What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2024-03-06 22:36:53 | Cloud-y Linux Malware Rains sur Apache, Docker, Redis &Confluence Cloud-y Linux Malware Rains on Apache, Docker, Redis & Confluence (lien direct) |
Les cyberattaques "filants" qui brandissent une volet en ligne Linux positionnent pour un compromis plus large en cloud en exploitant des erreurs de configurations courantes et un bogue de confluence atlassien connu.
"Spinning YARN" cyberattackers wielding a Linux webshell are positioning for broader cloud compromise by exploiting common misconfigurations and a known Atlassian Confluence bug. |
Malware Cloud | ★★ | ||
| 2024-03-06 21:59:52 | Veeam lance Veeam Data Cloud Veeam Launches Veeam Data Cloud (lien direct) |
Pas de details / No more details | Cloud | ★★ | ||
| 2024-03-06 16:53:40 | Snowflake s\'associe à Mistral AI pour proposer des modèles de langage grâce à Snowflake Cortex (lien direct) | Snowflake s'associe à Mistral AI pour proposer aux entreprises des modèles de langage de pointe grâce à Snowflake Cortex • Le modèle le plus récent et le plus puissant de Mistral AI, Mistral Large, est désormais disponible dans le Data Cloud de Snowflake pour exploiter en toute sécurité l'IA générative avec les données d'entreprise. • Snowflake Ventures s'associe à Mistral AI pour étendre les capacités de l'IA générative et permettre à davantage de développeurs d'exploiter de manière transparente la puissance des grands modèles de langage. • Snowflake Cortex LLM Functions, en public preview, permet aux utilisateurs de créer rapidement et facilement des applications d'IA générative. - Business | Cloud | ★★★ | ||
| 2024-03-06 15:50:14 | La campagne de logiciels malveillants Linux cible les serveurs cloud mortels Linux Malware Campaign Targets Misconfigured Cloud Servers (lien direct) |
> Une nouvelle campagne de logiciels malveillants a été observée ciblant les instances d'apache Hadoop, Confluence, Docker et Redis. .
>A new malware campaign has been observed targeting misconfigured Apache Hadoop, Confluence, Docker, and Redis instances. |
Malware Cloud | ★★ | ||
| 2024-03-06 15:00:00 | 10 processus essentiels pour réduire les 11 premiers risques de cloud 10 Essential Processes for Reducing the Top 11 Cloud Risks (lien direct) |
Les défis de la sécurité du cloud de Cloud Security Alliance \\ peuvent être relevés en mettant les bons processus en place.
The Cloud Security Alliance\'s "Pandemic 11" cloud security challenges can be addressed by putting the right processes in place. |
Cloud | ★★★ | ||
| 2024-03-06 15:00:00 | Mémo sur les menaces du cloud: Google Drive a abusé des organisations ciblées dans les pays asiatiques Cloud Threats Memo: Google Drive Abused to Target Organizations in Asian Countries (lien direct) |
> Le dernier exemple d'une menace persistante avancée exploitant un service cloud légitime pour fournir une charge utile malveillante a récemment été déterminé par les chercheurs de Trend Micro.En tant que suivi d'une campagne ciblant plusieurs pays européens, découvert en juillet 2023 et attribué à l'APT Earth Preta (également connu sous le nom de Mustang Panda et Bronze [& # 8230;]
>The latest example of an advanced persistent threat exploiting a legitimate cloud service to deliver a malicious payload was recently unearthed by researchers at Trend Micro. As a follow up of a campaign targeting several European countries, discovered in July 2023 and attributed to the APT Earth Preta (also known as Mustang Panda and Bronze […] |
Threat Prediction Cloud | ★★ | ||
| 2024-03-06 13:52:40 | (Déjà vu) F5 ajoute des tests de pénétration automatisés (lien direct) | F5 ajoute des tests de pénétration automatisés pour renforcer les capacités de sécurité des applications multicloud • La solution automatisée de reconnaissance de la sécurité et de test de pénétration sera intégrée à Distributed Cloud Services de F5. • La technologie acquise par Heyhack renforce le portefeuille de sécurité des applications multicloud de F5, permettant aux clients d'automatiser la découverte des vulnérabilités. - Produits | Cloud | ★★ | ||
| 2024-03-06 12:55:24 | Top 6 vecteurs de violation SaaS et comment les empêcher Top 6 SaaS Breach Vectors and How to Prevent Them (lien direct) |
> En moyenne, les équipes informatiques ne connaissent que 20% des applications SaaS utilisées dans leurs organisations1.Si les contrôles standard pouvaient être facilement appliqués aux applications SaaS, ce nombre serait peu de préoccupation.Cependant, la fréquence des incidents de sécurité liées au SaaS raconte une histoire différente, avec des titres fréquents sur les PII visibles publiquement, le rachat du compte via des tiers piratés et une exfiltration malveillante des bases de données clients entières.De toute évidence, les solutions actuelles ne suffisent pas.Quelle est la répartition des violations basées sur le SaaS?Les violations de données SaaS représentent l'exposition aux données dans quatre organisations sur cinq, et près de la moitié (43%) des incidents de sécurité liés [& # 8230;]
>On average, IT teams are only aware of 20% of the SaaS applications used in their organizations1. If standard controls could be easily applied to SaaS apps, then this number would be little cause for concern. However, the frequency of SaaS-related security incidents tells a different story, with frequent headlines on publicly visible PII, account takeover through hacked third parties and malicious exfiltration of entire customer databases. Clearly, current solutions are not enough. How Prevalent are SaaS-based Breaches? SaaS data breaches account for data exposure in four out of five organizations , and almost half (43%) experience security incidents related […] |
Cloud | ★★★ | ||
| 2024-03-06 09:37:40 | F5 ajoute des tests de pénétration automatisés pour renforcer les capacités de sécurité des applications multicloud F5 Adds Automated Penetration Testing to Strengthen Multicloud Application Security Capabilities (lien direct) |
F5 ajoute des tests de pénétration automatisés pour renforcer les capacités de sécurité des applications multicloud
• La solution automatisée de reconnaissance de reconnaissance et de test de pénétration sera incorporée dans les services cloud distribués F5.
• La technologie acquise via Heyhack renforce le portefeuille de sécurité des applications multicloud de F5 \\, permettant aux clients d'automatiser la découverte de vulnérabilité.
