What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2019-12-18 03:32:00 | New BlueKeep Scanner Lets You Find Vulnerable Windows PCs (lien direct) | A new scanning tool is now available for checking if your computer is vulnerable to the BlueKeep security issue in Windows Remote Desktop Services. [...] | Tool | |||
| 2019-12-11 14:00:00 | Google Cloud Platform security monitoring with USM Anywhere™ (lien direct) | According to a 2019 Cyber Security Report published by the International Information System Security Certification Consortium, 93 percent of organizations say they are concerned about cloud security and 28 percent admit to having experienced cloud security incidents during the past year. The reality is, most companies lack the specialized knowledge and skills needed to provide that customer data stored in the cloud is protected Cloud service providers (CSPs) do provide extra security layers, such as automating threat detection, with the intent of making their customers feel more confident in the security of the cloud. However, the number of cloud breaches that are being reported shows that CSPs and organizations alike continue to struggle with cloud security. Much of this is due to a lack of unified visibility not just in the cloud, but across an organization’s entire network, siloed teams and technologies, lack of threat intelligence, and partnerships with third-parties whose security controls are not up to snuff. To address these challenges, many in the industry are advocating for organizations to simplify and unify their security approach, i.e. bring as many controls as possible into a single solution in order to break down the silos between security teams and technologies and to give greater visibility across the organization. We at AT&T Cybersecurity help organizations to accomplish this with our Unified Security Management™ (USM) Anywhere platform. Of course, the effectiveness of any security solution is largely determined by the threat intelligence underpinning it. In any environment, we need to identify the common tactics, techniques, and procedures (TTPs) adversaries are using in their attacks. Below, we provide an overview of the latest threat intelligence from Alien Labs™ for Google Cloud Platform (GCP), which helps security practitioners to discover issues in their cloud workloads and detect adversaries exploiting attack vectors commonly seen in cloud environments. Google Cloud Platform integration in USM This summer, AT&T Cybersecurity launched the USM Anywhere™ integration with GCP. Through the USM Anywhere Alien App for GCP, USM can now consume all logging information managed by the Stackdriver utility in a configurable and intuitive way. Google Cloud Platform logs are provided through three major channels: Audit Logs. Record all events impacting objects within the environment. These logs are used to monitor any cloud assets, presenting a solid baseline for security detection. VPC Flow Logs. Half way between resource monitoring and cloud infrastructure security, these logs are the delights of NIDS enthusiasts. Firewall Logs. These help with auditing firewall rules events, and they are useful in detecting risky open ports and other configuration issues. In USM, these channels are processed by different plugins, which extract pieces of intelligence and map them to variables that are easy to steer into orchestration rules. The correlation engine allows for the combination of detections from different channels into a single orchestration rule, scaling GCP security to a new level. To prevent an intrusion from being recorded or triggering a notification, adversaries may try to disable audit logging once they get the necessary permissions. To protect against that, the product has out of the box correlation rules to generate an alert if any of the logging features is disabled. | Tool Threat Guideline | Uber | ||
| 2019-12-07 17:48:38 | Amazon battles leaky S3 buckets with a new security tool (lien direct) | A new AWS feature is supposed to help avoid accidental misconfigurations that could result in sensitive data being exposed, a company’s brand being damaged, and even – potentially – put its customers at risk. Read more in my article on the Bitdefender Business Insights blog. | Tool | |||
| 2019-12-06 19:25:22 | TeamViewer unveils new patch management system (lien direct) | The new tool will provide IT departments with system-wide visibility of all the patches needed. | Tool | |||
| 2019-12-05 12:34:51 | China used the Great Cannon DDoS Tool against forum used by Hong Kong protestors (lien direct) | China is accused to have used the “Great Cannon” DDoS tool to launch attacks against LIHKG, a forum used by Hong Kong residents to organize protests. The Great Cannon Distributed Denial of Service (DDoS) tool was used again by the Chinese government, this time it was used to target the LIHKG forum used by Hong Kong protesters to […] | Tool | |||
| 2019-12-04 15:28:00 | The “Great Cannon” has been deployed again (lien direct) |
Summary
The Great Cannon is a distributed denial of service tool (“DDoS”) that operates by injecting malicious Javascript into pages served from behind the Great Firewall. These scripts, potentially served to millions of users across the internet, hijack the users’ connections to make multiple requests against the targeted site. These requests consume all the resources of the targeted site, making it unavailable:
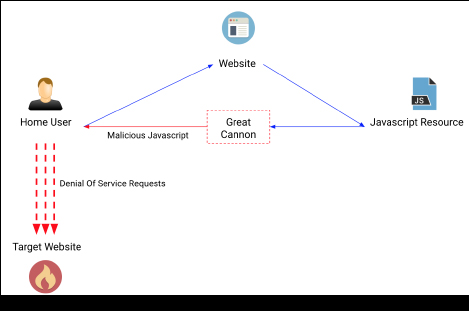 Figure 1: Simplified diagram of how the Great Cannon operates
The Great Cannon was the subject of intense research after it was used to disrupt access to the website Github.com in 2015. Little has been seen of the Great Cannon since 2015. However, we’ve recently observed new attacks, which are detailed below.
Most recent attacks against LIHKG
The Great Cannon is currently attempting to take the website LIHKG offline. LIHKG has been used to organize protests in Hong Kong. Using a simple script that uses data from UrlScan.io, we identified new attacks likely starting Monday November 25th, 2019.
Websites are indirectly serving a malicious javascript file from either:
http://push.zhanzhang.baidu.com/push.js; or
http://js.passport.qihucdn.com/11.0.1.js
Normally these URLs serve standard analytics tracking scripts. However, for a certain percentage of requests, the Great Cannon swaps these on the fly with malicious code:
Figure 1: Simplified diagram of how the Great Cannon operates
The Great Cannon was the subject of intense research after it was used to disrupt access to the website Github.com in 2015. Little has been seen of the Great Cannon since 2015. However, we’ve recently observed new attacks, which are detailed below.
