What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2022-08-31 10:00:00 | Examiner les journaux unifiés macOS Reviewing macOS Unified Logs (lien direct) |
En commençant par MacOS 10.12 (Sierra), Apple a introduit un changement de clé dans la façon dont la journalisation a été effectuée sur leurs systèmes.Ce nouveau système de journalisation a remplacé les journaux UNIX communs par des journaux unifiés macOS.Ces journaux peuvent fournir aux enquêteurs de la crisence un artefact précieux pour aider à étudier les systèmes MacOS ou d'autres appareils Apple.
Dans cet article de blog, nous couvrirons un aperçu des journaux unifiés et des défis présentés pour les utiliser lors d'une enquête.Avec ce billet de blog, nous avons également publié un outil intitulé « macOS-UnifiedLogs " pour aider à surmonter certains des défis dans l'analyse des données de journal, et à
Beginning with macOS 10.12 (Sierra), Apple introduced a key change to how logging was done on their systems. This new logging system replaced common Unix logs with macOS Unified Logs. These logs can provide forensic investigators a valuable artifact to aid in investigating macOS systems or other Apple devices. In this blog post, we will cover an overview of the Unified Logs and the challenges presented in using them during an investigation. Along with this blog post, we also released a tool called “macos-unifiedlogs" to help overcome some of the challenges in parsing log data, and to |
Tool | ★★★ | ||
| 2022-08-30 22:21:30 | New ODGen Tool Unearths 180 Zero-Days in Node.js Libraries (lien direct) | New graph-based tool offers a better alternative to current approaches for finding vulnerabilities in JavaScript code, they note. | Tool | |||
| 2022-08-30 15:01:00 | Anomali Cyber Watch: First Real-Life Video-Spoofing Attack, MagicWeb Backdoors via Non-Standard Key Identifier, LockBit Ransomware Blames Victim for DDoSing Back, and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: Authentication, DDoS, Fingerprinting, Iran, North Korea, Ransomware, and Russia. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
LastPass Hackers Stole Source Code
(published: August 26, 2022)
In August 2022, an unidentified threat actor gained access to portions of the password management giant LastPass development environment. LastPass informed that it happened through a single compromised developer account and the attacker took portions of source code and some proprietary LastPass technical information. The company claims that this incident did not affect customer data or encrypted password vaults.
Analyst Comment: This incident doesn’t seem to have an immediate impact on LastPass users. Still, organizations relying on LastPass should raise the concern in their risk assessment since “white-box hacking” (when source code of the attacking system is known) is easier for threat actors. Organizations providing public-facing software should take maximum measures to block threat actors from their development environment and establish robust and transparent security protocols and practices with all third parties involved in their code development.
Tags: LastPass, Password manager, Data breach, Source code
Mercury Leveraging Log4j 2 Vulnerabilities in Unpatched Systems to Target Israeli
(published: August 25, 2022)
Starting in July 2022, a new campaign by Iran-sponsored group Static Kitten (Mercury, MuddyWater) was detected targeting Israeli organizations. Microsoft researchers detected that this campaign was leveraging exploitation of Log4j 2 vulnerabilities (CVE-2021-45046 and CVE-2021-44228) in SysAid applications (IT management tools). For persistence Static Kitten was dropping webshells, creating local administrator accounts, stealing credentials, and adding their tools in the startup folders and autostart extensibility point (ASEP) registry keys. Overall the group was heavily using various open-source and built-in operating system tools: eHorus remote management software, Ligolo reverse tunneling tool, Mimikatz credential theft tool, PowerShell programs, RemCom remote service, Venom proxy tool, and Windows Management Instrumentation (WMI).
Analyst Comment: Network defenders should monitor for alerts related to web shell threats, suspicious RDP sessions, ASEP registry anomaly, and suspicious account creation. Similarly, SysAid users can monitor for webshells and abnormal processes related to SysAisServer instance. Even though Static Kitten was observed leveraging the Log4Shell vulnerabilities in the past (targeting VMware apps), most of their attacks still start with spearphishing, often from a compromised email account.
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] OS Credential Dumping - T1003 | [MITRE ATT&CK] Phishing - T1566 |
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
LastPass Hackers Stole Source Code
(published: August 26, 2022)
In August 2022, an unidentified threat actor gained access to portions of the password management giant LastPass development environment. LastPass informed that it happened through a single compromised developer account and the attacker took portions of source code and some proprietary LastPass technical information. The company claims that this incident did not affect customer data or encrypted password vaults.
Analyst Comment: This incident doesn’t seem to have an immediate impact on LastPass users. Still, organizations relying on LastPass should raise the concern in their risk assessment since “white-box hacking” (when source code of the attacking system is known) is easier for threat actors. Organizations providing public-facing software should take maximum measures to block threat actors from their development environment and establish robust and transparent security protocols and practices with all third parties involved in their code development.
Tags: LastPass, Password manager, Data breach, Source code
Mercury Leveraging Log4j 2 Vulnerabilities in Unpatched Systems to Target Israeli
(published: August 25, 2022)
Starting in July 2022, a new campaign by Iran-sponsored group Static Kitten (Mercury, MuddyWater) was detected targeting Israeli organizations. Microsoft researchers detected that this campaign was leveraging exploitation of Log4j 2 vulnerabilities (CVE-2021-45046 and CVE-2021-44228) in SysAid applications (IT management tools). For persistence Static Kitten was dropping webshells, creating local administrator accounts, stealing credentials, and adding their tools in the startup folders and autostart extensibility point (ASEP) registry keys. Overall the group was heavily using various open-source and built-in operating system tools: eHorus remote management software, Ligolo reverse tunneling tool, Mimikatz credential theft tool, PowerShell programs, RemCom remote service, Venom proxy tool, and Windows Management Instrumentation (WMI).
Analyst Comment: Network defenders should monitor for alerts related to web shell threats, suspicious RDP sessions, ASEP registry anomaly, and suspicious account creation. Similarly, SysAid users can monitor for webshells and abnormal processes related to SysAisServer instance. Even though Static Kitten was observed leveraging the Log4Shell vulnerabilities in the past (targeting VMware apps), most of their attacks still start with spearphishing, often from a compromised email account.
