoquer un déni de service sur la machine, si un utilisateur exécute la commande Inspecter Notation sur la même machine.Le problème a été résolu dans la version V1.0.0-RC.6.Les utilisateurs doivent mettre à niveau leurs packages de notation vers V1.0.0-RC.6 ou plus.Il est conseillé aux utilisateurs de mettre à niveau.Les utilisateurs incapables de mettre à niveau peuvent restreindre les registres des conteneurs à un ensemble de registres de conteneurs sécurisés et fiables.
notation is a CLI tool to sign and verify OCI artifacts and container images. An attacker who has compromised a registry and added a high number of signatures to an artifact can cause denial of service of services on the machine, if a user runs notation inspect command on the same machine. The problem has been fixed in the release v1.0.0-rc.6. Users should upgrade their notation packages to v1.0.0-rc.6 or above. Users are advised to upgrade. Users unable to upgrade may restrict container registries to a set of secure and trusted container registries. |
Tool | |||
| 2023-06-06 19:11:00 | Anomali Cyber Watch: LemurLoot sur les transferts Moveit exploités, exploite iOS zéro-clic ciblée Kaspersky, Qakbot transforme les bots en proxys Anomali Cyber Watch: LEMURLOOT on Exploited MOVEit Transfers, Zero-Click iOS Exploit Targeted Kaspersky, Qakbot Turns Bots into Proxies (lien direct) |
Les diverses histoires de l'intelligence de la menace dans cette itération de la cyber montre anomali discutent des sujets suivants: Adware, botnets, fuite de données, obscurcissement, phishing, vulnérabilités zéro-jour, et Exploits zéro cliquez en clic .Les CIO liés à ces histoires sont attachés à Anomali Cyber Watch et peuvent être utilisés pour vérifier vos journaux pour une activité malveillante potentielle. Figure 1 - Diagrammes de résumé du CIO.Ces graphiques résument les CIO attachés à ce magazine et donnent un aperçu des menaces discutées.
Cyber News et Intelligence des menaces
vulnérabilité de la journée zéro dansTransfert Moveit exploité pour le vol de données
(Publié: 2 juin 2023)
Une vulnérabilité du zéro-day dans le logiciel de transfert de fichiers géré de transfert Moveit (CVE-2023-34362) a été annoncée par Progress Software Corporation le 31 mai 2023. Les chercheurs mandiants ont observé une large exploitation qui avait déjà commencé le 27 mai le 27 mai, 2023. Cette campagne opportuniste a affecté le Canada, l'Allemagne, l'Inde, l'Italie, le Pakistan, les États-Unis et d'autres pays.Les attaquants ont utilisé le shell Web LemurLoot personnalisé se faisant passer pour un composant légitime du transfert Moveit.Il est utilisé pour exfiltrater les données précédemment téléchargées par les utilisateurs de systèmes de transfert Moveit individuels.Cette activité d'acteur est surnommée UNC4857 et elle a une faible similitude de confiance avec l'extorsion de vol de données attribuée à FIN11 via le site de fuite de données de ransomware CL0P.
Commentaire des analystes: L'agence américaine de sécurité de cybersécurité et d'infrastructure a ajouté le CVE-2023-34362 du CVE-2023-34362 à sa liste de vulnérabilités exploitées connues, ordonnant aux agences fédérales américaines de corriger leurs systèmes d'ici le 23 juin 2023.Progress Software Corporation STAPES RESTATIONS, notamment le durcissement, la détection, le nettoyage et l'installation des récentes correctifs de sécurité de transfert Moveit.Les règles YARA et les indicateurs basés sur l'hôte associés à la coque en ligne Lemurloot sont disponibles dans la plate-forme Anomali pour la détection et la référence historique.
mitre att & amp; ck: [mitre att & amp; ck] t1587.003 - développer des capacités:Certificats numériques | [mitre att & amp; ck] t1190 - exploiter la demande publique | [mitre att & amp; ck] t1036 - masquée | [mitre att & amp; ck] t1136 - créer un compte | [mitre att & amp; ck] t1083 - Discovery de dossier et d'annuaire | [mitre att & amp; ck] t1560.001 -Données collectées des archives: Archive via l'utilitaire
Signatures: LEMURLOOT WEBSHELL DLL TARDS - YARA BY BYMandiant | scénarisation de la webshell lemurloot ASP.net - yara par mandiant | Moveit Exploitation - Yara par Florian Roth .
Tags: Malware: LemurLoot,
Figure 1 - Diagrammes de résumé du CIO.Ces graphiques résument les CIO attachés à ce magazine et donnent un aperçu des menaces discutées.
Cyber News et Intelligence des menaces
vulnérabilité de la journée zéro dansTransfert Moveit exploité pour le vol de données
(Publié: 2 juin 2023)
Une vulnérabilité du zéro-day dans le logiciel de transfert de fichiers géré de transfert Moveit (CVE-2023-34362) a été annoncée par Progress Software Corporation le 31 mai 2023. Les chercheurs mandiants ont observé une large exploitation qui avait déjà commencé le 27 mai le 27 mai, 2023. Cette campagne opportuniste a affecté le Canada, l'Allemagne, l'Inde, l'Italie, le Pakistan, les États-Unis et d'autres pays.Les attaquants ont utilisé le shell Web LemurLoot personnalisé se faisant passer pour un composant légitime du transfert Moveit.Il est utilisé pour exfiltrater les données précédemment téléchargées par les utilisateurs de systèmes de transfert Moveit individuels.Cette activité d'acteur est surnommée UNC4857 et elle a une faible similitude de confiance avec l'extorsion de vol de données attribuée à FIN11 via le site de fuite de données de ransomware CL0P.
Commentaire des analystes: L'agence américaine de sécurité de cybersécurité et d'infrastructure a ajouté le CVE-2023-34362 du CVE-2023-34362 à sa liste de vulnérabilités exploitées connues, ordonnant aux agences fédérales américaines de corriger leurs systèmes d'ici le 23 juin 2023.Progress Software Corporation STAPES RESTATIONS, notamment le durcissement, la détection, le nettoyage et l'installation des récentes correctifs de sécurité de transfert Moveit.Les règles YARA et les indicateurs basés sur l'hôte associés à la coque en ligne Lemurloot sont disponibles dans la plate-forme Anomali pour la détection et la référence historique.
mitre att & amp; ck: [mitre att & amp; ck] t1587.003 - développer des capacités:Certificats numériques | [mitre att & amp; ck] t1190 - exploiter la demande publique | [mitre att & amp; ck] t1036 - masquée | [mitre att & amp; ck] t1136 - créer un compte | [mitre att & amp; ck] t1083 - Discovery de dossier et d'annuaire | [mitre att & amp; ck] t1560.001 -Données collectées des archives: Archive via l'utilitaire
Signatures: LEMURLOOT WEBSHELL DLL TARDS - YARA BY BYMandiant | scénarisation de la webshell lemurloot ASP.net - yara par mandiant | Moveit Exploitation - Yara par Florian Roth .
Tags: Malware: LemurLoot, |
Ransomware Malware Tool Vulnerability Threat | ★★ | ||
| 2023-06-06 17:05:00 | Trois vulnérabilités découvertes dans Game Dev Tool RenderDoc Three Vulnerabilities Discovered in Game Dev Tool RenderDoc (lien direct) |
Qualys a identifié une instance d'escalade de privilèges et deux débordements de tampons basés sur un tas
Qualys identified one instance of privilege escalation and two heap-based buffer overflows |
Tool | ★★ | ||
| 2023-06-06 16:55:00 | Université de Rochester, Nouvelle-Écosse, premières victimes de déménagement connues en Amérique du Nord University of Rochester, Nova Scotia first known MoveIT victims in North America (lien direct) |
 Le gouvernement de la Nouvelle-Écosse et l'Université de Rochester sont les premières organisations en Amérique du Nord à confirmer le vol de données à la suite de l'exploitation d'une nouvelle vulnérabilité affectant le déplacement de l'outil de transfert de fichiers populaire.Dimanche, le gouvernement de la Nouvelle-Écosse, une petite province de l'est du Canada, a averti que les informations personnelles
Le gouvernement de la Nouvelle-Écosse et l'Université de Rochester sont les premières organisations en Amérique du Nord à confirmer le vol de données à la suite de l'exploitation d'une nouvelle vulnérabilité affectant le déplacement de l'outil de transfert de fichiers populaire.Dimanche, le gouvernement de la Nouvelle-Écosse, une petite province de l'est du Canada, a averti que les informations personnelles
 The government of Nova Scotia and the University of Rochester are the first organizations in North America to confirm data theft as a result of the exploitation of a new vulnerability affecting popular file transfer tool MOVEit. On Sunday, the government of Nova Scotia, a small province in eastern Canada, warned that the personal information
The government of Nova Scotia and the University of Rochester are the first organizations in North America to confirm data theft as a result of the exploitation of a new vulnerability affecting popular file transfer tool MOVEit. On Sunday, the government of Nova Scotia, a small province in eastern Canada, warned that the personal information |
Tool Vulnerability | ★★ | ||
| 2023-06-06 13:00:00 | Cyberheistnews Vol 13 # 23 [réveil] Il est temps de se concentrer davantage sur la prévention du phishing de lance CyberheistNews Vol 13 #23 [Wake-Up Call] It\\'s Time to Focus More on Preventing Spear Phishing (lien direct) |
 CyberheistNews Vol 13 #23 | June 6th, 2023
[Wake-Up Call] It\'s Time to Focus More on Preventing Spear Phishing
Fighting spear phishing attacks is the single best thing you can do to prevent breaches. Social engineering is involved in 70% to 90% of successful compromises. It is the number one way that all hackers and malware compromise devices and networks. No other initial root cause comes close (unpatched software and firmware is a distant second being involved in about 33% of attacks).
A new, HUGE, very important, fact has been gleaned by Barracuda Networks which should impact the way that EVERYONE does security awareness training. Everyone needs to know about this fact and react accordingly.
This is that fact: "...spear phishing attacks that use personalized messages... make up only 0.1% of all email-based attacks according to Barracuda\'s data but are responsible for 66% of all breaches."
Let that sink in for a moment.
What exactly is spear phishing? Spear phishing is when a social engineering attacker uses personal or confidential information they have learned about a potential victim or organization in order to more readily fool the victim into performing a harmful action. Within that definition, spear phishing can be accomplished in thousands of different ways, ranging from basic attacks to more advanced, longer-range attacks.
[CONTINUED] at KnowBe4 blog:https://blog.knowbe4.com/wake-up-call-its-time-to-focus-more-on-preventing-spear-phishing
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human firewall as your last line of defense.
Join us TOMORROW, Wednesday, June 7, @ 2:00 PM (ET), for a live demonstration of how KnowBe4 introduces a new-school approach to security awareness training and simulated phishing.
Get a look at THREE NEW FEATURES and see how easy it is to train and phish your users.
