What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2018-10-14 04:57:46 | How to irregular cyber warfare (lien direct) | Somebody (@thegrugq) pointed me to this article on "Lessons on Irregular Cyber Warfare", citing the masters like Sun Tzu, von Clausewitz, Mao, Che, and the usual characters. It tries to answer:...as an insurgent, which is in a weaker power position vis-a-vis a stronger nation state; how does cyber warfare plays an integral part in the irregular cyber conflicts in the twenty-first century between nation-states and violent non-state actors or insurgenciesI thought I'd write a rebuttal.None of these people provide any value. If you want to figure out cyber insurgency, then you want to focus on the technical "cyber" aspects, not "insurgency". I regularly read military articles about cyber written by those, like in the above article, which demonstrate little experience in cyber.The chief technical lesson for the cyber insurgent is the Birthday Paradox. Let's say, hypothetically, you go to a party with 23 people total. What's the chance that any two people at the party have the same birthday? The answer is 50.7%. With a party of 75 people, the chance rises to 99.9% that two will have the same birthday.The paradox is that your intuitive way of calculating the odds is wrong. You are thinking the odds are like those of somebody having the same birthday as yourself, which is in indeed roughly 23 out of 365. But we aren't talking about you vs. the remainder of the party, we are talking about any possible combination of two people. This dramatically changes how we do the math.In cryptography, this is known as the "Birthday Attack". One crypto task is to uniquely fingerprint documents. Historically, the most popular way of doing his was with an algorithm known as "MD5" which produces 128-bit fingerprints. Given a document, with an MD5 fingerprint, it's impossible to create a second document with the same fingerprint. However, with MD5, it's possible to create two documents with the same fingerprint. In other words, we can't modify only one document to get a match, but we can keep modifying two documents until their fingerprints match. Like a room, finding somebody with your birthday is hard, finding any two people with the same birthday is easier.The same principle works with insurgencies. Accomplishing one specific goal is hard, but accomplishing any goal is easy. Trying to do a narrowly defined task to disrupt the enemy is hard, but it's easy to support a group of motivated hackers and let them do any sort of disruption they can come up with.The above article suggests a means of using cyber to disrupt a carrier attack group. This is an example of something hard, a narrowly defined attack that is unlikely to actually work in the real world.Conversely, consider the attacks attributed to North Korea, like those against Sony or the Wannacry virus. These aren't the careful planning of a small state actor trying to accomplish specific goals. These are the actions of an actor that supports hacker groups, and lets them loose without a lot of oversight and direction. Wannacry in particular is an example of an undirected cyber attack. We know from our experience with network worms that its effects were impossible to predict. Somebody just stuck the newly discovered NSA EternalBlue payload into an existing virus framework and let it run to see what happens. As we worm experts know, nobody could have predicted the results of doing so, not even its creators.Another example is the DNC election hacks. The reason we can attribute them to Russia is because it wasn't their narrow goal. Instead, by looking at things like their URL shortener, we can see that they flailed around broadly all over cyberspace. The DNC was just one of thei | Hack Guideline | Wannacry | ||
| 2018-10-10 20:44:05 | GAO report reveals new Pentagon weapon systems vulnerable to hack (lien direct) | According to a new report published by the Government Accountability Office (GAO) almost any new weapon systems in the arsenal of the Pentagon is vulnerable to hack. The new generation of weapon systems developed by the Pentagon is heavily computerized and for this reason more exposed to cyber attacks. According to a new 50-page report […] | Hack | |||
| 2018-10-10 00:43:04 | Just Answering A Video Call Could Compromise Your WhatsApp Account (lien direct) | What if just receiving a video call on WhatsApp could hack your smartphone?
This sounds filmy, but Google Project Zero security researcher Natalie Silvanovich found a critical vulnerability in WhatsApp messenger that could have allowed hackers to remotely take full control of your WhatsApp just by video calling you over the messaging app.