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] OS Credential Dumping - T1003 | [MITRE ATT&CK] Phishing - T1566 | |
Ransomware Hack Tool Vulnerability Threat Guideline Cloud | APT 37 APT 29 LastPass | ||
| 2022-08-30 08:00:09 | ModernLoader delivers multiple stealers, cryptominers and RATs (lien direct) |  By Vanja SvajcerCisco Talos recently observed three separate, but related, campaigns between March and June 2022 delivering a variety of threats, including the ModernLoader bot, RedLine information-stealer and cryptocurrency-mining malware to victims. The actors use PowerShell, .NET assemblies, and HTA and VBS files to spread across a targeted network, eventually dropping other pieces of malware, such as the SystemBC trojan and DCRAT, to enable various stages of their operations. The attackers' use of a variety of off-the-shelf tools makes it difficult to attribute this activity to a specific adversary.The final payload appears to be ModernLoader, which acts as a remote access trojan (RAT) by collecting system information and deploying various modules. In the earlier campaigns from March, we also observed the attackers delivering the cryptocurrency mining malware XMRig. The March campaigns appeared to be targeting Eastern European users, as the constructor utility we analyzed had predefined script templates written in Bulgarian, Polish, Hungarian and Russian.The actors are attempting to compromise vulnerable web applications to serve malware and deliver threats via files masquerading as fake Amazon gift cards. Technical detailsInitial findingsIn June 2022, Cisco Talos identified an unusual command line execution in our telemetry. The decoded base64 command is below: By Vanja SvajcerCisco Talos recently observed three separate, but related, campaigns between March and June 2022 delivering a variety of threats, including the ModernLoader bot, RedLine information-stealer and cryptocurrency-mining malware to victims. The actors use PowerShell, .NET assemblies, and HTA and VBS files to spread across a targeted network, eventually dropping other pieces of malware, such as the SystemBC trojan and DCRAT, to enable various stages of their operations. The attackers' use of a variety of off-the-shelf tools makes it difficult to attribute this activity to a specific adversary.The final payload appears to be ModernLoader, which acts as a remote access trojan (RAT) by collecting system information and deploying various modules. In the earlier campaigns from March, we also observed the attackers delivering the cryptocurrency mining malware XMRig. The March campaigns appeared to be targeting Eastern European users, as the constructor utility we analyzed had predefined script templates written in Bulgarian, Polish, Hungarian and Russian.The actors are attempting to compromise vulnerable web applications to serve malware and deliver threats via files masquerading as fake Amazon gift cards. Technical detailsInitial findingsIn June 2022, Cisco Talos identified an unusual command line execution in our telemetry. The decoded base64 command is below: Initial finding: A command executed on the system.The 31.41.244[.]231 IP is a Russian IP and hosts several other URLs with similar naming conventions. Autostart commandFollowing the discovery of the initial command, we identified two other command lines. They are a result of an autorun registered executable and the execution of a scheduled task. Initial finding: A command executed on the system.The 31.41.244[.]231 IP is a Russian IP and hosts several other URLs with similar naming conventions. Autostart commandFollowing the discovery of the initial command, we identified two other command lines. They are a result of an autorun registered executable and the execution of a scheduled task. |
Malware Tool Threat | Yahoo | ||
| 2022-08-29 15:15:09 | CVE-2022-0485 (lien direct) | A flaw was found in the copying tool `nbdcopy` of libnbd. When performing multi-threaded copies using asynchronous nbd calls, nbdcopy was blindly treating the completion of an asynchronous command as successful, rather than checking the *error parameter. This could result in the silent creation of a corrupted destination image. | Tool | |||
| 2022-08-28 11:24:43 | Dealing With False Positives when Scanning Memory Dumps for Cobalt Strike Beacons, (Sun, Aug 28th) (lien direct) | I updated my Cobalt Strike beacon analysis tool 1768.py to deal with false positives in Windows system&#;x26;#;39;s memory dumps. | Tool | |||
| 2022-08-26 15:45:25 | \'Sliver\' Emerges as Cobalt Strike Alternative for Malicious C2 (lien direct) | Microsoft and others say they have observed nation-state actors, ransomware purveyors, and assorted cybercriminals pivoting to an open source attack-emulation tool in recent campaigns. | Ransomware Tool | |||
| 2022-08-25 16:09:19 | ReasonLabs Launches Free Online Security Tool to Power Secure Web Experience for Millions of Global Users (lien direct) | Online Security autonomously blocks malicious URLs, extensions, ad trackers, and pop-ups 24/7, protecting consumers from complex and rapidly evolving cyber threats online. | Tool | |||
| 2022-08-25 10:16:06 | Microsoft Details New Post-Compromise Malware Used by Russian Cyberspies (lien direct) | Microsoft this week published technical details on 'MagicWeb', a new post-exploitation tool used by Russia-linked cyberespionage group APT29. | Malware Tool | APT 29 | ||
| 2022-08-24 19:29:23 | Efficient \'MagicWeb\' Malware Subverts AD FS Authentication, Microsoft Warns (lien direct) | The Russia-backed Nobelium APT has pioneered a post-exploitation tool allowing attackers to authenticate as any user. | Malware Tool | |||
| 2022-08-24 12:08:43 | Racing against the clock -- hitting a tiny kernel race window (lien direct) | TL;DR: How to make a tiny kernel race window really large even on kernels without CONFIG_PREEMPT:use a cache miss to widen the race window a little bitmake a timerfd expire in that window (which will run in an interrupt handler - in other words, in hardirq context)make sure that the wakeup triggered by the timerfd has to churn through 50000 waitqueue items created by epoll Racing one thread against a timer also avoids accumulating timing variations from two threads in each race attempt - hence the title. On the other hand, it also means you now have to deal with how hardware timers actually work, which introduces its own flavors of weird timing variations.Introduction I recently discovered a race condition (https://crbug.com/project-zero/2247) in the Linux kernel. (While trying to explain to someone how the fix for CVE-2021-0920 worked - I was explaining why the Unix GC is now safe, and then got confused because I couldn't actually figure out why it's safe after that fix, eventually realizing that it actually isn't safe.) It's a fairly narrow race window, so I was wondering whether it could be hit with a small number of attempts - especially on kernels that aren't built with CONFIG_PREEMPT, which would make it possible to preempt a thread with another thread, as I described at LSSEU2019. This is a writeup of how I managed to hit the race on a normal Linux desktop kernel, with a hit rate somewhere around 30% if the proof of concept has been tuned for the specific machine. I didn't do a full exploit though, I stopped at getting evidence of use-after-free (UAF) accesses (with the help of a very large file descriptor table and userfaultfd, which might not be available to normal users depending on system configuration) because that's the part I was curious about. This also demonstrates that even very small race conditions can still be exploitable if someone sinks enough time into writing an exploit, so be careful if you dismiss very small race windows as unexploitable or don't treat such issues as security bugs. The UAF reproducer is in our bugtracker.The bug In the UNIX domain socket garbage collection code (which is needed to deal with reference loops formed by UNIX domain sockets that use SCM_RIGHTS | Tool Guideline | APT 25 | ★★ | |