-
revues de produits
F5 Adds Automated Penetration Testing to Strengthen Multicloud Application Security Capabilities • Automated security reconnaissance and penetration testing solution will be incorporated into F5 Distributed Cloud Services. • Technology acquired through Heyhack strengthens F5\'s multicloud application security portfolio, enabling customers to automate vulnerability discovery. - Product Reviews |
Vulnerability Cloud | ★★★ | ||
| 2024-03-06 08:17:14 | Après Google Cloud, AWS : pourquoi ils suppriment les frais de sortie (lien direct) | Dans la lignée de Google Cloud, AWS supprime, sous conditions, les frais de changement de fournisseur. Dans quel contexte ? | Cloud | ★★★ | ||
| 2024-03-05 21:07:02 | Crowdsstrike pour acquérir la sécurité du flux, établit la norme pour la sécurité des données cloud moderne CrowdStrike to Acquire Flow Security, Sets the Standard for Modern Cloud Data Security (lien direct) |
Je suis ravi d'annoncer l'accord de Crowdsstrike \\ pour acquérir la sécurité de flux, un pionnier de la gestion de la posture de sécurité des données (DSPM) et de la première et la seule solution de sécurité d'exécution de données cloud de l'industrie.Avec cette acquisition, CrowdStrike établit la norme pour la sécurité du cloud moderne avec une protection complète de données en temps réel couvrant des environnements de terminaison et de cloud, offrant le seul cloud [& # 8230;]
I\'m thrilled to announce CrowdStrike\'s agreement to acquire Flow Security, a pioneer in data security posture management (DSPM) and the industry\'s first and only cloud data runtime security solution. With this acquisition, CrowdStrike is setting the standard for modern cloud security with complete real-time data protection spanning endpoint and cloud environments, delivering the only cloud […] |
Cloud | ★★ | ||
| 2024-03-05 16:25:00 | Qu'est-ce que la gestion de l'exposition et en quoi diffère-t-elle d'ASM? What is Exposure Management and How Does it Differ from ASM? (lien direct) |
Les startups et les échelles sont souvent des organisations d'abord en cloud et ont rarement des environnements d'héritage sur prémage étendus.De même, en connaissant l'agilité et la flexibilité que les environnements cloud offrent, le marché intermédiaire fonctionne principalement dans un état hybride, en partie dans le cloud mais avec certains actifs sur site.
Bien qu'il y ait eu un peu de backswing contre les prix et le verrouillage présentés lors de l'utilisation
Startups and scales-ups are often cloud-first organizations and rarely have sprawling legacy on-prem environments. Likewise, knowing the agility and flexibility that cloud environments provide, the mid-market is predominantly running in a hybrid state, partly in the cloud but with some on-prem assets. While there has been a bit of a backswing against the pricing and lock-in presented when using |
Cloud | ★★★ | ||
| 2024-03-05 16:22:28 | (Déjà vu) Vade rejoint le groupe HornetSecurity Vade joins Hornetsecurity Group (lien direct) |
Vade rejoint HornetSecurity Group, créant un leader européen de cybersécurité
Le partenariat vise à positionner le groupe en tant que fournisseur de cybersécurité prééminent pour les clients et les partenaires en Europe qui apprécient la souveraineté des données et les meilleurs services de cloud, de conformité et de sécurité des communications numériques
-
nouvelles commerciales
Vade joins Hornetsecurity Group, creating a European cybersecurity leader Partnership aims to position the group as the preeminent cybersecurity provider for customers and partners in Europe who value data sovereignty and best-in-class cloud, compliance and digital communications security services - Business News |
Cloud | ★★★ | ||
| 2024-03-05 15:23:31 | Cloud Range lance la formation initiale du commandant des cyber-incidents pour améliorer le temps de réponse, élever les performances Cloud Range launches initial cyber incident Commander Training to improve response time, elevate performance (lien direct) |
Cloud Range a annoncé mardi le lancement de son nouveau programme de formation, Cybersecurity Incident Commander Training.Offert pour un ...
Cloud Range announced Tuesday the launch of its new training program, Cybersecurity Incident Commander Training. Offered for a... |
Cloud | ★★★ | ||
| 2024-03-05 14:30:42 | Présentation du lancement de Multicloud de Red Canary \\ Introducing Red Canary\\'s multicloud launch (lien direct) |
Trouvez et arrêtez les risques et menaces dans le cloud à travers AWS, Azure, GCP et Linux avec nos nouvelles capabilties multi-multical.
Find and stop cloud risks and threats across AWS, Azure, GCP, and Linux with our new multicloud capabilties. |
Cloud | ★★ | ||
| 2024-03-05 14:30:16 | Red Canary apporte une expertise MDR à Microsoft Azure Cloud Red Canary brings MDR expertise to Microsoft Azure Cloud (lien direct) |
Red Canary ingère directement des données de télémétrie et des alertes à partir des journaux d'audit Azure et du défenseur du cloud, détectant les menaces que d'autres manquent.
Red Canary directly ingests telemetry data and alerts from Azure Audit logs and Defender for Cloud, detecting threats that others miss. |
Cloud | ★★ | ||
| 2024-03-05 13:04:41 | Vade rejoint Hornetsecurity Group (lien direct) | Vade rejoint Hornetsecurity Group, créant ainsi un leader européen de la cybersécurité Le partenariat vise à positionner le groupe comme le fournisseur de cybersécurité incontournable pour les clients et partenaires européens qui accordent de l'importance à la souveraineté des données et aux meilleurs services de sécurité pour le cloud, la conformité et les communications numériques. - Business | Cloud | ★★ | ||
| 2024-03-05 08:30:26 | Sécurité du cloud en question : la nécessité de renforcer la cybersécurité (lien direct) | Sécurité du cloud en question : la nécessité de renforcer la cybersécurité. Fanch Francis, CEO de NANO Corp, Acteur de la cybersécurité et spécialiste de la surveillance réseau en temps réel et de suivi des politiques de sécurité, partage sa réaction quant à cette actualité : - Points de Vue | Cloud | ★★ | ||
| 2024-03-04 11:46:32 | 75+ listes de contrôle technologiques pour améliorer l'efficacité 75+ Tech Checklists to Improve Efficiency (lien direct) |
De la réponse des logiciels malveillants au stockage cloud, chaque organisation peut bénéficier d'une liste de contrôle pour assurer des opérations efficaces et lisses.
From malware response to cloud storage, every organization can benefit from a checklist to ensure effective and smooth operations. |
Malware Cloud | ★★★ | ||
| 2024-03-03 12:46:21 | ZATAZ découvre un nid de hackers avec plus de 1,7 million de victimes (lien direct) | Un hacker malveillant stocke dans un cloud public plus de 1,3 million d'internautes piratés. ZATAZ met la main sur le stockage et tente de le faire fermer !... | Cloud | ★★★ | ||
| 2024-03-01 20:15:10 | Les problèmes NCSC de UK \\ ont avertissement en tant que pirates SVR ciblent les services cloud UK\\'s NCSC Issues Warning as SVR Hackers Target Cloud Services (lien direct) |
Cyber Espionage Group APT29 adapte ses tactiques aux environnements cloud.Voici ce que vous devez savoir.
