What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2019-03-08 15:25:00 | Marriott CEO shares post-mortem on last year\'s hack (lien direct) | Marriott investigators found Mimikatz and a remote access trojan (RAT) on hacked Starwood IT system. | Hack | |||
| 2019-03-07 03:00:00 | How to hack a smartcard to gain privileged access (lien direct) | I can change an email address and steal your most privileged credentials. | Hack | |||
| 2019-03-06 15:11:02 | StealthWorker Malware Uses Windows, Linux Bots to Hack Websites (lien direct) | Hackers are running a new campaign which drops the StealthWorker brute-force malware on Windows and Linux machines that end up being used to brute force other computers in a series of distributed brute force attacks. [...] | Malware Hack | |||
| 2019-03-04 21:00:03 | Hackers Listen In on What Synthetic DNA Machines Are Printing (lien direct) | Some of those sequences are worth millions of dollars, but fortunately the hack isn't easy to deploy-yet. | Hack | |||
| 2019-03-04 13:30:01 | Container Escape Hack Targets Vulnerable Linux Kernel (lien direct) | A proof-of-concept hack allows adversaries to tweak old exploits, have code jump containers and attack underlying infrastructure. | Hack | |||
| 2019-03-04 10:51:00 | As Trump and Kim Met, North Korean Hackers Hit Over 100 Targets in U.S. and Ally Nations. (lien direct) | North Korean hackers who have targeted American and European businesses for 18 months kept up their attacks last week even as President Trump was meeting with North Korea's leader in Hanoi. The attacks, which include efforts to hack into banks, utilities and oil and gas companies, began in 2017, according to researchers at the cybersecurity […] | Hack Guideline | |||
| 2019-03-03 17:16:03 | (Déjà vu) Hack the Box Access: Walkthrough (lien direct) | Today we are going to solve another CTF challenge “Access”. It is a retired vulnerable lab presented by Hack the Box for helping pentester's to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level. Level: Easy Task: To find user.txt and... Continue reading → | Hack | |||
| 2019-02-28 23:45:01 | US wiped some hard drives of Russia\'s \'troll factory\' in last year\'s hack (lien direct) | IRA news site reveals what happened last year on the day before the US midterms. | Hack | |||
| 2019-02-28 16:24:02 | UN Aviation Agency Concealed Serious Hack: Media (lien direct) | The Montreal-based United Nations aviation agency concealed for months a hack of its computers and allowed malware to spread throughout the airline industry, Canada's public broadcaster reported Wednesday. | Malware Hack | |||
| 2019-02-28 11:46:01 | (Déjà vu) Topps.com Sports Collectible Site Exposes Payment Info in MageCart Attack. (lien direct) | Last week, the sports trading card and collectible company Topps issued a data breach notification stating that it was affected by an attack, which possibly exposed the payment and address information of its customers. This type of attack is called a MageCart attack, which is when attackers hack a site to inject a malicious script into a site’s […] | Data Breach Hack | |||
| 2019-02-27 14:57:00 | Thunderclap vulnerabilities allows to hack most of moder computers (lien direct) | Researchers found a new set of flaws that can be exploited via Thunderbolt to compromise a broad range of modern computers with Thunderclap attacksResearchers found a new set of flaws that can be exploited via Thunderbolt to compromise a broad range of modern computers with Thunderclap attacks Security experts from Rice University in the United […] | Hack | |||
| 2019-02-27 10:23:00 | What is ethical hacking? How to get paid to break into computers (lien direct) | What is ethical hacking? Ethical hacking, also known as penetration testing or pen testing, is legally breaking into computers and devices to test an organization's defenses. It's among the most exciting IT jobs any person can be involved in. You are literally getting paid to keep up with the latest technology and get to break into computers without the threat of being arrested. Companies engage ethical hackers to identify vulnerabilities in their systems. From the penetration tester's point of view, there is no downside: If you hack in past the current defenses, you've given the client a chance to close the hole before an attacker discovers it. If you don't find anything, your client is even happier because they now get to declare their systems “secure enough that even paid hackers couldn't break into it.” Win-win! | Hack Threat | |||
| 2019-02-27 07:39:00 | Protecting the IoT: 3 things you must include in an IoT security plan (lien direct) | With many IT projects, security is often an afterthought, but that approach puts the business at significant risk. The rise of IoT adds orders of magnitude more devices to a network, which creates many more entry points for threat actors to breach. A bigger problem is that many IoT devices are easier to hack than traditional IT devices, making them the endpoint of choice for the bad guys.IoT is widely deployed in a few industries, but it is in the early innings still for most businesses. For those just starting out, IT and security leaders should be laying out their security plans for their implementations now. However, the landscape of security is wide and confusing so how to secure an IoT deployment may not be obvious. Below are three things you must consider when creating an IoT security plan. | Hack Threat Guideline | |||
| 2019-02-26 16:00:00 | New Golang brute forcer discovered amid rise in e-commerce attacks (lien direct) |
 E-commerce sites are a hot commodity these days. We dig into how compromised PCs are helping to hack into them to inject skimmers, whether via vulnerabilities in the websites themselves or through a new malware we discovered gaining entry via brute force.
