What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2020-01-28 10:37:16 | Cyber Threat Trends Dashboard (lien direct) | Marco Ramilli published the Cyber Threat Trends Dashboard, a useful tool that will allow us to better understand most active threats in real time. Introduction Information sharing is one of the most important activity that cybersecurity researchers do on daily basis. Thanks to “infosharing” activities it is possible to block or, in specific cases, to […] | Tool Threat | |||
| 2020-01-27 13:00:00 | Tinder Swipes Right on AI to Help Stop Harassment (lien direct) | The dating app says its new machine learning tool can help flag potentially offensive messages and encourage more users to report inappropriate behavior. | Tool | |||
| 2020-01-24 13:20:30 | Google: Flaws in Apple\'s privacy tool could enable tracking (lien direct) | Safari's anti-tracking feature could apparently give access to users' browsing habits | Tool | |||
| 2020-01-23 20:47:00 | Glassdoor offers new mobile device tool for job seekers (lien direct) | Mobile job applications are on the rise, and this new feature makes it easier to do from smartphones. | Tool | |||
| 2020-01-23 11:40:45 | A free tool for detecting Shitrix-related compromises on your business network (lien direct) | Citrix has announced that it has teamed up with security researchers at FireEye to produce a free forensic tool which can help your business hunt for potential Indicators of Compromise related to the CVE-2019-19781 vulnerability. | Tool | |||
| 2020-01-22 12:01:57 | (Déjà vu) Panorays And Hysolate Comment On New NIST 1.0 Privacy Framework (lien direct) | The National Institute of Standards and Technology (NIST) just released its first version of its privacy framework, a tool to give organizations guidance on how to manage risks and be in compliance with new privacy laws. The ISBuzz Post: This Post Panorays And Hysolate Comment On New NIST 1.0 Privacy Framework | Tool | |||
| 2020-01-21 14:00:00 | FUD-free analysis: Natural language processing (NLP) (lien direct) | If you follow me on Medium or Twitter, you may already be aware. Still, if you don’t (I assure you that you’re missing out), I have been researching several technologies in preparation for an OPSEC/Anti-OSINT tool that I am crafting. I am using this tool as a means to push myself harder to learn something new that I can apply professionally. I am also doing this to be able to make a positive difference in the world. Notably, I am explicitly trying to learn Machine Learning and Natural Language Processing (NLP) in Python and R. When we hear terms like Advanced Persistent, Next-Generation, Machine Learning, Artificial Intelligence (AI), Machine Learning (ML), Single Pane of Glass, etc. from a vendor, we typically think it’s hype or FUD. Talking about the vendor FUD phrases is ironic because my blog and podcast were called Advanced Persistent Security. Often, we are correct. I set off on the journey to learn about learning to build a tool, but also to understand the technologies. I like to stump salespeople from time to time. Also, if these are the wave of the future, there is no time like the present to get acquainted. So, NLP. What is it? In social engineering circles, it is Neuro-Linguistic Programming. Some (many, if not most) in the scientific community consider it pseudoscience. Regardless, it claims to be able to influence or manipulate people through non-verbal cues from the eyes or touching someone (cringe) or other means. That is not the NLP that I am working on learning. Natural Language Processing, the more scientific NLP, is a marriage of various disciplines: computer science, data science (including AI and ML), and linguistics. NLP allows libraries and code to read the language as it is written or spoken by humans (naturally, hence the name). When applying slang, pidgins, and dialects, it will “learn” to recognize and respond to them. Also adjacent to NLP is OCR or Optical Character Recognition. OCR is the means to read data from a document in a non-text format (i.e., pictures, PDF, or Word documents). Having the ability to read the data allows you to open a PDF with a script (perhaps written in Python) and read it, make sense of it, and act as scripted. Why is this important to InfoSec, and what do we do with it? We could use this in log analysis, network monitoring, analyzing phishing emails, and my personal favorite, OSINT, to name a few. Within log analysis, NLP could be applied to gain further intelligence from logs without writing ridiculously long regular expressions (REGEX) via “learning” the context of the data and what is being sought. This would likely be in parallel with some Machine Learning, but it is a start. From the ML perspective, it would probably need to utilize supervised or semi-supervised learning with online entry vice unsupervised or reinforcement learning. The online means that it would read the data more closely to real-time than by ingesting a defined dataset. The supervision of learning refers to telling the “machine” whether it was correct or not. In some instances of learning logs, unsupervised learning could be useful in determining indicators of compromise or adversarial TTPs based on log data in two sets: breached (event data) and non-breached data. Reinforcement training would be more applicable for tuning and improvement. Back to NLP, the same concepts apply in network monitoring as log analysis, except it would be network traffic and PCAPs being analyzed. PCAP analysis with NLP and ML may be better suited for analyzing a user’s beha | Tool Threat | |||
| 2020-01-21 07:13:59 | NIST releases version 1.0 of the Privacy Framework (lien direct) | The NIST released version 1.0 of Privacy Framework, it is a tool designed to help organizations to manage privacy risks. The National Institute of Standards and Technology (NIST) has published the release version 1.0 of its privacy framework. The Framework is a voluntary tool that can be used by organizations to manage risks in compliance […] | Tool | |||
| 2020-01-20 04:22:32 | Evaluating Your Security Controls? Be Sure to Ask the Right Questions (lien direct) | Testing security controls is the only way to know if they are truly defending your organization. With many different testing frameworks and tools to choose from, you have lots of options.
But what do you specifically want to know? And how are the findings relevant to the threat landscape you face at this moment?
