What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2020-04-23 12:28:54 | Cloud computing: This new tool from AWS could make life easier for developers (lien direct) | AppFlow has been designed to remove the need for manually-configured data transfers between AWS and services like Salesforce, Slack, Trend Micro and Zendesk. | Tool | |||
| 2020-04-21 15:48:18 | How to install the Gradle Build Tool on Linux for automated building (lien direct) | Learn how to install Gradle on a data center Linux server for project build automation and delivery. | Tool | |||
| 2020-04-21 13:00:00 | One Woman\'s Instagram-Fueled Ascent to \'Boss Lady Status\' (lien direct) | For New Orleans entrepreneur Jesseca Dupart, social media isn't just a tool for building her business-it's a platform for inspiring other black women to do the same. | Tool | |||
| 2020-04-20 12:04:12 | Cloudflare debuts Border Gateway Protocol safety check tool (lien direct) | The tool can be used to see if your ISP is adhering to modern BGP security frameworks. | Tool | |||
| 2020-04-17 06:02:30 | Windows Persistence using Bits Job (lien direct) | In this article, we are going to describe the ability of the Bits Job process to provide persistent access to the Target Machine. Table of Content Introduction Configurations used in Practical Manual Persistence Metasploit Persistence Metasploit (file-less) Persistence Mitigation Introduction Background Intelligent Transfer Service Admin is a command-line tool that creates downloads or uploads jobs... Continue reading → | Tool | |||
| 2020-04-15 13:00:07 | New tool detects AWS intrusions where hackers abuse self-replicating tokens (lien direct) | New SkyWrapper tool generates Excel spreadsheets so AWS account owners can easily spot compromised tokens. | Tool | |||
| 2020-04-14 21:01:19 | Apple and Google Develop Covid-19 Contact Tracing Tool (lien direct) | Apple and Google have announced that they're working together to create a Covid-19 contact tracing framework for mobile devices. In this piece, we'll tell you what you need to know about this important new technology. What is it? The joint project is aimed at developing a Bluetooth-based contact tracing system that will alert iOS and Android users if they've come into contact with someone who has been diagnosed with Covid-19. When will it ... | Tool | |||
| 2020-04-14 16:14:56 | Binwalk – Firmware Security Analysis & Extraction Tool (lien direct) |  Binwalk is a fast and easy to use Python-based firmware security analysis tool that allows for firmware analysis, reverse engineering, and extraction of firmware images.
Features of Binwalk Firmware Security Analysis & Extraction Tool
Scanning Firmware – Binwalk can scan a firmware image for many different embedded file types and file systems
File Extraction – You can tell binwalk to extract any files that it finds in the firmware image
Entropy Analysis – Can help identify interesting sections of data inside a firmware image
String Search – Allows you to search the specified file(s) for a custom string
There are also various filters such as by CPU architecture, number of instructions, include filter, exclude filter,
Installation of Binwalk Firmware Security Analysis & Extraction Tool
Download binwalk:
$ wget https://github.com/ReFirmLabs/binwalk/archive/master.zip
$ unzip master.zip
Install binwalk; if you have a previously installed version of binwalk, it is suggested that you uninstall it before upgrading:
$ (cd binwalk-master && sudo python setup.py uninstall && sudo python setup.py install)
Debian users can install all optional and suggested extractors/dependencies using the included deps.sh script (recommended):
$ sudo ./binwalk-master/deps.sh
If you are not a Debian user, or if you wish to install only selected dependencies, see the INSTALL documentation for more details.
Read the rest of Binwalk – Firmware Security Analysis & Extraction Tool now! Only available at Darknet. Binwalk is a fast and easy to use Python-based firmware security analysis tool that allows for firmware analysis, reverse engineering, and extraction of firmware images.
Features of Binwalk Firmware Security Analysis & Extraction Tool
Scanning Firmware – Binwalk can scan a firmware image for many different embedded file types and file systems
File Extraction – You can tell binwalk to extract any files that it finds in the firmware image
Entropy Analysis – Can help identify interesting sections of data inside a firmware image
String Search – Allows you to search the specified file(s) for a custom string
There are also various filters such as by CPU architecture, number of instructions, include filter, exclude filter,
Installation of Binwalk Firmware Security Analysis & Extraction Tool
Download binwalk:
$ wget https://github.com/ReFirmLabs/binwalk/archive/master.zip
$ unzip master.zip
Install binwalk; if you have a previously installed version of binwalk, it is suggested that you uninstall it before upgrading:
$ (cd binwalk-master && sudo python setup.py uninstall && sudo python setup.py install)
Debian users can install all optional and suggested extractors/dependencies using the included deps.sh script (recommended):
$ sudo ./binwalk-master/deps.sh
If you are not a Debian user, or if you wish to install only selected dependencies, see the INSTALL documentation for more details.
