What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2022-08-17 09:33:15 | (Déjà vu) Job Seekers Targeted in Lazarus Group Hack (lien direct) | The North Korea state-backed Lazarus Group has been observed to be targeting job seekers with malware capable of executing on Apple Macs with Intel and M1 chipsets. ESET, a Slovak cybersecurity firm, linked these events to a campaign dubbed “Operation In(ter)ception” that was first disclosed in June 2020 and involved using social engineering tactics to […] | Malware Hack Medical | APT 38 | ||
| 2022-08-16 14:15:00 | New Attack Weaponizes PLCs to Hack Enterprise and OT Networks (lien direct) | The research resulted in proof-of-concept exploits against seven market-leading automation firms | Hack Guideline | |||
| 2022-08-16 13:53:13 | Ransomware Group Claims Access to SCADA in Confusing UK Water Company Hack (lien direct) | A ransomware group has hit at least one water company in the United Kingdom, but there is some confusion over whose systems were actually breached. | Ransomware Hack | |||
| 2022-08-16 13:34:25 | (Déjà vu) CyberheistNews Vol 12 #33 [Eye Opener] Recent Cisco Hack by Ransomware Group Started Because of a Phishing Attack (lien direct) |

|
Ransomware Hack | |||
| 2022-08-16 13:30:00 | #DEFCON: How US Teen RickRolled His High School District (lien direct) | American teenager explains how he was able to hack his local high school district | Hack | |||
| 2022-08-16 11:30:27 | Il a hacké un tracteur John Deere… et a installé Doom (lien direct) | >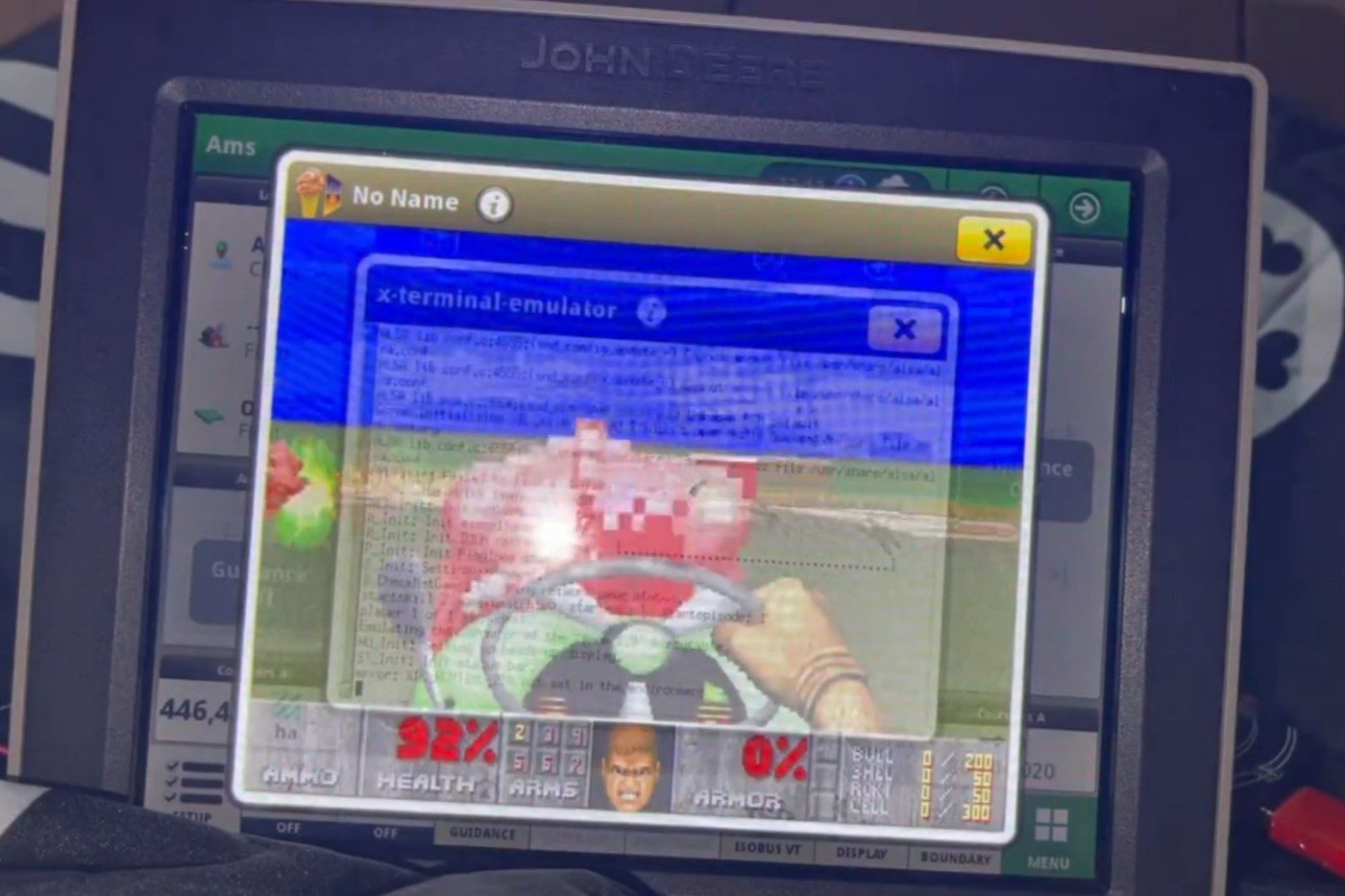 Au delà du jeu vidéo, ce hack permettrait aux utilisateurs de regagner le contrôle des équipements agricoles qu'ils possèdent et de ne plus être obligés de passer par un concessionnaire pour les mises à jour.
L'article Il a hacké un tracteur John Deere… et a installé Doom est à retrouver sur 01net.com.
Au delà du jeu vidéo, ce hack permettrait aux utilisateurs de regagner le contrôle des équipements agricoles qu'ils possèdent et de ne plus être obligés de passer par un concessionnaire pour les mises à jour.
L'article Il a hacké un tracteur John Deere… et a installé Doom est à retrouver sur 01net.com. |
Hack | |||
| 2022-08-16 11:09:42 | Signal Discloses Impact From Twilio Hack (lien direct) | Secure communications services provider Signal on Monday disclosed impact from the recent Twilio hack, after threat actors attempted to re-register the phone numbers of some of its users to new devices. | Hack Threat | |||
| 2022-08-15 22:42:11 | Nearly 1,900 Signal Messenger Accounts Potentially Compromised in Twilio Hack (lien direct) | Popular end-to-end encrypted messaging service Signal on Monday disclosed the cyberattack aimed at Twilio earlier this month may have exposed the phone numbers of roughly 1,900 users. "For about 1,900 users, an attacker could have attempted to re-register their number to another device or learned that their number was registered to Signal," the company said. "All users can rest assured that | Hack | |||
| 2022-08-15 17:46:24 | Twilio hack exposed Signal phone numbers of 1,900 users (lien direct) | Phone numbers of close to 1,900 Signal users were exposed in the data breach Twilio cloud communications company suffered at the beginning of the month. [...] | Data Breach Hack | |||
| 2022-08-15 10:46:06 | Weaponized PLCs Can Hack Engineering Workstations in Attacks on Industrial Orgs (lien direct) | Researchers have shown how hackers could weaponize programmable logic controllers (PLCs) and use them to exploit engineering workstations running software from several major industrial automation companies. | Hack | |||
| 2022-08-12 10:43:09 | Zero-Day Vulnerability Exploited to Hack Over 1,000 Zimbra Email Servers (lien direct) | A new zero-day vulnerability affecting Zimbra has been exploited to hack more than 1,000 enterprise email servers, according to incident response firm Volexity. | Hack Vulnerability | |||