The vulnerability is a memory heap overflow issue
|
Hack Vulnerability | |||
| 2018-10-09 22:22:05 | Pentagon\'s new next-gen weapons systems are laughably easy to hack (lien direct) | Bad passwords, non-encrypted communications, and a lot of unpatched bugs. | Hack | |||
| 2018-10-09 17:00:05 | Podcast Episode 115: Joe Grand on Unicorn Spotting and Bloomberg\'s Supply Chain Story (lien direct) | In this week's episode (#115), noted hardware enthusiast and hacker Joe Grand (aka “Kingpin”) told reporters from Bloomberg that finding an in-the-wild supply chain hack implanting malicious hardware on motherboards was akin to witnessing “a unicorn jumping over a rainbow.” They went with their story about just such an...Read the whole entry... _!fbztxtlnk!_ https://feeds.feedblitz.com/~/573788130/0/thesecurityledger -->» |
Hack | |||
| 2018-10-09 13:00:00 | New Magecart hack detected at Shopper Approved (lien direct) | Malicious code removed after two days. Impact is smaller compared to previous incidents at Ticketmaster, Feedify, or British Airways. | Hack | |||
| 2018-10-09 13:00:00 | 5 Steps to Maximize Your Financial Data Protection (lien direct) |
 A series of high-profile data breaches in 2017 made it clear that it's becoming more difficult to protect your and your customer's sensitive information from nefarious agents. As businesses expand, they develop and implement security policies that help protect their sensitive information from outsiders. Still, business growth means more computers, more laptops and more mobile phones—and more network endpoints means more security vulnerabilities and more opportunities for a small oversight to turn into a major data breach.
Financial data breaches can spell disaster, especially for small businesses that have fewer resources to allocate toward proactive security measures and fraud prevention. To help out, we've outlined five steps that you can take to maximize your financial data protection in 2018.
Take Inventory of Your Sensitive Financial Data
The first step to effective financial data protection is to identify the data that is more important to protect. Your full assessment should answer the following questions:
What data do I need to secure?
What computers, servers, laptops, networks, or other devices is the information stored on?
What devices can be used to access the data?
What roles/titles will have permission to view the data?
The best way to start enhancing data security is by restricting access. Isolate or segregate the data onto the fewest number of devices possible, and make it accessible to the fewest number of people. Conduct thorough background checks and ask for references when hiring employees that will come into contact with financial data.
Implement Effective Password Controls
Passwords are an important security measure used to prevent unauthorized users from accessing company laptops, e-mail accounts and other resources that could contain sensitive financial information. Password controls are a set of imposed guidelines for how your staff should set up the passwords that they use to access your sensitive data. Typical password controls include:
Ensuring that passwords are long enough and that they contain a mixture of upper and lower-case letters, numbers and symbols. As passwords get longer, they become exponentially harder to hack by brute force. Hackers use all kinds of tricks to try and guess passwords—writing software that guesses dictionary words or combinations of words from the dictionary, or that guesses birth dates formatted in different ways. Passwords should be 10-12 characters long.
Ensuring that passwords are changed on a regular basis, at least every 90 days for passwords used to access sensitive financial data.
Ensuring that each individual user is assigned one username and password, and that login credentials are never shared.
Protect Your Network with a Firewall
Companies storing and transmitting financial data on an internal network should implement a firewall. A firewall is a hardware or software security device that monitors all incoming and outgoing network traffic and uses predefined security guidelines to determine whether it should be allowed or blocked. Firewalls establish a barrier between your trusted internal network and unauthorized external actors that might try to access or attack it.
You may want to hire a cyber security expert who can help customize your firewall to your unique circumstances and advise you on how to address other potential network security threats.
Look Out for Phishing Scams
Sometimes, fraudsters don't have to gain access to your systems using technological means to attack your company financiall
A series of high-profile data breaches in 2017 made it clear that it's becoming more difficult to protect your and your customer's sensitive information from nefarious agents. As businesses expand, they develop and implement security policies that help protect their sensitive information from outsiders. Still, business growth means more computers, more laptops and more mobile phones—and more network endpoints means more security vulnerabilities and more opportunities for a small oversight to turn into a major data breach.
Financial data breaches can spell disaster, especially for small businesses that have fewer resources to allocate toward proactive security measures and fraud prevention. To help out, we've outlined five steps that you can take to maximize your financial data protection in 2018.
Take Inventory of Your Sensitive Financial Data
The first step to effective financial data protection is to identify the data that is more important to protect. Your full assessment should answer the following questions:
What data do I need to secure?
What computers, servers, laptops, networks, or other devices is the information stored on?