Read the rest of Binwalk – Firmware Security Analysis & Extraction Tool now! Only available at Darknet.
|
Tool | |||
| 2020-04-14 15:00:00 | Keep Zoombombing cybercriminals from dropping a load on your meetings (lien direct) |
 In a zeitgeisty moment, Zoom has become the web conference tool of choice for everyone. Unfortunately, cybercriminals are taking note and Zoombooming the public. We show readers how to protect against this intrusion of privacy.
Categories:
How-tos
Tags: coronaviruscovid-19exploitexploitshow-to zoomteleconferencingvirtual meetingswebinarszoomzoom squattingzoombomberszoombombingzooming
(Read more...)
In a zeitgeisty moment, Zoom has become the web conference tool of choice for everyone. Unfortunately, cybercriminals are taking note and Zoombooming the public. We show readers how to protect against this intrusion of privacy.
Categories:
How-tos
Tags: coronaviruscovid-19exploitexploitshow-to zoomteleconferencingvirtual meetingswebinarszoomzoom squattingzoombomberszoombombingzooming
(Read more...)
|
Tool | |||
| 2020-04-14 06:52:10 | Dell Releases A New Cybersecurity Utility To Detect BIOS Attacks (lien direct) | Computer manufacturing giant Dell has released a new security tool for its commercial customers that aims to protect their computers from stealthy and sophisticated cyberattacks involving the compromise of the BIOS.
Dubbed 'SafeBIOS Events & Indicators of Attack' (IoA), the new endpoint security software is a behavior-based threat detection system that alerts users when BIOS settings of their |
Tool Threat | |||
| 2020-04-13 18:40:00 | Dell Releases Security Tool to Defend PCs from BIOS Attacks (lien direct) | The SafeBIOS Events & Indicators of Attack tool gives admins visibility into BIOS configuration changes and alerts them to potential threats. | Tool | |||
| 2020-04-13 16:28:17 | Dell releases new tool to detect BIOS attacks (lien direct) | Dell makes new tool named SafeBIOS Events & Indicators of Attack available for download for all Dell commercial PCs. | Tool | |||
| 2020-04-13 15:13:19 | Apple and Google join forces to develop Contact Tracing app against Coronavirus (lien direct) | Google and Apple recently announced a joint project for the development of a Coronavirus ‘contact tracing’ tool for mobile devices. A contact tracing app is a tool that could be used to contain new diseases, like Coronavirus, by tracking down and quarantining everyone that gets infected and localize any person that has been in contact […] | Tool | |||
| 2020-04-11 01:42:52 | Google and Apple Plan to Turn Phones into COVID-19 Contact-Tracking Devices (lien direct) | Tech giants Apple and Google have joined forces to develop an interoperable contract-tracing tool that will help individuals determine if they have come in contact with someone infected with COVID-19.
As part of this new initiative, the companies are expected to release an API that public agencies can integrate into their apps. The next iteration will be a built-in system-level platform that |
Tool | |||
| 2020-04-10 16:18:30 | Sophos Sandboxie is now available as an open-source tool (lien direct) | Sophos announced the public release of the source code of the sandbox-based isolation program Sandboxie. Sophos is going to release the Windows sandbox-based isolation program Sandboxie in open source. “Sandboxie has long been a favorite sandbox-based isolation tool since its original release over fifteen years ago. Now this technology will live on in the hands of its […] | Tool | |||
| 2020-04-10 14:47:27 | How to use port forwarding with containers deployed in a Kubernetes cluster (lien direct) | Port forwarding within a Kubernetes cluster is a helpful tool for debugging. Find out how it's done. | Tool | Uber | ||
| 2020-04-09 15:49:55 | How to add and prevent startup applications in macOS (lien direct) | Startup items have long been a tool used to ensure applications and scripts execute when a Mac is started up. Here's how to easily modify these items. | Tool | |||
| 2020-04-09 15:36:23 | The Sandboxie Windows sandbox isolation tool is now open-source! (lien direct) | Cybersecurity firm Sophos announced today that it has open-sourced the Sandboxie Windows sandbox-based isolation utility 15 years after it was released. [...] | Tool | |||
| 2020-04-09 09:59:45 | Procurement solution used by government bodies found to contain zero-day bug (lien direct) | A zero-day cross-site scripting vulnerability has been discovered in BuySpeed, an automated procure-to-pay tool from Periscope Holdings, a provider of procurement software solutions for public-sector entities and their suppliers. The flaw, found in BuySpeed version 14.5, “could allow a local, authenticated attacker to store arbitrary JavaScript within the application,” warns a vulnerability advisory from the […] | Tool Vulnerability | |||
| 2020-04-08 15:00:18 | Box unveils new automated malware detection tool for cloud platform (lien direct) | The preview technology and controls will make it easier for IT teams to detect and contain threats before they infect systems, the company says. | Malware Tool | |||
