What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2020-03-19 11:35:31 | Experts Insight On NutriBullet.com Magecart Attack (lien direct) | Researchers have uncovered a Magecart Group 8 attack against blender vendor NutriBullet that installed credit card stealing malware on the company's website. Security experts provide insight into this attack. The ISBuzz Post: This Post Experts Insight On NutriBullet.com Magecart Attack | Malware | APT 17 | ★★★★ | |
| 2019-12-22 13:14:31 | NBlog Dec 22 - zero-based risk assessment (lien direct) |  In a thread on the ISO27k Forum, Ed Hodgson said:"There are many security controls we have already implemented that already manage risk to an acceptable level e.g. my building has a roof which helps ensure my papers don't get wet, soggy and illegible. But I don't tend to include the risk of papers getting damaged by rain in my risk assessment".Should we consider or ignore our existing information security controls when assessing information risks for an ISO27k ISMS? That question took me back to the origins of ISO27k, pre-BS7799 even. As I recall, Donn Parker originally suggested a standard laying out typical or commonplace controls providing a security baseline, a generally-applicable foundation or bedrock of basic or fundamental controls. The idea was to bypass the trivial justification for baseline controls: simply get on with implementing them, saving thinking-time and brain-power to consider the need for additional controls where the baseline controls are insufficient to mitigate the risks. [I'm hazy on the details now: that was ~30 years ago after all.]I have previous used and still have a soft-spot for the baseline concept … and yet it's no easier to define a generic baseline today than it was way back then. In deciding how to go about information risk analysis, should we:Go right back to basics and assume there are no controls at In a thread on the ISO27k Forum, Ed Hodgson said:"There are many security controls we have already implemented that already manage risk to an acceptable level e.g. my building has a roof which helps ensure my papers don't get wet, soggy and illegible. But I don't tend to include the risk of papers getting damaged by rain in my risk assessment".Should we consider or ignore our existing information security controls when assessing information risks for an ISO27k ISMS? That question took me back to the origins of ISO27k, pre-BS7799 even. As I recall, Donn Parker originally suggested a standard laying out typical or commonplace controls providing a security baseline, a generally-applicable foundation or bedrock of basic or fundamental controls. The idea was to bypass the trivial justification for baseline controls: simply get on with implementing them, saving thinking-time and brain-power to consider the need for additional controls where the baseline controls are insufficient to mitigate the risks. [I'm hazy on the details now: that was ~30 years ago after all.]I have previous used and still have a soft-spot for the baseline concept … and yet it's no easier to define a generic baseline today than it was way back then. In deciding how to go about information risk analysis, should we:Go right back to basics and assume there are no controls at |
APT 17 | |||
| 2019-11-07 17:00:15 | Helium activates wireless network for IoT devices in more than 425 US cities (lien direct) | Designed to connect Internet of Things devices over a long distance, Helium's network of hotspots uses peer-to-peer sharing and rewards adopters with cryptocurrency. | APT 17 | |||
| 2019-07-24 18:24:00 | APT-doxing group exposes APT17 as Jinan bureau of China\'s Security Ministry (lien direct) | Intrusion Truth's previous two exposes -- for APT3 and APT10 -- resulted in DOJ charges. Will this one as well? | APT 17 APT 10 APT 3 | |||
| 2019-06-26 08:43:01 | MY TAKE: Let\'s not lose sight of why Iran is pushing back with military, cyber strikes (lien direct) | It is not often that I hear details about the cyber ops capabilities of the USA or UK discussed at the cybersecurity conferences I attend. Related: We’re in the golden age of cyber spying Despite the hush-hush nature of Western cyber ops, it is axiomatic in technology and intelligence circles that the USA and UK […] | APT 17 | |||
