What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-11-04 17:56:07 | Android VPNS pour obtenir des badges d'audit dans Google Play Store s'ils ne sont pas comiques de merde comiquement Android VPNs to get audit badges in Google Play Store if they aren\\'t comically crap (lien direct) |
pas de promesse qu'il est en fait sécurisé, juste qu'il ne fait rien de toute évidemment stupide google veut aider les utilisateurs d'Android plus fiables grâce à une meilleure alerte de badge sur des audits indépendants.…
No promises it\'s actually secure, just that it doesn\'t do anything obviously dumb Google wants to help Android users find more trustworthy VPN apps through better badging alerting to independent audits.… |
Mobile | ★★ | ||
| 2023-11-04 11:08:00 | Google Play Store introduit \\ 'Indevance Review \\' Badge for Apps Google Play Store Introduces \\'Independent Security Review\\' Badge for Apps (lien direct) |
Google déploie un badge "Revue de sécurité indépendante" dans la section de sécurité des données de Play Store \\ pour les applications Android qui ont subi une audit d'évaluation de la sécurité des applications mobiles (MASA).
"Nous avons lancé cette bannière à partir des applications VPN en raison de la quantité sensible et importante de données utilisateur que ces applications gèrent", a déclaré Nataliya Stanetsky de l'équipe Android Security and Privacy.
Google is rolling out an "Independent security review" badge in the Play Store\'s Data safety section for Android apps that have undergone a Mobile Application Security Assessment (MASA) audit. "We\'ve launched this banner beginning with VPN apps due to the sensitive and significant amount of user data these apps handle," Nataliya Stanetsky of the Android Security and Privacy Team said. |
Mobile | ★★ | ||
| 2023-11-04 08:00:00 | Doctor Dignity – L\'IA médicale open-source (lien direct) | Doctor Dignity est un projet open-source qui utilise Llama2 de Meta et l'IA pour réussir l'examen de licence médicale américain. Disponible sur iOS, Android et Web, il préserve la confidentialité des patients et encourage les contributions pour améliorer ses fonctionnalités. Il fonctionne sans connexion internet et intègre une expérience d'apprentissage en ligne avec des retours humains. Il est utile pour les étudiants en médecine, les médecins et les passionnés de technologie. | Mobile | ★★★ | ||
| 2023-11-03 23:00:11 | Apple Slams Android comme un \\ 'un dispositif de suivi massif \\' dans les diapositives internes révélées dans Google Antitrust Battle Apple slams Android as a \\'massive tracking device\\' in internal slides revealed in Google antitrust battle (lien direct) |
Whinges sur la position de la confidentialité de Chrome Maker \\ tout en prenant des milliards pour, euh, à utiliser son moteur de recherche Le ministère américain de la Justice a publié une série de documents dans son procès antitrust contre Google, y compris hier, y comprisDes documents qui révèlent qu'Apple a conclu son accord de recherche par défaut avec la chocolaterie malgré des réservations de confidentialité considérables.…
Whinges about Chrome maker\'s privacy stance while taking billions to, er, use its search engine The US Department of Justice released a series of documents in its antitrust trial against Google yesterday, including documents that reveal Apple made its default search deal with the Chocolate Factory despite considerable privacy reservations. … |
Mobile | ★★ | ||
| 2023-11-03 22:56:10 | Mozilla dit aux développeurs d'extension de se préparer à enfin aller mobile Mozilla tells extension developers to get ready to finally go mobile (lien direct) |
Firefox Android Add-ons à venir bientôt Enfin, Mozilla prévoit de faire des extensions de navigateur, également connues sous le nom de modules complémentaires, disponibles pour Firefox sur Android, à un moment donné après le 21 novembre attenduversion de la version 120 du navigateur \\.…
Firefox Android add-ons coming soon At long last, Mozilla is planning to make browser extensions, also known as add-ons, available for Firefox on Android, at some point following the expected November 21 release of the browser\'s version 120 build.… |
Mobile | ★★ | ||
| 2023-11-03 15:05:00 | Les logiciels espions de Canesspy découverts dans les versions WhatsApp modifiées CanesSpy Spyware Discovered in Modified WhatsApp Versions (lien direct) |
Les chercheurs en cybersécurité ont déniché un certain nombre de mods WhatsApp pour Android qui sont équipés d'un module de logiciel espion sur baptisé Canesspy.
Ces versions modifiées de l'application de messagerie instantanée ont été observées propagées via des sites Web sommaires annonçant de tels logiciels ainsi que des canaux télégrammes utilisés principalement par les haut-parleurs arabes et azerbaïdjanais, dont l'un compte 2 millions d'utilisateurs.
"Le trojanisé
Cybersecurity researchers have unearthed a number of WhatsApp mods for Android that come fitted with a spyware module dubbed CanesSpy. These modified versions of the instant messaging app have been observed propagated via sketchy websites advertising such software as well as Telegram channels used primarily by Arabic and Azerbaijani speakers, one of which boasts 2 million users. "The trojanized |
Mobile | ★★ | ||
| 2023-11-03 14:05:00 | Les logiciels espions conçus pour les mods télégrammes ciblent également les modules complémentaires WhatsApp Spyware Designed for Telegram Mods Also Targets WhatsApp Add-Ons (lien direct) |
Les chercheurs ont découvert que les logiciels espions conçus pour voler des appareils Android et des mods Telegram peuvent également atteindre les utilisateurs de WhatsApp.
Researchers discovered spyware designed to steal from Android devices and from Telegram mods can also reach WhatsApp users. |
Mobile | ★★★ | ||
| 2023-11-03 12:48:58 | Google Play ajoute des badges d'audit de sécurité pour les applications VPN Android Google Play adds security audit badges for Android VPN apps (lien direct) |
Google Play, l'App Store officiel d'Android \\, marque maintenant des applications VPN avec un badge \\ 'de sécurité indépendante \' s'ils effectuaient un audit de sécurité indépendant de leur logiciel et de leur plate-forme.[...]