| 2022-08-24 12:02:07 | CVE-2021-1782, an iOS in-the-wild vulnerability in vouchers (lien direct) | Posted by Ian Beer, Google Project Zero This blog post is my analysis of a vulnerability exploited in the wild and patched in early 2021. Like the writeup published last week looking at an ASN.1 parser bug, this blog post is based on the notes I took as I was analyzing the patch and trying to understand the XNU vouchers subsystem. I hope that this writeup serves as the missing documentation for how some of the internals of the voucher subsystem works and its quirks which lead to this vulnerability. CVE-2021-1782 was fixed in iOS 14.4, as noted by @s1guza on twitter: 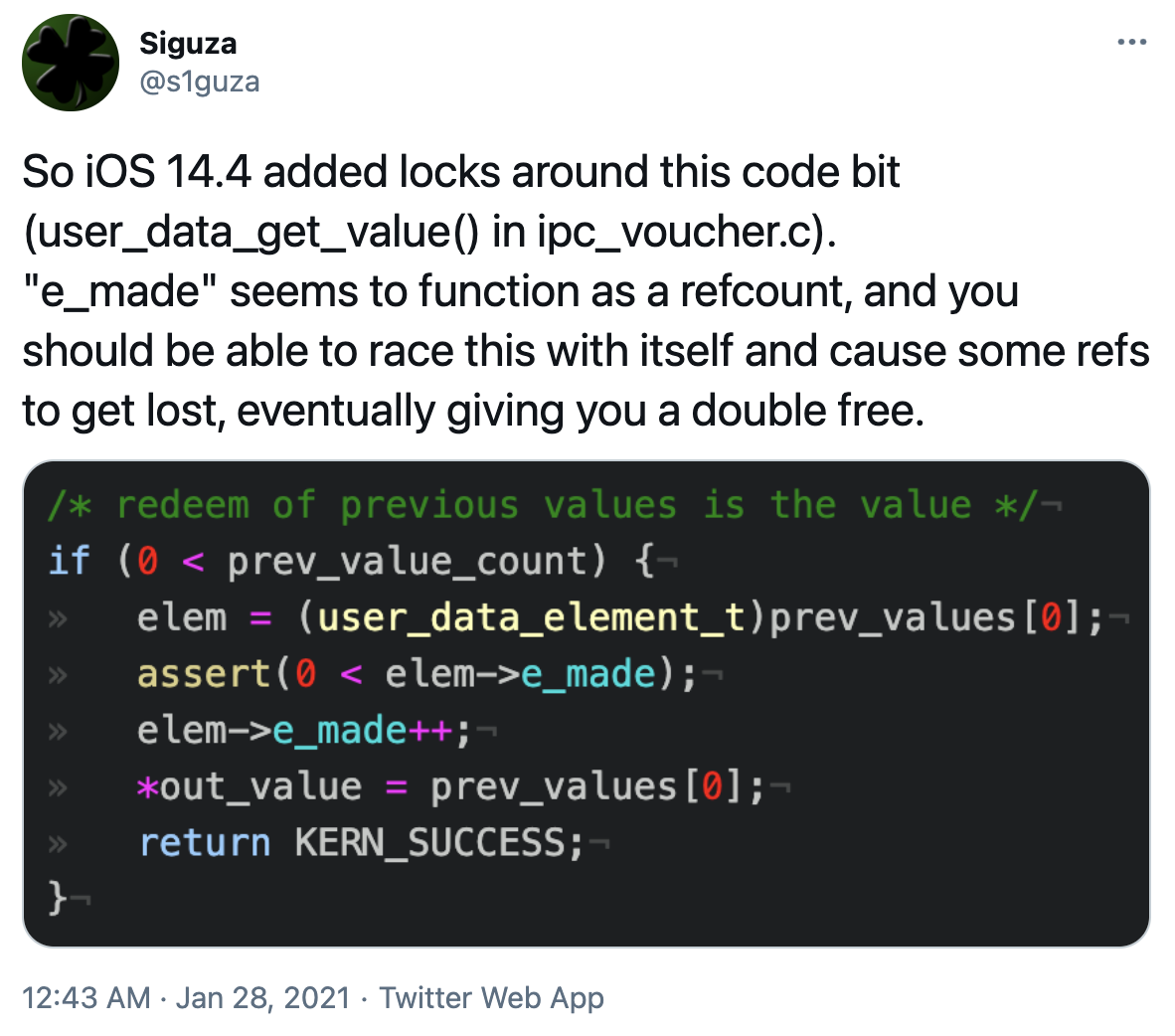 This vulnerability was fixed on January 26th 2021, and Apple updated the iOS 14.4 release notes on May 28th 2021 to indicate that the issue may have been actively exploited: This vulnerability was fixed on January 26th 2021, and Apple updated the iOS 14.4 release notes on May 28th 2021 to indicate that the issue may have been actively exploited: |
Hack Tool Vulnerability Guideline | ★★★ | ||
| 2022-08-24 04:26:37 | BitRAT and XMRig CoinMiner Being Distributed via Windows License Verification Tool (lien direct) | The ASEC analysis team has recently discovered the distribution of BitRAT and XMRig CoinMiner disguised as a Windows license verification tool. As introduced in previous posts, BitRAT has a history of being distributed on webhards as MS Windows license verification tools and MS Office installation programs. It is likely that the case covered by this post is being done by the same attacker. One thing to note is that a BitRAT remote control tool is installed in the environment without... | Tool | |||
| 2022-08-23 18:02:04 | Pirated 3DMark benchmark tool delivering info-stealer malware (lien direct) | Cybersecurity researchers have discovered multiple ongoing malware distribution campaigns that target internet users who seek to download copies of pirated software. [...] | Malware Tool | |||
| 2022-08-23 17:35:00 | Anomali Cyber Watch: Emissary Panda Adds New Operation Systems to Its Supply-Chain Attacks, Russia-Sponsored Seaborgium Spies on NATO Countries, TA558 Switches from Macros to Container Files, and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: China, Cyberespionage, DDoS, Russia, Spearphishing, Supply chain, Taiwan, and Ukraine. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Reservations Requested: TA558 Targets Hospitality and Travel
(published: August 18, 2022)
Since 2018, financially-motivated threat group TA558 has targeted hospitality and travel with reservation-themed, business-relevant phishing emails. The group concentrates on targeting Latin America using lures written in Portuguese and Spanish, and sometimes uses English and wider targeting (North America, Western Europe). TA558 was seen leveraging at least 15 different malware payloads, most often AsyncRAT, Loda RAT, Revenge RAT, and Vjw0rm. In 2022, Proofpoint researchers detected that TA558 increased its activity and moved from using malicious macros to URLs and container files (ISO, RAR).
Analyst Comment: Microsoft’s preparations to disable macros by default in Office products caused multiple threat groups including TA558 to adopt new filetypes to deliver payloads. It is crucial for personnel working with invoices and other external attachments to use updated, secured systems and be trained on phishing threats. Anomali Match can be used to quickly search your infrastructure for known TA558 IOCs.
MITRE ATT&CK: [MITRE ATT&CK] Phishing - T1566 | [MITRE ATT&CK] User Execution - T1204 | [MITRE ATT&CK] Command and Scripting Interpreter - T1059 | [MITRE ATT&CK] Scheduled Task - T1053 | [MITRE ATT&CK] Ingress Tool Transfer - T1105
Tags: TA558, AsyncRAT, Loda, RAT, Vjw0rm, BluStealer, Revenge RAT, XtremeRAT, Hospitality, Travel, Phishing, ISO, RAR, PowerShell, CVE-2017-11882, CVE-2017-8570
Estonia Subjected to 'Extensive' Cyberattacks after Moving Soviet Monuments
(published: August 18, 2022)
On August 17, 2022, Russian hacktivist group KillNet launched distributed denial-of-service (DDoS) attacks targeting Estonia. The Estonian government confirmed receiving the “most extensive” DDoS attacks in 15 years, but stressed that all services are back online after just some minor interruptions. Small and medium-sized DDoS attacks targeted 16 state and private organizations in the country, with seven of them experiencing downtime as a result. Specifically, the Estonian Tax and Customs Board website was unavailable for about 70 minutes.
Analyst Comment: Russian cyber activity follows political tensions, this time coinciding with the removal of a Red Army memorial. Estonia seemingly easily fended off this Russian DDoS attack, but the country is one of the top in cyber preparedness, and Russia limited it’s strike to using hacktivist groups that give plausible deniability when attributing the cyber attack on a NATO country. Organizations that rely on stable work of their I
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Reservations Requested: TA558 Targets Hospitality and Travel
(published: August 18, 2022)
Since 2018, financially-motivated threat group TA558 has targeted hospitality and travel with reservation-themed, business-relevant phishing emails. The group concentrates on targeting Latin America using lures written in Portuguese and Spanish, and sometimes uses English and wider targeting (North America, Western Europe). TA558 was seen leveraging at least 15 different malware payloads, most often AsyncRAT, Loda RAT, Revenge RAT, and Vjw0rm. In 2022, Proofpoint researchers detected that TA558 increased its activity and moved from using malicious macros to URLs and container files (ISO, RAR).
Analyst Comment: Microsoft’s preparations to disable macros by default in Office products caused multiple threat groups including TA558 to adopt new filetypes to deliver payloads. It is crucial for personnel working with invoices and other external attachments to use updated, secured systems and be trained on phishing threats. Anomali Match can be used to quickly search your infrastructure for known TA558 IOCs.
MITRE ATT&CK: [MITRE ATT&CK] Phishing - T1566 | [MITRE ATT&CK] User Execution - T1204 | [MITRE ATT&CK] Command and Scripting Interpreter - T1059 | [MITRE ATT&CK] Scheduled Task - T1053 | [MITRE ATT&CK] Ingress Tool Transfer - T1105
Tags: TA558, AsyncRAT, Loda, RAT, Vjw0rm, BluStealer, Revenge RAT, XtremeRAT, Hospitality, Travel, Phishing, ISO, RAR, PowerShell, CVE-2017-11882, CVE-2017-8570
Estonia Subjected to 'Extensive' Cyberattacks after Moving Soviet Monuments
(published: August 18, 2022)
On August 17, 2022, Russian hacktivist group KillNet launched distributed denial-of-service (DDoS) attacks targeting Estonia. The Estonian government confirmed receiving the “most extensive” DDoS attacks in 15 years, but stressed that all services are back online after just some minor interruptions. Small and medium-sized DDoS attacks targeted 16 state and private organizations in the country, with seven of them experiencing downtime as a result. Specifically, the Estonian Tax and Customs Board website was unavailable for about 70 minutes.