| 2020-04-08 13:47:41 | NSO CEO claims Facebook wanted NSO surveillance tool to spy on users (lien direct) | A new shocking revelation comes from the disputed from NSO Group and Facebook, NSO CEO claims Facebook tried to buy an Apple spying software in 2017. Reading this post you could have a better idea of the value of your privacy. In October 2019, WhatsApp sued the Israeli surveillance firm NSO Group accusing it of carrying out malicious attacks […] | Tool | |||
| 2020-04-07 11:28:11 | If You Can\'t Patch Your Email Server, You Should Not Be Running It (lien direct) | 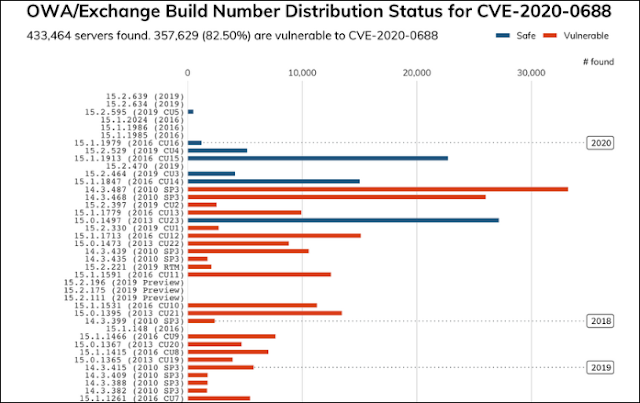 CVE-2020-0688 Scan Results, per Rapid7tl;dr -- it's the title of the post: "If You Can't Patch Your Email Server, You Should Not Be Running It."I read a disturbing story today with the following news:"Starting March 24, Rapid7 used its Project Sonar internet-wide survey tool to discover all publicly-facing Exchange servers on the Internet and the numbers are grim.As they found, 'at least 357,629 (82.5%) of the 433,464 Exchange servers' are still vulnerable to attacks that would exploit the CVE-2020-0688 vulnerability.To make matters even worse, some of the servers that were tagged by Rapid7 as being safe against attacks might still be vulnerable given that 'the related Microsoft update wasn't always updating the build number.'Furthermore, 'there are over 31,000 Exchange 2010 servers that have not been updated since 2012,' as the Rapid7 researchers observed. 'There are nearly 800 Exchange 2010 servers that have never been updated.'They also found 10,731 Exchange 2007 servers and more than 166,321 Exchange 2010 ones, with the former already running End of Support (EoS) software that hasn't received any security updates since 2017 and the latter reaching EoS in October 2020."In case you were wondering, threat actors have already been exploiting these flaws for weeks, if not months.Email is one of, if not the most, sensitive and important systems upon which organizations of all shapes and sizes rely. The are, by virtue of their function, inherently exposed to the Internet, meaning they are within the range of every targeted or opportunistic intruder, worldwide.In this particular case, unpatched servers are also vulnerable to any actor who can download and update Metasploit, which is virtually 100% of them.It is the height of negligence to run such an important system in an unpatched state, when there are much better alternatives -- namely, outsourcing your email to a competent provider, like Google, Microsoft, or several others.I expect some readers are saying "I would never put my email in the hands of those big companies!" That's fine, and I know several highly competent individuals who run their own email infrastructure. The problem is that they represent the small fraction of individuals and organizations who can do so. Even being extremely generous with the numbers, it appears that less than 20%, and probably less than 15% according to other estimates, can even keep their Exchange servers patched, let alone properly configured.If you think it's still worth the risk, and your organization isn't able to patch, because you want to avoid megacorp email providers or government access to your email, you've made a critical miscalculation. You've essentially decided that it's more important for you to keep your email out of megacorp or government hands than it is to keep i CVE-2020-0688 Scan Results, per Rapid7tl;dr -- it's the title of the post: "If You Can't Patch Your Email Server, You Should Not Be Running It."I read a disturbing story today with the following news:"Starting March 24, Rapid7 used its Project Sonar internet-wide survey tool to discover all publicly-facing Exchange servers on the Internet and the numbers are grim.As they found, 'at least 357,629 (82.5%) of the 433,464 Exchange servers' are still vulnerable to attacks that would exploit the CVE-2020-0688 vulnerability.To make matters even worse, some of the servers that were tagged by Rapid7 as being safe against attacks might still be vulnerable given that 'the related Microsoft update wasn't always updating the build number.'Furthermore, 'there are over 31,000 Exchange 2010 servers that have not been updated since 2012,' as the Rapid7 researchers observed. 'There are nearly 800 Exchange 2010 servers that have never been updated.'They also found 10,731 Exchange 2007 servers and more than 166,321 Exchange 2010 ones, with the former already running End of Support (EoS) software that hasn't received any security updates since 2017 and the latter reaching EoS in October 2020."In case you were wondering, threat actors have already been exploiting these flaws for weeks, if not months.Email is one of, if not the most, sensitive and important systems upon which organizations of all shapes and sizes rely. The are, by virtue of their function, inherently exposed to the Internet, meaning they are within the range of every targeted or opportunistic intruder, worldwide.In this particular case, unpatched servers are also vulnerable to any actor who can download and update Metasploit, which is virtually 100% of them.It is the height of negligence to run such an important system in an unpatched state, when there are much