What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2022-10-17 10:00:00 | Stories from the SOC: Feeling so foolish – SocGholish drive by compromise (lien direct) | Executive summary:
SocGholish, also known as FakeUpdate, is a JavaScript framework leveraged in social engineering drive by compromises that has been a thorn in cybersecurity professionals’ and organizations’ sides for at least 5 years now. Upon visiting a compromised website, users are redirected to a page for a browser update and a zip archive file containing a malicious JavaScript file is downloaded and unfortunately often opened and executed by the fooled end user.
An AT&T Managed Extended Detection and Response (MXDR) client with Managed Endpoint Security (MES) powered by SentinelOne (S1) received an alert regarding the detection and mitigation of one of these JavaScript files. The MXDR Threat Hunter assigned to this client walked them through the activity resulting from the execution of the malicious file, as well as provide additional guidance on containment and remediation of the host involved in the incident.
Investigation
Upon detection of the follow up activity of the malicious file executed by the end user, S1 created an Incident within the S1 portal. This in turn creates an Alarm within the USM Anywhere platform, where the MXDR SOC team works, reviews, and creates Investigations for client notification as necessary. Since this activity was observed all within S1, this analysis will be out of there.
 The best way to start looking into a S1 event is to go to the Storyline of the Incident within Deep Visibility.
The best way to start looking into a S1 event is to go to the Storyline of the Incident within Deep Visibility.
 Once we have all the events related to the Incident, we can also create a new Deep Visibility search for all activity related to the affected host from about an hour before right up to the first event for the incident. This will let us try to see what happened on the host that lead to the execution of the malicious JavaScript file.
Reviewing the events from both the overall logs on the host and the events related to the Storyline, we can build out a rough timeline of events. Note there are close to 15k events on the host in the timeframe and 448 events in total in the Storyline; I’m just going over the interesting findings for expediency sake.
12:07:08 The user is surfing on Chrome and using Google search to look up electricity construction related companies; we see two sites being visited, with both sites being powered by WordPress. The SocGholish campaign works by injecting malicious code into vulnerable WordPress websites. While I was unable to find the injected code within the potentially compromised sites, I see that one of the banners on the page contains spam messages; while there are no links or anything specifically malicious with this, it lets us know that this site is unsafe to a degree.
Once we have all the events related to the Incident, we can also create a new Deep Visibility search for all activity related to the affected host from about an hour before right up to the first event for the incident. This will let us try to see what happened on the host that lead to the execution of the malicious JavaScript file.
Reviewing the events from both the overall logs on the host and the events related to the Storyline, we can build out a rough timeline of events. Note there are close to 15k events on the host in the timeframe and 448 events in total in the Storyline; I’m just going over the interesting findings for expediency sake.
12:07:08 The user is surfing on Chrome and using Google search to look up electricity construction related companies; we see two sites being visited, with both sites being powered by WordPress. The SocGholish campaign works by injecting malicious code into vulnerable WordPress websites. While I was unable to find the injected code within the potentially compromised sites, I see that one of the banners on the page contains spam messages; while there are no links or anything specifically malicious with this, it lets us know that this site is unsafe to a degree.
 12:10:46 The user was redirected to a clean[.]godmessagedme[.]com for the initial download. It likely would have looked like this:
12:10:46 The user was redirected to a clean[.]godmessagedme[.]com for the initial download. It likely would have looked like this:
 We can assume the URI for the request looks like the /report as seen in VirusTotal and described in open-source intelligence (OSI). Note that the subdomain “clean” has a different resolution than the root domain; this is domain shadowing performed by the attackers by creating a new A-record within the DNS settings of the legitimate domain:
We can assume the URI for the request looks like the /report as seen in VirusTotal and described in open-source intelligence (OSI). Note that the subdomain “clean” has a different resolution than the root domain; this is domain shadowing performed by the attackers by creating a new A-record within the DNS settings of the legitimate domain:

 12:12:19 Chrome creates on disk: “C:\Users\[redacted]\Downloads\Сhrome.Updаte.zip”.
12:13:11 User has opened the zip
12:12:19 Chrome creates on disk: “C:\Users\[redacted]\Downloads\Сhrome.Updаte.zip”.
12:13:11 User has opened the zip |
Spam Threat Guideline | |||
| 2022-10-14 01:24:52 | Guloader Spam Indiscriminately Sent to State Elections Board (lien direct) | Recently, the United States Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) issued a joint public service announcement - Foreign Actors Likely to Use Information Manipulation Tactics for 2022 Midterm Elections (9I-100622-PSA). The focus of the PSA was to inform the public of the potential manipulation of the midterm election cycle in the United States by foreign agents using social engineering and social media disinformation tactics to influence voters and to sow discord as well.Around the same time of the announcement, FortiGuard Labs observed a Guloader campaign being sent to an elections body in the United States. Although there is no sign that they were specifically targeted, we want to highlight what's involved in these attacks given the 2022 U.S. midterm elections in November. The infection vectors are simple malicious spam that do not rely on exploiting a vulnerability or macros.FortiGuard Labs found a campaign from a purported industrial equipment manufacturer in Indonesia, containing a malicious ISO attachment. Figure 1. Email used in this spam campaignISO email attachments are often used to avoid detection by security solutions. Clicking on the attachment triggers the ISO file. Once mounted, an EXE file-a GuLoader malware variant-becomes visible. The victim then needs to run the "Requisition order-PT. LFC Teknologi,pdf.exe" executable manually to start the infection routine. Figure 2. GuLoader file in the mounted ISO fileThis file is digitally signed via an untrusted root certificate, seen below.Figure 3. Digital signature information for "Requisition order-PT. LFC Teknologi,pdf.exe".The GuLoader payload is a so-called first stage malware that has been seen in the wild for the past few years. It is designed to deliver a second stage payload that can be tailored to the attacker's liking. Some reported second stage payloads include Remote Access Trojans (RATs), infostealers, and ransomware.This particular GuLoader variant reaches out to 195[.]178[.]120[.]184/sMHxAbMCsvl181[.]java, which was no longer available at the time of the investigation. However, we believe the java file to either be a decryption key or a payload download. Another, GuLoader sample (SHA2: 46f8a8cec6bb92708a185cfea876ea1ae0cdef2321dc50f140f23c7cc650b65e) was submitted to VirusTotal on September 14th. This sample accesses 195[.]178[.]120[.]184/uFLBwGvx55[.]java and available OSINT suggests that the payload is the Azorult infostealer. Azorult is capable of exfiltrating data such as passwords from browsers, email, and FTP servers, and harvesting files with extensions specified by an attacker. It can also collect machine information such as user and computer name, installed programs, Windows version, and installed programs. Such stolen information can be a precursor to future attacks.Based on the traits of the GuLoader sample, FortiGuard Labs tracked down additional files involved in the same malicious spam campaign. The attacker mostly used IMG and ISO attachments along with file names in English, German, Spanish, Turkish, and Chinese. Taking a look at VirusTotal, submissions of the attachments are from the US, Czechia, China, Turkey, Germany, UK, Israel, Ireland, and Hungary. The GuLoader variant was also submitted to VirusTotal from the US, Bulgaria, Canada, China, the United Arab Emirates, and Korea. The email delivered to a board of elections in the United States was sent to a publicly available webmaster address. This indicates that the attacker sent these malicious emails to as many recipients as possible in the hope that someone would manually execute the malware. This is the first step to a potential compromise of machines related to the elections board of this United States state, and will allow the attacker to obtain a foothold to obtain unauthorized data for dissemination or simply various angles of disruption (ransomware, wiping, extortion, etc.) and even worse, perhaps sell access to an adversary for financial gain.Fortinet ProtectionsFortinet customers are already protected fr | Spam Malware Vulnerability | |||