Cyber espionage group APT29 is adapting its tactics for cloud environments. Here\'s what you should know. |
Cloud | APT 29 | ★★ | |
| 2024-03-01 18:45:16 | Accélérer l'adoption du cloud dans le secteur public écossais Accelerating Cloud Adoption Across the Scottish Public Sector (lien direct) |
> Le gouvernement écossais a développé un CPS pour donner un accès simplifié au secteur public écossais aux technologies cloud, offrant une arrêt aux plates-formes cloud.
>The Scottish Government developed a CPS to give Scottish Public Sector simplified access to cloud technologies, providing one stop to cloud platforms. |
Cloud | ★★ | ||
| 2024-03-01 18:09:55 | La régulation de la biométrie se réchauffe, présatant les maux de tête de la conformité Biometrics Regulation Heats Up, Portending Compliance Headaches (lien direct) |
Un fourré croissant de lois sur la vie privée régulant la biométrie vise à protéger les consommateurs au milieu des violations des nuages croissantes et des fesseurs profondes créées par l'IA.Mais pour les entreprises qui gèrent les données biométriques, rester conforme est plus facile à dire qu'à faire.
A growing thicket of privacy laws regulating biometrics is aimed at protecting consumers amid increasing cloud breaches and AI-created deepfakes. But for businesses that handle biometric data, staying compliant is easier said than done. |
Cloud | ★★★ | ||
| 2024-03-01 13:49:02 | Advanced Cyber Defenfispinon Systems (ADCS) pour présenter une solution de gestion de surface d'attaque innovante à Cloud & Cyber Security Expo Advanced Cyber Defence Systems (ADCS) to Showcase Innovative Attack Surface Management Solution at Cloud & Cyber Security Expo (lien direct) |
Continuant à partir de leur série de webinaires populaires, Advanced Cyber Defense Systems (ACDS) prend leur & # 8216; Pensez comme un pirate & # 8217;série au cloud & # 38;Cyber Expo.Lors de l'événement, l'équipe démontera sa solution de gestion de surface d'attaque de pointe.De plus, le CTO de la société \\, Elliott Wilkes, livrera également un discours lors de l'événement, [& # 8230;]
le post Systèmes de cyberdéfense avancés (ADC) pour présenter une solution innovante de gestion de surface d'attaque à Cloud & Cyber Security Expo Apparu pour la première fois sur gourou de la sécurité informatique .
Continuing on from their popular webinar series, Advanced Cyber Defence Systems (ACDS) are taking their ‘Think Like a Hacker’ series to The Cloud & Cyber Expo. At the event, the team will be demoing their cutting-edge Attack Surface Management solution. Additionally, the company\'s CTO, Elliott Wilkes, will also be delivering a keynote at the event, […] The post Advanced Cyber Defence Systems (ADCS) to Showcase Innovative Attack Surface Management Solution at Cloud & Cyber Security Expo first appeared on IT Security Guru. |
Cloud | ★★ | ||
| 2024-02-29 20:48:36 | Les applications cloud plaident pour la pentisting en tant que service Cloud Apps Make the Case for Pentesting-as-a-Service (lien direct) |
Les applications sont de plus en plus distribuées, en élargissant les surfaces d'attaque cloud des entreprises et nécessitant des tests réguliers pour trouver et corriger les vulnérabilités - sinon les entreprises risquent un étalement croissant de services.
Applications are increasingly distributed, expanding companies\' cloud attack surfaces, and requiring regular testing to find and fix vulnerabilities - else companies risk a growing sprawl of services. |
Vulnerability Cloud | ★★★ | ||
| 2024-02-29 15:31:42 | Veeam® Software annonce Veeam Data Cloud (lien direct) | Avec sa nouvelle offre Veeam Data Cloud, Veeam réunit les meilleurs services de protection et restauration des données au sein d'une plateforme cloud unique En fédérant les tâches de stockage, de sauvegarde sur le cloud et de lutte contre les ransomwares pour les environnements Microsoft Azure et Microsoft 365, la plateforme tout-en-un Veeam Data Cloud protège actuellement plus de 18 millions d'utilisateurs. - Produits | Cloud | ★★ | ||
| 2024-02-29 11:00:00 | Gouvernance de l'IA et préservation de la vie privée AI governance and preserving privacy (lien direct) |
AT&T Cybersecurity featured a dynamic cyber mashup panel with Akamai, Palo Alto Networks, SentinelOne, and the Cloud Security Alliance. We discussed some provocative topics around Artificial Intelligence (AI) and Machine Learning (ML) including responsible AI and securing AI. There were some good examples of best practices shared in an emerging AI world like implementing Zero Trust architecture and anonymization of sensitive data. Many thanks to our panelists for sharing their insights. Before diving into the hot topics around AI governance and protecting our privacy, let’s define ML and GenAI to provide some background on what they are and what they can do along with some real-world use case examples for better context on the impact and implications AI will have on our future. GenAI and ML Machine Learning (ML) is a subset of AI that relies on the development of algorithms to make decisions or predictions based on data without being explicitly programmed. It uses algorithms to automatically learn and improve from experience. GenAI is a subset of ML that focuses on creating new data samples that resemble real-world data. GenAI can produce new and original content through deep learning, a method in which data is processed like the human brain and is independent of direct human interaction. GenAI can produce new content based on text, images, 3D rendering, video, audio, music, and code and increasingly with multimodal capabilities can interpret different data prompts to generate different data types to describe an image, generate realistic images, create vibrant illustrations, predict contextually relevant content, answer questions in an informational way, and much more. Real world uses cases include summarizing reports, creating music in a specific style, develop and improve code faster, generate marketing content in different languages, detect and prevent fraud, optimize patient interactions, detect defects and quality issues, and predict and respond to cyber-attacks with automation capabilities at machine speed. Responsible AI Given the power to do good with AI - how do we balance the risk and reward for the good of society? What is an organization’s ethos and philosophy around AI governance? What is the organization’s philosophy around the reliability, transparency, accountability, safety, security, privacy, and fairness with AI, and one that is human-centered? It\'s important to build each of these pillarsn into an organization\'s AI innovation and business decision-making. Balancing the risk and reward of innovating AI/ML into an organization\'s ecosystem without compromising social responsibility and damaging the company\'s brand and reputation is crucial. At the center of AI where personal data is the DNA of our identity in a hyperconnected digital world, privacy is a top priority. Privacy concerns with AI In Cisco’s 2023 consumer privacy survey, a study of over 2600 consumers in 12 countries globally, indicates consumer awareness of data privacy rights is continuing to grow with the younger generations (age groups under 45) exercising their Data Subject Access rights and switching providers over their privacy practices and policies. Consumers support AI use but are also concerned. With those supporting AI for use: 48% believe AI can be useful in improving their lives 54% are willing to share anonymized personal data to improve AI products AI is an area that has some work to do to earn trust 60% of respondents believe the use of AI by organizations has already eroded trust in them 62% reported concerns about the business use of AI 72% of respondents indicated that having products and solutions aud | Studies Prediction Cloud Technical | ★★ | ||