| 2022-08-12 08:00:43 | Experts warn of mass exploitation of an RCE flaw in Zimbra Collaboration Suite (lien direct) | >Threat actors are exploiting an authentication bypass Zimbra flaw, tracked as CVE-2022-27925, to hack Zimbra Collaboration Suite email servers worldwide. An authentication bypass affecting Zimbra Collaboration Suite, tracked as CVE-2022-27925, is actively exploited to hack ZCS email servers worldwide. Zimbra is an email and collaboration platform used by more than 200,000 businesses from over 140 countries. Yesterday, August 11, CISA has […] | Hack | |||
| 2022-08-11 12:59:06 | Recent Cisco Hack by Ransomware Group Started Because of a Phishing Attack (lien direct) |

|
Ransomware Hack | |||
| 2022-08-11 03:53:00 | Cisco admits hack on IT network, links attacker to LAPSUS$ threat group (lien direct) | IT, networking, and cybersecurity solutions giant Cisco has admitted suffering a security incident targeting its corporate IT infrastructure in late May 2022. On August 10, the firm stated that an employee's credentials were compromised after an attacker gained control of a personal Google account where credentials saved in the victim's browser were being synchronized. Bad actors published a list of files from this security incident to the dark web, Cisco added.“The incident was contained to the corporate IT environment and Cisco did not identify any impact to any Cisco products or services, sensitive customer data or employee information, Cisco intellectual property, or supply chain operations,” the company said. Cisco claimed it took immediate action to contain and eradicate the bad actor, which it has linked to notorious threat group LAPSUS$. It also said that it has taken the decision to publicly announce the incident now as it was previously actively collecting information about the bad actor to help protect the security community.To read this article in full, please click here | Hack Threat | |||
| 2022-08-11 03:24:07 | What the Zola Hack Can Teach Us About Password Security (lien direct) | Password security is only as strong as the password itself. Unfortunately, we are often reminded of the danger of weak, reused, and compromised passwords with major cybersecurity breaches that start with stolen credentials. For example, in May 2022, the popular wedding planning site, Zola, was the victim of a significant cybersecurity breach where hackers used an attack known as credential | Hack | |||
| 2022-08-10 16:05:00 | Cyber-criminals Shift From Macros to Shortcut Files to Hack Business PCs, HP Report (lien direct) | The report shows an 11% rise in archive files containing malware, including LNK files | Hack | ★★ | ||
| 2022-08-10 12:00:24 | Making Linux Kernel Exploit Cooking Harder (lien direct) | Posted by Eduardo Vela, Exploit Critic |
Hack | Uber | ||
| 2022-08-08 16:28:03 | Twilio, a texting platform popular with political campaigns, reports breach (lien direct) | >The company says it became aware of the hack on Aug. 4 but it declined to say how many customers were affected by the incident. | Hack | |||
| 2022-08-08 13:49:02 | How You Can Hack Your Senses to Work Better (lien direct) | Cybersecurity has never been a low-stress field. The industry attracts dedicated, highly-skilled perfectionists who are all too willing to shoulder the burden of a company's cybersecurity without complaint. Yet, increased threats of ransomware and cyberattacks are creating an anxiety filled workplace. The current technological skills gap means there is frequently too much work for too […] | Ransomware Hack | |||