| 2022-10-12 10:00:00 | 12 Essential ways to improve your website security (lien direct) | This blog was written by an independent guest blogger. In today's digital age, a business website is essential for success. Not only does it provide potential customers with information about your products or services, but it also allows you to connect and engage with them directly. However, simply having a website is not enough. To ensure that your site is effective and safe, you need to make sure that it has all the necessary security features. In this article, we will discuss twelve security features that every business website must have. 1. Auto-update enabled for plugins and software One of the simplest but most effective security measures you can take, especially if you’re looking to protect your WordPress site, is to ensure that all your plugins and software are up-to-date. Outdated software is one of the most common ways that attackers gain access to websites. By keeping everything up to date, you can help to prevent vulnerabilities from being exploited. You can usually enable auto-updates for most plugins and software from within their setting's menus. For WordPress sites, there is also a plugin called Easy Updates Manager that can help you to keep everything up to date with ease. 2. A strong password policy A strong password policy is the first step to protecting your website from malicious actors. By requiring strong and unique passwords, you can make it significantly more difficult for attackers to gain access to your site. You need to ensure that your website's backend is well protected and that only authorized users have access. To do this, you should consider using a password manager to generate and store strong passwords for your site. You definitely should not be using the same password for multiple sites. 3. Two-factor authentication Two-factor authentication (2FA) is an important security measure that you should consider implementing for your website. 2FA adds an extra layer of security by requiring users to provide two pieces of information before they can access your site. This could include a password and a one-time code that is generated by an app on your phone. 2FA can help to prevent attackers from gaining access to your site, even if they have your password. 4. A secure socket layer (SSL) certificate An SSL certificate is a must-have for any website that wants to protect their users' information. SSL encrypts the communications between your website and your users' web browsers. This means that even if an attacker was able to intercept the communication, they would not be able to read it. SSL also provides authentication, which means you can be sure that your users are communicating with the intended website and not a fake site set up by an attacker. Increasingly, having things like HTTPS and an SSL certificate are part of Google's ranking metrics and will help your website's SEO. If you aren't making an effort to protect your visitors and users (the people who give you their sensitive credit card information), they may take their business elsewhere. 5. A web application firewall (WAF) A web application firewall (WAF) is a piece of software that sits between your website and the internet. It filters traffic to your site and blocks any requests that it considers to be malicious. WAFs can be very effective at stopping attacks such as SQL injection and cross-site scripting (XSS). 6. Intrusion detection and prevention systems (IDPS) Intrusion detection and prevention systems (IDPS) are designed to | Spam Malware Threat | ★★★★ | ||
| 2022-10-11 19:22:42 | Google Pixel 7 and Pixel 7 Pro: The next evolution in mobile security (lien direct) | Dave Kleidermacher, Jesse Seed, Brandon Barbello, Sherif Hanna, Eugene Liderman, Android, Pixel, and Silicon Security Teams Every day, billions of people around the world trust Google products to enrich their lives and provide helpful features – across mobile devices, smart home devices, health and fitness devices, and more. We keep more people safe online than anyone else in the world, with products that are secure by default, private by design and that put you in control. As our advancements in knowledge and computing grow to deliver more help across contexts, locations and languages, our unwavering commitment to protecting your information remains. That's why Pixel phones are designed from the ground up to help protect you and your sensitive data while keeping you in control. We're taking our industry-leading approach to security and privacy to the next level with Google Pixel 7 and Pixel 7 Pro, our most secure and private phones yet, which were recently recognized as the highest rated for security when tested among other smartphones by a third-party global research firm.1 Pixel phones also get better every few months with Feature Drops that provide the latest product updates, tips and tricks from Google. And Pixel 7 and Pixel 7 Pro users will receive at least five years of security updates2, so your Pixel gets even more secure over time. Your protection, built into PixelYour digital life and most sensitive information lives on your phone: financial information, passwords, personal data, photos – you name it. With Google Tensor G2 and our custom Titan M2 security chip, Pixel 7 and Pixel 7 Pro have multiple layers of hardware security to help keep you and your personal information safe. We take a comprehensive, end-to-end approach to security with verifiable protections at each layer - the network, application, operating system and multiple layers on the silicon itself. If you use Pixel for your business, this approach helps protect your company data, too.  Google Tensor G2 is Pixel's newest powerful processor custom built with Google AI, and makes Pixel 7 faster, more efficient and secure3. Every aspect of Tensor G2 was designed to improve Pixel's performance and efficiency for great battery life, amazing photos and videos. Tensor's built-in security core works with our Titan M2 security chip to keep your personal information, PINs and passwords safe. Titan family chips are also used to protect Google Cloud data centers and Chromebooks, so the same hardware that protects Google servers also secures your sensitive information stored on Pixel. And, in a first for Google, Titan M2 hardware has now been certified under Common Criteria PP0084: the international gold standard for hardware security components also used for identity, SIM cards, and bankcard security chips. Google Tensor G2 is Pixel's newest powerful processor custom built with Google AI, and makes Pixel 7 faster, more efficient and secure3. Every aspect of Tensor G2 was designed to improve Pixel's performance and efficiency for great battery life, amazing photos and videos. Tensor's built-in security core works with our Titan M2 security chip to keep your personal information, PINs and passwords safe. Titan family chips are also used to protect Google Cloud data centers and Chromebooks, so the same hardware that protects Google servers also secures your sensitive information stored on Pixel. And, in a first for Google, Titan M2 hardware has now been certified under Common Criteria PP0084: the international gold standard for hardware security components also used for identity, SIM cards, and bankcard security chips. |
Spam Malware Vulnerability Guideline Industrial | APT 40 | ||
| 2022-10-07 09:10:00 | Meta Sues Chinese Devs Over WhatsApp Malware Plot (lien direct) | Fake apps led to account takeovers and spam campaigns | Spam Malware | |||
| 2022-09-28 13:00:00 | FCC moves to block robotexts (lien direct) | >Categories: NewsCategories: ScamsThe Federal Communications Commission wants mobile carriers to block spam texts at the network level. (Read more...) | Spam | |||
| 2022-09-28 03:00:00 | Your Guide to the Latest Email Fraud and Identity Deception Trends (lien direct) | >There's a high chance that you or someone you know has been impacted by email fraud or identity theft. At the very least, you've likely received a variety of spam emails and text messages asking to provide a payment or confirm your identity. The good news is that cybersecurity protection is constantly evolving and improving, […]… Read More | Spam | |||
| 2022-09-27 16:51:00 | Anomali Cyber Watch: Sandworm Uses HTML Smuggling and Commodity RATs, BlackCat Ransomware Adds New Features, Domain Shadowing Is Rarely Detected, and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, China, Fraud, Inbound connectors, Phishing, Ransomware, Russia, and Ukraine. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
A Multimillion Dollar Global Online Credit Card Scam Uncovered
(published: September 23, 2022)
ReasonLabs researchers discovered a large network of fake dating and customer support websites involved in credit card fraud operations. The threat actor builds a basic website, registers it with a payment processor (RocketGate), buys credit card data from other threat actors, and subscribes victims to monthly charging plans. The US was the most targeted, and a lower number of sites were targeting France. To pass the processor checks and lower the number of charge-backs the actor avoided test charges, used a generic billing name, charged only a small, typical for the industry payment, and hired a legitimate support center provider, providing effortless canceling and returning of the payment.