What devices can be used to access the data?
What roles/titles will have permission to view the data?
The best way to start enhancing data security is by restricting access. Isolate or segregate the data onto the fewest number of devices possible, and make it accessible to the fewest number of people. Conduct thorough background checks and ask for references when hiring employees that will come into contact with financial data.
Implement Effective Password Controls
Passwords are an important security measure used to prevent unauthorized users from accessing company laptops, e-mail accounts and other resources that could contain sensitive financial information. Password controls are a set of imposed guidelines for how your staff should set up the passwords that they use to access your sensitive data. Typical password controls include:
Ensuring that passwords are long enough and that they contain a mixture of upper and lower-case letters, numbers and symbols. As passwords get longer, they become exponentially harder to hack by brute force. Hackers use all kinds of tricks to try and guess passwords—writing software that guesses dictionary words or combinations of words from the dictionary, or that guesses birth dates formatted in different ways. Passwords should be 10-12 characters long.
Ensuring that passwords are changed on a regular basis, at least every 90 days for passwords used to access sensitive financial data.
Ensuring that each individual user is assigned one username and password, and that login credentials are never shared.
Protect Your Network with a Firewall
Companies storing and transmitting financial data on an internal network should implement a firewall. A firewall is a hardware or software security device that monitors all incoming and outgoing network traffic and uses predefined security guidelines to determine whether it should be allowed or blocked. Firewalls establish a barrier between your trusted internal network and unauthorized external actors that might try to access or attack it.
You may want to hire a cyber security expert who can help customize your firewall to your unique circumstances and advise you on how to address other potential network security threats.
Look Out for Phishing Scams
Sometimes, fraudsters don't have to gain access to your systems using technological means to attack your company financiall |
Hack Vulnerability | |||
| 2018-10-09 10:34:00 | Security researcher source in Supermicro chip hack report casts doubt on story (lien direct) | The explosive report "doesn't make sense," according to the expert which described hardware implant uses in theoretical attacks. | Hack | |||
| 2018-10-08 14:36:04 | 5 tips to secure your supply chain from cyberattacks (lien direct) | It's nearly impossible to secure supply chains from attacks like the alleged Chinese chip hack that was reported last week. But here are some tips to protect your company. | Hack | |||
| 2018-10-08 14:30:03 | Chinese Inserting A Backdoor On Supermicro Server BMCs (lien direct) | US officials have shared details of a widespread hardware hack which saw Chinese spies infiltrate 30 American companies, including Amazon and Apple, in 2015 by planting rice-sized computer chips onto their server motherboards which gave hackers access to sensitive consumer and government data. Nicolas Waisman, VP of Security Consulting at Cyxtera: “The supply chain is … The ISBuzz Post: This Post Chinese Inserting A Backdoor On Supermicro Server BMCs | Hack | |||
| 2018-10-08 00:07:00 | PoC Attack Escalates MikroTik Router Bug to \'As Bad As It Gets\' (lien direct) | Researchers say a medium severity bug should now be rated critical because of a new hack technique that allows for remote code execution on MikroTik edge and consumer routers. | Hack | |||
| 2018-10-07 22:11:00 | DHS and GCHQ join Amazon and Apple in denying Bloomberg chip hack story (lien direct) | US and UK officials stand by Amazon and Apple's statements regarding Bloomberg chip hack story. | Hack | |||
| 2018-10-05 16:16:00 | China Tech Stocks Lenovo, ZTE Tumble After Chip Hack Report (lien direct) | HONG KONG (AP) - Chinese tech stocks Lenovo Group and ZTE Corp. tumbled in Hong Kong on Friday following a news report Chinese spies might have used chips supplied by another company to hack into U.S. computer systems. | Hack | |||
| 2018-10-05 13:10:03 | Apple and Amazon deny China hack claims (lien direct) | The tech giants dispute claims that a spy chip tried to steal their corporate secrets and data. | Hack | |||
