What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2024-04-24 19:34:05 | Arcaneroor - Nouvelle campagne axée sur l'espionnage a trouvé des dispositifs de réseau de périmètre ciblant ArcaneDoor - New Espionage-Focused Campaign Found Targeting Perimeter Network Devices (lien direct) |
## Instantané
Cisco Talos rend compte de la campagne ArcaneDoor, attribuée à l'acteur parrainé par l'État UAT4356 (suivi par Microsoft en tant que Storm-1849), cible les appareils de réseau périmètre de plusieurs fournisseurs, en particulier les appareils de sécurité adaptatifs Cisco (ASA).
Microsoft suit cet acteur en tant que Storm-1849, [en savoir plus ici.] (Https://sip.security.microsoft.com/intel-profiles/f3676211c9f06910f7f1f233d81347c1b837bddd93292c2e8f2eb860a27ad8d5)
## Description
Ces appareils sont cruciaux pour le flux de données dans et hors des réseaux, ce qui les rend idéaux pour les campagnes axées sur l'espionnage.L'UAT4356 a déployé deux baignoires, "Line Runner" et "Line Dancer", pour mener des actions malveillantes telles que la modification de la configuration, la reconnaissance, la capture / exfiltration du trafic réseau et les mouvements potentiellement latéraux.Le vecteur d'accès initial utilisé dans cette campagne reste non identifié, mais deux vulnérabilités (CVE-2024-20353 et CVE-2024-20359) ont été exploitées.
L'acteur a démontré un accent clair sur l'espionnage et une connaissance approfondie des dispositifs ciblés, indiquant une activité sophistiquée parrainée par l'État.Le calendrier de la campagne suggère que l'infrastructure contrôlée par l'acteur était active au début de novembre 2023, la plupart des activités se déroulant entre décembre 2023 et début janvier 2024.
L'implant "Line Dancer", un interprète ShellCode résident à la mémoire, permet aux adversaires de télécharger et d'exécuter des charges utiles de shellcode arbitraires sur les périphériques ASA compromis.Il permet aux acteurs de menace de désactiver les commandes syslog, exécuter et exfiltrater, créer et exfiltrater les captures de paquets et exécuter les commandes CLI, entre autres actions.
La porte dérobée "Line Runner", en revanche, maintient la persistance sur les appareils ASA compromis en tirant parti d'une capacité héritée qui permet la précharge de clients VPN et de plugins.
L'UAT4356 a pris des mesures délibérées pour prévenir la capture médico-légale des artefacts malveillants, y compris les capacités anti-forensiques et anti-analyse.Le niveau élevé de la campagne, le développement des capacités et l'exploitation des vulnérabilités de 0 jour indiquent un acteur parrainé par l'État.
## Recommandations
Microsoft recommande les atténuations suivantes pour réduire l'impact de l'activité associée au Storm-1849.
- durcir les actifs orientés Internet et identifier et sécuriser les systèmes de périmètre que les attaquants pourraient utiliser pour accéder à votre réseau.
- Encouragez les utilisateurs à utiliser Microsoft Edge et d'autres navigateurs Web qui prennent en charge SmartScreen, qui identifie et bloque des sites Web malveillants, y compris des sites de phishing, des sites d'arnaque et des sites contenant des exploits et hébergent des logiciels malveillants.
- Allumez la protection livrée par le cloud dans Microsoft Defender Antivirus ou l'équivalent pour que votre produit antivirus couvre des outils et techniques d'attaquant en évolution rapide.Les protections d'apprentissage automatique basées sur le cloud bloquent une majorité de variantes nouvelles et inconnues.
## Les références
[https://blog.talosintelligence.com/arcaneroor-new-espionage-foccused-campaign-found-targeting-perimeter-network-devices/-Campaign-Found-Targeting-Périmètre-Network-Devices /)
## Snapshot Cisco Talos reports on the ArcaneDoor campaign, attributed to the state-sponsored actor UAT4356 (Tracked by Microsoft as Storm-1849), targets perimeter network devices from multiple vendors, particularly Cisco Adaptive Security Appliances (ASA). Microsoft tracks this actor as Storm-1849, [read more about them here.](https://sip.security.microsoft.com/intel-profiles/f3676211c9f06910f7f1f233d81347c1b837bddd93292c2e8f2eb860a27ad8d5) # |
Malware Tool Vulnerability Threat | ★★★ | ||
| 2024-04-24 19:01:27 | CISA: Les vulnérabilités Cisco et Crushftp ont besoin de patchs urgents CISA: Cisco and CrushFTP vulnerabilities need urgent patches (lien direct) |
## Instantané
Cisco Talos rend compte de la campagne ArcaneDoor, attribuée à l'acteur parrainé par l'État UAT4356 (suivi par Microsoft en tant que Storm-1849), cible les appareils de réseau périmètre de plusieurs fournisseurs, en particulier les appareils de sécurité adaptatifs Cisco (ASA).
Microsoft suit cet acteur en tant que Storm-1849, [en savoir plus ici.] (Https://sip.security.microsoft.com/intel-profiles/f3676211c9f06910f7f1f233d81347c1b837bddd93292c2e8f2eb860a27ad8d5)
## Description
Ces appareils sont cruciaux pour le flux de données dans et hors des réseaux, ce qui les rend idéaux pour les campagnes axées sur l'espionnage.L'UAT4356 a déployé deux baignoires, "Line Runner" et "Line Dancer", pour mener des actions malveillantes telles que la modification de la configuration, la reconnaissance, la capture / exfiltration du trafic réseau et les mouvements potentiellement latéraux.Le vecteur d'accès initial utilisé dans cette campagne reste non identifié, mais deux vulnérabilités (CVE-2024-20353 et CVE-2024-20359) ont été exploitées.
L'acteur a démontré un accent clair sur l'espionnage et une connaissance approfondie des dispositifs ciblés, indiquant une activité sophistiquée parrainée par l'État.Le calendrier de la campagne suggère que l'infrastructure contrôlée par l'acteur était active au début de novembre 2023, la plupart des activités se déroulant entre décembre 2023 et début janvier 2024.
L'implant "Line Dancer", un interprète ShellCode résident à la mémoire, permet aux adversaires de télécharger et d'exécuter des charges utiles de shellcode arbitraires sur les périphériques ASA compromis.Il permet aux acteurs de menace de désactiver les commandes syslog, exécuter et exfiltrater, créer et exfiltrater les captures de paquets et exécuter les commandes CLI, entre autres actions.
La porte dérobée "Line Runner", en revanche, maintient la persistance sur les appareils ASA compromis en tirant parti d'une capacité héritée qui permet la précharge de clients VPN et de plugins.
L'UAT4356 a pris des mesures délibérées pour prévenir la capture médico-légale des artefacts malveillants, y compris les capacités anti-forensiques et anti-analyse.Le niveau élevé de la campagne, le développement des capacités et l'exploitation des vulnérabilités de 0 jour indiquent un acteur parrainé par l'État.
## Recommandations
Microsoft recommande les atténuations suivantes pour réduire l'impact de l'activité associée au Storm-1849.
- durcir les actifs orientés Internet et identifier et sécuriser les systèmes de périmètre que les attaquants pourraient utiliser pour accéder à votre réseau.
- Encouragez les utilisateurs à utiliser Microsoft Edge et d'autres navigateurs Web qui prennent en charge SmartScreen, qui identifie et bloque des sites Web malveillants, y compris des sites de phishing, des sites d'arnaque et des sites contenant des exploits et hébergent des logiciels malveillants.
- Allumez la protection livrée par le cloud dans Microsoft Defender Antivirus ou l'équivalent pour que votre produit antivirus couvre des outils et techniques d'attaquant en évolution rapide.Les protections d'apprentissage automatique basées sur le cloud bloquent une majorité de variantes nouvelles et inconnues.
## Les références
[https://blog.talosintelligence.com/arcaneroor-new-espionage-foccused-campaign-found-targeting-perimeter-network-devices/-Campaign-Found-Targeting-Périmètre-Network-Devices /)
## Snapshot Cisco Talos reports on the ArcaneDoor campaign, attributed to the state-sponsored actor UAT4356 (Tracked by Microsoft as Storm-1849), targets perimeter network devices from multiple vendors, particularly Cisco Adaptive Security Appliances (ASA). Microsoft tracks this actor as Storm-1849, [read more about them here.](https://sip.security.microsoft.com/intel-profiles/f3676211c9f06910f7f1f233d81347c1b837bddd93292c2e8f2eb860a27ad8d5) # |
Vulnerability | ★★★ | ||
| 2024-04-24 17:25:24 | Cisco stimule l'alarme pour \\ 'arcaneor \\' zéro-jours frappant les plates-formes de pare-feu ASA Cisco Raises Alarm for \\'ArcaneDoor\\' Zero-Days Hitting ASA Firewall Platforms (lien direct) |
> Cisco avertit que les pirates de pays nationaux exploitent au moins deux vulnérabilités de zéro jour dans ses plates-formes de pare-feu ASA pour planter des logiciels malveillants sur les télécommunications et les réseaux du secteur de l'énergie.
>Cisco warns that nation state-backed hackers are exploiting at least two zero-day vulnerabilities in its ASA firewall platforms to plant malware on telecommunications and energy sector networks. |
Malware Vulnerability Threat | ★★★ | ||
| 2024-04-24 16:11:26 | Piratage rapide, GPT privé, exploits et Deepfakes de profondeur zéro: le rapport révèle l'impact de l'IA sur le paysage de la cybersécurité Prompt Hacking, Private GPTs, Zero-Day Exploits and Deepfakes: Report Reveals the Impact of AI on Cyber Security Landscape (lien direct) |
Un nouveau rapport de la société de cybersécurité Radware identifie les quatre principaux impacts de l'IA sur le paysage des menaces émergeant cette année.
