What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-08-17 19:56:00 | New Labrat Campaign exploite Gitlab Flaw for Cryptojacking and Proxyjacking Activities New LABRAT Campaign Exploits GitLab Flaw for Cryptojacking and Proxyjacking Activities (lien direct) |
Une nouvelle opération à motivation financière surnommée Labrat a été observée en armement une faille critique désormais réglée à Gitlab dans le cadre d'une campagne de cryptojacking et de proxyjacking.
"L'attaquant a utilisé des outils basés sur une signature non détectés, des outils de logiciels malveillants multiplateformes sophistiqués et furtifs, des outils de logiciels de commande et de contrôle (C2) qui ont contourné les pare-feu et les rootkits basés sur le noyau pour cacher leur présence", Sysdig
A new, financially motivated operation dubbed LABRAT has been observed weaponizing a now-patched critical flaw in GitLab as part of a cryptojacking and proxyjacking campaign. "The attacker utilized undetected signature-based tools, sophisticated and stealthy cross-platform malware, command-and-control (C2) tools which bypassed firewalls, and kernel-based rootkits to hide their presence," Sysdig |
Tool | ★★ | ||
| 2023-08-17 18:15:17 | CVE-2023-40165 (lien direct) | Rubygems.org est le service d'hébergement de Gem (Library) de Ruby Community \\.La validation des entrées insuffisante a permis aux acteurs malveillants de remplacer toute version de gemm téléchargée qui avait une plate-forme, un numéro de version ou un nom de gemm correspondant `/ - \ d /`, en remplaçant définitivement le téléchargement légitime dans le seau de stockage canonique et en déclenchant une purge CDN immédiatede sorte que le joyau malveillant soit servi immédiatement.Les mainteneurs ont vérifié tous les gemmes correspondant au modèle `/ - \ d /` et peuvent confirmer qu'aucun `.gem est inattendu.En conséquence, nous pensons que cette vulnérabilité n'a pas été exploitée.Le moyen le plus simple de s'assurer que les applications d'un utilisateur n'ont pas été exploitées par cette vulnérabilité est de vérifier que tous vos .Gems téléchargés ont une somme de contrôle qui correspond à la somme de contrôle enregistrée dans la base de données RubyGems.org.Le contributeur de Rubygems Maciej Mensfeld a écrit un outil pour vérifier automatiquement que tous les fichiers .gem téléchargés correspondent aux sommes de contrôle enregistrées dans la base de données Rubygems.org.Vous pouvez l'utiliser en fonctionnant: «Bundle Ajouter Bundler-Integrity» suivi par `Bundle Exec Bundler-Integrity».Ni cet outil ni quoi que ce soit d'autre ne peut prouver que vous n'étiez pas exploité, mais le peut aider votre enquête en comparant rapidement les sommes de contrôle de RubyGems API avec la somme de contrôle des fichiers sur votre disque.Le problème a été corrigé avec une validation d'entrée améliorée et les modifications sont en direct.Aucune action n'est requise de la partie de l'utilisateur.Il est conseillé aux utilisateurs de valider leurs joyaux locaux.
rubygems.org is the Ruby community\'s primary gem (library) hosting service. Insufficient input validation allowed malicious actors to replace any uploaded gem version that had a platform, version number, or gem name matching `/-\d/`, permanently replacing the legitimate upload in the canonical gem storage bucket, and triggering an immediate CDN purge so that the malicious gem would be served immediately. The maintainers have checked all gems matching the `/-\d/` pattern and can confirm that no unexpected `.gem`s were found. As a result, we believe this vulnerability was _not_ exploited. The easiest way to ensure that a user\'s applications were not exploited by this vulnerability is to check that all of your downloaded .gems have a checksum that matches the checksum recorded in the RubyGems.org database. RubyGems contributor Maciej Mensfeld wrote a tool to automatically check that all downloaded .gem files match the checksums recorded in the RubyGems.org database. You can use it by running: `bundle add bundler-integrity` followed by `bundle exec bundler-integrity`. Neither this tool nor anything else can prove you were not exploited, but the can assist your investigation by quickly comparing RubyGems API-provided checksums with the checksums of files on your disk. The issue has been patched with improved input validation and the changes are live. No action is required on the part of the user. Users are advised to validate their local gems. |
Tool Vulnerability | |||
| 2023-08-17 18:05:31 | Ce que vous devez savoir sur Cisco Unified Communications Manager SQL Injection Vulnérabilité (CVE-2023-20211) What You Need to Know About Cisco Unified Communications Manager SQL Injection Vulnerability (CVE-2023-20211) (lien direct) |
Dans le monde connecté d'aujourd'hui, des outils efficaces comme le Cisco Unified Communications Manager (Unified CM) et ...
In today’s connected world, efficient tools like the Cisco Unified Communications Manager (Unified CM) and... |
Tool Vulnerability | ★★★ | ||
| 2023-08-17 15:33:00 | \\ 'jouer \\' groupe de ransomware ciblant les MSP dans le monde entier dans une nouvelle campagne \\'Play\\' Ransomware Group Targeting MSPs Worldwide in New Campaign (lien direct) |
Les attaquants utilisent des outils de surveillance et de gestion à distance chez MSPS pour obtenir un accès sans entrave aux réseaux cibles.
Attackers use remote monitoring and management tools at MSPs to gain unfettered access to target networks. |
Ransomware Tool | ★★ | ||
| 2023-08-17 13:01:00 | Amélioration de la sécurité du code avec une AI générative: Utilisation de la correction de Veracode pour sécuriser le code généré par Chatgpt Enhancing Code Security with Generative AI: Using Veracode Fix to Secure Code Generated by ChatGPT (lien direct) |
L'intelligence artificielle (IA) et le codage compagnon peuvent aider les développeurs à écrire des logiciels plus rapidement que jamais.Cependant, alors que les entreprises cherchent à adopter un codage compagnon propulsé par l'IA, elles doivent être conscientes des forces et des limites des différentes approches & # 8211;en particulier en ce qui concerne la sécurité du code.
Regardez cette vidéo de 4 minutes pour voir un développeur générer du code non sécurisé avec ChatGpt, trouvez la faille avec une analyse statique et sécurisez-la avec Veracode Fix pour développer rapidement une fonction sans écrire de code.
La vidéo ci-dessus expose les nuances de la sécurité générative du code AI.Alors que les outils de codage compagnon généraliste comme ChatGpt Excel dans la création de code fonctionnel, la qualité et la sécurité du code sont souvent insuffisantes.Des solutions spécialisées comme le correctif Veracode construit pour exceller dans le code d'insécurité de remédiation apportent une compétence de sécurité vitale à une IA générative.En utilisant des outils généralistes et spécialisés en collaboration, les organisations peuvent permettre à leurs équipes d'accélérer le développement de logiciels qui rencontre fonctionnellement et…
Artificial Intelligence (AI) and companion coding can help developers write software faster than ever. However, as companies look to adopt AI-powered companion coding, they must be aware of the strengths and limitations of different approaches – especially regarding code security. Watch this 4-minute video to see a developer generate insecure code with ChatGPT, find the flaw with static analysis, and secure it with Veracode Fix to quickly develop a function without writing any code. The video above exposes the nuances of generative AI code security. While generalist companion coding tools like ChatGPT excel at creating functional code, the quality and security of the code often falls short. Specialized solutions like Veracode Fix built to excel at remediation insecure code bring a vital security skillset to generative AI. By using generalist and specialist AI tools in collaboration, organizations can empower their teams to accelerate software development that meets functional and… |
Tool | ChatGPT ChatGPT | ★★ | |
| 2023-08-17 08:01:00 | Cuba Ransomware déploie de nouveaux outils: BlackBerry découvre des cibles, y compris le secteur des infrastructures critiques aux États-Unis et l'intégrateur informatique en Amérique latine Cuba Ransomware Deploys New Tools: BlackBerry Discovers Targets Including Critical Infrastructure Sector in the U.S. and IT Integrator in Latin America (lien direct) |
BlackBerry a découvert et documenté de nouveaux outils utilisés par le Cuba Ransomware Threat Group.La bonne nouvelle est que Blackberry protège contre les ransomwares de Cuba.