better alternatives -- namely, outsourcing your email to a competent provider, like Google, Microsoft, or several others.I expect some readers are saying "I would never put my email in the hands of those big companies!" That's fine, and I know several highly competent individuals who run their own email infrastructure. The problem is that they represent the small fraction of individuals and organizations who can do so. Even being extremely generous with the numbers, it appears that less than 20%, and probably less than 15% according to other estimates, can even keep their Exchange servers patched, let alone properly configured.If you think it's still worth the risk, and your organization isn't able to patch, because you want to avoid megacorp email providers or government access to your email, you've made a critical miscalculation. You've essentially decided that it's more important for you to keep your email out of megacorp or government hands than it is to keep i |
Tool | |||
| 2020-04-06 18:47:41 | ENISA released a Tool to map dependencies to International Standards (lien direct) | The European Agency for Cybersecurity ENISA has released a tool for the mapping of international security standards to interdependencies' indicators. ENISA has released a tool for the mapping of international security standards to interdependencies' indicators that have been introduced and demonstrated in the report Good practices on interdependencies between OES and DSPs. This ENISA report analyzed […] | Tool | |||
| 2020-04-06 12:05:52 | Windows 10: How to track down that irritating bug with DTrace (lien direct) | Microsoft has implemented the popular open tracing tool to help developers debug Windows code. | Tool | |||
| 2020-04-03 18:42:13 | Google Reveals Location Data to Help the Coronavirus Response (lien direct) | The search giant is disclosing trends in visits to broad categories of places, as a tool for public health officials. | Tool | ★★★★ | ||
| 2020-04-03 13:00:00 | The Right Gear for Your Home Tool Kit: Hammers, Screwdrivers, and More (lien direct) | Here's all the gear you need to handle any DIY job, from basic repairs to more ambitious home improvement projects. | Tool | |||
| 2020-04-02 14:43:04 | \'War Dialing\' Tool Exposes Zoom\'s Password Problems (lien direct) | As the Coronavirus pandemic continues to force people to work from home, countless companies are now holding daily meetings using videoconferencing services from Zoom. But without the protection of a password, there's a decent chance your next Zoom meeting could be "Zoom bombed" -- attended or disrupted by someone who doesn't belong. And according to data gathered by a new automated Zoom meeting discovery tool dubbed "zWarDial," a crazy number major corporations are setting up meetings without passwords enabled. | Tool | |||
| 2020-04-02 10:00:00 | Fakennet Genie: Amélioration de l'analyse dynamique des logiciels malveillants avec des codes de triche pour fakennet-ng FakeNet Genie: Improving Dynamic Malware Analysis with Cheat Codes for FakeNet-NG (lien direct) |
En tant que développeurs de l'outil de simulation de réseau FAKENET-NG, ingénieurs inverses de l'équipe Fireeye Flare et instructeurs d'analyse de logiciels malveillants, nous voyons comment différents analystes utilisent Fakennet-NG et les défis auxquels ils sont confrontés.Nous avons appris que Fakennet-NG fournit de nombreuses fonctionnalités et solutions utiles dont nos utilisateurs ignorent souvent.Dans cet article de blog, nous présenterons certains codes de triche pour améliorer votre analyse de réseau avec Fakennet-NG.Nous introduirons des réponses personnalisées et présenterons des fonctionnalités puissantes telles que l'exécution de commandes sur les événements de connexion et le décryptage du trafic SSL.
depuis son premier
As developers of the network simulation tool FakeNet-NG, reverse engineers on the FireEye FLARE team, and malware analysis instructors, we get to see how different analysts use FakeNet-NG and the challenges they face. We have learned that FakeNet-NG provides many useful features and solutions of which our users are often unaware. In this blog post, we will showcase some cheat codes to level up your network analysis with FakeNet-NG. We will introduce custom responses and demonstrate powerful features such as executing commands on connection events and decrypting SSL traffic. Since its first |
Malware Tool | ★★★ | ||
| 2020-04-02 06:26:28 | Comprehensive Guide on CryptCat (lien direct) | In this article, we will provide you with some basic functionality of CryptCat and how to get a session from it using this tool. Table of Content Introduction Chat Verbose mode Protect with Password Reverse Shell Randomize port Timeout and Delay interval Netcat vs CryptCat Introduction CryptCat is a standard NetCat enhanced tool with two-way... Continue reading → | Tool | |||
| 2020-04-01 08:07:18 | Unpatched Zoom App Bug Lets Hackers Steal Your Windows Password (lien direct) | Zoom has been there for nine years, but the immediate requirement of an easy-to-use video conferencing app during the coronavirus pandemic made it overnight a favorite tool for millions of people.