A new report by cyber security firm Radware identifies the four main impacts of AI on the threat landscape emerging this year. |
Vulnerability Threat | ★★★ | ||
| 2024-04-24 15:06:00 | Les principaux défauts de sécurité exposent des frappes de plus d'un milliard d'utilisateurs d'applications de clavier chinois Major Security Flaws Expose Keystrokes of Over 1 Billion Chinese Keyboard App Users (lien direct) |
Les vulnérabilités de sécurité découvertes dans les applications de clavier Pinyin basées sur le cloud pourraient être exploitées & nbsp; pour révéler les utilisateurs \\ 'clés à des acteurs néfastes.
Les résultats proviennent du Citizen Lab, qui a découvert les faiblesses dans huit des neuf applications de vendeurs comme Baidu, Honor, Iflytek, Oppo, Samsung, Tencent, Vivo et Xiaomi. & Nbsp; le seul vendeur dont l'application clavier & nbsp; n'a pas eu de nbsp;sécurité
Security vulnerabilities uncovered in cloud-based pinyin keyboard apps could be exploited to reveal users\' keystrokes to nefarious actors. The findings come from the Citizen Lab, which discovered weaknesses in eight of nine apps from vendors like Baidu, Honor, iFlytek, OPPO, Samsung, Tencent, Vivo, and Xiaomi. The only vendor whose keyboard app did not have any security |
Vulnerability | ★★★★ | ||
| 2024-04-24 13:24:44 | Patch maintenant: Exploit de nuages de nuages Crushftp Zero-Day cible les orgs américains Patch Now: CrushFTP Zero-Day Cloud Exploit Targets US Orgs (lien direct) |
Un exploit pour la vulnérabilité permet aux attaquants non authentifiés d'échapper à un bac à sable de système de fichiers virtuel pour télécharger des fichiers système et potentiellement réaliser RCE.
An exploit for the vulnerability allows unauthenticated attackers to escape a virtual file system sandbox to download system files and potentially achieve RCE. |
Vulnerability Threat Cloud | ★★ | ||
| 2024-04-24 13:07:51 | Les pirates Arcaneroor exploitent Cisco Zero-Days pour briser les réseaux Govt ArcaneDoor hackers exploit Cisco zero-days to breach govt networks (lien direct) |
Cisco a averti aujourd'hui qu'un groupe de piratage soutenu par l'État a exploité deux vulnérabilités de jour zéro dans l'appareil de sécurité adaptatif (ASA) et les pare-feu de la défense des menaces de feu (FTD) depuis novembre 2023 pour violer les réseaux gouvernementaux dans le monde.[...]
Cisco warned today that a state-backed hacking group has been exploiting two zero-day vulnerabilities in Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) firewalls since November 2023 to breach government networks worldwide. [...] |
Vulnerability Threat | ★★ | ||
| 2024-04-24 11:54:21 | Russian APT28 Exploitation de Windows Vulnérabilité avec outil d'Oeeegg Russian APT28 Exploiting Windows Vulnerability with GooseEgg Tool (lien direct) |
> Par waqas
Mettez à jour les fenêtres maintenant ou soyez piraté: Microsoft met en garde contre la vulnérabilité activement exploitée!
Ceci est un article de HackRead.com Lire le post original: Russian APT28 Exploitation de Windows Vulnérabilité avec l'outil Gooseegg
>By Waqas Update Windows Now or Get Hacked: Microsoft Warns of Actively Exploited Vulnerability! This is a post from HackRead.com Read the original post: Russian APT28 Exploiting Windows Vulnerability with GooseEgg Tool |
Tool Vulnerability | APT 28 | ★★★ | |
| 2024-04-24 10:00:00 | Comprendre comment la rationalité, la théorie de la dissuasion et l'indéterminisme influencent la cybercriminalité. Understanding how Rationality, Deterrence Theory, and Indeterminism Influence Cybercrime. (lien direct) |
Understanding the factors influencing cybercriminal behavior is essential for developing effective cybercrime prevention strategies. Rationality plays a significant role in shaping criminal decisions, particularly through the lens of the rational actor model and deterrence theory. This blog explores how rationality influences cybercriminal behavior, focusing on the rational actor model, the concepts of deterrence theory, their implications for understanding and preventing cybercrime activities, and how Bayesian theory can help overcome indeterministic human criminal behavior to provide risk management. Brief History of Deterrence Theory: Deterrence theory has its roots in classical criminology and the works of philosophers such as Cesare Beccaria and Jeremy Bentham, who introduced the concept of deterrence as a means of preventing crime through the application of punishment. This idea became further developed during the mid-20th century when the theory of nuclear deterrence emerged as a prominent concept in international relations. The understanding of deterrence broadened to be applied not only in preventing nuclear conflict but also in the context of criminal justice. It was John Nash through his work in game theory that contributed significantly to the understanding of strategic decision-making and the potential for deterrence in various competitive situations. His insights were crucial in shaping the modern understanding of deterrence theory, particularly when applied to criminal decision-making and cybersecurity.[1] Explanation of Deterministic, Non-Deterministic, and Indeterministic: Deterministic: In the context of decision-making, determinism refers to the philosophical concept that all events, including human actions, are the inevitable result of preceding causes. This perspective suggests that given the same initial conditions and knowledge, an individual\'s choices can be predicted with certainty. In other words, under deterministic assumptions, human behavior can be seen as fully predictable.[2] Non-Deterministic: Non-deterministic views reject the idea that every event, including human actions, can be precisely determined or predicted based on preceding causes. Instead, non-deterministic perspectives acknowledge the role of uncertainty, chance, and randomness in decision-making. From this standpoint, human behavior is seen as influenced by a combination of factors, including personal choice, external circumstances, and unpredictable elements.[3] Indeterministic: Indeterminism represents a specific form of non-determinism. In the context of decision-making, indeterministic views emphasize the idea that certain events or actions, particularly human choices, are not entirely determined by preceding causes or predictable factors. Instead, they are seen as influenced by random or unpredictable elements, such as personal spontaneity, free will, or external factors that defy precise prediction.[4] The Indeterministic Nature of Cybercriminal Behavior: The indeterministic nature of cybercriminal behavior suggests that not all cybercrimes are the result of rational choices. Some individuals may engage in cybercriminal behavior due to impulsive actions, vulnerabilities in systems, or external pressures that override rational decision-making processes. These factors highlight the limitations of solely relying on rationality as an explanatory framework for cybercriminal behavior. Rationality and the Rational Actor Model in Cybercrime: The rational actor model suggests that cybercriminals are rational decision-makers who engage in a cost-benefit analysis before committing a cybercrime.[5] According to this model, cybercriminals weigh the potential benefits and costs of engaging in cybercriminal behavior and make a rational choice based on their assessment. The rational actor model assumes that cybercriminals have the capability to accurately assess the potential outcomes of their cyber actions and aim to maximize th | Tool Vulnerability Studies Legislation Prediction | ★★★ | ||
| 2024-04-24 08:29:43 | SecureWorks mène avec une intégration avancée de la détection des menaces et du risque de vulnérabilité pour une résolution de menaces accélérée Secureworks Leads with Advanced Integration of Threat Detection and Vulnerability Risk for Expedited Threat Resolution (lien direct) |
La toute nouvelle innovation décompose les silos pour la menace et la priorisation de la vulnérabilité, créant une expérience unifiée pour les équipes et les équipes SECOPS SecureWorks & Reg;Annoncez la capacité d'intégrer le contexte du risque de vulnérabilité à la détection des menaces pour empêcher les attaquants d'exploiter les vulnérabilités connues et d'accélérer les temps de réponse, améliorant la posture de sécurité d'une organisation.L'intégration entre Taegis ™ XDR et Taegis VDR permet aux clients et aux partenaires de voir les vulnérabilités connues dans le contexte de (...)
-
revues de produits
Newest innovation breaks down silos for threat and vulnerability prioritization creating a unified experience for IT and SecOps teams Secureworks® announce the ability to integrate vulnerability risk context with threat detection to prevent attackers from exploiting known vulnerabilities and expedite response times, improving an organization\'s security posture. The integration between Taegis™ XDR and Taegis VDR enables customers and partners to view known vulnerabilities in the context of (...) - Product Reviews |
Vulnerability Threat | ★★ | ||
| 2024-04-24 08:05:50 | Nuageux avec une chance de ransomware: des outils cloud tiers vous mettent en danger, dit omniindex Cloudy with a chance of ransomware: Third-party cloud tools are putting you at risk, says OmniIndex (lien direct) |
Il est temps de passer de notre dépendance à l'égard des outils tiers construits sur une infrastructure facilement exploitée Actuellement, une proportion écrasante d'entreprises placent leurs données sensibles entre les mains dans les mainsd'outils cloud tiers qui sont en proie à une multitude de vulnérabilités.Ceci est selon le PDG d'OmniIndex et l'expert en sécurité des données Simon Bain, qui soutient que les entreprises doivent adopter des technologies modernes ou des attaques à risque, car les attaquants de ransomware exploitent continuellement le cloud tiers (...)