Most recent attacks against LIHKG
The Great Cannon is currently attempting to take the website LIHKG offline. LIHKG has been used to organize protests in Hong Kong. Using a simple script that uses data from UrlScan.io, we identified new attacks likely starting Monday November 25th, 2019.
Websites are indirectly serving a malicious javascript file from either:
http://push.zhanzhang.baidu.com/push.js; or
http://js.passport.qihucdn.com/11.0.1.js
Normally these URLs serve standard analytics tracking scripts. However, for a certain percentage of requests, the Great Cannon swaps these on the fly with malicious code:
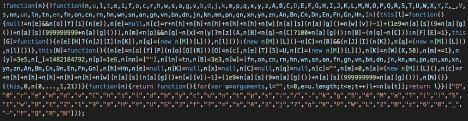 Figure 2: Malicious code served from the Great Cannon
The code attempts to repeatedly request the following resources, in order to overwhelm websites and prevent them from being accessible:
http://lihkg.com/
https://i.loli.net/2019/09/29/hXHglbYpykUGIJu.gif?t=
https://na.cx/i/XibbJAS.gif?t=
https://na.cx/i/UHr3Dtk.gif?t=
https://na.cx/i/9hjf7rg.gif?t=
https://na.cx/i/qKE4P2C.gif?t=
https://na.cx/i/0Dp4P29.gif?t=
https://na.cx/i/mUkDptW.gif?t=
https://na.cx/i/ekL74Sn.gif?t=
https://i.ibb.co/ZBDcP9K/LcSzXUb.gif?t=
https://66.media.tumblr.com/e06eda7617fb1b98cbaca0edf9a427a8/tumblr_oqrv3wHXoz1sehac7o1_540.gif?t=
https://na.cx/i/6hxp6x9.gif?t=
https://live.staticflickr.com/65535/48978420208_76b67bec15_o.gif?t=
https://i.lihkg.com/540/https://img.eservice-hk.net/upload/2018/08/09/181951_60e1e9bedea42535801bc785b6f48e7a.gif?t=
https://na.cx/i/E3sYryo.gif?t=
https://na.cx/i/ZbShS2F.gif?t=
https://na.cx/i/LBppBac.gif?t=
http://i.imgur.com/5qrZMPn.gif?t=
https://na.cx/i/J3q35jw.gif?t=
https://na.cx/i/QR7JjSJ.gif?t=
https://na.cx/i/haUzqxN.gif?t=
https://na.cx/i/3hS5xcW.gif?t=
https://na.cx/i/z340DGp.gif?t=
https://luna.komica
Figure 2: Malicious code served from the Great Cannon
The code attempts to repeatedly request the following resources, in order to overwhelm websites and prevent them from being accessible:
http://lihkg.com/
https://i.loli.net/2019/09/29/hXHglbYpykUGIJu.gif?t=
https://na.cx/i/XibbJAS.gif?t=
https://na.cx/i/UHr3Dtk.gif?t=
https://na.cx/i/9hjf7rg.gif?t=
https://na.cx/i/qKE4P2C.gif?t=
https://na.cx/i/0Dp4P29.gif?t=
https://na.cx/i/mUkDptW.gif?t=
https://na.cx/i/ekL74Sn.gif?t=
https://i.ibb.co/ZBDcP9K/LcSzXUb.gif?t=
https://66.media.tumblr.com/e06eda7617fb1b98cbaca0edf9a427a8/tumblr_oqrv3wHXoz1sehac7o1_540.gif?t=
https://na.cx/i/6hxp6x9.gif?t=
https://live.staticflickr.com/65535/48978420208_76b67bec15_o.gif?t=
https://i.lihkg.com/540/https://img.eservice-hk.net/upload/2018/08/09/181951_60e1e9bedea42535801bc785b6f48e7a.gif?t=
https://na.cx/i/E3sYryo.gif?t=
https://na.cx/i/ZbShS2F.gif?t=
https://na.cx/i/LBppBac.gif?t=
http://i.imgur.com/5qrZMPn.gif?t=
https://na.cx/i/J3q35jw.gif?t=
https://na.cx/i/QR7JjSJ.gif?t=
https://na.cx/i/haUzqxN.gif?t=
https://na.cx/i/3hS5xcW.gif?t=
https://na.cx/i/z340DGp.gif?t=
https://luna.komica |
Tool Threat | |||
| 2019-12-03 17:12:11 | NBlog Dec 3 - infosec driving principles (lien direct) | In an interview for CIO Dive, Maersk's recently-appointed CISO Andy Powell discussed aligning the organization with these five 'key operating principles': "The first is trust. The client has got to trust us with their data, to trust us to look at their business. So we've got to build trust through the cybersecurity solutions that we put in place. That is absolutely fundamental. So client trust, client buy-in has been fundamental to what we tried to drive as a key message. The second is resilience. Because you've got to have resilient systems because clients won't give you business if you're not resilient ... The third really is around the fact that security is everybody's responsibility. And we push that message really hard across the company … be clear about what you need to do and we train people accordingly. ...The fourth one really is accountability of security and I have pushed accountability for cyber risk to the business. ... And the final piece, and this has been one of the big call outs of my team to everybody, is that security is a benefit, not a burden. The reason I say that is people's perception is that security will slow things down, will get in the way ... the reality is that if you involve security early enough, you can build solutions that actually attract additional clients."Fair enough Andy. I wouldn't particularly quarrel with any of them, but as to whether they would feature in my personal top-five I'm not so sure. Here are five others they'd be competing against, with shipping-related illustrations just for fun:Governance involves structuring, positioning, setting things up and guiding the organization in the right overall direction - determining then plotting the optimal route to the ship's ultimate destination, loading up with the right tools, people and provisions. Corporate governance necessarily involves putting things in place for both protecting and exploiting information, a vital and valuable yet vulnerable business asset;Information is subject to risks that can and probably should be managed proactively, just as a ship's captain doesn't merely accept the inclement weather and various other hazards but, where appropriate, actively mitigates or avoids them, dynamically reacting and adjusting course as things change;Flexibility and responsiveness, along with resilience and ro "The first is trust. The client has got to trust us with their data, to trust us to look at their business. So we've got to build trust through the cybersecurity solutions that we put in place. That is absolutely fundamental. So client trust, client buy-in has been