Analyst Comment: Users are advised to regularly check their bank statements and dispute fraudulent charges. Researchers can identify a fraudulent website by overwhelming dominance of direct-traffic visitors from a single country, small network of fake profiles, and physical address typed on a picture to avoid indexing.
Tags: Credit card, Fraud, Scam, Chargeback, Payment processor, Fake dating site, USA, target-country:US, France, target-country:FR, target-sector:Finance NAICS 52
Malicious OAuth Applications Used to Compromise Email Servers and Spread Spam
(published: September 22, 2022)
Microsoft researchers described a relatively stealthy abuse of a compromised Exchange server used to send fraud spam emails. After using valid credentials to get access, the actor deployed a malicious OAuth application, gave it admin privileges and used it to change Exchange settings. The first modification created a new inbound connector allowing mails from certain actor IPs to flow through the victim’s Exchange server and look like they originated from the compromised Exchange domain. Second, 12 new transport rules were set to delete certain anti-spam email headers.
Analyst Comment: If you manage an Exchange server, strengthen account credentials and enable multifactor authentication. Investigate if receiving alerts regarding suspicious email sending and removal of antispam header.
MITRE ATT&CK: [MITRE ATT&CK] Valid Accounts - T1078 | [MITRE ATT&CK] Indicator Removal on Host - T1070
Tags: Exchange, Microsoft, PowerShell, Inbound connector, Transport rule, Fraud, Spam
NFT Malware Gets New Evasion Abilities
(published: September 22, 2022)
Morphisec researchers describe a campaign targeting non-fungible token (NFT) communities since November 2020. A malicious link is being sent via Discord or other forum private phishing message related to an NFT or financial opportunity. If the user
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
A Multimillion Dollar Global Online Credit Card Scam Uncovered
(published: September 23, 2022)
ReasonLabs researchers discovered a large network of fake dating and customer support websites involved in credit card fraud operations. The threat actor builds a basic website, registers it with a payment processor (RocketGate), buys credit card data from other threat actors, and subscribes victims to monthly charging plans. The US was the most targeted, and a lower number of sites were targeting France. To pass the processor checks and lower the number of charge-backs the actor avoided test charges, used a generic billing name, charged only a small, typical for the industry payment, and hired a legitimate support center provider, providing effortless canceling and returning of the payment.
Analyst Comment: Users are advised to regularly check their bank statements and dispute fraudulent charges. Researchers can identify a fraudulent website by overwhelming dominance of direct-traffic visitors from a single country, small network of fake profiles, and physical address typed on a picture to avoid indexing.
Tags: Credit card, Fraud, Scam, Chargeback, Payment processor, Fake dating site, USA, target-country:US, France, target-country:FR, target-sector:Finance NAICS 52
Malicious OAuth Applications Used to Compromise Email Servers and Spread Spam
(published: September 22, 2022)
Microsoft researchers described a relatively stealthy abuse of a compromised Exchange server used to send fraud spam emails. After using valid credentials to get access, the actor deployed a malicious OAuth application, gave it admin privileges and used it to change Exchange settings. The first modification created a new inbound connector allowing mails from certain actor IPs to flow through the victim’s Exchange server and look like they originated from the compromised Exchange domain. Second, 12 new transport rules were set to delete certain anti-spam email headers.
Analyst Comment: If you manage an Exchange server, strengthen account credentials and enable multifactor authentication. Investigate if receiving alerts regarding suspicious email sending and removal of antispam header.