BlackBerry has discovered and documented new tools used by the Cuba ransomware threat group. The good news is that BlackBerry protects against Cuba ransomware. |
Ransomware Tool Threat | ★★ | ||
| 2023-08-16 21:14:00 | CISA, les experts mettent en garde contre les vulnérabilités Citrix exploitées par des pirates CISA, experts warn of Citrix vulnerabilities being exploited by hackers (lien direct) |
 Des alarmes ont été soulevées sur plusieurs vulnérabilités affectant les produits de Citrix qui sont largement exploités par une variété d'acteurs de menace.Mercredi, l'Agence américaine de sécurité de la cybersécurité et de l'infrastructure a déclaré qu'une vulnérabilité affectant l'outil de collaboration de contenu Citrix avait été exploitée et a obligé aux agences civiles fédérales américaines [corriger le problème d'ici septembre
Des alarmes ont été soulevées sur plusieurs vulnérabilités affectant les produits de Citrix qui sont largement exploités par une variété d'acteurs de menace.Mercredi, l'Agence américaine de sécurité de la cybersécurité et de l'infrastructure a déclaré qu'une vulnérabilité affectant l'outil de collaboration de contenu Citrix avait été exploitée et a obligé aux agences civiles fédérales américaines [corriger le problème d'ici septembre
 Alarms have been raised about several vulnerabilities affecting products from Citrix that are being exploited widely by a variety of threat actors. On Wednesday, the U.S. Cybersecurity and Infrastructure Security Agency said a vulnerability affecting the Citrix Content Collaboration tool had been exploited and mandated that U.S. federal civilian agencies [patch the issue by September
Alarms have been raised about several vulnerabilities affecting products from Citrix that are being exploited widely by a variety of threat actors. On Wednesday, the U.S. Cybersecurity and Infrastructure Security Agency said a vulnerability affecting the Citrix Content Collaboration tool had been exploited and mandated that U.S. federal civilian agencies [patch the issue by September |
Tool Vulnerability Threat | ★★ | ||
| 2023-08-16 19:03:00 | CISA publie un plan pour les outils de surveillance à distance après l'exploitation des ransomwares à l'État-nation CISA publishes plan for remote monitoring tools after nation-state, ransomware exploitation (lien direct) |
 Une collaboration entre l'agence de défense de Cybersecurity des États-Unis et les sociétés privées a publié mercredi son premier plan pour résoudre les problèmes de sécurité avec les outils de surveillance et de gestion à distance (RMM).Le logiciel RMM est généralement utilisé par les services informatiques de la plupart des grandes organisations du monde
Une collaboration entre l'agence de défense de Cybersecurity des États-Unis et les sociétés privées a publié mercredi son premier plan pour résoudre les problèmes de sécurité avec les outils de surveillance et de gestion à distance (RMM).Le logiciel RMM est généralement utilisé par les services informatiques de la plupart des grandes organisations du monde
 A collaboration between the U.S.\'s cybersecurity defense agency and private companies published its first plan to address security issues with remote monitoring and management (RMM) tools on Wednesday. RMM software is typically used by the IT departments of most large organizations around the world as a way to get remote access to a computer to
A collaboration between the U.S.\'s cybersecurity defense agency and private companies published its first plan to address security issues with remote monitoring and management (RMM) tools on Wednesday. RMM software is typically used by the IT departments of most large organizations around the world as a way to get remote access to a computer to |
Ransomware Tool | ★★ | ||
| 2023-08-16 18:00:17 | Ransomware attaque la montée en flèche alors que l'IA génératrice devient un outil de marchandise dans l'arsenal de l'acteur de menace Ransomware Attacks Surge as Generative AI Becomes a Commodity Tool in the Threat Actor\\'s Arsenal (lien direct) |

|
Ransomware Tool Threat | ★★ | ||
| 2023-08-16 16:29:00 | Google présente la première clé de sécurité FIDO2 résiliente quantique Google Introduces First Quantum Resilient FIDO2 Security Key (lien direct) |
Google a annoncé mardi la première mise en œuvre de la clé de sécurité FIDO2 résiliente quantique dans le cadre de son initiative OpenK Security Keys.
"Cette implémentation optimisée sur le matériel open source utilise un nouveau schéma de signature hybride ECC / Dilithium qui profite de la sécurité de l'ECC contre les attaques standard et la résilience de Dilithium \\ contre les attaques quantiques", Elie Bursztein et Fabian Kaczmarczyck
Google on Tuesday announced the first quantum resilient FIDO2 security key implementation as part of its OpenSK security keys initiative. "This open-source hardware optimized implementation uses a novel ECC/Dilithium hybrid signature schema that benefits from the security of ECC against standard attacks and Dilithium\'s resilience against quantum attacks," Elie Bursztein and Fabian Kaczmarczyck |
Tool General Information | ★★★ | ||
| 2023-08-16 16:15:11 | CVE-2023-39250 (lien direct) | Les outils d'intégration de stockage Dell pour VMware (DSITV) 06.01.00.016 contiennent une vulnérabilité de divulgation d'informations.Un utilisateur malveillant local à faible privilégie pourrait potentiellement exploiter cette vulnérabilité pour récupérer une clé de chiffrement qui pourrait aider à d'autres attaques.
Dell Storage Integration Tools for VMware (DSITV) 06.01.00.016 contain an information disclosure vulnerability. A local low-privileged malicious user could potentially exploit this vulnerability to retrieve an encryption key that could aid in further attacks. |
Tool Vulnerability | |||
| 2023-08-16 11:00:00 | Proxynation: le lien sombre entre les applications proxy et les logiciels malveillants ProxyNation: The dark nexus between proxy apps and malware (lien direct) |
Executive summary
AT&T Alien Labs researchers recently discovered a massive campaign of threats delivering a proxy server application to Windows machines. A company is charging for proxy service on traffic that goes through those machines. This is a continuation of research described in our blog on Mac systems turned into proxy exit nodes by AdLoad.
In this research, Alien Labs identified a company that offers proxy services, wherein proxy requests are rerouted through compromised systems that have been transformed into residential exit nodes due to malware infiltration. Although the proxy website claims that its exit nodes come only from users who have been informed and agreed to the use of their device, Alien Labs has evidence that malware writers are installing the proxy silently in infected systems. In addition, as the proxy application is signed, it has no anti-virus detection, going under the radar of security companies.
In this follow up article we explore the dramatic rise in Windows malware delivering the same payload to create a 400,000 proxy botnet.
Key takeaways:
In just one week AT&T Alien Labs researchers observed more than a thousand new malware samples in the wild delivering the proxy application.
According to the proxy website, there are more than 400,000 proxy exit nodes, and it is not clear how many of them were installed by malware.
The application is silently installed by malware on infected machines without user knowledge and interaction.
The proxy application is signed and has zero anti-virus detection.
The proxy is written in Go programming language and is spread by malware both on Windows and macOS.
Analysis
In the constantly evolving landscape of cyber threats, malicious actors continuously find new and ingenious ways to exploit technology for their own gain. Recently Alien Labs has observed an emerging trend where malware creators are utilizing proxy applications as their tool of choice. Different malware strains are delivering the proxy - relying on users looking for interesting things, like cracked software and games.
The proxy is written in the Go programming language, giving it the flexibility to be compiled into binaries compatible with various operating systems, including macOS and Windows. Despite the fact that the binaries originated from the same source code, macOS samples are detected by numerous security checks while the Windows proxy application skirts around these measures unseen. This lack of detection is most likely due to the application being signed. (Figure 1)
 Figure 1. As on Virus Total: Proxy application – zero detections.
After being executed on a compromised system, the malware proceeds to quietly download and install the proxy application. This covert process takes place without requiring any user interaction and often occurs alongside the installation of additional malware or adware elements. The proxy application and most of the malware delivering it are packed using Inno Setup, a free and popular Windows installer.
Figure 1. As on Virus Total: Proxy application – zero detections.
After being executed on a compromised system, the malware proceeds to quietly download and install the proxy application. This covert process takes place without requiring any user interaction and often occurs alongside the installation of additional malware or adware elements. The proxy application and most of the malware delivering it are packed using Inno Setup, a free and popular Windows installer.
 Figure 2. As observed by Alien Labs: Malware embedded script to install the proxy silently.
As shown in the figure 2 above, the malware uses specific Inno
Figure 2. As observed by Alien Labs: Malware embedded script to install the proxy silently.
As shown in the figure 2 above, the malware uses specific Inno |
Malware Tool Threat Prediction | ★★ | ||
| 2023-08-16 10:00:00 | Histoires du SOC - dévoiler les tactiques furtives du malware aukill Stories from the SOC - Unveiling the stealthy tactics of Aukill malware (lien direct) |
Executive summary
On April 21st, 2023, AT&T Managed Extended Detection and Response (MXDR) investigated an attempted ransomware attack on one of our clients, a home improvement business. The investigation revealed the attacker used AuKill malware on the client\'s print server to disable the server\'s installed EDR solution, SentinelOne, by brute forcing an administrator account and downgrading a driver to a vulnerable version.
AuKill, first identified by Sophos X-Ops researchers in June 2021, is a sophisticated malware designed to target and neutralize specific EDR solutions, including SentinelOne and Sophos. Distributed as a dropper, AuKill drops a vulnerable driver named PROCEXP.SYS (from Process Explorer release version 16.32) into the system\'s C:\Windows\System32\drivers folder. This malware has been observed in the wild, utilized by ransomware groups to bypass endpoint security measures and effectively spread ransomware variants such as Medusa Locker and Lockbit on vulnerable systems.
In this case, SentinelOne managed to isolate most of the malicious files before being disabled, preventing a full-scale ransomware incident. As a result, AT&T MXDR found no evidence of data exfiltration or encryption. Despite this, the client opted to rebuild the print server as a precautionary measure. This study provides an in-depth analysis of the attack and offers recommendations to mitigate the risk of future attacks.
Investigating the first phase of the attack
Initial intrusion
The targeted asset was the print server, which we found unusual. However, upon further investigation we concluded the attacker misidentified the asset as a Domain Controller (DC), as it had recently been repurposed from a DC to a print server. The attacker needed both local administrator credentials and kernel-level access to successfully run AuKill and disable SentinelOne on the asset. To gain those local administrator credentials, the attacker successfully brute-forced an administrator account. Shortly after the compromise, this account was observed making unauthorized registry changes.

 Establishing a beachhead
After compromising the local administrator account, the attackers used the "\Users\Administrator\Music\aSentinel" folder as a staging area for subsequent phases of their attack. All AuKill-related binaries and scripts were executed from this path, with the innocuous "Music" folder name helping to conceal their malicious activities.
Establishing a beachhead
After compromising the local administrator account, the attackers used the "\Users\Administrator\Music\aSentinel" folder as a staging area for subsequent phases of their attack. All AuKill-related binaries and scripts were executed from this path, with the innocuous "Music" folder name helping to conceal their malicious activities.
 AuKill malware has been found to operate using two Windows services named "aSentinel.exe" and "aSentinelX.exe" in its SentinelOne variant. In other variants, it targets different EDRs, such as Sophos, by utilizing corresponding Windows services like "aSophos.exe" and "aSophosX.exe".
AuKill malware has been found to operate using two Windows services named "aSentinel.exe" and "aSentinelX.exe" in its SentinelOne variant. In other variants, it targets different EDRs, such as Sophos, by utilizing corresponding Windows services like "aSophos.exe" and "aSophosX.exe".