fundamental to what we tried to drive as a key message. The second is resilience. Because you've got to have resilient systems because clients won't give you business if you're not resilient ... The third really is around the fact that security is everybody's responsibility. And we push that message really hard across the company … be clear about what you need to do and we train people accordingly. ...The fourth one really is accountability of security and I have pushed accountability for cyber risk to the business. ... And the final piece, and this has been one of the big call outs of my team to everybody, is that security is a benefit, not a burden. The reason I say that is people's perception is that security will slow things down, will get in the way ... the reality is that if you involve security early enough, you can build solutions that actually attract additional clients."Fair enough Andy. I wouldn't particularly quarrel with any of them, but as to whether they would feature in my personal top-five I'm not so sure. Here are five others they'd be competing against, with shipping-related illustrations just for fun:Governance involves structuring, positioning, setting things up and guiding the organization in the right overall direction - determining then plotting the optimal route to the ship's ultimate destination, loading up with the right tools, people and provisions. Corporate governance necessarily involves putting things in place for both protecting and exploiting information, a vital and valuable yet vulnerable business asset;Information is subject to risks that can and probably should be managed proactively, just as a ship's captain doesn't merely accept the inclement weather and various other hazards but, where appropriate, actively mitigates or avoids them, dynamically reacting and adjusting course as things change;Flexibility and responsiveness, along with resilience and ro |
Tool Guideline | NotPetya | ||
| 2019-12-03 16:40:41 | Notorious spy tool taken down in global operation (lien direct) | IM-RAT, which could be had for as little as US$25, was bought by nearly 15,000 people | Tool | ★★★ | ||
| 2019-12-03 16:00:00 | Analyse exceller & # 8211;Conseils et astuces pour analyser les données avec Microsoft Excel Excelerating Analysis – Tips and Tricks to Analyze Data with Microsoft Excel (lien direct) |
Les enquêtes sur la réponse aux incidents n'impliquent pas toujours des artefacts standard basés sur l'hôte avec des outils d'analyse et d'analyse entièrement développés.Chez FireEye Mandiant, nous rencontrons fréquemment des incidents qui impliquent un certain nombre de systèmes et de solutions qui utilisent des données de journalisation ou d'artefacts personnalisés.La détermination de ce qui s'est passé dans un incident consiste à plonger dans le type de données qui nous sont présentés, à l'apprendre et à développer un moyen efficace d'analyser les preuves importantes.
L'un des outils les plus efficaces pour effectuer ce type d'analyse est celui qui est dans presque tout le monde \'s Toolkit
Incident response investigations don\'t always involve standard host-based artifacts with fully developed parsing and analysis tools. At FireEye Mandiant, we frequently encounter incidents that involve a number of systems and solutions that utilize custom logging or artifact data. Determining what happened in an incident involves taking a dive into whatever type of data we are presented with, learning about it, and developing an efficient way to analyze the important evidence. One of the most effective tools to perform this type of analysis is one that is in almost everyone\'s toolkit |
Tool | ★★★ | ||
| 2019-12-03 09:18:47 | Windows for Pentester: Certutil (lien direct) | In this article, we are going to describe the utility of Certutil tool and how vital it is in Windows Penetration Testing. TL; DR Certutil is a preinstalled tool on Windows OS that can be used to download malicious files and evade Antivirus. It is one of the Living Off Land (LOL) Binaries. Disclaimer The... Continue reading → | Tool | |||
| 2019-12-02 07:09:50 | truffleHog – Search Git for High Entropy Strings with Commit History (lien direct) |  truffleHog is a Python-based tool to search Git for high entropy strings, digging deep into commit history and branches. This is effective at finding secrets accidentally committed.
truffleHog previously functioned by running entropy checks on git diffs. This functionality still exists, but high signal regex checks have been added, and the ability to surpress entropy checking has also been added.
truffleHog --regex --entropy=False https://github.com/dxa4481/truffleHog.git
or
truffleHog file:///user/dxa4481/codeprojects/truffleHog/
truffleHog will go through the entire commit history of each branch, and check each diff from each commit, and check for secrets.
Read the rest of truffleHog – Search Git for High Entropy Strings with Commit History now! Only available at Darknet. truffleHog is a Python-based tool to search Git for high entropy strings, digging deep into commit history and branches. This is effective at finding secrets accidentally committed.
truffleHog previously functioned by running entropy checks on git diffs. This functionality still exists, but high signal regex checks have been added, and the ability to surpress entropy checking has also been added.
truffleHog --regex --entropy=False https://github.com/dxa4481/truffleHog.git
or
truffleHog file:///user/dxa4481/codeprojects/truffleHog/
truffleHog will go through the entire commit history of each branch, and check each diff from each commit, and check for secrets.
