What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2016-11-30 06:40:00 | Who\'s on your IT security dream team? (lien direct) | Getting the gang together Image by ThinkstockLast month, I presented you a chamber of horrors-the worst people you meet doing IT security, many of them your friends and, sadly, co-workers. But I don't like to dwell on the negative! So I asked a slew of IT pros about the best people, the ones they want on their side when facing down the toughest security challenges. There are a number of important roles to fill, and I'm not just talking about job titles: I mean attitudes, and abilities that verge on superpowers. IT security is a team sport, so who do you want on your team?To read this article in full or to leave a comment, please click here Image by ThinkstockLast month, I presented you a chamber of horrors-the worst people you meet doing IT security, many of them your friends and, sadly, co-workers. But I don't like to dwell on the negative! So I asked a slew of IT pros about the best people, the ones they want on their side when facing down the toughest security challenges. There are a number of important roles to fill, and I'm not just talking about job titles: I mean attitudes, and abilities that verge on superpowers. IT security is a team sport, so who do you want on your team?To read this article in full or to leave a comment, please click here |
Guideline | |||
| 2016-11-29 08:31:00 | Goodbye SIEM, hello SOAPA (lien direct) | Security Information and Event Management (SIEM) systems have been around for a dozen years or so. During that timeframe, SIEMs evolved from perimeter security event correlation tools to GRC platforms to security analytics systems. Early vendors such as eSecurity, GuardedNet, Intellitactics and NetForensics are distant memories. Today's SIEM market is now dominated by a few leaders: LogRhythm, McAfee (aka: Nitro Security), HP (aka: ArcSight), IBM (aka: QRadar) and Splunk.Of course, there is a community of innovative upstarts that believe SIEM is a legacy technology. They proclaim that log management and event correlation can't keep up with the pace of cybersecurity today, thus you need new technologies such as artificial intelligence, machine learning algorithms and neural networks to consume, process, and analyze security data in real time. To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-11-28 11:38:00 | Google security expert says antivirus apps don\'t work (lien direct) | A senior security engineer at Google told a hacker conference that traditional antivirus apps that use intrusion detection are useless and companies should switch to meaningful methods such as whitelisting applications. At Kiwicon X, the New Zealand equivalent of the Black Hat conference held in the United States, Darren Bilby called many existing tools ineffective "magic" that engineers are forced to install for the sake of compliance but at the expense of real security. "Please no more magic," he said, according to The Register. "We need to stop investing in those things we have shown do not work." To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-11-28 06:00:00 | How to protect the C-suite from spear phishing (lien direct) | CSO Editor-in-Chief Joan Goodchild sits down with Kevin O'Brien, founder and CEO of GreatHorn, to discuss ways that security leaders can fend off spear phishing attempts aimed at the executives at their companies. | Guideline | |||
| 2016-11-28 03:20:00 | IDG Contributor Network: Has IT become too complex to manage? (lien direct) | In the late 1990s, I was responsible for technical operations for a large healthcare organization. We supported more than 5,000 users across 50 locations and supported three distinct lines of business. We were a very progressive organization at the leading edge of technology innovation in healthcare. It was not a simple operation. Well, at least not for 1997. When I compare that environment to what IT leaders face today, however, a shudder of relief washes over me. There is no point in whitewashing this: Managing the function of IT in my day was child's play compared to the incredible diversity of challenges facing the modern IT leader. Is it so complex, in fact, that it cannot truly be managed?To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-11-27 23:36:42 | San Francisco\'s Muni transit system reportedly hit by ransomware (lien direct) | San Francisco's Muni transit system was reportedly hit by ransomware since Friday, leading to the message “You Hacked, ALL Data Encrypted†being displayed on the computer screens at stations, according to newspaper reports.The message asked that cryptom27 at yandex.com should be contacted for the key to unlock the data.Fare payment machines at stations also displayed that they were “out of service,†and San Francisco's Municipal Railway, widely known as Muni, was allowing free rides on its light-rail vehicles as it was unable to charge customers, according to the Examiner.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-11-22 04:56:00 | Who has the most impact in driving security advancement? (lien direct) | Depending on the size of the organization, the person who has the most impact on driving security advancement could be a C-level or board member, but non-executive administrators, and sometimes the one man IT/security show is the person paving the path.Whoever it is, every business needs someone who makes security not only a line item on the budget but also a part of the overall culture. More often than not, though, organizations prioritize security for one of two reasons.Josh Feinblum, vice president of information security at Rapid7 said,"Companies that care about security have either a progressive leadership team that believes it is important, or it is a company that has gone through a major event."To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-11-21 09:40:00 | CIO confab SIMposium to skip 2017 (lien direct) | The Society for Information Management has announced that is reworking its annual SIMposium conference, which took place last month in Connecticut, and will come back in the spring of 2018 with an event dubbed SIM Connect Live.This year's event attracted hundreds of CIOs and other IT decision makers and business strategists to exchange thoughts on everything from leadership to risk management to the workforce of the future (See also: "CIO Security Lessons -- Dark thinking on IoT & exploding enterprise networks").To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-11-18 15:32:03 | Trump\'s national security pick is a cybersecurity hawk (lien direct) | Michael Flynn, the man President-elect Donald Trump plans to name as U.S. national security advisor, believes the government is falling behind on cybersecurity. Trump named Flynn to his cabinet on Friday after the former military intelligence leader acted as the top military advisor to Trump's presidential campaign. Flynn previously was director of the Defense Intelligence Agency and has served in U.S. intelligence operations in Afghanistan and Iraq. Flynn holds strong views on cybersecurity. He's called U.S. cyber capabilities “underwhelming.