NEW! Executive Reports - Can create, tailor and deliver advanced executive-level reports
NEW! KnowBe4
CyberheistNews Vol 13 #23 | June 6th, 2023
[Wake-Up Call] It\'s Time to Focus More on Preventing Spear Phishing
Fighting spear phishing attacks is the single best thing you can do to prevent breaches. Social engineering is involved in 70% to 90% of successful compromises. It is the number one way that all hackers and malware compromise devices and networks. No other initial root cause comes close (unpatched software and firmware is a distant second being involved in about 33% of attacks).
A new, HUGE, very important, fact has been gleaned by Barracuda Networks which should impact the way that EVERYONE does security awareness training. Everyone needs to know about this fact and react accordingly.
This is that fact: "...spear phishing attacks that use personalized messages... make up only 0.1% of all email-based attacks according to Barracuda\'s data but are responsible for 66% of all breaches."
Let that sink in for a moment.
What exactly is spear phishing? Spear phishing is when a social engineering attacker uses personal or confidential information they have learned about a potential victim or organization in order to more readily fool the victim into performing a harmful action. Within that definition, spear phishing can be accomplished in thousands of different ways, ranging from basic attacks to more advanced, longer-range attacks.
[CONTINUED] at KnowBe4 blog:https://blog.knowbe4.com/wake-up-call-its-time-to-focus-more-on-preventing-spear-phishing
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human firewall as your last line of defense.
Join us TOMORROW, Wednesday, June 7, @ 2:00 PM (ET), for a live demonstration of how KnowBe4 introduces a new-school approach to security awareness training and simulated phishing.
Get a look at THREE NEW FEATURES and see how easy it is to train and phish your users.
NEW! Executive Reports - Can create, tailor and deliver advanced executive-level reports
NEW! KnowBe4 |
Ransomware Malware Hack Tool Threat | ★★ | ||
| 2023-06-06 09:10:00 | Kaspersky libère l'outil pour détecter les attaques iOS zéro cliquez sur zéro Kaspersky Releases Tool to Detect Zero-Click iOS Attacks (lien direct) |
Les retombées de l'opération Triangulation continue
Fallout from Operation Triangulation continues |
Tool | ★★★ | ||
| 2023-06-05 21:15:10 | CVE-2022-4569 (lien direct) | Une vulnérabilité locale d'escalade des privilèges dans l'outil HYBRID USB-C hybride ThinkPad avec USB-A Dock Firmware Update pourrait permettre à un attaquant avec un accès local pour exécuter du code avec des privilèges élevés pendant la mise à niveau ou l'installation du package.
A local privilege escalation vulnerability in the ThinkPad Hybrid USB-C with USB-A Dock Firmware Update Tool could allow an attacker with local access to execute code with elevated privileges during the package upgrade or installation. |
Tool Vulnerability | |||
| 2023-06-05 13:58:29 | Nouvel outil scanne iPhones pour \\ 'triangulation \\' Infection des logiciels malveillants New tool scans iPhones for \\'Triangulation\\' malware infection (lien direct) |
La société de cybersécurité Kaspersky a publié un outil pour détecter si les iPhones Apple et autres appareils iOS sont infectés par une nouvelle \\ 'triangulation \' malware.[...]
Cybersecurity firm Kaspersky has released a tool to detect if Apple iPhones and other iOS devices are infected with a new \'Triangulation\' malware. [...] |
Malware Tool | ★★ | ||
| 2023-06-05 10:00:00 | Trois façons dont l'agro-industrie peut protéger les actifs vitaux des cyberattaques Three ways agribusinesses can protect vital assets from cyberattacks (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. In an era where digital technology increasingly underpins food production and distribution, the urgency of cybersecurity in agriculture has heightened. A surge of cyberattacks in recent years, disrupting operations, causing economic losses, and threatening food industry security- all underscore this escalating concern. In April 2023, hackers targeted irrigation systems and wastewater treatment plants in Israel. The attack was part of an annual "hacktivist" campaign, and it temporarily disabled automated irrigation systems on about a dozen farms in the Jordan Valley. The attack also disrupted wastewater treatment processes at the Galil Sewage Corporation. In addition, in June 2022, six grain cooperatives in the US were hit by a ransomware attack during the fall harvest, disrupting their seed and fertilizer supplies. Adding to this growing list, a leading US agriculture firm also fell victim to a cyberattack the same year, which affected operations at several of its production facilities. These incidents highlight the pressing need for improved cybersecurity in the agricultural sector and underscore the challenges and risks this sector faces compared to others. As outlined in a study, “Various technologies are integrated into one product to perform specific agricultural tasks.” An example provided is that of an irrigation system which "has smart sensors/actuators, communication protocols, software, traditional networking devices, and human interaction." The study further elaborates that these complex systems are often outsourced from diverse vendors for many kinds of environments and applications. This complexity “increases the attack surface, and cyber-criminals can exploit vulnerabilities to compromise one or other parts of the agricultural application.” However, the situation is far from hopeless. By taking decisive action, we can significantly strengthen cybersecurity in the agricultural sector. Here are three strategies that pave the way toward a more secure future for the farming industry: 1. Strengthening password practices Weak or default passwords are an easily avoidable security risk that can expose vital assets in the agricultural sector to cyber threats. Arguably, even now, people have poor habits when it comes to password security. As per the findings of a survey conducted by GoodFirms: A significant percentage of people - 62.9%, to be exact - update their passwords only when prompted. 45.7% of people admitted to using the same password across multiple platforms or applications. More than half of the people had shared their passwords with others, such as colleagues, friends, or family members, raising the risk of unauthorized access. A surprising 35.7% of respondents reported keeping a physical record of their passwords on paper, sticky notes, or in planners. These lax password practices have had tangible negative impacts, with 30% of users experiencing security breaches attributable to weak passwords. Hackers can use various methods, such as brute force attacks or phishing attacks, to guess or obtain weak passwords and access sensitive inf | Ransomware Tool Vulnerability Patching | ★★ | ||
| 2023-06-02 20:09:55 | CrowdStrike améliore Falcon Discover pour réduire la surface d'attaque, rationaliser les opérations et réduire les coûts CrowdStrike Enhances Falcon Discover to Reduce the Attack Surface, Streamline Operations and Lower Costs (lien direct) |
Crowdsstrike Falcon & Reg;Discover offre une visibilité approfondie des actifs sans matériel à déployer ou à gérer, offrant un contexte précieux pour tous vos actifs.Pour les équipes et les équipes de sécurité, Falcon Discover est un outil puissant pour arrêter les violations.La majorité des clients Crowdsstrike utilisent déjà Falcon Discover pour améliorer leur posture informatique et de sécurité.Continuer [& # 8230;]
CrowdStrike Falcon® Discover delivers deep asset visibility with no hardware to deploy or manage, providing valuable context for all of your assets. For IT and security teams alike, Falcon Discover is a powerful tool to stop breaches. The majority of CrowdStrike customers already use Falcon Discover to improve their IT and security posture. To continue […] |
Tool | ★★ | ||
| 2023-06-02 18:23:00 | Le botnet brésilien cible les espagnols à travers les Amériques, dit Cisco Brazil-based botnet targets Spanish-speakers across Americas, Cisco says (lien direct) |
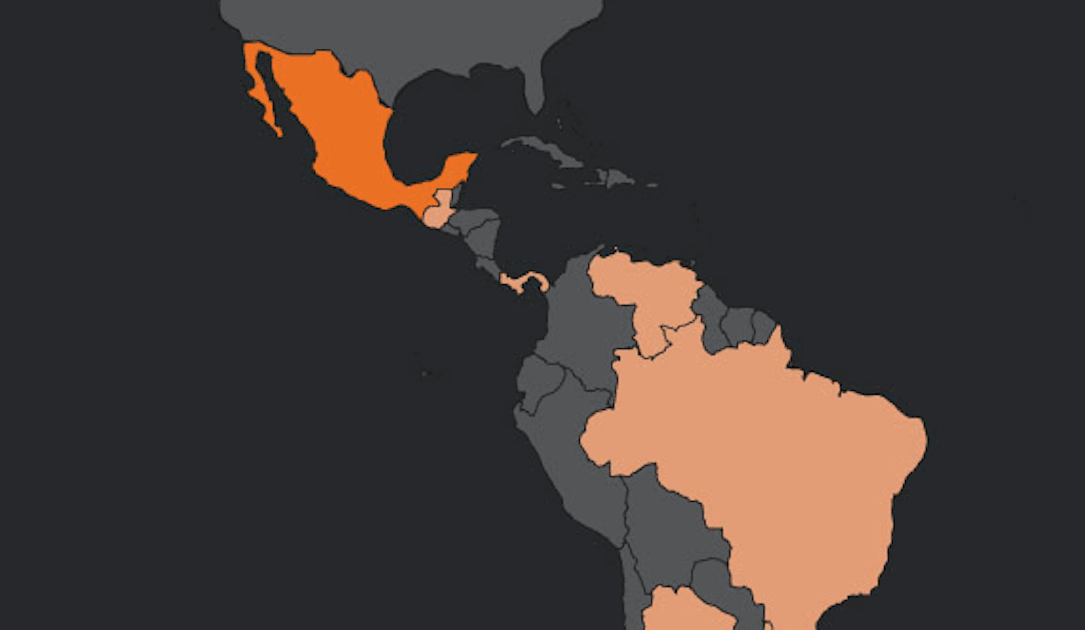 Les pirates soupçonnés de vivre au Brésil utilisent un botnet non identifié auparavant appelé à cibler les boîtes de réception par e-mail des espagnols à travers les Amériques.Des chercheurs de l'équipe de sécurité de Talos de Cisco \\ ont déclaré que le botnet, appelé «Horabot», livre un outil de chevaux de Troie et de spam bancaire sur une campagne qui se déroule depuis
Les pirates soupçonnés de vivre au Brésil utilisent un botnet non identifié auparavant appelé à cibler les boîtes de réception par e-mail des espagnols à travers les Amériques.Des chercheurs de l'équipe de sécurité de Talos de Cisco \\ ont déclaré que le botnet, appelé «Horabot», livre un outil de chevaux de Troie et de spam bancaire sur une campagne qui se déroule depuis
 Hackers suspected to be living in Brazil are using a previously unidentified botnet called to target the email inboxes of Spanish speakers across the Americas. Researchers from Cisco\'s Talos security team said the botnet, called “Horabot,” delivers a banking trojan and spam tool onto victim machines in a campaign that has been running since at
Hackers suspected to be living in Brazil are using a previously unidentified botnet called to target the email inboxes of Spanish speakers across the Americas. Researchers from Cisco\'s Talos security team said the botnet, called “Horabot,” delivers a banking trojan and spam tool onto victim machines in a campaign that has been running since at |
Spam Tool | ★★ | ||
| 2023-06-02 13:50:00 | Comment les CISO peuvent gérer l'intersection de la sécurité, de la vie privée et de la confiance How CISOs Can Manage the Intersection of Security, Privacy, And Trust (lien direct) |
Integrating a subject rights request tool with security and compliance solutions can help identify potential data conflicts more efficiently and with greater accuracy.