| 2018-10-05 00:36:03 | Apple, Amazon Throw Shade on Supply Chain Hack Story (lien direct) | A report by Bloomberg alleging a massive operation by China’s Peoples Liberation Army (PLA) to plant spy hardware on servers used by some of the U.S.’s most high profile corporations is being refuted by tech vendors Apple as well as Amazon, who contend that no such compromises took place. The report written by Jordon Robinson and...Read the whole entry... _!fbztxtlnk!_ https://feeds.feedblitz.com/~/572886254/0/thesecurityledger -->» | Hack | |||
| 2018-10-04 21:24:05 | Hacker wastes entire day hacking Pigeoncoin cryptocurrency only to make $15,000 (lien direct) | Pigeoncoin hack confirms that the CVE-2018-17144 vulnerability fixed in the Bitcoin source code in mid-September was, indeed, as bad as it gets. | Hack Vulnerability | |||
| 2018-10-04 18:39:05 | (Déjà vu) Hack the Box: Olympus Walkthrough (lien direct) | Today we are going to solve another CTF challenge “Olympus”. Olympus is a retired vulnerable lab presented by Hack the Box for helping pentester's to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level. Level: Easy Task: To find user.txt and... Continue reading → | Hack | |||
| 2018-10-04 18:30:05 | Hack The Marine Corps Results: Nearly 150 Vulnerabilities Reported, $151,542 Paid To Hackers (lien direct) | The U.S. Department of Defense (DoD) and HackerOne, the leading hacker-powered security platform, today announced the results of the DoD's sixth public bug bounty program. The Marine Corps is committed to fighting and winning in all domains, including cybersecurity, and Hack the Marine Corps is a key initiative of this campaign. The bug bounty challenge invited … The ISBuzz Post: This Post Hack The Marine Corps Results: Nearly 150 Vulnerabilities Reported, $151,542 Paid To Hackers | Hack Guideline | |||
| 2018-10-04 17:41:04 | How Russian Spies Infiltrated Hotel Wi-Fi to Hack Their Victims Up Close (lien direct) | A new indictment details how Russian agents camped outside hotels when remote hacking efforts weren't enough. | Hack | |||
| 2018-10-04 16:36:51 | Notes on the Bloomberg Supermicro supply chain hack story (lien direct) | Bloomberg has a story how Chinese intelligence inserted secret chips into servers bound for America. There are a couple issues with the story I wanted to address.The story is based on anonymous sources, and not even good anonymous sources. An example is this attribution:a person briefed on evidence gathered during the probe saysThat means somebody not even involved, but somebody who heard a rumor. It also doesn't the person even had sufficient expertise to understand what they were being briefed about.The technical detail that's missing from the story is that the supply chain is already messed up with fake chips rather than malicious chips. Reputable vendors spend a lot of time ensuring quality, reliability, tolerances, ability to withstand harsh environments, and so on. Even the simplest of chips can command a price premium when they are well made.What happens is that other companies make clones that are cheaper and lower quality. They are just good enough to pass testing, but fail in the real world. They may not even be completely fake chips. They may be bad chips the original manufacturer discarded, or chips the night shift at the factory secretly ran through on the equipment -- but with less quality control.The supply chain description in the Bloomberg story is accurate, except that in fails to discuss how these cheap, bad chips frequently replace the more expensive chips, with contract manufacturers or managers skimming off the profits. Replacement chips are real, but whether they are for malicious hacking or just theft is the sticking point.For example, consider this listing for a USB-to-serial converter using the well-known FTDI chip. The word "genuine" is in the title, because fake FTDI chips are common within the supply chain. As you can see form the $11 price, the amount of money you can make with fake chips is low -- these contract manufacturers hope to make it up in volume.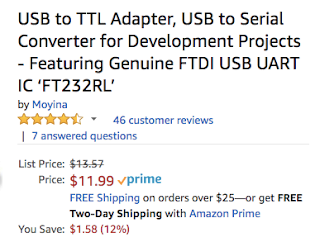 The story implies that Apple is lying in its denials of malicious hacking, and deliberately avoids this other supply chain issue. It's perfectly reasonable for Apple to have rejected Supermicro servers because of bad chips that have nothing to do with hacking.If there's hacking going on, it may not even be Chinese intelligence -- the manufacturing process is so lax that any intelligence agency could be responsible. Just because most manufacturing of server motherboards happen in China doesn't point the finger to Chinese intelligence as being the ones responsible.Finally, I want to point out the sensationalism of the story. It spends much effort focusing on the invisible nature of small chips, as evidence that somebody is trying to hide something. That