Read the rest of truffleHog – Search Git for High Entropy Strings with Commit History now! Only available at Darknet.
|
Tool | |||
| 2019-12-02 06:26:26 | New Facebook Tool Let Users Transfer Their Photos and Videos to Google (lien direct) | Facebook has finally started implementing the open source data portability framework as the first phase of 'Data Transfer Project,' an initiative the company launched last year in collaboration with Google, Apple, Microsoft, and Twitter.
Facebook today announced a new feature that will allow its users to transfer their Facebook photos and videos to their Google Photos accounts-directly and |
Tool | ★★★ | ||
| 2019-11-29 04:41:02 | Europol Shuts Down \'Imminent Monitor\' RAT Operations With 13 Arrests (lien direct) | In a coordinated International law enforcement operation, Europol today announced to shut down the global organized cybercrime network behind Imminent Monitor RAT, yet another hacking tool that allows cybercriminals to gain complete control over a victim's computer remotely.
The operation targeted both buyers and sellers of the IM-RAT (Imminent Monitor Remote Access Trojan), which was sold to |
Tool | ★★★★ | ||
| 2019-11-28 14:30:00 | How to decide when you should DIY or hire a project out (lien direct) | Leaders are often faced with questions on whether they should develop a capability or tool in-house or use outside partners. Here are guidelines for making the call. | Tool Guideline | |||
| 2019-11-25 20:00:00 | Fidl: Bibliothèque de décompilation Ida de Flare \\ FIDL: FLARE\\'s IDA Decompiler Library (lien direct) |
IDA Pro et les décompiler des rayons hexadécimaux font la base de toute boîte à outils pour la recherche en ingénierie inverse et en vulnérabilité.Dans un article de blog précédent, nous avons expliqué comment l'API des rayons hexadécimaux peut être utilisé pour résoudre de petits problèmes bien définis couramment considérés comme faisant partie de l'analyse des logiciels malveillants.Avoir accès à une représentation de code binaire de niveau supérieur fait du décompilateur des rayons hexagonaux un outil puissant pour l'ingénierie inverse.Cependant, l'interaction avec l'API Hexrays et ses sources de données sous-jacentes peut être intimidante, ce qui rend la création de scripts d'analyse générique difficile ou fastidieux.
Ce billet de blog présente le Fla
IDA Pro and the Hex Rays decompiler are a core part of any toolkit for reverse engineering and vulnerability research. In a previous blog post we discussed how the Hex-Rays API can be used to solve small, well-defined problems commonly seen as part of malware analysis. Having access to a higher-level representation of binary code makes the Hex-Rays decompiler a powerful tool for reverse engineering. However, interacting with the HexRays API and its underlying data sources can be daunting, making the creation of generic analysis scripts difficult or tedious. This blog post introduces the FLA |
Malware Tool Vulnerability | ★★★ | ||
| 2019-11-25 14:52:48 | Samsung adds two modems to help enable wider 5G rollout (lien direct) | Verizon will be the first customer to buy a tool that supports 5G networks that are easier to enable, smaller in size and more efficient in how they use power. | Tool | |||
| 2019-11-25 10:05:09 | Azure Arc: Managing hybrid cloud deployment (lien direct) | Microsoft's new management tool brings Azure management to any hybrid cloud. | Tool | |||
| 2019-11-22 12:33:34 | Expert Comments On Audit Voting Machine Arlo (lien direct) | The CISA and the DHS's main cyber division announced the launch of Arlo, a new tool to help election and government officials audit voting machines to determine they've been tampered with, and it has already been distributed in six states. The ISBuzz Post: This Post Expert Comments On Audit Voting Machine Arlo | Tool | |||
| 2019-11-21 23:58:53 | CISA and VotingWorks release open source post-election auditing tool (lien direct) | New Arlo open-source tool will help state officials verify electronically-tallied ballots. | Tool | |||
| 2019-11-20 06:35:59 | Ransomware Revival: Troldesh becomes a leader by the number of attacks (lien direct) | Ransomware accounted for over half of all malicious mailings in H1 2019, Troldesh aka Shade being the most popular tool among cybercriminals. Group-IB, a Singapore-based cybersecurity company: ransomware accounted for over half of all malicious mailings in H1 2019, detected and analyzed by Group-IB's Computer Emergency Response Team (CERT-GIB), with Troldesh aka Shade being the most popular tool […] | Ransomware Tool | |||
| 2019-11-19 20:20:14 | NBlog Nov 18 - enough is enough (lien direct) |  Keeping ISO27k Information Security Management Systems tight, constrained within narrow scopes, avoiding unnecessary elaboration, seems an admirable objective. The advantages of ISMS simplicity include having less to design, implement, monitor, manage, maintain, review and audit. There's less to go wrong. The ISMS is more focused, a valuable business tool with a specific purpose rather than a costly overhead. All good. However, that doesn't necessarily mean that it is better to have fewer ISMS documents. In practice, simplifying ISMS documentation generally means combining docs or dispensing with any that are deemed irrelevant. That may not be the best approach for every organization, especially if it goes a step too far.Take information security policies for example. Separate, smaller policy docs are easier to generate and maintain, {re}authorize and {re}circulate individually than a thick monolithic “policy manual”. It's easier for authors, authorisers and recipients to focus on the specific issue/s at hand. That's important from the governance, awareness and compliance perspective. At a basic level, what are the chances of people actually bothering to read the change management/version control/document history info then check out all the individual changes (many of which are relatively insignificant) when yet another updated policy manual update drops into their inbox? In practice, it aint gonna happen, much to the chagrin of QA experts!On the other hand, individual policies are necessarily interlinked, forming a governance mesh: substantial changes in one part can have a ripple effect across the rest, which means someone has the unenviable task of updating and maintaining the entire suite, keeping everything reasonably consistent. Having all the policies in one big document makes maintenance easier for the author/maintainer, but harder for change managers, authorisers and the intended audiences/users. Keeping ISO27k Information Security Management Systems tight, constrained within narrow scopes, avoiding unnecessary elaboration, seems an admirable objective. The advantages of ISMS simplicity include having less to design, implement, monitor, manage, maintain, review and audit. There's less to go wrong. The ISMS is more