†“We have competitors out there that are rapidly catching up with us,†he said in a speech posted online last year. In 2014, after retiring as a general, he started a consulting firm called Flynn Intel Group that specializes in preventing cyber threats for clients.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-11-17 19:14:06 | Without tech industry guidance, U.S. may resort to weakening encryption (lien direct) | Apple may have refused to help the FBI unlock an iPhone used by the San Bernardino shooter, but the tech industry is still better off working with the U.S. government on encryption issues than turning away, according to a former official with the Obama administration. “The government can get very creative,†said Daniel Rosenthal, who served as the counterterrorism director in the White House until January this year. He fears that the U.S. government will choose to “go it alone†and take extreme approaches to circumventing encryption, especially if another terrorist attack occurs.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-11-16 07:46:00 | SWIFT has not seen its last \'bank robbery\' (lien direct) | A former CSO of the World Bank Treasury calls the SWIFT system outdated and open to malware attacks. Those vulnerabilities could lead to manipulation of financial transactions.SWIFT is the interbank financial messaging system for sending international money transfer instructions. The Society for Worldwide Interbank Financial Telecommunications, which the industry refers to as the SWIFT co-op maintains this system.CSO looks at the SWIFT co-op's denial of the real issue, the cost of attacks, informed expert insights into these security flaws, how hackers are using and abusing these to their profit, and what the co-op should do to seal its messaging system to mitigate further falsifications.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-11-16 07:38:00 | Cisco Founders Forum: One creative way to keep & energize talent (lien direct) |
The tech industry brims with examples of bright entrepreneurs who have struck it big by selling their startups and then hightailing it out of those larger companies once contractually eligible so that they can pursue their next venture.So what the heck is Matt Cutler still doing at Cisco three years after selling his mobile collaboration startup to the networking giant? Well, among other things, he's teaching a bunch of his peers who have stayed at Cisco after having their own companies acquired -- as well as any Cisco lifers who will listen -- a thing or two about how to keep cranking out new ideas. Cisco
Matt Cutler, Lead Evangelist for Cisco Cloud Collaboration Technologies, has big ideas on ideation.To read this article in full or to leave a comment, please click here Cisco
Matt Cutler, Lead Evangelist for Cisco Cloud Collaboration Technologies, has big ideas on ideation.To read this article in full or to leave a comment, please click here |
Guideline | |||
| 2016-11-14 07:55:00 | Blockchain adoption in banks coming, but slower than expected (lien direct) | Recent headlines suggest that blockchain technology is revolutionizing financial services. JP Morgan Chase, Barclays, Commonwealth Bank, Wells Fargo and several other leading banks are using the digital ledger technology to conduct equity swaps, cross-border trades, and other transactions.You might think that blockchain has gone mainstream. Not so fast, says former UBS CIO Oliver Bussmann, who claims it may take banks two years to run blockchain in production due to regulatory hurdles, a lack of standards and other stumbling blocks. “This is real, this will come but in a very regulated environment. We will go through a lot of validation,†says Bussmann, who jumpstarted blockchain efforts when he was leading IT at the Swiss bank last year.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-11-10 11:00:00 | How to maintain data and document security with a mobile workforce (lien direct) | Pragmatic approach Image by ThinkstockData and document security with today's mobile workforce can be a difficult challenge. This is not a “one-size-fits-all†problem; one needs to weigh the risks to ensure that you are operating within a tolerable risk level or the opposite in which you put significant controls around devices, hamper productivity for no benefit. Take a pragmatic approach – you want the ability to clearly and justly answer the organization's question of, “Why is this security measure necessary?†As security leaders, we want to allow your teams to move as fast as possible and not deploy a policy or technology because someone touts it as the best way to do something. Security vendor Conga provides these tips for that healthy balance.To read this article in full or to leave a comment, please click here Image by ThinkstockData and document security with today's mobile workforce can be a difficult challenge. This is not a “one-size-fits-all†problem; one needs to weigh the risks to ensure that you are operating within a tolerable risk level or the opposite in which you put significant controls around devices, hamper productivity for no benefit. Take a pragmatic approach – you want the ability to clearly and justly answer the organization's question of, “Why is this security measure necessary?†As security leaders, we want to allow your teams to move as fast as possible and not deploy a policy or technology because someone touts it as the best way to do something. Security vendor Conga provides these tips for that healthy balance.To read this article in full or to leave a comment, please click here |
Guideline | |||