Analyst Comment: Russian cyber activity follows political tensions, this time coinciding with the removal of a Red Army memorial. Estonia seemingly easily fended off this Russian DDoS attack, but the country is one of the top in cyber preparedness, and Russia limited it’s strike to using hacktivist groups that give plausible deniability when attributing the cyber attack on a NATO country. Organizations that rely on stable work of their I |
Ransomware Malware Tool Threat | APT 27 | ||
| 2022-08-23 11:57:26 | Charming Kitten APT Wields New Scraper to Steal Email Inboxes (lien direct) | Google researchers say the nation-state hacking team is now employing a data-theft tool that targets Gmail, Yahoo!, and Microsoft Outlook accounts using previously acquired credentials. | Tool | Yahoo APT 35 | ||
| 2022-08-23 11:44:00 | True crime shows might be the biggest educational tool for cybercrime awareness (lien direct) | A survey of U.S. and UK residents conducted by Censuswide and commissioned by identity verification vendor Onfido released today said that popular culture – specifically, true-crime shows and movies – are having an outsized effect on the public's understanding of cybercrime.Two out of three survey respondents said that shows like Inventing Anna and documentaries like The Tinder Swindler have changed the way they view fraud in the modern day. Almost 60% of respondents also said that they're cautious about trusting other people online due to cultural depictions of fraud.Onfido CEO Mike Tuchen said in a press release that such programs have had a major impact on the public's view of fraud and cybercrime. “True crime and fraud-related entertainment stories have become widespread and popular. This is having a very real impact on how society views and perceives the prevalence and severity of fraud as a crime,” he said. “As a result, consumers are growing increasingly wary of online interactions, amid concerns over fraudster tactics and the security of their identities.”To read this article in full, please click here | Tool | |||
| 2022-08-23 11:00:00 | Google researchers expose Iranian hackers\' tool to steal emails from Gmail, Yahoo and Outlook (lien direct) | Security researchers linked the program to the so-called Charming Kitty Iranian hacker group known to carry out intelligence operations. | Tool | Yahoo Yahoo | ||
| 2022-08-23 10:00:00 | Establishing a mobile device vulnerability management program (lien direct) | The introduction of mobile devices has rapidly changed the world as we know it, as these small gadgets that are intended to fit into the palm of our hands rapidly gained dominance over our day-to-day activities. Thanks to these portable devices, we now have access to an abundance of information available to us on demand with minimal effort.
Mobile devices have become so powerful that your cellphone contains significant data about you as individual through your data storage, communication activities (social media, e-mail, text messages, audio calls), built-in health and fitness trackers, having access to financial accounts through NFC (near-field-communication) technology payment cards, GPS functionality. All this information that was once considered “personal data” is now contained on these portable devices that are more susceptible to physical theft, man-in-the-middle attacks when connected to unsecure wireless and cellular networks, as well as potential exploitation of vulnerabilities that are typically present on a mobile device operating system.
The periodic release of security updates for mobile devices is an attestation to the fact that the operating system software that runs on your mobile devices are never 100% secure. Data that is stored and processed by mobile devices are at high risk of potential breaches, and therefore business organizations are not factored out of this threat.
Businesses across a wide array of industry verticals are shifting their technological landscape to adapt to a portable ecosystem, by introducing mobile devices. While the presence of mobile devices in a business environment grows, these devices are not being effectively secured through appropriate patch update cycles, and that unauthorized users may also be accessing these company-owned devices.
These mobile devices typically have access to substantial amounts of information and may also literally serve as the “keys to the kingdom” through serving as Multi-Factor Authentication (MFA) tokens to business information systems. An organization may have invested countless hours and resources to secure information technology infrastructure, but all that effort is now simply undermined by the fact that data is longer static within the confines of your organizations firewall perimeter.
Your data is now always on the move with your employees’ mobile devices. As a result, the need for an effective mobile device vulnerability management program is more imperative than ever, in order to consistently identify, track and remediate vulnerabilities, as a way to prevent the exploitation of vulnerabilities that may allow malicious users to gain access to your resources.
 Mobile devices are not traditionally given a first thought when establishing a formal vulnerability management program. The devices that are typically given first thought include but are not limited to workstations, servers, networking appliances, web applications.
However, new threatening vulnerabilities are discovered and published daily in various vulnerability databases, and many of these discoveries specifically impact mobile devices. Mobile devices must not be overlooked when establishing your vulnerability program. A vulnerability scan can typically discover hundreds of vulnerabilities on your mobile devices, but all it takes to hand over the keys to your kingdom to a malicious actor is the exploitation of one of those vulnerabilities.
Organizations invest a significant amount of resources to secure their IT infrastructure, however these mobile devices now serve as an entry-point directly into the environment, providing access to potentially petabytes of your data. Despite these security concerns in mind, mobile device vulnerability management unfortunately remains an afterthought.
Without a formal vulnerability assessment for mobile devices, undetected vulnerabilities on these
Mobile devices are not traditionally given a first thought when establishing a formal vulnerability management program. The devices that are typically given first thought include but are not limited to workstations, servers, networking appliances, web applications.
However, new threatening vulnerabilities are discovered and published daily in various vulnerability databases, and many of these discoveries specifically impact mobile devices. Mobile devices must not be overlooked when establishing your vulnerability program. A vulnerability scan can typically discover hundreds of vulnerabilities on your mobile devices, but all it takes to hand over the keys to your kingdom to a malicious actor is the exploitation of one of those vulnerabilities.
Organizations invest a significant amount of resources to secure their IT infrastructure, however these mobile devices now serve as an entry-point directly into the environment, providing access to potentially petabytes of your data. Despite these security concerns in mind, mobile device vulnerability management unfortunately remains an afterthought.
Without a formal vulnerability assessment for mobile devices, undetected vulnerabilities on these |
Tool Vulnerability Guideline | |||
| 2022-08-23 07:50:00 | Google Uncovers Tool Used by Iranian Hackers to Steal Data from Email Accounts (lien direct) | The Iranian government-backed actor known as Charming Kitten has added a new tool to its malware arsenal that allows it to retrieve user data from Gmail, Yahoo!, and Microsoft Outlook accounts. Dubbed HYPERSCRAPE by Google Threat Analysis Group (TAG), the actively in-development malicious software is said to have been used against less than two dozen accounts in Iran, with the oldest known | Malware Tool Threat Conference | Yahoo APT 35 | ||
| 2022-08-22 20:30:34 | Metasploit Creator Renames His Startup and IT Discovery Tool Rumble to \'runZero\' (lien direct) | HD Moore's company has rebranded its IT, IoT, and OT asset discovery tool as the platform rapidly evolves. | Tool | |||
| 2022-08-22 14:00:00 | Threat Actor Deploys Raven Storm Tool to Perform DDoS Attacks (lien direct) | The malware is reportedly capable of server takedown, Wi-Fi attacks and application layer attacks | Malware Tool | |||
| 2022-08-22 13:30:00 | How Qualys Reduces Risk and Enables Tool Consolidation (lien direct) | Sumedh Thakar, CEO of Qualys, explains how moving to a cloud-based asset management platform can simplify their strategies and improve overall security. | Tool | |||
| 2022-08-20 13:00:00 | Janet Jackson\'s \'Rhythm Nation\' Can Crash Old Hard Drives (lien direct) | Plus: The Twilio hack snags a reporter, a new tool to check for spyware, and the Canadian weed pipeline gets hit by a cyberattack. | Hack Tool | |||