Integrating a subject rights request tool with security and compliance solutions can help identify potential data conflicts more efficiently and with greater accuracy. |
Tool | ★★ | ||
| 2023-06-01 18:42:00 | Comment réduire l'étalement de l'outil de sécurité dans mon environnement? How Do I Reduce Security Tool Sprawl in My Environment? (lien direct) |
En ce qui concerne la consolidation des outils, concentrez-vous sur les plates-formes sur les produits.
When it comes to tool consolidation, focus on platforms over products. |
Tool | ★★ | ||
| 2023-06-01 17:17:00 | Les experts mettent en garde contre l'exploitation des outils de transfert Moveit à l'aide de bogue zéro-jour Experts warn of MOVEit Transfer tool exploitation using zero-day bug (lien direct) |
 Les pirates exploitent une nouvelle vulnérabilité zéro-jour affectant un outil de transfert de fichiers populaire utilisé par des milliers de grandes entreprises. BleepingCompuller Pour signaler que les pirates exploitaient la vulnérabilité affectant le logiciel Moveit, et la société de sécurité Rapid7 a déclaré qu'elle voyait également l'exploitation du bogue «dans plusieurs environnements clients».L'outil a été créé par
Les pirates exploitent une nouvelle vulnérabilité zéro-jour affectant un outil de transfert de fichiers populaire utilisé par des milliers de grandes entreprises. BleepingCompuller Pour signaler que les pirates exploitaient la vulnérabilité affectant le logiciel Moveit, et la société de sécurité Rapid7 a déclaré qu'elle voyait également l'exploitation du bogue «dans plusieurs environnements clients».L'outil a été créé par
 Hackers are exploiting a new zero-day vulnerability affecting a popular file transfer tool used by thousands of major companies. BleepingComputer was first to report that hackers were exploiting the vulnerability affecting MOVEit software, and security company Rapid7 said it is also seeing exploitation of the bug “across multiple customer environments.” The tool was created by
Hackers are exploiting a new zero-day vulnerability affecting a popular file transfer tool used by thousands of major companies. BleepingComputer was first to report that hackers were exploiting the vulnerability affecting MOVEit software, and security company Rapid7 said it is also seeing exploitation of the bug “across multiple customer environments.” The tool was created by |
Tool Vulnerability | ★★★ | ||
| 2023-05-31 19:15:16 | CVE-2022-35743 (lien direct) | Microsoft Windows Prise en charge de l'outil de diagnostic (MSDT) Vulnérabilité d'exécution de code distant
Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability |
Tool Vulnerability | |||
| 2023-05-31 18:15:09 | CVE-2023-33967 (lien direct) | Easeprobe est un outil qui peut effectuer la vérification de la santé / de l'état.Un problème d'injection SQL a été découvert dans Easéprobe avant 2.1.0 lors de l'utilisation de la vérification des données MySQL / PostgreSQL.Ce problème a été résolu dans la v2.1.0.
EaseProbe is a tool that can do health/status checking. An SQL injection issue was discovered in EaseProbe before 2.1.0 when using MySQL/PostgreSQL data checking. This problem has been fixed in v2.1.0. |
Tool | |||
| 2023-05-31 17:19:00 | Anomali Cyber Watch: Shadow Force cible les serveurs coréens, Volt Typhoon abuse des outils intégrés, Cosmicenergy Tests Electric Distribution Perturbation Anomali Cyber Watch: Shadow Force Targets Korean Servers, Volt Typhoon Abuses Built-in Tools, CosmicEnergy Tests Electric Distribution Disruption (lien direct) |
Les différentes histoires de l'intelligence des menaces dans cette itération de la cyber-montre anomali discutent des sujets suivants: Chine, chargement de DLL, vivant de la terre, technologie opérationnelle, ransomware, et Russie .Les CIO liés à ces histoires sont attachés à Anomali Cyber Watch et peuvent être utilisés pour vérifier vos journaux pour une activité malveillante potentielle. Figure 1 - Diagrammes de résumé du CIO.Ces graphiques résument les CIO attachés à ce magazine et donnent un aperçu des menaces discutées.
Cyber News et Intelligence des menaces
shadowVictiticoor et Coinmin de Force Group \\
(Publié: 27 mai 2023)
Force Shadow est une menace qui cible les organisations sud-coréennes depuis 2013. Il cible principalement les serveurs Windows.Les chercheurs d'AHNLAB ont analysé l'activité du groupe en 2020-2022.Les activités de force fantôme sont relativement faciles à détecter car les acteurs ont tendance à réutiliser les mêmes noms de fichiers pour leurs logiciels malveillants.Dans le même temps, le groupe a évolué: après mars, ses fichiers dépassent souvent 10 Mo en raison de l'emballage binaire.Les acteurs ont également commencé à introduire divers mineurs de crypto-monnaie et une nouvelle porte dérobée surnommée Viticdoor.
Commentaire de l'analyste: Les organisations doivent garder leurs serveurs à jour et correctement configurés avec la sécurité à l'esprit.Une utilisation et une surchauffe du processeur inhabituellement élevées peuvent être un signe du détournement de ressources malveillantes pour l'exploitation de la crypto-monnaie.Les indicateurs basés sur le réseau et l'hôte associés à la force fantôme sont disponibles dans la plate-forme Anomali et il est conseillé aux clients de les bloquer sur leur infrastructure.
mitre att & amp; ck: [mitre att & amp; ck] t1588.003 - obtenir des capacités:Certificats de signature de code | [mitre att & amp; ck] t1105 - transfert d'outils d'entrée | [mitre att & amp; ck] t1027.002 - fichiers ou informations obscurcies: emballage logiciel | [mitre att & amp; ck] t1569.002: exécution du service | [mitre att & amp; ck] T1059.003 - Commande et script Interpréteur: Windows Command Shell | [mitre att & amp; ck] T1547.001 - Exécution de botter ou de connexion automatique: Registre Run Keys / Startup Folder | [mitre att & amp; ck] t1546.008 - Événement Exécution déclenchée: caractéristiques de l'accessibilité | [mitre att & amp; ck] t1543.003 - créer ou modifier le processus système: service Windows | [mitre att & amp; ck] t1554 - compromis le logiciel client binaire | [mitreAtt & amp; ck] t1078.001 - Comptes valides: comptes par défaut | [mitre att & amp; ck] t1140 - désobfuscate / décode ou infor
Figure 1 - Diagrammes de résumé du CIO.Ces graphiques résument les CIO attachés à ce magazine et donnent un aperçu des menaces discutées.
Cyber News et Intelligence des menaces
shadowVictiticoor et Coinmin de Force Group \\
(Publié: 27 mai 2023)
Force Shadow est une menace qui cible les organisations sud-coréennes depuis 2013. Il cible principalement les serveurs Windows.Les chercheurs d'AHNLAB ont analysé l'activité du groupe en 2020-2022.Les activités de force fantôme sont relativement faciles à détecter car les acteurs ont tendance à réutiliser les mêmes noms de fichiers pour leurs logiciels malveillants.Dans le même temps, le groupe a évolué: après mars, ses fichiers dépassent souvent 10 Mo en raison de l'emballage binaire.Les acteurs ont également commencé à introduire divers mineurs de crypto-monnaie et une nouvelle porte dérobée surnommée Viticdoor.
Commentaire de l'analyste: Les organisations doivent garder leurs serveurs à jour et correctement configurés avec la sécurité à l'esprit.Une utilisation et une surchauffe du processeur inhabituellement élevées peuvent être un signe du détournement de ressources malveillantes pour l'exploitation de la crypto-monnaie.Les indicateurs basés sur le réseau et l'hôte associés à la force fantôme sont disponibles dans la plate-forme Anomali et il est conseillé aux clients de les bloquer sur leur infrastructure.
mitre att & amp; ck: [mitre att & amp; ck] t1588.003 - obtenir des capacités:Certificats de signature de code | [mitre att & amp; ck] t1105 - transfert d'outils d'entrée | [mitre att & amp; ck] t1027.002 - fichiers ou informations obscurcies: emballage logiciel | [mitre att & amp; ck] t1569.002: exécution du service | [mitre att & amp; ck] T1059.003 - Commande et script Interpréteur: Windows Command Shell | [mitre att & amp; ck] T1547.001 - Exécution de botter ou de connexion automatique: Registre Run Keys / Startup Folder | [mitre att & amp; ck] t1546.008 - Événement Exécution déclenchée: caractéristiques de l'accessibilité | [mitre att & amp; ck] t1543.003 - créer ou modifier le processus système: service Windows | [mitre att & amp; ck] t1554 - compromis le logiciel client binaire | [mitreAtt & amp; ck] t1078.001 - Comptes valides: comptes par défaut | [mitre att & amp; ck] t1140 - désobfuscate / décode ou infor |
Ransomware Malware Tool Vulnerability Threat | APT 38 Guam CosmicEnergy | ★★ | |
| 2023-05-31 13:00:00 | Cyberheistnews Vol 13 # 22 [Eye on Fraud] Un examen plus approfondi de la hausse massive de 72% des attaques de phishing financier CyberheistNews Vol 13 #22 [Eye on Fraud] A Closer Look at the Massive 72% Spike in Financial Phishing Attacks (lien direct) |
 CyberheistNews Vol 13 #22 | May 31st, 2023
[Eye on Fraud] A Closer Look at the Massive 72% Spike in Financial Phishing Attacks
With attackers knowing financial fraud-based phishing attacks are best suited for the one industry where the money is, this massive spike in attacks should both surprise you and not surprise you at all.
When you want tires, where do you go? Right – to the tire store. Shoes? Yup – shoe store. The most money you can scam from a single attack? That\'s right – the financial services industry, at least according to cybersecurity vendor Armorblox\'s 2023 Email Security Threat Report.
According to the report, the financial services industry as a target has increased by 72% over 2022 and was the single largest target of financial fraud attacks, representing 49% of all such attacks. When breaking down the specific types of financial fraud, it doesn\'t get any better for the financial industry:
51% of invoice fraud attacks targeted the financial services industry
42% were payroll fraud attacks
63% were payment fraud
To make matters worse, nearly one-quarter (22%) of financial fraud attacks successfully bypassed native email security controls, according to Armorblox. That means one in five email-based attacks made it all the way to the Inbox.
The next layer in your defense should be a user that\'s properly educated using security awareness training to easily identify financial fraud and other phishing-based threats, stopping them before they do actual damage.
Blog post with links:https://blog.knowbe4.com/financial-fraud-phishing
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human firewall as your last line of defense.
Join us Wednesday, June 7, @ 2:00 PM (ET), for a live demonstration of how KnowBe4 introduces a new-school approach to security awareness training and simulated phishing.
Get a look at THREE NEW FEATURES and see how easy it is to train and phish your users.