focused, a valuable business tool with a specific purpose rather than a costly overhead. All good. However, that doesn't necessarily mean that it is better to have fewer ISMS documents. In practice, simplifying ISMS documentation generally means combining docs or dispensing with any that are deemed irrelevant. That may not be the best approach for every organization, especially if it goes a step too far.Take information security policies for example. Separate, smaller policy docs are easier to generate and maintain, {re}authorize and {re}circulate individually than a thick monolithic “policy manual”. It's easier for authors, authorisers and recipients to focus on the specific issue/s at hand. That's important from the governance, awareness and compliance perspective. At a basic level, what are the chances of people actually bothering to read the change management/version control/document history info then check out all the individual changes (many of which are relatively insignificant) when yet another updated policy manual update drops into their inbox? In practice, it aint gonna happen, much to the chagrin of QA experts!On the other hand, individual policies are necessarily interlinked, forming a governance mesh: substantial changes in one part can have a ripple effect across the rest, which means someone has the unenviable task of updating and maintaining the entire suite, keeping everything reasonably consistent. Having all the policies in one big document makes maintenance easier for the author/maintainer, but harder for change managers, authorisers and the intended audiences/users. |
Tool | |||
| 2019-11-19 17:00:00 | Slack\'s open source Nebula overlay network tool can solve multi region connectivity woes (lien direct) | The new point-to-point networking overlay was developed as a replacement to IPsec that allows for multi region connectivity in public cloud, though has broader applications for IoT devices. | Tool | ★★★★★ | ||
| 2019-11-18 18:53:17 | Joan is the office booking tool you need (lien direct) | If you need hardware to help manage the booking of your meeting rooms, Joan may be the ideal solution. | Tool | |||
| 2019-11-15 21:27:48 | How to add container management to Cockpit (lien direct) | The Cockpit web-based admin tool can be extended to include container management. | Tool | |||
| 2019-11-13 14:12:06 | Expert Comments On Why Jailbroken Devices May Threaten Mobile Financial Services (lien direct) | Banks and financial institutions have more reason to worry about the threat of jailbroken devices attempting to access their mobile financial services, with the release of the new Checkra1n jailbreak tool this week. The ISBuzz Post: This Post Expert Comments On Why Jailbroken Devices May Threaten Mobile Financial Services | Tool Threat | |||
| 2019-11-12 19:43:19 | How to batch rename files in Windows 10 with the PowerToys PowerRename tool (lien direct) | Learn how to use the PowerToys PowerRename tool to rename multiple files in one shot. | Tool | |||
| 2019-11-12 11:38:43 | General election 2019: \'Cyber-attack\' on Labour Party digital platforms (lien direct) | The party says the "large-scale" DDoS attack failed, but an online campaigning tool was disrupted. | Tool | |||
| 2019-11-12 06:04:11 | YouTube BitCoin Videos Pushing Predator Info-Stealing Trojan (lien direct) | A new scam is underway on YouTube that uses videos to promote a tool that can allegedly generate the private key for a bitcoin address. The attackers then claim this key would then allow you to gain access to the bitcoins stored in the bitcoin address, when in reality the victims will be infected with a password stealing Trojan. [...] | Tool | |||
| 2019-11-11 15:44:16 | CERTrating a new Tool to evaluate CERT/CSIRT maturity level (lien direct) | The Global Cyber Security Center has developed a tool named CERTrating to evaluate the Maturity Level of CERTs and services provided to the Constituency Cyber-attacks that have occurred in recent years have fully confirmed that Cybersecurity is an increasingly complex challenge that represents a priority for all companies both in terms of development and investments. […] | Tool | |||
| 2019-11-08 11:01:36 | Capesand is a new Exploit Kit that appeared in the threat landscape (lien direct) | A recently discovered exploit kit dubbed Capesand is being involved in live attacks despite the fact that it's still under development. In October 2019, researchers at TrendMicro discovered a new exploit kit dubbed Capesand that is being involved in live attacks. The tool was discovered while analyzing a malvertising campaign employing the RIG EK to […] | Tool Threat | |||
| 2019-11-07 21:02:02 | How to install applications from the command line in CentOS 8 (lien direct) | The default package manager for CentOS 8 has migrated from yum to dnf. Find out how this tool is used. | Tool | |||
| 2019-11-07 16:14:32 | 11 items project managers should include in a Problem Identification and Tracking document (lien direct) | A Problem Identification and Tracking document is an essential tool for every project. Learn what to include in the document to help your team manage and reduce project risks. | Tool | |||
| 2019-11-07 03:07:00 | Best Android antivirus? The top 9 tools (lien direct) | The following are the nine best business-class antivirus tools for Android, according to AV-TEST's September 2019 evaluations of 19 Android security apps. (The AV-TEST Institute is a Germany-based independent service provider of IT security and antivirus research.)AV-TEST rates each tool for three areas: protection (six points max), performance (six points max), and usability (six points max). The products listed here all had perfect scores of 18.[ Learn how SandBlast Mobile simplifies mobile security. | Get the latest from CSO by signing up for our newsletters. ] | Tool | |||
| 2019-11-05 21:13:00 | Kamerka OSINT tool shows your country\'s internet-connected critical infrastructure (lien direct) | Kamerka lets you see what a hacker sees. It plots maps with SCADA equipment, webcams, and printers that have been left exposed on the internet inside any given country. | Tool | |||
| 2019-11-05 06:29:03 | Flaws in Able2Extract Professional tool allow hacking targeted machine with malicious image files (lien direct) | Researchers found serious flaws in Investintech's Able2Extract Professional tool that could be exploited to execute arbitrary code using specially crafted image files. The Able2Extract Professional has over 250,000 licensed users across 135 countries, it allows them to view, convert and edit PDF files. Cisco Talos experts discovered two high-severity memory corruption vulnerabilities that can be […] | Tool | |||
| 2019-11-01 15:21:01 | Sooty – SOC Analyst All-In-One CLI Tool (lien direct) |  Sooty is a tool developed with the task of aiding a SOC analyst to automate parts of their workflow and speed up their process.