| 2022-08-18 18:34:08 | China\'s APT41 Embraces Baffling Approach for Dropping Cobalt Strike Payload (lien direct) | The state-sponsored threat actor has switched up its tactics, also adding an automated SQL-injection tool to its bag of tricks for initial access. | Tool Threat | APT 41 | ||
| 2022-08-18 11:45:45 | USB “Rubber Ducky” Attack Tool (lien direct) | The USB Rubber Ducky is getting better and better. Already, previous versions of the Rubber Ducky could carry out attacks like creating a fake Windows pop-up box to harvest a user’s login credentials or causing Chrome to send all saved passwords to an attacker’s webserver. But these attacks had to be carefully crafted for specific operating systems and software versions and lacked the flexibility to work across platforms. The newest Rubber Ducky aims to overcome these limitations. It ships with a major upgrade to the DuckyScript programming language, which is used to create the commands that the Rubber Ducky will enter into a target machine. While previous versions were mostly limited to writing keystroke sequences, DuckyScript 3.0 is a feature-rich language, letting users write functions, store variables, and use logic flow controls (i.e., if this… then that)... | Tool | |||
| 2022-08-17 22:15:08 | CVE-2022-2869 (lien direct) | libtiff's tiffcrop tool has a uint32_t underflow which leads to out of bounds read and write in the extractContigSamples8bits routine. An attacker who supplies a crafted file to tiffcrop could trigger this flaw, most likely by tricking a user into opening the crafted file with tiffcrop. Triggering this flaw could cause a crash or potentially further exploitation. | Tool Guideline | |||
| 2022-08-17 10:00:00 | A pragmatic approach to risk management & resilience (lien direct) | Cybersecurity starts with the ability to recognize your cyber risk. We will explore several topics related to taking a practical approach to managing risk and achieving cyber resilience. This is a blog series with collective thoughts from Bindu Sundaresan, Director AT&T Cybersecurity, and Nick Simmons, AVP, Cybersecurity. Cybercrime has become increasingly frequent, complex, and costly, posing a risk to all businesses regardless of size. How do you plan to respond when falling victim to a breach? Would you know who to call, how to react, or what to tell your employees, customers, and media? Could your organization absorb the potential financial and reputational impact of a lawsuit? The answer cannot be, "we store everything in the cloud, so we are good." Who owns the risk? Could your brand's image survive? What is acceptable, and how do you know your current plan will suffice? What more could your company do to understand better and manage the risk? These questions are all top of mind and need to be addressed from an overall business perspective. This blog summarizes the fundamental steps and offers suggestions to understand, manage, and respond to risk. Beyond technology, focus on risk and resilience It can be easy to deploy security technology and think you've mitigated risk to your business. Unfortunately, technology investment is no guarantee of protection against the latest threats. It is critical to take a risk-based approach to security, meaning leaders must identify and focus on specific elements of cyber risk to decrease enterprise risk. Specifically, the many components of cyber risk must be understood and prioritized for enterprise cybersecurity efforts. Organizations are increasingly aiming to shift from cybersecurity to cyber resilience, and the following recommendations can help forge this path: Understand the threats Measure the potential financial impact of cyber exposures compared to the company's risk appetite level; and Proactively manage cyber risks with clear action plans based on their capabilities and capacities to protect against cybercrime Risk-based approach Cyber resiliency requires a risk-based approach, accomplishing two critical things at once. First, it designates risk reduction as the primary goal, enabling the organization to prioritize investment, including implementation-related problem solving based squarely on a cyber program's effectiveness at reducing risk. Second, the program distills top management's risk-reduction targets into pragmatic implementation programs with precise alignment from senior executives to the front line. Following the risk-based approach, a company will no longer "build the control everywhere"; rather, the focus will be on building the appropriate controls for the worst vulnerabilities to defeat the most significant threats that target the business' most critical areas. The risk-based approach to cybersecurity is thus ultimately interactive and a dynamic tool to support strategic decision-making. Focused on business value, utilizing a common language among the interested parties, and directly linking enterprise risks to controls, the approach helps translate executive decisions about risk reduction into control implementation. The power of the risk-based approach to optimize risk reduction at any level of investment is enhanced by its flexibility, adjusting to an evolving risk-appetite strategy as needed. A risk-based approach recognizes that there are no perfect security solutions. Still, those that strategically balance security, scalability, access, usability, and cost can ultimately provide the best long-term protection against an evolving adversary. Fundamentally, risk transformation changes security strategy from an outside-in perspective, where external threats and regulations drive strategy, to an | Ransomware Data Breach Tool Vulnerability Threat Patching Guideline | |||
| 2022-08-16 15:30:00 | Healthcare Provider Issues Warning After Tracking Pixels Leak Patient Data (lien direct) | The leak was caused by incorrect configurations of an online tracking tool from Meta | Tool | |||
| 2022-08-16 15:06:00 | Anomali Cyber Watch: Ransomware Module Added to SOVA Android Trojan, Bitter APT Targets Mobile Phones with Dracarys, China-Sponsored TA428 Deploys Six Backdoors at Once, and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: Android, APT, China, Cyberespionage, India, Malspam, Ransomware, Spearphishing, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
APT-C-35: New Windows Framework Revealed
(published: August 11, 2022)
The DoNot Team (APT-C-35) are India-sponsored actors active since at least 2016. Morphisec Labs researchers discovered a new Windows framework used by the group in its campaign targeting Pakistani government and defense departments. The attack starts with a spearphishing RTF attachment. If opened in a Microsoft Office application, it downloads a malicious remote template. After the victim enables editing (macroses) a multi-stage framework deployment starts. It includes two shellcode stages followed by main DLL that, based on victim fingerprinting, downloads a custom set of additional information-stealing modules.
Analyst Comment: The described DoNot Team framework is pretty unique in its customisation, fingerprinting, and module implementation. At the same time, the general theme of spearphishing attachment that asks the targeted user to enable editing is not new and can be mitigated by anti-phishing training and Microsoft Office settings hardening.
MITRE ATT&CK: [MITRE ATT&CK] Phishing - T1566 | [MITRE ATT&CK] Virtualization/Sandbox Evasion - T1497 | [MITRE ATT&CK] Template Injection - T1221 | [MITRE ATT&CK] User Execution - T1204 | [MITRE ATT&CK] Ingress Tool Transfer - T1105 | [MITRE ATT&CK] Obfuscated Files or Information - T1027 | [MITRE ATT&CK] Deobfuscate/Decode Files or Information - T1140 | [MITRE ATT&CK] Scheduled Task - T1053 | [MITRE ATT&CK] System Information Discovery - T1082 | [MITRE ATT&CK] Input Capture - T1056 | [MITRE ATT&CK] Screen Capture - T1113 | [MITRE ATT&CK] Data from Local System - T1005 | [MITRE ATT&CK] Data from Removable Media - T1025 | [MITRE ATT&CK] Data from Network Shared Drive - T1039 | [MITRE ATT&CK] Credentials from Password Stores - T1555 | [MITRE ATT&CK] Data Staged - T1074 | [MITRE ATT&CK] Command and Scripting Interpreter - T1059
Tags: APT-C-35, DoNot Team, APT, India, source-country:IN, Government, Military, Pakistan, target-country:PK, Windows
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
APT-C-35: New Windows Framework Revealed
(published: August 11, 2022)
The DoNot Team (APT-C-35) are India-sponsored actors active since at least 2016. Morphisec Labs researchers discovered a new Windows framework used by the group in its campaign targeting Pakistani government and defense departments. The attack starts with a spearphishing RTF attachment. If opened in a Microsoft Office application, it downloads a malicious remote template. After the victim enables editing (macroses) a multi-stage framework deployment starts. It includes two shellcode stages followed by main DLL that, based on victim fingerprinting, downloads a custom set of additional information-stealing modules.
Analyst Comment: The described DoNot Team framework is pretty unique in its customisation, fingerprinting, and module implementation. At the same time, the general theme of spearphishing attachment that asks the targeted user to enable editing is not new and can be mitigated by anti-phishing training and Microsoft Office settings hardening.