"Decide what you want to know and then choose the best tool for the job." |
Tool Threat | |||
| 2020-01-17 10:32:23 | CVE-2019-19470: Rumble in the Pipe (lien direct) | This blog post describes an interesting privilege escalation from a local user to SYSTEM for a well-known local firewall solution called TinyWall in versions prior to 2.1.13. Besides a .NET deserialization flaw through Named Pipe communication, an authentication bypass is explained as well. Introduction TinyWall is a local firewall written in .NET. It consists of a single executable that runs once as SYSTEM and once in the user context to configure it. The server listens on a Named Pipe for messages that are transmitted in the form of serialized object streams using the well-known and beloved BinaryFormatter. However, there is an additional authentication check that we found interesting to examine and that we want to elaborate here a little more closely as it may also be used by other products to protect themselves from unauthorized access. For the sake of simplicity the remaining article will use the terms Server for the receiving SYSTEM process and Client for the sending process within an authenticated user context, respectively. Keep in mind that the authenticated user does not need any special privileges (e.g. SeDebugPrivilege) to exploit this vulnerability described.Named Pipe Communication Many (security) products use Named Pipes for inter-process communication (e.g. see Anti Virus products). One of the advantages of Named Pipes is that a Server process has access to additional information on the sender like the origin Process ID, Security Context etc. through Windows' Authentication model. Access to Named Pipes from a programmatic perspective is provided through Windows API calls but can also be achieved e.g. via direct filesystem access. The Named Pipe filessystem (NPFS) is accessible via the Named Pipe's name with a prefix \\.\pipe\.The screenshot below confirms that a Named Pipe "TinyWallController" exists and could be accessed and written into by any authenticated user. Talking to SYSTEMFirst of all, let's look how the Named Pipe is created and used. When TinyWall starts, a PipeServerWorker method takes care of a proper Named Pipe setup. For this the Windows API provides System.IO.Pipes.NamedPipeServerStream with one of it's constructors taking a parameter of System.IO.Pipes.PipeSecurity. This allows for fine-grained access control via System.IO.PipeAccessRule objects using SecurityIdentifiers and alike. Well, as one can observe from the first screenshot above, the only restriction seems to be that the Client process has to be executed in an authenticated user context which doesn't seem to be a hard restriction after all. Talking to SYSTEMFirst of all, let's look how the Named Pipe is created and used. When TinyWall starts, a PipeServerWorker method takes care of a proper Named Pipe setup. For this the Windows API provides System.IO.Pipes.NamedPipeServerStream with one of it's constructors taking a parameter of System.IO.Pipes.PipeSecurity. This allows for fine-grained access control via System.IO.PipeAccessRule objects using SecurityIdentifiers and alike. Well, as one can observe from the first screenshot above, the only restriction seems to be that the Client process has to be executed in an authenticated user context which doesn't seem to be a hard restriction after all.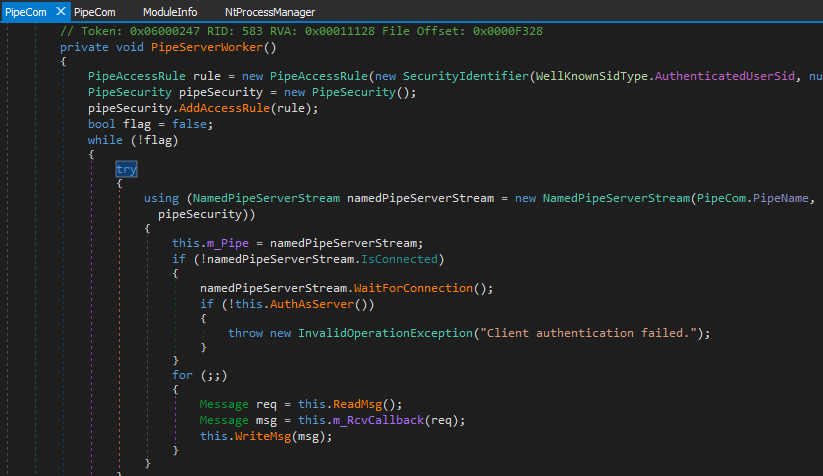 But as it turned out But as it turned out |
Tool Vulnerability | |||
| 2020-01-16 13:00:56 | Use the Correct Tool for the Job: Mobile Management Solutions are Not Security! (lien direct) | By Yael Macias, Product Marketing Manager, Threat Prevention In the past decade, the world went mobile. And businesses had to catch up and adapt to this trend, by allowing their employees to access corporate assets and seamlessly work from their mobile devices. For several years now, organizations have used mobile management solutions (UEM, EMM, MDM,… | Tool Threat | |||
| 2020-01-16 10:07:24 | Broadening the Scope: A Comprehensive View of Pen Testing (lien direct) | Penetration tests have long been known as a critical security tool that exposes security weaknesses through simulated attacks on an organization's IT environments. These test results can help prioritize weaknesses, providing a road-map towards remediation.
However, the results are also capable of doing even more. They identify and quantify security risk, and can be used as a keystone in |
Tool | |||
| 2020-01-16 00:01:45 | Smashing Security #161: Love, lucky dips, and 23andMe (lien direct) | The man who hacked the UK National Lottery didn’t end up a winner, Japanese Love hotel booking tool suffers a data breach, and just what is 23andMe planning to do with your DNA? All this and much more is discussed in the latest edition of the award-winning “Smashing Security” podcast by computer security veterans Graham Cluley and Carole Theriault, joined this week by Thom Langford. | Tool | ★★★★★ | ||
| 2020-01-15 14:00:00 | Alien Labs 2019 Analysis of Threat Groups Molerats and APT-C-37 (lien direct) |
In 2019, several industry analyst reports confused the threat groups Molerats and APT-C-37 due to their similarity, and this has led to some confusion and inaccuracy of attribution.