Categories:
Threat analysis
Tags: BotbotnetbruteforceGolanggoogletagmanagerMagecartmagentoskimmer
(Read more...)
E-commerce sites are a hot commodity these days. We dig into how compromised PCs are helping to hack into them to inject skimmers, whether via vulnerabilities in the websites themselves or through a new malware we discovered gaining entry via brute force.
Categories:
Threat analysis
Tags: BotbotnetbruteforceGolanggoogletagmanagerMagecartmagentoskimmer
(Read more...)
|
Malware Hack | |||
| 2019-02-26 15:27:00 | The Arsenal Behind the Australian Parliament Hack (lien direct) | Cybaze-Yoroi ZLab investigated artefacts behind Australian Parliament attack to have an insight of Tools and Capabilities associated with the attackers. Introduction In the past days, a cyber attack targeted a high profile target on the APAC area: the Australian Parliament House. As reported by the Australian prime minister there was no evidence of any information theft […] | Hack | |||
| 2019-02-26 08:57:02 | (Déjà vu) Hack the Box Zipper: Walkthrough (lien direct) | Today we are going to solve another CTF challenge “Zipper”. It is a retired vulnerable lab presented by Hack the Box for helping pentester's to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level. Level: Hard Task: To find user.txt and... Continue reading → | Hack | |||
| 2019-02-26 05:45:04 | Latest WinRAR Flaw Being Exploited in the Wild to Hack Windows Computers (lien direct) | It's not just the critical Drupal vulnerability that is being exploited by in the wild cybercriminals to attack vulnerable websites that have not yet applied patches already available by its developers, but hackers are also exploiting a critical WinRAR vulnerability that was also revealed last week.
A few days ago, The Hacker News reported about a 19-year-old remote code execution vulnerability |
Hack Vulnerability | |||
| 2019-02-25 14:30:01 | PoS Provider Hack That Affected Customers At 130 Locations (lien direct) | Point-of-Sale Solutions Provider – North County Business Products was hacked and credit-card stealing malware was put on the networks of clients across the country like Dunn Brothers Coffee, Zipps Sports Grill and Someburros outlets. POS Firm Hacked, Malware Deployed at 130+ Outlets: Clients of North County Business Products hit by data breach https://t.co/nNCAXYZbof pic.twitter.com/y5FZkGZh8C — Shah Sheikh (@shah_sheikh) February 22, … The ISBuzz Post: This Post PoS Provider Hack That Affected Customers At 130 Locations | Data Breach Malware Hack | |||
| 2019-02-25 14:00:00 | Why Cybersecurity Experts Are Being Recruited Left and Right (lien direct) |
 Once upon a time, businesses needed to take light cybersecurity precautions to ward off amateur hackers. A business owner may have recruited their tech-savvy nephew to protect their system, barely worrying about the risk. Today, the world of cybersecurity has done a 180 — it’s now a top concern for businesses. As businesses swiftly adapt to the changing digital environment, new technology means more cybersecurity concerns.
