What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2022-02-24 19:15:08 | CVE-2020-14481 (lien direct) | The DeskLock tool provided with FactoryTalk View SE uses a weak encryption algorithm that may allow a local, authenticated attacker to decipher user credentials, including the Windows user or Windows DeskLock passwords. If the compromised user has an administrative account, an attacker could gain full access to the user’s operating system and certain components of FactoryTalk View SE. | Tool | |||
| 2022-02-24 15:00:00 | LITE SUR LECTURE: Télégramme malveillant repéré dans la dernière activité de cyber-espionnage iranienne Left On Read: Telegram Malware Spotted in Latest Iranian Cyber Espionage Activity (lien direct) |
En novembre 2021, Défense gérée mandiante détecté et répondu à un UNC3313 Intrusion chez un client du Moyen-Orient.Au cours de l'enquête, Mandiant a identifié de nouveaux logiciels malveillants ciblés, gramdoor et Starwhale , qui implémentent les fonctionnalités de porte-portefeuille simples.Nous avons également identifié UNC3313 Utiliser un logiciel d'accès à distance accessible au public pour maintenir l'accès à l'environnement.UNC3313 a initialement eu accès à cette organisation par le biais d'un e-mail de phishing ciblé et des outils de sécurité offensifs open-source modifiés et à effet de levier pour identifier les systèmes accessibles et se déplacer latéralement.Unc3313 déplacé
In November 2021, Mandiant Managed Defense detected and responded to an UNC3313 intrusion at a Middle East government customer. During the investigation, Mandiant identified new targeted malware, GRAMDOOR and STARWHALE, which implement simple backdoor functionalities. We also identified UNC3313 use publicly available remote access software to maintain access to the environment. UNC3313 initially gained access to this organization through a targeted phishing email and leveraged modified, open-source offensive security tools to identify accessible systems and move laterally. UNC3313 moved |
Malware Tool | ★★★★ | ||
| 2022-02-23 23:15:07 | CVE-2022-23653 (lien direct) | B2 Command Line Tool is the official command line tool for the backblaze cloud storage service. Linux and Mac releases of the B2 command-line tool version 3.2.0 and below contain a key disclosure vulnerability that, in certain conditions, can be exploited by local attackers through a time-of-check-time-of-use (TOCTOU) race condition. The command line tool saves API keys (and bucket name-to-id mapping) in a local database file (`$XDG_CONFIG_HOME/b2/account_info`, `~/.b2_account_info` or a user-defined path) when `b2 authorize-account` is first run. This happens regardless of whether a valid key is provided or not. When first created, the file is world readable and is (typically a few milliseconds) later altered to be private to the user. If the directory is readable by a local attacker and the user did not yet run `b2 authorize-account` then during the brief period between file creation and permission modification, a local attacker can race to open the file and maintain a handle to it. This allows the local attacker to read the contents after the file after the sensitive information has been saved to it. Users that have not yet run `b2 authorize-account` should upgrade to B2 Command-Line Tool v3.2.1 before running it. Users that have run `b2 authorize-account` are safe if at the time of the file creation no other local users had read access to the local configuration file. Users that have run `b2 authorize-account` where the designated path could be opened by another local user should upgrade to B2 Command-Line Tool v3.2.1 and remove the database and regenerate all application keys. Note that `b2 clear-account` does not remove the database file and it should not be used to ensure that all open handles to the file are invalidated. If B2 Command-Line Tool cannot be upgraded to v3.2.1 due to a dependency conflict, a binary release can be used instead. Alternatively a new version could be installed within a virtualenv, or the permissions can be changed to prevent local users from opening the database file. | Tool Vulnerability | |||
| 2022-02-23 18:46:00 | Anomali Cyber Watch: EvilPlayout: Attack Against Iran\'s State Broadcaster, Microsoft Teams Targeted With Takeover Trojans, \'Ice phishing\' on the blockchain and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: Emotet, Ice Phishing, Iran, Trickbot and Zoho. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
EvilPlayout: Attack Against Iran’s State Broadcaster
(published: February 18, 2022)
Checkpoint Researchers have released an article detailing their findings regarding a wave of cyber attacks directed at Iranian broadcast infrastructure during late January 2022. IRIB, an Iranian state broadcaster, was compromised, with malicious executables and wipers being responsible for the attack. Said malware had multiple functions, including hijacking of several tv stations to play recordings of political opposition leaders demanding the assassination of Iran’s supreme leader. Additional functionality includes custom backdoors, screenshot capability and several bash scripts to download other malicious executables. The malware appears new, with no previous appearances, nor has there been any actor attribution as of the date of publication.
Analyst Comment: Utilize all telemetry and feed it into a SIEM to help identify malicious activity within your network. Anomali Match can collide this telemetry against global intelligence to assist in identifying malicious indicators within your network. A defense in depth approach will also mitigate the damage any compromises can do to your infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Screen Capture - T1113
Tags: Iran, IRIB, Ava, Telewebion
Microsoft Teams Targeted With Takeover Trojans
(published: February 17, 2022)
Researchers at Avanan have documented a new phishing technique that threat actors are using that abuses the trust users of Microsoft Teams have for the platform to deliver malware. Threat Actors send phishing links to victims which initiate a chat on the platform, after which they will post a link to a dll file within the chat box. When clicked, it will install a trojan of choice on the target machine. With over 279 million users, this presents a new attack vector for threat actors to abuse.
Analyst Comment: Never click on a link or open attachments from untrusted senders when receiving email. Be skeptical of strangers attempting to move conversation to another platform, even if you use that platform. Be wary of links posted in apps that are used for communication, as links that are posted on trusted platforms are not trustworthy themselves.
MITRE ATT&CK: [MITRE ATT&CK] Phishing - T1566 | [MITRE ATT&CK] Trusted Relationship - T1199
Tags: Microsoft Teams, trojan, phishing
Red Cross: State Hackers Breached our Network Using Zoho bug
(published: February 16, 2022)
The International Committee of the Red Cross (ICRC) suffered a data breach during January 2022. The incident led to the exfiltration of over 515,000 individual's PII, linked to their Restoring Family Links pro
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
EvilPlayout: Attack Against Iran’s State Broadcaster
(published: February 18, 2022)
Checkpoint Researchers have released an article detailing their findings regarding a wave of cyber attacks directed at Iranian broadcast infrastructure during late January 2022. IRIB, an Iranian state broadcaster, was compromised, with malicious executables and wipers being responsible for the attack. Said malware had multiple functions, including hijacking of several tv stations to play recordings of political opposition leaders demanding the assassination of Iran’s supreme leader. Additional functionality includes custom backdoors, screenshot capability and several bash scripts to download other malicious executables. The malware appears new, with no previous appearances, nor has there been any actor attribution as of the date of publication.
Analyst Comment: Utilize all telemetry and feed it into a SIEM to help identify malicious activity within your network. Anomali Match can collide this telemetry against global intelligence to assist in identifying malicious indicators within your network. A defense in depth approach will also mitigate the damage any compromises can do to your infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Screen Capture - T1113
Tags: Iran, IRIB, Ava, Telewebion
Microsoft Teams Targeted With Takeover Trojans
(published: February 17, 2022)
Researchers at Avanan have documented a new phishing technique that threat actors are using that abuses the trust users of Microsoft Teams have for the platform to deliver malware. Threat Actors send phishing links to victims which initiate a chat on the platform, after which they will post a link to a dll file within the chat box. When clicked, it will install a trojan of choice on the target machine. With over 279 million users, this presents a new attack vector for threat actors to abuse.