For example, both groups target the Middle East and North Africa region (with a special emphasis on Palestine territories). And, they both approach victims through the use of phishing emails that contain decoy documents (mostly in Arabic) and contain themes concerning the political situation in the area.
To improve understanding of the differences and similarities of the two groups (as well as the links between them), we at Alien Labs™ are providing an analysis of their 2019 activity.
 A recent spear-phishing document from Molerats
APT-C-37 Overview
APT-C-37, also known as Pat-Bear or the Syrian Electronic Army (SEA), was first seen in October 2015 targeting members of a terrorist organization. Since 2015, however, APT-C-37 has broadened their objectives to include government agencies, armed forces leadership, media organizations, political activists, and diplomats. The group mostly targets victims in Western countries, with the intent of defacing their websites and social accounts while leaving a public footprint after hacking one of their victims.
In previous attacks, APT-C-37 targeted Windows and Android systems, utilizing popular commercial remote access trojans (RATs) such as DroidJack, SpyNote, njRAT, SSLove, and H-Worm.
Technical Analysis: APT-C-37 2019
June 2019: APT-C-37 released an Android app named after the instant messaging software “WhatsApp” as an espionage tool to reportedly spy on the Syrian opposition forces. The app was capable of installing the SSLove RAT to pull private information from the phone and exfiltrating it to a remote location.
Molerats Overview
Molerats has been present in the cybercriminal landscape since 2012. In an analysis released by the Kaspersky’s GReAT (Global Research & Analysis Team) earlier this year on the Gaza Hacker Team and their various subgroups, Kaspersky concluded that Molerats is Gaza Cybergang “Group1.” The report also concluded that Molerats (i.e. Cybergang Group 1) operates with a lower level of sophistication than other groups within the Gaza Hacker Team. In addition, a 2016 article in Security Week reported that one of Molerats campaigns (October 2016) heavily used popular RATs like NjRat and H-Worm (aka Houdini).
Technical Analysis: Molerats 2019
October 2019: In Molerats’ October operation, the attack was distributed as a phishing campaign in the Middle East. Emails included a Microsoft Word file attachment with the title “Daily report on the most important Palestinian developments for the day 9-9-2019.doc” — content that spoke to the political situation in Palestine. When a victim opened the attachment, the malware performed the following:
Displayed the Microsoft Word doc
A recent spear-phishing document from Molerats
APT-C-37 Overview
APT-C-37, also known as Pat-Bear or the Syrian Electronic Army (SEA), was first seen in October 2015 targeting members of a terrorist organization. Since 2015, however, APT-C-37 has broadened their objectives to include government agencies, armed forces leadership, media organizations, political activists, and diplomats. The group mostly targets victims in Western countries, with the intent of defacing their websites and social accounts while leaving a public footprint after hacking one of their victims.
In previous attacks, APT-C-37 targeted Windows and Android systems, utilizing popular commercial remote access trojans (RATs) such as DroidJack, SpyNote, njRAT, SSLove, and H-Worm.
Technical Analysis: APT-C-37 2019
June 2019: APT-C-37 released an Android app named after the instant messaging software “WhatsApp” as an espionage tool to reportedly spy on the Syrian opposition forces. The app was capable of installing the SSLove RAT to pull private information from the phone and exfiltrating it to a remote location.
Molerats Overview
Molerats has been present in the cybercriminal landscape since 2012. In an analysis released by the Kaspersky’s GReAT (Global Research & Analysis Team) earlier this year on the Gaza Hacker Team and their various subgroups, Kaspersky concluded that Molerats is Gaza Cybergang “Group1.” The report also concluded that Molerats (i.e. Cybergang Group 1) operates with a lower level of sophistication than other groups within the Gaza Hacker Team. In addition, a 2016 article in Security Week reported that one of Molerats campaigns (October 2016) heavily used popular RATs like NjRat and H-Worm (aka Houdini).
Technical Analysis: Molerats 2019
October 2019: In Molerats’ October operation, the attack was distributed as a phishing campaign in the Middle East. Emails included a Microsoft Word file attachment with the title “Daily report on the most important Palestinian developments for the day 9-9-2019.doc” — content that spoke to the political situation in Palestine. When a victim opened the attachment, the malware performed the following:
Displayed the Microsoft Word doc |
Malware Tool Threat Guideline | APT-C-23 | ||
| 2020-01-13 10:37:27 | \'Rosegold\' National Lottery hacker steals £5, lands prison sentence (lien direct) | The Sentry MBA brute-force account cracking tool was used to compromise user accounts. | Tool | ★★★★★ | ||
| 2020-01-08 15:05:19 | Oracle using data science to give retailers an intelligence edge (lien direct) | A new tool will use analytics to help retailers better understand the characteristics of their best customers. | Tool | |||
| 2020-01-07 16:21:48 | How to install a bot on Slack (lien direct) | Learn how to make onboarding easier with the help of the Donut tool for Slack. | Tool | |||
| 2020-01-07 07:08:10 | Forensic Investigation of Social Networking Evidence using IEF (lien direct) | In this article, we will learn about this amazing forensic tool called Magnet Internet Evidence finder (Magnet IEF) which is used to recover or extract evidence from the various data source of the system and then integrate them into a single case file for analysis and reporting. Table of Content Introduction Features of Magnet IEF... Continue reading → | Tool | |||
| 2020-01-04 08:22:40 | (Déjà vu) Windows for Pentester: BITSAdmin (lien direct) | In this article, we are going to describe the utility of the BITSAdmin tool and how vital it is in Windows Penetration Testing. TL; DR BITSAdmin is a tool preinstalled on Windows OS that can be used to download malicious files. It is one of the Living Off Land (LOL) Binaries. Disclaimer The main objective... Continue reading → | Tool | |||
| 2019-12-29 09:25:34 | A previously undetected FIN7 BIOLOAD loader drops new Carbanak Backdoor (lien direct) | Experts uncovered a new tool dubbed BIOLOAD used by the FIN7 cybercrime group used as a dropper for a new variant of the Carbanak backdoor. Security experts from Fortinet’s enSilo have discovered a new loader, dubbed BIOLOAD, associated with the financially-motivated group FIN7. The group that has been active since late 2015 targeted businesses worldwide […] | Tool | |||
| 2019-12-27 11:31:00 | FIN7 Hackers\' BIOLOAD Malware Drops Fresher Carbanak Backdoor (lien direct) | Malware researchers have uncovered a new tool used by the financially-motivated cybercriminal group known as FIN7 to load newer builds of the Carbanak backdoor. [...] | Malware Tool | |||
| 2019-12-23 12:00:20 | Slowing Data Security Tool Sprawl in a Hybrid Multicloud World (lien direct) | Having centralized visibility and control over the organization's data security and compliance posture helps security teams take a comprehensive approach to hybrid multicloud data protection. | Tool | |||
| 2019-12-19 15:06:54 | WiFi-Dumper – Dump WiFi Profiles and Cleartext Passwords (lien direct) |  WiFi-Dumper is an open-source Python-based tool to dump WiFi profiles and cleartext passwords of the connected access points on a Windows machine. This tool will help you in a Wifi penetration testing and could also be useful when performing red team assessments or internal infrastructure engagements.