MITRE ATT&CK: [MITRE ATT&CK] Valid Accounts - T1078 | [MITRE ATT&CK] Indicator Removal on Host - T1070
Tags: Exchange, Microsoft, PowerShell, Inbound connector, Transport rule, Fraud, Spam
NFT Malware Gets New Evasion Abilities
(published: September 22, 2022)
Morphisec researchers describe a campaign targeting non-fungible token (NFT) communities since November 2020. A malicious link is being sent via Discord or other forum private phishing message related to an NFT or financial opportunity. If the user |
Ransomware Spam Malware Tool Threat | |||
| 2022-09-27 15:40:27 | Malicious Oauth app enables attackers to send spam through corporate cloud tenants (lien direct) | >Microsoft investigated a new kind of attack where malicious OAuth applications were deployed on compromised cloud tenants before being used for mass spamming. | Spam | |||
| 2022-09-27 11:00:00 | Exchange servers abused for spam through malicious OAuth applications (lien direct) | >Categories: NewsTags: Exchange Tags: OAuth Tags: spam Tags: MFA Tags: Transport rules Tags: connector Threat actors have been using malicious OAuth applications to abuse Microsoft Exchange servers for their spam campaign. (Read more...) | Spam | |||
| 2022-09-23 16:00:00 | Hackers Deploy Malicious OAuth Apps to Compromise Email Servers, Spread Spam (lien direct) | The spam emails were sent to trick recipients into signing up for fake paid subscriptions | Spam | |||
| 2022-09-23 15:22:53 | Cyberattackers Compromise Microsoft Exchange Servers Via Malicious OAuth Apps (lien direct) | Cybercriminals took control of enterprise Exchange Servers to spread large amounts of spam aimed at signing people up for bogus subscriptions. | Spam | |||
| 2022-09-23 08:00:13 | Mass email campaign with a pinch of targeted spam (lien direct) | Mass spam mailing posing as customer email delivers the Agent Tesla stealer disguised as a document to corporate users. | Spam | |||
| 2022-09-07 09:40:00 | UK Privacy Regulator Fines Halfords for Spam Deluge (lien direct) | Retailer sent half a million emails to people without their consent | Spam | |||
| 2022-08-29 18:15:08 | CVE-2022-1663 (lien direct) | The Stop Spam Comments WordPress plugin through 0.2.1.2 does not properly generate the Javascript access token for preventing abuse of comment section, allowing threat authors to easily collect the value and add it to the request. | Spam Threat | |||
| 2022-08-26 05:31:39 | Paypal Phishing/Coinbase in One Image, (Fri, Aug 26th) (lien direct) | There is a current wave of Paypal phishing emails ongoing. I already received a few of them. This time, the spam is based on a simple JPEG image. The subject has always this format (with the date changing): | Spam | |||
| 2022-08-23 00:00:00 | Emotet Resurgence: Cross-Industry Campaign Analysis (lien direct) | This blog aims to provide background and technical discoveries from the recent Emotet resurgence detected in early 2022 across multiple Darktrace client environments in multiple regions and industries. Predominantly in March and April 2022, Darktrace DETECT provided visibility over network activities associated with Emotet compromises using initial staged payload downloads involving algorithmically generated DLLs and subsequent outbound command and control, as well as spam activities. | Spam | ★★★★ | ||
| 2022-08-16 09:30:17 | How a spoofed email passed the SPF check and landed in my inbox (lien direct) | >The Sender Policy Framework can't help prevent spam and phishing if you allow billions of IP addresses to send as your domain | Spam | |||
| 2022-08-15 11:21:39 | CVE-2022-35958 (lien direct) | Discourse is a 100% open source discussion platform. A malicious user can use the invitation system to spam arbitrary email addresses by sending them invitation emails in some cases. This issue is patched in the latest stable, beta and tests-passed versions of Discourse. There are currently no known workarounds. | Spam | ★★★ | ||
| 2022-08-08 15:11:18 | LogoKit update – The phishing kit leveraging Open Redirect Vulnerabilities (lien direct) | >LogoKit – Threat actors leveraging Open Redirect Vulnerabilities popular in online services and apps to bypass spam filters in phishing campaigns. Resecurity, Inc. (USA), a Los Angeles-based cybersecurity company providing managed threat detection and response for Fortune 500’s, identified threat actors leveraging Open Redirect Vulnerabilities popular in online services and apps to bypass spam filters […] | Spam Threat | |||
| 2022-08-08 14:15:10 | CVE-2022-35488 (lien direct) | In Zammad 5.2.0, an attacker could manipulate the rate limiting in the 'forgot password' feature of Zammad, and thereby send many requests for a known account to cause Denial Of Service by many generated emails which would also spam the victim. | Spam | |||
| 2022-08-05 12:39:42 | FCC warns of steep rise in phishing over SMS (lien direct) | >Smishing attacks, or phishing attempts via SMS, are on the rise, and Americans are fighting off billions of spam messages each month. | Spam | |||
| 2022-08-04 08:00:13 | Attackers leveraging Dark Utilities "C2aaS" platform in malware campaigns (lien direct) |  By Edmund Brumaghin, Azim Khodjibaev and Matt Thaxton, with contributions from Arnaud Zobec.Executive SummaryDark Utilities, released in early 2022, is a platform that provides full-featured C2 capabilities to adversaries.It is marketed as a means to enable remote access, command execution, distributed denial-of-service (DDoS) attacks and cryptocurrency mining operations on infected systems.Payloads provided by the platform support Windows, Linux and Python-based implementations and are hosted within the Interplanetary File System (IPFS), making them resilient to content moderation or law enforcement intervention.Since its initial release, we've observed malware samples in the wild leveraging it to facilitate remote access and cryptocurrency mining.What is "Dark Utilities?"In early 2022, a new C2 platform called "Dark Utilities" was established, offering a variety of services such as remote system access, DDoS capabilities and cryptocurrency mining. The operators of the service also established Discord and Telegram communities where they provide technical support and assistance for customers on the platform. By