What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2016-10-13 05:46:00 | Darkweb marketplaces can get you more than just spam and phish (lien direct) | The underground market Image by ThinkstockUnderground markets offer a great variety of services for cyber criminals to profit from. These forums offer items ranging from physical world items like drugs and weapons to digital world items such as spam/phishing delivery, exploit kit services, "Crypters", "Binders", custom malware development, zero-day exploits, and bulletproof hosting.To read this article in full or to leave a comment, please click here Image by ThinkstockUnderground markets offer a great variety of services for cyber criminals to profit from. These forums offer items ranging from physical world items like drugs and weapons to digital world items such as spam/phishing delivery, exploit kit services, "Crypters", "Binders", custom malware development, zero-day exploits, and bulletproof hosting.To read this article in full or to leave a comment, please click here |
||||
| 2016-10-13 05:42:00 | Yahoo shows that breach impacts can go far beyond remediation expenses (lien direct) | Companies that focus on the immediate breach remediation costs may be missing the big picture, and could be under-investing in security as a result.Several studies have come out recently trying to get a handle on the total costs of a data breach, with a large variation in costs - from less than $1 million on average, to $6 million - based on the data sets and types of included costs.But the actual numbers could be several times higher.Take the Yahoo breach, for example, which could lead to a $1 billion drop in the company's value.To read this article in full or to leave a comment, please click here | Guideline | Yahoo | ||
| 2016-10-13 05:30:00 | IDG Contributor Network: Beyond logging: Using SIEM to combat security, compliance issues (lien direct) | As connectivity grows, so do threats to the IT infrastructures under your care-and, by extension, your organization's ability to profit and serve its customers. Security strategies that worked fine in the not-so-distant past have grown woefully inadequate as the technology terrain shifts. You've probably heard the acronym SIEM being thrown around a lot these days and for good reasons. As security experts, we know that perimeter defenses simply aren't enough anymore, and we need a holistic view of our IT infrastructures. + Also on Network World: SIEM market dynamics in play +To read this article in full or to leave a comment, please click here | ||||
| 2016-10-13 05:00:00 | How CSOs can better manage third-party risks (lien direct) | In the latest episode of Security Sessions, CSO Editor-in-Chief Joan Goodchild chats with Scott Schneider from CyberGRX, a startup in the third-party risk analysis space, about best practices and tips for CSOs when working on a risk analysis plan with third party vendors. | ||||
| 2016-10-12 14:59:00 | Cisco fashions tactical ransomware defense (lien direct) | Cisco has taken a look at its security capabilities and those of its partners and come up with a playbook to address ransomware.Ransomware Defense can incorporate a range of Cisco products and address different levels of concern customers might have about ransomware, says Dan Hubbard, the CTO for Cisco's security business.More on Network World: Cisco Talos: Spam at levels not seen since 2010To read this article in full or to leave a comment, please click here | ||||
| 2016-10-12 14:43:00 | Feds want to set a trail for future AI advances (lien direct) | Will future developments in the realm of Artificial Intelligence be like the wild west or a more controlled situation? The real answer is probably somewhere in the middle but the government at least would like to see more measured research and development.The White House today issued report on future directions for AI called Preparing for the Future of Artificial Intelligence. In it, the report comes to several conclusions – some obvious and some perhaps less so. For example, it accepts that AI technologies will continue to grow in sophistication and ubiquity, thanks to AI R&D investments by government and industry.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-12 12:37:21 | Putin denies any Russian interest in alleged US election hacking (lien direct) | Russian President Vladimir Putin is rejecting claims that his country is behind any U.S. election-related hacking, saying "hysteria" is fueling the allegations."This has nothing to do with Russia's interests," he said on Wednesday at an investors conference in Moscow.Putin made the comments after the U.S. publicly blamed the Russian government last Friday for hacking U.S. officials and political groups in an effort to influence the upcoming presidential election.Stolen documents from those hacks, including sensitive emails, have been leaking online over the past months, potentially hurting the election chances of Democratic presidential candidate Hillary Clinton.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-12 11:52:00 | The Truth About Cybersecurity Certifications (lien direct) | It's a common trait amongst cybersecurity professionals. When they meet each other, discuss their qualifications with prospective employers, or print their business cards, there is often an alphabet soup of initials by their names, specifying the many certifications they've achieved.Now some of these certifications are certainly worthwhile but over the last few years, the entire industry has gone gaga with dozens of new cybersecurity certifications offered by for-profit organizations. This has led to a marketing push with a consistent message that more certifications equate to more money, knowledge, and opportunities for cybersecurity professionals.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-12 08:31:00 | IDG Contributor Network: A night to remember: Engineering lessons from the Titanic (lien direct) | Some 31 years ago, the RMS Titanic was discovered resting on the ocean floor. The legend of its sinking has been retold many times in books and movies. One compelling aspect of the story is the safety claims made by its creators. Even as reports of the disaster began to filter into New York, the vice president of the White Star Line stated, without qualification, “We place absolute confidence in the Titanic. We believe that the boat is unsinkable.†Obviously reality betrayed those maritime engineers' confidence.What lessons might this famous disaster teach engineers in modern data centers? In particular, how do we prevent hostile attacks-the “icebergs†that lurk on the seas we sail-from causing catastrophic breaches?To read this article in full or to leave a comment, please click here | APT 32 | |||
| 2016-10-12 08:18:00 | Foreign spies used RAT to hack Australian weather bureau with weak security controls (lien direct) | Foreign spies made off with an “unknown quantity of documents†after infecting Australia's meteorology bureau with a RAT, but the fact that security controls at the bureau were “insufficient†even for common cybercrime threats only helped the “state-sponsored cyber adversaries.â€After Australia's Bureau of Meteorology systems was hacked, unnamed government officials immediately blamed China and China immediately denied the “groundless accusations.†When the hack hit the news in December 2015, the Bureau of Meteorology (BOM) would not confirm if its systems had been compromised. In April, Australian's Prime Minister did confirm there had been a “significant cyber intrusion†at the Bureau.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-12 05:36:00 | 10 highest-paying IT security jobs (lien direct) | Highest-paying IT security jobs Image by ThinkstockData breaches, DDOS attacks, hacks and threats continue to dominate the headlines, so it's no surprise that some of the most in-demand IT jobs are in the security area. And with a massive skills gap, companies are willing to pay handsomely for skilled security talent at all levels.