| 2024-02-29 06:00:13 | Briser la chaîne d'attaque: des mouvements décisifs Break the Attack Chain: Decisive Moves (lien direct) |
In our “Break the Attack Chain” blog series, we have looked at how threat actors compromise our defenses and move laterally within our networks to escalate privileges and prepare for their endgame. Now, we come to the final stage of the attack chain where it\'s necessary to broaden our outlook a little. While most external threat actors will follow the same playbook, they aren\'t our only adversaries. The modern reality is that data often just walks out of the door because our employees take it with them. More than 40% of employees admit to taking data when they leave. At the same time, careless employees who make security mistakes are responsible for more than half of insider-led data loss incidents. So, while it\'s important to detect and deter cybercriminals who want to exfiltrate our data, we must also watch out for our users. Whether they are malicious or careless, our users are just as capable of exposing sensitive data. In this third and final installment, we discuss how companies tend to lose data-and how we can better protect it from all manner of risks. Understanding data loss As with every stage in the attack chain, we must first understand threats before we can put protections in place. Let\'s start with the case of a cybercriminal following the typical attack chain. While this may not sound like a traditional insider attack, it\'s often aided by careless or reckless employees. Users expose data and open themselves and your business up to compromise in a multitude of ways, like using weak passwords, reusing credentials, forgoing security best practices and clicking on malicious links or attachments. Any of these risky moves give cybercriminals a way into your networks where they can embark on lateral movement and escalation. Incidents like these are so common that careless or compromised users cause over 80% of insider-led data loss. Malicious insiders make up the remainder. Insider threats could be a disgruntled employee looking to cause disruption, a user compromised by cybercriminals, or, increasingly, an employee who will soon leave your organization. In most cases, data exfiltration follows a three-stage pattern: Access. Users, whether malicious or compromised, will attempt to take as much information as possible. This could mean excessive downloading or copying from corporate drives or exporting data from web interfaces or client apps. Obfuscation. Both cybercriminals and malicious insiders will be aware of the kinds of activity likely to trigger alarms and will take steps to avoid them. Changing file names and extensions, deleting logs and browsing history, and encrypting files are typical strategies. Exfiltration. With targets acquired and tracks covered, data exfiltration is then carried out by copying files to a personal cloud or removable storage device and sharing files with personal or burner email accounts. Defending from the inside out As we explained in our webinar series, while the initial stage of the attack chain focuses on keeping malicious actors outside our organization, the final two stages are far more concerned with what\'s happening inside it. Therefore, any effective defense must work from the inside out. It must detect and deter suspicious activity before data can slip past internal protections and be exposed to the outside world. Of course, data can do many things-but it cannot leave an organization on its own. Whether compromised, careless or malicious, a human is integral to any data loss incident. That\'s why traditional data loss prevention (DLP) tools are not as effective as they used to be. By focusing on the content of an incident, they only address a third of the problem. Instead, a comprehensive defense against data loss must merge content classification with threat telemetry and user behavior. Proofpoint Information Protection is the only solution that uses all three across channels in a unified, cloud-native interface. With this information, security teams can identify who is accessing and moving data-when, where and why. And | Tool Threat Cloud | ★★★ | ||
| 2024-02-28 13:44:31 | Une menace ombragée: l'escalade des cyberattaques API Web en 2024 A Shadowed Menace : The Escalation of Web API Cyber Attacks in 2024 (lien direct) |
> Faits saillants: augmentation significative des attaques: au cours du premier mois de 2024, les tentatives d'attaquer les API Web ont eu un impact sur 1 sur 4,6 organisations dans le monde chaque semaine, marquant une augmentation de 20% par rapport à janvier 2023, mettant en évidence le risque croissant associé aux vulnérabilités d'API.Impact à l'échelle de l'industrie: l'éducation mène le secteur le plus touché, la plupart des secteurs ayant une augmentation à deux chiffres des attaques de l'année dernière.Pendant ce temps, les réseaux organisationnels basés sur le cloud connaissent une augmentation de 34% des attaques par rapport à la même période l'année dernière, et dépassent les réseaux organisationnels sur site dans l'impact global des attaques d'API, soulignant l'évolution du paysage des menaces du cloud.Vulnérabilités et incidents notables: exploits comme le [& # 8230;]
>Highlights: Significant Increase in Attacks: In the first month of 2024, attempts to attack Web APIs impacted 1 in 4.6 organizations worldwide every week, marking a 20% increase compared to January 2023, highlighting the growing risk associated with API vulnerabilities. Industry-Wide Impact: Education leads as the most impacted sector, with most sectors having a double-digit surge in attacks from last year. Meanwhile, cloud-based organizational networks experience a 34% rise in attacks compared to the same period last year, and overtake on-prem organizational networks in the overall impact of API attacks, underscoring the evolving cloud threat landscape. Notable Vulnerabilities and Incidents: Exploits like the […] |
Vulnerability Threat Cloud | ★★★ | ||
| 2024-02-27 21:49:18 | Russie \\ 'S \\' Midnight Blizzard \\ 'cible les comptes de service pour l'accès au cloud initial Russia\\'s \\'Midnight Blizzard\\' Targets Service Accounts for Initial Cloud Access (lien direct) |
La CISA et ses homologues au Royaume-Uni et dans d'autres pays cette semaine ont offert de nouvelles conseils sur la façon de gérer le récent passage de l'acteur de menace aux attaques cloud.