Businesses are now using new tech for an assortment of needs, from the recruitment process to audience discovery and beyond. On top of that, as consumers continue to shop online and use the internet to store all sorts of personal information, hackers have only grown in their knowledge and resourcefulness to create clever, threatening ways to attack businesses. And for good reason: Uncovering financial and health information is worth a lot of money for hackers.
The Demand for Cybersecurity Specialists
Cybersecurity professionals are in incredibly high demand right now. Experts predict that by the year 2021, as many as 3.5 million cybersecurity positions will be unfilled. That means a lot of businesses will be exposed to potentially ruinous risk.
The internet of things (IoT) has created more opportunities for employees and consumers to stay connected through an assortment of tools, from smartphones to smart home appliances. Every time another device connects to the internet, another security risk opens up. When valuable personal information is transmitted, those devices and connections become gold mines for hackers.
Additionally, any business that has some type of online presence, whether it’s a customer-facing retail store or employees who use an internal, internet-connected system, needs cybersecurity services. Certain industries have even more of a pressing need than others:
Finance
Government agencies
Media
Retail
Tech companies
These industries deal in high levels of personal information that, if a hacker accessed it, would be detrimental to the business as well as its customers.
How Do Cybersecurity Experts Protect Businesses?
In 2014, Sony Pictures was the target of a major cybersecurity attack. According to Michael Lynton, chief executive, “There's no playbook for this, so you are, in essence, trying to look at the situation as it unfolds and make decisions without being able to refer to a lot of experiences you've had in the past or other people's experiences. You're on completely new ground.”
This is a common sentiment, but it may be unfounded. Even five years ago, cybersecurity pros noted that Sony should have, and could have, been better prepared.
When you decide to go into the field of cybersecurity, you may opt to head back to sc
Once upon a time, businesses needed to take light cybersecurity precautions to ward off amateur hackers. A business owner may have recruited their tech-savvy nephew to protect their system, barely worrying about the risk. Today, the world of cybersecurity has done a 180 — it’s now a top concern for businesses. As businesses swiftly adapt to the changing digital environment, new technology means more cybersecurity concerns.
Businesses are now using new tech for an assortment of needs, from the recruitment process to audience discovery and beyond. On top of that, as consumers continue to shop online and use the internet to store all sorts of personal information, hackers have only grown in their knowledge and resourcefulness to create clever, threatening ways to attack businesses. And for good reason: Uncovering financial and health information is worth a lot of money for hackers.
The Demand for Cybersecurity Specialists
Cybersecurity professionals are in incredibly high demand right now. Experts predict that by the year 2021, as many as 3.5 million cybersecurity positions will be unfilled. That means a lot of businesses will be exposed to potentially ruinous risk.
The internet of things (IoT) has created more opportunities for employees and consumers to stay connected through an assortment of tools, from smartphones to smart home appliances. Every time another device connects to the internet, another security risk opens up. When valuable personal information is transmitted, those devices and connections become gold mines for hackers.
Additionally, any business that has some type of online presence, whether it’s a customer-facing retail store or employees who use an internal, internet-connected system, needs cybersecurity services. Certain industries have even more of a pressing need than others:
Finance
Government agencies
Media
Retail
Tech companies
These industries deal in high levels of personal information that, if a hacker accessed it, would be detrimental to the business as well as its customers.
How Do Cybersecurity Experts Protect Businesses?
In 2014, Sony Pictures was the target of a major cybersecurity attack. According to Michael Lynton, chief executive, “There's no playbook for this, so you are, in essence, trying to look at the situation as it unfolds and make decisions without being able to refer to a lot of experiences you've had in the past or other people's experiences. You're on completely new ground.”
This is a common sentiment, but it may be unfounded. Even five years ago, cybersecurity pros noted that Sony should have, and could have, been better prepared.