| 2022-08-08 07:00:00 | KMSpico explained: No, KMS is not "kill Microsoft" (lien direct) | >Categories: ExplainedA hack tool called KMSPico is hailed as the go-to tool when it comes to activiating Windows. But is it safe? (Read more...) | Hack Tool | |||
| 2022-08-05 21:30:37 | (Déjà vu) Cyberattack on Albanian government suggests new Iranian aggression (lien direct) | Tehran-linked hack of a NATO member is a significant escalation. | Hack | |||
| 2022-08-05 14:20:00 | (Déjà vu) How To Hack Web Applications in 2022: Part 2 (lien direct) | Tehran-linked hack of a NATO member is a significant escalation. | Hack | |||
| 2022-08-04 21:30:27 | An Attack on Albanian Government Suggests New Iranian Aggression (lien direct) | A Tehran-linked hack of a NATO member marks a significant escalation against the backdrop of US-Iran nuclear talks. | Hack | |||
| 2022-08-04 08:00:13 | Attackers leveraging Dark Utilities "C2aaS" platform in malware campaigns (lien direct) |  By Edmund Brumaghin, Azim Khodjibaev and Matt Thaxton, with contributions from Arnaud Zobec.Executive SummaryDark Utilities, released in early 2022, is a platform that provides full-featured C2 capabilities to adversaries.It is marketed as a means to enable remote access, command execution, distributed denial-of-service (DDoS) attacks and cryptocurrency mining operations on infected systems.Payloads provided by the platform support Windows, Linux and Python-based implementations and are hosted within the Interplanetary File System (IPFS), making them resilient to content moderation or law enforcement intervention.Since its initial release, we've observed malware samples in the wild leveraging it to facilitate remote access and cryptocurrency mining.What is "Dark Utilities?"In early 2022, a new C2 platform called "Dark Utilities" was established, offering a variety of services such as remote system access, DDoS capabilities and cryptocurrency mining. The operators of the service also established Discord and Telegram communities where they provide technical support and assistance for customers on the platform. By Edmund Brumaghin, Azim Khodjibaev and Matt Thaxton, with contributions from Arnaud Zobec.Executive SummaryDark Utilities, released in early 2022, is a platform that provides full-featured C2 capabilities to adversaries.It is marketed as a means to enable remote access, command execution, distributed denial-of-service (DDoS) attacks and cryptocurrency mining operations on infected systems.Payloads provided by the platform support Windows, Linux and Python-based implementations and are hosted within the Interplanetary File System (IPFS), making them resilient to content moderation or law enforcement intervention.Since its initial release, we've observed malware samples in the wild leveraging it to facilitate remote access and cryptocurrency mining.What is "Dark Utilities?"In early 2022, a new C2 platform called "Dark Utilities" was established, offering a variety of services such as remote system access, DDoS capabilities and cryptocurrency mining. The operators of the service also established Discord and Telegram communities where they provide technical support and assistance for customers on the platform.  Dark Utilities provides payloads consisting of code that is executed on victim systems, allowing them to be registered with the service and establish a command and control (C2) communications channel. The platform currently supports Windows, Linux and Python-based payloads, allowing adversaries to target multiple architectures without requiring significant development resources. During our analysis, we observed efforts underway to expand OS and system architecture support as the platform continues to see ongoing develo Dark Utilities provides payloads consisting of code that is executed on victim systems, allowing them to be registered with the service and establish a command and control (C2) communications channel. The platform currently supports Windows, Linux and Python-based payloads, allowing adversaries to target multiple architectures without requiring significant development resources. During our analysis, we observed efforts underway to expand OS and system architecture support as the platform continues to see ongoing develo |