| 2018-06-27 06:14:00 | Reduce breach risk and costs with security resilience (lien direct) | In cybersecurity circles, there's a common axiom that states, “There are two types of companies: those that have been breached and those that don't know they have been breached.” If the phrase sounds of doom and gloom, it's meant to be because the harsh reality is that almost every company will suffer a cybersecurity breach. Businesses can spend and spend on the latest and greatest security technology and still get breached for a number of reasons, including user-related issues. The challenge for businesses is to find the breach as soon as possible and return to normal operations as quickly as possible. [ Find out how 4 deception tools deliver truer network security. | Get the latest from CSO by signing up for our newsletters. ] | APT 17 | |||
| 2018-01-14 14:08:40 | Remembering When APT Became Public (lien direct) | 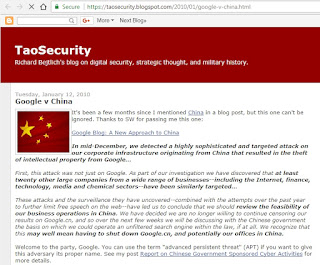 Last week I Tweeted the following on the 8th anniversary of Google's blog post about its compromise by Chinese threat actors:This intrusion made the term APT mainstream. I was the first to associate it with Aurora, in this post https://taosecurity.blogspot.com/2010/01/google-v-china.htmlMy first APT post was a careful reference in 2007, when we all feared being accused of "leaking classified" re China: https://taosecurity.blogspot.com/2007/10/air-force-cyberspace-report.htmlI should have added the term "publicly" to my original Tweet. There were consultants with years of APT experience involved in the Google incident response, and they recognized the work of APT17 at that company and others. Those consultants honored their NDAs and have stayed quiet.I wrote my original Tweet as a reminder that "APT" was not a popular, recognized term until the Google announcement on 12 January 2010. In my Google v China blog post I wrote:Welcome to the party, Google. You can use the term "advanced persistent threat" (APT) if you want to give this adversary its proper name.I also Tweeted a similar statement on the same day:This is horrifying: http://bit.ly/7x7vVW Google admits intellectual property theft from China; it's called Advanced Persistent Threat, GOOGI made the explicit link of China and APT because no one had done that publicly.This slide from a 2011 briefing I did in Hawaii captures a few historical points: Last week I Tweeted the following on the 8th anniversary of Google's blog post about its compromise by Chinese threat actors:This intrusion made the term APT mainstream. I was the first to associate it with Aurora, in this post https://taosecurity.blogspot.com/2010/01/google-v-china.htmlMy first APT post was a careful reference in 2007, when we all feared being accused of "leaking classified" re China: https://taosecurity.blogspot.com/2007/10/air-force-cyberspace-report.htmlI should have added the term "publicly" to my original Tweet. There were consultants with years of APT experience involved in the Google incident response, and they recognized the work of APT17 at that company and others. Those consultants honored their NDAs and have stayed quiet.I wrote my original Tweet as a reminder that "APT" was not a popular, recognized term until the Google announcement on 12 January 2010. In my Google v China blog post I wrote:Welcome to the party, Google. You can use the term "advanced persistent threat" (APT) if you want to give this adversary its proper name.I also Tweeted a similar statement on the same day:This is horrifying: http://bit.ly/7x7vVW Google admits intellectual property theft from China; it's called Advanced Persistent Threat, GOOGI made the explicit link of China and APT because no one had done that publicly.This slide from a 2011 briefing I did in Hawaii captures a few historical points: The Google incident was a watershed, for reasons I blogged on 16 January 2010. I remember the SANS DFIR 2008 event as effectively "APTCon," but beyond Mandiant, Northrup Grumman, and NetWitness, no one was really talking publicly about the APT until after Google.As I noted in the July 2009 blog post, You Down With APT? (ugh):Aside from Northrup Grumman, Mandiant, and a few vendors (like NetWitness, one of the full capture vendors out there) mentioning APT, there's not much else available. A Google search for "advanced persistent threat" -netwitness -mandiant -Northrop yields 34 results (prior to this blog post). (emphasis added)Today that search yields 244,000 results.I would argue we're "past APT." APT was the buzzword for The Google incident was a watershed, for reasons I blogged on 16 January 2010. I remember the SANS DFIR 2008 event as effectively "APTCon," but beyond Mandiant, Northrup Grumman, and NetWitness, no one was really talking publicly about the APT until after Google.As I noted in the July 2009 blog post, You Down With APT? (ugh):Aside from Northrup Grumman, Mandiant, and a few vendors (like NetWitness, one of the full capture vendors out there) mentioning APT, there's not much else available. A Google search for "advanced persistent threat" -netwitness -mandiant -Northrop yields 34 results (prior to this blog post). (emphasis added)Today that search yields 244,000 results.I would argue we're "past APT." APT was the buzzword for |