the chips are so small means nothing: except for the major chips, all the chips on a motherboard are small. It's hard to have large chips, except for the big things like the CPU and DRAM. Serial ROMs containing firmware are never going to be big, because they just don't hold that much information.A fake serial ROM is the focus here not so much because that's the chip they found by accident, but that's the chip they'd look for. The chips contain the firmware for other hardware devices on the motherboard. Thus, instead of designing complex hardware to do malicious things, a hacker simply has to make simple changes t The story implies that Apple is lying in its denials of malicious hacking, and deliberately avoids this other supply chain issue. It's perfectly reasonable for Apple to have rejected Supermicro servers because of bad chips that have nothing to do with hacking.If there's hacking going on, it may not even be Chinese intelligence -- the manufacturing process is so lax that any intelligence agency could be responsible. Just because most manufacturing of server motherboards happen in China doesn't point the finger to Chinese intelligence as being the ones responsible.Finally, I want to point out the sensationalism of the story. It spends much effort focusing on the invisible nature of small chips, as evidence that somebody is trying to hide something. That the chips are so small means nothing: except for the major chips, all the chips on a motherboard are small. It's hard to have large chips, except for the big things like the CPU and DRAM. Serial ROMs containing firmware are never going to be big, because they just don't hold that much information.A fake serial ROM is the focus here not so much because that's the chip they found by accident, but that's the chip they'd look for. The chips contain the firmware for other hardware devices on the motherboard. Thus, instead of designing complex hardware to do malicious things, a hacker simply has to make simple changes t |
Hack | |||
| 2018-10-04 10:23:02 | Hackers Earn $150,000 in Marine Corps Bug Bounty Program (lien direct) | The U.S. Department of Defense's sixth public bug bounty program, Hack the Marine Corps, has concluded, and white hat hackers who took part in the challenge earned more than $150,000. | Hack | |||
| 2018-10-03 13:10:01 | Experts found 9 NAS flaws that expose LenovoEMC, Iomega Devices to hack (lien direct) | Experts discovered nine vulnerabilities affecting NAS devices that could be exploited by unauthenticated attackers to access protected content. Nine flaws affecting NAS devices could be exploited by unauthenticated attackers to access protected content. The vulnerabilities are traked as CVE-2018-9074, CVE-2018-9075, CVE-2018-9076, CVE-2018-9077, CVE-2018-9078, CVE-2018-9079, CVE-2018-9080, CVE-2018-9081 and CVE-2018-9082. According to Lenovo, the flaws affect 20 models of network attached storage (NAS) devices sold by the […] | Hack | |||
| 2018-10-03 11:38:01 | Facebook says other apps not caught in hack (lien direct) | Third-party sites accepting Facebook log-ins like Tinder and Airbnb are not believed to be affected. | Hack | |||
| 2018-10-03 03:00:03 | Women in Information Security: Pam Armstrong (lien direct) | Last time, I spoke with Sharka. She's a pentester who knows how to hack a glucose meter. She also taught me a few things about physical security. Now I get to talk with Pam Armstrong. Web development eventually led her to healthcare security. Kim Crawley: Please tell me about what you do. Pam Armstrong: I […]… Read More | Hack | |||
| 2018-10-02 18:47:05 | iPhone Passcode Bypass Hack Exposes Contacts And Photos (lien direct) | Flaw in Apple's iOS 12 allows an attacker to access contacts and photos in iPhone XS model A passcode bypass vulnerability has been discovered in Apple's new iOS version 12 that could allow an attacker to access photos and contact details on a locked iPhone XS as well as other Apple devices. Jose Rodriguez, a […] | Hack Vulnerability | |||
| 2018-10-02 14:12:03 | The Facebook Hack Is an Internet-Wide Failure (lien direct) | Major sites using Facebook's Single Sign-On don't implement basic security features, potentially making the fallout of last week's hack much worse. | Hack | |||
| 2018-10-02 02:36:05 | New iPhone Passcode Bypass Hack Exposes Photos and Contacts (lien direct) | Looking for a hack to bypass the passcode or screen lock on iPhones?
Jose Rodriguez, an iPhone enthusiast, has discovered a passcode bypass vulnerability in Apple's new iOS version 12 that potentially allows an attacker to access photos and contacts, including phone numbers and emails, on a locked iPhone XS and other recent iPhone models.