Spam Malware Hack Tool Threat Guideline | APT 19 | ||
| 2022-08-03 13:51:03 | Analyse de Chainalysis concernant le hack de Nomad Bridge (lien direct) | À la suite du récent hack de Nomad, voici une analyse de Chainalysis, la plateforme des données des blockchains. Selon Chainalysis, le bridge cross-chain Nomad, qui permet de connecter deux blockchains entre elles, a perdu plus de 2 milliards de dollars en cryptomonnaies au cours des 13 piratages subis depuis début 2022. Chainalysis revient en détail sur les protocoles des bridges cross-chain, expose leurs vulnérabilités et recommande des actions que l'industrie peut entreprendre afin d'assurer (...) - Malwares | Hack | |||
| 2022-08-03 13:26:39 | Solana hack wipes more than 7,000 wallets, totaling nearly $5 million in losses (lien direct) | >The apparent software-based attack stands out among other major cryptocurrency hacks that have totaled nearly $2 billion so far in 2022. | Hack | |||
| 2022-08-03 10:10:14 | Nearly $200 Million Stolen From Cryptocurrency Bridge Nomad (lien direct) | Cryptocurrency bridge Nomad has lost nearly all of its funds as a result of a hack described by experts as chaotic. Losses total nearly $200 million, but the company appears hopeful that it will recover at least some of it. | Hack | |||
| 2022-07-28 10:17:24 | Microsoft: Windows, Adobe Zero-Day Used To Hack Windows Users (lien direct) | >The Microsoft Threat Intelligence Center (MSTIC) and the Microsoft Security Response Center (MSRC) on Wednesday claimed that they found an Austrian-based private-sector offensive actor (PSOA) exploiting multiple Windows and Adobe 0-day exploits in “limited and targeted attacks” against European and Central American customers. For the unversed, PSOAs are private companies that manufacture and sell cyberweapons […] | Hack Threat | |||
| 2022-07-28 09:20:39 | Microsoft Threat Intelligence Center Links Threat Group to Austrian Spyware Vendor DSRIF (lien direct) | Microsoft has linked the efforts of the threat group Knotweed to an Austrian spyware vendor. The group has so far used the malware dubbed ‘SubZero’ to attack groups in Europe and Central America. The Subzero malware, as used by Knotweed, can be used to hack a target’s phone, computers, network, and internet-connected devices. DSRIF markets […] | Malware Hack Threat | |||
| 2022-07-27 20:24:22 | 0-days sold by Austrian firm used to hack Windows users, Microsoft says (lien direct) | Windows and Adobe Reader exploits said to target orgs in Europe and Central America. | Hack | |||
| 2022-07-27 01:04:51 | A Retrospective on the 2015 Ashley Madison Breach (lien direct) | It's been seven years since the online cheating site AshleyMadison.com was hacked and highly sensitive data about its users posted online. The leak led to the public shaming and extortion of many AshleyMadison users, and to at least two suicides. To date, little is publicly known about the perpetrators or the true motivation for the attack. But a recent review of AshleyMadison mentions across Russian cybercrime forums and far-right underground websites in the months leading up to the hack revealed some previously unreported details that may deserve further scrutiny. | Hack Guideline | |||
| 2022-07-26 20:12:01 | European Lawmaker Targeted With Cytrox Predator Surveillance Spyware (lien direct) | A security audit by the European Parliament has unearthed attempts to plant high-end surveillance software on the phone of a Greek lawmaker and there are fresh reports linking the hack attempt to a known North Macedonia spyware vendor. | Hack | |||