-
opinion
It\'s time to move on from our reliance on third-party tools built on easily exploited infrastructure At present, an overwhelming proportion of businesses are placing their sensitive data in the hands of third-party cloud tools that are plagued by a multitude of vulnerabilities. This is according to OmniIndex CEO and data security expert Simon Bain, who argues that businesses must embrace modern technologies or risk attacks, as ransomware attackers continually exploit third-party cloud (...) - Opinion |
Ransomware Tool Vulnerability Threat Cloud | ★★★ | ||
| 2024-04-24 07:46:15 | Portnox et BugCrowd pour lancer le programme privé de primes de bug pour fournir le meilleur contrôle d'accès unifié Portnox and Bugcrowd to Launch Private Bug Bounty Program to Provide Best-In-Class Unified Access Control (lien direct) |
Portnox, un fournisseur leader de solutions de contrôle d'accès à la fiducie native du cloud, annoncera qu'il lancera bientôt un programme privé de prime avec BugCrowd, le leader de la sécurité crowdsourcée.Le programme de primes de Bug Portnox offrira une prime pour les pirates éthiques, également appelés «pirates de chapeau blanc», pour découvrir et signaler les vulnérabilités de sécurité des logiciels au sein des services de production de Portnox \\.BugCrowd gérera le processus de soumission et de récompense, qui est conçu pour assurer un rational (...)
-
nouvelles commerciales
Portnox, a leading provider of cloud-native, zero trust access control solutions, announce it will soon launch a private bug bounty program with Bugcrowd, the leader in crowdsourced security. The Portnox bug bounty program will offer a bounty for ethical hackers, also known as "white hat hackers," to uncover and report software security vulnerabilities within Portnox\'s production services. Bugcrowd will manage the submission and reward process, which is designed to ensure a streamlined (...) - Business News |
Vulnerability | ★★★ | ||
| 2024-04-23 22:47:49 | Les pirates de la Russie ont exploité Windows Flaw pour déployer & # 8216; GooseEgg & # 8217;Malware Russia’s APT28 Hackers Exploited Windows Flaw To Deploy ‘GooseEgg’ Malware (lien direct) |
Microsoft a récemment révélé que le groupe de menaces russes & # 8220; APT28 & # 8243;utilisé un outil de piratage précédemment inconnu, «GooseEgg & # 8221;Pour exploiter la vulnérabilité Windows Print Spooler pour obtenir un accès élevé aux systèmes cibles et voler des informations d'identification et des informations. Selon l'équipe de renseignement des menaces de Redmond, APT28, également appelée Fancy Bear and Forest Blizzard (anciennement Strontium), utilise l'outil post-compromis depuis au moins juin 2020 et peut-être dès avril 2019Pour exploiter le CVE-2022-38028 (score CVSS: 7.8) Vulnérabilité dans Windows Print Spooler Service. Cet outil modifie un fichier de contraintes JavaScript et l'exécute avec des autorisations au niveau du système. Bien que la société ait abordé la vulnérabilité, CVE-2022-38028, rapportée par la U.S.Mate Security Agency (NSA) dans le cadre de Microsoft & # 8217; s octobre 2022 Patch Mardi Security Mises à jour, elle n'a fait aucune mention du défaut dans son avis . Microsoft a observé APT28 en utilisant GooseEgg dans le cadre des activités post-compromis contre diverses cibles, y compris les organisations gouvernementales, non gouvernementales, de l'éducation et des transports en Ukraine, en Europe occidentale et en Amérique du Nord. Bien que Gooseegg soit une application de lanceur simple, il peut engendrer d'autres applications sur la ligne de commande avec des autorisations élevées. Cela permet aux acteurs de menace de prendre en charge les activités malveillantes telles que l'exécution du code distant, l'installation d'une porte dérobée et le déplacement latéralement à travers des réseaux compromis. Les gouvernements américains et britanniques ont lié Forest Blizzard à l'unité 26165 de la Fédération de Russie \'s Military Intelligence Agency, la principale Direction du renseignement de l'état-major général des Forces armées de la Fédération de Russie (GRU). «Microsoft a observé qu'après avoir obtenu l'accès à un appareil cible, Forest Blizzard utilise GooseEgg pour élever les privilèges dans l'environnement.GooseEgg est généralement déployé avec un script de lot, que nous avons observé en utilisant le nom execute.bat et doit.bat .Ce script de lot écrit le fichier servtask.bat, qui contient des commandes pour enregistrer / compresser les ruches de registre.Le script de lot invoque l'exécutable de GooseEgg apparié et configure la persistance en tant que tâche planifiée conçue pour exécuter servtask.bat », lit le Advisory publié par Microsoft lundi. Les chercheurs de Microsoft ont noté qu'un fichier DLL malveillant intégré généralement, qui comprend l'expression « wayzgoose»; par exemple, wayzgoose23.dll , est une application de lanceur utilisée par la menaceLes acteurs doivent lancer d'autres charges utiles avec des autorisations au niveau du système et installer une porte dérobée, se déplacer latéralement dans le réseau de la victime et exécuter à distance le code sur les systèmes violés. Comme mentionné précédemment, la société a corrigé le défaut de sécurité des spouleurs imprimés en 2022. Il a également corrigé les vulnérabilités imprimées précédemment exploitées en 2021. «Les clients qui n'ont pas encore mis en œuvre ces correctifs sont invités à le faire dès que possible pour la sécurité de leur organisation», a déclaré Microsoft dans son avis. De plus, la société recommande également de dé | Malware Tool Vulnerability Threat | APT 28 | ★★★ | |
| 2024-04-23 20:40:36 | Siemens travaillant sur Corre Siemens Working on Fix for Device Affected by Palo Alto Firewall Bug (lien direct) |
Des attaques croissantes ciblant la faille ont incité la CISA à l'inclure dans le catalogue connu des vulnérabilités exploitées plus tôt ce mois-ci.
Growing attacks targeting the flaw prompted CISA to include it in the known exploited vulnerabilities catalog earlier this month. |
Vulnerability | ★★★ | ||
| 2024-04-23 19:30:00 | Faisceau d'application Apache Cordova ciblé dans l'attaque de confusion de dépendance Apache Cordova App Harness Targeted in Dependency Confusion Attack (lien direct) |
Les chercheurs ont identifié une vulnérabilité de confusion de dépendance ayant un impact sur un projet d'Apache archivé appelé harnais d'applications Cordova.
Attaques de confusion de dépendance & nbsp; se déroulent & nbsp; en raison du fait que les gestionnaires de package de package consultent les référentiels publics avant les registres privés, permettant ainsi à un acteur de menace de publier un package malveillant avec le même nom à un référentiel de packages public.
Ce&
Researchers have identified a dependency confusion vulnerability impacting an archived Apache project called Cordova App Harness. Dependency confusion attacks take place owing to the fact that package managers check the public repositories before private registries, thus allowing a threat actor to publish a malicious package with the same name to a public package repository. This& |
Vulnerability Threat | ★★★ | ||
| 2024-04-23 13:47:59 | Inviciti lance la première notation prédictive des risques pour les tests de sécurité des applications compatibles avec l'IA pour les tests de sécurité des applications Invicti Launches First AI-Enabled Predictive Risk Scoring for Application Security Testing (lien direct) |
La capacité unique accélère l'identification des risques avec la hiérarchisation proactive des vulnérabilités des applications Web invicti, le principal fournisseur de solutions de test de sécurité des applications, annoncer sa nouvelle capacité de notation prédictive des risques compatible AI.La fonctionnalité attribue le risque prévu aux applications et aide les organisations à obtenir une vision stratégique de leur risque global de sécurité des applications.
La notation des risques redidictive permet aux organisations de déterminer quelles applications Web doivent être scannées (...)
-
nouvelles commerciales
Unique capability accelerates risk identification with proactive prioritization of web application vulnerabilities Invicti, the leading provider of application security testing solutions, announce its new AI-enabled Predictive Risk Scoring capability. The feature assigns predicted risk to applications and helps organizations gain a strategic view of their overall application security risk. redictive Risk Scoring allows organizations to determine which web applications should be scanned (...) - Business News |
Vulnerability | ★★★ | ||
| 2024-04-23 13:15:47 | Découvrir des menaces potentielles à votre application Web en tirant parti des rapports de sécurité Uncovering potential threats to your web application by leveraging security reports (lien direct) |
Posted by Yoshi Yamaguchi, Santiago Díaz, Maud Nalpas, Eiji Kitamura, DevRel team
The Reporting API is an emerging web standard that provides a generic reporting mechanism for issues occurring on the browsers visiting your production website. The reports you receive detail issues such as security violations or soon-to-be-deprecated APIs, from users\' browsers from all over the world.
Collecting reports is often as simple as specifying an endpoint URL in the HTTP header; the browser will automatically start forwarding reports covering the issues you are interested in to those endpoints. However, processing and analyzing these reports is not that simple. For example, you may receive a massive number of reports on your endpoint, and it is possible that not all of them will be helpful in identifying the underlying problem. In such circumstances, distilling and fixing issues can be quite a challenge.
In this blog post, we\'ll share how the Google security team uses the Reporting API to detect potential issues and identify the actual problems causing them. We\'ll also introduce an open source solution, so you can easily replicate Google\'s approach to processing reports and acting on them.
How does the Reporting API work?
Some errors only occur in production, on users\' browsers to which you have no access. You won\'t see these errors locally or during development because there could be unexpected conditions real users, real networks, and real devices are in. With the Reporting API, you directly leverage the browser to monitor these errors: the browser catches these errors for you, generates an error report, and sends this report to an endpoint you\'ve specified.