Rodriguez, who also discovered iPhone lock screen
|
Hack Vulnerability | |||
| 2018-10-01 14:52:01 | Will Facebook be fined after hack attack? (lien direct) | The social network could face a hefty fine if it is found to have breached data protection rules. | Hack | |||
| 2018-10-01 14:35:03 | (Déjà vu) Hack the Box: Sunday Walkthrough (lien direct) | Hello friends!! Today we are going to solve another CTF challenge “Sunday. Sunday is a retired vulnerable lab presented by Hack the Box for making online penetration practices according to your experience level; they have the collection of vulnerable labs as challenges, from beginners to Expert level. Level: Easy Task: find user.txt and root.txt file in victim's... Continue reading → | Hack | |||
| 2018-10-01 13:48:04 | Industry Reactions to Facebook Hack (lien direct) |  Facebook revealed last week that malicious actors may have obtained access tokens for 50 million accounts after exploiting several bugs related to the “Vi Facebook revealed last week that malicious actors may have obtained access tokens for 50 million accounts after exploiting several bugs related to the “Vi
|
Hack | |||
| 2018-10-01 08:16:02 | Several Bugs Exploited in Massive Facebook Hack (lien direct) | 
|
Hack | |||
| 2018-10-01 05:40:00 | Two SIM swappers arrested for CMCT hack (lien direct) | Suspects stand accused of stealing cryptocurrency worth $14 million from a California startup. | Hack | |||
| 2018-09-29 10:30:01 | Industry Leaders Reaction on Recent Facebook Hack (lien direct) | It is being reported that Facebook said an attack on its computer network led to the exposure of information from nearly 50 million of its users. The company discovered the breach earlier this week, finding that attackers had exploited a feature in Facebook's code that allowed them to take over user accounts. Facebook fixed the vulnerability and notified law enforcement officials. More … The ISBuzz Post: This Post Industry Leaders Reaction on Recent Facebook Hack | Hack Vulnerability Guideline | |||
| 2018-09-28 19:39:01 | Millions of accounts affected in latest Facebook hack (lien direct) |
 Facebook announced earlier today that its social network had been breached, resulting in 40 million accounts that were directly impacted. Learn more as the Facebook breach story develops.
Categories:
Cybercrime
Tags: access tokensbig breachesbreachdata breachfacebookFacebook breachfacebook hackpassword resetsocial mediasocial networksView Asvulnerabilitiesvulnerability
(Read more...)
Facebook announced earlier today that its social network had been breached, resulting in 40 million accounts that were directly impacted. Learn more as the Facebook breach story develops.
Categories:
Cybercrime
Tags: access tokensbig breachesbreachdata breachfacebookFacebook breachfacebook hackpassword resetsocial mediasocial networksView Asvulnerabilitiesvulnerability
(Read more...)
|
Hack | |||
| 2018-09-28 17:26:05 | iPhone XS Passcode Bypass Hack Exposes Contacts, Photos (lien direct) | Bypass works on iOS 12 and Apple's latest iPhone XS model phones allowing an attacker to access contacts and photos. | Hack | |||
| 2018-09-28 07:56:05 | Teenage Apple hacker avoids jail for \'hacky hack hack\' attack (lien direct) | The self-proclaimed Apple fan stole roughly 90GB of confidential data from the iPad and iPhone maker. | Hack | |||
| 2018-09-27 06:56:03 | Hack the Gemini inc:2 (CTF Challenge) (lien direct) | Hello Friends!! Today we are going to breach a new VM lab “Gemini inc:2” of the vulnhub series and before moving ahead you can also take a look over Gemini inc:1 which we had solved earlier. Gemini Inc has contacted you to perform a penetration testing on one of their internal system. This system has... Continue reading → | Hack | |||
| 2018-09-26 19:00:00 | Chegg to reset passwords for 40 million users after April 2018 hack (lien direct) | Chegg says it discovered the hack last week and that hackers didn't access financial or SSN data. | Hack | |||
| 2018-09-25 03:00:00 | The Sony hacker indictment: 5 lessons for IT security (lien direct) | In August 2018, the US Department of Justice (DoJ) unsealed the indictment of a North Korean spy, Park Jin Hyok, whom they claim was behind the hack against Sony and the creation and distribution of the WannaCry ransomware. The 170-plus-page document was written by Nathan Shields of the FBI's LA office and shows the careful sequence of forensic analysis they used to figure out how various attacks were conducted. | Hack | Wannacry | ||