Each option in the tool generates the “.txt” file as an output, if you run the tool multiple times, the output gets appended to the previous results.
Read the rest of WiFi-Dumper – Dump WiFi Profiles and Cleartext Passwords now! Only available at Darknet. WiFi-Dumper is an open-source Python-based tool to dump WiFi profiles and cleartext passwords of the connected access points on a Windows machine. This tool will help you in a Wifi penetration testing and could also be useful when performing red team assessments or internal infrastructure engagements.
Each option in the tool generates the “.txt” file as an output, if you run the tool multiple times, the output gets appended to the previous results.
Read the rest of WiFi-Dumper – Dump WiFi Profiles and Cleartext Passwords now! Only available at Darknet.
|
Tool | |||
| 2019-12-18 10:17:56 | (Déjà vu) Vulnerable Windows PCs identified with New BlueKeep Scanner (lien direct) | A new scanning tool is now available for checking if your computer is vulnerable to the BlueKeep security issue in Windows Remote Desktop Services. Despite Microsoft rolling out a patch in mid-May, there are tens of thousands of devices exposing a Remote Desktop Protocol (RDP) service to the public internet. Source: Bleeping Computer | Tool | |||
| 2019-12-18 03:32:00 | New BlueKeep Scanner Lets You Find Vulnerable Windows PCs (lien direct) | A new scanning tool is now available for checking if your computer is vulnerable to the BlueKeep security issue in Windows Remote Desktop Services. [...] | Tool | |||
| 2019-12-11 14:00:00 | Google Cloud Platform security monitoring with USM Anywhere™ (lien direct) | According to a 2019 Cyber Security Report published by the International Information System Security Certification Consortium, 93 percent of organizations say they are concerned about cloud security and 28 percent admit to having experienced cloud security incidents during the past year. The reality is, most companies lack the specialized knowledge and skills needed to provide that customer data stored in the cloud is protected Cloud service providers (CSPs) do provide extra security layers, such as automating threat detection, with the intent of making their customers feel more confident in the security of the cloud. However, the number of cloud breaches that are being reported shows that CSPs and organizations alike continue to struggle with cloud security. Much of this is due to a lack of unified visibility not just in the cloud, but across an organization’s entire network, siloed teams and technologies, lack of threat intelligence, and partnerships with third-parties whose security controls are not up to snuff. To address these challenges, many in the industry are advocating for organizations to simplify and unify their security approach, i.e. bring as many controls as possible into a single solution in order to break down the silos between security teams and technologies and to give greater visibility across the organization. We at AT&T Cybersecurity help organizations to accomplish this with our Unified Security Management™ (USM) Anywhere platform. Of course, the effectiveness of any security solution is largely determined by the threat intelligence underpinning it. In any environment, we need to identify the common tactics, techniques, and procedures (TTPs) adversaries are using in their attacks. Below, we provide an overview of the latest threat intelligence from Alien Labs™ for Google Cloud Platform (GCP), which helps security practitioners to discover issues in their cloud workloads and detect adversaries exploiting attack vectors commonly seen in cloud environments. Google Cloud Platform integration in USM This summer, AT&T Cybersecurity launched the USM Anywhere™ integration with GCP. Through the USM Anywhere Alien App for GCP, USM can now consume all logging information managed by the Stackdriver utility in a configurable and intuitive way. Google Cloud Platform logs are provided through three major channels: Audit Logs. Record all events impacting objects within the environment. These logs are used to monitor any cloud assets, presenting a solid baseline for security detection. VPC Flow Logs. Half way between resource monitoring and cloud infrastructure security, these logs are the delights of NIDS enthusiasts. Firewall Logs. These help with auditing firewall rules events, and they are useful in detecting risky open ports and other configuration issues. In USM, these channels are processed by different plugins, which extract pieces of intelligence and map them to variables that are easy to steer into orchestration rules. The correlation engine allows for the combination of detections from different channels into a single orchestration rule, scaling GCP security to a new level. To prevent an intrusion from being recorded or triggering a notification, adversaries may try to disable audit logging once they get the necessary permissions. To protect against that, the product has out of the box correlation rules to generate an alert if any of the logging features is disabled. | Tool Threat Guideline | Uber | ||
| 2019-12-07 17:48:38 | Amazon battles leaky S3 buckets with a new security tool (lien direct) | A new AWS feature is supposed to help avoid accidental misconfigurations that could result in sensitive data being exposed, a company’s brand being damaged, and even – potentially – put its customers at risk. Read more in my article on the Bitdefender Business Insights blog. | Tool | |||