| 2016-11-10 07:25:55 | European Parliament clears drone regulations for takeoff (lien direct) | Regulations to protect people from falling drones moved a little closer to takeoff at the European Parliament on Thursday.Ensuring drone safety took on a new urgency this week, with GoPro's recall of its Karma drone after unexplained mid-air power failures caused a number of them to drop out of the sky.Under the European Union's proposed regulations, drones will have to be registered so that their owners can be identified. While that won't in itself stop drones from falling, it could lead pilots to take their responsibilities more seriously, legislators hope.A 1-kilogram drone like the Karma falling from as little as 11 meters (around three stories) could kill even someone wearing a safety helmet, according to a calculator developed by the Dropped Object Prevention Scheme, which promotes safety in the oil and gas industry.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-11-10 04:00:00 | IDG Contributor Network: Major cloud is infested with malware, researchers say (lien direct) | Cloud repositories are actively supplying malware, according to computer experts. And problematically, it's insidious and hard to find.Hundreds of buckets have been undermined, says Xiaojing Liao, a graduate student at Georgia Tech who's the lead author on a study that's looking into the problem. Buckets are chunks of storage used in cloud operations.It's “challenging to find,†Georgia Tech writes in an article on its website. The problem being that the resulting malware is quick to “assemble from stored components that individually may not appear to be malicious.â€To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-11-08 06:46:40 | Android patches fix Drammer RAM attack, but not Dirty Cow exploit (lien direct) | Google released a new monthly batch of security patches for Android, fixing a dozen critical vulnerabilities that could allow attackers to compromise devices. One of the mitigated issues is a bit-flipping attack against memory chips that could lead to privilege escalation, but a more widespread rooting vulnerability in the Linux kernel remains unpatched.While Google releases firmware updates for its Nexus and Pixel devices on the first Monday of every month, the security patches are shared with third-party device manufacturers one month in advance and are also contributed later to the Android Open Source Project to benefit the entire ecosystem.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-11-07 13:06:00 | Microsoft postpones Windows anti-exploit tool\'s retirement (lien direct) | Microsoft last week announced that it would support the Enterprise Mitigation Experience Toolkit (EMET) through July 2018, a year-and-a-half extension for the anti-exploit utility.At the same time, the Redmond, Wash. company dismissed EMET as a behind-the-times tool, and again urged customers to upgrade to Windows 10, arguing that the new operating system is much more secure than previous editions when supplemented by EMET."EMET hasn't kept pace," wrote Jeffrey Sutherland, a Microsoft principal program manager lead, in a post to a company blog Nov. 3. "Its effectiveness against modern exploit kits has not been demonstrated, especially in comparison to the many security innovations built into Windows 10."To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-11-07 08:17:48 | 5 things you need to know about virtual private networks (lien direct) | A virtual private network is a secure tunnel between two or more computers on the internet, allowing them to access each other as if on a local network. In the past, VPNs were mainly used by companies to securely link remote branches together or connect roaming employees to the office network, but today they're an important service for consumers too, protecting them from attacks when they connect to public wireless networks. Given their importance, here's what you need to know about VPNs:VPNs are good for your privacy and securityOpen wireless networks pose a serious risk to users, because attackers sitting on the same networks can use various techniques to sniff web traffic and even hijack accounts on websites that don't use the HTTPS security protocol. In addition, some Wi-Fi network operators intentionally inject ads into web traffic, and these could lead to unwanted tracking.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-11-02 07:00:00 | Fixing the communications issues between IT security and the board and c-suite (lien direct) | In the months before an unexpected crisis, IT security requests specific tools, training, and additional staff to keep enterprise data safe, but does not substantiate the need in terms the business can understand. The c-suite denies the requests, pointing to the investments they have already made in security technologies. Suddenly, hackers strike with a massive cyber attack.Suffering financial losses and brand damage, the c-suite asks IT security what happened. Security responds that they need specific tools, training, and staff to mitigate these concerns. But again, security does not make a business case in language the c-suite can appreciate. The leadership turns to existing vendors, who sell them their latest security products.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-11-01 06:34:00 | Unencrypted pagers a security risk for hospitals, power plants (lien direct) | For most of us, pagers went out when cell phones came in, but some companies are still using them and when the messages are sent without encryption, attackers can listen in and even interfere with the communications.According to two new reports by Trend Micro, pagers are still in use in hospital settings and in industrial plants.Stephen Hilt, Trend Micro's lead researcher on the project, said they don't have a concrete percentage on the number of encrypted messages.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-10-31 07:28:00 | Trend Micro\'s Enterprise Play (lien direct) | I spent a few days with Trend Micro last week at its Insight event here in Boston. While Trend is a $1 billion + global cybersecurity vendor, too many cybersecurity professionals still think of Trend as an Asian-based AV player.   This perception is completely antiquated however, as Trend now offers: A tightly-integrated next-generation endpoint security suite. There's a lot of industry rhetoric out there proclaiming Trend as a legacy AV vendor. Don't believe it! Yes, Trend Micro's endpoint security product has been around forever but the company has continuously enhanced it technology to keep up with the latest requirements. Most recently, Trend added machine learning for pre- and post-execution prevention/detection of 0-day malware which puts in on par with the next-generation endpoint security crowd. Oh, and Trend also offers its own EDR functionality as well. Armed with its new product, Trend's layered endpoint defense should meet the security efficacy and operational efficiency requirements of even the most demanding enterprises. A strong network security defense portfolio. Now that the dust has settled from Trend's acquisition of TippingPoint a year ago, the company also has robust products for network security. After HP let TippingPoint languish for a few years, Trend is once again investing in R&D, enhancing its IPS performance and usability. Furthermore, Trend plans to integrate TippingPoint network prevention capabilities with its Deep Discovery network “sandbox†for malware detection.   