Though Zoom is an efficient online video meeting solution, it's still not the best choice in terms of privacy and security.
According to the latest finding by cybersecurity expert @_g0dmode and |
Tool | |||
| 2020-04-01 08:00:10 | LimeRAT malware delivered using 8-year-old VelvetSweatshop trick (lien direct) | Researchers spotted a campaign using Excel files to spread LimeRAT malware using the 8-year-old and well-known VelvetSweatshop bug. Researchers at the Mimecast Threat Center spotted a new campaign using Excel files to spread LimeRAT malware using the 8-year-old VelvetSweatshop bug. LimeRAT is a powerful Remote Administration Tool publicly available as an open-source project on Github, it […] | Malware Tool Threat | |||
| 2020-03-31 15:20:31 | zBang – Privileged Account Threat Detection Tool (lien direct) |  zBang is a risk assessment tool for Privileged Account Threat Detection on a scanned network, organizations and red teamers can utilize zBang to identify potential attack vectors and improve the security posture of the network.
The results can be analyzed with the graphic interface or by reviewing the raw output files.
The tool is built from five different scanning modules:
ACLight scan – discovers the most privileged accounts that must be protected, including suspicious Shadow Admins.
Read the rest of zBang – Privileged Account Threat Detection Tool now! Only available at Darknet. zBang is a risk assessment tool for Privileged Account Threat Detection on a scanned network, organizations and red teamers can utilize zBang to identify potential attack vectors and improve the security posture of the network.
The results can be analyzed with the graphic interface or by reviewing the raw output files.
The tool is built from five different scanning modules:
ACLight scan – discovers the most privileged accounts that must be protected, including suspicious Shadow Admins.
Read the rest of zBang – Privileged Account Threat Detection Tool now! Only available at Darknet.
|
Tool Threat | |||
| 2020-03-31 00:00:00 | Cyber Risk - du péril au produit adoptant une nouvelle approche pour gérer le cyber-risque silencieux Lire la suite Cyber Risk - From Peril to ProductTaking a New Approach for Managing Silent Cyber RiskRead More (lien direct) |
A New Approach for Managing Silent Cyber RiskâCyber is a multifaceted peril that is both a threat and an opportunity for the insurance industry: an opportunity because of the ever-evolving needs of coverage for businesses of any size, and a threat because of the systemic risk arising from its potential for overlap with other lines of business. Silent cyber refers to covered losses triggered by cyber events in P&C policies that were not specifically designed to cover cyber risk. Affirmative cyber refers to coverages specifically provided to protect policyholders against cyber events and presents a premium growth opportunity for insurance companies. As exposures to cyber continue to grow, insurance companies need tools to quantify the impact on allocated capital for cyber risk, regardless of whether the risk is silent or affirmative.With some estimates for accumulation across commercial lines running in the hundreds of billions, exposure managers are under pressure to more accurately estimate the potential impact of cyber events to ensure appropriate capital is held for this risk and enable decision makers, investors and regulators to quantify financial returns on a risk adjusted basis. Additionally, they are being forced to provide more transparency into methods used for measuring and controlling cyber accumulations. With various stakeholders and types of practitioners involved, the topic of cyber risk often presents seemingly conflicting priorities around managing capital at risk, estimating potential losses in existing lines of business, and finding new ways to market, through pricing new cyber specific business.Cyber events across different lines of business share a common trait. The key is to build tools capable of estimating realistic losses for both silent and affirmative cyber based on these shared traits. The focus of cyber risk for insurers should be gaining unique insights into events that truly matter -events capable of generating equity depleting losses. Measuring the impact of cyber events on capital is a three step process: identify, quantify and manage.Lately, the insurance industry seeks to consolidate most cyber risk into one dedicated line of business by implementing exclusion clauses in existing policies and inviting policy holders to âbuy backâ coverage. Several different wordings for such exclusions and endorsements have been introduced to the market. While intending to clearly define the scope of a cyber event and the coverage provided, the introduction of some of these clauses has produced unintended consequences. One example of this would be coverage for damage to a server due to flooding. In this example, the common expectation would be for the physical damage to the server as well as recovery of the data to be covered under flood insurance, however, the latest trend suggests data recovery might be excluded, as it relates to âdataâ, leaving a gap in coverage for property which some sources consider excessive.âSilent and AffirmativeThe issue with silent cyber, as with any circumstance presenting unexpected claims activity, is ensuring the premium charged is commensurate with the level of risk, usually referred to as pricing adequacy. Both cyber exposure and the potential impact of losses triggered by cyber perils continues to trend upwards annually. Unexpected claims lead to unexpectedly high loss ratios which clearly erode profits but can also lead to significant damage to an insurerâs financial stability.Insurance companies protect their balance sheets by purchasing reinsurance, but reinsurers face similar issues, they are also vulnerable to silent cyber. Therefore, insurers face the prospect of being denied recoveries from cyber losses and reinsurers are stepping up demands for clarity of coverage. Efforts to resolve the situation have taken two complementary directions: a conscious attempt to price for cyber risk and the introduction of increasingly restrictive exclusion clauses.âThe Status of Cyber ExclusionsCyber | Tool Vulnerability Threat Prediction | ★★★ | ||
| 2020-03-30 16:31:37 | How to configure a remote desktop connection in Windows (lien direct) | Microsoft's Remote Desktop Connection tool offers various settings you can tweak for better performance, reliability, and overall experience. | Tool | |||
| 2020-03-29 10:34:41 | Command & Control: PoshC2 (lien direct) | PoshC2 is an open-source remote administration and post-exploitation framework that is publicly available on GitHub. The server-side components of the tool are primarily written in Python, while the implants are written in PowerShell. Although PoshC2 primarily focuses on Windows implantation, it does contain a basic Python dropper for Linux/macOS. Table of Content Introduction Features Installation... Continue reading → | Tool | |||
| 2020-03-29 07:14:18 | Memhunter – Automated Memory Resident Malware Detection (lien direct) |  Memhunter is an Automated Memory Resident Malware Detection tool for the hunting of memory resident malware at scale, improving the threat hunter analysis process and remediation times.