MITRE ATT&CK: [MITRE ATT&CK] Phishing - T1566 | [MITRE ATT&CK] Virtualization/Sandbox Evasion - T1497 | [MITRE ATT&CK] Template Injection - T1221 | [MITRE ATT&CK] User Execution - T1204 | [MITRE ATT&CK] Ingress Tool Transfer - T1105 | [MITRE ATT&CK] Obfuscated Files or Information - T1027 | [MITRE ATT&CK] Deobfuscate/Decode Files or Information - T1140 | [MITRE ATT&CK] Scheduled Task - T1053 | [MITRE ATT&CK] System Information Discovery - T1082 | [MITRE ATT&CK] Input Capture - T1056 | [MITRE ATT&CK] Screen Capture - T1113 | [MITRE ATT&CK] Data from Local System - T1005 | [MITRE ATT&CK] Data from Removable Media - T1025 | [MITRE ATT&CK] Data from Network Shared Drive - T1039 | [MITRE ATT&CK] Credentials from Password Stores - T1555 | [MITRE ATT&CK] Data Staged - T1074 | [MITRE ATT&CK] Command and Scripting Interpreter - T1059
Tags: APT-C-35, DoNot Team, APT, India, source-country:IN, Government, Military, Pakistan, target-country:PK, Windows |
Ransomware Malware Tool Vulnerability Threat Guideline Medical | APT 38 | ||
| 2022-08-16 10:03:51 | Vulnerability Spotlight: Three vulnerabilities in HDF5 file format could lead to remote code execution (lien direct) |  Dave McDaniel of Cisco Talos discovered these vulnerabilities. Blog by Jon Munshaw. Cisco Talos recently discovered three vulnerabilities in a library that works with the HDF5 file format that could allow an attacker to execute remote code on a targeted device. These issues arise in the libhdf5 gif2h5 tool that's normally used to convert a GIF file to the HDF5 format, commonly used to store large amounts of numerical data. An attacker could exploit these vulnerabilities by tricking a user into opening a specially crafted, malicious file. TALOS-2022-1485 (CVE-2022-25972) and TALOS-2022-1486 (CVE-2022-25942) are out-of-bounds write vulnerabilities in the gif2h5 tool that trigger a specific crash, opening the door for code execution from the adversary. TALOS-2022-1487 (CVE-2022-26061) works similarly but is a heap-based buffer overflow vulnerability. Cisco Talos is disclosing these vulnerabilities despite no official fix from HDF5 in adherence to the 90-day deadline outlined in Cisco's vulnerability disclosure policy. Dave McDaniel of Cisco Talos discovered these vulnerabilities. Blog by Jon Munshaw. Cisco Talos recently discovered three vulnerabilities in a library that works with the HDF5 file format that could allow an attacker to execute remote code on a targeted device. These issues arise in the libhdf5 gif2h5 tool that's normally used to convert a GIF file to the HDF5 format, commonly used to store large amounts of numerical data. An attacker could exploit these vulnerabilities by tricking a user into opening a specially crafted, malicious file. TALOS-2022-1485 (CVE-2022-25972) and TALOS-2022-1486 (CVE-2022-25942) are out-of-bounds write vulnerabilities in the gif2h5 tool that trigger a specific crash, opening the door for code execution from the adversary. TALOS-2022-1487 (CVE-2022-26061) works similarly but is a heap-based buffer overflow vulnerability. Cisco Talos is disclosing these vulnerabilities despite no official fix from HDF5 in adherence to the 90-day deadline outlined in Cisco's vulnerability disclosure policy. |
Tool Vulnerability | |||
| 2022-08-12 21:00:00 | Anti-tracking tool tells you if you\'re being followed (lien direct) | >Categories: NewsCategories: PrivacyAt Black Hat, a cybersecurity expert presented an anti-stalking tool they made for a friend. (Read more...) | Tool | |||
| 2022-08-11 06:54:45 | InfoStealer Script Based on Curl and NSudo, (Thu, Aug 11th) (lien direct) | If sudo[1] is a well known tool used daily by most UNIX system administrators, NSudo[2] remains less below the radar. This is a tool running on Microsoft Windows which allows you to execute processes with different access tokens and privileges like: | Tool | |||
| 2022-08-10 14:14:08 | Why robotexts are scammers\' favorite new tool (lien direct) | Technology meant to limit robocalls has pushed scammers toward SMS-based attacks, which experts say can be even more dangerous. | Tool | |||
| 2022-08-10 13:10:00 | Sensitive data in the cloud gets new automated remediation tool from BigID (lien direct) | Data intelligence company BigID announced this week at the Black Hat conference in Las Vegas that it has rolled out new features for its privacy and data protection platform, allowing users to programmatically restrict access to sensitive cloud-based information when it's under threat.BigID's core product, its Data Intelligence platform, already boasts numerous capabilities focused on the privacy, organization and discovery of a company's data. The new features announced this week build on that framework, allowing IT staff to automatically lock down access to sensitive information tagged as having open or overprivileged access in the big three public cloud platforms.To read this article in full, please click here | Tool | |||
| 2022-08-10 11:45:56 | Microsoft Patch Tuesday Fixed 0-day Arbitrary Code Execution Vulnerability (CVE-2022-34713) (lien direct) | Microsoft has released 141 security fixes for this month's August 2022 release. Besides the usual security fixes, there was a zero-day of note:CVE-2022-34713: This is a vulnerability in Microsoft Support Diagnostic Tool (MSDT). Microsoft confirmed in their advisory that the vulnerability was exploited in the wild as a zero-day. CVE-2022-34713 is an arbitrary code execution (ACE) vulnerability, which requires user interaction. As such an user need to open a specifically crafted file or visit a specially designed Web site to be exploited. This has a CVSS score of 7.8 and is rated important.Why is this Significant?This is significant as Microsoft observed CVE-2022-34713 was exploited as a 0-day in the wild. Because the exploitation requires user interaction, an attacker likely uses social engineering to get users to open a specifically crafted file or visit a specially designed Web site for exploitation.How Widespread is the Attack that Leverages CVE-2022-34713?At this time, there is no information available as to how widespread the attack is. However, since the vulnerability was publicly disclosed, attacks that leverage CVE-2022-34713 may increase.Also, a similar vulnerability in MSDT (CVE-2022-30190, also known as Follina) that was patched in June 2022 by Microsoft is widely exploited in the wild. This is another indicator that likelihood of CVE-2022-34713 exploitation will likely increase.FortiGuard Labs previously released a Threat Signal for CVE-2022-30190 (Follina). See the Appendix for a link to "Follina: 0-day Windows MSDT Vulnerability (CVE-2022-30190) Exploited In The Wild".Is there Any Other Vulnerability in the August Patch Tuesday that Requires Attention?Microsoft also released a patch for another vulnerability in MSDT (CVE-2022-35743). While the vulnerability was not reported nor observed to have been exploited in the wild, the Microsoft advisory states that exploitation is likely to occur. As such a patch for CVE-2022-35743 should also be applied as soon as possible. This has a CVSS score of 7.8 and is rated important.Has Microsoft Released Security Advisories for CVE-2022-34713?Yes, Microsoft has issued an advisory for the vulnerability. See the Appendix for a link to "CVE-2022-34713: Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability".Has Microsoft Released a Patch for CVE-2022-34713?Yes, Microsoft has released a patch for CVE-2022-34713 on August 9th, 2022 as part of regular MS Tuesday for the month.What is the Status of Coverage?FortiGuard Labs is investigating coverage, and will update this threat signal once any relevant updates are available. | Tool Vulnerability Threat | |||
| 2022-08-10 07:00:00 | (Déjà vu) capa v4: couler un .net plus large capa v4: casting a wider .NET (lien direct) |
Nous sommes ravis d'annoncer la version 4.0 de CAPA avec la prise en charge de l'analyse des exécutables .NET.Cet outil open source identifie automatiquement les capacités des programmes à l'aide d'un ensemble de règles extensible.L'outil prend en charge à la fois le triage de logiciels malveillants et l'ingénierie inverse de plongée profonde.Si vous n'avez pas entendu parler de CAPA auparavant ou si vous avez besoin d'un rafraîchissement, consultez notre Premier article de blog .Vous pouvez télécharger des binaires autonomes CAPA V4.0 à partir des Project \ Project \\ 's Page de libération Et vérifiez le code source sur github .