This integration should bolster security while streamlining operations. Trend faces stiff competition here and the company doesn't offer a network firewall, but its IPS/sandbox story should play well, especially in the small enterprise market. Cloud and virtualization support. Trend has a history here as it was one of the first vendors to work with VMware VMSafe APIs years ago. Today, Trend provides server security tools for VMware NSX as well as other cloud technologies like OpenStack, Amazon AWS, Microsoft Azure, etc. It has quietly become a hybrid cloud security leader while it watches for opportunities with container security in the near future.   A reputation for good field and product support. While our industry is gaga over “next-generation†security technologies, Trend recognizes that technology alone isn't enough. To bridge this gap, Trend is committed to training its people, hiring field engineering talent, and providing proactive support. Several customers I spoke with raved about Trend's support capabilities, saying that they view the Trend people as, “an extension of my own staff.â€Â This is strong compliment indeed. These highlights just scratch the surface of what's happening at Trend Micro. The company's enterprise portfolio also includes threat intelligence, email security, DLP, etc.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-10-31 06:00:00 | Why Blockchain\'s growing pains will be worth it (lien direct) |
HALF MOON BAY, Calif. – Experts at a recent technology conference agreed that blockchain has a bright future, but warned it may be a rocky ride until that future arrives. Blockchain is a distributed database that uses a secure digital ledger of transactions that users can share across a computer network. It's also the technology behind virtual currency bitcoin.      “When you are at the leading edge there will be mistakes. People will get a lot wrong in the next five years. I think of it kind of like running with scissors,†says Constellation Research analyst Steve Wilson at the Oct. 26 Connected Enterprise conference hosted by his company. Constellation Research Connected Enterprise conference
From left to right: Shawn Wiora, CEO of Maxxsure, Silicon Valley Product Exec Chirag Mehta, and Aron Dutta, Global Head of Blockchain at IBMTo read this article in full or to leave a comment, please click here Constellation Research Connected Enterprise conference
From left to right: Shawn Wiora, CEO of Maxxsure, Silicon Valley Product Exec Chirag Mehta, and Aron Dutta, Global Head of Blockchain at IBMTo read this article in full or to leave a comment, please click here |
Guideline | |||
| 2016-10-26 10:33:44 | Emergency Flash Player patch fixes zero-day critical flaw (lien direct) | Adobe Systems has released an emergency patch for Flash Player in order to fix a critical vulnerability that attackers are already taking advantage of.The vulnerability, tracked as CVE-2016-7855 in the Common Vulnerabilities and Exposures database, is a use-after-free error that could lead to arbitrary code execution."Adobe is aware of a report that an exploit for CVE-2016-7855 exists in the wild, and is being used in limited, targeted attacks against users running Windows versions 7, 8.1 and 10," the company warned in a security advisory Wednesday.Users are advised to upgrade to Flash Player 23.0.0.205 on Windows and Mac and to version 11.2.202.643 on Linux. The Flash Player runtime bundled with Google Chrome and Microsoft Edge or Internet Explorer 11 on Windows 10 and 8.1 will be updated automatically through those browsers' update mechanisms.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-10-25 12:25:00 | Rise of the IoT machines (lien direct) | Friday's distributed denial-of-service attack on domain name service provider Dyn may have seemed like the end of the world for millions of Netflix, Twitter and Spotify users, but security professionals say the service disruption was merely a nuisance attack – although an eye opening one – compared to the potential damage that can be unleashed by billions of unsecure IoT devices.“It's really just the tip of the iceberg,†says Nicholas Evans, vice president and general manager within the Office of the CTO at Unisys, where he leads its worldwide applied innovation program. “You can grade the threat intensity as the IoT devices become more autonomous, like self-driving cars, or more controllable, like some of factory-type devices that actually manipulate the physical environment. That's where the real threat is.â€To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-10-25 10:00:02 | (Déjà vu) Workstation software flaw exposes industrial control systems to hacking (lien direct) | The software used to program and deploy code to various Schneider Electric industrial controllers has a weakness that could allow hackers to remotely take over engineering workstations.The software, known as Unity Pro, runs on PCs used by engineers and includes a simulator for testing code before deploying it to programmable logic controllers (PLCs). These are the specialized hardware devices that monitor and control mechanical processes -- spinning motors, opening and closing valves, etc. -- inside factories, power stations, gas refineries, public utilities and other industrial installations.Researchers from industrial cybersecurity firm Indegy found that unauthenticated attackers could execute malicious code on Windows computers where the Unity Pro PLC simulator is installed. That code would run with debug privileges leading to a complete system compromise.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-10-25 05:46:30 | Schneider Electric PLC simulator flaw exposes workstations to hacking (lien direct) | The software used to program and deploy code to various Schneider Electric industrial controllers has a weakness that could allow hackers to remotely take over engineering workstations.The software, known as Unity Pro, runs on PCs used by engineers and includes a simulator for testing code before deploying it to programmable logic controllers (PLCs). These are the specialized hardware devices that monitor and control mechanical processes -- spinning motors, opening and closing valves, etc. -- inside factories, power stations, gas refineries, public utilities and other industrial installations.Researchers from industrial cybersecurity firm Indegy found that unauthenticated attackers could execute malicious code on Windows computers where the Unity Pro PLC simulator is installed. That code would run with debug privileges leading to a complete system compromise.