"One area we're still seeing huge demand for is in cybersecurity, and hiring companies are willing to pay whatever it takes for talent that can help secure data and mitigate threats while simultaneously ensuring consistent and simplified accessibility from desktop to mobile devices. Companies are sending the message with their budgets: you can't put a price on that," says Jack Cullen, CEO of IT staffing firm Modis.
Here are the top 10 highest-paying security roles, culled from career site Dice.com clients' job postings and median salary range data from cloud compensation solutions firm PayScale.com.
1. Lead Software Security Engineer Image by ThinkstockData breaches, DDOS attacks, hacks and threats continue to dominate the headlines, so it's no surprise that some of the most in-demand IT jobs are in the security area. And with a massive skills gap, companies are willing to pay handsomely for skilled security talent at all levels.
"One area we're still seeing huge demand for is in cybersecurity, and hiring companies are willing to pay whatever it takes for talent that can help secure data and mitigate threats while simultaneously ensuring consistent and simplified accessibility from desktop to mobile devices. Companies are sending the message with their budgets: you can't put a price on that," says Jack Cullen, CEO of IT staffing firm Modis.
Here are the top 10 highest-paying security roles, culled from career site Dice.com clients' job postings and median salary range data from cloud compensation solutions firm PayScale.com.
1. Lead Software Security Engineer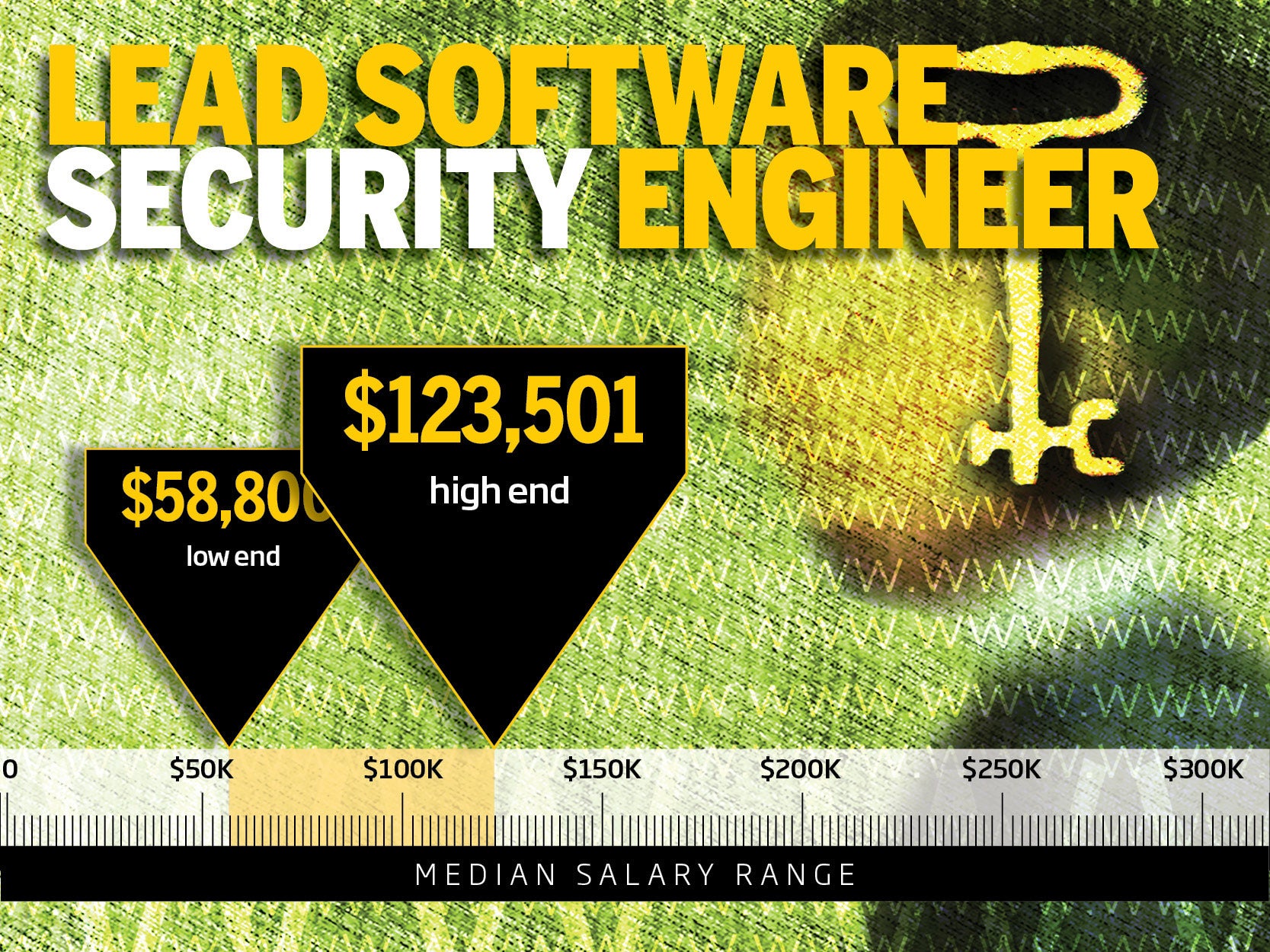 Image by ThinkstockTo read this article in full or to leave a comment, please click here Image by ThinkstockTo read this article in full or to leave a comment, please click here |
Guideline | |||
| 2016-10-12 05:31:00 | 12 hardware and software vulnerabilities you should address now (lien direct) | It's not a stretch to say that most organizations have at least some old hardware and software still in use. An old computer that's still chugging along, running an old operating system and perhaps an application that is hard to replace, doesn't necessarily raise a red flag with IT staff. Why spend money on new equipment or software if what's already in-house is adequate and functioning?Walker White, president of BDNA, a company that tracks and analyzes end-of-life (EOL) data for hardware, software and medical devices, says that the main problem with out-of-date software and legacy hardware is that once they pass their EOL cycle, the vendor no longer maintains or supports the products, resulting in security vulnerabilities and risk to organizations. As BDNA's State of the Enterprise Report (Q2 2016) indicates, many organizations are unaware of the potential liabilities, which can cost millions of dollars in the case of a successful attack after a vulnerability is exploited.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-12 05:29:00 | Leaky IoT devices help hackers attack e-commerce sites (lien direct) | Millions of IoT devices are misconfigured so that they can forward messages -- which, combined with default admin settings, allows them to be used to attack e-commerce and other websites, a new report says.The problem is well known and has been around for a more than a decade, said Ryan Barnett, principal security researcher at Akamai Technologies, which produced the report.The problem first came to Akamai's attention when the content delivery network noticed attacks against its customers where the attackers were checking to see whether particular user name and password combinations were valid on the site.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-12 05:28:00 | Thousands of internet-connected devices are a security disaster in the making (lien direct) | Set and forget Image by ThinkstockWe talked to a host of tech experts about the state of security in the internet of things world, and found out the good, the bad, and the very ugly.Under attack by ... cameras? Image by ThinkstockWe talked to a host of tech experts about the state of security in the internet of things world, and found out the good, the bad, and the very ugly.Under attack by ... cameras? Image by ThinkstockTo read this article in full or to leave a comment, please click here Image by ThinkstockTo read this article in full or to leave a comment, please click here |
||||
| 2016-10-12 04:38:00 | Record IoT DDoS attacks raise bar for defenders (lien direct) | Now that its source code has been released you can expect more attacks from Mirai, the malware behind the largest DDoS attack on record, which was powered by hijacked IoT devices.Since release of that code last week it has been responsible for smaller attacks that look like newcomers experimenting with the malware in preparation for bigger things, say security researchers at Incapsula. “Likely, these are signs of things to come and we expect to deal with Mirai-powered attacks in the near future,†they say in their blog post.That concern is echoed by researchers at F5, who say, “we can definitely expect the IoT DDoSing trend to rise massively in the global threat landscape.â€To read this article in full or to leave a comment, please click here | ||||