Edmund Brumaghin, Azim Khodjibaev and Matt Thaxton, with contributions from Arnaud Zobec.Executive SummaryDark Utilities, released in early 2022, is a platform that provides full-featured C2 capabilities to adversaries.It is marketed as a means to enable remote access, command execution, distributed denial-of-service (DDoS) attacks and cryptocurrency mining operations on infected systems.Payloads provided by the platform support Windows, Linux and Python-based implementations and are hosted within the Interplanetary File System (IPFS), making them resilient to content moderation or law enforcement intervention.Since its initial release, we've observed malware samples in the wild leveraging it to facilitate remote access and cryptocurrency mining.What is "Dark Utilities?"In early 2022, a new C2 platform called "Dark Utilities" was established, offering a variety of services such as remote system access, DDoS capabilities and cryptocurrency mining. The operators of the service also established Discord and Telegram communities where they provide technical support and assistance for customers on the platform.  Dark Utilities provides payloads consisting of code that is executed on victim systems, allowing them to be registered with the service and establish a command and control (C2) communications channel. The platform currently supports Windows, Linux and Python-based payloads, allowing adversaries to target multiple architectures without requiring significant development resources. During our analysis, we observed efforts underway to expand OS and system architecture support as the platform continues to see ongoing develo Dark Utilities provides payloads consisting of code that is executed on victim systems, allowing them to be registered with the service and establish a command and control (C2) communications channel. The platform currently supports Windows, Linux and Python-based payloads, allowing adversaries to target multiple architectures without requiring significant development resources. During our analysis, we observed efforts underway to expand OS and system architecture support as the platform continues to see ongoing develo |
Spam Malware Hack Tool Threat Guideline | APT 19 | ||
| 2022-08-01 20:15:08 | CVE-2022-31184 (lien direct) | Discourse is the an open source discussion platform. In affected versions an email activation route can be abused to send mass spam emails. A fix has been included in the latest stable, beta and tests-passed versions of Discourse which rate limits emails. Users are advised to upgrade. Users unable to upgrade should manually rate limit email. | Spam | ★★★★★ | ||
| 2022-07-26 10:11:15 | Quarterly Report: Incident Response Trends in Q2 2022 (lien direct) | Commodity malware usage surpasses ransomware by narrow margin  By Caitlin Huey.For the first time in more than a year, ransomware was not the top threat Cisco Talos Incident Response (CTIR) responded to this quarter, as commodity malware surpassed ransomware by a narrow margin. This is likely due to several factors, including the closure of several ransomware groups, whether it be of their own volition or the actions of global law enforcement agencies and governments. By Caitlin Huey.For the first time in more than a year, ransomware was not the top threat Cisco Talos Incident Response (CTIR) responded to this quarter, as commodity malware surpassed ransomware by a narrow margin. This is likely due to several factors, including the closure of several ransomware groups, whether it be of their own volition or the actions of global law enforcement agencies and governments. 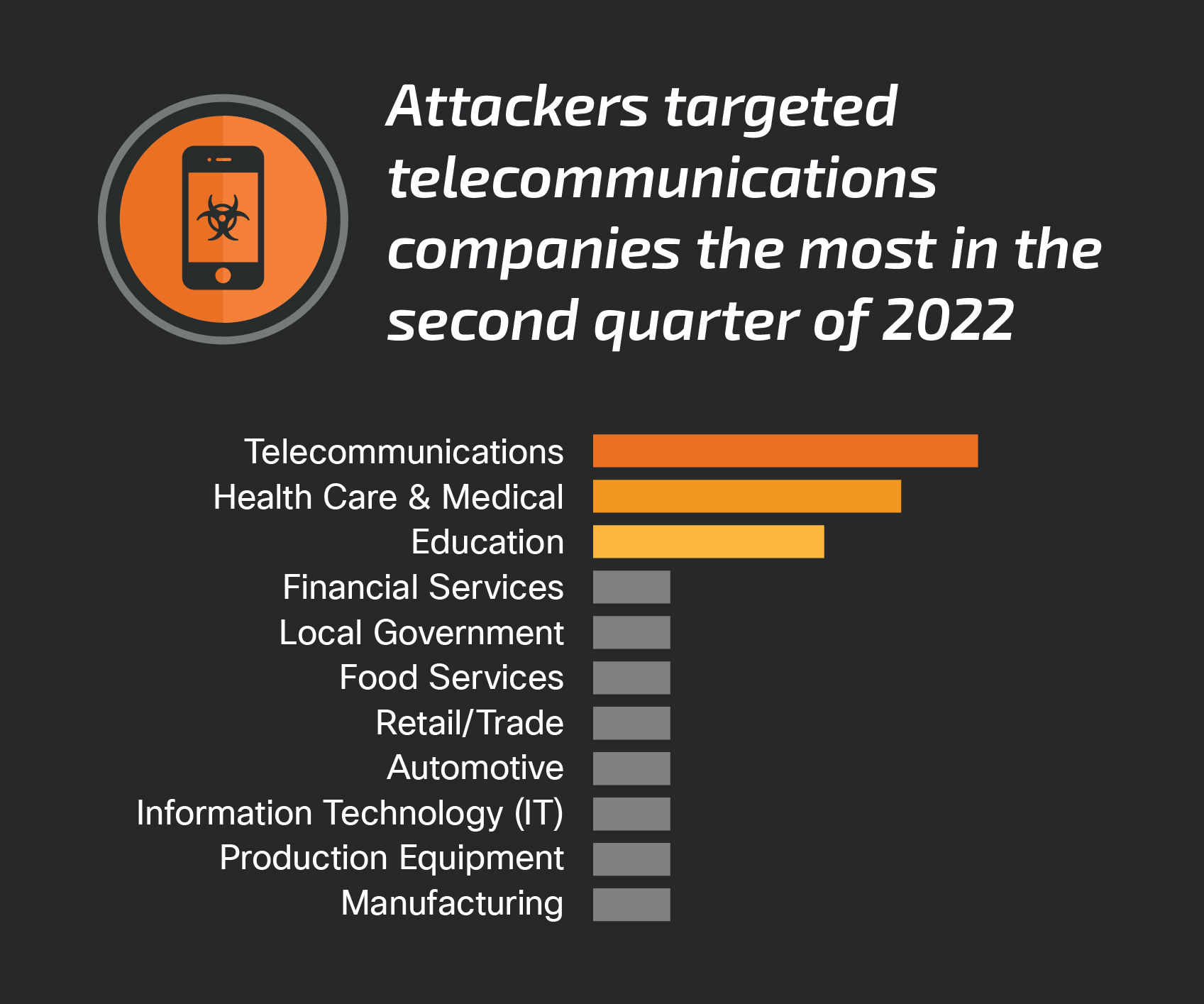 Commodity malwareThis quarter saw a notable increase in commodity malware threats compared to previous quarters. Commodity Commodity malwareThis quarter saw a notable increase in commodity malware threats compared to previous quarters. Commodity |
Ransomware Spam Malware Threat | |||
| 2022-07-19 15:13:21 | Who on earth would be trying to promote EC-Council University via comment spam on my website? (lien direct) | I can't tell you not to seek ethical hacking certification from EC-Council. But I can suggest that if you are looking for an online university to boost your cybersecurity career, you don't settle for an outfit that has proven itself to be of questionable ethics and utterly clueless. | Spam | ★★★ | ||
| 2022-07-19 13:08:17 | " Stranger scams " : des cybercriminels vident le portefeuille des fans de la série fantastique à succès (lien direct) | Début juillet, la quatrième saison de la série acclamée Stranger Things a été diffusée. Malgré une interruption de trois ans liée à la pandémie, la série fortement attendue a battu de nouveau des records d'audience en streaming. Malheureusement, l'impatience des fans, avides de visionner sans plus tarder les nouveaux épisodes, a été exploitée de diverses manières par des fraudeurs. En effet, les chercheurs de Kaspersky ont découvert de nombreux exemples d'emails de spam et de pages de phishing conçus pour (...) - Malwares | Spam | |||
| 2022-07-07 08:10:19 | Alert (AA22-181A) #StopRansomware: MedusaLocker (lien direct) | FortiGuard Labs is aware that a joint Cybersecurity Advisory (CSA) on MedusaLocker ransomware was released by the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), the Department of the Treasury, and the Financial Crimes Enforcement Network (FinCEN). MedusaLocker infection typically occurs through Remote Desktop Protocol (RDP) compromise, propagates MedusaLocker throughout the network, and uses AES-256 encryption to encrypt files.Why is this Significant?This is significant as the joint Cybersecurity Advisory (CSA) is the latest #StopRansomware advisory released by the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), the Department of the Treasury, and the Financial Crimes Enforcement Network (FinCEN), which provides observed tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) to help organizations protect against ransomware.What is MedusaLocker Ransomware?MedusaLocker is a ransomware that encrypts files in the compromised machines with the AES-256 encryption algorithm and demands victims to pay a ransom in order to recover the affected files. According to the advisory, MedusaLocker