 Establishing persistence
We also discovered "aSentinel.exe" running from "C:\Windows\system32", indicating that the attackers attempted to establish a foothold on the compromised server. Malware authors frequently target the system32 folder because it is a trusted location, and security software may not scrutinize files within it as closely as those in other locations. This can help malware bypass security measures and remain hidden. It is likely that the malware was initially placed in the "\Users\Administrator\Music\aSentinel" direct
Establishing persistence
We also discovered "aSentinel.exe" running from "C:\Windows\system32", indicating that the attackers attempted to establish a foothold on the compromised server. Malware authors frequently target the system32 folder because it is a trusted location, and security software may not scrutinize files within it as closely as those in other locations. This can help malware bypass security measures and remain hidden. It is likely that the malware was initially placed in the "\Users\Administrator\Music\aSentinel" direct |
Ransomware Malware Tool Threat Studies | ★★★★ | ||
| 2023-08-15 19:41:00 | Monti Ransomware revient avec de nouvelles variantes Linux et des tactiques d'évasion améliorées Monti Ransomware Returns with New Linux Variant and Enhanced Evasion Tactics (lien direct) |
Les acteurs de la menace derrière le ransomware de Monti ont refait surface après une pause de deux mois avec une nouvelle version Linux de l'encrypteur dans ses attaques ciblant le gouvernement et les secteurs juridiques.
Monti a émergé en juin 2022, des semaines après que le groupe de ransomwares continu a fermé ses opérations, imitant délibérément les tactiques et les outils associés à ce dernier, y compris son code source divulgué.Pas plus.
The threat actors behind the Monti ransomware have resurfaced after a two-month break with a new Linux version of the encryptor in its attacks targeting government and legal sectors. Monti emerged in June 2022, weeks after the Conti ransomware group shut down its operations, deliberately imitating the tactics and tools associated with the latter, including its leaked source code. Not anymore. |
Ransomware Tool Threat | ★★ | ||
| 2023-08-15 13:00:00 | Menace de chasse 101: comment dépasser les attaquants Threat hunting 101: How to outthink attackers (lien direct) |
> La chasse aux menaces implique la recherche de menaces et d'adversaires dans une infrastructure numérique de l'organisation que les outils de sécurité existants ne détectent pas.Il recherche de manière proactive des menaces dans l'environnement en supposant que l'adversaire est en train de compromettre l'environnement ou a compromis l'environnement.Les chasseurs de menaces peuvent avoir des objectifs et des mentalités différents tandis que [& # 8230;]
>Threat hunting involves looking for threats and adversaries in an organization’s digital infrastructure that existing security tools don’t detect. It is proactively looking for threats in the environment by assuming that the adversary is in the process of compromising the environment or has compromised the environment. Threat hunters can have different goals and mindsets while […] |
Tool Threat | ★★ | ||
| 2023-08-15 10:00:00 | Pourquoi la sécurité de l'API est-elle la prochaine grande chose en cybersécurité? Why is API security the next big thing in Cybersecurity? (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. APIs, formally known as application programming interfaces, occupy a significant position in modern software development. They revolutionized how web applications work by facilitating applications, containers, and microservices to exchange data and information smoothly. Developers can link APIs with multiple software or other internal systems that help businesses to interact with their clients and make informed decisions. Despite the countless benefits, hackers can exploit vulnerabilities within the APIs to gain unauthorized access to sensitive data resulting in data breaches, financial losses, and reputational damage. Therefore, businesses need to understand the API security threat landscape and look out for the best ways to mitigate them. The urgent need to enhance API security APIs enable data exchanges among applications and systems and help in the seamless execution of complex tasks. But as the average number of APIs rises, organizations often overlook their vulnerabilities, making them a prime target of hackers. The State of API Security Q1 Report 2023 survey finding concluded that the attacks targeting APIs had increased 400% during the past six months. Security vulnerabilities within APIs compromise critical systems, resulting in unauthorized access and data breaches like Twitter and Optus API breaches. Cybercriminals can exploit the vulnerabilities and launch various attacks like authentication attacks, distributed denial-of-service attacks (DDoS), and malware attacks. API security has emerged as a significant business issue as another report reveals that by 2023, API abuses will be the most frequent attack vector causing data breaches, and also, 50% of data theft incidents will happen due to insecure APIs. As a result, API security has. become a top priority for organizations to safeguard their data, which may cost businesses $75 billion annually. Why does API security still pose a threat in 2023? Securing APIs has always been a daunting task for most organizations, mainly because of the misconfigurations within APIs and the rise in cloud data breaches. As the security landscape evolved, API sprawl became the top reason that posed a threat to API security. API sprawl is the uncontrolled proliferation of APIs across an organization and is a common problem for enterprises with multiple applications, services, and development teams. As more APIs are created, they expanded the attack surface and emerged as an attractive target for hackers. The issue is that the APIs are not always designed by keeping security standards in mind. This leads to a lack of authorization and authentication, exposing sensitive data like personally identifiable information (PII) or other business data. API sprawl | Malware Tool Vulnerability Threat Cloud | Uber | ★★★ | |
| 2023-08-14 21:15:13 | CVE-2023-39950 (lien direct) | EFibootGuard est un simple chargeur de démarrage UEFI avec prise en charge de la commutation en toute sécurité entre les ensembles de partition actuels et mis à jour.La validation et la désinfection insuffisantes ou manquantes de l'entrée des fichiers d'environnement de chargeur de démarrage indigne de la fiducie peuvent provoquer des accidents et probablement également des injections de code dans `BG_SETENV`) ou des programmes en utilisant` LIBEBGENV`.Ceci est déclenché lorsque les composants affectés tentent de modifier un environnement manipulé, en particulier ses variables utilisateur.En outre, `BG_PRINTENV` peut s'écraser sur des accès de lecture non valides ou signaler les résultats non valides.Le binaire EFI EFI Boot Guard \\ est pas affecté par ce problème.EFI Boot Guard Release V0.15 contient des correctifs requis pour désinfecter et valider l'environnement de chargeur de démarrage avant de le traiter dans Userspace.Sa bibliothèque et ses outils doivent être mis à jour, les programmes doivent donc être liés statiquement à celui-ci.Une mise à jour de l'exécutable Bootloader EFI n'est pas requise.La seule façon d'éviter le problème avec une version non corrigée EFI Boot Guard est d'éviter les accès aux variables de l'utilisateur, en particulier des modifications.
efibootguard is a simple UEFI boot loader with support for safely switching between current and updated partition sets. Insufficient or missing validation and sanitization of input from untrustworthy bootloader environment files can cause crashes and probably also code injections into `bg_setenv`) or programs using `libebgenv`. This is triggered when the affected components try to modify a manipulated environment, in particular its user variables. Furthermore, `bg_printenv` may crash over invalid read accesses or report invalid results. Not affected by this issue is EFI Boot Guard\'s bootloader EFI binary. EFI Boot Guard release v0.15 contains required patches to sanitize and validate the bootloader environment prior to processing it in userspace. Its library and tools should be updated, so should programs statically linked against it. An update of the bootloader EFI executable is not required. The only way to prevent the issue with an unpatched EFI Boot Guard version is to avoid accesses to user variables, specifically modifications to them. |
Tool | |||
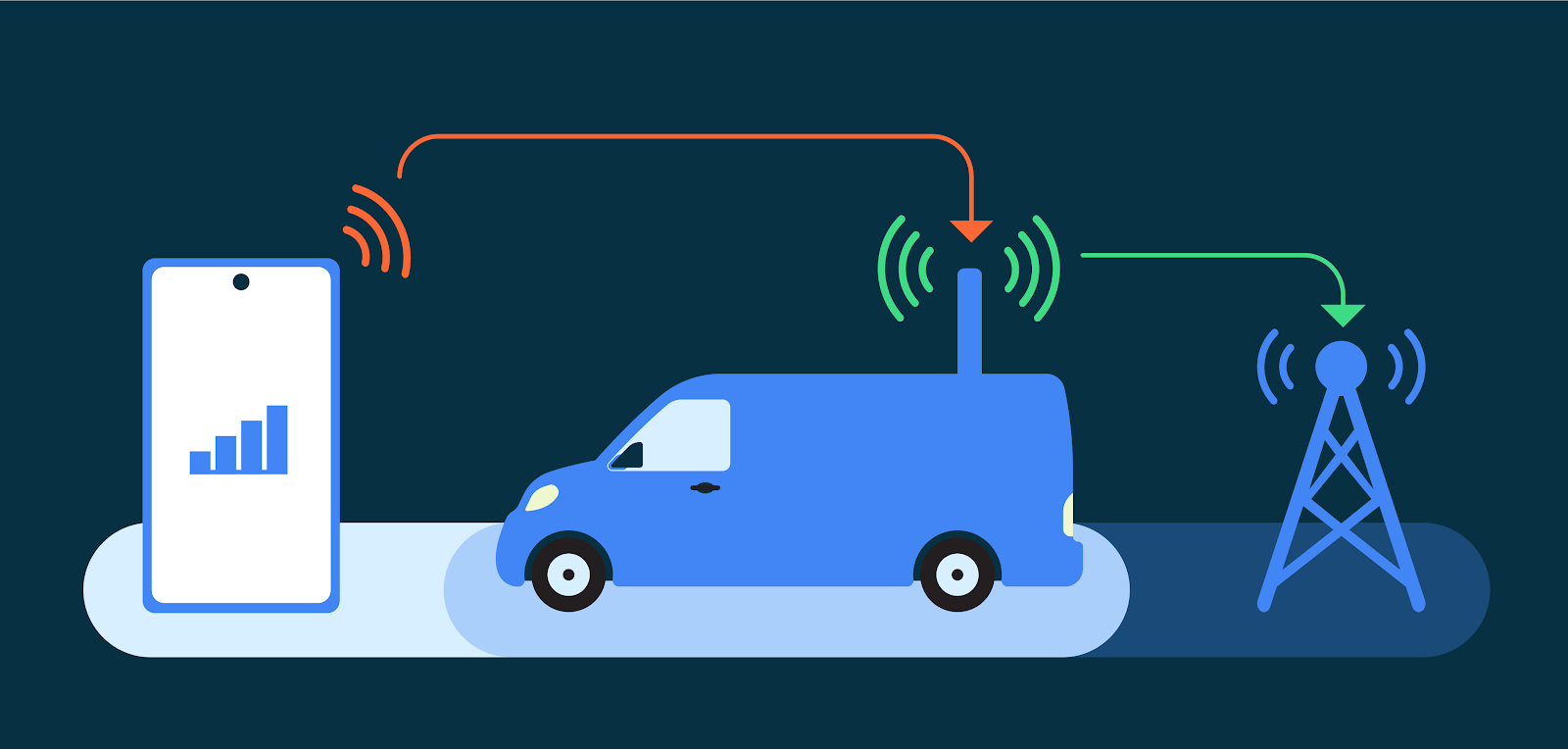
| 2023-08-14 16:39:00 | La plupart des attaques DDOS liées au jeu, aux litiges commerciaux, au FBI et aux procureurs disent Most DDoS attacks tied to gaming, business disputes, FBI and prosecutors say (lien direct) |
 Las Vegas & # 8211; La majorité des attaques de déni de service distribué (DDOS) sont lancées en réponse aux différends sur les affaires ou les jeux, selon des responsables fédéraux enquêtant sur les incidents.Les attaques DDOS se produisent lorsque quelqu'un rend un service ou un outil indisponible en le surchargeant avec des demandes.La grande majorité de la couverture médiatique des attaques DDOS ces dernières années
Las Vegas & # 8211; La majorité des attaques de déni de service distribué (DDOS) sont lancées en réponse aux différends sur les affaires ou les jeux, selon des responsables fédéraux enquêtant sur les incidents.Les attaques DDOS se produisent lorsque quelqu'un rend un service ou un outil indisponible en le surchargeant avec des demandes.La grande majorité de la couverture médiatique des attaques DDOS ces dernières années