When you decide to go into the field of cybersecurity, you may opt to head back to sc |
Spam Malware Hack Threat | ★★★★★ | ||
| 2019-02-24 16:36:04 | (Déjà vu) Hack the Box: Giddy Walkthrough (lien direct) | Today we are going to solve another CTF challenge “Giddy”. It is a retired vulnerable lab presented by Hack the Box for helping pentester's to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level. Level: Expert Task: To find user.txt and... Continue reading → | Hack | |||
| 2019-02-21 19:30:05 | How to hack the Windows 10 Taskbar to display your last active app window (lien direct) | Learn how to edit the Windows Registry to change the default behavior of the Microsoft Windows 10 Taskbar. | Hack | |||
| 2019-02-21 02:18:01 | Another Critical Flaw in Drupal Discovered - Update Your Site ASAP! (lien direct) | Developers of Drupal-a popular open-source content management system software that powers millions of websites-have released the latest version of their software to patch a critical vulnerability that could allow remote attackers to hack your site.
The update came two days after the Drupal security team released an advance security notification of the upcoming patches, giving websites |
Hack Vulnerability | |||
| 2019-02-20 21:42:01 | Canada Helping Australia Determine \'Full Extent\' of Hack (lien direct) | Canada's electronic eavesdropping agency said Wednesday it is working with Canberra to try to determine the scale of computer hacking on Australia's parliament and political parties just months from an election. | Hack | ★★★★★ | ||
| 2019-02-20 11:19:04 | (Déjà vu) Hack the Box: Dab Walkthrough (lien direct) | Today we are going to solve another CTF challenge “Dab”. It is a retired vulnerable lab presented by Hack the Box for helping pentester's to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level. Level: Expert Task: To find user.txt and... Continue reading → | Hack | |||
| 2019-02-19 18:30:05 | AdventHealth Breach Of 42,000 Patients (lien direct) | It was reported late last week that about 42,000 AdventHealth Medical Group patients are being notified that their personal and health data was breached for more than a year due to a hack of the Florida provider's systems. The breached data contained troves of personal and health data, including medical histories, insurance carriers, Social Security numbers, along with demographic … The ISBuzz Post: This Post AdventHealth Breach Of 42,000 Patients | Hack | |||
| 2019-02-19 13:23:05 | Podcast Episode 134: The Deep Fake Threat to Authentication and analyzing the PEAR Compromise (lien direct) | Vijay Balasubramaniyan of Pindrop joins us to talk about it. And, in our second segment, Sam Bisbee the CSO of the firm ThreatStack joins us to talk about last month's hack of the PEAR open source package manager and why data deserialization attacks are a growing threat to projects that use open source components.
The post Podcast Episode 134:...Read the whole entry... _!fbztxtlnk!_ https://feeds.feedblitz.com/~/598068876/0/thesecurityledger -->» |
Hack Threat | |||
| 2019-02-19 01:55:04 | LPG Gas Company Leaked Details, Aadhaar Numbers of 6.7 Million Indian Customers (lien direct) | Why would someone bother to hack a so-called "ultra-secure encrypted database that is being protected behind 13 feet high and 5 feet thick walls," when one can simply fetch a copy of the same data from other sources.
French security researcher Baptiste Robert, who goes by the pseudonym "Elliot Alderson" on Twitter, with the help of an Indian researcher, who wants to remain anonymous, |
Hack | |||
| 2019-02-18 02:15:01 | Australian political parties hit by \'state actor\' hack, PM says (lien direct) | The "sophisticated" activity follows an attempted hack on the parliament, Scott Morrison says. | Hack | |||
| 2019-02-18 01:37:01 | How to Hack Facebook Accounts? Just Ask Your Targets to Open a Link (lien direct) | It's 2019, and just clicking on a specially crafted URL would have allowed an attacker to hack your Facebook account without any further interaction.