| 2016-10-11 13:18:55 | Facebook, Twitter cut access to monitoring tool used by police (lien direct) | Facebook, Instagram, and Twitter were handing over data to a monitoring tool that law enforcement agencies were using to track protesters, according to the American Civil Liberties Union.The social media analysis tool, called Geofeedia, had been harvesting posts from the social media networks for surveillance purposes, and more than 500 law enforcement and public safety agencies have been using it, the ACLU said in a Tuesday report.Through a public records request, the ACLU found that Geofeedia had entered into agreements with Facebook, Twitter, and Instagram for their users' data.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-11 11:59:00 | Microsoft released 10 patches, 6 rated critical, 5 fixed zero-day flaws (lien direct) | It is the first month for Microsoft's new patching model. Older Windows OSes will be treated like Windows 10, with the patches all rolled into a big bundle meant to fix security and non-security issues. However, there will also be a monthly security update that is supposed to resolve that month's issues without the previous month's fixes as well. On the third Tuesday of the month, the week after Patch Tuesday, Microsoft will release a preview of the upcoming patches so the non-security fixes can be tested to make sure the big rolled up patch doesn't blow anything up on some systems.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-11 11:02:38 | Second group of hackers found also targeting SWIFT users (lien direct) | A second hacking group is also trying to rob banks by exploiting the SWIFT money transfer system, following a US$81 million heist in February that used a similar approach.The cyberattacks have been going on since January and have been targeting companies in the U.S., Hong Kong, Australia, and other countries, according to a Tuesday report from security firm Symantec.A "rough guess" is that about 100 organizations have been hit so far, based on the 74 individual computer infections detected, the security firm added.As part of their attacks, the hackers used malware to cover up records of fraudulent transactions made over SWIFT, preventing their victims from learning about the money theft.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-11 09:12:31 | Encrypted communications could have an undetectable backdoor (lien direct) | Researchers warn that many 1024-bit keys used to secure communications on the internet today might be based on prime numbers that have been intentionally backdoored in an undetectable way.Many public-key cryptography algorithms that are used to secure web, email, VPN, SSH and other types of connections on the internet derive their strength from the mathematical complexity of discrete logarithms -- computing discrete logarithms for groups of large prime numbers cannot be efficiently done using classical methods. This is what makes cracking strong encryption computationally impractical.Most key-generation algorithms rely on prime parameters whose generation is supposed to be verifiably random. However, many parameters have been standardized and are being used in popular crypto algorithms like Diffie-Hellman and DSA without the seeds that were used to generate them ever being published. That makes it impossible to tell whether, for example, the primes were intentionally "backdoored" -- selected to simplify the computation that would normally be required to crack the encryption.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-11 08:41:00 | President Obama, NASA desire Mars habitation too (lien direct) | Hot on the heels of Elon Musk and his SpaceX company's grand plan to inhabit Mars, President Obama and NASA reminded the scientific world it too has a designs to inhabit the red planet – though at perhaps a far more deliberate pace than Musk wants.“We have set a clear goal vital to the next chapter of America's story in space: sending humans to Mars by the 2030s and returning them safely to Earth, with the ultimate ambition to one day remain there for an extended time. Getting to Mars will require continued cooperation between government and private innovators, and we're already well on our way. Within the next two years, private companies will for the first time send astronauts to the International Space Station,†Obama wrote in an editorial for CNN this week. “The next step is to reach beyond the bounds of Earth's orbit. I'm excited to announce that we are working with our commercial partners to build new habitats that can sustain and transport astronauts on long-duration missions in deep space. These missions will teach us how humans can live far from Earth -- something we'll need for the long journey to Mars.â€To read this article in full or to leave a comment, please click here | ||||