CyberheistNews Vol 13 #22 | May 31st, 2023
[Eye on Fraud] A Closer Look at the Massive 72% Spike in Financial Phishing Attacks
With attackers knowing financial fraud-based phishing attacks are best suited for the one industry where the money is, this massive spike in attacks should both surprise you and not surprise you at all.
When you want tires, where do you go? Right – to the tire store. Shoes? Yup – shoe store. The most money you can scam from a single attack? That\'s right – the financial services industry, at least according to cybersecurity vendor Armorblox\'s 2023 Email Security Threat Report.
According to the report, the financial services industry as a target has increased by 72% over 2022 and was the single largest target of financial fraud attacks, representing 49% of all such attacks. When breaking down the specific types of financial fraud, it doesn\'t get any better for the financial industry:
51% of invoice fraud attacks targeted the financial services industry
42% were payroll fraud attacks
63% were payment fraud
To make matters worse, nearly one-quarter (22%) of financial fraud attacks successfully bypassed native email security controls, according to Armorblox. That means one in five email-based attacks made it all the way to the Inbox.
The next layer in your defense should be a user that\'s properly educated using security awareness training to easily identify financial fraud and other phishing-based threats, stopping them before they do actual damage.
Blog post with links:https://blog.knowbe4.com/financial-fraud-phishing
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human firewall as your last line of defense.
Join us Wednesday, June 7, @ 2:00 PM (ET), for a live demonstration of how KnowBe4 introduces a new-school approach to security awareness training and simulated phishing.
Get a look at THREE NEW FEATURES and see how easy it is to train and phish your users.
|
Ransomware Malware Hack Tool Threat Conference | Uber ChatGPT ChatGPT Guam | ★★ | |
| 2023-05-30 22:00:00 | Rat Seroxen à vendre SeroXen RAT for sale (lien direct) |
This blog was jointly written with Alejandro Prada and Ofer Caspi.
Executive summary
SeroXen is a new Remote Access Trojan (RAT) that showed up in late 2022 and is becoming more popular in 2023. Advertised as a legitimate tool that gives access to your computers undetected, it is being sold for only $30 for a monthly license or $60 for a lifetime bundle, making it accessible.
Key takeaways:
SeroXen is a fileless RAT, performing well at evading detections on static and dynamic analysis.
The malware combines several open-source projects to improve its capabilities. It is a combination of Quasar RAT, r77-rootkit and the command line NirCmd.
Hundreds of samples have shown up since its creation, being most popular in the gaming community. It is only a matter of time before it is used to target companies instead of individual users.
Analysis
Quasar RAT is a legitimate open-source remote administration tool. It is offered on github page to provide user support or employee monitoring. It has been historically associated with malicious activity performed by threat actors, APT groups (like in this Mandiant report from 2017), or government attacks (in this report by Unit42 in 2017).
It was first released in July 2014 as “xRAT” and renamed to “Quasar” in August 2015. Since then, there have been released updates to the code until v1.4.1 in March 2023, which is the most current version. As an open-source RAT tool with updates 9 years after its creation, it is no surprise that it continues to be a common tool used by itself or combined with other payloads by threat actors up to this day.
In a review of the most recent samples, a new Quasar variant was observed by Alien Labs in the wild: SeroXen. This new RAT is a modified branch of the open-source version, adding some modifications features to the original RAT. They’re selling it for monthly or lifetime fee. Figure 1 contains some of the features advertised on their website.
 Figure 1. SeroXen features announced on its website.
This new RAT first showed up on a Twitter account, established in September 2022. The person advertising the RAT appeared to be an English-speaking teenager. The same Twitter handle published a review of the RAT on YouTube. The video approached the review from an attacking/Red Team point of view, encouraging people to buy the tool because it is worth the money. They were claiming to be a reseller of the tool.
In December 2022, a specific domain was registered to market/sell the tool, seroxen[.]com. The RAT was distributed via a monthly license for $30 USD or a lifetime license of $60 USD. It was around that time that the malware was first observed in the wild, appearing with 0 detections on VirusTotal.
After a few months, on the 1st of February, the YouTuber CyberSec Zaado published a video alerting the community about the capabilities of the RAT from a defensive perspective. In late February, the RAT was advertised on social media platforms such as TikTok, Twitter, YouTube, and several cracking forums, including hackforums. There were some conversations on gaming forums complaining about being infected by malware after downloading some video games. The artifacts described by the users matched with SeroXen RAT.
The threat actor updated the domain name to seroxen[.]net by the end of March. This domain name was registered on March 27th
Figure 1. SeroXen features announced on its website.
This new RAT first showed up on a Twitter account, established in September 2022. The person advertising the RAT appeared to be an English-speaking teenager. The same Twitter handle published a review of the RAT on YouTube. The video approached the review from an attacking/Red Team point of view, encouraging people to buy the tool because it is worth the money. They were claiming to be a reseller of the tool.
In December 2022, a specific domain was registered to market/sell the tool, seroxen[.]com. The RAT was distributed via a monthly license for $30 USD or a lifetime license of $60 USD. It was around that time that the malware was first observed in the wild, appearing with 0 detections on VirusTotal.
After a few months, on the 1st of February, the YouTuber CyberSec Zaado published a video alerting the community about the capabilities of the RAT from a defensive perspective. In late February, the RAT was advertised on social media platforms such as TikTok, Twitter, YouTube, and several cracking forums, including hackforums. There were some conversations on gaming forums complaining about being infected by malware after downloading some video games. The artifacts described by the users matched with SeroXen RAT.
The threat actor updated the domain name to seroxen[.]net by the end of March. This domain name was registered on March 27th |
Malware Tool Threat | Uber APT 10 | ★★ | |
| 2023-05-30 20:30:00 | Le fait de renouveler l'article 702 \\ 'aura des coûts importants pour la diplomatie américaine, \\' le haut responsable de l'État dit Failing to renew Section 702 \\'will have significant costs for US diplomacy,\\' top State official says (lien direct) |
 Les efforts diplomatiques américains à travers le monde en souffriraient si le Congrès ne renouvelle pas un outil de surveillance étrangers avant qu'il ne s'allume à la fin de l'année civile, a averti le chef de la succursale du renseignement du Département d'État \\.«Ne vous y trompez pas, l'avenir sans 702, ou un programme 702 beaucoup diminué, aura des coûts importants pour
Les efforts diplomatiques américains à travers le monde en souffriraient si le Congrès ne renouvelle pas un outil de surveillance étrangers avant qu'il ne s'allume à la fin de l'année civile, a averti le chef de la succursale du renseignement du Département d'État \\.«Ne vous y trompez pas, l'avenir sans 702, ou un programme 702 beaucoup diminué, aura des coûts importants pour
 U.S. diplomatic efforts around the globe would suffer if Congress fails to renew a foreign surveillance tool before it lapses at the end of the calendar year, the head of the State Department\'s intelligence branch warned Tuesday. “Make no mistake, the future without 702, or a much diminished 702 program, will have significant costs for
U.S. diplomatic efforts around the globe would suffer if Congress fails to renew a foreign surveillance tool before it lapses at the end of the calendar year, the head of the State Department\'s intelligence branch warned Tuesday. “Make no mistake, the future without 702, or a much diminished 702 program, will have significant costs for |
Tool | ★★ | ||
| 2023-05-30 19:55:01 | Écoutez ces enregistrements: Deepfake Social Engineering Scams effraye les victimes Listen to These Recordings: Deepfake Social Engineering Scams Are Scaring Victims (lien direct) |
> Deepfake Social Engineering Les escroqueries sont devenues une tendance de plus en plus effrayante parmi les cybercriminels à l'ingénierie socialement des victimes de la soumission.Les acteurs de la menace utilisent l'intelligence artificielle (AI) et les outils de clonage vocal d'apprentissage automatique (ML) pour disperser la désinformation pour les escroqueries cybercrimins.Cela ne prend pas beaucoup pour un enregistrement audio d'une voix & # 8211;seulement environ 10 à [& # 8230;]
Le post écoutez ces enregistrements: Deepfake Social Engineering Scams effraye les victimes href = "https://slashnext.com"> slashnext .
>Deepfake social engineering scams have become an increasingly scary trend among cybercriminals to socially engineer victims into submission. The threat actors are using Artificial Intelligence (AI) and Machine Learning (ML) voice cloning tools to disperse misinformation for cybercriminal scams. It doesn\'t take much for an audio recording of a voice – only about 10 to […] The post Listen to These Recordings: Deepfake Social Engineering Scams Are Scaring Victims first appeared on SlashNext. |
Tool Threat Prediction | ★★★ | ||
| 2023-05-30 17:00:00 | Attaques non détectées contre les cibles du Moyen-Orient menées depuis 2020 Undetected Attacks Against Middle East Targets Conducted Since 2020 (lien direct) |
Targeted attacks against Saudi Arabia and other Middle East nations have been detected with a tool that\'s been in the wild since 2020.
Targeted attacks against Saudi Arabia and other Middle East nations have been detected with a tool that\'s been in the wild since 2020. |
Tool | ★★ | ||
| 2023-05-30 10:00:00 | Introduction à l'objectif de la passerelle AWS Transit Introduction to the purpose of AWS Transit Gateway (lien direct) |
Introduction
Today you look at the Global/Multi-site Enterprise Security Architecture of an organization and see a myriad of concerns. Increased levels of complexity, difficulties managing multiple third parties, difficulties implementing consistent levels of security, and so on. This makes it imperative for organizations to identify opportunities to simplify, streamline, and generally improve their infrastructure wherever possible.
Managing the level of complexity is becoming increasingly difficult. Security may be partially implemented, which is an ongoing challenging issue.
Terminology
AWS Region - a physical location around the world where we cluster data centers.
AWS Availability Zone (AZ) - is one or more discrete data centers with redundant power, networking, and connectivity in an AWS Region.
AWS Services - AWS offers a broad set of global cloud-based products, including compute, storage, database, analytics, networking, machine learning and AI, mobile, developer tools, IoT, security, enterprise applications, and more.
AWS Transit Gateway (TGW) - A transit gateway is a network transit hub that you can use to interconnect your virtual private clouds (VPCs) and on-premises networks. As your cloud infrastructure expands globally, inter-Region peering connects transit gateways together using the AWS Global Infrastructure.
Global/Multi-Site Enterprise Architecture
Many organizations are using Global/Multi-site with dated technology spread throughout data centers and networks mixed in with some newer technologies. This can include uncounted third parties as well. These sites often include multiple environments (like Dev, QA, Pre-Prod, and Prod) supported by numerous technologies spread across both physical and virtual servers, including databases, web, and application servers, and more.
Modifications can be challenging when integrating legacy with new technologies. Sometimes can require a static approach when completely redesigning existing infrastructure. Understandably, most organizations tend to shy away from exploring anything that seems like a significant upgrade or change. Thankfully there are some solutions available that can substantially improve operations and infrastructure without the typical complexities and implementation challenges.
One such example is outlined below.