Google Play, Android\'s official app store, is now tagging VPN apps with an \'independent security reviews\' badge if they conducted an independent security audit of their software and platform. [...] |
Mobile | ★★★ | ||
| 2023-11-03 10:04:59 | Premier combiné avec MTE sur le marché First handset with MTE on the market (lien direct) |
By Mark Brand, Google Project ZeroIntroduction It\'s finally time for me to fulfill a long-standing promise. Since I first heard about ARM\'s Memory Tagging Extensions, I\'ve said (to far too many people at this point to be able to back out…) that I\'d immediately switch to the first available device that supported this feature. It\'s been a long wait (since late 2017) but with the release of the new Pixel 8 / Pixel 8 Pro handsets, there\'s finally a production handset that allows you to enable MTE! The ability of MTE to detect memory corruption exploitation at the first dangerous access is a significant improvement in diagnostic and potential security effectiveness. The availability of MTE on a production handset for the first time is a big step forward, and I think there\'s real potential to use this technology to make 0-day harder. I\'ve been running my Pixel 8 with MTE enabled since release day, and so far I haven\'t found any issues with any of the applications I use on a daily basis1, or any noticeable performance issues. Currently, MTE is only available on the Pixel as a developer option, intended for app developers to test their apps using MTE, but we can configure it to default to synchronous mode for all2 apps and native user mode binaries. This can be done on a stock image, without bootloader unlocking or rooting required - just a couple of debugger commands. We\'ll do that now, but first:Disclaimer This is absolutely not a supported device configuration; and it\'s highly likely that you\'ll encounter issues with at least some applications crashing or failing to run correctly with MTE if you set your device up in this way. This is how I\'ve configured my personal Pixel 8, and so far I\'ve not experienced any issues, but this was somewhat of a surprise to me, and I\'m still waiting to see what the first app that simply won\'t work at all will be...Enabling MTE on Pixel 8/Pixel 8 Pro | Tool Mobile | ★★ | ||
| 2023-11-03 04:15:21 | CVE-2023-36621 (lien direct) | Un problème a été découvert dans l'application de contrôle parental de Boomerang via 13.83 pour Android.L'enfant peut utiliser le mode sûr pour éliminer toutes les restrictions temporairement ou désinstaller la demande sans que les parents ne le remarquent.
An issue was discovered in the Boomerang Parental Control application through 13.83 for Android. The child can use Safe Mode to remove all restrictions temporarily or uninstall the application without the parents noticing. |
Mobile | |||
| 2023-11-03 04:15:21 | CVE-2023-36620 (lien direct) | Un problème a été découvert dans l'application de contrôle parental de Boomerang avant 13.83 pour Android.L'application manque l'attribut Android: allongBackup = "false" dans le manifeste.Cela permet à l'utilisateur de sauvegarder la mémoire interne de l'application sur un PC.Cela donne à l'utilisateur l'accès au jeton API qui est utilisé pour authentifier les demandes à l'API.
An issue was discovered in the Boomerang Parental Control application before 13.83 for Android. The app is missing the android:allowBackup="false" attribute in the manifest. This allows the user to backup the internal memory of the app to a PC. This gives the user access to the API token that is used to authenticate requests to the API. |
Mobile | |||
| 2023-11-02 23:02:15 | Google abandonne cette API qui ressemblait un peu à DRM pour les sites Web Google gives up on that API that looked more than a bit like DRM for websites (lien direct) |
Au lieu de cela, Chocolate Factory se concentre sur une attestation plus limitée pour Android WebViews Au milieu de l'inquiétude croissante de la communauté, Google dit qu'il ne développera plus de technologies controversées qui auraient lutté contre la fraude en ligne, mais les critiques ressemblaient davantage à DRMpour les sites Web… | Mobile | ★★★ | ||
| 2023-11-02 20:13:20 | Apple glisse de 2013 Skewer Android comme "un appareil de suivi massif" Apple slides from 2013 skewer Android as “a massive tracking device” (lien direct) |
Mais Apple voulait également savoir quels résultats les utilisateurs ont cliqué sur Google à partir d'iPhones.
But Apple also wanted to know what results users clicked on Google from iPhones. |
Mobile | ★★ | ||
| 2023-11-02 15:17:00 | Utilisateurs de WhatsApp de langue arabophone ciblés avec des logiciels espions Arabic-speaking WhatsApp users targeted with spyware (lien direct) |
 Les pirates inconnus ciblent les utilisateurs en Arabie saoudite, au Yémen et en Azerbaïdjan avec l'espionnage des logiciels malveillants distribués via des mods WhatsApp créés par l'utilisateur qui personnalisent ou ajoutent de nouvelles fonctionnalités au service.Dans la dernière campagne, les chercheurs de la société de cybersécurité Kaspersky ont découvert des mods WhatsApp auparavant inoffensifs qui avaient reçu un code malveillant conçu pour espionner sur Android
Les pirates inconnus ciblent les utilisateurs en Arabie saoudite, au Yémen et en Azerbaïdjan avec l'espionnage des logiciels malveillants distribués via des mods WhatsApp créés par l'utilisateur qui personnalisent ou ajoutent de nouvelles fonctionnalités au service.Dans la dernière campagne, les chercheurs de la société de cybersécurité Kaspersky ont découvert des mods WhatsApp auparavant inoffensifs qui avaient reçu un code malveillant conçu pour espionner sur Android
 Unknown hackers are targeting users in Saudi Arabia, Yemen and Azerbaijan with spying malware distributed through user-created WhatsApp mods that customize or add new features to the service. In the latest campaign, researchers at the cybersecurity firm Kaspersky discovered previously harmless WhatsApp mods that had been injected with malicious code designed to spy on Android
Unknown hackers are targeting users in Saudi Arabia, Yemen and Azerbaijan with spying malware distributed through user-created WhatsApp mods that customize or add new features to the service. In the latest campaign, researchers at the cybersecurity firm Kaspersky discovered previously harmless WhatsApp mods that had been injected with malicious code designed to spy on Android |
Malware Mobile | ★★★ | ||
| 2023-11-02 13:53:20 | AppDome s'associe à JetBrains TeamCity pour automatiser la livraison des applications mobiles sécurisées Appdome Partners with JetBrains TeamCity to Automate Delivery of Secure Mobile Apps (lien direct) |
AppDome s'associe à JetBrains TeamCity pour automatiser la livraison d'applications mobiles sécurisées
Le partenariat amène Android et IOS Cyber Defense Automation à l'intérieur du pipeline CI / CD de JetBrains TeamCity
-
nouvelles commerciales
Appdome Partners with JetBrains TeamCity to Automate Delivery of Secure Mobile Apps Partnership Brings Android and iOS Cyber Defense Automation Inside the JetBrains TeamCity CI/CD Pipeline - Business News |
Mobile | ★★ | ||
| 2023-11-02 13:00:00 | Collection d'adhésion de Lenovo \\'s Tab: une preuve de concept de vêtements pour prendre des comprimés à l'extérieur Lenovo\\'s Tab Wear Collection: A Clothing Proof-of-Concept for Taking Tablets Outdoors (lien direct) |
Lenovo s'est associé à des créateurs de mode pour faire des vêtements d'extérieur pour transporter et utiliser - ses tablettes Android à l'extérieur de la maison.