| 2018-09-24 21:57:00 | SHEIN fashion retailer announces breach affecting 6.42 million users (lien direct) | Hack took place somewhere in June, but the company only discovered the breach in late August. | Hack | |||
| 2018-09-24 17:03:01 | Q&A: Reddit breach shows use of \'SMS 2FA\' won\'t stop privileged access pillaging (lien direct) | The recent hack of social media giant Reddit underscores the reality that all too many organizations — even high-visibility ones that ought to know better — are failing to adequately lock down their privileged accounts. Related: 6 best practices for cloud computing An excerpt from Reddit's mea culpa says it all: “On June 19, we […] | Hack | |||
| 2018-09-24 10:42:05 | (Déjà vu) Hack the Box Challenge: Canape Walkthrough (lien direct) | Hello friends!! Today we are going to solve another CTF challenge “Canape” which is available online for those who want to increase their skill in penetration testing and black box testing. Canape is retired vulnerable lab presented by Hack the Box for making online penetration practices according to your experience level; they have the collection of vulnerable... Continue reading → | Hack | |||
| 2018-09-22 05:20:00 | Hack the MinU: 1 (CTF Challenge) (lien direct) | Hello Friends! Today we are going to solve another CTF challenge “MinU: 1” This boot2root is an Ubuntu Based virtual machine and has been tested using Virtual Box. The network interface of the virtual machine will take its IP settings from DHCP. Your goal is to capture the flag on /root. You can download it... Continue reading → | Hack | |||
| 2018-09-21 13:09:02 | Homebuyers Being Targeted by Money Transfer Scam (lien direct) | Money Transfer Scam – Scammers hack the victims’s email accounts, monitor conversations between the buyers and title agents, send instructions on where to wire the money. A new homebuyer moves through a period of vulnerable transition as they invest in their future. This sensitive stage - a confusing flurry of representatives, documentation and planning - […] | Hack | |||
| 2018-09-19 20:00:00 | Zaif cryptocurrency exchange loses $60 million in recent hack (lien direct) | The Osaka-based cryptocurrency exchange discovered hack two days ago, and is working to secure funds to reimburse affected users. | Hack | |||
| 2018-09-19 17:30:04 | Cold Boot Attacks A Threat To All Modern Computers (lien direct) | After researchers recently discovered a way to physically hack into PC’s, Tyler Reese, Product Manager from One Identity, explains how organisations can protect systems from these attacks and what users can do to protect their data. Tyler Reese, Product Manager at One Identity: “Physical security is just as important as cyber security. Organization should make … The ISBuzz Post: This Post Cold Boot Attacks A Threat To All Modern Computers | Hack Threat | |||
| 2018-09-19 15:35:03 | (Déjà vu) Hack the ROP Primer: 1.0.1 (CTF Challenge) (lien direct) | Hello friends! Today we are going to take another CTF challenge known as ROP Primer. The credit for making this vm machine goes to “Bas” and it is another capture the flag challenge in which our goal is to capture all the flags to complete the challenge. You can download this VM here. We have 3... Continue reading → | Hack | |||
| 2018-09-19 10:12:00 | US judge allows e-voting despite hack fears (lien direct) | The judge, in the state of Georgia, is "gravely concerned" about hacking - but allows e-voting to go ahead. | Hack | |||
| 2018-09-18 17:35:00 | Internet-Connected CCTV Cameras Vulnerable to \'Peekaboo\' Hack (lien direct) | Zero-day flaw in China-based NUUO's video recorder technology still unfixed three months after vendor was alerted. | Hack | |||
| 2018-09-18 14:24:01 | Swiss, Russian FMs to Meet Next Week on Spy Row (lien direct) | Switzerland's foreign minister said Monday that he will meet his Russian counterpart next week after details emerged of alleged attempts by two Russian spies to hack sensitive Swiss targets. | Hack |
To see everything:
Our RSS (filtrered)