 Example AWS Transit Gateway (TGW) Global Diagram
AWS Transit Gateway diagram
AWS Transit Gateway is a cloud-based tool that permits a simplified, secure networking approach for companies requiring a hybrid solution that can scale according to their global/multi-site enterprise business needs. The AWS Transit Gateway integrates with Palo Alto Security Devices, which helps to reduce the organization’s risk footprint.
AWS Transit Gateway architecture is used to consolidate site-to-site VPN connections from your on-premises network to your AWS environment and support connectivity between your team development and workload hosting VPCs and your infrastructure shared services VPC. This information will help you make a more informed decision as you consider the recommended approach of using AWS Transit Gateway.
AWS Transit Gateway connects your Amazon Virtual Private Clouds (VPCs) and on-premises networks through a central hub. This simplifies your network and puts an end to complex peering relationships. It acts as a cloud router – each new connection is only made once.
As you expand globally, inter-region peering connects AWS Transit Gateways together using the AWS global network. Your data is secured automatically and encrypted; it never travels over the public internet, only on the AWS Global Network. Because of its central position, AWS Transit Gateway Network Manager has a unique view over your entire n
Example AWS Transit Gateway (TGW) Global Diagram
AWS Transit Gateway diagram
AWS Transit Gateway is a cloud-based tool that permits a simplified, secure networking approach for companies requiring a hybrid solution that can scale according to their global/multi-site enterprise business needs. The AWS Transit Gateway integrates with Palo Alto Security Devices, which helps to reduce the organization’s risk footprint.
AWS Transit Gateway architecture is used to consolidate site-to-site VPN connections from your on-premises network to your AWS environment and support connectivity between your team development and workload hosting VPCs and your infrastructure shared services VPC. This information will help you make a more informed decision as you consider the recommended approach of using AWS Transit Gateway.
AWS Transit Gateway connects your Amazon Virtual Private Clouds (VPCs) and on-premises networks through a central hub. This simplifies your network and puts an end to complex peering relationships. It acts as a cloud router – each new connection is only made once.
As you expand globally, inter-region peering connects AWS Transit Gateways together using the AWS global network. Your data is secured automatically and encrypted; it never travels over the public internet, only on the AWS Global Network. Because of its central position, AWS Transit Gateway Network Manager has a unique view over your entire n |
Tool Threat Cloud | ★★ | ||
| 2023-05-30 06:16:36 | CVE-2023-33186 (lien direct) | Zulip est un outil de collaboration d'équipe open source avec un threading unique basé sur un sujet qui combine le meilleur e-mail et le chat pour rendre le travail à distance productif et délicieux.La branche de développement principale du serveur Zulip à partir du 2 mai 2023 et plus tard, y compris les versions bêta 7.0-bêta1 et 7.0-beta2, est vulnérable à une vulnérabilité de script de site transversale dans les infractions sur le flux de messages.Un attaquant qui peut envoyer des messages pourrait élaborer avec malveillance un sujet pour le message, de sorte qu'une victime qui oscille l'influence pour ce sujet dans leur flux de messages déclenche l'exécution du code JavaScript contrôlé par l'attaquant.
Zulip is an open-source team collaboration tool with unique topic-based threading that combines the best of email and chat to make remote work productive and delightful. The main development branch of Zulip Server from May 2, 2023 and later, including beta versions 7.0-beta1 and 7.0-beta2, is vulnerable to a cross-site scripting vulnerability in tooltips on the message feed. An attacker who can send messages could maliciously craft a topic for the message, such that a victim who hovers the tooltip for that topic in their message feed triggers execution of JavaScript code controlled by the attacker. |
Tool Vulnerability | |||
| 2023-05-30 05:15:12 | CVE-2023-33198 (lien direct) | TGStation-Server est un outil d'échelle de production pour Byond Server Management.Le cache de canal de chat Dreammaker API (DMAPI) peut éventuellement être empoisonné par un redémarrage et un relais Tgstation-Server (TGS).Cela peut entraîner l'envoi de messages de chat à l'un des canaux IRC ou Discord configurés pour l'instance sur les robots de chat activés.Cela dure jusqu'à ce que les canaux de chat de l'instance \\ soient mis à jour dans TGS ou DreamDaemon est redémarré.Les commandes de chat TGS ne sont pas affectées, personnalisées ou autrement.
tgstation-server is a production scale tool for BYOND server management. The DreamMaker API (DMAPI) chat channel cache can possibly be poisoned by a tgstation-server (TGS) restart and reattach. This can result in sending chat messages to one of any of the configured IRC or Discord channels for the instance on enabled chat bots. This lasts until the instance\'s chat channels are updated in TGS or DreamDaemon is restarted. TGS chat commands are unaffected, custom or otherwise. |
Tool | |||
| 2023-05-29 21:15:09 | CVE-2023-32072 (lien direct) | Tuleap est un outil open source pour la traçabilité de bout en bout des développements d'application et de système.TULEAP Community Edition avant la version 14.8.99.60 et Tuleap Enterprise Edition avant 14.8-3 et 14.7-7, les journaux des URL de travail Jenkins déclenchés ne sont pas correctement échappés.Un administrateur Git malveillant peut configurer un crochet Jenkins malveillant pour faire une victime, également un administrateur GIT, exécuter du code incontrôlé.TULEAP Community Edition 14.8.99.60, Tuleap Enterprise Edition 14.8-3 et Tuleap Enterprise Edition 14.7-7 contiennent un correctif pour ce numéro.
Tuleap is an open source tool for end to end traceability of application and system developments. Tuleap Community Edition prior to version 14.8.99.60 and Tuleap Enterprise edition prior to 14.8-3 and 14.7-7, the logs of the triggered Jenkins job URLs are not properly escaped. A malicious Git administrator can setup a malicious Jenkins hook to make a victim, also a Git administrator, execute uncontrolled code. Tuleap Community Edition 14.8.99.60, Tuleap Enterprise Edition 14.8-3, and Tuleap Enterprise Edition 14.7-7 contain a patch for this issue. |
Tool | |||
| 2023-05-29 13:22:52 | Les nouveaux Raas ont émergé, l'accès RDP, la base de données et les ventes de cartes de crédit New RaaS Emerged, RDP Access, Database, and Credit Card Sales (lien direct) |
Bienvenue à cette semaine Résumé des nouvelles du Web Dark.Nous découvrons un nouvel outil de ransomware appelé ...
Welcome to this week’s dark web news summary. We uncover a new ransomware tool called... |
Ransomware Tool | ★★★ | ||
| 2023-05-28 15:04:35 | Padre & # 8211;Outil de padding Oracle Attack Exploiter padre – Padding Oracle Attack Exploiter Tool (lien direct) |
Padre est un outil d'attaque Oracle exploiteur et padding avancé qui peut être déployé par rapport au cryptage en mode CBC.
padre is an advanced exploiter and Padding Oracle attack tool that can be deployed against CBC mode encryption. |
Tool | ★★ | ||
| 2023-05-25 12:00:55 | API de services Google Trust ACME disponibles pour tous les utilisateurs sans frais Google Trust Services ACME API available to all users at no cost (lien direct) |
David Kluge, Technical Program Manager, and Andy Warner, Product ManagerNobody likes preventable site errors, but they happen disappointingly often. The last thing you want your customers to see is a dreaded \'Your connection is not private\' error instead of the service they expected to reach. Most certificate errors are preventable and one of the best ways to help prevent issues is by automating your certificate lifecycle using the ACME standard. Google Trust Services now offers our ACME API to all users with a Google Cloud account (referred to as “users” here), allowing them to automatically acquire and renew publicly-trusted TLS certificates for free. The ACME API has been available as a preview and over 200 million certificates have been issued already, offering the same compatibility as major Google services like google.com or youtube.com. | Tool Cloud | ★★★ | ||
| 2023-05-24 18:15:08 | Les domaines de Google \\ S .zip, .mov offrent aux ingénieurs sociaux un nouvel outil brillant Google\\'s .zip, .mov Domains Give Social Engineers a Shiny New Tool (lien direct) |
Security professionals warn that Google\'s new top-level domains, .zip and .mov, pose social engineering risks while providing little reason for their existence.
Security professionals warn that Google\'s new top-level domains, .zip and .mov, pose social engineering risks while providing little reason for their existence. |
Tool | ★★ | ||
| 2023-05-24 12:49:28 | Annonçant le lancement de Guac V0.1 Announcing the launch of GUAC v0.1 (lien direct) |
Brandon Lum and Mihai Maruseac, Google Open Source Security TeamToday, we are announcing the launch of the v0.1 version of Graph for Understanding Artifact Composition (GUAC). Introduced at Kubecon 2022 in October, GUAC targets a critical need in the software industry to understand the software supply chain. In collaboration with Kusari, Purdue University, Citi, and community members, we have incorporated feedback from our early testers to improve GUAC and make it more useful for security professionals. This improved version is now available as an API for you to start developing on top of, and integrating into, your systems.The need for GUACHigh-profile incidents such as Solarwinds, and the recent 3CX supply chain double-exposure, are evidence that supply chain attacks are getting more sophisticated. As highlighted by the | Tool Vulnerability Threat | Yahoo | ★★ | |
| 2023-05-23 22:56:08 | Dexray, DFIR et l'art de l'ambulance Chasing… DeXRAY, DFIR, and the art of ambulance chasing… (lien direct) |
Presque tous mes articles Dexray ont jamais été publiés sur les nouvelles versions de cet outil publiées.Aujourd'hui, je vais parler de la fabrication des saucisses & # 8217;partie [& # 8230;]
Pretty much all of my DeXRAY posts ever published been focusing on new versions of this tool being released. Today I will talk about the ‘making of the sausages’ part […] |
Tool | ★★★★ | ||
| 2023-05-23 13:00:00 | Cyberheistnews Vol 13 # 21 [Double Trouble] 78% des victimes de ransomwares sont confrontées à plusieurs extensions en tendance effrayante CyberheistNews Vol 13 #21 [Double Trouble] 78% of Ransomware Victims Face Multiple Extortions in Scary Trend (lien direct) |
 CyberheistNews Vol 13 #21 | May 23rd, 2023
[Double Trouble] 78% of Ransomware Victims Face Multiple Extortions in Scary Trend
New data sheds light on how likely your organization will succumb to a ransomware attack, whether you can recover your data, and what\'s inhibiting a proper security posture.
You have a solid grasp on what your organization\'s cybersecurity stance does and does not include. But is it enough to stop today\'s ransomware attacks? CyberEdge\'s 2023 Cyberthreat Defense Report provides some insight into just how prominent ransomware attacks are and what\'s keeping orgs from stopping them.
According to the report, in 2023:
7% of organizations were victims of a ransomware attack
7% of those paid a ransom
73% were able to recover data
Only 21.6% experienced solely the encryption of data and no other form of extortion
It\'s this last data point that interests me. Nearly 78% of victim organizations experienced one or more additional forms of extortion. CyberEdge mentions threatening to publicly release data, notifying customers or media, and committing a DDoS attack as examples of additional threats mentioned by respondents.