| 2016-10-11 08:07:00 | Netgear goes even more flexible with Arlo Pro video security cameras (lien direct) | Netgear is updating its Arlo wireless and wire-free home security camera systems with a professional version that takes the 'wire-free' and flexibility angle even further. Coming to retail shelves on October 23, the Arlo Pro system (small cameras that connect via a low-power, proprietary Wi-Fi to a router-connected base station) will now include two-way audio, a 100+ decibel siren, rechargeable batteries that can last up to six months, and improved motion detection software functionality. The new system will work with older cameras in the Arlo line, and newer cameras can work with older base station (if so desired).In addition, NETGEAR is announcing a set of accessories to make the cameras more flexible for placement and charging. For example, users who don't want to utilize the rechargeable batteries can recharge the unit through a micro-USB charger. The Arlo Pro Charging Station ($59.99) will let you charge up to two batteries simultaneously so you can swap out one quickly if the initial battery (extra batteries sold at $49.99 each) goes low.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-11 07:04:00 | Microsoft fleshes out seismic change to Windows patching (lien direct) | Microsoft has elaborated on the new patching policy for Windows 7 and Windows 8.1 that takes effect Tuesday.In a post to a company blog accompanied by graphics that resembled a periodic table, Michael Niehaus, a product marketing director for Windows 10, fleshed out the massive change in how Windows 7, the standard in business and the most popular OS on the planet, will be serviced starting with this month's Patch Tuesday.Microsoft announced the new plan two months ago, saying then that as of Oct. 11 it would offer only cumulative security updates for Windows 7 and 8.1, ending the decades-old practice of letting customers choose which patches they apply.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-11 06:55:00 | Yahoo Mail suspends automatic mail forwarding as privacy controversies swirl (lien direct) | In what can only be called awfully suspicious timing, Yahoo has turned off automatic email forwarding-a crucial feature when changing email accounts-for Yahoo Mail users. Anyone who has already enabled the feature is not affected, but others cannot activate it.On its help pages, Yahoo says mail forwarding is currently under development. “While we work to improve it, we've temporarily disabled the ability to turn on Mail Forwarding for new forwarding addresses,†the help page says.To read this article in full or to leave a comment, please click here | Yahoo | |||
| 2016-10-11 04:00:00 | A breach alone means liability (lien direct) | Rich Santalesa, a programmer turned writer and lawyer, brought an interesting turn of events to my attention last week. We need to pay heed: A litigant can have standing in a U.S. Federal breach case where no personal fraud or identity theft has yet occurred.Usually, a litigant has to have suffered injury-a breech caused them identity theft or other fraudulent activity based upon information released in a security breach. This means if you're cracked, you can be liable if personally identifiable information is released, exfiltrated, absconded, whatever. It also means that should you believe the axiom that currently most of us are hacked, we're in for a litigious treat. To read this article in full or to leave a comment, please click here | APT 17 | |||
| 2016-10-10 16:20:43 | WikiLeaks dumps another trove of email, allegedly from Clinton aide (lien direct) | U.S. accusations that WikiLeaks is helping Russian hackers influence the upcoming election hasn't stopped the controversial website from dumping emails allegedly stolen from a Hillary Clinton aide.On Monday, WikiLeaks released an additional batch of 2,000 emails stolen from Clinton's campaign chairman, John Podesta, which could fuel negative press coverage of her candidacy.This came after the site dumped the first batch of emails last Friday, the same day U.S. intelligence agencies publicly blamed the Russian government for hacking the emails of U.S. officials and political groups earlier this year.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-10 13:48:31 | Potential Apple Watch snooping: a not-so-paranoid cyberespionage risk (lien direct) | It may sound paranoid, but the next time you enter a highly confidential meeting, leave your smart watch behind. It's possible the device could be spying on you.That's what ministers in the U.K. are reportedly being told. They've recently been banned from wearing Apple Watches during cabinet meetings on fears that the devices could be hacked by Russian cyberspies, according to The Telegraph.Mobile phones have already been prohibited from cabinet meetings, but the U.K. government has reportedly taken the extra step of also banning smart watches.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-10 08:05:57 | Certificate policy violations force reform at StartCom and WoSign (lien direct) | The top management of StartCom and WoSign will be replaced and the two certificate authorities will undergo audits after browser vendors discovered that they mis-issued many digital certificates, violating industry rules. The investigation launched by Mozilla led to the discovery of 13 instances where China-based WoSign and its subsidiary StartCom issued certificates with various types of problems. Evidence was also found that both CAs issued certificates signed with the SHA-1 algorithm after Jan. 1 in violation of industry rules and intentionally backdated them to avoid being caught. As a result, Mozilla said that it has lost faith in the ability of WoSign and StartCom to correctly carry out the functions of a CA and announced that it will stop trusting new certificates from the two companies. Apple followed suit and announced its own ban for future WoSign and StartCom certificates last week.