It's a self contained binary that can be deployed and managed at scale, does not use memory dumps and relies purely on memory inspection to do its work. It also does not require any complex infrastructure to deploy.
The tool was designed as a replacement of memory forensic volatility plugins such as malfind and hollowfind.
Read the rest of Memhunter – Automated Memory Resident Malware Detection now! Only available at Darknet. Memhunter is an Automated Memory Resident Malware Detection tool for the hunting of memory resident malware at scale, improving the threat hunter analysis process and remediation times.
It's a self contained binary that can be deployed and managed at scale, does not use memory dumps and relies purely on memory inspection to do its work. It also does not require any complex infrastructure to deploy.
The tool was designed as a replacement of memory forensic volatility plugins such as malfind and hollowfind.
Read the rest of Memhunter – Automated Memory Resident Malware Detection now! Only available at Darknet.
|
Malware Tool Threat | |||
| 2020-03-28 13:00:00 | AI Can Help Find Scientists Find a Covid-19 Vaccine (lien direct) | Artificial intelligence has already played a vital role in the outbreak since day 1-a reminder for the first time in a while that it can be a tool for good. | Tool | |||
| 2020-03-27 19:39:00 | Apple partners with CDC to release new COVID-19 screening tool and app for coronavirus (lien direct) | The new screening tools are available online and in the App Store and provide a questionnaire to see if coronavirus symptoms warrant treatment and testing. | Tool | |||
| 2020-03-27 16:28:36 | US Small Business Administration Grants Used as Phishing Bait (lien direct) | Attackers are attempting to deliver Remcos remote access tool (RAT) payloads on the systems of small businesses via phishing emails impersonating the U.S. Small Business Administration (U.S. SBA). [...] | Tool | |||
| 2020-03-25 18:02:58 | How to control a remote computer using Microsoft\'s Remote Desktop Connection (lien direct) | Learn how to access and work with a remote PC using the Remote Desktop Connection tool in Windows. | Tool | ★★★★ | ||
| 2020-03-24 15:48:52 | Sandcastle – AWS S3 Bucket Enumeration Tool (lien direct) |  Sandcastle is a Python-based Amazon AWS S3 Bucket Enumeration Tool, formerly known as bucketCrawler. The script takes a target's name as the stem argument (e.g. shopify) and iterates through a file of bucket name permutations.
Amazon S3 [Simple Storage Service] is cloud storage for the Internet. To upload your data (photos, videos, documents etc.), you first create a bucket in one of the AWS Regions. You can then upload any number of objects to the bucket.
Read the rest of Sandcastle – AWS S3 Bucket Enumeration Tool now! Only available at Darknet. Sandcastle is a Python-based Amazon AWS S3 Bucket Enumeration Tool, formerly known as bucketCrawler. The script takes a target's name as the stem argument (e.g. shopify) and iterates through a file of bucket name permutations.
Amazon S3 [Simple Storage Service] is cloud storage for the Internet. To upload your data (photos, videos, documents etc.), you first create a bucket in one of the AWS Regions. You can then upload any number of objects to the bucket.
Read the rest of Sandcastle – AWS S3 Bucket Enumeration Tool now! Only available at Darknet.
|
Tool | |||
| 2020-03-24 14:00:00 | Squids\' Gene-Editing Superpowers May Unlock Human Cures (lien direct) | Researchers found that the cephalopod is the only creature that can edit its RNA outside the nucleus. It's a tool that may one day help genetic medicine. | Tool | |||
| 2020-03-23 19:35:57 | Fake “Corona Antivirus” distributes BlackNET remote administration tool (lien direct) |
 Beware of fraudulent antivirus products taking advantage of the COVID-19 crisis.