The main goal of Sooty is to perform as much of the routine checks as possible which allows the analyst more time to spend on deeper analysis.
Features of Sooty SOC Analyst CLI Tool
Sanitise URL's to be safe to send in emails
Perform reverse DNS and DNS lookups
Perform reputation checks from:
VirusTotal
BadIP's
Abuse IPDB
Check if an IP address is a TOR exit node
Decode Proofpoint URL's, UTF-8 encoded URLS, Office SafeLink URL's and Base64 Strings
Get file hashes and compare them against VirusTotal (see requirements)
Perform WhoIs Lookups
Check Usernames and Emails against HaveIBeenPwned to see if a breach has occurred.
Read the rest of Sooty – SOC Analyst All-In-One CLI Tool now! Only available at Darknet. Sooty is a tool developed with the task of aiding a SOC analyst to automate parts of their workflow and speed up their process.
The main goal of Sooty is to perform as much of the routine checks as possible which allows the analyst more time to spend on deeper analysis.
Features of Sooty SOC Analyst CLI Tool
Sanitise URL's to be safe to send in emails
Perform reverse DNS and DNS lookups
Perform reputation checks from:
VirusTotal
BadIP's
Abuse IPDB
Check if an IP address is a TOR exit node
Decode Proofpoint URL's, UTF-8 encoded URLS, Office SafeLink URL's and Base64 Strings
Get file hashes and compare them against VirusTotal (see requirements)
Perform WhoIs Lookups
Check Usernames and Emails against HaveIBeenPwned to see if a breach has occurred.
Read the rest of Sooty – SOC Analyst All-In-One CLI Tool now! Only available at Darknet.
|
Tool | |||
| 2019-10-31 13:51:11 | Chinese Hackers Steal SMS Messages from Linux Routing Servers (lien direct) | Chinese hackers deployed a new cyber-espionage tool on Linux servers belonging to a telecommunications network provider to steal SMS message content for specific recipients. [...] | Tool | |||
| 2019-10-31 08:00:00 | Messagetap: Qui lit vos messages texte? MESSAGETAP: Who\\'s Reading Your Text Messages? (lien direct) |
Fireeye Mandiant a récemment découvert une nouvelle famille de logiciels malveillants utilisé par APT41 (un groupe APT chinois) conçu pour surveiller et enregistrer le trafic SMS à partir de numéros de téléphone spécifiques, de numéros IMSI et de mots clés pour le vol ultérieur.Nommé Messagetap, l'outil a été déployé par APT41 dans un fournisseur de réseaux de télécommunications à l'appui des efforts d'espionnage chinois.Les opérations d'APT41 \\ ont inclus des missions de cyber-espionnage parrainées par l'État ainsi que des intrusions financièrement motivées.Ces opérations se sont déroulées depuis 2012 à nos jours.Pour un aperçu de l'APT41, consultez notre Août 2019 Blog Post ou | Malware Tool | APT 41 | ★★★ | |
| 2019-10-30 16:59:04 | Facebook builds tool to confound facial recognition (lien direct) | However, the social network harbors no plans to deploy the technology in any of its services any time soon | Tool | |||
| 2019-10-30 15:34:12 | Emsisoft released a free decryption tool for Paradise ransomware (lien direct) | Researchers at Emsisoft firm has released a new free tool to decrypt files encrypted by the Paradise ransomware Security experts at Emsisoft have developed a tool to decrypt files encrypted by the Paradise ransomware. This ransomware family encrypts files using Salsa20 and RSA-1024 and it appends several extensions to theis filenames. “The Paradise ransomware encrypts […] | Ransomware Tool | |||
| 2019-10-30 14:14:36 | Python support added to Threat Stack\'s Application Security Monitoring tool (lien direct) | The utility can identify insecure code in production from third-party packages as well as original code. | Tool Threat | |||
| 2019-10-29 15:05:10 | Microsoft Updates Windows 10 PowerToys with Batch Renamer Tool (lien direct) | Microsoft updated the open-source PowerToys toolset for Windows 10 with a new utility named PowerRename that will allow users to batch rename large file collections. [...] | Tool | |||
| 2019-10-28 13:00:00 | Lessons learned conducting an information security risk assessment (lien direct) |
In an age where businesses are relying more than ever on the rapid advancements in technology to drive innovation, strategy, growth and competitive advantage, it is clear the prevalence of technology is not slowing down. But the increase in new devices and systems that utilize connectivity, as well as the transition to the network of devices and systems that were traditionally air-gapped, brings with it an increased cybersecurity risk.
Organizations large and small are attempting to defend against a constant barrage of potentially damaging cybersecurity attacks and struggling to keep up. Increasingly, they are finding that the best approach is taking a proactive, risk-based approach. By repeatedly conducting risk assessments, a holistic understanding of the organization’s risk landscape can be developed, and gaps that exist between people, processes and technology can be utilized to develop a prioritized roadmap for managing and tracking risk over time. The organizations gain the ability to make informed business decisions and move away from a reactive, whack-a-mole approach to cybersecurity.[endif]---->
 Policies and procedures are the foundation
Strong cybersecurity policies and procedures are the foundation of a robust security program. A risk assessor can glean a significant amount of insight into the maturity of an organization’s cybersecurity program simply by looking at a few key areas of cybersecurity policies and procedures, such as those areas identified in the graphic below. They allow the assessor to gain valuable insight on the culture of cybersecurity within the organization, the reporting structure within the organization, the types of technologies present within the organization, and ultimately allows the assessor to drive discovery of information efficiently. This quick and efficient information discovery is especially important for external assessors or those that don’t already have an intimate understanding of the organization.