Analyst Comment: Never click on a link or open attachments from untrusted senders when receiving email. Be skeptical of strangers attempting to move conversation to another platform, even if you use that platform. Be wary of links posted in apps that are used for communication, as links that are posted on trusted platforms are not trustworthy themselves.
MITRE ATT&CK: [MITRE ATT&CK] Phishing - T1566 | [MITRE ATT&CK] Trusted Relationship - T1199
Tags: Microsoft Teams, trojan, phishing
Red Cross: State Hackers Breached our Network Using Zoho bug
(published: February 16, 2022)
The International Committee of the Red Cross (ICRC) suffered a data breach during January 2022. The incident led to the exfiltration of over 515,000 individual's PII, linked to their Restoring Family Links pro |
Ransomware Data Breach Malware Tool Vulnerability Threat Guideline | |||
| 2022-02-23 12:38:05 | CISA Warns of Attacks Exploiting Recent Vulnerabilities in Zabbix Monitoring Tool (lien direct) | The United States Cybersecurity and Infrastructure Security Agency (CISA) this week expanded its Known Exploited Vulnerabilities Catalog with two critical flaws in the Zabbix enterprise monitoring solution. | Tool | |||
| 2022-02-23 00:39:07 | Chinese Experts Uncover Details of Equation Group\'s Bvp47 Covert Hacking Tool (lien direct) | Researchers from China's Pangu Lab have disclosed details of a "top-tier" backdoor put to use by the Equation Group, an advanced persistent threat (APT) with alleged ties to the cyber-warfare intelligence-gathering unit of the U.S. National Security Agency (NSA). Dubbed "Bvp47" owing to numerous references to the string "Bvp" and the numerical value "0x47" used in the encryption algorithm, the | Tool Threat | |||
| 2022-02-22 15:00:00 | Mandiant en vedette sur la liste de la sécurité 100 de CRN \\'s 2022 Mandiant Featured on CRN\\'s 2022 Security 100 List (lien direct) |
Alors que les organisations cherchent à renforcer leur posture de sécurité et à renforcer leurs défenses contre un paysage de menace en constante évolution, Mandiant reste dédié à les équiper d'outils de pointe et de services gérés.Après tout, une sécurité efficace nécessite la fusion de la technologie et des talents.
Depuis qu'il a rejoint Mandiant, j'ai vu de première main comment nous mettons notre mission pour que chaque organisation soit sécurisée des cyber-menaces et confiant dans leur action de préparation-into.Et c'est à travers cet objectif que nous approchons de la chaîne, s'alignant avec des partenaires clés qui partagent la mise en marché aux vues similaires
As organizations seek to strengthen their security posture and bolster their defenses against a continuously evolving threat landscape, Mandiant remains dedicated to equipping them with industry-leading tools and managed services. After all, effective security requires the fusion of technology and talent. Since joining Mandiant, I\'ve seen first-hand how we put our mission-to make every organization secure from cyber threats and confident in their readiness-into action. And it is through this lens that we approach the channel, aligning with key partners who share like-minded go-to-market |
Tool Threat | ★★★ | ||
| 2022-02-21 23:22:21 | Hackers Backdoor Unpatched Microsoft SQL Database Servers with Cobalt Strike (lien direct) | Vulnerable internet-facing Microsoft SQL (MS SQL) Servers are being targeted by threat actors as part of a new campaign to deploy the Cobalt Strike adversary simulation tool on compromised hosts. "Attacks that target MS SQL servers include attacks to the environment where its vulnerability has not been patched, brute forcing, and dictionary attack against poorly managed servers," South Korean | Tool Vulnerability Threat | |||
| 2022-02-18 00:37:46 | New Linux Privilege Escalation Flaw Uncovered in Snap Package Manager (lien direct) | Multiple security vulnerabilities have been disclosed in Canonical's Snap software packaging and deployment system, the most critical of which can be exploited to escalate privilege to gain root privileges. Snaps are self-contained application packages that are designed to work on operating systems that use the Linux kernel and can be installed using a tool called snapd. Tracked | Tool | |||
| 2022-02-17 19:14:22 | How to use the ONLYOFFICE project management tool (lien direct) | Looking to manage your projects in-house but aren't sure what software to use? ONLYOFFICE includes such a tool and might serve you well. Jack Wallen shows you the ropes. | Tool | |||
| 2022-02-17 01:22:21 | This New Tool Can Retrieve Pixelated Text from Redacted Documents (lien direct) | The practice of blurring out text using a method called pixelation may not be as secure as previously thought. While the most foolproof way of concealing sensitive textual information is to use opaque black bars, other redaction methods like pixelation can achieve the opposite effect, enabling the reversal of pixelized text back into its original form. Dan Petro, a lead researcher at offensive | Tool Guideline | |||
| 2022-02-17 00:00:00 | WatchGuard et Ava6 présentent " Red SOC ", un service d\'EDR managé inédit, dédié aux PME, ETI et autres collectivités (lien direct) | Paris, le 17 février 2022 - WatchGuard® Technologies, leader mondial en matière de sécurité et d'intelligence réseau, de Wi-Fi sécurisé, d'authentification multifacteur et de protection avancée des postes de travail, et son partenaire Ava6, ESN française spécialiste de la cybersécurité, présentent un service d'EDR managé inédit, baptisé Red SOC. Le service repose sur la technologie Endpoint Protection Detection and Response (EPDR) reconnue de WatchGuard Technologies et est opéré par les experts du SOC endpoint d'Ava6, 24h sur 24 et 7 jours sur 7. Avec Red SOC, WatchGuard et Ava6 entendent rendre accessible le SOC endpoint – traditionnellement réservé aux grandes comptes – et l'EDR managé aux PME, ETI et autres collectivités souhaitant renforcer leur niveau de sécurité face aux cyberattaques et notamment les ransomwares. Pascal Le Digol, Country Manager France chez WatchGuard Technologies déclare : " Même si les entreprises ont compris qu'il était urgent de hausser le niveau de sécurité de leur système d'information, elles sont généralement confrontées à plusieurs problématiques. Les PME ont peu de moyens et de ressources à allouer à la cybersécurité, alors que les ETI et les collectivités équipées ou souhaitant s'équiper en EDR managé n'ont pas la capacité de former des équipes de sécurité capables de traiter les nombreuses alertes remontées par les solutions. Avec Ava6, nous avons eu l'idée de créer l'offre Red SOC pour permettre à ces entreprises d'accéder à une solution de sécurité de haut niveau tout en en externalisant la supervision à une équipe de professionnels. Grâce à Red SOC, nous espérons permettre à de nombreuses entreprises et collectivités d'élever leur niveau de sécurité ". Red SOC : Rendre le SOC endpoint et l'EDR managé accessibles au plus grand nombre d'entreprises et de collectivités Red SOC s'articule autour de l'offre logicielle WatchGuard Endpoint Protection Detection and Response (EPDR), et allie technologie et expertise humaine de pointe pour permettre aux entreprises de tirer le meilleur profit de leur solution EDR. La technologie WatchGuard détecte les comportements malveillants susceptibles d'intervenir sur les endpoints (ordinateur de bureau, PC portable, tablette, smartphone et serveur), tandis qu'Ava6 se charge de piloter les actions de remédiation, afin de neutraliser les attaques avant qu'elles ne se propagent dans le système d'information de l'entreprise. La solution WatchGuard joue le rôle de maillon central d'un SOC endpoint car elle collecte, enregistre et agrège les données, à savoir les logs ; une équipe d'experts en sécurité se charge dès lors de délivrer le service permettant de tirer la quintessence de la solution logicielle : en analysant les données et les événements remontés par la solution, les incidents sont qualifiés, ce qui permet d'accélérer la détection ainsi que la remédiation des attaques et autres menaces détectées. Outre la surveillance des endpoints, le suivi et la réponse aux incidents et autres alertes, l'équipe de consultants en sécurité d'Ava6 prend également en charge les mises à jour de la solution WatchGuard et son maintien en conditions de sécurité. Une offre EDR modulaire, packagée as-a-Service L'offre Red SOC est modulaire et s'adapte à la typologie et aux besoins spécifiques de l'entreprise clie | Tool Threat | ★★★ | ||
| 2022-02-15 20:01:00 | Anomali Cyber Watch: Mobile Malware Is On The Rise, APT Groups Are Working Together, Ransomware For The Individual, and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: Mobile Malware, APTs, Ransomware, Infostealers, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
What’s With The Shared VBA Code Between Transparent Tribe And Other Threat Actors?