| 2019-12-06 19:25:22 | TeamViewer unveils new patch management system (lien direct) | The new tool will provide IT departments with system-wide visibility of all the patches needed. | Tool | |||
| 2019-12-05 12:34:51 | China used the Great Cannon DDoS Tool against forum used by Hong Kong protestors (lien direct) | China is accused to have used the “Great Cannon” DDoS tool to launch attacks against LIHKG, a forum used by Hong Kong residents to organize protests. The Great Cannon Distributed Denial of Service (DDoS) tool was used again by the Chinese government, this time it was used to target the LIHKG forum used by Hong Kong protesters to […] | Tool | |||
| 2019-12-04 15:28:00 | The “Great Cannon” has been deployed again (lien direct) |
Summary
The Great Cannon is a distributed denial of service tool (“DDoS”) that operates by injecting malicious Javascript into pages served from behind the Great Firewall. These scripts, potentially served to millions of users across the internet, hijack the users’ connections to make multiple requests against the targeted site. These requests consume all the resources of the targeted site, making it unavailable:
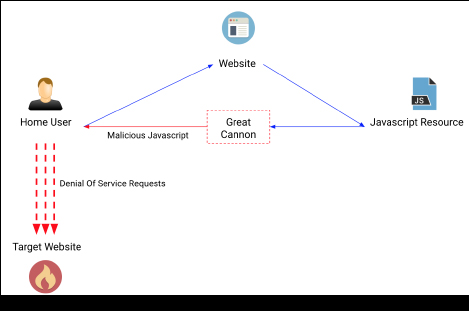 Figure 1: Simplified diagram of how the Great Cannon operates
The Great Cannon was the subject of intense research after it was used to disrupt access to the website Github.com in 2015. Little has been seen of the Great Cannon since 2015. However, we’ve recently observed new attacks, which are detailed below.
Most recent attacks against LIHKG
The Great Cannon is currently attempting to take the website LIHKG offline. LIHKG has been used to organize protests in Hong Kong. Using a simple script that uses data from UrlScan.io, we identified new attacks likely starting Monday November 25th, 2019.
Websites are indirectly serving a malicious javascript file from either:
http://push.zhanzhang.baidu.com/push.js; or
http://js.passport.qihucdn.com/11.0.1.js
Normally these URLs serve standard analytics tracking scripts. However, for a certain percentage of requests, the Great Cannon swaps these on the fly with malicious code:
Figure 1: Simplified diagram of how the Great Cannon operates
The Great Cannon was the subject of intense research after it was used to disrupt access to the website Github.com in 2015. Little has been seen of the Great Cannon since 2015. However, we’ve recently observed new attacks, which are detailed below.
Most recent attacks against LIHKG
The Great Cannon is currently attempting to take the website LIHKG offline. LIHKG has been used to organize protests in Hong Kong. Using a simple script that uses data from UrlScan.io, we identified new attacks likely starting Monday November 25th, 2019.
Websites are indirectly serving a malicious javascript file from either:
http://push.zhanzhang.baidu.com/push.js; or
http://js.passport.qihucdn.com/11.0.1.js
Normally these URLs serve standard analytics tracking scripts. However, for a certain percentage of requests, the Great Cannon swaps these on the fly with malicious code:
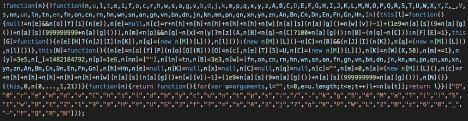 Figure 2: Malicious code served from the Great Cannon
The code attempts to repeatedly request the following resources, in order to overwhelm websites and prevent them from being accessible:
http://lihkg.com/
https://i.loli.net/2019/09/29/hXHglbYpykUGIJu.gif?t=
https://na.cx/i/XibbJAS.gif?t=
https://na.cx/i/UHr3Dtk.gif?t=
https://na.cx/i/9hjf7rg.gif?t=
https://na.cx/i/qKE4P2C.gif?t=
https://na.cx/i/0Dp4P29.gif?t=
https://na.cx/i/mUkDptW.gif?t=
https://na.cx/i/ekL74Sn.gif?t=
https://i.ibb.co/ZBDcP9K/LcSzXUb.gif?t=
https://66.media.tumblr.com/e06eda7617fb1b98cbaca0edf9a427a8/tumblr_oqrv3wHXoz1sehac7o1_540.gif?t=
https://na.cx/i/6hxp6x9.gif?t=
https://live.staticflickr.com/65535/48978420208_76b67bec15_o.gif?t=
https://i.lihkg.com/540/https://img.eservice-hk.net/upload/2018/08/09/181951_60e1e9bedea42535801bc785b6f48e7a.gif?t=
https://na.cx/i/E3sYryo.gif?t=
https://na.cx/i/ZbShS2F.gif?t=
https://na.cx/i/LBppBac.gif?t=
http://i.imgur.com/5qrZMPn.gif?t=
https://na.cx/i/J3q35jw.gif?t=
https://na.cx/i/QR7JjSJ.gif?t=
https://na.cx/i/haUzqxN.gif?t=
https://na.cx/i/3hS5xcW.gif?t=
https://na.cx/i/z340DGp.gif?t=
https://luna.komica
Figure 2: Malicious code served from the Great Cannon
The code attempts to repeatedly request the following resources, in order to overwhelm websites and prevent them from being accessible:
http://lihkg.com/
https://i.loli.net/2019/09/29/hXHglbYpykUGIJu.gif?t=
https://na.cx/i/XibbJAS.gif?t=
https://na.cx/i/UHr3Dtk.gif?t=
https://na.cx/i/9hjf7rg.gif?t=
https://na.cx/i/qKE4P2C.gif?t=
https://na.cx/i/0Dp4P29.gif?t=
https://na.cx/i/mUkDptW.gif?t=
https://na.cx/i/ekL74Sn.gif?t=
https://i.ibb.co/ZBDcP9K/LcSzXUb.gif?t=
https://66.media.tumblr.com/e06eda7617fb1b98cbaca0edf9a427a8/tumblr_oqrv3wHXoz1sehac7o1_540.gif?t=
https://na.cx/i/6hxp6x9.gif?t=
https://live.staticflickr.com/65535/48978420208_76b67bec15_o.gif?t=
https://i.lihkg.com/540/https://img.eservice-hk.net/upload/2018/08/09/181951_60e1e9bedea42535801bc785b6f48e7a.gif?t=
https://na.cx/i/E3sYryo.gif?t=
https://na.cx/i/ZbShS2F.gif?t=
https://na.cx/i/LBppBac.gif?t=
http://i.imgur.com/5qrZMPn.gif?t=
https://na.cx/i/J3q35jw.gif?t=
https://na.cx/i/QR7JjSJ.gif?t=
https://na.cx/i/haUzqxN.gif?t=
https://na.cx/i/3hS5xcW.gif?t=
https://na.cx/i/z340DGp.gif?t=
https://luna.komica |
Tool Threat | |||