CAPA 4.0 ajoute de nouvelles fonctionnalités majeures qui étendent sa capacité à analyser et à raisonner sur les programmes.Ce billet de blog couvre
We are excited to announce version 4.0 of capa with support for analyzing .NET executables. This open-source tool automatically identifies capabilities in programs using an extensible rule set. The tool supports both malware triage and deep dive reverse engineering. If you have not heard of capa before, or need a refresher, check out our first blog post. You can download capa v4.0 standalone binaries from the project\'s release page and checkout the source code on GitHub. capa 4.0 adds major new features that extends its ability to analyze and reason about programs. This blog post covers |
Malware Tool | ★★★★ | ||
| 2022-08-09 23:12:13 | (Déjà vu) Microsoft Issues Patches for 121 Flaws, Including Zero-Day Under Active Attack (lien direct) | As many as 121 new security flaws were patched by Microsoft as part of its Patch Tuesday updates for the month of August, which also includes a fix for a Support Diagnostic Tool vulnerability that the company said is being actively exploited in the wild. Of the 121 bugs, 17 are rated Critical, 102 are rated Important, one is rated Moderate, and one is rated Low in severity. Two of the issues | Tool Vulnerability | ★★★★ | ||
| 2022-08-09 23:01:10 | Microsoft Patch Tuesday, August 2022 Edition (lien direct) | Microsoft today released updates to fix a record 141 security vulnerabilities in its Windows operating systems and related software. Once again, Microsoft is patching a zero-day vulnerability in the Microsoft Support Diagnostics Tool (MSDT), a service built into Windows. Redmond also addressed multiple flaws in Exchange Server - including one that was disclosed publicly prior to today - and it is urging organizations that use Exchange for email to update as soon as possible and to enable additional protections. | Tool Vulnerability Patching | |||
| 2022-08-09 20:25:07 | Microsoft Patches Zero-Day Actively Exploited in the Wild (lien direct) | The computing giant issued a massive Patch Tuesday update, including a pair of remote execution flaws in the Microsoft Support Diagnostic Tool (MSDT) after attackers used one of the vulnerabilities in a zero-day exploit. | Tool | |||
| 2022-08-09 20:15:11 | CVE-2022-34713 (lien direct) | Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability. This CVE ID is unique from CVE-2022-35743. | Tool | |||
| 2022-08-09 17:12:16 | Researchers Debut Fresh RCE Vector for Common Google API Tool (lien direct) | The finding exposes the danger of older, unpatched bugs, which plague at least 4.5 million devices. | Tool | |||
| 2022-08-09 16:44:37 | Microsoft Patch Tuesday for August 2022 - Snort rules and prominent vulnerabilities (lien direct) |  By Jon Munshaw and Vanja Svajcer.Microsoft released its monthly security update Tuesday, disclosing more than 120 vulnerabilities across its line of products and software, the most in a single Patch Tuesday in four months. This batch of updates also includes a fix for a new vulnerability in the Microsoft Windows Support Diagnostic Tool (MSDT) that's actively being exploited in the wild, according to Microsoft. MSDT was already the target of the so-called “Follina” zero-day vulnerability in June. In all, August's Patch Tuesday includes 15 critical vulnerabilities and a single low- and moderate-severity issue. The remainder is classified as “important.” Two of the important vulnerabilities CVE-2022-35743 and CVE-2022-34713 are remote code execution vulnerabilities in MSDT. However, only CVE-2022-34713 has been exploited in the wild and Microsoft considers it “more likely” to be exploited. Microsoft Exchange Server contains two critical elevation of privilege vulnerabilities, CVE-2022-21980 and CVE-2022-24477. An attacker could exploit this vulnerability by tricking a target into visiting a malicious, attacker-hosted server or website. In addition to applying the patch released today, potentially affected users should enable Extended Protection on vulnerable versions of the server. The Windows Point-to-Point Tunneling Protocol is also vulnerable to three critical vulnerabilities. Two of them, CVE-2022-35744 and CVE-2022-30133, could allow an attacker to execute remote code on an RAS server machine. The other, CVE-2022-35747, could lead to a denial-of-service condition. CVE-2022-35744 has a CVSS severity score of 9.8 out of 10, one of the highest-rated vulnerabilities this month. An attacker could exploit these vulnerabilities by communicating via Port 1723. Affected users can render these issues unexploitable by blocking that port, though it runs the risk of disrupting other legitimate communications. Another critical code execution vulnerability, CVE-2022-35804, affects the SMB Client and Server and the way the protocol handles specific requests. An attacker could exploit this on the SMB Client by config By Jon Munshaw and Vanja Svajcer.Microsoft released its monthly security update Tuesday, disclosing more than 120 vulnerabilities across its line of products and software, the most in a single Patch Tuesday in four months. This batch of updates also includes a fix for a new vulnerability in the Microsoft Windows Support Diagnostic Tool (MSDT) that's actively being exploited in the wild, according to Microsoft. MSDT was already the target of the so-called “Follina” zero-day vulnerability in June. In all, August's Patch Tuesday includes 15 critical vulnerabilities and a single low- and moderate-severity issue. The remainder is classified as “important.” Two of the important vulnerabilities CVE-2022-35743 and CVE-2022-34713 are remote code execution vulnerabilities in MSDT. However, only CVE-2022-34713 has been exploited in the wild and Microsoft considers it “more likely” to be exploited. Microsoft Exchange Server contains two critical elevation of privilege vulnerabilities, CVE-2022-21980 and CVE-2022-24477. An attacker could exploit this vulnerability by tricking a target into visiting a malicious, attacker-hosted server or website. In addition to applying the patch released today, potentially affected users should enable Extended Protection on vulnerable versions of the server. The Windows Point-to-Point Tunneling Protocol is also vulnerable to three critical vulnerabilities. Two of them, CVE-2022-35744 and CVE-2022-30133, could allow an attacker to execute remote code on an RAS server machine. The other, CVE-2022-35747, could lead to a denial-of-service condition. CVE-2022-35744 has a CVSS severity score of 9.8 out of 10, one of the highest-rated vulnerabilities this month. An attacker could exploit these vulnerabilities by communicating via Port 1723. Affected users can render these issues unexploitable by blocking that port, though it runs the risk of disrupting other legitimate communications. Another critical code execution vulnerability, CVE-2022-35804, affects the SMB Client and Server and the way the protocol handles specific requests. An attacker could exploit this on the SMB Client by config |
Tool Vulnerability Guideline | ★★★★ | ||
| 2022-08-09 15:01:00 | Anomali Cyber Watch: RapperBot Persists on SSH Servers, Manjusaka Attack Framework Tested in China, BlackCat/DarkSide Ransom Energy Again, and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Botnet, China, Data breach, DDoS, Phishing, Ransomware, and Taiwan. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
So RapperBot, What Ya Bruting For?
(published: August 3, 2022)
RapperBot, a new Internet of things (IoT) botnet, is rapidly evolving despite appearing in the wild just two months ago (June 2022). Fortinet researchers discovered that RapperBot heavily reuses parts of the Mirai source code, but changed the attack vector (brute-forcing SSH instead of Telnet), command and control (C2) protocol, and added persistence capabilities. RapperBot maintains remote access by adding the attacker's public key to ~/.ssh/authorized_keys. The latest RapperBot samples also started adding the root user "suhelper” to /etc/passwd and /etc/shadow/, and continue to add the root user account every hour. Top targeted IPs were from Taiwan, USA, and South Korea, in that order. RapperBot has basic DDoS capabilities such as UDP and TCP STOMP flood copied from Mirai source code.
Analyst Comment: Despite sharing a significant amount of source code with Mirai variants, RapperBot appears to be developed by a persistent actor and not a novice motivated by notoriety. It is possible that the actors will add new impact functionality after the RapperBot botnet grows substantially. SSH server administrators should adhere to secure password practices. It is also important to note that simply restarting the device, changing SSH credentials or even disabling SSH password authentication does not remove the RapperBot infection.