 LAS VEGAS – The majority of distributed denial-of-service (DDoS) attacks are launched in response to disputes over business or gaming, according to federal officials investigating the incidents. DDoS attacks occur when someone makes a service or tool unavailable by overloading it with requests. The vast majority of media coverage of DDoS attacks in recent years
LAS VEGAS – The majority of distributed denial-of-service (DDoS) attacks are launched in response to disputes over business or gaming, according to federal officials investigating the incidents. DDoS attacks occur when someone makes a service or tool unavailable by overloading it with requests. The vast majority of media coverage of DDoS attacks in recent years |
Tool | ★★ | ||
| 2023-08-14 15:01:22 | La plate-forme OpenXDR stellar Cyber \\ est désormais disponible sur Oracle Cloud Infrastructure Stellar Cyber\\'s OpenXDR Platform Now Available On Oracle Cloud Infrastructure (lien direct) |
Silicon Valley-based cybersecurity company, Stellar Cyber, announced today that their OpenXDR platform is now accessible to those that use Oracle Cloud Infrastructure (OCI). Customers who have adopted the cloud and seek simpler and smarter solutions to improve their security can now purchase Stellar Cyberr\'s platform via the Oracle Cloud Marketplace, applying Oracle Universal Credits (OUCs) toward the purchase price. How does OpenXDR technology help businesses to better manage the security of their cloud structures, and what does this new partnership mean for Oracle Cloud users? Table Of ContentsCapabilities of Stellar Cyber\'s OpenXDR PlatformNow Available on Oracle Cloud InfrastructureThe Future of Cloud Security Capabilities of Stellar Cyber\'s OpenXDR Platform Stellar Cyber has developed Open Extended Detection and Response (OpenXDR) to facilitate security for both companies facing a large volume of attacks and overwhelmed security professionals. To achieve this, it unites the capabilities of several tools that are essential for security - many of which used to be incompatible. Some of the security solutions that are currently integrated into the platform are NextGen SIEM and Network Detection and Response (NDR). One of the key issues that the company has focused on since its beginning is the large quantity of data that is incoming from versatile incompatible security tools. Today, the issue of having to manage and make sense of large amounts of data is more emphasized than ever before. Why? Because organizations have added more security points to their systems - mostly to protect the new cloud technology that is now a regular part of their network. For instance, the data management solution integrated within OpenXDR can gather insights that are generated from versatile tools the platform supports. To make the reports more accurate and comprehensive, it can correlate the findings gathered from the tools it supports. As a result, the professionals retain visibility of ever-growing attack surfaces and get correct as well as actionable reports on the state of security in real-time. This helps them to react to sophisticated threats early - before they escalate into major security incidents. The tools that can be found under Stellar Cyber\'s umbrella platform are AI and machine-learning-powered. This means that they promptly and automatically mitigate well-known threats, but they continually learn about the company and use the findings to detect anomalies early. Also, they\'re available from a single dashboard since the platform unites the capabilities of versatile previously siloed solutions in one place. For those that already use Oracle Cloud, the new collaborations mean they\'ll now have the capabilities of the OpenXDR platform at their disposal as well. “Stellar Cyber is committed to providing the critical capabilities security teams need to deliver consistent security outcomes-all for a single license and price on a single platform,” said Jim O\'Hara, Chief Revenue Officer at Stellar Cyber. “This simple yet comprehensive model makes it easy for customers to measure how our Open XDR platform dramatically impacts their security ROI.” Now Available on Oracle Cloud Infrastructure Oracle Clou | Tool Threat Cloud | ★★ | ||
| 2023-08-14 14:47:00 | Microsoft révèle des vulnérabilités graves dans le logiciel d'automatisation industrielle de codesys Microsoft reveals severe vulnerabilities in CODESYS industrial automation software (lien direct) |
 Las Vegas & # 8211; Seize nouvelles vulnérabilités ont été découvertes par les chercheurs de Microsoft affectant les outils utilisés dans les opérations industrielles du monde entier.Le chercheur en sécurité Microsoft Vladimir Eliezer Tokarev a décrit les problèmes affectant CodeSys - un logiciel d'automatisation industriel largement utilisé - Pendant une présentation à la sécurité BlackHatConférence la semaine dernière et Microsoft [a également publié le sien
Las Vegas & # 8211; Seize nouvelles vulnérabilités ont été découvertes par les chercheurs de Microsoft affectant les outils utilisés dans les opérations industrielles du monde entier.Le chercheur en sécurité Microsoft Vladimir Eliezer Tokarev a décrit les problèmes affectant CodeSys - un logiciel d'automatisation industriel largement utilisé - Pendant une présentation à la sécurité BlackHatConférence la semaine dernière et Microsoft [a également publié le sien
 LAS VEGAS – Sixteen new vulnerabilities have been uncovered by Microsoft researchers affecting tools used in industrial operations around the world. Microsoft security researcher Vladimir Eliezer Tokarev outlined the issues affecting CODESYS - a widely-used industrial automation software - during a presentation at the BlackHat security conference last week, and Microsoft [also published its own
LAS VEGAS – Sixteen new vulnerabilities have been uncovered by Microsoft researchers affecting tools used in industrial operations around the world. Microsoft security researcher Vladimir Eliezer Tokarev outlined the issues affecting CODESYS - a widely-used industrial automation software - during a presentation at the BlackHat security conference last week, and Microsoft [also published its own |
Tool Vulnerability Industrial Conference | ★★ | ||
| 2023-08-14 14:30:00 | Indicateurs du scanner de compromis pour Citrix ADC Zero-Day (CVE-2023-3519) Indicators of Compromise Scanner for Citrix ADC Zero-Day (CVE-2023-3519) (lien direct) |
mandiant a récemment publié un Article de blog sur le compromis de Citrix NetScaler Delivery Controller (ADC) et des appareils de passerelle NetScaler liés à la vulnérabilité du jour zéro suivi sous le nom de cve-2023-3519 .Le CVE-2023-3519 est une vulnérabilité zéro-jour qui peut permettre l'exécution du code distant, et a été observé exploité dans la nature par un acteur de menace cohérent avec une Chine-Nexus basée sur des capacités connues et une histoire de ciblage des ADC Citrix.Récemment, la preuve de concepts pour exploiter cette vulnérabilité a été publiquement posté .
Aujourd'hui, nous publions un outil pour aider
Mandiant recently published a blog post about the compromise of Citrix NetScaler Application Delivery Controller (ADC) and NetScaler Gateway Appliances related to the zero-day vulnerability tracked as CVE-2023-3519. CVE-2023-3519 is a zero-day vulnerability that can enable remote code execution, and has been observed being exploited in the wild by a threat actor consistent with a China-nexus based on known capabilities and history of targeting Citrix ADCs. Recently, proof-of-concepts to exploit this vulnerability have been publicly posted. Today we are releasing a tool to help |
Tool Vulnerability Threat | ★★★ | ||
| 2023-08-11 20:10:00 | Générateur d'alimentation en Afrique du Sud ciblée avec des logiciels malveillants Droxidat Southern African power generator targeted with DroxiDat malware (lien direct) |
 Les chercheurs ont découvert une cyberattaque suspectée ciblant un générateur d'énergie en Afrique australe avec une nouvelle variante du malware SystemBC.L'attaque a été menée par un groupe de pirates inconnu en mars de cette année, selon un rapport de la société de cybersécurité SecureList .Les pirates ont utilisé un outil de frappe de cobalt et du droxidat - un
Les chercheurs ont découvert une cyberattaque suspectée ciblant un générateur d'énergie en Afrique australe avec une nouvelle variante du malware SystemBC.L'attaque a été menée par un groupe de pirates inconnu en mars de cette année, selon un rapport de la société de cybersécurité SecureList .Les pirates ont utilisé un outil de frappe de cobalt et du droxidat - un
 Researchers have uncovered a suspected cyberattack targeting a power generator in southern Africa with a new variant of the SystemBC malware. The attack was carried out by an unknown hacker group in March of this year, according to a report by cybersecurity firm Securelist. The hackers used a Cobalt Strike tool and DroxiDat - a
Researchers have uncovered a suspected cyberattack targeting a power generator in southern Africa with a new variant of the SystemBC malware. The attack was carried out by an unknown hacker group in March of this year, according to a report by cybersecurity firm Securelist. The hackers used a Cobalt Strike tool and DroxiDat - a |
Malware Tool | ★★★ | ||
| 2023-08-11 10:00:00 | Image Steganography: dissiper les secrets dans les pixels Image steganography: Concealing secrets within pixels (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article.