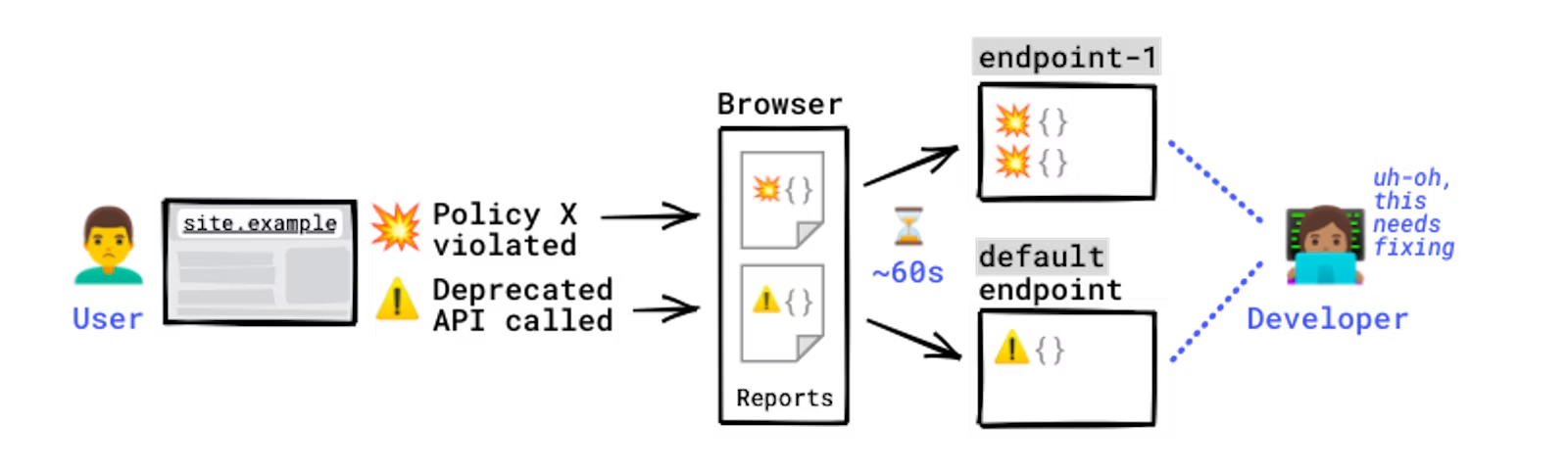 How reports are generated and sent.
Errors you can monitor with the Reporting API include:
Security violations: Content-Security-Policy (CSP), Cross-Origin-Opener-Policy (COOP), Cross-Origin-Embedder-Policy (COEP)
Deprecated and soon-to-be-deprecated API calls
Browser interventions
Permissions policy
And more
For a full list of error types you can monitor, see use cases and report types.
The Reporting API is activated and configured using HTTP response headers: you need to declare the endpoint(s) you want the browser to send reports to, and which error types you want to monitor. The browser then sends reports to your endpoint in POST requests whose payload is a list of reports.
Example setup:#
How reports are generated and sent.
Errors you can monitor with the Reporting API include:
Security violations: Content-Security-Policy (CSP), Cross-Origin-Opener-Policy (COOP), Cross-Origin-Embedder-Policy (COEP)
Deprecated and soon-to-be-deprecated API calls
Browser interventions
Permissions policy
And more
For a full list of error types you can monitor, see use cases and report types.
The Reporting API is activated and configured using HTTP response headers: you need to declare the endpoint(s) you want the browser to send reports to, and which error types you want to monitor. The browser then sends reports to your endpoint in POST requests whose payload is a list of reports.
Example setup:# |
Malware Tool Vulnerability Mobile Cloud | ★★★ | ||
| 2024-04-23 13:00:16 | Protéger contre les attaques de tsunami DDOS Protecting Against DDoS Tsunami Attacks (lien direct) |
> Le protecteur DDOS quantique aide à se défendre contre les attaques sophistiquées du tsunami DDOS sans temps d'arrêt ni perturbation de service.Check Point a une histoire de longue date de protection de nombreux clients dans le monde entier contre les attaques DDOS Web à grande échelle (déni de service distribué), gérant efficacement de grandes quantités de trafic dépassant 1 million de demandes par seconde (RPS).Les attaques émergentes du DDOS, notamment les attaques au tsunami, ont augmenté en fréquence et en sophistication depuis le début de la guerre de Russie-Ukraine, tirée à la fois par des acteurs parrainés par l'État et des «hacktivistes» à l'aide de botnets et d'outils de pointe.Ces cybercriminels évoluent continuellement, tirant parti des techniques avancées pour exploiter les vulnérabilités, en magnifiant la surface d'attaque des organisations du monde entier.À Check [& # 8230;]
>Quantum DDoS Protector helps defend against sophisticated Tsunami DDoS Attacks without downtime or service disruption. Check Point has a long-standing history of protecting numerous customers worldwide from large-scale web DDoS (Distributed Denial of Service) attacks, effectively handling large amounts of traffic exceeding 1 million requests per second (RPS). Emerging DDoS attacks, notably Tsunami attacks, have surged in frequency and sophistication since the start of the Russia-Ukraine War, driven by both state-sponsored actors and “hacktivists” using botnets and cutting-edge tools. These cyber criminals are continuously evolving, leveraging advanced techniques to exploit vulnerabilities, magnifying the attack surface for organizations worldwide. At Check […] |
Tool Vulnerability Threat | ★★★ | ||
| 2024-04-23 12:01:00 | Exploitation de la vulnérabilité à la hausse en tant que phishing de fossé de l'attaquant Vulnerability Exploitation on the Rise as Attacker Ditch Phishing (lien direct) |
Le dernier rapport M-Trends de Mandiant \\ a révélé que l'exploitation de la vulnérabilité était le vecteur d'infection initial le plus courant en 2023, représentant 38% des intrusions
Mandiant\'s latest M-Trends report found that vulnerability exploitation was the most common initial infection vector in 2023, making up 38% of intrusions |
Vulnerability | ★★★ | ||
| 2024-04-23 12:00:00 | Tenage sur le bord: VPNS, pare-feu \\ 'La télémétrie non existante attire Apts Teetering on the Edge: VPNs, Firewalls\\' Nonexistent Telemetry Lures APTs (lien direct) |
Les groupes parrainés par l'État ciblent les vulnérabilités critiques dans les passerelles de réseau privé virtuel (VPN), les appareils de pare-feu et d'autres appareils Edge pour rendre la vie difficile aux répondeurs incidents, qui ont rarement une visibilité sur les appareils.
State-sponsored groups are targeting critical vulnerabilities in virtual private network (VPN) gateways, firewall appliances, and other edge devices to make life difficult for incident responders, who rarely have visibility into the devices. |
Vulnerability | ★★★ | ||
| 2024-04-23 10:00:00 | L'impact de l'UNECE R155 sur la cybersécurité automobile The Impact of UNECE R155 on Automotive Cybersecurity (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. In an era where technology and transportation converge, the fusion of vehicles with IoT technologies heralds a new dawn of mobility. This leap forward promises enhanced connectivity and autonomous capabilities, yet casts a shadow of cyber vulnerabilities that could jeopardize not just the integrity of the vehicles but the safety of their passengers. Recognizing the urgency of this issue, the UNECE stepped forward with the R155 regulation, a vanguard initiative to fortify the digital fortresses of our vehicles against potential cyber onslaughts. The Genesis of UNECE R155: Forging the Shields of Cybersecurity The essence of the UNECE R155 regulation unfolds as a carefully crafted framework designed to preemptively address the burgeoning threat landscape in the automotive sector. Rooted in the principle of proactive defense, R155 isn\'t just about compliance; it represents a paradigm shift in how vehicle cybersecurity is perceived and integrated. At its core, the regulation mandates the establishment of a Cybersecurity Management System (CSMS), compelling manufacturers to weave a tapestry of cyber resilience that spans the entire lifecycle of a vehicle. The ambition of R155 is pretty clear at this point: to transform the automotive industry\'s approach to cybersecurity from reactive patchwork to a strategic, foundational pillar. This involves not only the adoption of \'security by design\' principles but also a commitment to continual vigilance and adaptation in the face of evolving cyber threats. The regulation, thus, sets the stage for a future where vehicles are not merely transport mechanisms but fortified nodes within an expansive network of connected mobility. The Journey to CSMS Certification The path to CSMS certification under R155 is a clear yet challenging journey that demands attention to detail and a commitment to security from vehicle manufacturers. This process starts with a considerable risk assessment, where manufacturers must identify any potential cybersecurity risks within their vehicles. This step is crucial for understanding where vulnerabilities might exist and how they can be addressed to ensure vehicles are secure. Following this, the principle of \'security by design\' becomes central to the certification process. This means that from the very beginning of designing a vehicle, cybersecurity needs to be a key consideration. It\'s about making sure that security measures are built into the vehicle from the start, rather than being added on later. This approach challenges manufacturers to think about cybersecurity as an integral part of the vehicle, just like its engine or wheels. Achieving certification is a team effort that involves not only the manufacturers but also suppliers and regulatory bodies. It\'s about working together to make sure that every part of the vehicle, from its software to its hardware, meets the high security standards set out by R155. Addressing R155 Implementation Challenges As manufacturers and suppliers are gearing up to align with the R155 regulation, however, they encounter a set of practical challenges that test their adaptability and foresight. One of the most sign | Vulnerability Threat | ★★★ | ||
| 2024-04-23 09:52:00 | Microsoft DRM Hack pourrait autoriser les téléchargements de films à partir de services de streaming populaires Microsoft DRM Hack Could Allow Movie Downloads From Popular Streaming Services (lien direct) |
> Microsoft Playready Vulnérabilités qui pourraient permettre aux abonnés Rogue de télécharger illégalement des films à partir de services de streaming populaires.