Lenovo teamed up with fashion designers to make outerwear for carrying-and using-its Android tablets outside the home. |
Mobile | ★★ | ||
| 2023-11-02 12:00:24 | Plus de moyens pour les utilisateurs d'identifier les applications testées sur la sécurité indépendante sur Google Play More ways for users to identify independently security tested apps on Google Play (lien direct) |
Posted by Nataliya Stanetsky, Android Security and Privacy Team
Keeping Google Play safe for users and developers remains a top priority for Google. As users increasingly prioritize their digital privacy and security, we continue to invest in our Data Safety section and transparency labeling efforts to help users make more informed choices about the apps they use.
Research shows that transparent security labeling plays a crucial role in consumer risk perception, building trust, and influencing product purchasing decisions. We believe the same principles apply for labeling and badging in the Google Play store. The transparency of an app\'s data security and privacy play a key role in a user\'s decision to download, trust, and use an app.
Highlighting Independently Security Tested VPN Apps
Last year, App Defense Alliance (ADA) introduced MASA (Mobile App Security Assessment), which allows developers to have their apps independently validated against a global security standard. This signals to users that an independent third-party has validated that the developers designed their apps to meet these industry mobile security and privacy minimum best practices and the developers are going the extra mile to identify and mitigate vulnerabilities. This, in turn, makes it harder for attackers to reach users\' devices and improves app quality across the ecosystem. Upon completion of the successful validation, Google Play gives developers the option to declare an “Independent security review” badge in its Data Safety section, as shown in the image below. While certification to baseline security standards does not imply that a product is free of vulnerabilities, the badge associated with these validated apps helps users see at-a-glance that a developer has prioritized security and privacy practices and committed to user safety.
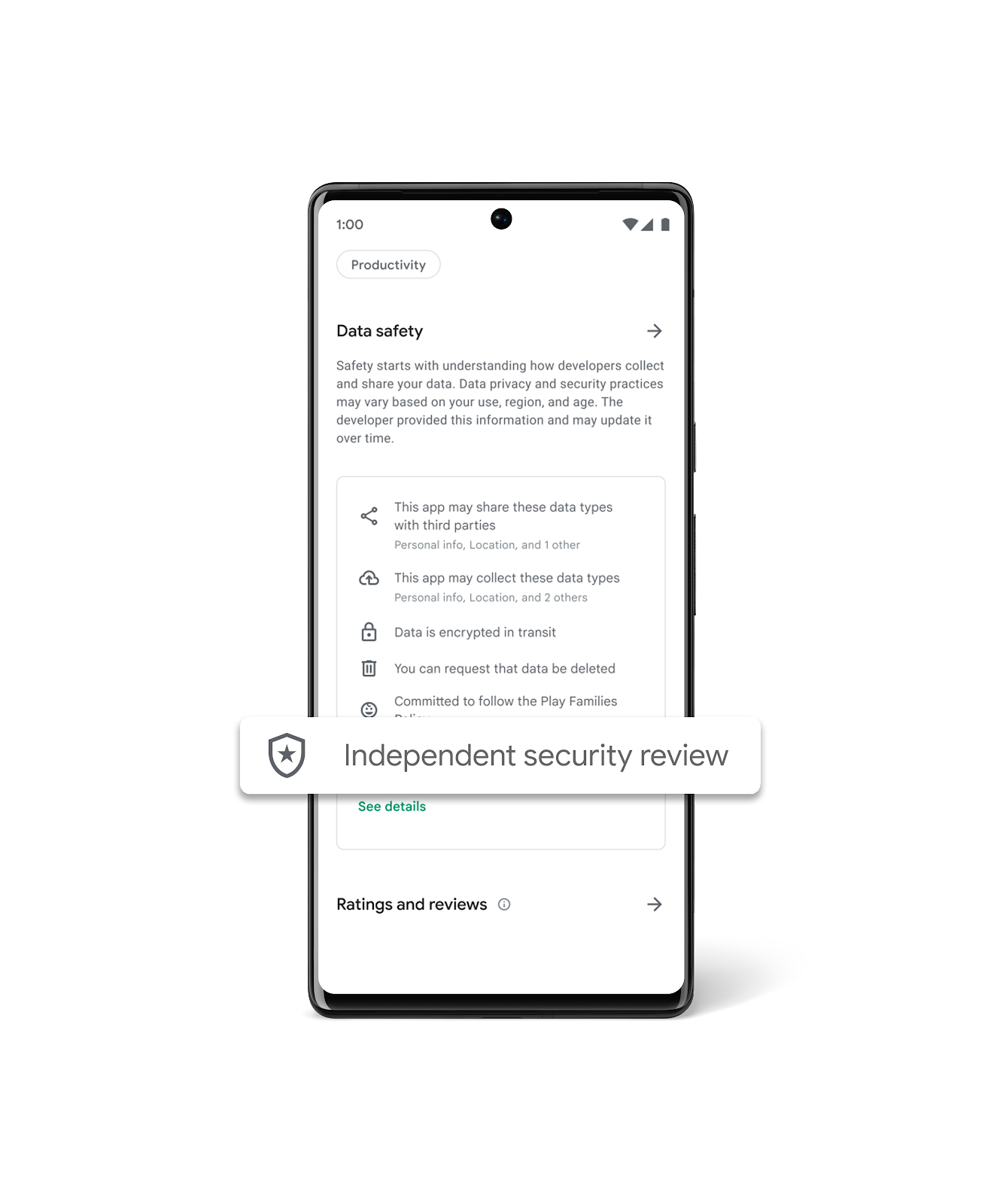 To help give users a simplified view of which apps have undergone an independent security validation, we\'re introducing a new Google Play store banner for specific app types, starting with VPN apps. We\'ve launched this banner beginning with VPN apps due to the sensitive and significant amount of user data these apps handle. When a user searches for VPN apps, they will now see a banner at the top of Google Play that educates them about the “Independent security review” badge in the Data Safety Section. Users also have the ability to “Learn More”, which redirects them to the App Validation Directory, a centralized place to view all VPN apps that have been independently security reviewed. Users can also discover additional technical assessment details in the App Validation Directory, helping them to make more informed decisions about what VPN apps to download, use, and trust with their data.