IT decision makers were asked to rate on a scale of 1-5 (5 being the highest) what were the top inhibitors of establishing and maintaining an adequate defense. The top inhibitor (with an average rank of 3.66) was a lack of skilled personnel – we\'ve long known the cybersecurity industry is lacking a proper pool of qualified talent.
In second place, with an average ranking of 3.63, is low security awareness among employees – something only addressed by creating a strong security culture with new-school security awareness training at the center of it all.
Blog post with links:https://blog.knowbe4.com/ransomware-victim-threats
[Free Tool] Who Will Fall Victim to QR Code Phishing Attacks?
Bad actors have a new way to launch phishing attacks to your users: weaponized QR codes. QR code phishing is especially dangerous because there is no URL to check and messages bypass traditional email filters.
With the increased popularity of QR codes, users are more at
CyberheistNews Vol 13 #21 | May 23rd, 2023
[Double Trouble] 78% of Ransomware Victims Face Multiple Extortions in Scary Trend
New data sheds light on how likely your organization will succumb to a ransomware attack, whether you can recover your data, and what\'s inhibiting a proper security posture.
You have a solid grasp on what your organization\'s cybersecurity stance does and does not include. But is it enough to stop today\'s ransomware attacks? CyberEdge\'s 2023 Cyberthreat Defense Report provides some insight into just how prominent ransomware attacks are and what\'s keeping orgs from stopping them.
According to the report, in 2023:
7% of organizations were victims of a ransomware attack
7% of those paid a ransom
73% were able to recover data
Only 21.6% experienced solely the encryption of data and no other form of extortion
It\'s this last data point that interests me. Nearly 78% of victim organizations experienced one or more additional forms of extortion. CyberEdge mentions threatening to publicly release data, notifying customers or media, and committing a DDoS attack as examples of additional threats mentioned by respondents.
IT decision makers were asked to rate on a scale of 1-5 (5 being the highest) what were the top inhibitors of establishing and maintaining an adequate defense. The top inhibitor (with an average rank of 3.66) was a lack of skilled personnel – we\'ve long known the cybersecurity industry is lacking a proper pool of qualified talent.
In second place, with an average ranking of 3.63, is low security awareness among employees – something only addressed by creating a strong security culture with new-school security awareness training at the center of it all.
Blog post with links:https://blog.knowbe4.com/ransomware-victim-threats
[Free Tool] Who Will Fall Victim to QR Code Phishing Attacks?
Bad actors have a new way to launch phishing attacks to your users: weaponized QR codes. QR code phishing is especially dangerous because there is no URL to check and messages bypass traditional email filters.
With the increased popularity of QR codes, users are more at |
Ransomware Hack Tool Vulnerability Threat Prediction | ChatGPT | ★★ | |
| 2023-05-22 10:41:02 | Une nouvelle ère d'AppSec: 10 fois en tant que leader de Gartner & Reg;Magic Quadrant ™ pour les tests de sécurité des applications A New Era of AppSec: 10 Times as a Leader in Gartner® Magic Quadrant™ for Application Security Testing (lien direct) |
Ten représente l'achèvement d'un cycle et le début d'un nouveau, car il y a dix chiffres dans notre système de nombres de base-10.Nous avons scanné près de 140 billions de lignes de code, nous ne pouvons donc aider à reprendre le seul et le zéro dans notre annonce passionnante.C'est la dixième publication du Gartner & Reg;Magic Quadrant ™ pour les tests de sécurité des applications (AST), et nous sommes heureux d'annoncer que nous sommes un leader pour le dixième temps consécutif.Voici un aperçu du nouveau cycle que nous voyons commencer: la nécessité d'une sécurité logicielle intelligente.
Des tests de sécurité des applications à la sécurité des logiciels intelligents
Ce marché n'est pas ce qu'il était auparavant, et nous voyons un nouveau cycle commençant que nous considérons comme la nécessité d'une sécurité logicielle intelligente.Ce qui a commencé comme un outil de balayage de code SaaS reconnu est devenu une plate-forme de sécurité logicielle intelligente qui empêche, détecte et répond aux défauts de sécurité et aux vulnérabilités et gère les risques et la conformité pour des milliers d'organisations de premier plan autour du…
Ten represents the completion of a cycle and the beginning of a new one, as there are ten digits in our base-10 number system. We\'ve scanned nearly 140 trillion lines of code, so we can\'t help but pick up on the one and the zero in our exciting announcement. It\'s the tenth publication of the Gartner® Magic Quadrant™ for Application Security Testing (AST), and we are pleased to announce we are a Leader for the tenth consecutive time. Here\'s a look at the new cycle we see beginning: the need for intelligent software security. From Application Security Testing to Intelligent Software Security This market isn\'t what it used to be, and we see a new cycle beginning which we see as the need for intelligent software security. What started as a recognized SaaS code scanning tool has evolved into an intelligent software security platform that prevents, detects, and responds to security flaws and vulnerabilities and manages risk and compliance for thousands of leading organizations around the… |
Tool Cloud | ★★★ | ||
| 2023-05-22 10:00:00 | Partager les données de votre entreprise avec Chatgpt: à quel point est-elle risquée? Sharing your business\\'s data with ChatGPT: How risky is it? (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. As a natural language processing model, ChatGPT - and other similar machine learning-based language models - is trained on huge amounts of textual data. Processing all this data, ChatGPT can produce written responses that sound like they come from a real human being. ChatGPT learns from the data it ingests. If this information includes your sensitive business data, then sharing it with ChatGPT could potentially be risky and lead to cybersecurity concerns. For example, what if you feed ChatGPT pre-earnings company financial information, company proprietary software codeor materials used for internal presentations without realizing that practically anybody could obtain that sensitive information just by asking ChatGPT about it? If you use your smartphone to engage with ChatGPT, then a smartphone security breach could be all it takes to access your ChatGPT query history. In light of these implications, let\'s discuss if - and how - ChatGPT stores its users\' input data, as well as potential risks you may face when sharing sensitive business data with ChatGPT. Does ChatGPT store users’ input data? The answer is complicated. While ChatGPT does not automatically add data from queries to models specifically to make this data available for others to query, any prompt does become visible to OpenAI, the organization behind the large language model. Although no membership inference attacks have yet been carried out against the large language learning models that drive ChatGPT, databases containing saved prompts as well as embedded learnings could be potentially compromised by a cybersecurity breach. OpenAI, the parent company that developed ChatGPT, is working with other companies to limit the general access that language learning models have to personal data and sensitive information. But the technology is still in its nascent developing stages - ChatGPT was only just released to the public in November of last year. By just two months into its public release, ChatGPT had been accessed by over 100 million users, making it the fastest-growing consumer app ever at record-breaking speeds. With such rapid growth and expansion, regulations have been slow to keep up. The user base is so broad that there are abundant security gaps and vulnerabilities throughout the model. Risks of sharing business data with ChatGPT In June 2021, researchers from Apple, Stanford University, Google, Harvard University, and others published a paper that revealed that GPT-2, a language learning model similar to ChatGPT, could accurately recall sensitive information from training documents. The report found that GPT-2 could call up information with specific personal identifiers, recreate exact sequences of text, and provide other sensitive information when prompted. These “training data extraction attacks” could present a growing threat to the security of researchers working on machine learning models, as hackers may be able to access machine learning researcher data and steal their protected intellectual property. One data security company called Cyberhaven has released reports of ChatGPT cybersecurity vulnerabilities it has recently prevented. According to the reports, Cyberhaven has identified and prevented insecure requ | Tool Threat Medical | ChatGPT ChatGPT | ★★ | |
| 2023-05-22 09:00:00 | Don \\ 't @ moi: l'obscurcissement de l'URL à travers les abus de schéma Don\\'t @ Me: URL Obfuscation Through Schema Abuse (lien direct) |
Une technique est utilisée dans la distribution de plusieurs familles de logiciels malveillants qui obscurcissent la destination finale d'une URL en abusant du schéma URL .Mandiant suit cette méthodologie adversaire en tant que " URL Schema Obfuscation ” . La technique pourrait augmenter la probabilité d'une attaque de phishing réussie, et pourrait provoquer des erreurs d'extraction de domaine dans l'exploitation forestière ou l'outillage de sécurité. Si un réseau défense le réseauL'outil s'appuie sur la connaissance du serveur qu'une URL pointe vers (par exemple, la vérification si un domaine est sur un flux Intel de menace), il pourrait potentiellement le contourner et provoquer des lacunes dans la visibilité et la couverture.
A technique is being used in the distribution of multiple families of malware that obfuscates the end destination of a URL by abusing the URL schema. Mandiant tracks this adversary methodology as "URL Schema Obfuscation”. The technique could increase the likelihood of a successful phishing attack, and could cause domain extraction errors in logging or security tooling. If a network defense tool is relying on knowing the server a URL is pointing to (e.g. checking if a domain is on a threat intel feed), it could potentially bypass it and cause gaps in visibility and coverage. Common URL parsing |
Malware Tool Threat | ★★★★ | ||
| 2023-05-20 11:08:16 | Les sites Web de Capcut cloné poussent des informations sur le vol de logiciels malveillants Cloned CapCut websites push information stealing malware (lien direct) |
Une nouvelle campagne de distribution de logiciels malveillants est en cours d'identification de l'outil d'édition vidéo Capcut pour pousser diverses souches de logiciels malveillants à des victimes sans méfiance.[...]
A new malware distribution campaign is underway impersonating the CapCut video editing tool to push various malware strains to unsuspecting victims. [...] |
Malware Tool | ★★ | ||
| 2023-05-19 22:15:09 | CVE-2023-28623 (lien direct) | Zulip est un outil de collaboration d'équipe open source avec un thread unique basé sur un sujet.Dans le cas où 1: `zulipldapauthbackend` et un backend d'authentification externe (toute mis à part de` ZulipldapAuthBackend` et `CourrielAuthBackend`) sont les seules activées dans` Authentication_backends` dans `/ etc / zulip / settings.py` et 2: TheLes autorisations d'organisation n'exigent pas les invitations à rejoindre.Un attaquant peut créer un nouveau compte dans l'organisation avec une adresse e-mail arbitraire sous leur contrôle qui n'est pas dans le répertoire LDAP de l'organisation.L'impact est limité aux installations qui ont cette combinaison spécifique de backends d'authentification comme décrit ci-dessus, en plus d'avoir des invitations nécessaires pour rejoindre l'autorisation de l'organisation désactivée de cette organisation.Ce problème a été résolu dans la version 6.2.Il est conseillé aux utilisateurs de mettre à niveau.Les utilisateurs non en mesure de mettre à niveau peuvent permettre aux «invitations sont nécessaires pour rejoindre l'autorisation de l'organisation de cette organisation pour empêcher ce problème.