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-10-24 11:15:38 | Physical RAM attack can root Android and possibly other devices (lien direct) | Researchers have devised a new way to compromise Android devices without exploiting any software vulnerabilities and instead of taking advantage of a physical design weakness in RAM chips. The attack technique could also affect other ARM and x86-based devices and computers.The attack stems from the push over the past decade to pack more DRAM (dynamic random-access memory) capacity onto increasingly smaller chips, which can lead to memory cells on adjacent rows leaking electric charges to one another under certain conditions.For example, repeated and rapid accessing of physical memory locations -- an action now dubbed "hammering" -- can cause the bit values from adjacent locations to flip from 0 to 1 or the other way around.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-10-24 09:38:00 | Media fails to tell consumers about device flaws in Friday\'s internet outage (lien direct) | Hacked cameras, DVRs and other internet-connected consumer devices were conscripted by perpetrators who installed botnet malware, causing last Friday's internet outages. The national media reported the event, but it failed to tell consumers what they need to know about buying those types of devices. For example, before making a purchase, consumers need to ask: Does the manufacturer routinely update this device with security patches? Can I change the default passwords when I install the device? The national media could have talked to someone who has first-hand experience with this type of attack, such as Brian Krebs, former Washington Post journalist and now one of the leading security industry bloggers, who would have repeated what he posted on Friday:To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-10-20 07:48:00 | 3 ways Windows Server 2016 is tackling security (lien direct) | Every version of Windows - client and server - has promised improved security. But with Windows 10 and Windows Server 2016, Microsoft is going beyond the usual incremental improvements and closing of loopholes and giving you the tools to reduce the dangers of phished credentials, over-privileged admins and untrustworthy binaries.“In the past, security was always something that was part of another technology†says Jeff Woolsey, principal group program manager at Microsoft. “We needed to pull it out.â€Security and protecting identity comes up in every conversation Microsoft has with customers, he says. And the scale of attacks means that security isn't just something for the IT team to worry about any more, adds Jeffrey Snover, lead architect for the enterprise cloud group and the Microsoft Azure stack. “When we asked customers 'what are your IT concerns?' there were some messages we heard consistently. There were too many stories about getting hacked and not knowing for months.â€To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-10-19 05:19:00 | Tim Cook or Bill Gates as Clinton\'s VP? It was considered (lien direct) | Apple CEO Tim Cook and Microsoft founder Bill Gates were both on a list of potential vice presidential candidates for Democrat Hillary Clinton, according to a leaked email published on Tuesday by Wikileaks.The email, apparently sent by campaign chairman John Podesta on March 17, named the two tech titans alongside 37 other people as "a first cut of people to consider for VP."Also on the list, published by WikiLeaks, was Gates' wife Melinda. She co-founded the charitable foundation that bears both their names.MORE ON NETWORK WORLD: 6 simple tricks for protecting your passwords Other business leaders that made the cut were General Motors CEO Mary Barra, Bloomberg News founder and former New York Mayor Michael Bloomberg, Xerox CEO Ursula Burns, Coca-Cola CEO Muhtar Kent, Rockefeller Foundation president Judith Rodin, and Starbucks CEO Howard Schultz.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-10-17 14:07:00 | Breaches, IT skills & innovation keeping CIOs up at night (lien direct) | To say that CIOs have full plates – from guarding against breaches to cloud migration to embracing innovation – is an understatement. But given the growing recognition of IT's importance to organizations of all kinds, it's also a tremendous time to be a CIO despite the complications and demands of the job.These are among the findings of the Society for Information Management's (SIM) 37th Anniversary IT Trends Study, which is being released to SIM members this week as a lead-in to next week's annual SIMposium conference that's taking place in Connecticut. Non-members can get a peek at the study next week.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-10-13 09:48:00 | What is MANRS and does your network have it? (lien direct) | While the internet itself was first envisioned as a way of enabling robust, fault-tolerant communication, the global routing infrastructure that underlies it is relatively fragile. A simple error like the misconfiguration of routing information in one of the 7,000 to 10,000 networks central to global routing can lead to a widespread outage, and deliberate actions, like preventing traffic with spoofed source IP addresses, can lead to distributed denial of service (DDoS) attacks.The Internet Society (ISOC), a cause-driven nonprofit organization that seeks to promote the open development, evolution and use of the Internet and the parent organization of the Internet Engineering Task Force (IETF) standards body, is moving to change that. In 2014, ISOC introduced its Mutually Agreed Norms for Routing Security (MANRS) initiative. Today ISOC announced that the initiative membership has more than quadrupled in its first two years, growing from its initial nine network operators to 42 network operators today.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-10-13 05:42:00 | Yahoo shows that breach impacts can go far beyond remediation expenses (lien direct) | Companies that focus on the immediate breach remediation costs may be missing the big picture, and could be under-investing in security as a result.Several studies have come out recently trying to get a handle on the total costs of a data breach, with a large variation in costs - from less than $1 million on average, to $6 million - based on the data sets and types of included costs.But the actual numbers could be several times higher.Take the Yahoo breach, for example, which could lead to a $1 billion drop in the company's value.To read this article in full or to leave a comment, please click here | Guideline | Yahoo | ||
| 2016-10-12 05:36:00 | 10 highest-paying IT security jobs (lien direct) | Highest-paying IT security jobs Image by ThinkstockData breaches, DDOS attacks, hacks and threats continue to dominate the headlines, so it's no surprise that some of the most in-demand IT jobs are in the security area. And with a massive skills gap, companies are willing to pay handsomely for skilled security talent at all levels.