APT 17 APT 1 | |||
| 2017-10-04 11:12:03 | Intezer researchers link CCleaner hack to Chinese APT17 hackers (lien direct) | Researchers from security firm Intezer speculate that the attack was powered by nation-state actor, likely the Chinese APT17 group. Security experts continue to investigate the recent attack against the supply chain of the popular software CCleaner. The hackers first compromised in July a CCleaner server, then exploited it to deliver a backdoored version of the 32-bit CCleaner […] | CCleaner APT 17 | |||
| 2017-09-21 08:34:32 | Piratage CCleaner : la Chine se cache-t-elle derrière cette attaque ? (lien direct) | Plusieurs indices techniques pointent vers le groupe de hackers chinois APT17, spécialisé dans le cyberespionnage et le vol de données au travers de moyens sophistiqués.  |
CCleaner APT 17 | ★★★ | ||
| 2017-05-01 05:22:00 | Career Watch: Be wary of IT employment contracts (lien direct) | Jeffrey Scolaro, an attorney at Daley Mohan Groble PC in Chicago and a member of Legal Services Link, answers questions about employment contracts.Are employment contracts for IT workers negotiable, or are they one-size-fits-all? The axiom that “everything is negotiable†should be where all IT professionals begin their assessment of proposed employment contracts. However, the IT industry in particular can be especially rigid in its collective enforcement of employment agreements.To read this article in full or to leave a comment, please click here | APT 17 | |||
| 2016-10-11 04:00:00 | A breach alone means liability (lien direct) | Rich Santalesa, a programmer turned writer and lawyer, brought an interesting turn of events to my attention last week. We need to pay heed: A litigant can have standing in a U.S. Federal breach case where no personal fraud or identity theft has yet occurred.Usually, a litigant has to have suffered injury-a breech caused them identity theft or other fraudulent activity based upon information released in a security breach. This means if you're cracked, you can be liable if personally identifiable information is released, exfiltrated, absconded, whatever. It also means that should you believe the axiom that currently most of us are hacked, we're in for a litigious treat. To read this article in full or to leave a comment, please click here | APT 17 | |||
| 2016-09-13 13:00:00 | Free and Commercial Tools to Implement the Center for Internet Security (CIS) Security Controls, Part 17: Data Protection (lien direct) | This is Part 17 of a 'How-To' effort to compile a list of tools (free and commercial) that can help IT administrators comply with what was formerly known as the "SANS Top 20 Security Controls". It is now known as the Center for Internet Security (CIS) Security Controls. A summary of the previous posts is here: Part 1 - we looked at Inventory of Authorized and Unauthorized Devices. Part 2 - we looked at Inventory of Authorized and Unauthorized Software. Part 3 - we looked at Secure Configurations. Part 4 - we looked at Continuous Vulnerability Assessment and Remediation. Part 5 - we looked at Malware Defenses. Part 6 - we looked at Application Security. Part 7 - we looked at Wireless Access Control. Part 8/9 – we looked at Data Recovery and Security Training. Part 10/11 - we looked at Secure Configurations for Network Devices such as Firewalls, Routers, and Switches and Limitation and Control of Network Ports, Protocols and Services. Part 12 - we looked at Controlled Use of Administrative Privileges Part 13 - we looked at Boundary Defense Part 14 - we looked at Maintenance, Monitoring and Analysis of Audit Logs Part 15 - We looked at Controlled Access Based on the Need to Know. | APT 17 | |||
| 2016-05-27 03:00:57 | From Monkey to Man – The Evolution of a CISO (lien direct) | I think we are all familiar with the popular axiom, “It's not IF you get compromised, it's WHEN you get compromised.” I'm also pretty sure we all know that IT security is no longer viewed purely as an operational concern but as a significant contributor to business risk. As a result of this, IT security […]… Read More | APT 17 |
To see everything:
Our RSS (filtrered)