(published: February 9, 2022)
A recent discovery has been made that links malicious VBA macro code between multiple groups, namely: Transparent Tribe, Donot Team, SideCopy, Operation Hangover, and SideWinder. These groups operate (or operated) out of South Asia and use a variety of techniques with phishing emails and maldocs to target government and military entities within India and Pakistan. The code is similar enough that it suggests cooperation between APT groups, despite having completely different goals/targets.
Analyst Comment: This research shows that APT groups are sharing TTPs to assist each other, regardless of motive or target. Files that request content be enabled to properly view the document are often signs of a phishing attack. If such a file is sent to you via a known and trusted sender, that individual should be contacted to verify the authenticity of the attachment prior to opening. Thus, any such file attachment sent by unknown senders should be viewed with the utmost scrutiny, and the attachments should be avoided and properly reported to appropriate personnel.
MITRE ATT&CK: [MITRE ATT&CK] Command and Scripting Interpreter - T1059 | [MITRE ATT&CK] Phishing - T1566
Tags: Transparent Tribe, Donot, SideWinder, Asia, Military, Government
Fake Windows 11 Upgrade Installers Infect You With RedLine Malware
(published: February 9, 2022)
Due to the recent announcement of Windows 11 upgrade availability, an unknown threat actor has registered a domain to trick users into downloading an installer that contains RedLine malware. The site, "windows-upgraded[.]com", is a direct copy of a legitimate Microsoft upgrade portal. Clicking the 'Upgrade Now' button downloads a 734MB ZIP file which contains an excess of dead code; more than likely this is to increase the filesize for bypassing any antivirus scan. RedLine is a well-known infostealer, capable of taking screenshots, using C2 communications, keylogging and more.
Analyst Comment: Any official Windows update or installation files will be downloaded through the operating system directly. If offline updates are necessary, only go through Microsoft sites and subdomains. Never update Windows from a third-party site due to this type of attack.
MITRE ATT&CK: [MITRE ATT&CK] Video Capture - T1125 | [MITRE ATT&CK] Input Capture - T1056 | [MITRE ATT&CK] Exfiltration Over C2 Channel - T1041
Tags: RedLine, Windows 11, Infostealer
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
What’s With The Shared VBA Code Between Transparent Tribe And Other Threat Actors?
(published: February 9, 2022)
A recent discovery has been made that links malicious VBA macro code between multiple groups, namely: Transparent Tribe, Donot Team, SideCopy, Operation Hangover, and SideWinder. These groups operate (or operated) out of South Asia and use a variety of techniques with phishing emails and maldocs to target government and military entities within India and Pakistan. The code is similar enough that it suggests cooperation between APT groups, despite having completely different goals/targets.
Analyst Comment: This research shows that APT groups are sharing TTPs to assist each other, regardless of motive or target. Files that request content be enabled to properly view the document are often signs of a phishing attack. If such a file is sent to you via a known and trusted sender, that individual should be contacted to verify the authenticity of the attachment prior to opening. Thus, any such file attachment sent by unknown senders should be viewed with the utmost scrutiny, and the attachments should be avoided and properly reported to appropriate personnel.
MITRE ATT&CK: [MITRE ATT&CK] Command and Scripting Interpreter - T1059 | [MITRE ATT&CK] Phishing - T1566
Tags: Transparent Tribe, Donot, SideWinder, Asia, Military, Government
Fake Windows 11 Upgrade Installers Infect You With RedLine Malware
(published: February 9, 2022)
Due to the recent announcement of Windows 11 upgrade availability, an unknown threat actor has registered a domain to trick users into downloading an installer that contains RedLine malware. The site, "windows-upgraded[.]com", is a direct copy of a legitimate Microsoft upgrade portal. Clicking the 'Upgrade Now' button downloads a 734MB ZIP file which contains an excess of dead code; more than likely this is to increase the filesize for bypassing any antivirus scan. RedLine is a well-known infostealer, capable of taking screenshots, using C2 communications, keylogging and more.
Analyst Comment: Any official Windows update or installation files will be downloaded through the operating system directly. If offline updates are necessary, only go through Microsoft sites and subdomains. Never update Windows from a third-party site due to this type of attack.
MITRE ATT&CK: [MITRE ATT&CK] Video Capture - T1125 | [MITRE ATT&CK] Input Capture - T1056 | [MITRE ATT&CK] Exfiltration Over C2 Channel - T1041
Tags: RedLine, Windows 11, Infostealer
|
Ransomware Malware Tool Vulnerability Threat Guideline | Uber APT 43 APT 36 APT-C-17 | ||
| 2022-02-15 16:15:09 | CVE-2022-23604 (lien direct) | x26-Cogs is a repository of cogs made by Twentysix for the Red Discord bot. Among these cogs is the Defender cog, a tool for Discord server moderation. A vulnerability in the Defender cog prior to version 1.10.0 allows users with admin privileges to issue commands as other users who share the same server. If a bot owner shares the same server as the attacker, it is possible for the attacker to issue bot-owner restricted commands. The issue has been patched in version 1.10.0. One may unload the Defender cog as a workaround. | Tool Vulnerability | |||
| 2022-02-15 15:00:00 | La nouvelle offre de validation de la sécurité mandiante avantage aide les organisations à répondre avec confiance à la question: sommes-nous en mesure d'empêcher une attaque de ransomware? New Mandiant Advantage Security Validation Offering Helps Organizations Confidently Answer the Question: Are We Able to Prevent a Ransomware Attack? (lien direct) |
Les titres quotidiens disent que la fréquence et la prolifération des ransomwares accélèrent.Non seulement les intervenants incidents de Mandiant ont vu des attaques de ransomwares augmenter considérablement ces dernières années, mais les rançons eux-mêmes sont passés de 416 millions de dollars pour tous les 2020 à 590 millions de dollars pour les six premiers mois de 2021, selon le U.S.Trésor .Les organisations, grandes et petites, reconnaissent que sans les bons outils en place, ils pourraient être la prochaine victime.