primarily takes advantage of an insecure RDP configuration as an initial infection vector, however email spam and malicious attachments are also used.The advisory also states that MedusaLocker ransomware uses multiple infection processes:Uses a batch file to execute PowerShell script, which propagates the ransomware throughout the network. Restarts the LanmanWorkstation service, which allows registry edits to take effect. Kills the processes belonging to well-known security, accounting, and forensic software. Restarts the machine in safe mode.Encrypts files in the compromised machines with the AES-256 encryption algorithmRuns every 60 seconds, encrypting all files except those critical to the functionality of the victim's machine and those that have the designated encrypted file extension. Establishes persistence by copying an executable (svhost.exe or svhostt.exe) to the %APPDATA%\Roaming directory and scheduling a task to run the ransomware every 15 minutes. Attempts to prevent standard recovery techniques by deleting local backups, disabling startup recovery options, and deleting shadow copies.Leaves a ransom note into every folder containing instruction on how to reach out to the attacker either via MedusaLocker's Tor sites or emails.The following is a list of known file extensions that MedusaLocker adds to the encrypts files:.1btc.bec.cn.datalock.deadfilesgr.decrypme.encrypted.faratak.FartingGiraffeAttacks.fileslock.fileslocked.jpz.nz.key1.lock.lockdata7.lockfiles.lockfilesUS.marlock01.marlock02.marlock08.marlock11.marlock13.marlock25.marlock6.marlock011.matlock20.mylock.newware.NET1.NZ.perfection.Readinstruction.READINSTRUCTION.ReadInstructions.readinstructions.rs.skynet.stopflies.tyco.tyco.uslockhh.uslockhh.zoomzoomn.exent_lock20.networkmaze.VinDizelPux.EG.support.deadfiles.readtheinstructions.lr.divsouth.lockfilesCO.lockfilesKR.EMPg296LCKThe following is a list of known MedusaLocker's ransom notes:! _HOW_RECOVERY_FILES _!. HTML!!!HOW_TO_DECRYPT!!!how_to_ recover_data.html HOW_TO_OPEN_FILES.htmlHOW_TO_RECOVER_DATA.htmlhow_to_recover_data.html.marlock01How_to_recovery.txtinstructions.html READINSTRUCTION.html readinstructions.html readme_to_recover_filesrecovery_instruction.htmlrecovery_instructions.html What is the Status of Coverage?FortiGuard Labs provides the following AV coverage against known samples of MedusaLocker ransomware:W32/MedusaLocker.0FEB!trW32/MedusaLocker.9106!tr.ransomW32/MedusaLocker.C!tr.ransomW32/Ransom_Win32_MEDUSALOCKER.SMTHW32/Ransom_Win32_MEDUSALOCKER.SMTH!trW32/Ransom_Win32_MEDUSALOCKER.SMTH!tr.ransomW32/DelShad.BMQ!tr.ransomW32/Filecoder.FV!trW32/Filecoder.NSF!tr.ransomW32/Filecoder.NYA!tr.ransomW32/Generic.AC.171!trW32/Generik.DGWKQJO!trW32/Kryptik.HFBI!trW32/PossibleThreatW32/Ransomware.GUN!trW32/Zudochka.VHO!tr.ransomW64/Filecoder.DF!tr.ransomPossibleThreat.FAIRiskware/DelShad | Ransomware Spam | |||
| 2022-07-01 05:48:14 | I Don\'t Want to Receive Any Unnecessary Information! (lien direct) | According to Section 50 of the ACT ON PROMOTION OF INFORMATION AND COMMUNICATIONS NETWORK UTILIZATION AND INFORMATION PROTECTION, anyone who wishes to send promotional information for commercial purposes via electronic transmission media must receive explicit consent of the receiver in advance. Spam refers to promotional information sent or posted for commercial purposes through communications networks although it is unwanted by the user. This post will present the analysis of a program that sends messages automatically on a particular web portal.... | Spam | |||
| 2022-06-28 19:11:00 | Anomali Cyber Watch: API Hammering Confuses Sandboxes, Pirate Panda Wrote in Nim, Magecart Obfuscates Variable Names, and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: API hammering, APT, China, Phishing, Ransomware, Russia, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Lockbit Ransomware Disguised as Copyright Claim E-mail Being Distributed
(published: June 24, 2022)
ASEC researchers have released their analysis of a recent phishing campaign, active since February 2022. The campaign aims to infect users with Lockbit ransomware, using the pretense of a copyright claim as the phishing lure. The phishing email directs the recipient to open the attached zip file which contains a pdf of the infringed material. In reality, the pdf is a disguised NSIS executable which downloads and installs Lockbit. The ransomware is installed onto the desktop for persistence through desktop change or reboot. Prior to data encryption, Lockbit will delete the volume shadow copy to prevent data recovery, in addition to terminating a variety of services and processes to avoid detection.
Analyst Comment: Never click on suspicious attachments or run any executables from suspicious emails. Copyright infringement emails are a common phishing lure. Such emails will be straight forward to rectify if legitimate. If a copyright email is attempting to coerce you into opening attachments, such emails should be treated with extreme caution.
MITRE ATT&CK: [MITRE ATT&CK] Phishing - T1566 | [MITRE ATT&CK] Data Encrypted for Impact - T1486 | [MITRE ATT&CK] Impair Defenses - T1562
Tags: malware:Phishing, malware:Lockbit, Lockbit, Copyright, Ransomware
There is More Than One Way To Sleep: Deep Dive into the Implementations of API Hammering by Various Malware Families
(published: June 24, 2022)
Researchers at Palo Alto Networks have released their analysis of new BazarLoader and Zloader samples that utilize API Hammering as a technique to evade sandbox detection. API Hammering makes use of a large volume of Windows API calls to delay the execution of malicious activity to trick sandboxes into thinking the malware is benign. Whilst BazarLoader has utilized the technique in the past, this new variant creates large loops of benign API using a new process. Encoded registry keys within the malware are used for the calls and the large loop count is created from the offset of the first null byte of the first file in System32 directory. Zloader uses a different form of API Hammering to evade sandbox detection. Hardcoded within Zloader are four large functions with many smaller functions within. Each function makes an input/output (I/O) call to mimic the behavior of many legitimate processes.