Zulip is an open-source team collaboration tool with unique topic-based threading. In the event that 1: `ZulipLDAPAuthBackend` and an external authentication backend (any aside of `ZulipLDAPAuthBackend` and `EmailAuthBackend`) are the only ones enabled in `AUTHENTICATION_BACKENDS` in `/etc/zulip/settings.py` and 2: The organization permissions don\'t require invitations to join. An attacker can create a new account in the organization with an arbitrary email address in their control that\'s not in the organization\'s LDAP directory. The impact is limited to installations which have this specific combination of authentication backends as described above in addition to having `Invitations are required for joining this organization` organization permission disabled. This issue has been addressed in version 6.2. Users are advised to upgrade. Users unable to upgrade may enable the `Invitations are required for joining this organization` organization permission to prevent this issue. |
Tool | |||
| 2023-05-19 21:15:08 | CVE-2023-32677 (lien direct) | Zulip est un outil de collaboration d'équipe open source avec un thread unique basé sur un sujet.Les administrateurs de Zulip peuvent configurer Zulip pour limiter qui peut ajouter des utilisateurs aux flux et séparément pour limiter qui peut inviter des utilisateurs à l'organisation.Dans Zulip Server 6.1 et ci-dessous, l'interface utilisateur qui permet à un utilisateur d'inviter un nouvel utilisateur lui permet également de définir les flux auxquels le nouvel utilisateur est invité - même si l'utilisateur invitant n'aurait pas d'autorisations pour ajouter un utilisateur existant aux flux.Bien qu'une telle configuration soit probablement rare dans la pratique, le comportement viole les contrôles liés à la sécurité.Cela ne permet pas à un utilisateur d'inviter de nouveaux utilisateurs à des flux qu'ils ne peuvent pas voir ou ne seraient pas en mesure d'ajouter des utilisateurs s'ils avaient cette autorisation générale.Ce problème a été résolu dans la version 6.2.Il est conseillé aux utilisateurs de mettre à niveau.Les utilisateurs incapables de mettre à niveau peuvent limiter l'envoi d'invitations aux utilisateurs qui ont également l'autorisation d'ajouter des utilisateurs aux flux.
Zulip is an open-source team collaboration tool with unique topic-based threading. Zulip administrators can configure Zulip to limit who can add users to streams, and separately to limit who can invite users to the organization. In Zulip Server 6.1 and below, the UI which allows a user to invite a new user also allows them to set the streams that the new user is invited to -- even if the inviting user would not have permissions to add an existing user to streams. While such a configuration is likely rare in practice, the behavior does violate security-related controls. This does not let a user invite new users to streams they cannot see, or would not be able to add users to if they had that general permission. This issue has been addressed in version 6.2. Users are advised to upgrade. Users unable to upgrade may limit sending of invitations down to users who also have the permission to add users to streams. |
Tool | |||
| 2023-05-19 17:40:00 | FBI misused controversial surveillance tool to investigate Jan. 6 protesters (lien direct) |
 The FBI improperly searched the personal communications of Americans who participated in the Jan. 6 attack on the Capitol and the 2020 protests over police violence, newly declassified documents show. The inappropriate searches of data intercepted under the Foreign Intelligence Surveillance Act (FISA) were originally detailed in a classified April 2021 certification issued by the
The FBI improperly searched the personal communications of Americans who participated in the Jan. 6 attack on the Capitol and the 2020 protests over police violence, newly declassified documents show. The inappropriate searches of data intercepted under the Foreign Intelligence Surveillance Act (FISA) were originally detailed in a classified April 2021 certification issued by the
 The FBI improperly searched the personal communications of Americans who participated in the Jan. 6 attack on the Capitol and the 2020 protests over police violence, newly declassified documents show. The inappropriate searches of data intercepted under the Foreign Intelligence Surveillance Act (FISA) were originally detailed in a classified April 2021 certification issued by the
The FBI improperly searched the personal communications of Americans who participated in the Jan. 6 attack on the Capitol and the 2020 protests over police violence, newly declassified documents show. The inappropriate searches of data intercepted under the Foreign Intelligence Surveillance Act (FISA) were originally detailed in a classified April 2021 certification issued by the |
Tool | ★★★ | ||
| 2023-05-18 11:44:32 | L'outil POC exploite la vulnérabilité Keepass non corrigée pour récupérer les mots de passe maîtres PoC Tool Exploits Unpatched KeePass Vulnerability to Retrieve Master Passwords (lien direct) |
Le chercheur publie un outil POC qui exploite la vulnérabilité Keepass non corrigée pour récupérer le mot de passe maître à partir de la mémoire.
Researcher publishes PoC tool that exploits unpatched KeePass vulnerability to retrieve the master password from memory. |
Tool Vulnerability | ★★★ | ||
| 2023-05-18 10:03:27 | Vulnerability in KeePass Password Manager Permits Retrieving Master Password (CVE-2023-32784) (lien direct) | Une vulnérabilité dans l'outil de gestion du mot de passe open-source peut permettre la récupération du maître ...
Le post vulnérabilité dans le gestionnaire de mot de passe de Keepass permetRécupération du mot de passe maître (CVE-2023-32784) est apparu pour la première fois sur socradar & reg;Cyber Intelligence Inc. .
A vulnerability in the open-source password manager tool KeePass could allow retrieval of the master... The post Vulnerability in KeePass Password Manager Permits Retrieving Master Password (CVE-2023-32784) first appeared on SOCRadar® Cyber Intelligence Inc.. |
Tool Vulnerability | ★★ | ||
| 2023-05-17 23:20:00 | Sparkrat est distribué dans un programme d'installation VPN coréen SparkRAT Being Distributed Within a Korean VPN Installer (lien direct) |
Ahnlab Security Emergency Response Center (ASEC) a récemment découvert que Sparkrat était distribué au sein de l'installateur d'un certain VPNprogramme.Sparkrat est un outil d'administration à distance (rat) développé avec Golang.Lorsqu'il est installé sur un système d'utilisateur, il peut effectuer une variété de comportements malveillants, tels que l'exécution de commandes à distance, le contrôle des fichiers et les processus, le téléchargement de charges utiles supplémentaires et la collecte d'informations à partir du système infecté comme en prenant des captures d'écran.1. Cas de distribution Le fournisseur VPN, dont l'installateur contenait Sparkrat semble ...
AhnLab Security Emergency response Center (ASEC) has recently discovered SparkRAT being distributed within the installer of a certain VPN program. SparkRAT is a Remote Administration Tool (RAT) developed with GoLang. When installed on a user’s system, it can perform a variety of malicious behaviors, such as executing commands remotely, controlling files and processes, downloading additional payloads, and collecting information from the infected system like by taking screenshots. 1. Case of Distribution The VPN provider, whose installer contained SparkRAT appears to... |
Tool | ★★ | ||
| 2023-05-17 18:15:09 | CVE-2023-31135 (lien direct) | DGRAPH est une base de données GraphQL distribuée open source.Les journaux d'audit DGRAPH existants sont vulnérables aux attaques de force brute en raison des collisions non -ce.Les 12 premiers octets proviennent d'une base de base qui est initialisée lorsqu'un journal d'audit est créé.Les 4 derniers octets proviennent de la longueur de la ligne de journal cryptée.Ceci est problématique car deux lignes de journal auront souvent la même longueur, donc en raison de ces collisions, nous réutilisons les mêmes non-non.Tous les journaux d'audit générés par les versions de DGRAPH | Tool | |||
| 2023-05-16 21:39:00 | Les attaquants ciblent les macOS avec \\ 'geacon \\' outil de frappe de cobalt Attackers Target macOS With \\'Geacon\\' Cobalt Strike Tool (lien direct) |
Les acteurs de la menace ont vu en utilisant la mise en œuvre de l'outil d'équipement rouge sur les systèmes MacOS basés sur Intel et Apple silicium.
Threat actors seen using Go-language implementation of the red-teaming tool on Intel and Apple silicon-based macOS systems. |
Tool Threat | ★★★ | ||
| 2023-05-16 18:03:00 | Anomali Cyber Watch: Lancefly APT adopte des alternatives au phishing, BPFDoor a supprimé les indicateurs codés en dur, le FBI a ordonné aux logiciels malveillants russes de s'auto-destruction Anomali Cyber Watch: Lancefly APT Adopts Alternatives to Phishing, BPFdoor Removed Hardcoded Indicators, FBI Ordered Russian Malware to Self-Destruct (lien direct) |
Les diverses histoires de l'intelligence des menaces dans cette itération de la cyber surveillance de l'anomali discutent des sujets suivants: apt, bourse, vol d'identification, Chine, exploits, phishing, ransomware, et Russie .Les CIO liés à ces histoires sont attachés à Anomali Cyber Watch et peuvent être utilisés pour vérifier vos journaux pour une activité malveillante potentielle. Figure 1 - Diagrammes de résumé du CIO.Ces graphiques résument les CIO attachés à ce magazine et donnent un aperçu des menaces discutées.
Cyber News et Intelligence des menaces
lancefly: Le groupe utilise la porte dérobée personnalisée pour cibler les orgs au gouvernement, l'aviation, d'autres secteurs
(Publié: 15 mai 2023)
Les chercheurs de Symantec ont détecté une nouvelle campagne de cyberespionnage par le groupe parrainé par Lancefly Chine ciblant les organisations en Asie du Sud et du Sud-Est.De la mi-2022 à 2023, le groupe a ciblé les secteurs de l'aviation, du gouvernement, de l'éducation et des télécommunications.Les indications des vecteurs d'intrusion montrent que Lancefly est peut-être passé des attaques de phishing à la force brute SSH et en exploitant des dispositifs accessibles au public tels que les équilibreurs de charge.Un petit nombre de machines ont été infectées de manière très ciblée pour déployer la porte dérobée Merdoor personnalisée et une modification de la ZXShell Rootkit open source.Lancefly abuse d'un certain nombre de binaires légitimes pour le chargement latéral DLL, le vol d'identification et d'autres activités de vie (lolbin).
Commentaire des analystes: Les organisations sont conseillées de surveiller l'activité suspecte des PME et les activités LOLBIN indiquant une éventuelle injection de processus ou un dumping de la mémoire LSASS.Les hachages de fichiers associés à la dernière campagne Lancefly sont disponibles dans la plate-forme Anomali et il est conseillé aux clients de les bloquer sur leur infrastructure.
mitre att & amp; ck: [mitre att & amp; ck] t1190 - exploiter l'application de formation publique | [mitreAtt & amp; ck] t1078 - comptes valides | [mitre att & amp; ck] t1056.001 - Capture d'entrée: keylogging | [mitre att & amp; ck] t1569 - services système | [mitre att & amp; ck] t1071.001 - couche d'applicationProtocole: protocoles Web | [mitre att & amp; ck] t1071.004 - protocole de couche d'application: DNS | [mitre att & amp; ck] t1095 - couche non applicationProtocole | [mitre att & amp; ck] t1574.002 - flux d'exécution de hijack: chargement secondaire dll | [mitre att & amp; ck] T1003.001 - Dumping des informations d'identification du système d'exploitation: mémoire lsass | [mitre att & amp; ck] T1003.002 - Dumping des informations d'identification du système d'exploitation: gestionnaire de compte de s
Figure 1 - Diagrammes de résumé du CIO.Ces graphiques résument les CIO attachés à ce magazine et donnent un aperçu des menaces discutées.