MITRE ATT&CK: [MITRE ATT&CK] Valid Accounts - T1078 | [MITRE ATT&CK] Obfuscated Files or Information - T1027 | [MITRE ATT&CK] Deobfuscate/Decode Files or Information - T1140 | [MITRE ATT&CK] Network Denial of Service - T1498 | [MITRE ATT&CK] Account Manipulation - T1098 | [MITRE ATT&CK] Create Account - T1136 | [MITRE ATT&CK] Scheduled Task - T1053
Tags: RapperBot, Taiwan, target-country:TW, USA, target-country:US, South Korea, target-country:KR, SSH brute force, DDoS, IoT, ARM, MIPS, SPARC, x86, Linux, UDP flood, TCP STOMP, port:4343, port:4344, port:4345, port:48109, Mirai
Woody RAT: A New Feature-Rich Malware Spotted in the Wild
(published: August 3, 2022)
Malwarebytes researchers have identified a new Remote Access Trojan (RAT) dubbed Woody Rat. It has been used by unidentified attackers for at least one year targeting Russian organizations in the aerospace industry. Two kinds of spearphishing attachment were used. Initially, Woody Rat was delivered via archived executable with double extension .DOC.EXE. More recently, the attackers switched to Microsoft Office documents leveraging the Follina (CVE-2022-30190) vulnerability. Woody Ra
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
So RapperBot, What Ya Bruting For?
(published: August 3, 2022)
RapperBot, a new Internet of things (IoT) botnet, is rapidly evolving despite appearing in the wild just two months ago (June 2022). Fortinet researchers discovered that RapperBot heavily reuses parts of the Mirai source code, but changed the attack vector (brute-forcing SSH instead of Telnet), command and control (C2) protocol, and added persistence capabilities. RapperBot maintains remote access by adding the attacker's public key to ~/.ssh/authorized_keys. The latest RapperBot samples also started adding the root user "suhelper” to /etc/passwd and /etc/shadow/, and continue to add the root user account every hour. Top targeted IPs were from Taiwan, USA, and South Korea, in that order. RapperBot has basic DDoS capabilities such as UDP and TCP STOMP flood copied from Mirai source code.
Analyst Comment: Despite sharing a significant amount of source code with Mirai variants, RapperBot appears to be developed by a persistent actor and not a novice motivated by notoriety. It is possible that the actors will add new impact functionality after the RapperBot botnet grows substantially. SSH server administrators should adhere to secure password practices. It is also important to note that simply restarting the device, changing SSH credentials or even disabling SSH password authentication does not remove the RapperBot infection.
MITRE ATT&CK: [MITRE ATT&CK] Valid Accounts - T1078 | [MITRE ATT&CK] Obfuscated Files or Information - T1027 | [MITRE ATT&CK] Deobfuscate/Decode Files or Information - T1140 | [MITRE ATT&CK] Network Denial of Service - T1498 | [MITRE ATT&CK] Account Manipulation - T1098 | [MITRE ATT&CK] Create Account - T1136 | [MITRE ATT&CK] Scheduled Task - T1053
Tags: RapperBot, Taiwan, target-country:TW, USA, target-country:US, South Korea, target-country:KR, SSH brute force, DDoS, IoT, ARM, MIPS, SPARC, x86, Linux, UDP flood, TCP STOMP, port:4343, port:4344, port:4345, port:48109, Mirai
Woody RAT: A New Feature-Rich Malware Spotted in the Wild
(published: August 3, 2022)
Malwarebytes researchers have identified a new Remote Access Trojan (RAT) dubbed Woody Rat. It has been used by unidentified attackers for at least one year targeting Russian organizations in the aerospace industry. Two kinds of spearphishing attachment were used. Initially, Woody Rat was delivered via archived executable with double extension .DOC.EXE. More recently, the attackers switched to Microsoft Office documents leveraging the Follina (CVE-2022-30190) vulnerability. Woody Ra |
Ransomware Malware Tool Vulnerability Threat | |||
| 2022-08-09 11:11:31 | More tools don\'t equal a stronger SOC (lien direct) | >Logpoint's latest release helps analysts integrate their tech stack and combines many capabilities in a single tool to help reduce the number of cybersecurity toolsby Gitte Gade, Product Marketing ManagerWith the development of new technology, the number of tools added to the list for security analysts keeps increasing. A study by ESG found that 40% [...] | Tool | |||
| 2022-08-08 07:00:00 | KMSpico explained: No, KMS is not "kill Microsoft" (lien direct) | >Categories: ExplainedA hack tool called KMSPico is hailed as the go-to tool when it comes to activiating Windows. But is it safe? (Read more...) | Hack Tool | |||
| 2022-08-07 07:00:00 | Comment scanner des QRCode depuis le Terminal Linux ? (lien direct) | Si vous travaillez essentiellement sur PC Linux et que vous n’avez de smartphone sous la main pour scanner un éventuel QRCode, j’ai ce qu’il vous faut. Il s’agit d’un petit tool qui s’appelle Qrscan et qui permet au choix d’utiliser la webcam de votre PC pour scanner un QRCode sur … Suite | Tool | |||
| 2022-08-04 14:00:00 | Hackers deploy new ransomware tool in attacks on Albanian government websites (lien direct) | >The hackers linked to the Iranian government claimed to have attacked Albania for hosting an opposition group conference. | Ransomware Tool | |||
| 2022-08-04 13:34:26 | Protect domain-joined computer passwords with Windows\' Local Administrator Password Solution (lien direct) | Windows finally includes a tool to manage local admin passwords, but admins will still need to do some work to make it useful. | Tool | |||
| 2022-08-04 08:00:13 | Attackers leveraging Dark Utilities "C2aaS" platform in malware campaigns (lien direct) |  By Edmund Brumaghin, Azim Khodjibaev and Matt Thaxton, with contributions from Arnaud Zobec.Executive SummaryDark Utilities, released in early 2022, is a platform that provides full-featured C2 capabilities to adversaries.It is marketed as a means to enable remote access, command execution, distributed denial-of-service (DDoS) attacks and cryptocurrency mining operations on infected systems.Payloads provided by the platform support Windows, Linux and Python-based implementations and are hosted within the Interplanetary File System (IPFS), making them resilient to content moderation or law enforcement intervention.Since its initial release, we've observed malware samples in the wild leveraging it to facilitate remote access and cryptocurrency mining.What is "Dark Utilities?"In early 2022, a new C2 platform called "Dark Utilities" was established, offering a variety of services such as remote system access, DDoS capabilities and cryptocurrency mining. The operators of the service also established Discord and Telegram communities where they provide technical support and assistance for customers on the platform. By Edmund Brumaghin, Azim Khodjibaev and Matt Thaxton, with contributions from Arnaud Zobec.Executive SummaryDark Utilities, released in early 2022, is a platform that provides full-featured C2 capabilities to adversaries.It is marketed as a means to enable remote access, command execution, distributed denial-of-service (DDoS) attacks and cryptocurrency mining operations on infected systems.Payloads provided by the platform support Windows, Linux and Python-based implementations and are hosted within the Interplanetary File System (IPFS), making them resilient to content moderation or law enforcement intervention.Since its initial release, we've observed malware samples in the wild leveraging it to facilitate remote access and cryptocurrency mining.What is "Dark Utilities?"In early 2022, a new C2 platform called "Dark Utilities" was established, offering a variety of services such as remote system access, DDoS capabilities and cryptocurrency mining. The operators of the service also established Discord and Telegram communities where they provide technical support and assistance for customers on the platform.  Dark Utilities provides payloads consisting of code that is executed on victim systems, allowing them to be registered with the service and establish a command and control (C2) communications channel. The platform currently supports Windows, Linux and Python-based payloads, allowing adversaries to target multiple architectures without requiring significant development resources. During our analysis, we observed efforts underway to expand OS and system architecture support as the platform continues to see ongoing develo Dark Utilities provides payloads consisting of code that is executed on victim systems, allowing them to be registered with the service and establish a command and control (C2) communications channel. The platform currently supports Windows, Linux and Python-based payloads, allowing adversaries to target multiple architectures without requiring significant development resources. During our analysis, we observed efforts underway to expand OS and system architecture support as the platform continues to see ongoing develo |
Spam Malware Hack Tool Threat Guideline | APT 19 |
To see everything:
Our RSS (filtrered)