Categories:
Social engineering
Threat analysis
Tags: antivirusbotnetcoronaviruscovid-19fakemalwarerat
(Read more...)
Beware of fraudulent antivirus products taking advantage of the COVID-19 crisis.
Categories:
Social engineering
Threat analysis
Tags: antivirusbotnetcoronaviruscovid-19fakemalwarerat
(Read more...)
|
Tool | ★★★ | ||
| 2020-03-23 12:00:00 | Windows Server 2019 OS hardening (lien direct) | This blog was written by an independent guest blogger. Windows Server 2019 ships and installs with an existing level of hardening that is significantly more secure compared to previous Windows Server operating systems. Gone are the bloat of Xbox integration and services and the need for third-party security solutions to fill security gaps. Operating System (OS) hardening provides additional layers of security and preventative measures against both unauthorized changes and access. Hardening is critical in securing an operating system and reducing its attack surface. Be careful! If you harden an operation system too much, you risk breaking key functionality. Hardening approach Harden your Windows Server 2019 servers or server templates incrementally. Implement one hardening aspect at a time and then test all server and application functionality. Your cadence should be to harden, test, harden, test, etc. Mistakes to avoid Reducing the surface area of vulnerability is the goal of operating system hardening. Keeping the area as small as possible means avoiding common bad practices. Do not turn off User Access Control (UAC). You should move the UAC slider to the top: Always notify. The few extra clicks to make while trying to install a new application or change system settings might prevent system compromise in the future. Do not install Google Chrome, Firefox, JAVA, Adobe Flash, PDF viewers, email clients, etc. on your Windows Server 2019 operating systems unless you have an application dependency for these applications. Do not install unnecessary roles and features on your Windows Server 2019 servers. If you need to install a role such as IIS, only enable the minimum features you require and do not enable all role features. Do not forget to fully patch your Windows Server 2019 operating system and establish a monthly patch window allowing you to patch and reboot your servers monthly. Hardening Windows 2019 Server Core As a foundation to Windows Server 2019, the Core version of Windows Server 2019, should be installed. This version is Windows 2019 Server Core. Server Core removes the traditional GUI interface to the operating system and provides the following security benefits. • Server Core has a smaller attack surface than Server with a GUI • Requires fewer software updates and reboots • Can be managed using new Windows Admin Center • Improved Application Compatibility features in Windows Server 2019 Traditional Windows administrators may be apprehensive running Server Core due to a lack of PowerShell familiarity. The new Windows Admin Center provides a free, locally deployed, browser-based app for managing servers, clusters, hyper-converged infrastructure, and Windows 10 PC’s. Windows Admin Center comes at no additional cost beyond Windows and is ready to use in production. You can install Windows Admin Center on Windows Server 2019 as well as Windows 10 and earlier versions of Windows and Windows Server and use it to manage servers and clusters running Windows Server 2008 R2 and later. Secure the Local Administrator Account Local Administrator Password Solution (LAPS) If Windows Server does get compromised, the attacker will quickly try to move laterally across your network to find highly valuable systems and information. Credenti | Ransomware Malware Tool Vulnerability Patching | |||
| 2020-03-23 07:00:00 | Surveillance des outils de cyber-opération ICS et des modules d'exploitation de logiciels pour anticiper les menaces futures Monitoring ICS Cyber Operation Tools and Software Exploit Modules To Anticipate Future Threats (lien direct) |
Il n'y a eu qu'un petit nombre de cyberattaques largement documentées ciblant les technologies opérationnelles (OT) / systèmes de contrôle industriel (ICS) au cours de la dernière décennie.Bien que moins d'attaques soit clairement une bonne chose, l'absence d'une taille d'échantillon adéquate pour déterminer les seuils de risque peut rendre difficile pour les défenseurs de comprendre l'environnement de menace, de hiérarchiser les efforts de sécurité et de justifier l'allocation des ressources.