>Microsoft PlayReady vulnerabilities that could allow rogue subscribers to illegally download movies from popular streaming services. |
Hack Vulnerability | ★★★ | ||
| 2024-04-23 08:54:08 | Le nouveau rapport CGCYBER met en garde contre les risques de cybersécurité dans le milieu marin en raison des systèmes OT connectés au réseau New CGCYBER report warns of cybersecurity risks in marine environment due to network-connected OT systems (lien direct) |
> Le Cyber Command (CGCyber) de la Garde côtière américaine a annoncé lundi que l'OT (technologie opérationnelle) connecté au réseau introduit des vulnérabilités potentielles ...
>The U.S. Coast Guard Cyber Command (CGCYBER) announced on Monday that network-connected OT (operational technology) introduces potential vulnerabilities... |
Vulnerability Industrial | ★★★★ | ||
| 2024-04-23 01:15:11 | Old Windows Print Spooler Bug est la dernière cible du gang d'ours sophistiqué de la Russie Old Windows print spooler bug is latest target of Russia\\'s Fancy Bear gang (lien direct) |
Les copains de Poutine \\ utilisent \\ 'gooseegg \' malware pour lancer des attaques que vous pouvez vaincre avec des correctifs ou une suppression Les espions russes exploitent une vulnérabilité de spooler d'impression Windows vieille et utilisent unUn outil personnalisé appelé GooseEgg pour élever les privilèges et voler des informations d'identification sur des réseaux compromis, selon Microsoft Threat Intelligence.…
Putin\'s pals use \'GooseEgg\' malware to launch attacks you can defeat with patches or deletion Russian spies are exploiting a years-old Windows print spooler vulnerability and using a custom tool called GooseEgg to elevate privileges and steal credentials across compromised networks, according to Microsoft Threat Intelligence.… |
Malware Tool Vulnerability Threat | APT 28 | ★★★ | |
| 2024-04-22 20:36:56 | Vulnérabilité Windows rapportée par la NSA exploitée pour installer des logiciels malveillants russes Windows vulnerability reported by the NSA exploited to install Russian malware (lien direct) |
Microsoft n'a pas divulgué les exploits dans le groupe par le Kremlin jusqu'à présent.
Microsoft didn\'t disclose the in-the-wild exploits by Kremlin-backed group until now. |
Malware Vulnerability | ★★ | ||
| 2024-04-22 19:35:01 | Le domaine Nespresso sert une tasse de phish torride, pas de crème ou de sucre Nespresso Domain Serves Up Steamy Cup of Phish, No Cream or Sugar (lien direct) |
Une vulnérabilité directe ouverte dans le domaine Web Nespresso permet aux attaquants de contourner la détection alors qu'ils tentent de voler les références Microsoft.
An open direct vulnerability in the Nespresso Web domain lets attackers bypass detection as they attempt to steal victims\' Microsoft credentials. |
Vulnerability | ★★★ | ||
| 2024-04-22 19:02:33 | Botnets Continue Exploiting CVE-2023-1389 for Wide-Scale Spread (lien direct) | ## Instantané
Des botnets tels que Moobot, Miori, AgoEnt et Gafgyt Variant exploitent la vulnérabilité CVE-2023-1389, qui a été divulguée l'année dernière.La vulnérabilité est une vulnérabilité d'injection de commande non authentifiée dans l'API «Locale» disponible via l'interface de gestion Web du TP-Link Archer AX21 (AX1800).
## Description
Plusieurs botnets, dont Moobot, Miroi, Agoent, et la variante Gafgyt, ont été observés en exploitant cette vulnérabilité.Chaque botnet utilise des méthodes uniques d'infection et d'attaque, avec Agoant et la variante Gafgyt ciblant les architectures basées sur Linux pour lancer des attaques DDOS, tandis que Moobot initie les attaques DDOS sur les IPs distants après avoir récupéré des fichiers ELF à partir d'une URL spécifique.L'infiltration initiale se produit par la vulnérabilité d'injection de commande non authentifiée dans l'API "Locale", permettant aux attaquants d'atteindre l'injection de commandement en manipulant la forme "pays" et en "écriture".
## Les références
[https://www.fortinet.com/blog/thereat-research/botnets-continue-exploiting-cve-2023-1389-for-wide-scale-spreadmenace-research / botnets-continue-exploitant-cve-2023-1389 pour l'échelle de l'échelle)
## Snapshot Botnets such as Moobot, Miori, AGoent, and Gafgyt Variant are exploiting the CVE-2023-1389 vulnerability, which was disclosed last year. The vulnerability is an unauthenticated command injection vulnerability in the “locale” API available via the web management interface of the TP-Link Archer AX21 (AX1800). ## Description Multiple botnets, including Moobot, Miroi, AGoent, and the Gafgyt Variant, have been observed exploiting this vulnerability. Each botnet employs unique methods of infection and attack, with AGoent and the Gafgyt Variant targeting Linux-based architectures to launch DDoS attacks, while Moobot initiates DDoS attacks on remote IPs after retrieving ELF files from a specific URL. The initial infiltration occurs through the unauthenticated command injection vulnerability in the "locale" API, allowing attackers to achieve command injection by manipulating the "country" form and "write" operation. ## References [https://www.fortinet.com/blog/threat-research/botnets-continue-exploiting-cve-2023-1389-for-wide-scale-spread](https://www.fortinet.com/blog/threat-research/botnets-continue-exploiting-cve-2023-1389-for-wide-scale-spread) |
Vulnerability | ★★★ | ||
| 2024-04-22 16:35:00 | Miter Corporation violé par des pirates d'État-nation exploitant Ivanti Flaws MITRE Corporation Breached by Nation-State Hackers Exploiting Ivanti Flaws (lien direct) |
La Miter Corporation a révélé que c'était la cible d'une cyberattaque nationale qui a exploité deux défauts zéro jour dans les appareils sécurisés à Ivanti Connect à partir de janvier 2024.
L'intrusion a conduit au compromis de son environnement d'expérimentation, de recherche et de virtualisation en réseau (nerf), un réseau de recherche et de prototypage non classifié.
L'adversaire inconnu "a réalisé une reconnaissance
The MITRE Corporation revealed that it was the target of a nation-state cyber attack that exploited two zero-day flaws in Ivanti Connect Secure appliances starting in January 2024. The intrusion led to the compromise of its Networked Experimentation, Research, and Virtualization Environment (NERVE), an unclassified research and prototyping network. The unknown adversary "performed reconnaissance |
Vulnerability Threat | ★★★ | ||
| 2024-04-22 15:04:06 | Faits saillants hebdomadaires, 22 avril 2024 Weekly OSINT Highlights, 22 April 2024 (lien direct) |
## Snapshot Last week\'s OSINT reporting focused on attack activity by APT groups and the infamous FIN7 (tracked by Microsoft as Sangria Tempest). These articles showcase the evolution of threat actor tactics, from FIN7\'s precise spear-phishing campaign targeting a US-based automotive manufacturer with the Anunak backdoor to TA427\'s (Emerald Sleet) strategic information gathering efforts aligned with North Korea\'s interests. ## Description 1. **[Spear-Phishing Campaign by FIN7 (Sangria Tempest) Targeting US-Based Automotive Manufacturer](https://sip.security.microsoft.com/intel-explorer/articles/e14e343c):** BlackBerry analysts detect a spear-phishing campaign by FIN7, tracked by Microsoft as Sangria Tempest, targeting a US-based automotive manufacturer with the Anunak backdoor. The attackers focus on IT department employees with elevated privileges, deploying living off the land binaries (lolbas) and multi-stage processes to mask malicious activity, illustrating a shift towards precise targeting in high-value sectors. 2. **[Information Gathering Tactics of TA427 (Emerald Sleet)](https://sip.security.microsoft.com/intel-explorer/articles/5d36b082):** Proofpoint details the information gathering tactics of TA427, a North Korea-aligned threat actor engaged in benign conversation starter campaigns targeting US and South Korea foreign policy initiatives. TA427 heavily relies on social engineering tactics and web beacons for reconnaissance, impersonating individuals from various verticals to gather strategic intelligence, demonstrating persistence and adaptability in adjusting tactics and infrastructure. 3. **[Analysis of Russia\'s Notorious APT44 (Seashell Blizzard)](https://sip.security.microsoft.com/intel-explorer/articles/24c2a760):** Sponsored by Russian military intelligence, APT44 is a dynamic and operationally mature threat actor that is actively engaged in the full spectrum of espionage, attack, and influence operations. Tracked by Microsoft as Seashell Blizzard, APT44 is actively engaged in espionage, attack, and influence operations to serve Russian national interests. APT44 presents a persistent, high-severity threat to governments and critical infrastructure globally, with a history of aggressive cyber attacks undermining democratic processes and presenting a significant proliferation risk for new cyber attack concepts and methods. 4. **[Zero-Day Exploitation of Palo Alto Networks PAN-OS by UTA0218](https://sip.security.microsoft.com/intel-explorer/articles/958d183b):** Volexity discovers zero-day exploitation of a vulnerability in Palo Alto Networks PAN-OS by threat actor UTA0218, resulting in unauthenticated remote code execution. UTA0218 exploits firewall devices to deploy malicious payloads, facilitating lateral movement within victim organizations, demonstrating highly capable threat actor tradecraft and a clear playbook to further their objectives. ## Learn More For the latest security research from the Microsoft Threat Intelligence community, check out the Microsoft Threat Intelligence Blog: [https://aka.ms/threatintelblog](https://aka.ms/threatintelblog). Microsoft customers can use the following reports in Microsoft Defender Threat Intelligence to get the most up-to-date information about the threat actor, malicious activity, and techniques discussed in this summary. The following reports provide the intelligence, protection information, and recommended actions to prevent, mitigate, or respond to associated threats found in customer environments: - Vulnerability Profile: [CVE-2024-3400](https://sip.security.microsoft.com/intel-profiles/CVE-2024-3400) - Actor Profile: [Sangria Tempest](https://security.microsoft.com/intel-profiles/3e4a164ad64958b784649928499521808aea4d3565df70afc7c85eae69f74278) - Actor Profile: [Seashell Blizzard](https://sip.security.microsoft.com/intel-profiles/cf1e406a16835d56cf614430aea3962d7ed99f01ee3d9ee3048078288e5201bb) - Actor Profile: [Emerald Sleet](https://sip.security.microsoft.com/intel-profiles/f1e214422d | Vulnerability Threat | ★★★ | ||
| 2024-04-22 13:30:00 | Vulnérabilité de confusion de dépendance trouvée dans le projet Apache Dependency Confusion Vulnerability Found in Apache Project (lien direct) |