Les acteurs de la menace continuent d'augmenter leur jeu avec des attaques de plus en plus agressives et sophistiquées, passant des ransomwares standard
Daily headlines say it all-the frequency and proliferation of ransomware is accelerating. Not only have Mandiant\'s incident responders seen ransomware attacks increase dramatically in recent years, ransoms themselves have increased from $416 million for all of 2020 to $590 million for the first six months of 2021, according to the U.S. Treasury. Organizations, large and small, recognize that without the right tools in place they could be the next victim. Threat actors continue to up their game with increasingly aggressive and sophisticated attacks, shifting from standard ransomware |
Ransomware Tool | ★★★ | ||
| 2022-02-10 20:15:07 | CVE-2022-23630 (lien direct) | Gradle is a build tool with a focus on build automation and support for multi-language development. In some cases, Gradle may skip that verification and accept a dependency that would otherwise fail the build as an untrusted external artifact. This occurs when dependency verification is disabled on one or more configurations and those configurations have common dependencies with other configurations that have dependency verification enabled. If the configuration that has dependency verification disabled is resolved first, Gradle does not verify the common dependencies for the configuration that has dependency verification enabled. Gradle 7.4 fixes that issue by validating artifacts at least once if they are present in a resolved configuration that has dependency verification active. For users who cannot update either do not use `ResolutionStrategy.disableDependencyVerification()` and do not use plugins that use that method to disable dependency verification for a single configuration or make sure resolution of configuration that disable that feature do not happen in builds that resolve configuration where the feature is enabled. | Tool | |||
| 2022-02-10 10:00:00 | CISO Stories Podcast: Creating Security Budget Where There is No Budget (lien direct) |
 Over the years, security departments acquire tool after tool, sometimes integrated, and many times under-utilized. Kevin Richards, President at Secure Systems Innovation, walks through a very creative method for getting the budget you need, and explains how to leverage the current environment to “find” new sources of funding for the right cybersecurity investments - check it out...
Over the years, security departments acquire tool after tool, sometimes integrated, and many times under-utilized. Kevin Richards, President at Secure Systems Innovation, walks through a very creative method for getting the budget you need, and explains how to leverage the current environment to “find” new sources of funding for the right cybersecurity investments - check it out... |
Tool | |||
| 2022-02-07 23:31:56 | How to use DuckDuckGo on your PC and mobile devices (lien direct) | You can use the privacy-oriented search tool through desktop browser extensions and a mobile app. | Tool | |||
| 2022-02-07 22:01:44 | Google Cloud Gets Virtual Machine Threat Detection (lien direct) | Google on Monday announced the public preview of a new tool to help identify threats within virtual machines (VMs) running on its Google Cloud infrastructure. | Tool Threat | |||
| 2022-02-07 19:13:06 | (Déjà vu) Avast released a free decryptor for TargetCompany ransomware (lien direct) | Cybersecurity firm Avast has released a decryption tool to allow victims of TargetCompany ransomware to recover their files for free. Czech cybersecurity software firm Avast has released a decryption tool that could allow victims of the TargetCompany ransomware to recover their files for free under certain circumstances. The experts warn that the decryptor consumes most of the […] | Tool | |||
| 2022-02-07 18:33:58 | Linux Privilege Escalation: PwnKit (CVE 2021-4034) (lien direct) | Introduction Team Qualys discovered a local privilege escalation vulnerability in PolicyKit's (polkit) setuid tool pkexec which allows low-level users to run commands as privileged users. | Tool Vulnerability | |||
| 2022-02-06 13:49:13 | Argo CD flaw could allow stealing sensitive data from Kubernetes Apps (lien direct) | A flaw in Argo CD tool for Kubernetes could be exploited by attackers to steal sensitive data from Kubernetes Apps. A zero-day vulnerability, tracked as CVE-2022-24348, in the Argo CD tool for Kubernetes could be exploited by attackers to steal sensitive data from Kubernetes Apps, including passwords and API keys. The flaw received a CVSS […] | Tool | Uber | ||
| 2022-02-06 00:03:38 | Working with PDFs is a breeze with PDF Converter Pro (lien direct) | PDF Converter Pro is an all-in-one tool that allows you create or convert PDF documents into a variety of formats or from a variety of formats with ease. | Tool | |||
| 2022-02-05 21:48:25 | New Argo CD Bug Could Let Hackers Steal Secret Info from Kubernetes Apps (lien direct) | Users of the Argo continuous deployment (CD) tool for Kubernetes are being urged to push through updates after a zero-day vulnerability was found that could allow an attacker to extract sensitive information such as passwords and API keys. The flaw, tagged as CVE-2022-24348 (CVSS score: 7.7), affects all versions and has been addressed in versions 2.3.0, 2.2.4, and 2.1.9. Cloud security firm | Tool Vulnerability | Uber | ||
| 2022-02-04 15:23:32 | Ditto wants to help you sync critical data in real time, even without an internet connection (lien direct) | If fractured databases have ever created a headache for your business, Ditto may have the offline syncing tool you've been looking for. | Tool | |||
| 2022-02-04 13:19:05 | (Déjà vu) Retail giant Target open sources Merry Maker e-skimmer detection tool (lien direct) | Retail giant Target is going to open-source an internal tool, dubbed Merry Maker, designed to detect e-skimming attacks. Retail giant Target announced the release in open-source of an internal tool, dubbed Merry Maker, designed to detect e-skimming attacks. Merry Maker is a tool designed by Target security developers Eric Brandel and Caleb Walch (@ebrandel and @cawalch) to […] | Tool | |||
| 2022-02-04 11:42:27 | Target Open Sources Web Skimmer Detection Tool (lien direct) | Retail giant Target this week announced the open source availability of an internal tool designed for the detection of web skimming attacks. | Tool | |||
| 2022-02-03 02:58:35 | FBI Confirms It Bought Spyware From Israel\'s NSO Group (lien direct) | The FBI has confirmed purchasing NSO Group's powerful spyware tool Pegasus, whose chronic abuse to surveil journalists, dissidents and human rights activists has long been established. It suggested its motivation was to “stay abreast of emerging technologies and tradecraft.” | Tool | |||
| 2022-02-02 17:30:00 | Online Ad Association Fined for Privacy Violation (lien direct) | Belgian data watchdog penalizes IAB Europe over ad-targeting tool | Tool | |||
| 2022-02-02 12:15:07 | CVE-2020-26208 (lien direct) | JHEAD is a simple command line tool for displaying and some manipulation of EXIF header data embedded in Jpeg images from digital cameras. In affected versions there is a heap-buffer-overflow on jhead-3.04/jpgfile.c:285 ReadJpegSections. Crafted jpeg images can be provided to the user resulting in a program crash or potentially incorrect exif information retrieval. Users are advised to upgrade. There is no known workaround for this issue. | Tool | |||
| 2022-02-02 09:46:34 | SEO poisoning pushes malware-laced Zoom, TeamViewer, Visual Studio installers (lien direct) | A new SEO poisoning campaign is underway, dropping the Batloader and Atera Agent malware onto the systems of targeted professionals searching for productivity tool downloads, such as Zoom, TeamViewer, and Visual Studio. [...] | Malware Tool | |||
| 2022-02-01 15:15:07 | CVE-2021-44746 (lien direct) | UNIVERGE DT 820 V3.2.7.0 and prior, UNIVERGE DT 830 V5.2.7.0 and prior, UNIVERGE DT 930 V2.4.0.0 and prior, IP Phone Manager V8.9.1 and prior, Data Maintenance Tool for DT900 Series V5.3.0.0 and prior, Data Maintenance Tool for DT800 Series V4.2.0.0 and prior allows a remote attacker who can access to the internal network, the configuration information may be obtained. | Tool | |||
| 2022-02-01 15:00:00 | Zoom pour vous - Empoisonnement du référencement pour distribuer Batloader et Atera Agent Zoom For You - SEO Poisoning to Distribute BATLOADER and Atera Agent (lien direct) |
Tout en défendant nos clients contre les menaces, manage managedDéfense continue de voir de nouvelles menaces qui abusent de la confiance dans les outils et les produits légitimes pour mener à bien leurs attaques.Ces attaques sont efficaces pour obtenir des défenses de sécurité passées et rester non détecté dans un réseau.