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-10 07:30:00 | Doxing, trolling and \'grossly offensive\' communications are now illegal in the UK (lien direct) | To observe Hate Crime Awareness Week, the UK's Crown Prosecution Service (CPS) is cracking down on internet bullies and trolls. Actions like posting humiliating photoshopped images of people on social media platforms, creating derogatory hashtags and doxing can get cyber bullies prosecuted.CPS published new social media guidelines to help prosecutors determine which online actions are illegal. The guidelines take aim at doxing, inciting virtual mobbing – encouraging others to participate in online harassment – and fake social media profiles used for online abuse to name but a few.Retweeting something the CPS considers “grossly offensive, indecent, obscene or false†can also land a person in legal hot water. Yet Alison Saunders, CPS director of public prosecutions, stressed to the BCC that prosecutors can't use the guidelines to “stifle free speech.†People in the UK better check out what actions are now illegal since saying you didn't know it was illegal just won't cut it.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-10 03:37:00 | What IT admins love/hate about 8 top network monitoring tools (lien direct) | Network monitoring systems typically look for slow, overloaded, failing or crashed servers, routers, switches and network connections – and alert network administrators to the problem. According to the IT Central Station user community, the most important criteria to consider when choosing network monitoring software are scalability, flexibility and multi-tenancy.Eight of the top-ranked network monitoring software products are CA Unified Infrastructure Management, SevOne, Microsoft SCOM, FortiSIEM (AccelOps), ScienceLogic, NetScout TruView, Opsview Enterprise and Nagios, according to online reviews by enterprise users in the IT Central Station community.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-10 02:51:00 | New products of the week 10.10.16 (lien direct) | New products of the week Our roundup of intriguing new products. Read how to submit an entry to Network World's products of the week slideshow.NetScaler VPX 100G Our roundup of intriguing new products. Read how to submit an entry to Network World's products of the week slideshow.NetScaler VPX 100G  Key features: NetScaler VPX 100G is the industry's first fully-featured, virtualized ADC that delivers 100 Gigabits per second performance on commodity hardware. More info.To read this article in full or to leave a comment, please click here Key features: NetScaler VPX 100G is the industry's first fully-featured, virtualized ADC that delivers 100 Gigabits per second performance on commodity hardware. More info.To read this article in full or to leave a comment, please click here |
||||
| 2016-10-09 09:41:00 | 3 replacement Galaxy Note 7 phones caught fire in the past week (lien direct) | Replacement Galaxy Note 7 phones may not be any safer than the Note 7 devices which caught fire and caused a recall, based on three replacement Note 7 devices catching fire in the past week.Samsung is reportedly investigating the fire fiascos, claiming that the company takes every Galaxy Note 7 fire report “seriously.†Yet after a company official goofed and mistakenly sent a text message meant for a colleague to one of the melted phone owners, the company's concern for customers hardly seems sincere.Replacement Galaxy Note 7 catches fire, fills bedroom with smokeMichael Klering of Kentucky had his replacement Galaxy Note 7 for a little more than a week. On Tuesday, October 4, he was “scared to death†when he and his wife awoke to a bedroom full of smoke.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-07 17:40:58 | US may use sanctions to punish Russia for election hacking (lien direct) | The U.S. response to election-related hacks that the Obama administration now blames on the Russian government could include sanctions against that country. The administration has said that it has a range of options, including economic sanctions, to respond to Russian cyber attacks. On Friday, a Republican lawmaker said he would propose legislation to move those sanctions forward. Senator Cory Gardner, who represents Colorado, said his planned legislation would mandate that the U.S. government investigate Russian cyber criminals and sanction them when appropriate.