Analyst Comment: Defense in depth is the best defense against sophisticated malware. The Anomali Platform can assist in detection of malware and Match anomalous activity from all telemetry sources to provide the complete picture of adversary activity within your network.
MITRE ATT&CK: [MITRE ATT&CK] Virtualization/Sandbox Evasion - T1497
Tags: malware:BazarLoad
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Lockbit Ransomware Disguised as Copyright Claim E-mail Being Distributed
(published: June 24, 2022)
ASEC researchers have released their analysis of a recent phishing campaign, active since February 2022. The campaign aims to infect users with Lockbit ransomware, using the pretense of a copyright claim as the phishing lure. The phishing email directs the recipient to open the attached zip file which contains a pdf of the infringed material. In reality, the pdf is a disguised NSIS executable which downloads and installs Lockbit. The ransomware is installed onto the desktop for persistence through desktop change or reboot. Prior to data encryption, Lockbit will delete the volume shadow copy to prevent data recovery, in addition to terminating a variety of services and processes to avoid detection.
Analyst Comment: Never click on suspicious attachments or run any executables from suspicious emails. Copyright infringement emails are a common phishing lure. Such emails will be straight forward to rectify if legitimate. If a copyright email is attempting to coerce you into opening attachments, such emails should be treated with extreme caution.
MITRE ATT&CK: [MITRE ATT&CK] Phishing - T1566 | [MITRE ATT&CK] Data Encrypted for Impact - T1486 | [MITRE ATT&CK] Impair Defenses - T1562
Tags: malware:Phishing, malware:Lockbit, Lockbit, Copyright, Ransomware
There is More Than One Way To Sleep: Deep Dive into the Implementations of API Hammering by Various Malware Families
(published: June 24, 2022)
Researchers at Palo Alto Networks have released their analysis of new BazarLoader and Zloader samples that utilize API Hammering as a technique to evade sandbox detection. API Hammering makes use of a large volume of Windows API calls to delay the execution of malicious activity to trick sandboxes into thinking the malware is benign. Whilst BazarLoader has utilized the technique in the past, this new variant creates large loops of benign API using a new process. Encoded registry keys within the malware are used for the calls and the large loop count is created from the offset of the first null byte of the first file in System32 directory. Zloader uses a different form of API Hammering to evade sandbox detection. Hardcoded within Zloader are four large functions with many smaller functions within. Each function makes an input/output (I/O) call to mimic the behavior of many legitimate processes.
Analyst Comment: Defense in depth is the best defense against sophisticated malware. The Anomali Platform can assist in detection of malware and Match anomalous activity from all telemetry sources to provide the complete picture of adversary activity within your network.
MITRE ATT&CK: [MITRE ATT&CK] Virtualization/Sandbox Evasion - T1497
Tags: malware:BazarLoad |
Ransomware Spam Malware Tool Vulnerability Threat | APT 28 APT 23 | ||
| 2022-06-22 10:31:08 | (Déjà vu) New Phishing Attack Infects Devices With Cobalt Strike (lien direct) | Security researchers have discovered a new malicious spam campaign that delivers the ‘Matanbuchus’ malware to drop Cobalt Strike beacons on compromised machines. Cobalt Strike is a penetration testing suite that is frequently used by threat actors for lateral movement and to drop additional payloads. First spotted in February 2021 in advertisements on the dark web, […] | Spam Malware Threat | |||
| 2022-06-20 11:15:09 | CVE-2022-1801 (lien direct) | The Very Simple Contact Form WordPress plugin before 11.6 exposes the solution to the captcha in the rendered contact form, both as hidden input fields and as plain text in the page, making it very easy for bots to bypass the captcha check, rendering the page a likely target for spam bots. | Spam | ★★ | ||
| 2022-06-18 10:06:03 | (Déjà vu) New phishing attack infects devices with Cobalt Strike (lien direct) | Security researchers have noticed a new malicious spam campaign that delivers the 'Matanbuchus' malware to drop Cobalt Strike beacons on compromised machines. [...] | Spam Malware | ★★★ | ||
| 2022-06-18 10:06:03 | Wave of \'Matanbuchus\' spam is infecting devices with Cobalt Strike (lien direct) | Security researchers have noticed a new malicious spam campaign that delivers the 'Matanbuchus' malware to drop Cobalt Strike beacons on compromised machines. [...] | Spam Malware | |||
| 2022-06-17 16:00:25 | How to spot malicious spam – Week in security with Tony Anscombe (lien direct) | >As the risk of receiving a malware-laden email increases, take a moment to consider how to spot attacks involving malicious spam | Spam | |||
| 2022-06-13 02:00:00 | 9 ways hackers will use machine learning to launch attacks (lien direct) | Machine learning and artificial intelligence (AI) are becoming a core technology for some threat detection and response tools. The ability to learn on the fly and automatically adapt to changing cyberthreats give security teams an advantage.However, some threat actors are also using machine learning and AI a to scale up their cyberattacks, evade security controls, and find new vulnerabilities all at an unprecedented pace and to devastating results. Here are the nine most common ways attackers leverage these technologies.1. Spam, spam, spam, spam Defenders have been using machine learning to detect spam for decades, says Fernando Montenegro, analyst at Omdia. "Spam prevention is the best initial use case for machine learning," he says.To read this article in full, please click here | Spam Threat | ★★★ | ||
| 2022-06-11 00:04:22 | Adconion Execs Plead Guilty in Federal Anti-Spam Case (lien direct) | On the eve of their federal criminal trial for allegedly stealing vast swaths of Internet addresses for use in large-scale email spam campaigns, three current or former executives at online advertising firm Adconion Direct have agreed to plead guilty to lesser misdemeanor charges of fraud and misrepresentation via email. | Spam Guideline | |||
| 2022-06-10 15:49:40 | WhatsApp spam offers up “B&Q Father\'s Day Contest 2022” (lien direct) | We take a look at a scam barbeque quiz that asks "winners" to send a lot of WhatsApp messages to qualify. | Spam | |||
| 2022-06-08 10:15:10 | CVE-2022-1709 (lien direct) | The Throws SPAM Away WordPress plugin before 3.3.1 does not have CSRF checks in place when deleting comments (either all, spam, or pending), allowing attackers to make a logged in admin delete comments via a CSRF attack | Spam | |||
| 2022-06-08 10:15:09 | CVE-2022-1569 (lien direct) | The Drag & Drop Builder, Human Face Detector, Pre-built Templates, Spam Protection, User Email Notifications & more! WordPress plugin before 1.4.9.4 does not sanitise and escape some of its form fields, which could allow high privilege users such as admin to perform Cross-Site Scripting attacks when unfiltered_html is disallowed | Spam | ★★★★★ | ||
| 2022-06-07 16:38:51 | Texas AG enters Musk/Twitter fight by ordering Twitter to provide spam data (lien direct) | Paxton demands the spam data that Musk hasn't been able to get from Twitter. | Spam | |||
| 2022-06-07 01:14:19 | Researchers Warn of Spam Campaign Targeting Victims with SVCReady Malware (lien direct) | A new wave of phishing campaigns has been observed spreading a previously documented malware called SVCReady. "The malware is notable for the unusual way it is delivered to target PCs - using shellcode hidden in the properties of Microsoft Office documents," Patrick Schläpfer, a threat analyst at HP, said in a technical write-up. SVCReady is said to be in its early stage of development, with the | Spam Malware Threat | |||
| 2022-06-06 16:11:22 | Musk seeks a way out, claims Twitter violated deal by not providing spam data (lien direct) | Musk waived due diligence but claims he can kill deal if he doesn't get user data. | Spam | |||
| 2022-05-27 12:04:11 | The $44 Billion Smishing Problem and How to Not Be a Victim (lien direct) |
 Consumer Affairs reported on how big of a problem SMS phishing scams have become, and how it's about to get a lot worse. According to a recent FBI report, more than 320,000 Americans were targeted by these schemes in 2021, resulting in $44 billion in losses. Consumers on average get an average of 19.5 spam texts per month, over double the rate it was three years ago.