Policies and procedures are the foundation
Strong cybersecurity policies and procedures are the foundation of a robust security program. A risk assessor can glean a significant amount of insight into the maturity of an organization’s cybersecurity program simply by looking at a few key areas of cybersecurity policies and procedures, such as those areas identified in the graphic below. They allow the assessor to gain valuable insight on the culture of cybersecurity within the organization, the reporting structure within the organization, the types of technologies present within the organization, and ultimately allows the assessor to drive discovery of information efficiently. This quick and efficient information discovery is especially important for external assessors or those that don’t already have an intimate understanding of the organization.
 Documentation is not implementation
Having a strong cybersecurity posture on paper does not mean much if it is not implemented. It’s why conducting interviews of personnel is so important in a risk assessment and why the phrase “Trust but verify” is often half-facetiously repeated by cybersecurity professionals.
When seeking to verify through conducting interviews, it’s tempting to simply go down a list of specific and tailored questions, likely from a framework or compliance standard. Questions like “Does your organization implement a cybersecurity training and awareness training program?”, are to the point, brief, and answer the question asked by the assessment framework, but are not the best way to conduct interviews. Risk assessments are not audits and getting a yes/no answer to a question is not nearly as valuable as taking the time to develop a comprehensive understanding. By having a guided cybersecurity conversation and not simply going through a list of questions, an assessor is able to glean more information on an organization’s risk and develop more valuable findings and recommendations.
Start broad and go narrow
When conducting interviews, start at a ten-thousand-foot level of the topic being discussed, then use the framework as a general guide to steer the conversation and narrow down on specifics. As seen in the below example, the risk assessor should first ask open-ended questions that allow the interviewee a chance to explain the topic in-depth. This allows for a less restrictive and narrow-minded conversation and gives a potential view into how the topic at hand fits into the entire business.
Documentation is not implementation
Having a strong cybersecurity posture on paper does not mean much if it is not implemented. It’s why conducting interviews of personnel is so important in a risk assessment and why the phrase “Trust but verify” is often half-facetiously repeated by cybersecurity professionals.
When seeking to verify through conducting interviews, it’s tempting to simply go down a list of specific and tailored questions, likely from a framework or compliance standard. Questions like “Does your organization implement a cybersecurity training and awareness training program?”, are to the point, brief, and answer the question asked by the assessment framework, but are not the best way to conduct interviews. Risk assessments are not audits and getting a yes/no answer to a question is not nearly as valuable as taking the time to develop a comprehensive understanding. By having a guided cybersecurity conversation and not simply going through a list of questions, an assessor is able to glean more information on an organization’s risk and develop more valuable findings and recommendations.
Start broad and go narrow
When conducting interviews, start at a ten-thousand-foot level of the topic being discussed, then use the framework as a general guide to steer the conversation and narrow down on specifics. As seen in the below example, the risk assessor should first ask open-ended questions that allow the interviewee a chance to explain the topic in-depth. This allows for a less restrictive and narrow-minded conversation and gives a potential view into how the topic at hand fits into the entire business.
|
Tool | |||
| 2019-10-25 13:34:46 | MWC19 Los Angeles: Blockchain\'s role in the 5G movement (lien direct) | Blockchain is a powerful security tool for mobile providers. Here's how to unlock its potential. | Tool | ★★ | ||
| 2019-10-22 22:03:24 | Google Chrome 78 is out: Forced dark mode, DoH trials, no more XSS Auditor (lien direct) | Password Checkup tool makes its debut and the New Tab page gets more customization features. | Tool | |||
| 2019-10-22 09:12:26 | (Déjà vu) Chinese hackers use malware to backdoor Microsoft SQL servers (lien direct) | New malware created by Chinese-backed Winnti Group has been discovered by researchers at ESET while being used to gain persistence on Microsoft SQL Server (MSSQL) systems. The new malicious tool dubbed skip-2.0 can be used by the attackers to backdoor MSSQL Server 11 and 12 servers, enabling them to connect to any account on the server using a so-called “magic password” and […] | Malware Tool | |||
| 2019-10-22 04:50:06 | Stealthy Microsoft SQL Server Backdoor Malware Spotted in the Wild (lien direct) | Cybersecurity researchers claim to have discovered a previously undocumented backdoor specifically designed for Microsoft SQL servers that could allow a remote attacker to control an already compromised system stealthily.
Dubbed Skip-2.0, the backdoor malware is a post-exploitation tool that runs in the memory and lets remote attackers connect to any account on the server running MSSQL version |
Malware Tool | |||
| 2019-10-21 13:00:00 | Reviewing best practices for IT asset management in the cloud (lien direct) |
 It used to be that businesses needing their own large computer networks had to do everything themselves. They had to buy all of their servers, all of their networking appliances. They needed the physical space on premises for all of their datacenters, the HVAC people to keep everything cool, and the massive electricity bills to keep all of that going.