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-07 13:50:29 | US officially blames Russian government for election-related hacking (lien direct) | U.S. officials are publicly blaming the Russian government for several high-profile hacks against political groups that they claim were meant to interfere with the upcoming election.U.S. intelligence agencies are confident Russia was responsible, the Department of Homeland Security and the Office of the Director of National Intelligence said in a statement on Friday.They allege that the Russian government compromised the emails of U.S. officials and institutions and then publicly leaked them online through sites such as WikiLeaks, DCLeaks, and the anonymous hacker Guccifer 2.0, who took credit for breaching the Democratic National Committee earlier this year.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-07 06:12:00 | 4 ways Cognizant customers can protect themselves amid corruption probe (lien direct) | Following Cognizant's announcement late last week that it had launched an internal investigation into possible anti-corruption violations, there have been more questions than answers about what may have occurred at the Teaneck, N.J.-headquartered provider of offshore IT services. Particularly perplexing to some was the attendant news that the company's long-time president Gordon Coburn was stepping down.Cognizant gave no reason for the departure of Coburn, who has been replaced by head of IT services Rajeev Mehta. However, the company did say in a regulatory filing that it was looking into whether it had violated the U.S. Foreign Corrupt Practices Act (FCPA) within a small number of company-owned facilities. Cognizant owns 12 of the 45 delivery centers it operates in India, where 75 percent of its employees work.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-07 04:00:00 | IDG Contributor Network: DDoS attacks using IoT devices follow The Manchurian Candidate model (lien direct) | In the movie The Manchurian Candidate, two soldiers are kidnapped and brainwashed into sleeper agents. Later the soldiers become unwitting assassins when activated by a handler.  Sound familiar? It should.Hackers use a similar model for Distributed Denial of Service (DDoS) attacks using IoT devices. This process has four phases. Capture: Identify and take over control of IoT devices Subvert: Reprogram the device to conduct malicious acts Activate: Instruct the hacked device to launch attack Attack: Launch the DDoS attack Why are such attacks increasing? How can IoT device security be hardened? What DDoS protections are available? What advisory resources are available? Let's take a look.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-07 03:41:00 | (Déjà vu) How to keep IT security together in a company that\'s gone bankrupt (lien direct) | Corporate chaos Image by peteThe supply chain upon which modern multinational commerce depends was thrown into chaos earlier this year when South Korea's Hanjin Shipping filed for bankruptcy. Dozens of container ships with hundreds of crew and thousands of pounds of cargo onboard were essentially stranded at sea, as ports barred the ships' entry for fear that they wouldn't be able to pay for docking services.To read this article in full or to leave a comment, please click here Image by peteThe supply chain upon which modern multinational commerce depends was thrown into chaos earlier this year when South Korea's Hanjin Shipping filed for bankruptcy. Dozens of container ships with hundreds of crew and thousands of pounds of cargo onboard were essentially stranded at sea, as ports barred the ships' entry for fear that they wouldn't be able to pay for docking services.To read this article in full or to leave a comment, please click here |
||||
| 2016-10-07 03:40:00 | How Shodan helped bring down a ransomware botnet (lien direct) | Shodan is a search engine that looks for internet-connected devices. Hackers use it to find unsecured ports and companies use it to make sure that their infrastructure is locked down. This summer, it was also used by security researchers and law enforcement to shut down a ransomware botnet.The Encryptor RaaS botnet offered ransomware as a service, allowing would-be criminals to get up and going quickly with their ransomware campaigns, without having to write code themselves, according to report released last week.The ransomware first appeared in the summer of 2015. It didn't make a big impact -- in March, Cylance reported that it had just 1,818 victims, only eight of whom had paid the ransom.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-07 03:01:00 | IDG Contributor Network: IoT security guidance emerges (lien direct) | More than a year ago, an eye-opening RAND study on cybersecurity comprehensively explored just how vulnerable the Internet of Things (IoT) is and was going to be. Afterthought-style patch-on-patch security, as well as significant vulnerability risks involved with slapping internet connectivity on previously non-connected objects, were among the startling findings and predictions in that report. Since then, questions have arisen as to just how one should approach the security needs of the soon-to-be billions of networked, smart, cheap sensors expanding around the globe like popcorn.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-06 17:40:02 | Verizon may want a $1 billion discount on Yahoo (lien direct) | Verizon may be getting cold feet with its acquisition of Yahoo. Reportedly, it's asking for a $1 billion discount on the original $4.8 billion deal for the Internet company.Recent news about Yahoo's massive data breach and its alleged secret email scanning program has diminished the company's value in the eyes of Verizon, according to a Thursday report by the New York Post.Tim Armstrong, the head of AOL, which Verizon acquired in 2015, reportedly has met with Yahoo executives about reducing the acquisition price. Â "He's pretty upset about the lack of disclosure and he's saying can we get out of this or can we reduce the price?" the report said, quoting what it called a source familiar with Verizon's thinking.To read this article in full or to leave a comment, please click here | Yahoo | |||