CISA and its counterparts in the UK and other countries this week offered new guidance on how to deal with the threat actor\'s recent shift to cloud attacks. |
Threat Cloud | ★★ | ||
| 2024-02-27 20:00:14 | CloudGuard rationalise Azure Virtual Wan Security avec entrée directe CloudGuard Streamlines Azure Virtual WAN security with Direct Ingress (lien direct) |
> Alors qu'Azure Virtual Wan continue de gagner en popularité auprès des clients d'entreprise avec des environnements informatiques distribués et complexes, la nécessité d'une solution de sécurité complète, consolidée et collaborative pour protéger ces déploiements devient encore plus cruciale.Check Point CloudGuard offre aux clients une sécurité de réseau cloud de pointe pour leurs déploiements WAN virtuels, une connectivité sécurisée pour les environnements informatiques hétérogènes et distribués.La solution de point de contrôle permet une gestion de la sécurité unifiée et cohérente pour les nuages hybrides et les déploiements sur site avec une efficacité opérationnelle maximale.Microsoft a récemment annoncé que la nouvelle fonctionnalité à entrave directe (également appelée Internet Inbound ou Internet) est désormais en avant-première.Vérifier le point [& # 8230;]
>As Azure Virtual WAN continues to gain popularity among enterprise customers with distributed and complex IT environments, the need for a comprehensive, consolidated, and collaborative security solution to protect these deployments becomes even more crucial. Check Point CloudGuard provides customers with industry-leading cloud network security for their Virtual WAN deployments, secured connectivity for heterogeneous and distributed IT environments. The Check Point solution enables unified and consistent security management for hybrid-clouds and on-prem deployments with maximum operational efficiency. Microsoft recently announced that the new Direct Ingress functionality (also called internet inbound or internet ingress) is now in public preview. Check Point […] |
Cloud | ★★ | ||
| 2024-02-27 16:04:00 | Cinq agences Eyes exposent des tactiques d'évolution des nuages en évolution de l'APT29 \\ Five Eyes Agencies Expose APT29\\'s Evolving Cloud Attack Tactics (lien direct) |
La cybersécurité et les agences de renseignement des cinq yeux des Nations ont publié un conseil conjoint détaillant les tactiques évolutives de l'acteur de menace parrainé par l'État russe connu sous le nom de & NBSP; APT29.
La tenue de piratage, également connue sous le nom de Bluebravo, Ursa masqué, Cozy Bear, Midnight Blizzard (anciennement Nobelium) et les Dukes, est évaluée pour être affiliée au Foreign Intelligence Service (SVR) de la
Cybersecurity and intelligence agencies from the Five Eyes nations have released a joint advisory detailing the evolving tactics of the Russian state-sponsored threat actor known as APT29. The hacking outfit, also known as BlueBravo, Cloaked Ursa, Cozy Bear, Midnight Blizzard (formerly Nobelium), and The Dukes, is assessed to be affiliated with the Foreign Intelligence Service (SVR) of the |
Threat Cloud | APT 29 | ★★★ | |
| 2024-02-27 14:00:00 | Le besoin convaincant de protection des données natives dans le cloud The compelling need for cloud-native data protection (lien direct) |
> Les environnements cloud étaient des cibles fréquentes pour les cyberattaquants en 2023. Quatre-vingt-deux pour cent des violations qui impliquaient des données stockées dans le cloud se trouvaient dans des environnements publics, privés ou multi-clouds.Les attaquants ont acquis le plus d'accès aux environnements multi-cloud, avec 39% des violations couvrant des environnements multi-cloud en raison des problèmes de sécurité plus compliqués.Le coût de ces nuages [& # 8230;]
>Cloud environments were frequent targets for cyber attackers in 2023. Eighty-two percent of breaches that involved data stored in the cloud were in public, private or multi-cloud environments. Attackers gained the most access to multi-cloud environments, with 39% of breaches spanning multi-cloud environments because of the more complicated security issues. The cost of these cloud […] |
Cloud | ★★ | ||
| 2024-02-27 11:50:59 | MWC 2024 : Huawei Cloud cherche à s\'étendre malgré les sanctions (lien direct) | Huawei Cloud ouvre de nouvelles zones de disponibilité, développe ses activités européennes et se concentre sur l'IA en s'adaptant aux sanctions américaines. | Cloud | ★★ | ||
| 2024-02-27 11:00:00 | L'évolution du point de terminaison - passant des critères de terminaison traditionnels aux charges de travail cloud ou conteneurisées et les solutions de sécurité pour les protéger The endpoint evolution - Evolving from traditional endpoints to cloud or containerized workloads and the security solutions to protect them (lien direct) |
As organizations grow and more endpoints are added across the enterprise, they create an increasingly broad attack surface sophisticated attackers are looking to compromise. According to the 2019 Endpoint Security Trends Report 70% of breaches originate at the endpoint¹. That is likely because endpoints typically represent the Intersection between humans and machines creating vulnerable points of entry for cybercriminals. This is why it is increasingly important to secure your endpoints.
Growth in endpoints
An endpoint is defined as any computing device that communicates back and forth with a network to which it is connected. Some end user devices serve as an interface with human users while others are servers that communicate with other endpoints on the network. Traditional endpoints began as physical devices including servers, workstations, desktops, and laptops, all connected to a corporate network. When smartphones and tablets became handheld computing devices with access to corporate email, document sharing and collaboration tools the number of endpoints at least doubled.
Then came the rise of the Internet of Things (IoT) including devices like printers, webcams, smartwatches, and thermostats, all of which are connected to the network. Industries like healthcare and manufacturing are using millions of IoT sensors to collect and exchange data. This continued growth in IoT only increases the number of endpoints that need to be protected.
Another contribution to the growth in endpoints is the migration to the cloud. It is estimated that 67% of enterprise infrastructure is cloud-based². This cloud transformation is the evolution from physical devices to virtualization and containerization.
Endpoint virtualization
The cloud is a multi-tenant environment where multiple users run services on the same server hardware. Virtualization and containerization are both virtualization technologies that separate the host operating system from the programs that run in them.
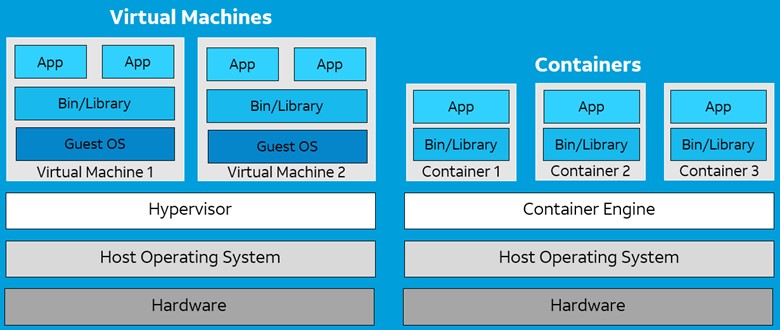 Virtualization is achieved using a hypervisor, which splits CPU, RAM, and storage resources between multiple virtual machines (VMs). Each VM behaves like a separate computer that gets a guest operating system and each VM is independent of each other. This allows organizations to run multiple OS instances on a single server.
Containerization, on the other hand, runs a single host OS instance and uses a container engine to help package applications into container images that can be easily deployed and re-used. By splitting each individual application function or microservice into containers they can operate independently to improve enterprise resilience and scalability. Kubernetes then manages the orchestration of multiple containers. VMs and containers present very different security challenges so let’s look at the evolution of endpoint security and the solutions that meet the needs of complex customer environments.