"One area we're still seeing huge demand for is in cybersecurity, and hiring companies are willing to pay whatever it takes for talent that can help secure data and mitigate threats while simultaneously ensuring consistent and simplified accessibility from desktop to mobile devices. Companies are sending the message with their budgets: you can't put a price on that," says Jack Cullen, CEO of IT staffing firm Modis.
Here are the top 10 highest-paying security roles, culled from career site Dice.com clients' job postings and median salary range data from cloud compensation solutions firm PayScale.com.
1. Lead Software Security Engineer Image by ThinkstockData breaches, DDOS attacks, hacks and threats continue to dominate the headlines, so it's no surprise that some of the most in-demand IT jobs are in the security area. And with a massive skills gap, companies are willing to pay handsomely for skilled security talent at all levels.
"One area we're still seeing huge demand for is in cybersecurity, and hiring companies are willing to pay whatever it takes for talent that can help secure data and mitigate threats while simultaneously ensuring consistent and simplified accessibility from desktop to mobile devices. Companies are sending the message with their budgets: you can't put a price on that," says Jack Cullen, CEO of IT staffing firm Modis.
Here are the top 10 highest-paying security roles, culled from career site Dice.com clients' job postings and median salary range data from cloud compensation solutions firm PayScale.com.
1. Lead Software Security Engineer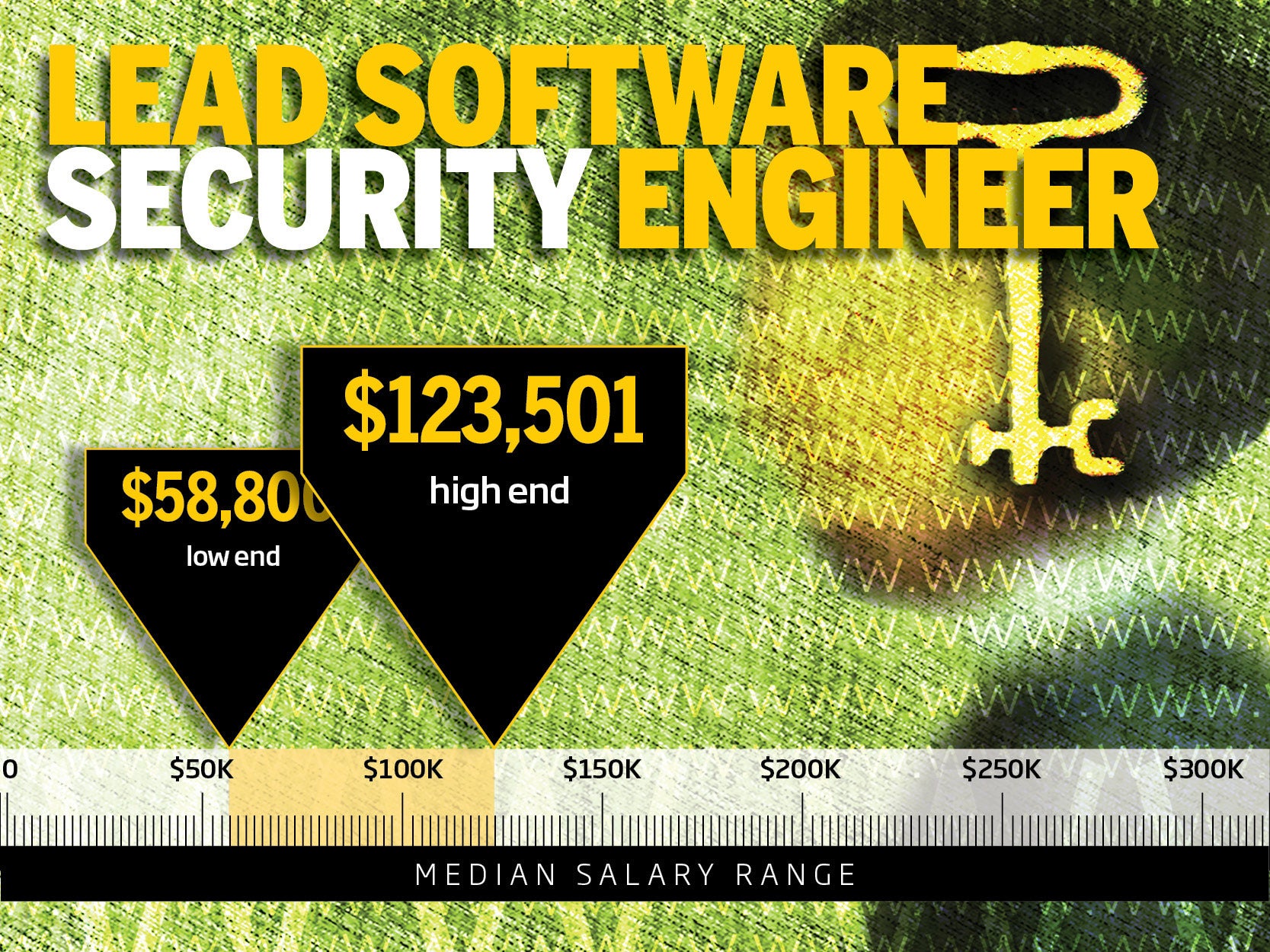 Image by ThinkstockTo read this article in full or to leave a comment, please click here Image by ThinkstockTo read this article in full or to leave a comment, please click here |
Guideline | |||
| 2016-10-06 13:19:00 | How to shield your company from cyber enforcement (lien direct) | This vendor-written tech primer has been edited by Network World to eliminate product promotion, but readers should note it will likely favor the submitter's approach.A lot has changed in the world of cyber regulation. September 2015 saw the widely reported SEC administrative proceeding against RT Jones for violating the “Safeguard Rule†in failing to establish and implement written cyber protection policies. Next was Morgan Stanley. And this past March the Consumer Financial Protection Bureau (CFPB) brought a pre-emptive action against a company that hadn't even had a breach.At this stage, it's safe to assume the list of regulators and their security requirements will continue to grow and fines and penalties will become more severe. In fact, just last week the New York Department of Financial Services (DFS) proposed new cyber guidelines for financial institutions.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-10-06 10:51:00 | What CSOs can learn from the Yahoo breach (lien direct) | In the latest episode of Security Sessions, CSO Editor-in-chief Joan Goodchild talks about the implications of the Yahoo data breach, in which up to 500 million accounts were hacked. Joining Goodchild in the discussion is Kevin O'Brien, CEO and founder of GreatHorn, who offers advice to CSOs and other IT security leaders on ways to learn from this particular breach. | Guideline | Yahoo | ||
| 2016-10-05 07:30:06 | Yahoo calls report of secret email scanning \'misleading\' (lien direct) | Yahoo has called a Reuters article about a secret email scanning program "misleading," and said no such system exists. On Tuesday, the Reuters article claimed that Yahoo had created the custom software program after receiving a classified U.S. government order.  That software program is reportedly capable of scanning all incoming emails from Yahoo customers for information provided by U.S. intelligence officials.However, on Wednesday Yahoo disputed the report.“We narrowly interpret every government request for user data to minimize disclosure. The mail scanning described in the article does not exist on our systems," the company said in an email. To read this article in full or to leave a comment, please click here | Guideline | Yahoo | ||