Consumer Affairs reported on how big of a problem SMS phishing scams have become, and how it's about to get a lot worse. According to a recent FBI report, more than 320,000 Americans were targeted by these schemes in 2021, resulting in $44 billion in losses. Consumers on average get an average of 19.5 spam texts per month, over double the rate it was three years ago. |
Spam | |||
| 2022-05-17 17:15:07 | Musk says Twitter must show data behind spam estimate or he\'ll kill the deal (lien direct) | Musk replied to Twitter CEO's spam explanation with criticism and a poop emoji. | Spam | |||
| 2022-05-17 12:24:22 | Musk: Doubt About Spam Accounts Could Scuttle Twitter Deal (lien direct) | 
|
Spam | |||
| 2022-05-17 12:11:00 | Twitter réplique à Elon Musk au sujet des spams, et explique comment il lutte contre les faux comptes (lien direct) | Le PDG du réseau social joue la carte de la transparence en expliquant comment ses équipes traquent les spams et faux comptes. Un processus complexe qui nécessite une adaptation constante.  |
Spam | |||
| 2022-05-13 15:28:09 | Musk says Twitter deal “on hold” over concern about number of spam accounts (lien direct) | Musk "still committed" to purchase amid talk he could back out or renegotiate. | Spam | |||
| 2022-05-11 15:49:52 | I/O 2022: Android 13 security and privacy (and more!) (lien direct) | Posted by Eugene Liderman and Sara N-Marandi, Android Security and Privacy TeamEvery year at I/O we share the latest on privacy and security features on Android. But we know some users like to go a level deeper in understanding how we're making the latest release safer, and more private, while continuing to offer a seamless experience. So let's dig into the tools we're building to better secure your data, enhance your privacy and increase trust in the apps and experiences on your devices. Low latency, frictionless securityRegardless of whether a smartphone is used for consumer or enterprise purposes, attestation is a key underpinning to ensure the integrity of the device and apps running on the device. Fundamentally, key attestation lets a developer bind a secret or designate data to a device. This is a strong assertion: "same user, same device" as long as the key is available, a cryptographic assertion of integrity can be made. With Android 13 we have migrated to a new model for the provisioning of attestation keys to Android devices which is known as Remote Key Provisioning (RKP). This new approach will strengthen device security by eliminating factory provisioning errors and providing key vulnerability recovery by moving to an architecture where Google takes more responsibility in the certificate management lifecycle for these attestation keys. You can learn more about RKP here.  We're also making even more modules updatable directly through Google Play System Updates so we can automatically upgrade more system components and fix bugs, seamlessly, without you having to worry about it. We now have more than 30 components in Android that can be automatically updated through Google Play, including new modules in Android 13 for Bluetooth and ultra-wideband (UWB). Last year we talked about how the majority of vulnerabilities in major operating systems are caused by undefined behavior in programming languages like C/C++. Rust is an alternative language that provides the efficiency and flexibility required in advanced systems programming (OS, networking) but Rust comes with the added boost of memory safety. We are happy to report that Rust is being adopted in security critical parts of Android, such as our key management components and networking stacks. Hardening the platform doesn't just stop with continual improvements with memory safety and expansion of anti-exploitation techniques. It also includes hardening our API surfaces to provide a more secure experience to our end users. In Android 13 we implemented numerous enhancements to help mitigate potential vulnerabilities that app developers may inadvertently introduce. This includes making runtime receivers safer by allowing developers to specify whether a particular broadcast receiver in their app s We're also making even more modules updatable directly through Google Play System Updates so we can automatically upgrade more system components and fix bugs, seamlessly, without you having to worry about it. We now have more than 30 components in Android that can be automatically updated through Google Play, including new modules in Android 13 for Bluetooth and ultra-wideband (UWB). Last year we talked about how the majority of vulnerabilities in major operating systems are caused by undefined behavior in programming languages like C/C++. Rust is an alternative language that provides the efficiency and flexibility required in advanced systems programming (OS, networking) but Rust comes with the added boost of memory safety. We are happy to report that Rust is being adopted in security critical parts of Android, such as our key management components and networking stacks. Hardening the platform doesn't just stop with continual improvements with memory safety and expansion of anti-exploitation techniques. It also includes hardening our API surfaces to provide a more secure experience to our end users. In Android 13 we implemented numerous enhancements to help mitigate potential vulnerabilities that app developers may inadvertently introduce. This includes making runtime receivers safer by allowing developers to specify whether a particular broadcast receiver in their app s |
Spam Vulnerability | |||
| 2022-05-11 12:13:51 | Novel Phishing Trick Uses Weird Links to Bypass Spam Filters (lien direct) | A novel form of phishing takes advantage of a disparity between how browsers and email inboxes read web domains. | Spam | ★★★ |
To see everything:
Our RSS (filtrered)