Pour résoudre ce problème, Fireeye Mandiant Threat Intelligence produit une gamme de rapports pour abonnement Les clients qui se concentrent sur différents indicateurs pour prédire les menaces futures
There has only been a small number of broadly documented cyber attacks targeting operational technologies (OT) / industrial control systems (ICS) over the last decade. While fewer attacks is clearly a good thing, the lack of an adequate sample size to determine risk thresholds can make it difficult for defenders to understand the threat environment, prioritize security efforts, and justify resource allocation. To address this problem, FireEye Mandiant Threat Intelligence produces a range of reports for subscription customers that focus on different indicators to predict future threats |
Tool Threat Industrial Prediction | ★★★★ | ||
| 2020-03-22 00:00:00 | Compter le coût d'une grande panne de service de messagerie de messagerie dans la panne de service de service de messagerie Ukmajor pourrait entraîner une perte brute brute de 3,25 milliards de dollars. Counting the Cost of a Major Email Service Provider Outage in the UKMajor email service provider outage could lead to $3.25B gross insured loss.Read More (lien direct) |
Modeling a Cyber CatastropheâCounting the Cost of a Major Email Service Provider Outage in the UKExecutive SummaryThe cyber books of many (re)insurers may be modest; however, their potential exposure to a cyber catastrophe could be very large. Even though overall cyber premiums are significantly lower than property in the UK, this report demonstrates that the potential for a multi-billion dollar insured loss is similar to the risk of floods catastrophes covered by property insurance.IntroductionEvery day 290 billion email messages are sent worldwide by 3.9billion users, facilitating a $15 trillion global economy comprised of over 150 million organizations. Email is an integral critical business service for organizations operating in the digital age. Businesses use email to communicate internally with staff and externally with their customers, clients, partners, and supply chain. Behind these huge numbers are a small number of email service providers (such as Microsoft, Google, and Rackspace) that account for the majority of all emails sent. This presents a potentially disastrous risk to the availability of this essential service if one was to suffer an outage as the result of a cyber-attack.A cyber-attack on an email service provider lasting hours, days or weeks and the resulting outage would lead to a substantial financial impact on a (re)insurance carrier. The key characteristics of this type of cyber catastrophe are high severity and low frequency, meaning, an event that does not occur regularly but entails great damage potential, effecting numerous businesses and leading to multiple claims on a (re) insurance carrier at a single point in time.âThe financial damage caused by a cyber catastrophe, such as an email outage, could also manifest through silent risk. Regulators are increasing requirements to quantify this potential silent cyber risk. In January 2019 the PRA(Prudential Regulation Authority) that regulates the UK Financial Services market (inc. the insurance market) demanded that UK insurance firms should seek risk models and expertise to estimate the potential silent (non-affirmative) cyber exposure across their portfolios and introduce robust mitigation strategies for limiting any potential risks.âThis report examines an attack on an email service provider in the UK leading to a service outage resulting from a single point of failure, an event that can lead to financial damage and claims due to affirmative cyber coverage. In this report the authors utilized Kovrrâs ability to quantify potential exposure to cyber catastrophes based on the composition of specific portfolios. Kovrrâs predictive modeling platform was used to map the underlying technologies and services used by the insured companies, enabling an understanding of the potential accumulation risks that are derived from the aggregation of their network of utilized technologies and service providers.âData Wipe Case Study: VFEmail.netOn the 11th February, 2019, hackers breached the servers of the email provider VFEmail.net and deleted all the data from its US servers, destroying all US customers data in the process. Users withVFEmail accounts were faced with empty inboxes and left with no recovery backup options. This was not the first occasion that VFEmail had been targeted. In 2015, VFEmail suffered a DDoS (DistributedDenial of Service) attack after the owner declined to pay a ransom demand from an online extortion group. The company was also forced to find a new hosting provider after a series of DDoS attacks in 2017.âAnatomy Of An AttackAn attack on an email service provider, larger thanVFEmail, could result in critical data being held hostage, altered or destroyed for multiple organizations. This analysis reflects the financial loss resulting from this large-scale business interruption event and the insured loss due to insurance claims that would be triggered in the event of an email service provider outage. In order to perform this analysis, we simulated multiple events includi | Malware Tool Vulnerability | ★★★ | ||
| 2020-03-20 11:02:57 | Linux tool developed by Google to tackle USB keystroke attacks (lien direct) | Google has developed a tool for Linux machines that combats USB keystroke injection attacks by flagging suspicious keystroke speeds and blocking devices classified as malicious. Keystroke injection attacks can execute malicious commands via a thumb drive connected to a host machine, by running code that mimics keystrokes entered by a human user. Source: Daily Swig | Tool | |||
| 2020-03-19 17:25:13 | Comprehensive Guide to tcpdump (Part 2) (lien direct) | In the previous article of tcpdump, we learned about some basic functionalities of this amazing tool called tcpdump. If you haven't check until now, click here. Hence, in this part, we will cover some of the advance options and data types. So that we can analyze our data traffic in a much faster way. Table... Continue reading → | Tool | |||
| 2020-03-19 16:50:26 | Comprehensive Guide to tcpdump (Part 1) (lien direct) | In this article, we are going to learn about tcpdump. It is a powerful command-line tool for network packet analysis. Tcpdump helps us troubleshoot the network issues as well as help us analyze the working of some security tools. Table of Content Introduction Available Options List of interfaces Default working Capturing traffic of a particular... Continue reading → | Tool | |||
| 2020-03-19 07:00:00 | Objective by the Sea 3.0 (lien direct) | The world's only Mac and iOS security conference returned home to Maui last week, with some of the best minds in Apple security research coming together for a few days of learning, training, information sharing, and tool demos. The conference is a truly one-of-a-kind event, and not only strengthens the Mac security community but also allows students and younger researchers to network with some of the top experts in their field. ... | Tool |
To see everything:
Our RSS (filtrered)