To help give users a simplified view of which apps have undergone an independent security validation, we\'re introducing a new Google Play store banner for specific app types, starting with VPN apps. We\'ve launched this banner beginning with VPN apps due to the sensitive and significant amount of user data these apps handle. When a user searches for VPN apps, they will now see a banner at the top of Google Play that educates them about the “Independent security review” badge in the Data Safety Section. Users also have the ability to “Learn More”, which redirects them to the App Validation Directory, a centralized place to view all VPN apps that have been independently security reviewed. Users can also discover additional technical assessment details in the App Validation Directory, helping them to make more informed decisions about what VPN apps to download, use, and trust with their data.
|
Tool Vulnerability Mobile Technical | ★★ | ||
| 2023-11-02 11:30:00 | Bugy octets # 216 & # 8211;Injections SQL, Android XSS et rédaction de rapports de qualité Bug Bytes #216 – SQL injections, Android XSS and Writing Quality Reports (lien direct) |
> Bug Bytes est une newsletter hebdomadaire organisée par les membres de la communauté Bug Bounty.La deuxième série est organisée par InsiderPhd.Chaque semaine, elle nous tient à jour avec une liste complète des articles, des outils, des tutoriels et des ressources.Ce numéro couvre la semaine du 23 octobre au 29 octobre Intigriti News de mon cahier
>Bug Bytes is a weekly newsletter curated by members of the bug bounty community. The second series is curated by InsiderPhD. Every week, she keeps us up to date with a comprehensive list of write-ups, tools, tutorials and resources. This issue covers the week from October 23rd to October 29th Intigriti News From my notebook |
Tool Mobile Technical | ★★★ | ||
| 2023-11-01 13:00:00 | Tirer parti des normes NIST pour rationaliser votre stratégie de sécurité sur mobile axée sur le mobile Leveraging NIST Standards to Streamline Your Mobile-First Security Strategy (lien direct) |
> Ce webinaire enseigne comment les professionnels de la cybersécurité s'appuient sur des ressources, telles que les normes NIST, pour développer leur approche de sécurité des appareils mobiles.
>This webinar teaches how cybersecurity professionals rely on resources, such as NIST standards, to develop their mobile device security approach. |
Mobile | ★★★ | ||
| 2023-10-25 15:00:00 | Gardez les résidents \\ 'les appareils mobiles en sécurité avec Secure Boston Keep Residents\\' Mobile Devices Safe with Secure Boston (lien direct) |
Secure Boston garde les appareils mobiles de Boston en sécurité avec les alertes du réseau Wi-Fi, la sécurité des applications Android, la falsification du système & # 038;détection de phishing, et plus.
Secure Boston keeps Boston residents\' mobile devices safe with Wi-Fi network alerts, Android app safety, system tampering & phishing detection, and more. |
Mobile | ★★★ | ||
| 2023-10-16 17:41:00 | Spynote: Méfiez-vous de ce cheval de Troie Android qui enregistre les appels audio et téléphoniques SpyNote: Beware of This Android Trojan that Records Audio and Phone Calls (lien direct) |
Le cheval de Troie bancaire Android connu sous le nom de Spynote a été disséqué pour révéler ses diverses fonctionnalités de collecte d'informations.
Selon F-Secure, les campagnes de phishing SMS impliquant les victimes potentielles de l'astuce spyware pour installer l'application en cliquant sur le lien intégré, selon F-Secure.
En plus de demander des autorisations invasives pour accéder aux journaux d'appels, à la caméra, aux messages SMS et
The Android banking trojan known as SpyNote has been dissected to reveal its diverse information-gathering features. Typically spread via SMS phishing campaigns, attack chains involving the spyware trick potential victims into installing the app by clicking on the embedded link, according to F-Secure. Besides requesting invasive permissions to access call logs, camera, SMS messages, and external |
Mobile | ★★★ | ||
| 2023-10-16 11:18:28 | Fake \\ 'RedAlert \\' Rocket Alert App for Israel installe Android Spyware Fake \\'RedAlert\\' rocket alert app for Israel installs Android spyware (lien direct) |
Les utilisateurs d'Android israéliens sont ciblés par une version malveillante de l'application \\ 'redalert - Rocket Alertes \' qui, bien qu'elle offre la fonctionnalité promise, agit comme un logiciel espion en arrière-plan.[...]
Israeli Android users are targeted by a malicious version of the \'RedAlert - Rocket Alerts\' app that, while it offers the promised functionality, acts as spyware in the background. [...] |
Mobile | ★★ | ||
| 2023-10-04 20:34:30 | Transformer la sécurité basée sur l'identité avec la défense des menaces mobiles de Zimperium et la plate-forme de protection des menaces d'identité OKTA Transforming Identity-Based Security with Zimperium Mobile Threat Defense and Okta Identity Threat Protection Platform (lien direct) |
> Zimperium est ravi d'annoncer qu'il s'agit d'un partenaire d'intégration fondateur de la protection des menaces d'identité d'Okta \\ avec Okta AI, offrant une protection contre les menaces d'identité en temps réel et améliorant la sécurité des clients conjoints.