Grâce à la chasse à la menace proactive, notre équipe de première ligne de défense gérée a découvert une campagne qui a utilisé l'empoisonnement d'optimisation des moteurs de recherche (SEO) pour conduire les victimes à télécharger le Batloader MALWWare pour le compromis initial.Nous avons également observé une technique d'évasion de défense astucieuse à l'aide de mshta.exe, un utilitaire Windows-Native
While defending our customers against threats, Mandiant Managed Defense continues to see new threats that abuse trust in legitimate tools and products to carry out their attacks. These attacks are effective in getting past security defenses and staying undetected in a network. Through proactive threat hunting, our Managed Defense frontline team uncovered a campaign that used search engine optimization (SEO) poisoning to lead victims to download the BATLOADER malware for the initial compromise. We also observed a crafty defense evasion technique using mshta.exe, a Windows-native utility |
Malware Tool Threat | ★★★ | ||
| 2022-02-01 14:37:29 | CyberheistNews Vol 12 #05 [Heads Up] DHS Sounds Alarm on New Russian Destructive Disk Wiper Attack Potential (lien direct) |
![CyberheistNews Vol 12 #05 [Heads Up] DHS Sounds Alarm on New Russian Destructive Disk Wiper Attack Potential](https://blog.knowbe4.com/hubfs/Stu_Headshot_2021_resize.png)
|
Ransomware Malware Hack Tool Threat Guideline | NotPetya NotPetya Wannacry Wannacry APT 27 APT 27 | ||
| 2022-01-31 17:49:42 | Microsoft PowerToys adds Mouse and File Explorer utilities (lien direct) | Microsoft has updated PowerToys with three new utilities, including a new mouse crosshair tool to quickly find the pointer on the screen and two new File Explorer add-ons. [...] | Tool | |||
| 2022-01-31 15:33:58 | No, a researcher didn\'t find Olympics app spying on you (lien direct) | For the Beijing 2022 Winter Olympics, the Chinese government requires everyone to download an app onto their phone. It has many security/privacy concerns, as CitizenLab documents. However, another researcher goes further, claiming his analysis proves the app is recording all audio all the time. His analysis is fraudulent. He shows a lot of technical content that looks plausible, but nowhere does he show anything that substantiates his claims.Average techies may not be able to see this. It all looks technical. Therefore, I thought I'd describe one example of the problems with this data -- something the average techie can recognize.His "evidence" consists screenshots from reverse-engineering tools, with red arrows pointing to the suspicious bits. An example of one of these screenshots is this on: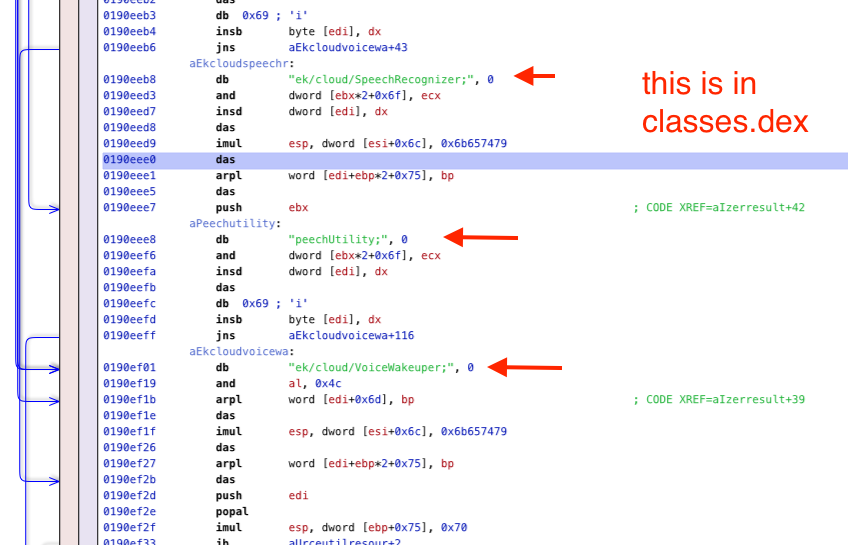 This screenshot is that of a reverse-engineering tool (Hopper, I think) that takes code and "disassembles" it. When you dump something into a reverse-engineering tool, it'll make a few assumptions about what it sees. These assumptions are usually wrong. There's a process where the human user looks at the analyzed output, does a "sniff-test" on whether it looks reasonable, and works with the tool until it gets the assumptions correct.That's the red flag above: the researcher has dumped the results of a reverse-engineering tool without recognizing that something is wrong in the analysis.It fails the sniff test. Different researchers will notice different things first. Famed google researcher Tavis Ormandy points out one flaw. In this post, I describe what jumps out first to me. That would be the 'imul' (multiplication) instruction shown in the blowup below: This screenshot is that of a reverse-engineering tool (Hopper, I think) that takes code and "disassembles" it. When you dump something into a reverse-engineering tool, it'll make a few assumptions about what it sees. These assumptions are usually wrong. There's a process where the human user looks at the analyzed output, does a "sniff-test" on whether it looks reasonable, and works with the tool until it gets the assumptions correct.That's the red flag above: the researcher has dumped the results of a reverse-engineering tool without recognizing that something is wrong in the analysis.It fails the sniff test. Different researchers will notice different things first. Famed google researcher Tavis Ormandy points out one flaw. In this post, I describe what jumps out first to me. That would be the 'imul' (multiplication) instruction shown in the blowup below: It's obviously ASCII. In other words, it's a series of bytes. The tool has tried to interpret these bytes as Intel x86 instructions (like 'and', 'insd', 'das', 'imul', etc.). But it's obviously not Intel x86, because those instructions make no sense.That 'imul' instruction is multiplying something by the (hex) number 0x6b657479. That doesn't look like a number -- it looks like four lower-case ASCII letters. ASCII lower-case letters are in the range 0x61 through 0x7A, so it's not the single 4-byte number 0x6b657479 but the 4 individual bytes 6b 65 74 79, which map to the ASCII letters 'k', 'e', 't It's obviously ASCII. In other words, it's a series of bytes. The tool has tried to interpret these bytes as Intel x86 instructions (like 'and', 'insd', 'das', 'imul', etc.). But it's obviously not Intel x86, because those instructions make no sense.That 'imul' instruction is multiplying something by the (hex) number 0x6b657479. That doesn't look like a number -- it looks like four lower-case ASCII letters. ASCII lower-case letters are in the range 0x61 through 0x7A, so it's not the single 4-byte number 0x6b657479 but the 4 individual bytes 6b 65 74 79, which map to the ASCII letters 'k', 'e', 't |
Tool | |||
| 2022-01-31 13:03:41 | The Third Building Block for the SOC of the Future: Balanced Automation (lien direct) | When automation is balanced between humans and machines, we can ensure teams always have the best tool for the job | Tool | |||
| 2022-01-31 12:18:55 | Twelve-Year-Old Linux Vulnerability Discovered and Patched (lien direct) | It’s a privilege escalation vulnerability: Linux users on Tuesday got a major dose of bad news — a 12-year-old vulnerability in a system tool called Polkit gives attackers unfettered root privileges on machines running most major distributions of the open source operating system. Previously called PolicyKit, Polkit manages system-wide privileges in Unix-like OSes. It provides a mechanism for nonprivileged processes to safely interact with privileged processes. It also allows users to execute commands with high privileges by using a component called pkexec, followed by the command... | Tool Vulnerability | |||
| 2022-01-28 20:15:12 | CVE-2021-4034 (lien direct) | A local privilege escalation vulnerability was found on polkit's pkexec utility. The pkexec application is a setuid tool designed to allow unprivileged users to run commands as privileged users according predefined policies. The current version of pkexec doesn't handle the calling parameters count correctly and ends trying to execute environment variables as commands. An attacker can leverage this by crafting environment variables in such a way it'll induce pkexec to execute arbitrary code. When successfully executed the attack can cause a local privilege escalation given unprivileged users administrative rights on the target machine. | Tool Vulnerability | |||