In the realm of information security and covert communication, image steganography serves as a powerful technique for hiding sensitive data within innocent-looking images. By embedding secret messages or files within the pixels of an image, steganography enables covert transmission without arousing suspicion. This article aims to delve into the world of image steganography, exploring its principles, techniques, and real-world applications.
Understanding image steganography
Image steganography is the practice of concealing information within the data of digital images without altering their visual appearance. The hidden data can include text, images, audio, or any other form of binary information.
Image steganography serves as a clandestine communication method, providing a means to transmit sensitive information without arousing the suspicion of adversaries or unauthorized individuals. It offers an additional layer of security and confidentiality in digital communication.
Steganography vs. Cryptography: While cryptography focuses on encrypting data to render it unreadable, steganography aims to hide the existence of the data itself, making it inconspicuous within an image. Steganography can be used in conjunction with encryption to further enhance the security of covert communication.
Techniques of image steganography
LSB substitution: The Least Significant Bit (LSB) substitution method involves replacing the least significant bits of pixel values with secret data. As the least significant bits have minimal impact on the visual appearance of the image, this technique allows for the hiding of information without noticeably altering the image.
Spatial domain techniques: Various spatial domain techniques involve modifying the pixel values directly to embed secret data. These techniques include modifying pixel intensities, color values, or rearranging pixels based on a predefined pattern.
Transform domain techniques: Transform domain techniques, such as Discrete Cosine Transform (DCT) or Discrete Fourier Transform (DFT), manipulate the frequency domain representation of an image to embed secret data. This allows for the concealment of information within the frequency components of an image.
Spread spectrum techniques: Inspired by radio frequency communication, spread spectrum techniques spread the secret data across multiple pixels by slightly modifying their values. This method makes the hidden data more robust against detection and extraction attempts.
Adaptive steganography: Adaptive techniques dynamically adjust the embedding process based on the image content and local characteristics, making the hidden data even more resistant to detection. This approach enhances security and makes it harder for adversaries to identify stego images.
Let’s see a working example of image steganography using a free tool called OpenStego, the same can be downloaded from here. You will be required to have Java Runtime Environment for OpenStego to work on your system.
Once, you’ve installed OpenStego, you will see its interface as shown below:
 It has multiple options including Hide Data and Extract Data - more about these options can be found at official documentation of the tool.
We need to have two files, Message File (Which will be hidden data or data we want to hide) and Cover File (The file which we will use as a cover to hide the message file.)
I have downloaded two image files for the same.
It has multiple options including Hide Data and Extract Data - more about these options can be found at official documentation of the tool.
We need to have two files, Message File (Which will be hidden data or data we want to hide) and Cover File (The file which we will use as a cover to hide the message file.)
I have downloaded two image files for the same.
|
Tool | ★★★ | ||
| 2023-08-11 03:15:31 | CVE-2023-31246 (lien direct) | Les autorisations par défaut incorrectes dans certains logiciels d'outils SDP Intel (R) avant la version 1.4 Build 5 peuvent permettre à un utilisateur authentifié d'activer potentiellement l'escalade de privilèges via l'accès local.
Incorrect default permissions in some Intel(R) SDP Tool software before version 1.4 build 5 may allow an authenticated user to potentially enable escalation of privilege via local access. |
Tool | |||
| 2023-08-11 03:15:27 | CVE-2023-28938 (lien direct) | La consommation de ressources non contrôlées dans certains logiciels Intel (R) SSD Tools avant la version MDADM-4.2-RC2 peut permettre à un utilisateur privilégié d'activer potentiellement le déni de service via un accès local.
Uncontrolled resource consumption in some Intel(R) SSD Tools software before version mdadm-4.2-rc2 may allow a priviledged user to potentially enable denial of service via local access. |
Tool | |||
| 2023-08-11 03:15:25 | CVE-2023-28736 (lien direct) | Le débordement de tampon dans certains logiciels Intel (R) SSD Tools avant la version MDADM-4.2-RC2 peut permettre à un utilisateur privilégié d'activer potentiellement l'escalade des privilèges via l'accès local.
Buffer overflow in some Intel(R) SSD Tools software before version mdadm-4.2-rc2 may allow a privileged user to potentially enable escalation of privilege via local access. |
Tool | |||
| 2023-08-11 03:15:19 | CVE-2023-25944 (lien direct) | L'élément de chemin de recherche incontrôlé dans certains logiciels d'outils Intel (R) téléchargés avant le 3 février 2023 peut permettre à un utilisateur authentifié d'activer potentiellement l'escalade du privilège via l'accès local.
Uncontrolled search path element in some Intel(R) VCUST Tool software downloaded before February 3nd 2023 may allow an authenticated user to potentially enable escalation of privilege via local access. |
Tool | |||
| 2023-08-10 18:39:58 | Le rôle de l'AI \\ dans la cybersécurité: Black Hat USA 2023 révèle comment les grands modèles de langage façonnent l'avenir des attaques de phishing et de la défense AI\\'s Role in Cybersecurity: Black Hat USA 2023 Reveals How Large Language Models Are Shaping the Future of Phishing Attacks and Defense (lien direct) |
 à Black Hat USA 2023, une session dirigée par une équipe de chercheurs en sécurité, dont Fredrik Heiding, Bruce Schneier, Arun Vishwanath et Jeremy Bernstein, ont dévoilé une expérience intrigante.Ils ont testé de grands modèles de langue (LLM) pour voir comment ils ont fonctionné à la fois dans l'écriture de courriels de phishing convaincants et les détecter.Ceci est le PDF document technique . L'expérience: l'élaboration des e-mails de phishing L'équipe a testé quatre LLM commerciaux, y compris le chatppt de l'Openai \\, Bard de Google \\, Claude \\ de Google et Chatllama, dans des attaques de phishing expérimentales contre les étudiants de Harvard.L'expérience a été conçue pour voir comment la technologie de l'IA pouvait produire des leurres de phishing efficaces. Heriding, chercheur à Harvard, a souligné qu'une telle technologie a déjà eu un impact sur le paysage des menaces en facilitant la création de courriels de phishing.Il a dit: "GPT a changé cela. Vous n'avez pas besoin d'être un orateur anglais natif, vous n'avez pas besoin de faire beaucoup. Vous pouvez entrer une invite rapide avec seulement quelques points de données." L'équipe a envoyé des e-mails de phishing offrant des cartes-cadeaux Starbucks à 112 étudiants, en comparant Chatgpt avec un modèle non AI appelé V-Triad.Les résultats ont montré que l'e-mail V-Triad était le plus efficace, avec un taux de clic de 70%, suivi d'une combinaison V-Triad-Chatgpt à 50%, Chatgpt à 30% et le groupe témoin à 20%. Cependant, dans une autre version du test, Chatgpt a fonctionné beaucoup mieux, avec un taux de clic de près de 50%, tandis que la combinaison V-Triad-Chatgpt a mené avec près de 80%.Heriding a souligné qu'un LLM non formé et à usage général a pu créer rapidement des attaques de phishing très efficaces. Utilisation de LLMS pour la détection de phishing La deuxième partie de l'expérience s'est concentrée sur l'efficacité des LLM pour déterminer l'intention des e-mails suspects.L'équipe a utilisé les e-mails de Starbucks de la première partie de l'expérience et a demandé aux LLM de déterminer l'intention, qu'elle ait été composée par un humain ou une IA, d'identifier tout aspect suspect et d'offrir des conseils sur la façon de répondre. Les résultats étaient à la fois surprenants et encourageants.Les modèles avaient des taux de réussite élevés dans l'identification des e-mails marketing, mais ont eu des difficultés avec l'intention des e-mails de phishing V-Triad et Chatgpt.Ils se sont mieux comportés lorsqu'ils sont chargés d'identifier le contenu suspect, les résultats de Claude \\ étant mis en évidence pour non seulement pour obtenir des résultats élevés dans les tests de détection mais aussi fournir des conseils judicieux pour les utilisateurs. La puissance de phishing de LLMS Dans l'ensemble, Heriding a conclu que les LLMS prêtesété formé sur toutes les données de sécurité.Il a déclaré: "C'est vraiment quelque chose que tout le monde peut utiliser en ce moment. C'est assez puissant." L'expér
à Black Hat USA 2023, une session dirigée par une équipe de chercheurs en sécurité, dont Fredrik Heiding, Bruce Schneier, Arun Vishwanath et Jeremy Bernstein, ont dévoilé une expérience intrigante.Ils ont testé de grands modèles de langue (LLM) pour voir comment ils ont fonctionné à la fois dans l'écriture de courriels de phishing convaincants et les détecter.Ceci est le PDF document technique . L'expérience: l'élaboration des e-mails de phishing L'équipe a testé quatre LLM commerciaux, y compris le chatppt de l'Openai \\, Bard de Google \\, Claude \\ de Google et Chatllama, dans des attaques de phishing expérimentales contre les étudiants de Harvard.L'expérience a été conçue pour voir comment la technologie de l'IA pouvait produire des leurres de phishing efficaces. Heriding, chercheur à Harvard, a souligné qu'une telle technologie a déjà eu un impact sur le paysage des menaces en facilitant la création de courriels de phishing.Il a dit: "GPT a changé cela. Vous n'avez pas besoin d'être un orateur anglais natif, vous n'avez pas besoin de faire beaucoup. Vous pouvez entrer une invite rapide avec seulement quelques points de données." L'équipe a envoyé des e-mails de phishing offrant des cartes-cadeaux Starbucks à 112 étudiants, en comparant Chatgpt avec un modèle non AI appelé V-Triad.Les résultats ont montré que l'e-mail V-Triad était le plus efficace, avec un taux de clic de 70%, suivi d'une combinaison V-Triad-Chatgpt à 50%, Chatgpt à 30% et le groupe témoin à 20%. Cependant, dans une autre version du test, Chatgpt a fonctionné beaucoup mieux, avec un taux de clic de près de 50%, tandis que la combinaison V-Triad-Chatgpt a mené avec près de 80%.Heriding a souligné qu'un LLM non formé et à usage général a pu créer rapidement des attaques de phishing très efficaces. Utilisation de LLMS pour la détection de phishing La deuxième partie de l'expérience s'est concentrée sur l'efficacité des LLM pour déterminer l'intention des e-mails suspects.L'équipe a utilisé les e-mails de Starbucks de la première partie de l'expérience et a demandé aux LLM de déterminer l'intention, qu'elle ait été composée par un humain ou une IA, d'identifier tout aspect suspect et d'offrir des conseils sur la façon de répondre. Les résultats étaient à la fois surprenants et encourageants.Les modèles avaient des taux de réussite élevés dans l'identification des e-mails marketing, mais ont eu des difficultés avec l'intention des e-mails de phishing V-Triad et Chatgpt.Ils se sont mieux comportés lorsqu'ils sont chargés d'identifier le contenu suspect, les résultats de Claude \\ étant mis en évidence pour non seulement pour obtenir des résultats élevés dans les tests de détection mais aussi fournir des conseils judicieux pour les utilisateurs. La puissance de phishing de LLMS Dans l'ensemble, Heriding a conclu que les LLMS prêtesété formé sur toutes les données de sécurité.Il a déclaré: "C'est vraiment quelque chose que tout le monde peut utiliser en ce moment. C'est assez puissant." L'expér |