Cela se produit lorsqu'un package privé récupère un public similaire, conduisant à l'exploit en raison de erreurs de configuration dans les gestionnaires de packages
This occurs when a private package fetches a similar public one, leading to exploit due to misconfigurations in package managers |
Vulnerability Threat | ★★ | ||
| 2024-04-22 12:50:21 | 22 avril & # 8211;Rapport de renseignement sur les menaces 22nd April – Threat Intelligence Report (lien direct) |
> Pour les dernières découvertes en cyberLes meilleures attaques et violations Mitre Corporation ont révélé un événement de sécurité qui s'est produit en janvier 2024. L'attaque, liée au groupe chinois de l'APP, UNC5221, a impliqué l'exploitation de deux vulnérabilités zéro jour dans les produits VPN Ivanti.L'attaquant [& # 8230;]
>For the latest discoveries in cyber research for the week of 22nd April, please download our Threat_Intelligence Bulletin. TOP ATTACKS AND BREACHES MITRE Corporation disclosed a security event that occurred in January 2024. The attack, which is linked to Chinese APT group UNC5221, involved exploitation of two zero-day vulnerabilities in Ivanti VPN products. The attacker […] |
Vulnerability Threat | ★★ | ||
| 2024-04-22 12:30:29 | DC3, DCSA collabore pour lancer le programme de divulgation de vulnérabilité pour la base industrielle de la défense DC3, DCSA collaborate to launch vulnerability disclosure program for defense industrial base (lien direct) |
> Le Département américain de la Défense (DOD) Cyber Crime Center (DC3) et l'agence de contre-espionnage et de sécurité de la défense (DCSA) annoncent ...
>The U.S. Department of Defense (DoD) Cyber Crime Center (DC3) and Defense Counterintelligence and Security Agency (DCSA) announce... |
Vulnerability Industrial | ★★ | ||
| 2024-04-22 11:00:00 | La vulnérabilité de transfert de fichiers Crushftp permet aux attaquants de télécharger des fichiers système CrushFTP File Transfer Vulnerability Lets Attackers Download System Files (lien direct) |
Crushftp exhorte les clients à télécharger V11 de sa plate-forme de transfert de fichiers, les attaquants exploitant activement une vulnérabilité qui leur permet de télécharger des fichiers système
CrushFTP is urging customers to download v11 of its file transfer platform, with attackers actively exploiting a vulnerability that allows them to download system files |
Vulnerability | ★★★ | ||
| 2024-04-22 10:00:00 | Apportez votre propre appareil: comment éduquer vos employés sur les meilleures pratiques de cybersécurité Bring Your Own Device: How to Educate Your Employees On Cybersecurity Best Practices (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article.
 With the rise of remote and flexible work arrangements, Bring Your Own Device (BYOD) programs that allow employees to use their personal devices for work are becoming increasingly mainstream. In addition to slashing hardware costs, BYOD improves employee satisfaction by 56% and productivity by 55%, a survey by Crowd Research Partners finds. Yet, cybersecurity remains a concern for businesses. 72% are worried about data leakage or loss, while 52% fear the potential for malware on personal devices. But by implementing a strong BYOD policy and educating your employees on cybersecurity best practices, you can reap the benefits of BYOD without putting your company assets and data at risk.
Put a Formal BYOD Policy in Place
Just as your business has acceptable use policies in place for corporate devices, similar policies for personal devices are just as important. Your company’s BYOD policy should provide your employees with clear rules and guidelines on how they can use their devices safely at work without compromising cybersecurity. This policy should cover:
Devices, software, and operating systems that can be used to access digital business resources
Devices, software, and operating systems that can’t be used to access digital business resources
Policies that outline the acceptable use of personal devices for corporate activities
Essential security measures employees must follow on personal devices (such as, complex passwords and regular security updates)
Steps employees must follow if their device is stolen or lost (like immediately report it to their manager or IT department)
A statement that your business will erase company-related data from lost or stolen devices remotely
What happens if an employee violates your BYOD policy (are you going to revoke certain access privileges? If you give employees an allowance to cover BYOD costs, will you freeze the funds? Provide additional corrective training?).
Don’t forget to also include a signature field the employee must sign in to indicate their agreement with your BYOD policies. The best time to introduce employees to the policy is during onboarding or, for existing employees, during the network registration process for the BYOD device. Setting expectations and educating your employees is essential to protect both company data and employee privacy.
Basic Cybersecurity Training
When putting together your BYOD employee training program, don’t make the mistake of thinking basic device security is too…basic. It’s not. Since personal devices are usually less secure than corporate devices, they’re generally at a greater risk of data breaches, viruses, and loss or theft. Comprehensive user education that includes the basics is therefore all the more important to mitigate these risks.
So as a basic rule, your employees should know not to allow their devices to auto-connect to public networks. If, on rare occasions, employees really do need to access company data on an open network, they should use a virtual private network (VPN). VPNs encrypt data and hide we
With the rise of remote and flexible work arrangements, Bring Your Own Device (BYOD) programs that allow employees to use their personal devices for work are becoming increasingly mainstream. In addition to slashing hardware costs, BYOD improves employee satisfaction by 56% and productivity by 55%, a survey by Crowd Research Partners finds. Yet, cybersecurity remains a concern for businesses. 72% are worried about data leakage or loss, while 52% fear the potential for malware on personal devices. But by implementing a strong BYOD policy and educating your employees on cybersecurity best practices, you can reap the benefits of BYOD without putting your company assets and data at risk.
Put a Formal BYOD Policy in Place
Just as your business has acceptable use policies in place for corporate devices, similar policies for personal devices are just as important. Your company’s BYOD policy should provide your employees with clear rules and guidelines on how they can use their devices safely at work without compromising cybersecurity. This policy should cover:
Devices, software, and operating systems that can be used to access digital business resources
Devices, software, and operating systems that can’t be used to access digital business resources
Policies that outline the acceptable use of personal devices for corporate activities
Essential security measures employees must follow on personal devices (such as, complex passwords and regular security updates)
Steps employees must follow if their device is stolen or lost (like immediately report it to their manager or IT department)
A statement that your business will erase company-related data from lost or stolen devices remotely
What happens if an employee violates your BYOD policy (are you going to revoke certain access privileges? If you give employees an allowance to cover BYOD costs, will you freeze the funds? Provide additional corrective training?).
Don’t forget to also include a signature field the employee must sign in to indicate their agreement with your BYOD policies. The best time to introduce employees to the policy is during onboarding or, for existing employees, during the network registration process for the BYOD device. Setting expectations and educating your employees is essential to protect both company data and employee privacy.
Basic Cybersecurity Training
When putting together your BYOD employee training program, don’t make the mistake of thinking basic device security is too…basic. It’s not. Since personal devices are usually less secure than corporate devices, they’re generally at a greater risk of data breaches, viruses, and loss or theft. Comprehensive user education that includes the basics is therefore all the more important to mitigate these risks.
So as a basic rule, your employees should know not to allow their devices to auto-connect to public networks. If, on rare occasions, employees really do need to access company data on an open network, they should use a virtual private network (VPN). VPNs encrypt data and hide we |
Malware Vulnerability | ★★★ | ||
| 2024-04-22 02:35:32 | La NSA lance les 10 meilleurs stratégies d'atténuation de la sécurité du cloud NSA Debuts Top 10 Cloud Security Mitigation Strategies (lien direct) |
Alors que les entreprises passent aux configurations hybrides et multi-clouds, les vulnérabilités résultant de erreurs de configuration et de lacunes de sécurité augmentent, attirant l'attention des mauvais acteurs.En réponse, l'Agence américaine de sécurité nationale (NSA) a publié un ensemble de dix stratégies d'atténuation recommandées, publiées plus tôt cette année (avec le soutien de l'Agence américaine de sécurité de la cybersécurité et des infrastructures sur six des stratégies).Les recommandations couvrent la sécurité du cloud, la gestion de l'identité, la protection des données et la segmentation du réseau.Laissez \\ examiner de plus près: 1. Conservez le modèle de responsabilité partagée dans le cloud ...