Securing endpoints
For decades, organizations have heavily relied on antivirus (AV) software to secure endpoints. However, traditional antivirus worked by matching known malicious signatures in a database and can no longer protect against today’s sophisticated threats. Modern endpoint security solutions are less signature-based and much more behavior-based. Endpoint protection platforms (EPP) offer cloud native architectures that provide a layered defense against fileless attacks using machine learning and behavioral AI to protect against malicious activity. Endpoint detection and response (EDR) solutions went beyond protection by recording and storing endpoint-system level behaviors to detect malicious threats.
EDR solutions use data analytics combined with threat intelligence feeds to provide incident responders with the forensic data for completing investigations and threat hunting. In addi
Virtualization is achieved using a hypervisor, which splits CPU, RAM, and storage resources between multiple virtual machines (VMs). Each VM behaves like a separate computer that gets a guest operating system and each VM is independent of each other. This allows organizations to run multiple OS instances on a single server.
Containerization, on the other hand, runs a single host OS instance and uses a container engine to help package applications into container images that can be easily deployed and re-used. By splitting each individual application function or microservice into containers they can operate independently to improve enterprise resilience and scalability. Kubernetes then manages the orchestration of multiple containers. VMs and containers present very different security challenges so let’s look at the evolution of endpoint security and the solutions that meet the needs of complex customer environments.
Securing endpoints
For decades, organizations have heavily relied on antivirus (AV) software to secure endpoints. However, traditional antivirus worked by matching known malicious signatures in a database and can no longer protect against today’s sophisticated threats. Modern endpoint security solutions are less signature-based and much more behavior-based. Endpoint protection platforms (EPP) offer cloud native architectures that provide a layered defense against fileless attacks using machine learning and behavioral AI to protect against malicious activity. Endpoint detection and response (EDR) solutions went beyond protection by recording and storing endpoint-system level behaviors to detect malicious threats.
EDR solutions use data analytics combined with threat intelligence feeds to provide incident responders with the forensic data for completing investigations and threat hunting. In addi |
Malware Tool Vulnerability Threat Mobile Cloud | ★★ | ||
| 2024-02-27 06:48:00 | CISA, NCSC, les partenaires mondiaux exposent les tactiques de cyber-espionnage SVR ciblant les environnements cloud CISA, NCSC, global partners expose SVR cyber espionage tactics targeting cloud environments (lien direct) |
> L'Agence américaine de sécurité de cybersécurité et d'infrastructure (CISA), en collaboration avec le UK National Cyber Security Center (NCSC) ...
>The U.S. Cybersecurity and Infrastructure Security Agency (CISA), in collaboration with the UK National Cyber Security Centre (NCSC)... |
Cloud | ★★ | ||
| 2024-02-27 01:00:06 | L'ours confortable de la Russie plonge dans des environnements cloud avec un nouveau sac de trucs Russia\\'s Cozy Bear dives into cloud environments with a new bag of tricks (lien direct) |
Les espions du Kremlin \\ ont essayé le TTPS sur Microsoft, et maintenant ils se rendent aux courses Russia \'s Cozy Bear, l'équipage derrière la chaîne d'approvisionnement de SolarwindsAttack, a élargi ses objectifs et a évolué ses techniques pour pénétrer dans les organisations \\ 'Cloud Environments, selon les Five Eyes Governments.…
Kremlin\'s spies tried out the TTPs on Microsoft, and now they\'re off to the races Russia\'s notorious Cozy Bear, the crew behind the SolarWinds supply chain attack, has expanded its targets and evolved its techniques to break into organizations\' cloud environments, according to the Five Eyes governments.… |
Cloud | APT 29 | ★★★ | |
| 2024-02-26 18:43:28 | La région du Golfe accélère l'adoption de zéro confiance Gulf Region Accelerates Adoption of Zero Trust (lien direct) |
Les Émirats arabes unis seront probablement l'un des premiers de la région à mettre en œuvre une sécurité zéro-confiance en raison de sa forte adoption des technologies cloud.
United Arab Emirates will likely be one of the first in the region to implement zero-trust security due to its heavy adoption of cloud technologies. |
Cloud | ★★ | ||
| 2024-02-26 17:18:53 | Cinq Nations Eyes préviennent d'évolution des pratiques de cyberespionnage russes ciblant les environnements cloud Five Eyes nations warn of evolving Russian cyberespionage practices targeting cloud environments (lien direct) |
> L'avis émis par le Centre national de cybersécurité du Royaume-Uni décompose les tactiques et les techniques de SVR Hacking Ops.
>The advisory issued by the U.K.\'s National Cyber Security Centre breaks down tactics and techniques from SVR hacking ops. |
Cloud | TYPEFRAME | ★★★ | |
| 2024-02-26 17:15:00 | CISA Issues Alert sur les tactiques d'infiltration des nuages d'APT29 \\ CISA Issues Alert on APT29\\'s Cloud Infiltration Tactics (lien direct) |
Connu sous le nom de Midnight Blizzard, les dukes ou l'ours confortable, le groupe a été identifié comme une entité russe opérant probablement sous le SVR
Known as Midnight Blizzard, the Dukes or Cozy Bear, the group has been identified as a Russian entity likely operating under the SVR |
Cloud | APT 29 | ★★ | |
| 2024-02-26 16:43:37 | Genetec lance Security Center SaaS (lien direct) | Genetec introduit une solution SaaS unifiée à l'échelle des entreprises Security Center SaaS redéfinit les possibilités pour la sécurité physique basée sur le cloud. - Produits | Cloud | ★★ | ||
| 2024-02-26 15:21:00 | Les chevaux de Troie bancaires ciblent l'Amérique latine et l'Europe via Google Cloud Run Banking Trojans Target Latin America and Europe Through Google Cloud Run (lien direct) |
Les chercheurs en cybersécurité mettent en garde contre un pic dans les campagnes de phishing par e-mail qui armement le service Google Cloud Run pour livrer divers chevaux de Troie bancaires tels que & nbsp; Astaroth & nbsp; (aka guildma), & nbsp; mekotio et & nbsp; Ousaban & nbsp; (aka javali) to ciblers à travers letin; OUSABAN & NBSP; (AKA JAVALI) pour cibler à travers le latin;Amérique (Latam) et Europe.