| 2022-07-26 17:49:17 | How big is the risk that someone will hack an EV charging network? (lien direct) | EV chargers are on the spectrum of the Internet of Things, and that means risk. | Hack | |||
| 2022-07-26 17:14:09 | Phishing – 967 faux sites voient le jour : comment ne pas se faire avoir ? (lien direct) | >D'après un article du Parisien, un anonyme a déposé la semaine dernière 967 adresses de sites web en .fr qui reprennent, avec quelques fautes de frappe, les noms de marques et d'institutions bien connues. Si les intentions sont encore inconnues, il y a fort à parier qu'une tentative de hack ou de phishing soit en train […] The post Phishing – 967 faux sites voient le jour : comment ne pas se faire avoir ? first appeared on UnderNews. | Hack | |||
| 2022-07-25 00:51:25 | T-Mobile Settles to Pay $350M to Customers in Data Breach (lien direct) | T- Mobile has agreed to pay $350 million to customers affected by a class action lawsuit filed after the company disclosed last August that personal data like social security numbers had been stolen in a | Data Breach Hack | |||
| 2022-07-22 18:41:33 | Hackers leak huge cache of data from evangelical organization that supported Dobbs decision (lien direct) | >The hack is meant to expose donors to evangelical Christian groups opposed to LGBTQ and abortion rights, a message read. | Hack | |||
| 2022-07-20 21:15:25 | Pro-Russia hack campaigns are running rampant in Ukraine (lien direct) | Hacks also exploit critical Follina vulnerability and phishing campaigns. | Hack Vulnerability | |||
| 2022-07-20 14:53:48 | Million of vehicles can be attacked via MiCODUS MV720 GPS Trackers (lien direct) | >Multiple flaws in MiCODUS MV720 Global Positioning System (GPS) trackers shipped with over 1.5 million vehicles can allow hackers to remotely hack them. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) published an advisory to warn of multiple security vulnerabilities in MiCODUS MV720 Global Positioning System (GPS) trackers which are used by over 1.5 million vehicles. An attacker […] | Hack | |||
| 2022-07-19 15:03:20 | SATAn Hack Uses SATA Cable As An Antenna To Steal Data (lien direct) | >Security researchers at the Department of Software and Information Systems Engineering, Ben-Gurion University of the Negev, Israel have published a paper illustrating how a hacker can steal data and sensitive information from an “air-gapped system” through a Serial ATA (SATA) cable and transfer it from a compromised PC on to a nearby receiver. For those […] | Hack | |||
| 2022-07-19 14:36:53 | U.S. government recovers nearly $500,000 from North Korean hack on Kansas medical facility (lien direct) | >Deputy Attorney General Lisa Monaco said it's just the latest example of the benefits of prompt incident reporting. | Hack | |||
| 2022-07-18 07:50:10 | Pegasus Spyware Used to Hack Devices of Pro-Democracy Activists in Thailand (lien direct) | Thai activists involved in the country's pro-democracy protests have had their smartphones infected with the infamous Pegasus government-sponsored spyware. At least 30 individuals, spanning activists, academics, lawyers, and NGO workers, are believed to have been infected between October 2020 and November 2021, many of whom have been previously detained, arrested and imprisoned for their | Hack | |||