| 2016-10-06 16:40:25 | How companies can deal with insider data theft (lien direct) | To learn that your company's confidential data was stolen -- not by any hacker, but by an employee -- is a nightmare scenario that no one wants to face.But it's also a risk that's very real. The recent arrest of a former NSA contractor suspected of stealing classified government files is just the latest high-profile example, and security experts say all companies need to be on guard against potential insider threats.How serious is the threat? It's not every day that thieving employees take to the digital black market to sell their company's sensitive information, but it does happen, and incidents have been occurring more frequently, said Andrei Barysevich, a director at security firm Flashpoint.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-06 13:19:00 | How to shield your company from cyber enforcement (lien direct) | This vendor-written tech primer has been edited by Network World to eliminate product promotion, but readers should note it will likely favor the submitter's approach.A lot has changed in the world of cyber regulation. September 2015 saw the widely reported SEC administrative proceeding against RT Jones for violating the “Safeguard Rule†in failing to establish and implement written cyber protection policies. Next was Morgan Stanley. And this past March the Consumer Financial Protection Bureau (CFPB) brought a pre-emptive action against a company that hadn't even had a breach.At this stage, it's safe to assume the list of regulators and their security requirements will continue to grow and fines and penalties will become more severe. In fact, just last week the New York Department of Financial Services (DFS) proposed new cyber guidelines for financial institutions.To read this article in full or to leave a comment, please click here | Guideline | |||
| 2016-10-06 12:31:00 | How Google Home\'s \'always on\' will affect privacy (lien direct) | Google this week took the wraps off Google Home, its smart speaker and home entertainment hub, but questions remain about the impact the device will have on users' privacy.A direct rival to Amazon Echo, Google Home is the company's entry into the smart home market.Want Google Home to play your favorite song? Just say, "OK, Google" and ask for it to play the music. Want the device, which is equipped with its artificial-intelligence based Assistant, to play that funny cat video from YouTube on your TV? You get the picture.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-06 11:16:00 | Spammers prefer Trump over Clinton, but are rapidly losing faith in Trump (lien direct) | Whatever difficulties Donald Trump may be having with white college-educated women, African Americans, Latinos, hawkish conservatives and the co-hosts of “Morning Joe,†he's far and away the favorite presidential candidate of at least one demographic group: spammers.However, he seems to have lost significant support among that group as well.These conclusions are drawn from a year's worth of data assembled by Network World Test Alliance member Joel Snyder, a senior partner at Opus One in Tucson, Ariz. Opus One has been testing anti-spam products for more than a decade, and, as the following chart shows, Trump-related spam has dwarfed Clinton-related spam over the past year … only less so as the campaign has worn on.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-06 10:51:00 | What CSOs can learn from the Yahoo breach (lien direct) | In the latest episode of Security Sessions, CSO Editor-in-chief Joan Goodchild talks about the implications of the Yahoo data breach, in which up to 500 million accounts were hacked. Joining Goodchild in the discussion is Kevin O'Brien, CEO and founder of GreatHorn, who offers advice to CSOs and other IT security leaders on ways to learn from this particular breach. | Guideline | Yahoo | ||
| 2016-10-06 09:54:07 | FCC to vote on strict privacy rules for ISPs in late October (lien direct) | The U.S. Federal Communications Commission will push forward with controversial privacy regulations that would require broadband providers to get customer permission before using and sharing geolocation, browsing histories, and other personal information.Broadband providers have complained the proposal puts stronger privacy rules in place for them than for internet companies like Google and Facebook. But FCC Chairman Tom Wheeler has scheduled a final vote on the regulations for Oct. 27.Broadband customers should have the ability to make informed decisions about their privacy, and the rules are designed to help them, FCC officials said in a press briefing,To read this article in full or to leave a comment, please click here | ||||