As businesses transition to hybrid and multi-cloud setups, vulnerabilities arising from misconfigurations and security gaps are escalating, attracting attention from bad actors. In response, the US National Security Agency (NSA) issued a set of ten recommended mitigation strategies, published earlier this year (with support from the US Cybersecurity and Infrastructure Security Agency on six of the strategies). The recommendations cover cloud security, identity management, data protection, and network segmentation. Let \' s take a closer look: 1. Uphold the Cloud Shared Responsibility Model... |
Vulnerability Cloud | ★★★ | ||
| 2024-04-21 05:44:44 | Améliorer la cybersécurité industrielle en s'attaquant aux menaces, en respectant les réglementations, en stimulant la résilience opérationnelle Enhancing industrial cybersecurity by tackling threats, complying with regulations, boosting operational resilience (lien direct) |
> Les organisations de l'espace de cybersécurité industrielle traitent constamment des défis, notamment les violations de logiciels, les vulnérabilités matérielles, la chaîne d'approvisionnement ...
>Organizations across the industrial cybersecurity space are constantly dealing with challenges including software breaches, hardware vulnerabilities, supply chain... |
Vulnerability Industrial | ★★ | ||
| 2024-04-20 11:23:00 | Palo Alto Networks révèle plus de détails sur la faille Pan-OS critique Palo Alto Networks Discloses More Details on Critical PAN-OS Flaw Under Attack (lien direct) |
Palo Alto Networks a partagé plus de détails sur un défaut de sécurité critique ayant un impact sur Pan-OS qui a été soumis à l'exploitation active & nbsp; in the wild & nbsp; par des acteurs malveillants.
La société a décrit la vulnérabilité, suivie comme & nbsp; CVE-2024-3400 & nbsp; (score CVSS: 10,0), comme "complexe" et une combinaison de deux bugs dans les versions Pan-OS 10.2, Pan-OS 11.0 et Pan-OS 11.1 & nbspdu logiciel.
"Dans
Palo Alto Networks has shared more details of a critical security flaw impacting PAN-OS that has come under active exploitation in the wild by malicious actors. The company described the vulnerability, tracked as CVE-2024-3400 (CVSS score: 10.0), as "intricate" and a combination of two bugs in versions PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1 of the software. "In |
Vulnerability | ★★★ | ||
| 2024-04-20 10:48:00 | Mise à jour critique: une défaut zéro-jour Crushftp exploité dans des attaques ciblées Critical Update: CrushFTP Zero-Day Flaw Exploited in Targeted Attacks (lien direct) |
Les utilisateurs du logiciel de transfert de fichiers d'entreprise CRrsUfTP sont & nbsp; être & nbsp; exhorté & nbsp; à mettre à jour vers la dernière version & nbsp; après la découverte de & nbsp; un défaut de sécurité qui a été soumis à l'exploitation ciblée dans la nature.
"Les versions Crushftp V11 inférieures à 11.1 ont une vulnérabilité où les utilisateurs peuvent échapper à leurs VFS et télécharger des fichiers système", Crushftp & nbsp; Said & NBSP; dans un avis publié vendredi.
Users of the CrushFTP enterprise file transfer software are being urged to update to the latest version following the discovery of a security flaw that has come under targeted exploitation in the wild. "CrushFTP v11 versions below 11.1 have a vulnerability where users can escape their VFS and download system files," CrushFTP said in an advisory released Friday. |
Vulnerability Threat | ★★★ | ||
| 2024-04-20 09:09:57 | Alertes de vulnérabilité de vigilance - FreeGlut: fuite de mémoire via glutaddsubmenu (), analysé le 20/02/2024 Vigilance Vulnerability Alerts - freeglut: memory leak via glutAddSubMenu(), analyzed on 20/02/2024 (lien direct) |
Un attaquant peut créer une fuite de mémoire de FreeGlut, via glutaddsubMenu (), afin de déclencher un déni de service.
-
vulnérabilité de sécurité
An attacker can create a memory leak of freeglut, via glutAddSubMenu(), in order to trigger a denial of service. - Security Vulnerability |
Vulnerability | ★★ | ||
| 2024-04-19 20:15:33 | FBI: Akira Ransomware Group a fait 42 millions de dollars sur plus de 250 orgs FBI: Akira Ransomware Group Made $42 Million From 250+ Orgs (lien direct) |
The Akira ransomware group has breached the networks of over 250 organizations and claimed approximately $42 million (USD) in ransomware proceeds, according to a recent joint cybersecurity advisory issued by the United States Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), Europol\'s European Cybercrime Centre (EC3), and the Netherlands\' National Cyber Security Centre (NCSC-NL). According to FBI investigations, Akira ransomware has targeted a wide range of businesses and critical infrastructure entities across North America, Europe, and Australia since March 2023. While the ransomware initially targeted Windows systems, the FBI recently found Akira\'s Linux variant targeting VMware ESXi virtual machines that are used widely across many large businesses and organizations. ? #StopRansomare: Review our ? #cybersecurity advisory, outlining known #AkiraRansomware #TTPs & #IOCs, developed with @FBI, @EC3Europol, & @NCSC_NL to reduce the exploitation of businesses and critical infrastructure. https://t.co/2VBMKhoAXK pic.twitter.com/Nn0fEK4HRw — CISA Cyber (@CISACyber) April 18, 2024 “Early versions of the Akira ransomware variant were written in C++ and encrypted files with a .akira extension; however, beginning in August 2023, some Akira attacks began deploying Megazord, using Rust-based code which encrypts files with a .powerranges extension. Akira threat actors have continued to use both Megazord and Akira, including Akira_v2 (identified by trusted third party investigations) interchangeably,” the joint cybersecurity advisory reads. The FBI and cybersecurity researchers have observed Akira threat actors obtaining initial access to organizations through a virtual private network (VPN) service without multifactor authentication (MFA) configured, mostly using known Cisco vulnerabilities CVE-2020-3259 and CVE-2023-20269. Additional methods of initial access include the use of external-facing services such as Remote Desktop Protocol (RDP), spear phishing attacks, and credential abuse. Once initial access is obtained, Akira threat actors attempt to exploit the functions of domain controllers by creating new domain accounts to establish persis | Ransomware Vulnerability Threat Studies | ★★★ | ||
| 2024-04-19 19:17:22 | Mitre a été violée par des vulnérabilités Ivanti Zero-Day MITRE was breached through Ivanti zero-day vulnerabilities (lien direct) |
The Akira ransomware group has breached the networks of over 250 organizations and claimed approximately $42 million (USD) in ransomware proceeds, according to a recent joint cybersecurity advisory issued by the United States Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), Europol\'s European Cybercrime Centre (EC3), and the Netherlands\' National Cyber Security Centre (NCSC-NL). According to FBI investigations, Akira ransomware has targeted a wide range of businesses and critical infrastructure entities across North America, Europe, and Australia since March 2023. While the ransomware initially targeted Windows systems, the FBI recently found Akira\'s Linux variant targeting VMware ESXi virtual machines that are used widely across many large businesses and organizations. ? #StopRansomare: Review our ? #cybersecurity advisory, outlining known #AkiraRansomware #TTPs & #IOCs, developed with @FBI, @EC3Europol, & @NCSC_NL to reduce the exploitation of businesses and critical infrastructure. https://t.co/2VBMKhoAXK pic.twitter.com/Nn0fEK4HRw — CISA Cyber (@CISACyber) April 18, 2024 “Early versions of the Akira ransomware variant were written in C++ and encrypted files with a .akira extension; however, beginning in August 2023, some Akira attacks began deploying Megazord, using Rust-based code which encrypts files with a .powerranges extension. Akira threat actors have continued to use both Megazord and Akira, including Akira_v2 (identified by trusted third party investigations) interchangeably,” the joint cybersecurity advisory reads. The FBI and cybersecurity researchers have observed Akira threat actors obtaining initial access to organizations through a virtual private network (VPN) service without multifactor authentication (MFA) configured, mostly using known Cisco vulnerabilities CVE-2020-3259 and CVE-2023-20269. Additional methods of initial access include the use of external-facing services such as Remote Desktop Protocol (RDP), spear phishing attacks, and credential abuse. Once initial access is obtained, Akira threat actors attempt to exploit the functions of domain controllers by creating new domain accounts to establish persis | Vulnerability Threat | ★★★ | ||
| 2024-04-19 08:59:00 | Les vulnérabilités d'Openmetadata exploitées pour abuser des grappes de Kubernetes pour la cryptomiminage OpenMetadata Vulnerabilities Exploited to Abuse Kubernetes Clusters for Cryptomining (lien direct) |
> Microsoft avertit que plusieurs vulnérabilités Openmetadata sont exploitées pour déployer des logiciels malveillants de cryptomine dans les environnements Kubernetes.
>Microsoft warns that several OpenMetadata vulnerabilities are being exploited to deploy cryptomining malware to Kubernetes environments. |
Malware Vulnerability | ★★ | ||
| 2024-04-18 20:23:46 | GPT-4 peut exploiter la plupart des vulnes simplement en lisant les avis de menace GPT-4 Can Exploit Most Vulns Just by Reading Threat Advisories (lien direct) |
La technologie d'IA existante peut permettre aux pirates d'automatiser les exploits pour les vulnérabilités publiques en minutes à plat.Très bientôt, le correctif diligent ne sera plus facultatif.
Existing AI technology can allow hackers to automate exploits for public vulnerabilities in minutes flat. Very soon, diligent patching will no longer be optional. |
Vulnerability Threat Patching | ★★ | ||
| 2024-04-18 15:11:02 | UE Cyber Agency ne créera pas de base de données de vulnérabilité active, explique le chef de la cybersécurité EU cyber agency will not create active vulnerability database, says chief cybersecurity officer (lien direct) |
La technologie d'IA existante peut permettre aux pirates d'automatiser les exploits pour les vulnérabilités publiques en minutes à plat.Très bientôt, le correctif diligent ne sera plus facultatif.