A security researcher discovered a critical cross-site request forgery (CSRF) vulnerability in the most popular social media platform that could have been allowed attackers to hijack Facebook accounts by simply tricking the targeted users into |
Hack Vulnerability | |||
| 2019-02-16 09:20:02 | (Déjà vu) Hack the Box: Ypuffy Walkthrough (lien direct) | Today we are going to solve another CTF challenge “Ypuffy”. It is a retired vulnerable lab presented by Hack the Box for helping pentester's to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level. Level: Intermediate Task: To find user.txt and... Continue reading → | Hack | |||
| 2019-02-15 11:15:04 | Coffee Meets Bagel dating app confirms data breach (lien direct) | The week closes with the news of another embarrassing data breach, the Coffee Meets Bagel confirmed a hack on Valentine’s Day. The dating app Coffee Meets Bagel confirmed that hackers breached its systems on Valentine’s Day and may have obtained access to users’ account data. The company notified the incident to account holders, the intrusion […] | Data Breach Hack | |||
| 2019-02-14 15:45:00 | Coffee Meets Bagel Confirms Hack on Valentine\'s Day (lien direct) | The dating app says users' account data may have been obtained by an unauthorized party. | Hack | |||
| 2019-02-13 19:29:00 | US Air Force Defector Allegedly Helped Iran Hack Americans (lien direct) | In an astonishing indictment, the DoJ details how Monica Witt allegedly turned on her former counterintelligence colleagues. | Hack | |||
| 2019-02-13 17:58:01 | Game of Thrones hacker worked with US defector to hack Air Force employees for Iran (lien direct) | Former US Air Force intelligence agent passed crucial information to Iranian state hackers after she defected to Iran in 2013. | Hack | |||
| 2019-02-13 16:24:01 | 5 ways project management can help you hack digital transformation (lien direct) | Only 25% of digital transformation projects yield real benefits, according to the Project Management Institute. Here's how your organization can improve. | Hack | |||
| 2019-02-12 13:33:03 | Email Provider VFEmail Suffers \'Catastrophic\' Hack (lien direct) | Email provider VFEmail has suffered what the company is calling "catastrophic destruction" at the hands of an as-yet unknown intruder who trashed all of the company's primary and backup data in the United States. The firm's founder says he now fears some 18 years' worth of customer email may be gone forever. | Hack | |||
| 2019-02-11 16:53:04 | Australian Parliament Cyber-Hack Attempt (lien direct) | Australian authorities are investigating an attempt to hack into the national parliament's computer network, two senior lawmakers said on Friday, but there was no evidence yet that any data had been accessed or stolen. China link possible in cyber attack on Australian Parliament – https://t.co/yqGgeY15bF via @Shareaholic — Petrov Dempski (@petrovdempski) February 10, 2019 Experts … The ISBuzz Post: This Post Australian Parliament Cyber-Hack Attempt | Hack | |||
| 2019-02-11 15:15:00 | OkCupid Denies Data Breach Amid Account Hack Complaints (lien direct) | Users on the dating website report hackers breaking into their accounts, changing email addresses, and resetting passwords. | Data Breach Hack | |||
| 2019-02-09 00:49:00 | China\'s cybersecurity law update lets state agencies \'pen-test\' local companies (lien direct) | China draws up law that makes it perfectly legal to hack any internet-related company activating in its borders. | Hack | |||
| 2019-02-08 10:08:18 | How Bezo\'s dick pics might\'ve been exposed (lien direct) | In the news, the National Enquirer has extorted Amazon CEO Jeff Bezos by threatening to publish the sext-messages/dick-pics he sent to his mistress. How did the National Enquirer get them? There are rumors that maybe Trump's government agents or the "deep state" were involved in this sordid mess. The more likely explanation is that it was a simple hack. Teenage hackers regularly do such hacks -- they aren't hard.This post is a description of how such hacks might've been done.To start with, from which end were they stolen? As a billionaire, I'm guessing Bezos himself has pretty good security, so I'm going to assume it was the recipient, his girlfriend, who was hacked.The hack starts by finding the email address she uses. People use the same email address for both public and private purposes. There are lots of "people finder" services on the Internet that you can use to track this information down. These services are partly scams, using "dark patterns" to get you to spend tons of money on them without realizing it, so be careful.Using one of these sites, I quickly found a couple of a email accounts she's used, one at HotMail, another at GMail. I've blocked out her address. I want to describe how easy the process is, I'm not trying to doxx