| 2019-12-03 17:12:11 | NBlog Dec 3 - infosec driving principles (lien direct) | In an interview for CIO Dive, Maersk's recently-appointed CISO Andy Powell discussed aligning the organization with these five 'key operating principles': "The first is trust. The client has got to trust us with their data, to trust us to look at their business. So we've got to build trust through the cybersecurity solutions that we put in place. That is absolutely fundamental. So client trust, client buy-in has been fundamental to what we tried to drive as a key message. The second is resilience. Because you've got to have resilient systems because clients won't give you business if you're not resilient ... The third really is around the fact that security is everybody's responsibility. And we push that message really hard across the company … be clear about what you need to do and we train people accordingly. ...The fourth one really is accountability of security and I have pushed accountability for cyber risk to the business. ... And the final piece, and this has been one of the big call outs of my team to everybody, is that security is a benefit, not a burden. The reason I say that is people's perception is that security will slow things down, will get in the way ... the reality is that if you involve security early enough, you can build solutions that actually attract additional clients."Fair enough Andy. I wouldn't particularly quarrel with any of them, but as to whether they would feature in my personal top-five I'm not so sure. Here are five others they'd be competing against, with shipping-related illustrations just for fun:Governance involves structuring, positioning, setting things up and guiding the organization in the right overall direction - determining then plotting the optimal route to the ship's ultimate destination, loading up with the right tools, people and provisions. Corporate governance necessarily involves putting things in place for both protecting and exploiting information, a vital and valuable yet vulnerable business asset;Information is subject to risks that can and probably should be managed proactively, just as a ship's captain doesn't merely accept the inclement weather and various other hazards but, where appropriate, actively mitigates or avoids them, dynamically reacting and adjusting course as things change;Flexibility and responsiveness, along with resilience and ro "The first is trust. The client has got to trust us with their data, to trust us to look at their business. So we've got to build trust through the cybersecurity solutions that we put in place. That is absolutely fundamental. So client trust, client buy-in has been fundamental to what we tried to drive as a key message. The second is resilience. Because you've got to have resilient systems because clients won't give you business if you're not resilient ... The third really is around the fact that security is everybody's responsibility. And we push that message really hard across the company … be clear about what you need to do and we train people accordingly. ...The fourth one really is accountability of security and I have pushed accountability for cyber risk to the business. ... And the final piece, and this has been one of the big call outs of my team to everybody, is that security is a benefit, not a burden. The reason I say that is people's perception is that security will slow things down, will get in the way ... the reality is that if you involve security early enough, you can build solutions that actually attract additional clients."Fair enough Andy. I wouldn't particularly quarrel with any of them, but as to whether they would feature in my personal top-five I'm not so sure. Here are five others they'd be competing against, with shipping-related illustrations just for fun:Governance involves structuring, positioning, setting things up and guiding the organization in the right overall direction - determining then plotting the optimal route to the ship's ultimate destination, loading up with the right tools, people and provisions. Corporate governance necessarily involves putting things in place for both protecting and exploiting information, a vital and valuable yet vulnerable business asset;Information is subject to risks that can and probably should be managed proactively, just as a ship's captain doesn't merely accept the inclement weather and various other hazards but, where appropriate, actively mitigates or avoids them, dynamically reacting and adjusting course as things change;Flexibility and responsiveness, along with resilience and ro |
Tool Guideline | NotPetya | ||
| 2019-12-03 16:40:41 | Notorious spy tool taken down in global operation (lien direct) | IM-RAT, which could be had for as little as US$25, was bought by nearly 15,000 people | Tool | ★★★ | ||
| 2019-12-03 16:00:00 | Analyse exceller & # 8211;Conseils et astuces pour analyser les données avec Microsoft Excel Excelerating Analysis – Tips and Tricks to Analyze Data with Microsoft Excel (lien direct) |
Les enquêtes sur la réponse aux incidents n'impliquent pas toujours des artefacts standard basés sur l'hôte avec des outils d'analyse et d'analyse entièrement développés.Chez FireEye Mandiant, nous rencontrons fréquemment des incidents qui impliquent un certain nombre de systèmes et de solutions qui utilisent des données de journalisation ou d'artefacts personnalisés.La détermination de ce qui s'est passé dans un incident consiste à plonger dans le type de données qui nous sont présentés, à l'apprendre et à développer un moyen efficace d'analyser les preuves importantes.