Tool Threat | ChatGPT ChatGPT | ★★ | |
| 2023-08-10 12:36:30 | DTX Europe 2023 (lien direct) | DTX rassemble des esprits créatifs, des experts techniques et les derniers outils nécessaires pour stimuler le changement et générer de la valeur dans les organisations d'aujourd'hui.«Votre maison de transformation numérique» couvrant le cloud, les réseaux et les infrastructures;données, analyses et IA;Génie logiciel et DevOps;et la cybersécurité, l'événement présente la technologie, les solutions et les stratégies essentielles pour faire avancer les projets numériques [& # 8230;]
DTX brings together creative minds, technical experts and the latest tools needed to drive change and generate value across today\'s organisations. “Your Home of Digital Transformation” Covering cloud, networks and infrastructure; data, analytics and AI; software engineering and DevOps; and cyber security, the event showcases the technology, solutions and strategies essential to advance digital projects […] |
Tool | ★★★ | ||
| 2023-08-10 12:01:36 | Rendre le chrome plus sécurisé en apportant une épingle clé sur Android Making Chrome more secure by bringing Key Pinning to Android (lien direct) |
Posted by David Adrian, Joe DeBlasio and Carlos Joan Rafael Ibarra Lopez, Chrome Security
Chrome 106 added support for enforcing key pins on Android by default, bringing Android to parity with Chrome on desktop platforms. But what is key pinning anyway?
One of the reasons Chrome implements key pinning is the “rule of two”. This rule is part of Chrome\'s holistic secure development process. It says that when you are writing code for Chrome, you can pick no more than two of: code written in an unsafe language, processing untrustworthy inputs, and running without a sandbox. This blog post explains how key pinning and the rule of two are related.
The Rule of Two
 Chrome is primarily written in the C and C++ languages, which are vulnerable to memory safety bugs. Mistakes with pointers in these languages can lead to memory being misinterpreted. Chrome invests in an ever-stronger multi-process architecture built on sandboxing and site isolation to help defend against memory safety problems. Android-specific features can be written in Java or Kotlin. These languages are memory-safe in the common case. Similarly, we\'re working on adding support to write Chrome code in Rust, which is also memory-safe.
Much of Chrome is sandboxed, but the sandbox still requires a core high-privilege “broker” process to coordinate communication and launch sandboxed processes. In Chrome, the broker is the browser process. The browser process is the source of truth that allows the rest of Chrome to be sandboxed and coordinates communication between the rest of the processes.
If an attacker is able to craft a malicious input to the browser process that exploits a bug and allows the attacker to achieve remote code execution (RCE) in the browser process, that would effectively give the attacker full control of the victim\'s Chrome browser and potentially the rest of the device. Conversely, if an attacker achieves RCE in a sandboxed process, such as a renderer, the attacker\'s capabilities are extremely limited. The attacker cannot reach outside of the sandbox unless they can additionally exploit the sandbox itself.
Without sandboxing, which limits the actions an attacker can take, and without memory safety, which removes the ability of a bug to disrupt the intended control flow of the program, the rule of two requires that the browser process does not handle untrustworthy inputs. The relative risks between sandboxed processes and the browser process are why the browser process is only allowed to parse trustworthy inputs and specific IPC messages.
Trustworthy inputs are defined extremely strictly: A “trustworthy source” means that Chrome can prove that the data comes from Google. Effectively, this means that in situations where the browser process needs access to data from e
Chrome is primarily written in the C and C++ languages, which are vulnerable to memory safety bugs. Mistakes with pointers in these languages can lead to memory being misinterpreted. Chrome invests in an ever-stronger multi-process architecture built on sandboxing and site isolation to help defend against memory safety problems. Android-specific features can be written in Java or Kotlin. These languages are memory-safe in the common case. Similarly, we\'re working on adding support to write Chrome code in Rust, which is also memory-safe.
Much of Chrome is sandboxed, but the sandbox still requires a core high-privilege “broker” process to coordinate communication and launch sandboxed processes. In Chrome, the broker is the browser process. The browser process is the source of truth that allows the rest of Chrome to be sandboxed and coordinates communication between the rest of the processes.
If an attacker is able to craft a malicious input to the browser process that exploits a bug and allows the attacker to achieve remote code execution (RCE) in the browser process, that would effectively give the attacker full control of the victim\'s Chrome browser and potentially the rest of the device. Conversely, if an attacker achieves RCE in a sandboxed process, such as a renderer, the attacker\'s capabilities are extremely limited. The attacker cannot reach outside of the sandbox unless they can additionally exploit the sandbox itself.
Without sandboxing, which limits the actions an attacker can take, and without memory safety, which removes the ability of a bug to disrupt the intended control flow of the program, the rule of two requires that the browser process does not handle untrustworthy inputs. The relative risks between sandboxed processes and the browser process are why the browser process is only allowed to parse trustworthy inputs and specific IPC messages.
Trustworthy inputs are defined extremely strictly: A “trustworthy source” means that Chrome can prove that the data comes from Google. Effectively, this means that in situations where the browser process needs access to data from e |
Tool | ★★ | ||
| 2023-08-09 21:39:00 | DARPA lance un concours de deux ans pour construire des outils d'IA pour réparer les vulnérabilités DARPA Launches Two-Year Contest to Build AI Tools to Fix Vulnerabilities (lien direct) |
Un défi sera offert aux équipes pour créer des outils à l'aide de l'IA afin de résoudre les défis de vulnérabilité de l'Open Source.
A challenge will be offered to teams to build tools using AI in order to solve open source\'s vulnerability challenges. |
Tool Vulnerability | ★★ | ||
| 2023-08-09 20:38:00 | Un nouvel outil LLM cherche et corrige les vulnérabilités New LLM Tool Seeks and Remediates Vulnerabilities (lien direct) |
Vicarius a lancé vuln_gpt, qui, selon lui, générera et exécutera des scripts pour améliorer les défauts tels que la porte arrière Tetra.
Vicarius launched vuln_GPT, which it says will generate and execute scripts to ameliorate flaws such as the TETRA backdoor. |
Tool Vulnerability | ★★ | ||
| 2023-08-09 18:15:10 | CVE-2022-48580 (lien direct) | Une vulnérabilité d'injection de commande existe dans la fonction d'outil de périphérique Ping ARP de ScienceLogic SL1 qui prend une entrée contrôlée par l'utilisateur non animé et la transmet directement à une commande shell.Cela permet & acirc; & nbsp; l'injection de commandes arbitraires au système d'exploitation sous-jacent.
A command injection vulnerability exists in the ARP ping device tool feature of the ScienceLogic SL1 that takes unsanitized user controlled input and passes it directly to a shell command. This allows for the injection of arbitrary commands to the underlying operating system. |
Tool Vulnerability | |||
| 2023-08-09 17:06:00 | Validation de sécurité continue avec les tests de pénétration en tant que service (PTAAS) Continuous Security Validation with Penetration Testing as a Service (PTaaS) (lien direct) |
Validez la sécurité en continu à travers votre pile complète avec test de stylo en tant que service.
Dans le centre d'opérations de sécurité moderne d'aujourd'hui (SOC), c'est une bataille entre les défenseurs et les cybercriminels.Les deux utilisent des outils et de l'expertise & # 8211;Cependant, les cybercriminels ont l'élément de surprise de leur côté et une multitude de tactiques, de techniques et de procédures (TTP) qui ont évolué.Ces externes
Validate security continuously across your full stack with Pen Testing as a Service. In today\'s modern security operations center (SOC), it\'s a battle between the defenders and the cybercriminals. Both are using tools and expertise – however, the cybercriminals have the element of surprise on their side, and a host of tactics, techniques, and procedures (TTPs) that have evolved. These external |
Tool | ★★★★ | ||
| 2023-08-09 16:26:00 | Sweet Security débute la gestion de l'exécution pour le cloud Sweet Security Debuts Runtime Management for Cloud (lien direct) |
Les outils de détection existants fournissent des fonctionnalités limitées ou sont optimisées pour le cloud, affirme les startups israéliennes.