>Zimperium is excited to announce it is a founding integration partner of Okta\'s Identity Threat Protection with Okta AI, delivering real-time identity threat protection and enhancing the security of joint customers. |
Threat Mobile | ★★★ | ||
| 2023-10-03 14:12:57 | La mise à jour de la sécurité Android Octobre corrige les jours zéro exploités dans les attaques Android October security update fixes zero-days exploited in attacks (lien direct) |
Google a publié les mises à jour de sécurité d'octobre 2023 pour Android, abordant 54 vulnérabilités uniques, dont deux connues pour être activement exploitées.[...]
Google has released the October 2023 security updates for Android, addressing 54 unique vulnerabilities, including two known to be actively exploited. [...] |
Vulnerability Mobile | ★★★ | ||
| 2023-09-29 18:43:00 | Le fournisseur de logiciels espions cible les organisations égyptiennes avec une chaîne d'exploitation iOS rare Spyware Vendor Targets Egyptian Orgs With Rare iOS Exploit Chain (lien direct) |
La société israélienne a développé des logiciels malveillants mobiles très ciblés qui rendraient tout jaloux.
The Israeli company developed highly-targeted, mobile malware that would make any APT jealous. |
Malware Mobile | ★★★ | ||
| 2023-09-28 11:25:36 | La société d'acquisition russe zéro-jour offre 20 millions de dollars pour Android, iOS exploits Russian Zero-Day Acquisition Firm Offers $20 Million for Android, iOS Exploits (lien direct) |
La société d'acquisition russe zéro-jour Operation Zero propose désormais 20 millions de dollars pour les chaînes d'exploitation Android complètes et iOS.
Russian zero-day acquisition firm Operation Zero is now offering $20 million for full Android and iOS exploit chains. |
Threat Mobile | ★★★★ | ||
| 2023-09-08 08:30:00 | Apple Patches deux jours zéro exploités dans les attaques de pégase Apple Patches Two Zero-Days Exploited in Pegasus Attacks (lien direct) |
Les utilisateurs d'appareils iOS ont demandé à activer le mode de verrouillage
Users of iOS devices urged to enable lockdown mode |
Patching Mobile | ★★ | ||
| 2023-09-06 19:32:00 | Alerte zéro-jour: la dernière mise à jour du patch Android comprend une correction pour une faille nouvellement activement exploitée Zero-Day Alert: Latest Android Patch Update Includes Fix for Newly Actively Exploited Flaw (lien direct) |
Google a déployé des correctifs de sécurité mensuels pour Android afin de traiter un certain nombre de défauts, y compris un bug zéro-jour qui, selon lui, pourrait avoir été exploité dans la nature.
Suivi en CVE-2023-35674, la vulnérabilité de haute sévérité est décrite comme un cas d'escalade de privilèges impactant le cadre Android.
«Il y a des indications que le CVE-2023-35674 peut être sous une exploitation limitée et ciblée», le
Google has rolled out monthly security patches for Android to address a number of flaws, including a zero-day bug that it said may have been exploited in the wild. Tracked as CVE-2023-35674, the high-severity vulnerability is described as a case of privilege escalation impacting the Android Framework. “There are indications that CVE-2023-35674 may be under limited, targeted exploitation,” the |
Vulnerability Mobile | ★★ | ||
| 2023-08-29 11:00:00 | Dévoiler les tactiques de la lapsus $: une revue des vecteurs d'attaques internes, de l'exploitation des appareils mobiles et des techniques d'ingénierie sociale Unveiling the Tactics of Lapsus$: A Review of Internal Attacks Vectors, Mobile Device Exploitation, and Social Engineering Techniques (lien direct) |
> Le 10 août 2023, le rapport du Département américain de la sécurité intérieure (DHS) a publié le rapport du Cyber Safety Review Board (CSRB) résumant les conclusions de son examen dans les activités du groupe d'acteur de menace Lapsus $, qui, à la fin de 2021 et à continuerà la fin de 2022, a tenté d'extorquer des dizaines de mondiaux bien connus [& # 8230;]
>On August 10, 2023, the U.S. Department of Homeland Security (DHS) released the Cyber Safety Review Board (CSRB) report summarizing the findings of its review into the activities of threat actor group Lapsus$, who, beginning in late 2021 and continuing into late 2022, attempted to extort dozens of well-known global […] |
Threat Mobile | ★★★ | ||
| 2023-08-18 00:00:00 | Rejoignez notre équipe Cyber Skills!Libérez votre potentiel dans le développement de la sécurité des réseaux à Munster Technological University! Join Our Cyber Skills Team! Unleash Your Potential in Network Security Development at Munster Technological University! (lien direct) |
Une opportunité incroyable vous attend alors que nous recherchons des développeurs passionnés de sécurité du réseau pour devenir membres intégraux de notre équipe dynamique des Cyberskills au Nimbus Research Center de Munster Technological University.
À propos du rôle:
En tant que développeur de sécurité de réseau, vous travaillerez dans le cadre d'une équipe fournissant des services d'éducation et de recherche sur la cybersécurité à l'industrie et à la recherche des progrès de la cybersécurité.Vous aurez l'autonomie pour créer et fournir des services de cybersécurité pour des projets de recherche avec des clients de l'industrie, des chercheurs et des professeurs.Travaillant à la fois sur un Airbus Mobile et une cyber-gamme basée sur le cloud, vous collaborerez avec des experts de premier plan en cybersécurité de l'industrie et du monde universitaire.Ces cyber-gammes sont des infrastructures de cybersécurité à la pointe de la technologie et sont une offre unique chez Cyber Skills et MTU.
Exigences:
Connaissance des concepts de réseautage et de cybersécurité logiciels.
Boulangement éprouvé de la recherche et du développement de solutions de sécurité.
SORTS SOB SWER ET SCRIPTING SACTIONNEMENTS.
Capacité à s'adapter à l'évolution des pratiques de travail.
Couramment l'anglais parlé et écrit
Volonté de travailler des heures flexibles et de voyager à l'échelle nationale au besoin.
Une qualification de troisième niveau appropriée au niveau NFQ 8 ou équivalent ou supérieur.
Date limite d'inscription:
Ne manquez pas cette opportunité excitante!Soumettez votre demande avant 13 h 00 le mardi 12 septembre 2023 pour être considérée pour ce poste.
Pour en savoir plus sur ce que le travail implique, téléchargez la spécification du travail ici.