"Les chaînes d'infection associées à ces familles de logiciels malveillants comportent l'utilisation de malveillants
Cybersecurity researchers are warning about a spike in email phishing campaigns that are weaponizing the Google Cloud Run service to deliver various banking trojans such as Astaroth (aka Guildma), Mekotio, and Ousaban (aka Javali) to targets across Latin America (LATAM) and Europe. "The infection chains associated with these malware families feature the use of malicious |
Malware Cloud | ★★ | ||
| 2024-02-26 13:56:26 | Russie Cyber Spies derrière Solarwinds Breach adoptant de nouvelles tactiques, avertissez cinq agences Eyes Russia cyber spies behind SolarWinds breach adopting new tactics, warn Five Eyes agencies (lien direct) |
 Les cyber-espions russes derrière la violation de Solarwinds adaptent leurs techniques pour pirater des organisations qui ont déplacé leurs réseaux dans des environnements hébergés dans le cloud, les responsables occidentaux avertissent.L'hébergement cloud a posé un défi pour les pirates, car il a effectivement réduit la surface d'attaque en termes de capacité à exploiter les vulnérabilités logicielles que les organisations
Les cyber-espions russes derrière la violation de Solarwinds adaptent leurs techniques pour pirater des organisations qui ont déplacé leurs réseaux dans des environnements hébergés dans le cloud, les responsables occidentaux avertissent.L'hébergement cloud a posé un défi pour les pirates, car il a effectivement réduit la surface d'attaque en termes de capacité à exploiter les vulnérabilités logicielles que les organisations
 The Russian cyber spies behind the SolarWinds breach are adapting their techniques to hack into organizations that have moved their networks into cloud-hosted environments, Western officials are warning. Cloud hosting has posed a challenge to hackers because it has effectively reduced the attack surface in terms of their ability to exploit software vulnerabilities that organizations
The Russian cyber spies behind the SolarWinds breach are adapting their techniques to hack into organizations that have moved their networks into cloud-hosted environments, Western officials are warning. Cloud hosting has posed a challenge to hackers because it has effectively reduced the attack surface in terms of their ability to exploit software vulnerabilities that organizations |
Hack Vulnerability Threat Cloud | ★★★ | ||
| 2024-02-26 13:00:31 | Sécuriser la route à venir: aborder les erreurs de configuration du cloud persistant dans l'industrie automobile Securing the Road Ahead: Addressing Persistent Cloud Misconfigurations in the Automotive Industry (lien direct) |
> Explorez une paire d'expositions de sécurité de l'industrie automobile et comment les outils de sécurité appropriés auraient pu empêcher ces mêmes anciens problèmes \\ 'de se produire.Plus tôt ce mois-ci, BMW a été encore une autre victime de dangereux erronés dans leur stockage cloud, qui exposent des clés privées et des données sensibles.Selon un récent article de TechCrunch, un seau de stockage Azure public contenait des «fichiers de script qui comprenaient des informations d'accès, des clés secrètes pour accéder aux adresses de godet privées et des détails sur d'autres services cloud».Pour être juste, BMW n'est pas seul dans ces questions, en fait, selon le rapport de sécurité du cloud de point de contrôle de 2023, [& # 8230;]
>Explore a pair of security exposures from the automotive industry and how the proper security tools could have prevented these \'same old issues\' from happening. Earlier this month, BMW was yet another victim of dangerous misconfigurations in their cloud storage, which exposed private keys and sensitive data. According to a recent article by TechCrunch, a public Azure storage bucket held “script files that included access information, secret keys for accessing private bucket addresses, and details about other cloud services.” To be fair, BMW is not alone in these issues, in fact, according to the 2023 Check Point Cloud Security Report, […] |
Tool Cloud | ★★ | ||
| 2024-02-26 05:03:36 | Les tenants et aboutissants de la confidentialité des données, partie 2: confidentialité par conception en protection de l'information The Ins and Outs of Data Privacy, Part 2: Privacy by Design in Information Protection (lien direct) |
This is the second blog in a two-part series about data privacy. In our previous post, we discussed how data privacy has become increasingly important. And we covered why data loss protection (DLP) and insider threat management (ITM) tools are critical to ensuring data privacy. The shift to “work from anywhere” and the increase in cloud adoption have caused a rise in data loss and insider threats. To defend data from careless, malicious and compromised insiders-and the harm that they cause-security teams must implement data security tools like data loss prevention (DLP) and insider threat management (ITM) platforms. These tools monitor and control how employees interact with data. At the same time, companies are collecting more and more data about employees themselves, like protected health information (PHI). The abundance of all this data-which is being collected and processed in the cloud-creates a critical challenge for security teams. They must protect employee privacy without impeding productivity. In this post, we\'ll explore the topic of privacy by design, which aims to strike a balance between these two challenges. We\'ll cover why it\'s so important. And we\'ll discuss how Proofpoint Information Protection can help you build a modern DLP program and comply with data privacy laws. Why privacy by design matters for DLP and ITM Privacy by design is a framework that embeds privacy into the design of IT systems, infrastructure and business processes. Privacy is not an afterthought. It is considered right from the start-in the initial design phase. What\'s more, it\'s a core component that integrates visibility, transparency and user-centricity into its design. In short, privacy by design ensures that everything is built with the user in mind. Privacy by design is important to DLP and ITM because it helps to: Protect employee rights. Personal data is sacred. Employees expect their personal data to be safe and their rights protected. When a company takes a proactive, transparent approach to data privacy, it helps maintain trust with employees. Comply with privacy laws. Data privacy laws protect people by requiring businesses to keep their data safe and avoid sharing it unethically with third parties. These laws often require companies to tell users exactly how their data is used and collected, and to notify them in the event of a data breach. Failure to comply can lead to hefty fines and penalties, which can damage a firm\'s finances and brand image. Prevent bias in investigations. When user data is kept secure and private, it ensures insider threat investigations maintain their integrity and objectivity. If a user is identified, it could influence a security analyst\'s response to an incident. User privacy helps take emotion and subjectivity out of the picture. Ensure data privacy with Proofpoint DLP and ITM Proofpoint Information Protection includes administration and access controls. These controls can help your business keep data private and meet compliance requirements. Data residency and storage Proofpoint uses regional data centers in the U.S., Europe, Australia and Japan to meet data privacy and data residency requirements. You can control exactly where your data is stored at all of these data centers. For example, you can group your endpoints and map each group to a regional data center. This ensures that data on all those endpoints are stored in that regional center. So, a U.S. realm can manage U.S. endpoint data, which is sent to the U.S. data center. Attribute-based access controls Attribute-based access controls give you a flexible and easy way to manage access to data. You can use these controls to ensure that security analysts have visibility into data on a need-to-know basis only. For instance, you can write granular policies and assign access so that a U.S.-based security analyst can only see U.S. data. They cannot see data in Europe or the Asia-Pacific region. And when an analyst needs to access a specific user\'s data for an | Data Breach Tool Threat Cloud | ★★ | ||
| 2024-02-23 20:51:22 | Astaroth, Mekotio & Ousaban abusant Google Cloud Run dans les campagnes de logiciels malveillants axés sur LATAM Astaroth, Mekotio & Ousaban Abusing Google Cloud Run in LATAM-Focused Malware Campaigns (lien direct) |
#### Description
Depuis septembre 2023, Cisco Talos a observé une augmentation significative du volume de courriels malveillants tirant parti du service Google Cloud Run pour infecter les victimes potentielles avec des chevaux de Troie bancaires.