Existing detection tools either provide limited functionality or aren\'t optimized for the cloud, Israeli startup claims. |
Tool Cloud | ★★ | ||
| 2023-08-09 14:35:00 | La base de données sur les risques d'IA aborde les risques de la chaîne d'approvisionnement de l'IA AI Risk Database Tackles AI Supply Chain Risks (lien direct) |
L'outil open source - une collaboration entre Robust Intelligence, Mitre et Indiana University - évalue les modèles d'apprentissage automatique fortement partagé pour le risque.
The open source tool - a collaboration between Robust Intelligence, MITRE, and Indiana University - assesses heavily shared, public machine learning models for risk. |
Tool | ★★★ | ||
| 2023-08-09 13:00:00 | Découvrir les vulnérabilités de sécurité cachées avec un sast plus profond Uncovering hidden security vulnerabilities with deeper SAST (lien direct) |
Découvrir les vulnérabilités de sécurité est particulièrement difficile car ces problèmes peuvent être complexes et profondément cachés lorsque votre code utilise et interagit avec le code de dépendance tiers.Nous sommes ravis de partager davantage sur une percée majeure dans notre détection de vulnérabilités de sécurité profondément cachées que les outils traditionnels ne peuvent pas détecter.
Uncovering security vulnerabilities is particularly challenging because these issues can be complex and deeply hidden when your code uses and interacts with third-party dependency code. We are excited to share more about a major breakthrough in our detection of deeply hidden security vulnerabilities that traditional tools cannot detect. |
Tool Vulnerability | ★★ | ||
| 2023-08-09 10:00:00 | Attention à l'écart (d'interprétation): une autre raison pour laquelle la modélisation des menaces est importante Mind the (Interpretation) gap: Another reason why threat modeling is important (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Where do vulnerabilities fit with respect to security standards and guidelines? Was it a coverage issue or an interpretation and implementation issue? Where does a product, environment, organization, or business vertical fail the most in terms of standards requirements? These questions are usually left unanswered because of the gap between standards or regulations on the one hand, and requirements interpretation and implementation, on the other. Certified products and environments often suffer from security issues that were supposed to be covered by the requirements of the standard. In [1], for instance, the authors give examples of vulnerable products that were IEC 62443 certified. In [2], SANS discusses the case of PCI-certified companies and why they are still being breached. This “interpretation gap,” whether it manifests in the implementation of requirements or in the assessment process, hinders security and leads to the fact that being compliant is not necessarily the same as being secure. Admittedly, the interpretation of guidelines and requirements in standards, which have a descriptive approach in general, is not an easy task. Requirements can be rather generic and wide open to interpretation depending on the context, resources, the current threat landscape, the underlying technologies, etc. Specific requirements might also lead to conflicting interpretations depending on the type of stakeholder, which will inevitably affect the implementation side. Threat modeling is one way to avoid shortcomings (or even possible shortcuts) in the implementation of standards, and the organization\'s own security policies. Think of threat modeling as an enforcement mechanism for the proper implementation of requirements. The reason this is the case is simple; threat modeling thinks of the requirements in terms of relevant threats to the system, and determines mitigations to reduce or completely avoid the associated risks. Consequently, each requirement is mapped to a set of threats and mitigations that covers relevant use cases under specific conditions or context, e.g., what are the trust boundaries, protocols and technologies under use or consideration, third-party interactions, dataflows, data storage, etc. This is becoming a must-have nowadays since, when it comes to technical requirements, the concern about their interpretation still persists even when companies have been audited against them. In the following, the presented data analysis makes the link between disclosed vulnerabilities in Industrial Control Systems (ICS) and the technical requirements reported in the ‘gold standard’ of standards in this area, namely the IEC 62443. It shows the difficulty of satisfying the requirements in broad terms and the need for more specific context and processes. CISA ICS advisories’ mapping The analysis of CISA ICS advisories data, representing close to 2,5K advisories released between 2010 and mid-2023 [3], reveals the extent of the challenge an implementer or an assessor is faced with. Table 1 presents the top weaknesses and the associated count of advisories as well as IEC 62443 requirements’ mapping. Affected sectors, the CVSS severity distribution, and top weaknesses per sector are also reported; in Figures 1 and 2, and Table 2. Table 1. Top weaknesses in CISA’s ICS advisories and their IEC 62443 mapping. Weakness Name | Tool Vulnerability Threat Industrial Prediction | ★★ | ||
| 2023-08-08 18:15:16 | CVE-2023-36903 (lien direct) | Élévation de l'outil d'évaluation du système Windows Élévation de la vulnérabilité des privilèges
Windows System Assessment Tool Elevation of Privilege Vulnerability |
Tool Vulnerability | |||
| 2023-08-08 18:15:15 | CVE-2023-36897 (lien direct) | Outils Visual Studio pour la vulnérabilité de l'usurpation de l'Office Runtime
Visual Studio Tools for Office Runtime Spoofing Vulnerability |
Tool Vulnerability | |||
| 2023-08-08 11:59:13 | Android 14 présente les fonctionnalités de sécurité de la connectivité cellulaire en son genre Android 14 introduces first-of-its-kind cellular connectivity security features (lien direct) |
Posted by Roger Piqueras Jover, Yomna Nasser, and Sudhi Herle
Android is the first mobile operating system to introduce advanced cellular security mitigations for both consumers and enterprises. Android 14 introduces support for IT administrators to disable 2G support in their managed device fleet. Android 14 also introduces a feature that disables support for null-ciphered cellular connectivity.
Hardening network security on Android
The Android Security Model assumes that all networks are hostile to keep users safe from network packet injection, tampering, or eavesdropping on user traffic. Android does not rely on link-layer encryption to address this threat model. Instead, Android establishes that all network traffic should be end-to-end encrypted (E2EE).
When a user connects to cellular networks for their communications (data, voice, or SMS), due to the distinctive nature of cellular telephony, the link layer presents unique security and privacy challenges. False Base Stations (FBS) and Stingrays exploit weaknesses in cellular telephony standards to cause harm to users. Additionally, a smartphone cannot reliably know the legitimacy of the cellular base station before attempting to connect to it. Attackers exploit this in a number of ways, ranging from traffic interception and malware sideloading, to sophisticated dragnet surveillance.
 Recognizing the far reaching implications of these attack vectors, especially for at-risk users, Android has prioritized hardening cellular telephony. We are tackling well-known insecurities such as the risk presented by 2G networks, the risk presented by null ciphers, other false base station (FBS) threats, and baseband hardening with our ecosystem partners.
2G and a history of inherent security risk
The mobile ecosystem is rapidly adopting 5G, the latest wireless standard for mobile, and many carriers have started to turn down 2G service. In the United States, for example, most major carriers have shut down 2G networks. However, all existing mobile devices still have support for 2G. As a result, when available, any mobile device will connect to a 2G network. This occurs automatically when 2G is the only network available, but this can also be remotely triggered in a malicious attack, silently inducing devices to downgrade to 2G-only connectivity and thus, ignoring any non-2G network. This behavior happens regardless of whether local operators have already sunset their 2G infrastructure.
2G networks, first implemented in 1991, do not provide the same level of security as subsequent mobile generat
Recognizing the far reaching implications of these attack vectors, especially for at-risk users, Android has prioritized hardening cellular telephony. We are tackling well-known insecurities such as the risk presented by 2G networks, the risk presented by null ciphers, other false base station (FBS) threats, and baseband hardening with our ecosystem partners.
2G and a history of inherent security risk
The mobile ecosystem is rapidly adopting 5G, the latest wireless standard for mobile, and many carriers have started to turn down 2G service. In the United States, for example, most major carriers have shut down 2G networks. However, all existing mobile devices still have support for 2G. As a result, when available, any mobile device will connect to a 2G network. This occurs automatically when 2G is the only network available, but this can also be remotely triggered in a malicious attack, silently inducing devices to downgrade to 2G-only connectivity and thus, ignoring any non-2G network. This behavior happens regardless of whether local operators have already sunset their 2G infrastructure.
2G networks, first implemented in 1991, do not provide the same level of security as subsequent mobile generat |
Malware Tool Threat Conference | ★★★ | ||
| 2023-08-08 11:15:12 | CVE-2023-4203 (lien direct) | Les appareils EKI-1524, EKI-1522, EKI-1521 EKI-1522, EKI-1521 via 1,21 sont affectés par une vulnérabilité de script de site transversale stockée, qui peut être déclenchée par des utilisateurs authentifiés dans l'outil Ping de l'interface Web.
Advantech EKI-1524, EKI-1522, EKI-1521 devices through 1.21 are affected by a Stored Cross-Site Scripting vulnerability, which can be triggered by authenticated users in the ping tool of the web-interface. |
Tool | |||
| 2023-08-04 21:15:00 | Le procès accuse l'hôpital de partager les données de santé des patients avec Facebook Lawsuit accuses hospital of sharing patient health data with Facebook (lien direct) |
 Un procès en recours collectif déposé jeudi allègue qu'un hôpital de la région de Seattle a autorisé les outils de suivi en ligne de Facebook \\ pour s'intégrer à son site Web, conduisant à des données de santé personnelles appartenant à des centaines de milliers de personnes à partager avec Meta et d'autres tiers.Le demandeur, Jacq Nienaber, allègue que Meta Pixel ainsi que le
Un procès en recours collectif déposé jeudi allègue qu'un hôpital de la région de Seattle a autorisé les outils de suivi en ligne de Facebook \\ pour s'intégrer à son site Web, conduisant à des données de santé personnelles appartenant à des centaines de milliers de personnes à partager avec Meta et d'autres tiers.Le demandeur, Jacq Nienaber, allègue que Meta Pixel ainsi que le
 A proposed class action lawsuit filed Thursday alleges that a Seattle-area hospital allowed Facebook\'s online tracking tools to integrate with its website, leading to personal health data belonging to hundreds of thousands of people to be shared with Meta and other third parties. The plaintiff, Jacq Nienaber, alleges that Meta Pixel as well as the
A proposed class action lawsuit filed Thursday alleges that a Seattle-area hospital allowed Facebook\'s online tracking tools to integrate with its website, leading to personal health data belonging to hundreds of thousands of people to be shared with Meta and other third parties. The plaintiff, Jacq Nienaber, alleges that Meta Pixel as well as the |
Tool | ★★ | ||
| 2023-08-04 13:20:47 | Les acteurs de la menace abusent du tunnel Cloudflare pour un accès persistant, vol de données Threat Actors Abuse Cloudflare Tunnel for Persistent Access, Data Theft (lien direct) |
> Les acteurs de menace ont été observés abusant de l'outil de tunnel de nuage de nuage open source.