Toutes les candidatures doivent être présentées en ligne sur https://www.mtu.ie/vacancies/ sélectionner Nimbus comme département.
An incredible opportunity awaits you as we seek passionate Network Security Developers to become integral members of our dynamic CyberSkills team at the Nimbus Research Centre in Munster Technological University. About the Role: As a Network Security Developer, you\'ll be working as part of a team providing cybersecurity education and research services to Industry and researching cybersecurity advancements. You will have the autonomy to create and deliver cyber security services for research projects with industry clients, researchers, and lecturers. Working on both an AIRBUS mobile and a cloud based Cyber Range, you will be collaborating with leading experts in cybersecurity from both industry and academia. These Cyber Ranges are state-of-the-art cybersecurity infrastructures and are a unique offering at Cyber Skills and MTU. Requirements: Knowledge of Networking and Software Cyber security concepts. Proven track record of research and development of security solutions. Strong SW development and scripting skills. Ability to adapt to changing working practices. Fluent in spoken and written English Willingness to work flexible hours and travel nationally as required. An appropriate third-level qualification at NFQ level 8 or equivalent or above. Application Deadline: Don\'t miss out on this exciting opportunity! Submit your application by 1.00 pm on Tuesday, 12th September 2023 to be considered for this position. To read more about what the job entails, download the job specification here. All applications must be made online at https://www.mtu.ie/vacancies/ select Nimbus as department. |
Mobile Cloud | ★★ | ||
| 2023-08-09 12:19:00 | Nouvelle fonctionnalité de sécurité Android 14: les administrateurs informatiques peuvent désormais désactiver les réseaux 2G New Android 14 Security Feature: IT Admins Can Now Disable 2G Networks (lien direct) |
Google a introduit une nouvelle fonctionnalité de sécurité dans Android 14 qui permet aux administrateurs informatiques de désactiver la prise en charge des réseaux cellulaires 2G dans leur flotte de périphériques gérés.
Le géant de la recherche a déclaré qu'il introduisait un deuxième paramètre utilisateur pour désactiver la prise en charge, au niveau du modèle, pour les connexions cellulaires à nuls nuls.
"Le modèle de sécurité Android suppose que tous les réseaux sont hostiles pour protéger les utilisateurs
Google has introduced a new security feature in Android 14 that allows IT administrators to disable support for 2G cellular networks in their managed device fleet. The search giant said it\'s introducing a second user setting to turn off support, at the model level, for null-ciphered cellular connections. "The Android Security Model assumes that all networks are hostile to keep users safe from |
Mobile | ★★★ | ||
| 2023-08-04 13:36:07 | Adware invisible: dévoilement de la fraude publicitaire ciblant les utilisateurs d'Android Invisible Adware: Unveiling Ad Fraud Targeting Android Users (lien direct) |
>  Rendu par Sangryol Ryu, chercheur à menace McAfee, nous vivons dans un monde où les publicités sont partout, et ce n'est pas une surprise ...
Rendu par Sangryol Ryu, chercheur à menace McAfee, nous vivons dans un monde où les publicités sont partout, et ce n'est pas une surprise ...
>  Authored by SangRyol Ryu, McAfee Threat Researcher We live in a world where advertisements are everywhere, and it’s no surprise...
Authored by SangRyol Ryu, McAfee Threat Researcher We live in a world where advertisements are everywhere, and it’s no surprise...
|
Threat Mobile | ★★ | ||
| 2023-07-28 00:00:00 | Cherryblos connexes et logiciels malveillants Android associés impliqués dans des campagnes d'escroquerie Related CherryBlos and FakeTrade Android Malware Involved in Scam Campaigns (lien direct) |
L'équipe du Service de réputation d'application mobile de Trend Micro \'s Mobile a découvert deux nouvelles familles de logiciels malveillants Android impliqués dans des crypto-monnaies et des campagnes d'escroquerie motivées financièrement ciblant les utilisateurs d'Android.
Trend Micro\'s Mobile Application Reputation Service (MARS) team discovered two new related Android malware families involved in cryptocurrency-mining and financially-motivated scam campaigns targeting Android users. |
Malware Mobile Prediction | ★★ | ||
| 2023-07-20 09:34:15 | Lookout découvre un logiciel de surveillance Android avancée lié à l'APT41 de la Chine Lookout Uncovers Advanced Android Surveillanceware Linked To China\\'s APT41 (lien direct) |
Hier, Lookout, Inc., a annoncé la découverte de logiciels de surveillance Android sophistiqués connus sous le nom de Wyrmspy et Dragonegg, qui a été lié au groupe d'espionnage chinois Apt41 (aka Double Dragon, Barium et Winnti).Bien qu'il ait été inculpé de plusieurs accusations du gouvernement américain pour ses attaques contre plus de 100 entreprises privées et publiques aux États-Unis [& # 8230;]
Yesterday, Lookout, Inc., announced the discovery of sophisticated Android surveillanceware known as WyrmSpy and DragonEgg, which has been linked to the Chinese espionage group APT41 (AKA Double Dragon, BARIUM and Winnti). Despite being indicted on multiple charges by the U.S. government for its attacks on more than 100 private and public enterprises in the U.S. […] |
Mobile | APT 41 APT 41 | ★★★ | |
| 2023-07-13 08:27:12 | Vigilance.fr - IBM QRadar SIEM : obtention d\'information via Delegated Admin Tenant User, analysé le 28/06/2023 (lien direct) | Un attaquant peut contourner les restrictions d'accès aux données de IBM QRadar SIEM, via Delegated Admin Tenant User, afin d'obtenir des informations sensibles. - Vulnérabilités | Vulnerability Mobile | ★★★ | ||
| 2023-07-10 07:50:05 | Android dans Windows : les dernières avancées chez Microsoft (lien direct) | Coup d'œil sur quelques-uns des derniers ajouts dans le sous-système Windows pour Android, ainsi que sur la roadmap. | Mobile | ★★ | ||
| 2023-03-23 17:25:00 | Nexus: un nouveau cheval de Troie bancaire androïde croissant ciblant 450 applications financières [Nexus: A New Rising Android Banking Trojan Targeting 450 Financial Apps] (lien direct) | Un troyen bancaire Android émergent surnommé Nexus a déjà été adopté par plusieurs acteurs de menace pour cibler 450 demandes financières et procéder à une fraude.