L'un des outils les plus efficaces pour effectuer ce type d'analyse est celui qui est dans presque tout le monde \'s Toolkit
Incident response investigations don\'t always involve standard host-based artifacts with fully developed parsing and analysis tools. At FireEye Mandiant, we frequently encounter incidents that involve a number of systems and solutions that utilize custom logging or artifact data. Determining what happened in an incident involves taking a dive into whatever type of data we are presented with, learning about it, and developing an efficient way to analyze the important evidence. One of the most effective tools to perform this type of analysis is one that is in almost everyone\'s toolkit |
Tool | ★★★ | ||
| 2019-12-03 09:18:47 | Windows for Pentester: Certutil (lien direct) | In this article, we are going to describe the utility of Certutil tool and how vital it is in Windows Penetration Testing. TL; DR Certutil is a preinstalled tool on Windows OS that can be used to download malicious files and evade Antivirus. It is one of the Living Off Land (LOL) Binaries. Disclaimer The... Continue reading → | Tool | |||
| 2019-12-02 07:09:50 | truffleHog – Search Git for High Entropy Strings with Commit History (lien direct) |  truffleHog is a Python-based tool to search Git for high entropy strings, digging deep into commit history and branches. This is effective at finding secrets accidentally committed.
truffleHog previously functioned by running entropy checks on git diffs. This functionality still exists, but high signal regex checks have been added, and the ability to surpress entropy checking has also been added.
truffleHog --regex --entropy=False https://github.com/dxa4481/truffleHog.git
or
truffleHog file:///user/dxa4481/codeprojects/truffleHog/
truffleHog will go through the entire commit history of each branch, and check each diff from each commit, and check for secrets.
Read the rest of truffleHog – Search Git for High Entropy Strings with Commit History now! Only available at Darknet. truffleHog is a Python-based tool to search Git for high entropy strings, digging deep into commit history and branches. This is effective at finding secrets accidentally committed.
truffleHog previously functioned by running entropy checks on git diffs. This functionality still exists, but high signal regex checks have been added, and the ability to surpress entropy checking has also been added.
truffleHog --regex --entropy=False https://github.com/dxa4481/truffleHog.git
or
truffleHog file:///user/dxa4481/codeprojects/truffleHog/
truffleHog will go through the entire commit history of each branch, and check each diff from each commit, and check for secrets.
Read the rest of truffleHog – Search Git for High Entropy Strings with Commit History now! Only available at Darknet.
|
Tool | |||
| 2019-12-02 06:26:26 | New Facebook Tool Let Users Transfer Their Photos and Videos to Google (lien direct) | Facebook has finally started implementing the open source data portability framework as the first phase of 'Data Transfer Project,' an initiative the company launched last year in collaboration with Google, Apple, Microsoft, and Twitter.
Facebook today announced a new feature that will allow its users to transfer their Facebook photos and videos to their Google Photos accounts-directly and |
Tool | ★★★ | ||
| 2019-11-29 04:41:02 | Europol Shuts Down \'Imminent Monitor\' RAT Operations With 13 Arrests (lien direct) | In a coordinated International law enforcement operation, Europol today announced to shut down the global organized cybercrime network behind Imminent Monitor RAT, yet another hacking tool that allows cybercriminals to gain complete control over a victim's computer remotely.
The operation targeted both buyers and sellers of the IM-RAT (Imminent Monitor Remote Access Trojan), which was sold to |
Tool | ★★★★ | ||
| 2019-11-28 14:30:00 | How to decide when you should DIY or hire a project out (lien direct) | Leaders are often faced with questions on whether they should develop a capability or tool in-house or use outside partners. Here are guidelines for making the call. | Tool Guideline | |||
| 2019-11-25 20:00:00 | Fidl: Bibliothèque de décompilation Ida de Flare \\ FIDL: FLARE\\'s IDA Decompiler Library (lien direct) |
IDA Pro et les décompiler des rayons hexadécimaux font la base de toute boîte à outils pour la recherche en ingénierie inverse et en vulnérabilité.Dans un article de blog précédent, nous avons expliqué comment l'API des rayons hexadécimaux peut être utilisé pour résoudre de petits problèmes bien définis couramment considérés comme faisant partie de l'analyse des logiciels malveillants.Avoir accès à une représentation de code binaire de niveau supérieur fait du décompilateur des rayons hexagonaux un outil puissant pour l'ingénierie inverse.Cependant, l'interaction avec l'API Hexrays et ses sources de données sous-jacentes peut être intimidante, ce qui rend la création de scripts d'analyse générique difficile ou fastidieux.