Les chaînes d'infection associées à ces familles de logiciels malveillants présentent l'utilisation de installateurs Microsoft malveillants (MSIS) qui fonctionnent comme des gouttes ou des téléchargeurs pour la charge utile des logiciels malveillants finaux.Les campagnes de distribution pour ces familles de logiciels malveillants sont liées, Astaroth et Mekotio distribués sous le même projet Google Cloud et Google Cloud Storage Bucket.Ousaban est également abandonné dans le cadre du processus d'infection Astaroth.
Le malware est distribué par e-mails qui sont envoyés à l'aide de thèmes liés aux factures ou aux documents financiers et fiscaux, et se présentent parfois comme étant envoyés par l'agence fiscale du gouvernement local dans le pays ciblé.Les e-mails contiennent des hyperliens vers Google Cloud Run, qui peuvent être identifiés en raison de l'utilisation de l'application Run [.] Comme domaine de niveau supérieur (TLD).Lorsque les victimes accèdent à ces hyperliens, elles sont redirigées vers les services Web d'exécution du cloud déployés par les acteurs de la menace et ont livré les composants nécessaires pour initier le processus d'infection.
#### URL de référence (s)
1. https://blog.talosintelligence.com/google-cloud-run-abuse/
#### Date de publication
20 février 2024
#### Auteurs)
Edmund Brumaghin
Ashley Shen
Holger Unterbrink
Guilherme Veree
#### Description Since September 2023, Cisco Talos have observed a significant increase in the volume of malicious emails leveraging the Google Cloud Run service to infect potential victims with banking trojans. The infection chains associated with these malware families feature the use of malicious Microsoft Installers (MSIs) that function as droppers or downloaders for the final malware payload(s). The distribution campaigns for these malware families are related, with Astaroth and Mekotio being distributed under the same Google Cloud Project and Google Cloud storage bucket. Ousaban is also being dropped as part of the Astaroth infection process. The malware is being distributed via emails that are being sent using themes related to invoices or financial and tax documents, and sometimes pose as being sent from the local government tax agency in the country being targeted. The emails contain hyperlinks to Google Cloud Run, which can be identified due to the use of run[.]app as the top-level domain (TLD). When victims access these hyperlinks, they are redirected to the Cloud Run web services deployed by the threat actors and delivered the components necessary to initiate the infection process. #### Reference URL(s) 1. https://blog.talosintelligence.com/google-cloud-run-abuse/ #### Publication Date February 20, 2024 #### Author(s) Edmund Brumaghin Ashley Shen Holger Unterbrink Guilherme Venere |
Malware Threat Cloud | ★★ | ||
| 2024-02-23 11:00:00 | Détection des connexions anormales O365 et des techniques d'évasion Detecting anomalous O365 logins and evasion techniques (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Summary Businesses across multiple industries, regardless of size, are at risk of being targeted with Microsoft 365 phishing campaigns. These campaigns trick users into visiting fake Microsoft login page where threat actors capture the user’s credentials. Even accounts with MFA can be victim to these types of attacks. There are several ways in which MFA is being bypassed with these types of campaigns. MFA Fatigue is one of the ways threat actors are bypassing MFA and this method attempts to exploit human error by repeatedly logging in with the stolen credentials causing an overwhelming number of MFA prompts in attempts to get the user to approve the login. Another MFA bypass technique is SIM Swapping. A SIM card is a small chip that your mobile carrier uses to hold identification information to tie your phone to you and your mobile carrier. Threat actors have found a weakness in this because there are scenarios where a customer may need a new SIM card (for example, they lost their phone). Carriers can transfer your identification information from your old SIM card to new one. SIM Swapping is when a threat actor abuses this feature and impersonates you to convince your mobile carrier to switch your phone number to a SIM card that is in the threat actor’s possession. This then allows the threat actor to receive MFA codes sent to your number via phone call or SMS. | Tool Threat Mobile Cloud | ★★★ | ||
| 2024-02-23 00:00:00 | Des millions d'URL malveillants indétectables générés via les services de violence du cloud public et du Web 3.0 Millions of Undetectable Malicious URLs Generated Via the Abuse of Public Cloud and Web 3.0 Services (lien direct) |
Pas de details / No more details | Cloud | ★★ | ||
| 2024-02-22 16:53:12 | UOB, Samsung Back Singapore \\'s Startale Labs en 7 millions de dollars web3 push UOB, Samsung Back Singapore\\'s Startale Labs in $7 Million Web3 Push (lien direct) |
par owais sultan
Startale Labs, le développeur derrière les principaux produits Web3 du Japon comme Astar Network et Startale Web3 Cloud, a sécurisé & # 8230;
Ceci est un article de HackRead.com Lire le post original: UOB, Samsung Back Singapour & # 8217; s startale labs en 7 millions de dollars web3 push
By Owais Sultan Startale Labs, the developer behind Japan’s leading Web3 products like Astar Network and Startale Web3 Cloud, has secured… This is a post from HackRead.com Read the original post: UOB, Samsung Back Singapore’s Startale Labs in $7 Million Web3 Push |
Cloud | ★★ | ||
| 2024-02-22 16:00:00 | Résoudre le défi de l'expérience utilisateur Sase avec la gestion de l'expérience numérique proactive (P-DEM) Solving the SASE User Experience Challenge with Proactive Digital Experience Management (P-DEM) (lien direct) |
> La transformation numérique et ses défis à l'époque de la transformation numérique de la transformation numérique, les organisations se déplacent rapidement vers une infrastructure numérique distribuée et dynamique.Cette nouvelle réalité est caractérisée par des effectifs hybrides, des logiciels en tant que service (SaaS) et l'hébergement cloud.Bien que cette transformation apporte de nombreux avantages, il introduit également des défis importants pour les organisations informatiques, en particulier en termes [& # 8230;]
>Digital transformation and its challenges In today’s era of digital transformation, organizations are rapidly shifting towards a distributed and dynamic digital infrastructure. This new reality is characterized by hybrid workforces, software as a service (SaaS), and cloud hosting. While this transformation brings numerous benefits, it also introduces significant challenges for IT organizations, particularly in terms […] |
Cloud | ★★ |
To see everything:
Our RSS (filtrered)