"Nexus semble être à ses débuts de développement", a déclaré Cleafy, la société italienne de cybersécurité, dans un rapport publié cette semaine.
"Nexus fournit toutes les principales fonctionnalités pour effectuer des attaques ATO (rachat de compte) contre les portails bancaires et
An emerging Android banking trojan dubbed Nexus has already been adopted by several threat actors to target 450 financial applications and conduct fraud. "Nexus appears to be in its early stages of development," Italian cybersecurity firm Cleafy said in a report published this week. "Nexus provides all the main features to perform ATO attacks (Account Takeover) against banking portals and |
Threat Mobile | ★★★ | ||
| 2023-03-23 12:02:12 | \\ 'Nexus \\' Android Trojan cible 450 applications financières [\\'Nexus\\' Android Trojan Targets 450 Financial Applications] (lien direct) | Promu comme un maas, le Trojan Android Nexus cible 450 applications financières pour la prise de contrôle du compte.
Promoted as a MaaS, the Nexus Android trojan targets 450 financial applications for account takeover. |
Mobile | ★★ | ||
| 2023-03-15 14:17:16 | Russia Calling? Scammers Target High-level Western Officials (lien direct) | Pas de details / No more details | Mobile | ★★★ | ||
| 2022-12-13 06:13:36 | Cette application d\'espionnage siphonne les données de milliers de smartphones (lien direct) |  Des dizaines de milliers d'utilisateurs d'iPhone et de smartphones Android ont peut-être vu leurs données personnelles volées sans même le savoir. En cause, une application d'espionnage compromise par des failles de sécurité. Des dizaines de milliers d'utilisateurs d'iPhone et de smartphones Android ont peut-être vu leurs données personnelles volées sans même le savoir. En cause, une application d'espionnage compromise par des failles de sécurité. |
Mobile | ★★ | ||
| 2022-12-07 09:30:23 | Over 75 Vulnerabilities Patched in Android With December 2022 Security Updates (lien direct) | Google this week announced the December 2022 Android updates with patches for over 75 vulnerabilities, including multiple critical remote code execution (RCE) flaws. The most severe of the RCE bugs is CVE-2022-20411, an issue in Android's System component that could be exploited over Bluetooth. | Mobile | ★★★★ | ||
| 2022-12-05 14:04:27 | Nouvelle vulnérabilité sur Android Venafi pointe l\'absence de contrôles de sécurité appropriés sur les certificats de signature de code (lien direct) | Les équipes Venafi se sont intéressées à une importante fuite de sécurité qui a mené à la création d'applications malveillantes " de confiance " pouvant accéder à l'ensemble du système d'exploitation Android sur les appareils de Samsung, LG, et d'autres. Plusieurs OEM Android ont eu leurs clés de signature de plate-forme fuité en dehors de leurs entreprises respectives. Cette clé est utilisée pour s'assurer que la version d'Android qui s'exécute sur un appareil est légitime et créée par le fabricant. Cette même clé peut également être utilisée pour signer des applications individuelles. - Vulnérabilités | Mobile | ★★★ | ||
| 2022-12-04 10:11:22 | Android malware apps with 2 million installs spotted on Google Play (lien direct) | A new set of Android malware, phishing, and adware apps have infiltrated the Google Play store, tricking over two million people into installing them. [...] | Malware Mobile | ★★★ | ||
| 2022-11-25 11:15:09 | Google lance l\'alerte : des millions de smartphones Android exposés à des failles de sécurité (lien direct) |  L'équipe d'experts en sécurité informatique de Google, connue sous le nom " Project Zero ", a publié un billet de blog alertant sur la vulnérabilité des GPU Mali que l'on retrouve dans des millions de smartphones Android. L'équipe d'experts en sécurité informatique de Google, connue sous le nom " Project Zero ", a publié un billet de blog alertant sur la vulnérabilité des GPU Mali que l'on retrouve dans des millions de smartphones Android. |
Mobile | ★★★ | ||
| 2022-11-24 16:00:00 | Bahamut Spyware Group Compromises Android Devices Via Fake VPN Apps (lien direct) | The app used as part of the campaign was a trojanized version of SoftVPN or OpenVPN | Mobile | Bahamut Bahamut | ★★ | |
| 2022-03-16 00:00:00 | Cybersécurité - la valeur et le besoin de formation pratique Cyber Security -The Value and Need for Practical Training (lien direct) |
Whenever we are trying to master a new skill, we have all heard about the importance of practise. The associated attention, rehearsal and repetition leads to the acquisition of new knowledge or skills that can later be developed into more complex skillsets. This sentiment has been seen throughout history, where some of the world\'s most masterful people have shared a similar philosophy that is still true today: Bruce Lee - “Practice makes perfect. After a long time of practising, our work will become natural, skillfull, swift and steady” Abraham Lincoln - “Give me six hours to chop down a tree and I will spend the first four sharpening the axe.” Japanese Proverb – “Tomorrow\'s battle is won during todays practice” Vincent Van Gough – “As practise makes perfect, I cannot but make progress, each drawing one makes, each study one paints is a step forward” Marshawn Lynch - “When you get to practice against the best, it brings the best out of you.” Martha Graham – “Practice means to perform, over and over again in the face of all obstacles, some act of vision, of faith, of desire. Practice is a means of inviting the perfection desired” Unknown - “Don\'t practise until you get it right, practice until you can\'t get it wrong” Others might disagree slightly: Vince Lombardi – “Practise does not make perfect. Only perfect practise makes perfect” So, the message is clear, to master a skill, we need to practise but we need to practise against the best and in the best most realistic possible environment. In terms of cybersecurity, as the cyber threat environment grows more intense, cyber defence groups require more and more skilled professionals to help with the onslaught of cyberattacks. However, they are finding it increasingly difficult to recruit and hire trained security professionals as having a degree in cybersecurity is usually not enough to give an individual the skills required for mitigating sophisticated attacks. For Cyber Security professionals, the required practise involves realistic breach scenarios or cyberattacks. These breaches or cyberattacks are any attempt to gain unauthorized access to a computer, computing system or computer network with the intent to cause damage. The aim to disable, disrupt, destroy or control computer systems or to alter, block, delete, manipulate or steal the data held within these systems. Day-to-day work in cybersecurity offers few opportunities for such training on the job, resulting in the required practise being an extremely difficult thing to achieve. When you think about it, cyberattacks are seemingly in the news every day, which seems to contradict my previous statement. However, the results of a cyberattack can range from causing inconvenience to dire consequences. A cyberattack on critical infrastructure and/or healthcare sectors don\'t just affect data or computer systems, they can wreak havoc in the physical world. This was seen all too well in Ireland in the not so distant past. So, cyberattacks are prevalent but the consequences mean we aim to prevent as many breaches as possible and reduce the impact, contain and eradicate any attack that exploits a system. There lies the problem, cyber security professionals require realistic breach scenarios and cyberattacks to train and become sufficiently skilled but cyber professionals are consistently working hard to prevent such attacks in the real-world. So the question is, “how do we train cyber security professionals to deal with the challenging ever-changing cyber environment?”