| 2016-10-03 12:05:14 | Dell EMC patches critical flaws in VMAX enterprise storage systems (lien direct) | Dell EMC has fixed six flaws in its management interfaces for VMAX enterprise storage systems, including three vulnerabilities that are rated critical and could lead to the exposure of sensitive files or a complete system compromise.One of the critical flaws is located in the Unisphere for VMAX enterprise storage arrays, an appliance that provides a web-based management interface to provision, manage, and monitor such systems.More specifically, the flaw is in the GraniteDS library that provides server-side support for the Flash-based portion of the Unisphere web application. According to researchers from vulnerability management firm Digital Defense, the issue allows unauthenticated attackers to retrieve arbitrary text files from the virtual appliance with root privileges.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-10-03 08:27:48 | Trump calls for US to use offensive cyberweapons (lien direct) | The U.S. government needs to be ready to use its offensive cyberweapons in response to attacks from other nations, Republican presidential candidate Donald Trump said Monday.The U.S. has significant offensive cybercapabilities, but it has been shy about deploying them, Trump said during a speech in Herdon, Virginia. "This is the warfare of the future," he said. The U.S. should also increase its use of cyberweapons to attack terrorists, Trump said. President Barack Obama has failed to protect the nation's cybersecurity and a new focus is needed, added Trump, who has largely avoided technology issues in his campaign. Trump said he will create an international cybersecurity task force to battle hackers, and he will ask U.S. military leaders for suggestions on how to improve the nation's cyberdefenses. To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-09-30 10:16:00 | Splunk Intent on Extending Cybersecurity Leadership (lien direct) | I attending the Splunk user conference earlier this week (.Conf2016) and came away pretty impressed. Since I started watching Splunk years ago, the company climbed from a freemium log management and query tool for IT and security nerds to one of the leading security analytics and operations platform. Not surprisingly then, security now represents around 40% of Splunk's revenue. Given the state of the cybersecurity market, Splunk wants to work with existing customers and get new ones to join in to build on this financial and market success.To that end, Splunk really highlighted three enhancements for its enterprise security product:1.     An ecosystem and architecture for incident response. Splunk often acts as a security nexus for its customers, integrating disparate data into a common platform. It now wants to extend this position from analytics to incident response by building IR capabilities into its own software and extending this architecture to partners through APIs, workflows, and automation. Splunk calls this adaptive response. For now, Splunk doesn't see itself as an IR automation and orchestration platform for complex enterprise environments (in fact Phantom and ServiceNow were both exhibiting at the event) but it does want to use its position and market power to make IR connections, data flows, and tasks easier and more effective for security and IT personnel alike.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-09-28 05:31:00 | Elon Musk\'s next great adventure: Colonizing Mars (lien direct) | You cannot say that Elon Musk doesn't dream big. Today he outlined what would be his biggest aspiration ever – colonizing Mars.If you watched Musk, who is SpaceX Founder, CEO, and Lead Designer deliver the details today on his Mars colonizing mission to the International Astronautical Congress in Guadalajara, Mexico you may have been struck by the matter-of-fact way he delivered the details of what even he calls a very complex and dangerous mission.“I think the first trips to Mars are going to be really, very dangerous. The risk of fatality will be high. There is just no way around it," he said. "It would basically be, 'Are you prepared to die?' Then if that's ok, then you are a candidate for going."To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-09-27 10:38:08 | Six senators demand more details about the Yahoo data breach (lien direct) | Six U.S. senators have called Yahoo's massive data breach "unacceptable," and they're demanding that the company provide more details about the incident.In a letter addressed to Yahoo's CEO, the lawmakers said they were particularly "disturbed" that the breach occurred in 2014, but that Yahoo only publicized it last week."That means millions of Americans' data may have been compromised for two years," the letter said. "This is unacceptable."The hacking incident, which Yahoo said it only learned recently, affects at least 500 million users, making it perhaps the largest known data breach in history. Account information, including email addresses, telephone numbers, and hashed passwords, may have been stolen.To read this article in full or to leave a comment, please click here | Guideline | Yahoo | ||