| 2022-01-27 16:00:33 | .NET Remoting Revisited (lien direct) | .NET Remoting is the built-in architecture for remote method invocation in .NET. It is also the origin of the (in-)famous BinaryFormatter and SoapFormatter serializers and not just for that reason a promising target to watch for. This blog post attempts to give insights into its features, security measures, and especially its weaknesses/vulnerabilities that often result in remote code execution. We're also introducing major additions to the ExploitRemotingService tool, a new ObjRef gadget for YSoSerial.Net, and finally a RogueRemotingServer as counterpart to the ObjRef gadget. If you already understand the internal of .NET Remoting, you may skip the introduction and proceed right with Security Features, Pitfalls, and Bypasses. Introduction .NET Remoting is deeply integrated into the .NET Framework and allows invocation of methods across so called remoting boundaries. These can be different app domains within a single process, different processes on the same computer, or different processes on different computers. Supported transports between the client and server are HTTP, IPC (named pipes), and TCP. Here is a simple example for illustration: the server creates and registers a transport server channel and then registers the class as a service with a well-known name at the server's registry: var channel = new TcpServerChannel(12345);ChannelServices.RegisterChannel(channel);RemotingConfiguration.RegisterWellKnownServiceType( typeof(MyRemotingClass), "MyRemotingClass"); Then a client just needs the URL of the registered service to do remoting with the server: var remote = (MyRemotingClass)RemotingServices.Connect( typeof(MyRemotingClass), "tcp://remoting-server:12345/MyRemotingClass"); With this, every invocation of a method or property accessor on remote gets forwarded to the remoting server, executed there, and the result gets returned to the client. This all happens transparently to the developer. And although .NET Remoting has already been deprecated with the release of .NET Framework 3.0 in 2009 and is no longer available on .NET Core and .NET 5+, it is still around, even in contemporary enterprise level software products. Remoting Internals If you are interested in how .NET Remoting works under the hood, here are some insights. In simple terms: when the client connects to the remoting object provided by the server, it creates a RemotingProxy that implements the specified type MyRemotingClass. All method invocations on remote at the client (except for GetType() and GetHashCode()) will get sent to the server as remoting calls. When a method gets invoked on remote, the proxy creates a MethodCall object that holds the information of the method and passed parameters. It is then passed to a chain of sinks that prepare the MethodCall and handle the remoting communication with the server over the given transport. On the server side, the received request is also passed to a chain of sinks that reverses the process, which also includes deserialization of the MethodCall object. It ends in a dispatcher sink, which invokes the actual implementation of the method with the passed parameters. The result of the method invocation is then put in a MethodResponse object and gets returned to the client where the client s | Tool | |||
| 2022-01-26 22:39:34 | TrickBot Crashes Security Researchers\' Browsers in Latest Upgrade (lien direct) | The malware has added an anti-debugging tool that crashes browser tabs when researchers use code beautifying for analysis. | Malware Tool | |||
| 2022-01-26 16:09:43 | New Open Source Tool Helps Identify EtherNet/IP Stacks for ICS Research, Analysis (lien direct) | Industrial cybersecurity firm Claroty on Wednesday announced a new open source tool designed for identifying EtherNet/IP stacks. According to the company, the new “EtherNet/IP & CIP Stack Detector” tool can be useful to security researchers, operational technology (OT) engineers, and asset owners. | Tool | |||
| 2022-01-25 16:00:00 | Anomali Cyber Watch: MoonBounce, AccessPress, QR Code Scams and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Linux Malware, Supply-Chain Attacks, Malspam, Phishing, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
FBI Warns Of Malicious QR Codes Used To Steal Your Money
(published: January 23, 2022)
The Federal Bureau of Investigation (FBI) recently released a notice that malicious QR codes have been found in the wild. These codes, when scanned, will redirect the victim to a site where they are prompted to enter personal and payment details. The site will then harvest these credentials for cybercriminals to commit fraud and empty bank accounts. This threat vector has been seen in Germany as of December 2021.
Analyst Comment: Always be sure to check that emails have been sent from a legitimate source, and that any financial details or method of payment is done through the website. While QR codes are useful and being used by businesses more often, it is easy for cybercriminals to perform this kind of scam. If scanning a physical QR code, ensure the code has not been replaced with a sticker placed on top of the original code. Check the final URL to make sure it is the intended site and looks authentic.
MITRE ATT&CK: [MITRE ATT&CK] Phishing - T1566
Tags: EU & UK, Banking and Finance
MoonBounce: The Dark Side Of UEFI Firmware
(published: January 20, 2022)
Kaspersky has reported that in September 2021, a bootloader malware infection had been discovered that embeds itself into UEFI firmware. The malware patches existing UEFI drivers and resides in the SPI flash memory located on the motherboard. This means that it will persist even if the hard drive is replaced. Code snippets and IP addresses link the activity to APT41, a group that is operated by a group of Chinese-speaking individuals. MoonBounce is highly sophisticated and very difficult to detect.
Analyst Comment: Systems should be configured to take advantage of Trusted Platform Module (TPM) hardware security chips to secure their systems' boot image and firmware, where available. Secure boot is also a viable option to mitigate against attacks that would patch, reconfigure, or flash existing UEFI firmware to implant malicious code.
MITRE ATT&CK: [MITRE ATT&CK] Pre-OS Boot - T1542 | [MITRE ATT&CK] Data Obfuscation - T1001 | [MITRE ATT&CK] Data Encoding - T1132 | [MITRE ATT&CK] Exploitation of Remote Services - T1210 | [MITRE ATT&CK] Remote Services - T1021 | [MITRE ATT&CK] Shared Modules - T1129 | [MITRE ATT&CK] Hijack Execution Flow - T1574 |
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
FBI Warns Of Malicious QR Codes Used To Steal Your Money
(published: January 23, 2022)
The Federal Bureau of Investigation (FBI) recently released a notice that malicious QR codes have been found in the wild. These codes, when scanned, will redirect the victim to a site where they are prompted to enter personal and payment details. The site will then harvest these credentials for cybercriminals to commit fraud and empty bank accounts. This threat vector has been seen in Germany as of December 2021.