. The answer is a Cyber Range! A Cyber Range provides a secure, sandboxed virtual interactive training environment that can simulate real-world feel scenarios and environments, including complex IT environments and attacks on IT infrastructure, networks, software platforms and applications. As a result, a cyber range infrastructure provides the required training and practise elements of realistic breach scenarios and cyberattacks. A Cyber Range enables students to practice newly acquire | Tool Threat Studies Mobile Industrial Medical Cloud | ★★ | ||
| 2021-07-29 00:00:00 | Pourquoi les fraudeurs nous blitz-ils avec des appels téléphoniques sur l'escroquerie? Why are fraudsters blitzing us with scam phone calls? (lien direct) |
Chair of Cybersecurity at MTU, Dr. Donna O\'Shea, contributed to this article in the Irish Times This week I have received a half dozen mobile calls from a number purporting to be very similar to my own. The caller ID shows an 087 number – like my own – and the subsequent four digits were also identical to mine, while the last three varied each time. In the jargon, this is known as “neighbour spoofing”, when a false caller ID is sent, seeming to come from the same area you live in, or a familiar looking number, to make it more likely that you will answer. When I did answer a not very convincing automated recording from “the department of social protection department” said fraud had been associated with my Personal Public Service Number (PPSN). Many of you will have received similar calls, trying to get you to “press a key” and talk to someone who tries to get you to divulge your PPSN, name, and in some cases, bank details. A recent scam text pretending to be from an Irish bank tells users that access to their account has been restricted due to a hacking attempt and invites them to input details to unlock it. These are all part of the seemingly endless cycle of scams which seem to have exploded over the past couple of years – and got increasingly sophisticated. But why is this happening? Let\'s look, as we would with any business, at the economics of the phone frauds. 1. Falling barriers to entry One of the first things with any business is to look at the barriers to getting involved. Whether for a criminal or legal enterprise, the cost of establishment is vital and can have a key bearing on activity levels and competition. Up to recent years, undertaking phone scams that involved hiding numbers and making thousands of calls required a significant level of technical knowledge. Now, according to Dr Donna O\'Shea, head of the computer science department of Cork Institute of Technology (CIT), the requisite “exploit” kits are downloadable, can leverage VOIP (voice over internet protocol) technology to call from PCs and display fake numbers on the user\'s phone. “You don\'t have to be a technical person to do it any more,” she said. It is still hard to account for the massive volumes of calls now happening, according to O\'Shea, but there appears to be a sharp rise in call numbers as well as increased sophistication. Relatively easily spotted calls from far-away countries are now replaced by more sophisticated “spoofing” – using numbers displaying themselves as “ordinary” Irish numbers. Showing a number close to your one is just one variant of this. It has also led to people “returning” calls to these numbers, which in some cases are valid numbers with real – and puzzled – owners. “You rang me”. . . “No I didn\'t . . .” At the moment incoming calls cannot be easily verified as coming from valid numbers. As the industry deregulated, numbers became portable – an 087 number can operate as part of the 086 network and so on – making checking incoming numbers to see if they are valid difficult – though here and internationally this issue is being examined. Some US operators have introduced controls, but it is a constant battle to stay ahead of the scammers. Not only it is relatively easy, but generating tens of thousands of phone calls is cheap, with operators taking on a tiny – or zero – cost per call. And so the “success” rate required to make money is tiny. Business Insider calculated in the US that some 2.5 million calls could be bought from a provider for just $875 by illegal telemarketers or scammers. Even if one in every 10,000 yielded revenue averaging $7 on average, the initial investment would be doubled. And of course, phone calls are just one variant of the scammers\' art, which also includes text messages and emails, all in many ways increasingly sophisticated, particularly texts allegedly from financial institutions which click through to plausible fake sites inviting you to enter your details. 2. | Tool Mobile Technical | ★★★ | ||
| 2021-01-19 07:04:55 | Researchers Discover Raindrop - 4th Malware Linked to the SolarWinds Attack (lien direct) | Cybersecurity researchers have unearthed a fourth new malware strain-designed to spread the malware onto other computers in victims' networks-which was deployed as part of the SolarWinds supply chain attack disclosed late last year.
Dubbed "Raindrop" by Broadcom-owned Symantec, the malware joins the likes of other malicious implants such as Sunspot, Sunburst (or Solorigate), and Teardrop that |
Malware Mobile | Solardwinds Solardwinds | ||
| 2021-01-12 12:32:07 | Potential Link between SolarWinds and Turla APT (lien direct) | Researchers at Kaspersky have recently discovered considerable similarities between the Sunburst and Kazuar backdoors. The similarities potentially link the Sunburst backdoors, used in the SolarWinds supply-chain attack, to a previously known Turla weapon. Kazuar, a malware written using the .NET framework, was first reported in 2017. These have been used in unison throughout various breaches […] | Malware Mobile | Solardwinds Solardwinds | ||
| 2021-01-12 11:25:00 | Third Malware Strain Discovered as Part of SolarWinds Attack (lien direct) | Sunspot used to inject Sunburst into Orion platform, says CrowdStrike | Malware Mobile | Solardwinds Solardwinds |
To see everything:
Our RSS (filtrered)