| 2016-09-23 01:03:40 | Vint Cerf\'s dream do-over: 2 ways he\'d make the internet different (lien direct) | Vint Cerf is considered a father of the internet, but that doesn't mean there aren't things he would do differently if given a fresh chance to create it all over again."If I could have justified it, putting in a 128-bit address space would have been nice so we wouldn't have to go through this painful, 20-year process of going from IPv4 to IPv6," Cerf told an audience of journalists Thursday during a press conference at the Heidelberg Laureate Forum in Germany.IPv4, the first publicly used version of the Internet Protocol, included an addressing system that used 32-bit numerical identifiers. It soon became apparent that it would lead to an exhaustion of addresses, however, spurring the creation of IPv6 as a replacement. Roughly a year ago, North America officially ran out of new addresses based on IPv4. Â To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-09-21 10:50:00 | More than 840,000 Cisco devices are vulnerable to NSA-related exploit (lien direct) | More than 840,000 Cisco networking devices from around the world are exposed to a vulnerability that's similar to one exploited by a hacking group believed to be linked to the U.S. National Security Agency.The vulnerability was announced by Cisco last week and it affects the IOS, IOS XE, and IOS XR software that powers many of its networking devices. The flaw allows hackers to remotely extract the contents of a device's memory, which can lead to the exposure of sensitive information.The vulnerability stems from how the OS processes IKEv1 (Internet Key Exchange version 1) requests. This key exchange protocol is used for VPNs (Virtual Private Networks) and other features that are popular in enterprise environments.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-09-21 03:00:00 | IT security: 3 things you need to know now (lien direct) | Computerworld, CSO and CIO surveyed 287 business and IT leaders on the state of security in their organization. Here's what they had to say (it ain't always pretty...). | Guideline | |||
| 2016-09-20 11:09:00 | IDG Contributor Network: Data breaches: This time it\'s more personal (lien direct) | Summer 2016 was not a good time for data breaches.First, news broke that the Democratic National Committee was hacked, leading to the resignation of DNC Chair Debbie Wasserman Schultz and driving a wedge between Democratic Party members.Later, the World Anti-Doping Agency (WADA) announced that Russian hackers had illegally accessed its Anti-Doping Administration and Management System (ADAMS) database, leaking confidential medical information for U.S. athletes, including Simone Biles and Serena Williams.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-09-19 07:59:00 | Cisco discloses PIX firewall, IOS software security holes (lien direct) | Cisco has warned of a high priority security hole in its IOS software that could have let attackers snatch memory contents from a variety of products that could lead to the disclosure of confidential information.+More on Network World: Cisco buys into containers with Container X acquisition+Specifically Cisco said the vulnerability is due to “insufficient condition checks in the part of the code that handles [Internet Key Exchange] IKEv1 security negotiation requests. An attacker could exploit this vulnerability by sending a crafted IKEv1 packet to an affected device configured to accept IKEv1 security negotiation requests.â€To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-09-19 07:08:07 | Cisco patches Equation group exploit in IOS, IOS XE and IOS XR devices (lien direct) | Cisco Systems has patched a vulnerability similar to one exploited by a cyberespionage group believed to be linked to the U.S. National Security Agency.The vulnerability affects networking devices running Cisco's IOS, IOS XE and IOS XR operating systems that process IKEv1 (Internet Key Exchange version 1) packets. When exploited, it allows remote unauthenticated attackers to extract contents from a device's memory, potentially leading to the exposure of sensitive and confidential information.IKE is a key exchange protocol used by several popular features including LAN-to-LAN VPN (Virtual Private Network), remote access VPN, Dynamic Multipoint VPN (DMVPN) and Group Domain of Interpretation (GDOI). It is likely to be enabled on many Cisco devices in enterprise environments.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-09-15 16:19:26 | Don\'t pardon Snowden, lawmakers tell Obama (lien direct) | U.S. lawmakers are trying to stifle any hope that National Security Agency leaker Edward Snowden will receive a pardon. On Thursday, the House intelligence committee sent a letter to President Obama urging him to treat Snowden as a criminal.“Mr. Snowden is not a patriot. He is not a whistleblower,†the letter said.The letter was sent amid calls from tech leaders and liberal activists for Obama to pardon Snowden. The campaign, supported by Apple co-founder Steve Wozniak and celebrities including actor Daniel Radcliffe, argues that Snowden sparked an important debate about government mass surveillance.To read this article in full or to leave a comment, please click here | Guideline |
To see everything:
Our RSS (filtrered)