Cyber News et Intelligence des menaces
lancefly: Le groupe utilise la porte dérobée personnalisée pour cibler les orgs au gouvernement, l'aviation, d'autres secteurs
(Publié: 15 mai 2023)
Les chercheurs de Symantec ont détecté une nouvelle campagne de cyberespionnage par le groupe parrainé par Lancefly Chine ciblant les organisations en Asie du Sud et du Sud-Est.De la mi-2022 à 2023, le groupe a ciblé les secteurs de l'aviation, du gouvernement, de l'éducation et des télécommunications.Les indications des vecteurs d'intrusion montrent que Lancefly est peut-être passé des attaques de phishing à la force brute SSH et en exploitant des dispositifs accessibles au public tels que les équilibreurs de charge.Un petit nombre de machines ont été infectées de manière très ciblée pour déployer la porte dérobée Merdoor personnalisée et une modification de la ZXShell Rootkit open source.Lancefly abuse d'un certain nombre de binaires légitimes pour le chargement latéral DLL, le vol d'identification et d'autres activités de vie (lolbin).
Commentaire des analystes: Les organisations sont conseillées de surveiller l'activité suspecte des PME et les activités LOLBIN indiquant une éventuelle injection de processus ou un dumping de la mémoire LSASS.Les hachages de fichiers associés à la dernière campagne Lancefly sont disponibles dans la plate-forme Anomali et il est conseillé aux clients de les bloquer sur leur infrastructure.
mitre att & amp; ck: [mitre att & amp; ck] t1190 - exploiter l'application de formation publique | [mitreAtt & amp; ck] t1078 - comptes valides | [mitre att & amp; ck] t1056.001 - Capture d'entrée: keylogging | [mitre att & amp; ck] t1569 - services système | [mitre att & amp; ck] t1071.001 - couche d'applicationProtocole: protocoles Web | [mitre att & amp; ck] t1071.004 - protocole de couche d'application: DNS | [mitre att & amp; ck] t1095 - couche non applicationProtocole | [mitre att & amp; ck] t1574.002 - flux d'exécution de hijack: chargement secondaire dll | [mitre att & amp; ck] T1003.001 - Dumping des informations d'identification du système d'exploitation: mémoire lsass | [mitre att & amp; ck] T1003.002 - Dumping des informations d'identification du système d'exploitation: gestionnaire de compte de s |
Ransomware Malware Tool Vulnerability Threat Cloud | ★★ | ||
| 2023-05-16 13:00:00 | CyberheistNews Vol 13 # 20 [pied dans la porte] Les escroqueries de phishing du Q1 2023 \\ |Infographie CyberheistNews Vol 13 #20 [Foot in the Door] The Q1 2023\\'s Top-Clicked Phishing Scams | INFOGRAPHIC (lien direct) |
 CyberheistNews Vol 13 #20 | May 16th, 2023
[Foot in the Door] The Q1 2023\'s Top-Clicked Phishing Scams | INFOGRAPHIC
KnowBe4\'s latest reports on top-clicked phishing email subjects have been released for Q1 2023. We analyze "in the wild" attacks reported via our Phish Alert Button, top subjects globally clicked on in phishing tests, top attack vector types, and holiday email phishing subjects.
IT and Online Services Emails Drive Dangerous Attack Trend
This last quarter\'s results reflect the shift to IT and online service notifications such as laptop refresh or account suspension notifications that can affect your end users\' daily work.
Cybercriminals are constantly increasing the damage they cause to organizations by luring unsuspecting employees into clicking on malicious links or downloading fake attachments that seem realistic. Emails that are disguised as coming from an internal source, such as the IT department, are especially dangerous because they appear to come from a trusted place where an employee would not necessarily question it or be as skeptical.
Building up your organization\'s human firewall by fostering a strong security culture is essential to outsmart bad actors. The report covers the following:
Common "In-The-Wild" Emails for Q1 2023
Top Phishing Email Subjects Globally
Top 5 Attack Vector Types
Top 10 Holiday Phishing Email Subjects in Q1 2023
This post has a full PDF infographic you can download and share with your users:https://blog.knowbe4.com/q1-2023-top-clicked-phishing
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blocklist
Now there\'s a super easy way to keep malicious emails away from all your users through the power of the KnowBe4 PhishER platform!
The new PhishER Blocklist feature lets you use reported messages to prevent future malicious email with the same sender, URL or attachment from reaching other users. Now you can create a unique list of blocklist entries and dramatically improve your Microsoft 365 email filters without ever leaving the PhishER console.
Join us TOMORROW, Wednesday, May 17, @ 2:00 PM (ET) for a l
CyberheistNews Vol 13 #20 | May 16th, 2023
[Foot in the Door] The Q1 2023\'s Top-Clicked Phishing Scams | INFOGRAPHIC
KnowBe4\'s latest reports on top-clicked phishing email subjects have been released for Q1 2023. We analyze "in the wild" attacks reported via our Phish Alert Button, top subjects globally clicked on in phishing tests, top attack vector types, and holiday email phishing subjects.
IT and Online Services Emails Drive Dangerous Attack Trend
This last quarter\'s results reflect the shift to IT and online service notifications such as laptop refresh or account suspension notifications that can affect your end users\' daily work.
Cybercriminals are constantly increasing the damage they cause to organizations by luring unsuspecting employees into clicking on malicious links or downloading fake attachments that seem realistic. Emails that are disguised as coming from an internal source, such as the IT department, are especially dangerous because they appear to come from a trusted place where an employee would not necessarily question it or be as skeptical.
Building up your organization\'s human firewall by fostering a strong security culture is essential to outsmart bad actors. The report covers the following:
Common "In-The-Wild" Emails for Q1 2023
Top Phishing Email Subjects Globally
Top 5 Attack Vector Types
Top 10 Holiday Phishing Email Subjects in Q1 2023
This post has a full PDF infographic you can download and share with your users:https://blog.knowbe4.com/q1-2023-top-clicked-phishing
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blocklist
Now there\'s a super easy way to keep malicious emails away from all your users through the power of the KnowBe4 PhishER platform!
The new PhishER Blocklist feature lets you use reported messages to prevent future malicious email with the same sender, URL or attachment from reaching other users. Now you can create a unique list of blocklist entries and dramatically improve your Microsoft 365 email filters without ever leaving the PhishER console.
Join us TOMORROW, Wednesday, May 17, @ 2:00 PM (ET) for a l |
Ransomware Spam Malware Hack Tool Threat | ★★ | ||
| 2023-05-16 10:00:00 | Crypting des fichiers et des e-mails: un guide débutant pour sécuriser les informations sensibles Encrypting files and emails: A beginner\\'s guide to securing sensitive information (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. In today\'s digital age, sensitive information is constantly being shared and transmitted over various electronic devices and networks. Whether it\'s personal information like social security numbers and financial information like card information, or business information like trade secrets and client data, it\'s important to ensure that this information is kept secure and protected from unauthorized access. One of the most effective ways to do this is through encryption. Encryption is the process of converting plain text or data into an unreadable format using an encryption algorithm, which can only be deciphered or decrypted by those who have the decryption key. This ensures that if the file or email is intercepted or accessed by unauthorized users, they will not be able to read the information. In cybersecurity, encryption plays a crucial role in ensuring data confidentiality, integrity, and authenticity. In day-to-day life, encryption is used in various ways to make life easier for the common man. For example, encryption is used in online transactions to protect the user\'s financial information from being intercepted and stolen by hackers. Encryption is also used in messaging and email applications to protect the privacy of conversations and messages from being read by unauthorized users. Why encrypt files and Emails? It is important for computer users to encrypt their files and emails because they may contain sensitive information that could be intercepted or accessed by unauthorized users. Encryption adds an extra layer of security to protect against the risks. Encryption ensures that even if the information is intercepted by a malicious user, it is unreadable and unusable. This can prevent the loss of sensitive data. Encryption is becoming more important for organisations in order to comply with privacy and data protection regulations like GDPR, PCI-DSS, and HIPAA. These regulations require businesses to take steps to protect sensitive data, and failure to comply can result in legal and financial penalties. Encrypting emails and files can save individuals and organisations from various cyberthreats such as identity theft, financial fraud etc., as well encryption ensures the confidentiality and integrity of data. How to encrypt files: Here are some steps you can follow to encrypt files: Identify the file you want to encrypt, it can be any file such as document, image, video etc. Choose the encryption software, there are various tools available alongside built in encryption features in Windows and MacOS. Some popular encryption tools available are Veracrypt, 7-zip, GnuPG, AxCrypt. Proceed with the installation of the tool you chose. Browse the file which you want to encrypt in the encryption tool you installed. Choose the encryption algorithm, you can choose as per your needs from algorithms given in the tool, such as AES, blowfish etc. Now, encryption tool will ask you to create a passphrase or password, which will be used to encrypt and decrypt the file. Choose a strong and complex password. Keep the password safe since it is the key to decrypt the file and avoid sharing it with anyone. After choosing the password, start the encryption process within the encryption tool. Time consumed for encrypting files may vary based on file size and encryption algorithm chosen. Once the encryption process is complete, the encrypted will be saved with a new file extension depending on the encryption tool used. By following these steps, you can encrypt your files and protect sensitive information from unauthorized access and interception. How to encrypt E-mails: Encrypting emails is another effective way to protect sensitive information from | Tool | ★★ | ||
| 2023-05-12 00:00:00 | Annonces d'outils d'IA malveillants utilisés pour livrer le voleur Redline Malicious AI Tool Ads Used to Deliver Redline Stealer (lien direct) |
Nous avons observé des campagnes publicitaires malveillantes dans le moteur de recherche de Google \\ avec des thèmes liés à des outils d'IA tels que MidJourney et Chatgpt.
We\'ve been observing malicious advertisement campaigns in Google\'s search engine with themes that are related to AI tools such as Midjourney and ChatGPT. |
Tool | ChatGPT | ★★ | |
| 2023-05-11 21:22:00 | Tool de phishing Microsoft 365 Plug-and-play \\ 'démocratise \\' Campagnes d'attaque Plug-and-Play Microsoft 365 Phishing Tool \\'Democratizes\\' Attack Campaigns (lien direct) |
Nouvelle «grandeur» phishing-as-a-service utilisé dans les attaques ciblant la fabrication, les soins de santé, la technologie et d'autres secteurs.
New "Greatness" phishing-as-a-service used in attacks targeting manufacturing, healthcare, technology, and other sectors. |
Tool | ★★ |
To see everything:
Our RSS (filtrered)