her. Next, I enter those email addresses into the website http://haveibeenpwned.com to see if hackers have ever stolen her account password. When hackers break into websites, they steal the account passwords, and then exchange them on the dark web with other hackers. The above website tracks this, helping you discover if one of your accounts has been so compromised. You should take this opportunity to enter your email address in this site to see if it's been so "pwned".I find that her email addresses have been included in that recent dump of 770 million accounts called "Collection#1". Next, I enter those email addresses into the website http://haveibeenpwned.com to see if hackers have ever stolen her account password. When hackers break into websites, they steal the account passwords, and then exchange them on the dark web with other hackers. The above website tracks this, helping you discover if one of your accounts has been so compromised. You should take this opportunity to enter your email address in this site to see if it's been so "pwned".I find that her email addresses have been included in that recent dump of 770 million accounts called "Collection#1".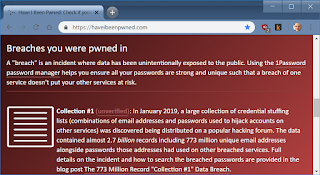 The http://haveibeenpwned.com won't disclose the passwords, only the fact they've been pwned. However, I have a copy of that huge Collection#1 dump, so I can search it myself to get her password. As this output shows, I get a few hits, all with the same password. The http://haveibeenpwned.com won't disclose the passwords, only the fact they've been pwned. However, I have a copy of that huge Collection#1 dump, so I can search it myself to get her password. As this output shows, I get a few hits, all with the same password.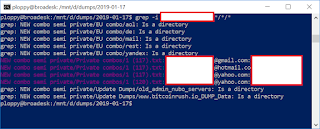 At this point, I have a password, but not necessarily the password to access any useful accounts. For all I know, this was the At this point, I have a password, but not necessarily the password to access any useful accounts. For all I know, this was the |
Hack | |||
| 2019-02-08 00:02:00 | Get a Lifetime Subscription to Unlimited VPN for just $59.99 (5 Devices) (lien direct) | For all of the undeniable conveniences the Internet has brought us, it's becoming an increasingly dangerous place to be.
Both individual hackers and entire government agencies are now able to hack into your computer or smartphone from across the globe and steal everything from your browsing history to your credit card numbers, and they're often able to do so without your knowledge.
A Virtual
|
Hack | |||
| 2019-02-07 11:26:03 | Hackers can hack an Android smartphone just by looking at a PNG image (lien direct) | Vulnerability in PNG file can allow hackers to hack Android smartphones Beware, while opening a harmless-looking image downloaded from the internet, emails, social media apps, or messaging apps, as it could compromise your smartphone. Google has discovered three new critical vulnerabilities that allow hackers to hack an Android smartphone just by looking at a PNG […] | Hack | |||
| 2019-02-07 06:28:05 | Android devices could be hacked by viewing a malicious PNG Image (lien direct) | Google patched a critical flaw in its Android OS that allows an attacker to send a specially crafted PNG image file to hack a target device, Opening an image file on your smartphone could allow attackers to hack into your Android device due to three critical vulnerabilities, CVE-2019-1986, CVE-2019-1987, and CVE-2019-1988. The flaws affect millions […] | Hack | |||
| 2019-02-07 03:00:00 | Power LogOn offers 2FA and networked password management for the enterprise (lien direct) | Like most humans, I'm more vocal about the things I don't like and less likely to crow about the things I do like. Since I wrote my popular 11 ways to hack 2FA article, I've been besieged by vendors eager to show me how their authentication solution defeats all the hacking issues I wrote about. | Hack | |||
| 2019-02-06 06:14:03 | Android Phones Can Get Hacked Just by Looking at a PNG Image (lien direct) | Using an Android device?
Beware! You have to remain more caution while opening an image file on your smartphone-downloaded anywhere from the Internet or received through messaging or email apps.
Yes, just viewing an innocuous-looking image could hack your Android smartphone-thanks to three newly-discovered critical vulnerabilities that affect millions of devices running recent versions of
|
Hack | |||
| 2019-02-05 12:05:04 | Flaws in Popular RDP Clients Allow Malicious Servers to Reverse Hack PCs (lien direct) | You've always been warned not to share remote access to your computer with any untrusted people for many reasons-it's basic cyber security advice, and common sense, right?
But what if I say, you should not even trust anyone who invites or offers you full remote access to their computers?