Analyst Comment: Always be sure to check that emails have been sent from a legitimate source, and that any financial details or method of payment is done through the website. While QR codes are useful and being used by businesses more often, it is easy for cybercriminals to perform this kind of scam. If scanning a physical QR code, ensure the code has not been replaced with a sticker placed on top of the original code. Check the final URL to make sure it is the intended site and looks authentic.
MITRE ATT&CK: [MITRE ATT&CK] Phishing - T1566
Tags: EU & UK, Banking and Finance
MoonBounce: The Dark Side Of UEFI Firmware
(published: January 20, 2022)
Kaspersky has reported that in September 2021, a bootloader malware infection had been discovered that embeds itself into UEFI firmware. The malware patches existing UEFI drivers and resides in the SPI flash memory located on the motherboard. This means that it will persist even if the hard drive is replaced. Code snippets and IP addresses link the activity to APT41, a group that is operated by a group of Chinese-speaking individuals. MoonBounce is highly sophisticated and very difficult to detect.
Analyst Comment: Systems should be configured to take advantage of Trusted Platform Module (TPM) hardware security chips to secure their systems' boot image and firmware, where available. Secure boot is also a viable option to mitigate against attacks that would patch, reconfigure, or flash existing UEFI firmware to implant malicious code.
MITRE ATT&CK: [MITRE ATT&CK] Pre-OS Boot - T1542 | [MITRE ATT&CK] Data Obfuscation - T1001 | [MITRE ATT&CK] Data Encoding - T1132 | [MITRE ATT&CK] Exploitation of Remote Services - T1210 | [MITRE ATT&CK] Remote Services - T1021 | [MITRE ATT&CK] Shared Modules - T1129 | [MITRE ATT&CK] Hijack Execution Flow - T1574 | |
Ransomware Malware Tool Vulnerability Threat Guideline | APT 41 APT 28 | ||
| 2022-01-24 08:15:09 | CVE-2021-24976 (lien direct) | The Smart SEO Tool WordPress plugin before 3.0.6 does not sanitise and escape the search parameter before outputting it back in an attribute when the TDK optimisation setting is enabled, leading to a Reflected Cross-Site Scripting | Tool Guideline | |||
| 2022-01-23 17:15:41 | CFRipper – CloudFormation Security Scanning & Audit Tool (lien direct) |  CFRipper is a Python-based Library and CLI security analyzer that functions as an AWS CloudFormation security scanning and audit tool, it aims to prevent vulnerabilities from getting to production infrastructure through vulnerable CloudFormation scripts.
You can use CFRipper to prevent deploying insecure AWS resources into your Cloud environment. You can write your own compliance checks by adding new custom plugins.
CFRipper should be part of your CI/CD pipeline. It runs just before a CloudFormation stack is deployed or updated and if the CloudFormation script fails to pass the security check it fails the deployment and notifies the team that owns the stack.
Read the rest of CFRipper – CloudFormation Security Scanning & Audit Tool now! Only available at Darknet. CFRipper is a Python-based Library and CLI security analyzer that functions as an AWS CloudFormation security scanning and audit tool, it aims to prevent vulnerabilities from getting to production infrastructure through vulnerable CloudFormation scripts.
You can use CFRipper to prevent deploying insecure AWS resources into your Cloud environment. You can write your own compliance checks by adding new custom plugins.
CFRipper should be part of your CI/CD pipeline. It runs just before a CloudFormation stack is deployed or updated and if the CloudFormation script fails to pass the security check it fails the deployment and notifies the team that owns the stack.
Read the rest of CFRipper – CloudFormation Security Scanning & Audit Tool now! Only available at Darknet.
|
Tool | |||
| 2022-01-20 00:00:00 | Rapport WatchGuard Threat Lab : 2021, l\'année de l\'explosion du nombre de malwares et ransomwares ciblant les endpoints (lien direct) | Paris, le 19 janvier 2022 - WatchGuard® Technologies, leader mondial en matière de sécurité et d\'intelligence réseau, de Wi-Fi sécurisé, d\'authentification multifacteur et de protection avancée des postes de travail, publie aujourd\'hui les résultats de son dernier rapport trimestriel sur la sécurité Internet. Ce rapport met en évidence les principales tendances en matière de malwares et menaces pour la sécurité réseau au troisième trimestre 2021, analysées par les chercheurs du Threat Lab de WatchGuard. Les données indiquent que si le volume total de détections de malwares dans le périmètre a diminué par rapport aux sommets atteints au trimestre précédent, les détections de malwares sur les endpoints ont quant à elles déjà dépassé le volume total observé en 2020 (les données du quatrième trimestre 2021 n\'ayant pas encore été communiquées). En outre, un pourcentage important de malwares continue de mettre à profit des connexions chiffrées, confirmant la tendance des trimestres précédents. Les rapports de recherche trimestriels de WatchGuard sont basés sur des données anonymisées provenant d\'appliances Firebox actives chez les clients WatchGuard et dont les propriétaires ont choisi de partager les données pour soutenir directement les efforts de recherche du Threat Lab. Au troisième trimestre 2021, WatchGuard a bloqué plus de 16,6 millions de variantes de malwares et près de 4 millions de menaces réseau. Corey Nachreiner, Chief Security Officer chez WatchGuard commente : " Alors que le volume total d\'attaques réseau a légèrement diminué au troisième trimestre, le nombre de malwares détectés par terminal a progressé pour la première fois depuis le début de la pandémie. Mais il est important que les entreprises voient plus loin que les fluctuations à court terme pour se concentrer sur les tendances persistantes et préoccupantes telles que l\'utilisation accélérée des connexions chiffrées dans les attaques Zero-Day ". Parmi ses conclusions les plus notables, le rapport sur la sécurité Internet du troisième trimestre 2021 de WatchGuard révèle ce qui suit : Près de la moitié des malwares Zero-Day sont désormais diffusés via des connexions chiffrées – Alors que le nombre total de malwares 0-Day a connu une augmentation modeste de 3 % pour atteindre 67,2 % de l\'ensemble des malwares au troisième trimestre, le pourcentage de malwares diffusés via le protocole TLS (Transport Layer Security) a grimpé de 31,6 % à 47 %. Même si une moindre proportion des attaques Zero-Day chiffrées sont considérées comme avancées, la situation reste préoccupante d\'après les données de WatchGuard : celles-ci montrent en effet qu\'un grand nombre d\'organisations ne déchiffrent pas ces connexions et ont donc une mauvaise visibilité sur la quantité de malwares qui pénètrent leurs réseaux. Les cybercriminels ciblent les nouvelles vulnérabilités au fur et à mesure que les utilisateurs passent à des versions plus récentes de Microsoft Windows et Office – Si les vulnérabilités non corrigées des anciens logiciels restent un terrain de chasse prisé des cybercriminels, ces derniers cherchent également à exploiter les faiblesses des toutes dernières versions des produits Microsoft les plus répandus. Au troisième trimestre, CVE-2018-0802, qui exploite une vulné | Ransomware Tool Threat | ★★★ | ||
| 2022-01-19 22:45:00 | Anomali Cyber Watch: Russia-Sponsored Cyber Threats, China-Based Earth Lusca Active in Cyberespionage and Cybertheft, BlueNoroff Hunts Cryptocurrency-Related Businesses, and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, China, HTTP Stack, Malspam, North Korea, Phishing, Russia and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Earth Lusca Employs Sophisticated Infrastructure, Varied Tools and Techniques
(published: January 17, 2022)
The Earth Lusca threat group is part of the Winnti cluster. It is one of different Chinese groups that share aspects of their tactics, techniques, and procedures (TTPs) including the use of Winnti malware. Earth Lusca were active throughout 2021 committing both cyberespionage operations against government-connected organizations and financially-motivated intrusions targeting gambling and cryptocurrency-related sectors. For intrusion, the group tries different ways in including: spearphishing, watering hole attacks, and exploiting publicly facing servers. Cobalt Strike is one of the group’s preferred post-exploitation tools. It is followed by the use of the BioPass RAT, the Doraemon backdoor, the FunnySwitch backdoor, ShadowPad, and Winnti. The group employs two separate infrastructure clusters, first one is rented Vultr VPS servers used for command-and-control (C2), second one is compromised web servers used to scan for vulnerabilities, tunnel traffic, and Cobalt Strike C2.