>Threat actors have been observed abusing the open source Cloudflare Tunnel tool Cloudflared to maintain stealthy, persistent access to compromised systems. |
Tool Threat | ★★ | ||
| 2023-08-03 19:13:38 | Pathlock reconnu comme un leader dans deux rapports de l'industrie Kuppingercole mettant en évidence le leadership dans les solutions de contrôle d'accès pour les applications commerciales Pathlock Recognized as a Leader in Two KuppingerCole Industry Reports Highlighting Leadership in Access Control Solutions for Business Applications (lien direct) |
Pathlock reconnu comme un leader dans deux rapports de l'industrie de Kuppingercole mettant en évidence le leadership dans les solutions de contrôle d'accès pour les applications commerciales
Pathlock a nommé un leader global des outils de contrôle d'accès pour les environnements LOB multi-vendeurs
-
magic quadrant
Pathlock Recognized as a Leader in Two KuppingerCole Industry Reports Highlighting Leadership in Access Control Solutions for Business Applications Pathlock Named an Overall Leader in Access Control Tools for Multi-Vendor LoB Environments - MAGIC QUADRANT |
Tool | ★ | ||
| 2023-08-03 15:15:30 | CVE-2023-3348 (lien direct) | L'outil de ligne de commande Wrangler ( | Tool Vulnerability | |||
| 2023-08-02 17:20:00 | Les chercheurs découvrent l'agent AWS SSM abusant comme un accès à distance secrète Researchers Uncover AWS SSM Agent Misuse as a Covert Remote Access Trojan (lien direct) |
Les chercheurs en cybersécurité ont découvert une nouvelle technique post-exploitation dans Amazon Web Services (AWS) qui permet à l'agent AWS Systems Manager (Agent SSM) d'être exécuté en tant que Troie à distance sur Windows et Linux
"L'agent SSM, un outil légitime utilisé par les administrateurs pour gérer leurs instances, peut être réutilisé par un attaquant qui a obtenu un accès élevé sur un point final avec un point final avec
Cybersecurity researchers have discovered a new post-exploitation technique in Amazon Web Services (AWS) that allows the AWS Systems Manager Agent (SSM Agent) to be run as a remote access trojan on Windows and Linux environments "The SSM agent, a legitimate tool used by admins to manage their instances, can be re-purposed by an attacker who has achieved high privilege access on an endpoint with |
Tool | ★★★ | ||
| 2023-08-02 10:00:00 | Code Mirage: Comment les cybercriminels exploitent le code halluciné AI pour les machinations malveillantes Code Mirage: How cyber criminals harness AI-hallucinated code for malicious machinations (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article.
Introduction:
The landscape of cybercrime continues to evolve, and cybercriminals are constantly seeking new methods to compromise software projects and systems. In a disconcerting development, cybercriminals are now capitalizing on AI-generated unpublished package names also known as “AI-Hallucinated packages” to publish malicious packages under commonly hallucinated package names. It should be noted that artificial hallucination is not a new phenomenon as discussed in [3]. This article sheds light on this emerging threat, wherein unsuspecting developers inadvertently introduce malicious packages into their projects through the code generated by AI.
 AI-hallucinations:
AI-hallucinations:
 Artificial intelligence (AI) hallucinations, as described [2], refer to confident responses generated by AI systems that lack justification based on their training data. Similar to human psychological hallucinations, AI hallucinations involve the AI system providing information or responses that are not supported by the available data. However, in the context of AI, hallucinations are associated with unjustified responses or beliefs rather than false percepts. This phenomenon gained attention around 2022 with the introduction of large language models like ChatGPT, where users observed instances of seemingly random but plausible-sounding falsehoods being generated. By 2023, it was acknowledged that frequent hallucinations in AI systems posed a significant challenge for the field of language models.
The exploitative process:
Cybercriminals begin by deliberately publishing malicious packages under commonly hallucinated names produced by large language machines (LLMs) such as ChatGPT within trusted repositories. These package names closely resemble legitimate and widely used libraries or utilities, such as the legitimate package ‘arangojs’ vs the hallucinated package ‘arangodb’ as shown in the research done by Vulcan [1].
The trap unfolds:
Artificial intelligence (AI) hallucinations, as described [2], refer to confident responses generated by AI systems that lack justification based on their training data. Similar to human psychological hallucinations, AI hallucinations involve the AI system providing information or responses that are not supported by the available data. However, in the context of AI, hallucinations are associated with unjustified responses or beliefs rather than false percepts. This phenomenon gained attention around 2022 with the introduction of large language models like ChatGPT, where users observed instances of seemingly random but plausible-sounding falsehoods being generated. By 2023, it was acknowledged that frequent hallucinations in AI systems posed a significant challenge for the field of language models.
The exploitative process:
Cybercriminals begin by deliberately publishing malicious packages under commonly hallucinated names produced by large language machines (LLMs) such as ChatGPT within trusted repositories. These package names closely resemble legitimate and widely used libraries or utilities, such as the legitimate package ‘arangojs’ vs the hallucinated package ‘arangodb’ as shown in the research done by Vulcan [1].
The trap unfolds:
 When developers, unaware of the malicious intent, utilize AI-based tools or large language models (LLMs) to generate code snippets for their projects, they inadvertently can fall into a trap. The AI-generated code snippets can include imaginary unpublished libraries, enabling cybercriminals to publish commonly used AI-generated imaginary package names. As a result, developers unknowingly import malicious packages into their projects, introducing vulnerabilities, backdoors, or other malicious functionalities that compromise the security and integrity of the software and possibly other projects.
Implications for developers:
The exploitation of AI-generated hallucinated package names poses significant risks to developers and their projects. Here are some key implications:
Trusting familiar package names: Developers commonly rely on package names they recognize to introduce code snippets into their projects. The presence of malicious packages under commonly hallucinated names makes it increasingly difficult to distinguish between legitimate and malicious options when relying on the trust from AI generated code.
Blind trust in AI-generated code: Many develo
When developers, unaware of the malicious intent, utilize AI-based tools or large language models (LLMs) to generate code snippets for their projects, they inadvertently can fall into a trap. The AI-generated code snippets can include imaginary unpublished libraries, enabling cybercriminals to publish commonly used AI-generated imaginary package names. As a result, developers unknowingly import malicious packages into their projects, introducing vulnerabilities, backdoors, or other malicious functionalities that compromise the security and integrity of the software and possibly other projects.
Implications for developers:
The exploitation of AI-generated hallucinated package names poses significant risks to developers and their projects. Here are some key implications:
Trusting familiar package names: Developers commonly rely on package names they recognize to introduce code snippets into their projects. The presence of malicious packages under commonly hallucinated names makes it increasingly difficult to distinguish between legitimate and malicious options when relying on the trust from AI generated code.
Blind trust in AI-generated code: Many develo |
Tool | APT 15 ChatGPT ChatGPT | ★★★ | |
| 2023-08-01 21:55:00 | Sniffier le parphon sur sa chasse à l'administrateur du domaine Sniffing Out SharpHound on its Hunt for Domain Admin (lien direct) |
Type: Blogs reniflant Sharphound sur sa chasse à l'administrateur de domaine Les graphiques tactiques SecureWorks Taegis XDR recherchent la télémétrie qui peut identifier la présence d'outils malveillants utilisés pour obtenir l'accès administrateur du domaine. Les graphiques tactiques SecureWorks Taegis XDR recherchent une télémétrie qui peut identifier la présence d'outils malveillants utilisés pour obtenir l'accès à l'administrateur de domaine.
Type: BlogsSniffing Out SharpHound on its Hunt for Domain AdminThe Secureworks Taegis XDR Tactic Graphs searches for telemetry that can identify the presence of malicious tools used to gain domain administrator access.The Secureworks Taegis XDR Tactic Graphs searches for telemetry that can identify the presence of malicious tools used to gain domain administrator access. |
Tool | ★★ | ||
| 2023-08-01 20:21:32 | GuardZ identifie les nouveaux logiciels malveillants macOS HVNC, révélant la tendance émergente des outils d'attaque de macOS en tant que service Guardz Identifies New macOS hVNC Malware, Revealing Emerging Trend of macOS Attack-as-a-Service Tools (lien direct) |
Guardz identifie les nouveaux logiciels malveillants MacOS HVNC, révélant la tendance émergente des outils d'attaque macOS en tant que service
Pour la deuxième fois en un mois, l'équipe de recherche GuardZ révèle l'existence d'un autre logiciel malveillant ciblant les appareils MacOS disponibles sur le Web Dark, qui permet aux acteurs malveillants d'obtenir un accès furtif et continu aux systèmes infectés
-
mise à jour malveillant
Guardz Identifies New macOS hVNC Malware, Revealing Emerging Trend of macOS Attack-as-a-Service Tools For the second time in one month, the Guardz research team discloses the existence of another malware targeting macOS devices available on the dark web, which enables malicious actors to obtain stealthy and continuous access to infected systems - Malware Update |
Malware Tool Prediction | ★★ |