Security researchers at cybersecurity firm Check Point have discovered more than two dozen
|
Hack | |||
| 2019-02-01 21:20:05 | Banks\' Online Security Is Not Tough Enough To Stop Hackers (lien direct) | Less than half of Britain's leading banks are doing enough to protect customers from hackers, according to a Which? investigation. Only five of the 12 investigated banks used two-factor authentication at login, a feature which makes it harder for criminals to hack into accounts. Dewald Nolte, Chief Commerical Officer at Entersekt: “The rise in popularity … The ISBuzz Post: This Post Banks' Online Security Is Not Tough Enough To Stop Hackers | Hack Guideline | |||
| 2019-02-01 14:00:00 | Things I Hearted This Week, 1st Feb 2019 (lien direct) |
Hello February! I was doing some research last night and was surprised to discover that the Target breach is over five years old! Five years! I was sure it only happened a couple of years ago - but such is the fast-paced nature of the industry, and also I guess a testament to how certain major breaches become part of infosec folklore. Like TJX, or Heartland - and no, I’m not going to look up when any of those occurred because I’ll probably end up feeling a lot older than I already do.
Enough reminiscing - let’s get down to it.
The Big Five
There’s been a lot of things I didn’t heart this week, although for one reason or another they ended up in my list of things to talk about. So, if you’re wondering about the stories regarding Facebook and Apple, and also Google, then yes, I did see them, and no, I don’t fancy talking about them.
But speaking of large companies, Kashmir Hill has undertaken what is perhaps becoming my favourite piece of tech journalism ever. WIth detailed write ups and slick videos showcasing how she cut out the big five of Amazon, Facebook, Google, Microsoft, and Apple from her life, one week at a time.
Life without the tech giants | Gizmondo
Week 1, Amazon | Gizmondo
Week 2, Facebook | Gizmondo
Week 3, Google | Gizmondo
Considerations for When Your Apartment Goes “Smart”
Everything is getting ‘smart’ these days. By smart, I mean connected and vulnerable. So, what should you do if you live in an apartment where everyone is getting fancy new smart locks (or terribly insecure cheap locks depending on how you look at it).
Lesley Carhart recently found herself in the same position, and has written a really good post on security considerations if you ever find yourself in a similar position.
Security Things to Consider When Your Apartment Goes ‘Smart’ | tisiphone
Abusing Exchange: One API Call Away From Domain Admin
An attacker with just the credentials of a single lowly Exchange mailbox user can gain Domain Admin privileges by using a simple tool. Very good writeup here.
Abusing Exchange: One API call away from Domain Admin | dirkjanm.io
_(1)_(1)_500_369.jpg) Sending Love Letters
The "Love Letter" malspam campaign has now changed its focus to Japanese targets and almost doubled the volume of malicious attachments it delivers.
Love Letter Malspam Serves Cocktail of Malware, Heavily Targets Japan | Bleeping Computer
While we’re talking about Japan, a new law in Japan allows the nation's National Institute of Information and Communications Technology (NICT) to hack into citizens' personal IoT equipment as part of a survey of vuln
Sending Love Letters
The "Love Letter" malspam campaign has now changed its focus to Japanese targets and almost doubled the volume of malicious attachments it delivers.
Love Letter Malspam Serves Cocktail of Malware, Heavily Targets Japan | Bleeping Computer
While we’re talking about Japan, a new law in Japan allows the nation's National Institute of Information and Communications Technology (NICT) to hack into citizens' personal IoT equipment as part of a survey of vuln |
Data Breach Hack | Yahoo | ||
| 2019-02-01 13:45:00 | Nest Hack Leaves Homeowner Sleepless in Chicago (lien direct) | A Chicago-area family's smart home controls were compromised in a hack that has left them feeling vulnerable in their own home. | Hack | |||
| 2019-01-31 21:51:04 | Credit Card Info Sold On The Dark Web From City Of St. John\'s Parking System Hack (lien direct) | Credit card information from about 6,000 people was sold on the dark web after The City of St. John discovered that it's parking system had been hacked with a malware that collected credit card information for the previous 18 months from those paying parking tickets. Ryan Wilk, VP of Customer Success at NuData Security: “Once … The ISBuzz Post: This Post Credit Card Info Sold On The Dark Web From City Of St. John's Parking System Hack | Malware Hack |
To see everything:
Our RSS (filtrered)