Analyst Comment: Earth Lusca often relies on tried-and-true techniques that can be stopped by security best practices, such as avoiding clicking on suspicious email/website links and or reacting on random banners urging to update important public-facing applications. Don’t be tricked to download Adobe Flash update, it was discontinued at the end of December 2020. Administrators should keep their important public-facing applications (such as Microsoft Exchange and Oracle GlassFish Server) updated.
MITRE ATT&CK: [MITRE ATT&CK] Drive-by Compromise - T1189 | [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] Phishing - T1566 | [MITRE ATT&CK] Command and Scripting Interpreter - T1059 | [MITRE ATT&CK] Scheduled Task - T1053 | [MITRE ATT&CK] System Services - T1569 | [MITRE ATT&CK] Windows Management Instrumentation - T1047 | [MITRE ATT&CK] Account Manipulation - T1098 | [MITRE ATT&CK] BITS Jobs - T1197 | [MITRE ATT&CK] Create Account - T1136 | [MITRE ATT&CK] Create or Modify System Process - T1543 | [MITRE ATT&CK] External Remote Services - T1133 | [MITRE ATT&CK] Hijack Execution Flow
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Earth Lusca Employs Sophisticated Infrastructure, Varied Tools and Techniques
(published: January 17, 2022)
The Earth Lusca threat group is part of the Winnti cluster. It is one of different Chinese groups that share aspects of their tactics, techniques, and procedures (TTPs) including the use of Winnti malware. Earth Lusca were active throughout 2021 committing both cyberespionage operations against government-connected organizations and financially-motivated intrusions targeting gambling and cryptocurrency-related sectors. For intrusion, the group tries different ways in including: spearphishing, watering hole attacks, and exploiting publicly facing servers. Cobalt Strike is one of the group’s preferred post-exploitation tools. It is followed by the use of the BioPass RAT, the Doraemon backdoor, the FunnySwitch backdoor, ShadowPad, and Winnti. The group employs two separate infrastructure clusters, first one is rented Vultr VPS servers used for command-and-control (C2), second one is compromised web servers used to scan for vulnerabilities, tunnel traffic, and Cobalt Strike C2.
Analyst Comment: Earth Lusca often relies on tried-and-true techniques that can be stopped by security best practices, such as avoiding clicking on suspicious email/website links and or reacting on random banners urging to update important public-facing applications. Don’t be tricked to download Adobe Flash update, it was discontinued at the end of December 2020. Administrators should keep their important public-facing applications (such as Microsoft Exchange and Oracle GlassFish Server) updated.
MITRE ATT&CK: [MITRE ATT&CK] Drive-by Compromise - T1189 | [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] Phishing - T1566 | [MITRE ATT&CK] Command and Scripting Interpreter - T1059 | [MITRE ATT&CK] Scheduled Task - T1053 | [MITRE ATT&CK] System Services - T1569 | [MITRE ATT&CK] Windows Management Instrumentation - T1047 | [MITRE ATT&CK] Account Manipulation - T1098 | [MITRE ATT&CK] BITS Jobs - T1197 | [MITRE ATT&CK] Create Account - T1136 | [MITRE ATT&CK] Create or Modify System Process - T1543 | [MITRE ATT&CK] External Remote Services - T1133 | [MITRE ATT&CK] Hijack Execution Flow |
Ransomware Malware Tool Vulnerability Threat Patching Guideline | APT 41 APT 38 APT 29 APT 28 APT 28 | ||
| 2022-01-19 21:15:08 | CVE-2021-23843 (lien direct) | The Bosch software tools AccessIPConfig.exe and AmcIpConfig.exe are used to configure certains settings in AMC2 devices. The tool allows putting a password protection on configured devices to restrict access to the configuration of an AMC2. An attacker can circumvent this protection and make unauthorized changes to configuration data on the device. An attacker can exploit this vulnerability to manipulate the device\'s configuration or make it unresponsive in the local network. The attacker needs to have access to the local network, typically even the same subnet. | Tool Vulnerability | |||
| 2022-01-19 10:00:00 | Reducing Security Risks in Open Source Software at Scale: Scorecards Launches V4 (lien direct) |  Posted by Laurent Simon and Azeem Shaikh, Google Open Source Security Team (GOSST) Since our July announcement of Scorecards V2, the Scorecards project-an automated security tool to flag risky supply chain practices in open source projects-has grown steadily to over 40 unique contributors and 18 implemented security checks. Today we are proud to announce the V4 release of Scorecards, with larger scaling, a new security check, and a new Scorecards GitHub Action for easier security automation.The Scorecards Action is released in partnership with GitHub and is available from GitHub's Marketplace. The Action makes using Scorecards easier than ever: it runs automatically on repository changes to alert developers about risky supply-chain practices. Maintainers can view the alerts on GitHub's code scanning dashboard, which is available for free to public repositories on GitHub.com and via GitHub Advanced Security for private repositories. Additionally, we have scaled our weekly Scorecards scans to over one million GitHub repositories, and have partnered with the Open Source Insights website for easy user access to the data. For more details about the release, including the new Dangerous-Workflow security check, visit the OpenSSF's official blog post here. Posted by Laurent Simon and Azeem Shaikh, Google Open Source Security Team (GOSST) Since our July announcement of Scorecards V2, the Scorecards project-an automated security tool to flag risky supply chain practices in open source projects-has grown steadily to over 40 unique contributors and 18 implemented security checks. Today we are proud to announce the V4 release of Scorecards, with larger scaling, a new security check, and a new Scorecards GitHub Action for easier security automation.The Scorecards Action is released in partnership with GitHub and is available from GitHub's Marketplace. The Action makes using Scorecards easier than ever: it runs automatically on repository changes to alert developers about risky supply-chain practices. Maintainers can view the alerts on GitHub's code scanning dashboard, which is available for free to public repositories on GitHub.com and via GitHub Advanced Security for private repositories. Additionally, we have scaled our weekly Scorecards scans to over one million GitHub repositories, and have partnered with the Open Source Insights website for easy user access to the data. For more details about the release, including the new Dangerous-Workflow security check, visit the OpenSSF's official blog post here.
|
Tool | |||
| 2022-01-19 06:39:32 | Russian Hackers Heavily Using Malicious Traffic Direction System to Distribute Malware (lien direct) | Potential connections between a subscription-based crimeware-as-a-service (Caas) solution and a cracked copy of Cobalt Strike have been established in what the researchers suspect is being offered as a tool for its customers to stage post-exploitation activities. Prometheus, as the service is called, first came to light in August 2021 when cybersecurity company Group-IB disclosed details of | Malware Tool |
To see everything:
Our RSS (filtrered)