| 2016-10-06 08:00:00 | Spotify ads slipped malware onto PCs and Macs (lien direct) | Spotify's ads crossed from nuisance over to outright nasty this week, after the music service's advertising started serving up malware to users on Wednesday. The malware was able to automatically launch browser tabs on Windows and Mac PCs, according to complaints that surfaced online.As is typical for this kind of malware, the ads directed users' browsers to other malware-containing sites in the hopes that someone would be duped into downloading more malicious software. The “malvertising†attack didn't last long as Spotify was able to quickly correct the problem.“We've identified an issue where a small number of users were experiencing a problem with questionable website pop-ups in their default browsers as a result of an isolated issue with an ad on our Free tier,†Spotify said on several threads in its support forums. “We have now identified the source of the problem and have shut it down. We will continue to monitor the situation.â€To read this article in full or to leave a comment, please click here | ||||
| 2016-10-06 07:07:00 | The State of Cybersecurity Professional Careers (lien direct) | I've written about and researched the cybersecurity skills shortage for many years. For example, ESG research indicates that 46% of organizations claim to have a “problematic shortage†of cybersecurity skills this year – an 18% increase from 2015 (note: I am an ESG employee).Of course, I'm not the only one looking into the cybersecurity skills shortage. For example: According to Peninsula Press (a project of the Stanford University Journalism Program), more than 209,000 U.S.-based cybersecurity jobs remained unfilled, and postings are up 74 percent over the past five years. Analysis of the U.S. Bureau of Labor Statistics indicates that the demand for cybersecurity professionals is expected to grow 53 percent by 2018. So many researchers agree then that we don't have enough skilled prospects to fill all of the open cybersecurity jobs. Okay but that puts a heck of a lot of burden on the existing cybersecurity workforce. Are they up to the task? Do they have the right training? Are they managing their careers appropriately?To read this article in full or to leave a comment, please click here | ||||
| 2016-10-06 06:44:03 | EU privacy watchdogs have questions about Yahoo\'s secret email scanning (lien direct) | European Union privacy watchdogs are concerned by reports that Yahoo has been secretly scanning its users' email at the request of U.S. intelligence services."It goes far beyond what is acceptable," said Johannes Caspar, Commissioner for Data Protection and Freedom of Information in Hamburg, Germany.Reuters reported on Tuesday that Yahoo had built a system for U.S. government agencies to search all of its users' incoming emails. Other tech companies were quick to distance themselves, saying they would have challenged any such request in court.To read this article in full or to leave a comment, please click here | Yahoo | |||
| 2016-10-06 06:16:00 | Security vs. privacy: The endless fiery debate continues (lien direct) | The intractable nature of the “privacy vs. security†debate, in a world where the internet is a tool for criminals, spies and terrorists as well as for billions of law-abiding citizens, was on full display during Wednesday's Cambridge Cyber Summit at MIT.Not surprisingly, it didn't get resolved.The event, hosted by The Aspen Institute, CNBC and MIT, featured top-level government officials, private-sector experts and activists, who all agreed that there needs to be a “conversation†about how to “balance†the two, and that to achieve it will require more effective cooperation between the public and private sectors.But there was no agreement about where that balance lies. About the best they could do, after some conversation that got chaotic at times, was agree that they should continue the conversation.To read this article in full or to leave a comment, please click here | ||||
| 2016-10-05 16:06:20 | Yahoo\'s secret email scans helped the FBI probe terrorists (lien direct) | What Yahoo was looking for with its alleged email scanning program may have been signs of code used by a foreign terrorist group. The company was searching for a digital "signature" of a communication method used by a state-sponsored terrorist group, according to a new report from The New York Times that provided more details on Yahoo's email scanning.  The report on Wednesday report didn't identify the signature or say if it involved any cryptographic computer code. But the article said it was the U.S. Department of Justice, and not the National Security Agency, that had obtained a court order forcing Yahoo to comply. A Reuters report on Tuesday wasn't clear about what agencies were involved in the probe.To read this article in full or to leave a comment, please click here | Yahoo |
To see everything:
Our RSS (filtrered)