Ce billet de blog présente le Fla
IDA Pro and the Hex Rays decompiler are a core part of any toolkit for reverse engineering and vulnerability research. In a previous blog post we discussed how the Hex-Rays API can be used to solve small, well-defined problems commonly seen as part of malware analysis. Having access to a higher-level representation of binary code makes the Hex-Rays decompiler a powerful tool for reverse engineering. However, interacting with the HexRays API and its underlying data sources can be daunting, making the creation of generic analysis scripts difficult or tedious. This blog post introduces the FLA |
Malware Tool Vulnerability | ★★★ | ||
| 2019-11-25 14:52:48 | Samsung adds two modems to help enable wider 5G rollout (lien direct) | Verizon will be the first customer to buy a tool that supports 5G networks that are easier to enable, smaller in size and more efficient in how they use power. | Tool | |||
| 2019-11-25 10:05:09 | Azure Arc: Managing hybrid cloud deployment (lien direct) | Microsoft's new management tool brings Azure management to any hybrid cloud. | Tool | |||
| 2019-11-22 12:33:34 | Expert Comments On Audit Voting Machine Arlo (lien direct) | The CISA and the DHS's main cyber division announced the launch of Arlo, a new tool to help election and government officials audit voting machines to determine they've been tampered with, and it has already been distributed in six states. The ISBuzz Post: This Post Expert Comments On Audit Voting Machine Arlo | Tool | |||
| 2019-11-21 23:58:53 | CISA and VotingWorks release open source post-election auditing tool (lien direct) | New Arlo open-source tool will help state officials verify electronically-tallied ballots. | Tool | |||
| 2019-11-20 06:35:59 | Ransomware Revival: Troldesh becomes a leader by the number of attacks (lien direct) | Ransomware accounted for over half of all malicious mailings in H1 2019, Troldesh aka Shade being the most popular tool among cybercriminals. Group-IB, a Singapore-based cybersecurity company: ransomware accounted for over half of all malicious mailings in H1 2019, detected and analyzed by Group-IB's Computer Emergency Response Team (CERT-GIB), with Troldesh aka Shade being the most popular tool […] | Ransomware Tool | |||
| 2019-11-19 20:20:14 | NBlog Nov 18 - enough is enough (lien direct) |  Keeping ISO27k Information Security Management Systems tight, constrained within narrow scopes, avoiding unnecessary elaboration, seems an admirable objective. The advantages of ISMS simplicity include having less to design, implement, monitor, manage, maintain, review and audit. There's less to go wrong. The ISMS is more focused, a valuable business tool with a specific purpose rather than a costly overhead. All good. However, that doesn't necessarily mean that it is better to have fewer ISMS documents. In practice, simplifying ISMS documentation generally means combining docs or dispensing with any that are deemed irrelevant. That may not be the best approach for every organization, especially if it goes a step too far.Take information security policies for example. Separate, smaller policy docs are easier to generate and maintain, {re}authorize and {re}circulate individually than a thick monolithic “policy manual”. It's easier for authors, authorisers and recipients to focus on the specific issue/s at hand. That's important from the governance, awareness and compliance perspective. At a basic level, what are the chances of people actually bothering to read the change management/version control/document history info then check out all the individual changes (many of which are relatively insignificant) when yet another updated policy manual update drops into their inbox? In practice, it aint gonna happen, much to the chagrin of QA experts!On the other hand, individual policies are necessarily interlinked, forming a governance mesh: substantial changes in one part can have a ripple effect across the rest, which means someone has the unenviable task of updating and maintaining the entire suite, keeping everything reasonably consistent. Having all the policies in one big document makes maintenance easier for the author/maintainer, but harder for change managers, authorisers and the intended audiences/users. Keeping ISO27k Information Security Management Systems tight, constrained within narrow scopes, avoiding unnecessary elaboration, seems an admirable objective. The advantages of ISMS simplicity include having less to design, implement, monitor, manage, maintain, review and audit. There's less to go wrong. The ISMS is more focused, a valuable business tool with a specific purpose rather than a costly overhead. All good. However, that doesn't necessarily mean that it is better to have fewer ISMS documents. In practice, simplifying ISMS documentation generally means combining docs or dispensing with any that are deemed irrelevant. That may not be the best approach for every organization, especially if it goes a step too far.Take information security policies for example. Separate, smaller policy docs are easier to generate and maintain, {re}authorize and {re}circulate individually than a thick monolithic “policy manual”. It's easier for authors, authorisers and recipients to focus on the specific issue/s at hand. That's important from the governance, awareness and compliance perspective. At a basic level, what are the chances of people actually bothering to read the change management/version control/document history info then check out all the individual changes (many of which are relatively insignificant) when yet another updated policy manual update drops into their inbox? In practice, it aint gonna happen, much to the chagrin of QA experts!On the other hand, individual policies are necessarily interlinked, forming a governance mesh: substantial changes in one part can have a ripple effect across the rest, which means someone has the unenviable task of updating and maintaining the entire suite, keeping everything reasonably consistent. Having all the policies in one big document makes maintenance easier for the author/maintainer, but harder for change managers, authorisers and the intended audiences/users. |
Tool | |||
| 2019-11-19 17:00:00 | Slack\'s open source Nebula overlay network tool can solve multi region connectivity woes (lien direct) | The new point-to-point networking overlay was developed as a replacement to IPsec that allows for multi region connectivity in public cloud, though has broader applications for IoT devices. | Tool | ★★★★★ | ||
| 2019-11-18 18:53:17 | Joan is the office booking tool you need (lien direct) | If you need hardware to help manage the booking of your meeting rooms, Joan may be the ideal solution. | Tool | |||
| 2019-11-15 21:27:48 | How to add container management to Cockpit (lien direct) | The Cockpit web-based admin tool can be extended to include container management. | Tool | |||
| 2019-11-13 14:12:06 | Expert Comments On Why Jailbroken Devices May Threaten Mobile Financial Services (lien direct) | Banks and financial institutions have more reason to worry about the threat of jailbroken devices attempting to access their mobile financial services, with the release of the new Checkra1n jailbreak tool this week. The ISBuzz Post: This Post Expert Comments On Why Jailbroken Devices May Threaten Mobile Financial Services | Tool Threat | |||
| 2019-11-12 19:43:19 | How to batch rename files in Windows 10 with the PowerToys PowerRename tool (lien direct) | Learn how to use the PowerToys PowerRename tool to rename multiple files in one shot. | Tool |
To see everything:
Our RSS (filtrered)