Existing AI technology can allow hackers to automate exploits for public vulnerabilities in minutes flat. Very soon, diligent patching will no longer be optional. |
Vulnerability | ★★★ | ||
| 2024-04-18 11:24:00 | Les pirates exploitent Openmetadata Flaws to Mine Crypto sur Kubernetes Hackers Exploit OpenMetadata Flaws to Mine Crypto on Kubernetes (lien direct) |
Les acteurs de la menace exploitent activement les vulnérabilités critiques à Openmetadata pour obtenir un accès non autorisé aux charges de travail de Kubernetes et les exploiter pour l'activité minière des crypto-monnaies.
C'est selon l'équipe Microsoft Threat Intelligence, qui & nbsp; a dit & nbsp; les défauts sont armées depuis le début d'avril 2024.
OpenMetadata est un & nbsp; plateforme open source & nbsp; qui fonctionne comme un
Threat actors are actively exploiting critical vulnerabilities in OpenMetadata to gain unauthorized access to Kubernetes workloads and leverage them for cryptocurrency mining activity. That\'s according to the Microsoft Threat Intelligence team, which said the flaws have been weaponized since the start of April 2024. OpenMetadata is an open-source platform that operates as a |
Vulnerability Threat | ★★ | ||
| 2024-04-18 11:06:45 | Autres tentatives pour reprendre les projets open source Other Attempts to Take Over Open Source Projects (lien direct) |
Après la découverte de XZ Utils, les gens ont été Examen .Ne surprenant personne, l'incident n'est pas unique:
Le Conseil OpenJS Foundation Cross Project a reçu une série suspecte d'e-mails avec des messages similaires, portant différents noms et chevauchant des e-mails associés à GitHub.Ces e-mails ont imploré OpenJS pour prendre des mesures pour mettre à jour l'un de ses projets JavaScript populaires à & # 8220; Addressez toutes les vulnérabilités critiques, & # 8221;Pourtant, aucune spécification n'a cité.L'auteur de courriels voulait que OpenJS les désigne en tant que nouveau responsable du projet malgré peu de participation préalable.Cette approche ressemble fortement à la manière dont & # 8220; Jia Tan & # 8221;se positionné dans la porte dérobée XZ / Liblzma ...
After the XZ Utils discovery, people have been examining other open-source projects. Surprising no one, the incident is not unique: The OpenJS Foundation Cross Project Council received a suspicious series of emails with similar messages, bearing different names and overlapping GitHub-associated emails. These emails implored OpenJS to take action to update one of its popular JavaScript projects to “address any critical vulnerabilities,” yet cited no specifics. The email author(s) wanted OpenJS to designate them as a new maintainer of the project despite having little prior involvement. This approach bears strong resemblance to the manner in which “Jia Tan” positioned themselves in the XZ/liblzma backdoor... |
Vulnerability | ★★ | ||
| 2024-04-18 09:53:59 | The Windows Registry Adventure # 1: Résultats d'introduction et de recherche The Windows Registry Adventure #1: Introduction and research results (lien direct) |
Posted by Mateusz Jurczyk, Google Project Zero In the 20-month period between May 2022 and December 2023, I thoroughly audited the Windows Registry in search of local privilege escalation bugs. It all started unexpectedly: I was in the process of developing a coverage-based Windows kernel fuzzer based on the Bochs x86 emulator (one of my favorite tools for security research: see Bochspwn, Bochspwn Reloaded, and my earlier font fuzzing infrastructure), and needed some binary formats to test it on. My first pick were PE files: they are very popular in the Windows environment, which makes it easy to create an initial corpus of input samples, and a basic fuzzing harness is equally easy to develop with just a single GetFileVersionInfoSizeW API call. The test was successful: even though I had previously fuzzed PE files in 2019, the new element of code coverage guidance allowed me to discover a completely new bug: issue #2281. For my next target, I chose the Windows registry. That\'s because arbitrary registry hives can be loaded from disk without any special privileges via the RegLoadAppKey API (since Windows Vista). The hives use a binary format and are fully parsed in the kernel, making them a noteworthy local attack surface. Furthermore, I was also somewhat familiar with basic harnessing of the registry, having fuzzed it in 2016 together with James Forshaw. Once again, the code coverage support proved useful, leading to the discovery of issue #2299. But when I started to perform a root cause analysis of the bug, I realized that: The hive binary format is not very well suited for trivial bitflipping-style fuzzing, because it is structurally simple, and random mutations are much more likely to render (parts of) the hive unusable than to trigger any interesting memory safety violations.On the other hand, the registry has many properties that make it an attractive attack | Tool Vulnerability Threat Studies | ★★★★ | ||
| 2024-04-18 06:00:36 | FAQ à partir de l'état du rapport Phish 2024, partie 2: comportements et attitudes des utilisateurs envers la sécurité FAQs from the 2024 State of the Phish Report, Part 2: User Behaviors and Attitudes Toward Security (lien direct) |
Welcome to the second installment of our two-part blog series where we answer the most frequently asked questions about the 2024 State of the Phish Report. In our previous article, we answered questions related to the threat landscape findings. Here, we answer questions related to user behaviors and attitudes, as well as how to grow your security awareness program. One of the most interesting findings that came out of the 2024 State of the Phish report was the fact that 71% of users admitted to engaging in a risky action and 96% of those users understood the risk. This suggests that people are not acting out of ignorance. Despite knowing that their actions could compromise themselves or their organization, people chose to proceed anyway. This information is crucial for the growth of any security awareness program. It enables organizations to tailor their efforts. By observing and analyzing how users interact with security policies, organizations can identify knowledge gaps and areas of resistance. When you engage users in this manner, you not only educate them but also transform them into active participants in protecting your organization. 96% of users who took a risky action knew that it was risky. (Source: 2024 State of the Phish from Proofpoint.) Our findings inspired hundreds of questions from audiences across the world. What follows are some of the questions that repeatedly came up. Frequently asked questions What are some ways to get users to care about security and get engaged? Two-way communication is key. Take a moment to explain to your employees why you\'re running a behavior change program, what the expectations are and what projected outcomes you foresee. Make it personal. Let people know that cybersecurity isn\'t just a work skill but a portable skill they can take home to help themselves and their families be safer in life. Keep your employees up to speed on what\'s happening in the current threat landscape. For example: What types of threats does your business see? Which departments are under attack? How does the security team handle these incidents? What can people do to defend against emerging threats that target them? Research for the 2024 State of the Phish report found that 87% of end users are more motivated to prioritize security when they see increased engagement from leadership or the security team. In short: You need to open up the lines of communication, listen to your employees and incorporate their feedback, and establish a security champion network to help facilitate communication more effectively. Any ideas on why the click rate for phishing simulations went up for many industries this year? There may be a few possible reasons. For starters, there has been an increase in the number of phishing tests sent. Our customers sent out a total of 183 million simulated phishing tests over a 12-month period, up from 135 million in the previous 12-month period. This 36% increase suggests that our customers may have either tested their users more frequently or tested more users in general. Also, some users might be new to these tests, resulting in a higher click rate. Regardless, if you are conducting a phishing campaign throughout the year, the click rates of phishing tests are expected to go up and down because you want to challenge your employees with new attack tactics they have not seen. Otherwise, the perception would be, “Oh, this is the face of a phish,” if you keep phishing your users with the same test. At Proofpoint, we use machine learning-driven leveled phishing to provide a more reliable way to accurately assess user vulnerability. This unique feature allows security teams to examine the predictability of a phishing template and obtain more consistent outcomes while improving users\' resilience against human-activated threats. People need to understand how attackers exploit human vulnerability. Phishing tests should reflect reality and be informed by real-world threats. They are designed to help people spot and re | Tool Vulnerability Threat | ★★ | ||
| 2024-04-17 18:07:07 | Ivanti verse des correctifs pour plus de 2 douzaines de vulnérabilités Ivanti Releases Fixes for More Than 2 Dozen Vulnerabilities (lien direct) |
Les utilisateurs devront télécharger la dernière version de l'avalanche d'Ivanti \\ pour appliquer des correctifs pour tous les bogues.
Users will need to download the latest version of Ivanti\'s Avalanche to apply fixes for all of the bugs. |
Vulnerability | ★★ | ||
| 2024-04-17 16:27:00 | Flaw atlassien critique exploité pour déployer la variante Linux de Cerber Ransomware Critical Atlassian Flaw Exploited to Deploy Linux Variant of Cerber Ransomware (lien direct) |
Les acteurs de la menace exploitent les serveurs Atlassian non corrigés pour déployer une variante Linux du ransomware Cerber (AKA C3RB3R).
Les attaques Levier et NBSP; CVE-2023-22518 & NBSP; (Score CVSS: 9.1), une vulnérabilité de sécurité critique ayant un impact sur le centre de données de Confluence Atlassian qui permet un attaquant non authentifié pour réinitialiser la confluence et créer un compte administrateur.
Armé de cet accès, un
Threat actors are exploiting unpatched Atlassian servers to deploy a Linux variant of Cerber (aka C3RB3R) ransomware. The attacks leverage CVE-2023-22518 (CVSS score: 9.1), a critical security vulnerability impacting the Atlassian Confluence Data Center and Server that allows an unauthenticated attacker to reset Confluence and create an administrator account. Armed with this access, a |
Ransomware Vulnerability Threat | ★★ |
To see everything:
Our RSS (filtrered)