But in the past several years, the growth of cloud services has been exponential. It’s great for the enterprise because depending on a business’s specific needs, they can either have everything but their local area network on the cloud, or they can have some hybrid of their own on premises network and a cloud provider or two, fully integrated. Either way, they can put at least some of their networking needs in the hands of a cloud provider such as AWS, Microsoft Azure, or Google Cloud. That can save a company a lot of time, labor, space, and money. Plus, the agility and flexibility that cloud providers offer is great! Do you need to double the data capacity of your network as soon as possible? It’s much quicker and easier to change your cloud provider plan and do some adjustments on your end than it is to double the size of your on prem network. The cloud can be a lifesaver, but your IT people still need to know how to manage their computing assets there, especially when it comes to cybersecurity. Cloud asset management is a special matter, and it’s absolutely vital to understand.
What is cloud asset management?
Your IT assets are the hardware, software, and networking entities that your company has as tools and resources for their objectives. An excellent example of an IT asset is a database. Databases are very important, particularly in the backend of your applications.
With the implementation of cloud networks, these IT assets become cloud assets too. So instead of having your MySQL databases entirely on your on premises servers and data storage, you can have them run from the server and data storage capacity that your cloud provider offers your business.
But making sure your cloud-hosted assets function well and maintain security is its own area of knowledge: cloud asset management. There are challenges involved in cloud asset management which differ from managing assets on your own infrastructure. For instance, developers and administrators often don’t use the security tools that their cloud providers offer them. Also, visibility into your assets can be more difficult in the cloud. You can’t secure what you can’t see!
Cloud asset management best practices
There’s a lot to learn when it comes to cloud asset management. It can seem overwhelming to start. Thankfully, there are some best practices to keep in mind which will provide you with a strong foundation for properly handling the cloud.
Monitor your cloud as thoroughly as possible
As I mentioned, visibility in cloud networks can be a special challenge. There’s also the everyday performance of your network to consider. You won’t be physically inside of your cloud provider’s datacenter, so you’ll need to be able to see as much as possible with monitoring tools. This isn’t all directly security related. You need to make sure that your provider honors your Service Level Agreement. Watch your bandwidth and make sure that it suits your organization’s needs at all times. Make sure all of your cloud assets have excellent availability, as much uptime as possible. You could have thousands of users depending on your cloud at any given second. Monitor thoroughly and constantly to make sure that your cloud is always capable and reliable.
Redundancy and automation are your friends
Redundancy goes a long way when it comes to keeping good uptime and everything working properly. There should be as few single points of failure as possible, preferably no
It used to be that businesses needing their own large computer networks had to do everything themselves. They had to buy all of their servers, all of their networking appliances. They needed the physical space on premises for all of their datacenters, the HVAC people to keep everything cool, and the massive electricity bills to keep all of that going.
But in the past several years, the growth of cloud services has been exponential. It’s great for the enterprise because depending on a business’s specific needs, they can either have everything but their local area network on the cloud, or they can have some hybrid of their own on premises network and a cloud provider or two, fully integrated. Either way, they can put at least some of their networking needs in the hands of a cloud provider such as AWS, Microsoft Azure, or Google Cloud. That can save a company a lot of time, labor, space, and money. Plus, the agility and flexibility that cloud providers offer is great! Do you need to double the data capacity of your network as soon as possible? It’s much quicker and easier to change your cloud provider plan and do some adjustments on your end than it is to double the size of your on prem network. The cloud can be a lifesaver, but your IT people still need to know how to manage their computing assets there, especially when it comes to cybersecurity. Cloud asset management is a special matter, and it’s absolutely vital to understand.
What is cloud asset management?
Your IT assets are the hardware, software, and networking entities that your company has as tools and resources for their objectives. An excellent example of an IT asset is a database. Databases are very important, particularly in the backend of your applications.
With the implementation of cloud networks, these IT assets become cloud assets too. So instead of having your MySQL databases entirely on your on premises servers and data storage, you can have them run from the server and data storage capacity that your cloud provider offers your business.
But making sure your cloud-hosted assets function well and maintain security is its own area of knowledge: cloud asset management. There are challenges involved in cloud asset management which differ from managing assets on your own infrastructure. For instance, developers and administrators often don’t use the security tools that their cloud providers offer them. Also, visibility into your assets can be more difficult in the cloud. You can’t secure what you can’t see!
Cloud asset management best practices
There’s a lot to learn when it comes to cloud asset management. It can seem overwhelming to start. Thankfully, there are some best practices to keep in mind which will provide you with a strong foundation for properly handling the cloud.
Monitor your cloud as thoroughly as possible
As I mentioned, visibility in cloud networks can be a special challenge. There’s also the everyday performance of your network to consider. You won’t be physically inside of your cloud provider’s datacenter, so you’ll need to be able to see as much as possible with monitoring tools. This isn’t all directly security related. You need to make sure that your provider honors your Service Level Agreement. Watch your bandwidth and make sure that it suits your organization’s needs at all times. Make sure all of your cloud assets have excellent availability, as much uptime as possible. You could have thousands of users depending on your cloud at any given second. Monitor thoroughly and constantly to make sure that your cloud is always capable and reliable.
Redundancy and automation are your friends
Redundancy goes a long way when it comes to keeping good uptime and everything working properly. There should be as few single points of failure as possible, preferably no |
Tool Guideline | ★★★★★ | ||
| 2019-10-20 12:00:00 | Computers Are Learning to Read-But They\'re *Still* Not So Smart (lien direct) | A tool called BERT can now outperform us on advanced reading-comprehension tests. It's also revealed how far AI has to go. | Tool | |||
| 2019-10-19 07:36:45 | Emsisoft released a free decryption tool for the STOP (Djvu) ransomware (lien direct) | Emsisoft firm has released a new free decryption tool the STOP (Djvu) ransomware, in the last months the research team helped victims of many other threats. STOP (Djvu) ransomware has 160 variants that infected more hundreds of thousands of victims worldwide. Experts estimated a total number of 460,000 victims, that makes this threat the most […] | Ransomware Tool Threat |
To see everything:
Our RSS (filtrered)