| 2022-07-14 14:31:04 | New Browser De-anonymization Technique (lien direct) | Researchers have a new way to de-anonymize browser users, by correlating their behavior on one account with their behavior on another: The findings, which NJIT researchers will present at the Usenix Security Symposium in Boston next month, show how an attacker who tricks someone into loading a malicious website can determine whether that visitor controls a particular public identifier, like an email address or social media account, thus linking the visitor to a piece of potentially personal data. When you visit a website, the page can capture your IP address, but this doesn’t necessarily give the site owner enough information to individually identify you. Instead, the hack analyzes subtle features of a potential target’s browser activity to determine whether they are logged into an account for an array of services, from YouTube and Dropbox to Twitter, Facebook, TikTok, and more. Plus the attacks work against every major browser, including the anonymity-focused Tor Browser... | Hack | |||
| 2022-07-14 14:30:46 | Bandai Namco Confirms Hack And Data At Risk Of Being Leaked (lien direct) | >Bandai Namco, the Japanese video game publisher of many popular games such as Elden Ring, Dark Souls, Pac-Man, Tekken and more, on Wednesday confirmed that they suffered a cyberattack earlier this month and warned that some of their customers’ confidential data may have been stolen. The confirmation of the breach by Bandai Namco comes after […] | Hack | |||
| 2022-07-14 10:00:00 | Chinese hackers targeted U.S. political reporters just ahead of Jan. 6 attack, researchers say (lien direct) | >The previously unreported campaigns represent one of several ongoing nation-state attempts to hack journalists, the researchers said. | Hack | |||
| 2022-07-13 16:50:18 | Bandai Namco confirms hack after ALPHV ransomware data leak threat (lien direct) | Game publishing giant Bandai Namco has confirmed that they suffered a cyberattack that may have resulted in the theft of customers' personal data. [...] | Ransomware Hack Threat | |||
| 2022-07-13 08:13:00 | BrandPost: Why Hackers are Increasingly Targeting Digital Supply Chains (lien direct) | For a large majority of the world, the SolarWinds hack in December 2020 was the first real introduction to digital supply chains and their vulnerabilities. But the reality is that hackers increasingly have been vested in software supply chain attacks, which increased 650% from July 2019 to May 2020 alone.Likewise, data from Netscout's 2H 2021 Threat Intelligence Report shows that hackers remain laser-focused on attacking the digital supply chain. Specifically, there was a 606% increase in attacks against software publishers from 1H 2021, as well as a 162% increase in attacks on computer manufacturers and a 263% increase against computer storage manufacturing. To read this article in full, please click here | Hack Threat | |||
| 2022-07-12 22:58:06 | Ongoing phishing campaign can hack you even when you\'re protected with MFA (lien direct) | Campaign that steals email has targeted at least 10,000 organizations since October. | Hack | |||
| 2022-07-12 14:03:27 | Hackers stole $620 million from Axie Infinity via fake job interviews (lien direct) | The hack that caused Axie Infinity losses of $620 million in crypto started with a fake job offer from North Korean hackers to one of the game's developers. [...] | Hack | |||
| 2022-07-12 08:12:36 | Marriott Hotels Repeat Hack Proves Businesses Still Way Behind On Cybersecurity (lien direct) | Marriott Hotels has been the victim of a third data breach in four years, according to reports. It is clear that today’s businesses are way off the mark when it comes to responsible resilience against cyber threats – especially in preventing repeat attacks. | Data Breach Hack Threat | |||
| 2022-07-11 12:15:05 | Microsoft resorts to Registry hack to keep Outlook from using Windows 11 search (lien direct) | Only a short-term solution to prevent the OS interfering with email results Microsoft has identified Windows Indexing as the culprit for broken Outlook Search results in Windows 11.… | Hack |
To see everything:
Our RSS (filtrered)
