What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2020-03-04 14:14:25 | Microsoft Releases PowerShell 7.0 With New Features, Update Alerts (lien direct) | Microsoft released PowerShell 7.0, the latest version of its cross-platform automation and configuration tool with new features including automatic new version notifications, bug fixes, and improvements. [...] | Tool | |||
| 2020-03-04 10:31:22 | CleanMaster: An Android Security App With 1 Billion Downloads Is Recording Users\' Web Browsing – Expert Insight (lien direct) | Forbes published an article earlier today regarding an app called CleanMaster, a security tool promising anti-virus and private browsing. It had more than 1 billion installs before it was evicted and, despite Google's ban, is one of Android's most downloaded apps ever devices and is likely still running on millions of phones. Whilst Google hasn't commented … The ISBuzz Post: This Post CleanMaster: An Android Security App With 1 Billion Downloads Is Recording Users' Web Browsing – Expert Insight | Tool | |||
| 2020-03-04 10:07:14 | Android app records web browsing (lien direct) | In February, Google threw 600 apps out of its Play store. Amongst those was an app called Clean Master, a security tool promising antivirus protection and private browsing. It had more than 1 billion installs before it was evicted and, despite Google's ban, is one of Android's most downloaded apps ever and is likely […] | Tool | |||
| 2020-03-03 11:08:12 | Experts On Credit Score Builder Loqbox Hit By Data Breach (lien direct) | According to MoneySavingExpert, customers of credit history-building tool Loqbox have had personal and financial data compromised after the firm was hit by a “sophisticated and complex” cyber attack. Loqbox has announced that it’s been hit by a cyber attack, in which hackers accessed both customers’ personal data – such as addresses and phone numbers – and, … The ISBuzz Post: This Post Experts On Credit Score Builder Loqbox Hit By Data Breach | Data Breach Tool | |||
| 2020-03-03 10:27:57 | Loqbox data breach (lien direct) | Some customers of credit history-building tool Loqbox have had personal and financial data compromised after the firm was hit by a “sophisticated and complex” cyber attack. Loqbox is a tool which helps those with patchy credit histories build a credit score by buying a ‘digital voucher’ – essential a loan – and then ‘repaying’ […] | Data Breach Tool | |||
| 2020-03-03 09:42:59 | Microsoft Immersive Reader: Use this handy tool to make your own apps better (lien direct) | Having text read aloud, highlighted automatically or translated into different languages can make dense text much easier to work with. Now you can add this functionality to line-of-business apps. | Tool | |||
| 2020-02-28 21:15:33 | How to install and use the open source OTPClient 2FA tool on Linux (lien direct) | If your desktop of choice is Linux, you don't have to be without a 2FA tool, thanks to OTPClient. | Tool | |||
| 2020-02-28 19:33:56 | How to manage VMs from the Multipass system tray tool (lien direct) | Multipass includes a system tray GUI that makes managing your virtual machines simple and efficient. | Tool | |||
| 2020-02-28 11:18:33 | (Déjà vu) Phishing Experts On Norton LifeLock Phishing Scam Installs Remote Access Trojan (lien direct) | In response to reports that indicate cybercriminals behind a recently observed phishing campaign used a clever ruse in the form of a bogus NortonLifelock document to fool victims into installing a remote access tool (RAT) that is typically used for legitimate purposes, experts provide an inisght below. The ISBuzz Post: This Post Phishing Experts On Norton LifeLock Phishing Scam Installs Remote Access Trojan | Tool | |||
| 2020-02-28 10:23:14 | (Déjà vu) Remote Access Trojan used by Norton Lifelock Scam (lien direct) | Cybercriminals behind a recently observed phishing campaign used a clever ruse in the form of a bogus NortonLifelock document to fool victims into installing a remote access tool (RAT) that is typically used for legitimate purposes. The malicious activity has the hallmarks of a seasoned threat actor familiar with evasion techniques and offensive security […] | Tool Threat | |||
| 2020-02-27 09:01:00 | Norton LifeLock Phishing Scam Installs Remote Access Trojan (lien direct) | Cybercriminals behind a recently observed phishing campaign used a clever ruse in the form of a bogus NortonLifelock document to fool victims into installing a remote access tool (RAT) that is typically used for legitimate purposes. [...] | Tool | |||
| 2020-02-26 16:36:00 | Astra – API Automated Security Testing For REST (lien direct) |  Astra is a Python-based tool for API Automated Security Testing, REST API penetration testing is complex due to continuous changes in existing APIs and newly added APIs.
Astra can be used by security engineers or developers as an integral part of their process, so they can detect and patch vulnerabilities early during development cycle. Astra can automatically detect and test login & logout (Authentication API), so it's easy for anyone to integrate this into CI/CD pipeline.
Read the rest of Astra – API Automated Security Testing For REST now! Only available at Darknet. Astra is a Python-based tool for API Automated Security Testing, REST API penetration testing is complex due to continuous changes in existing APIs and newly added APIs.
Astra can be used by security engineers or developers as an integral part of their process, so they can detect and patch vulnerabilities early during development cycle. Astra can automatically detect and test login & logout (Authentication API), so it's easy for anyone to integrate this into CI/CD pipeline.
Read the rest of Astra – API Automated Security Testing For REST now! Only available at Darknet.
|
Tool | |||
| 2020-02-25 12:00:00 | North Korea Is Recycling Mac Malware. That\'s Not the Worst Part (lien direct) | Lazarus Group hackers have long plagued the internet-using at least one tool they picked up just by looking around online. | Tool Medical | APT 38 | ||
| 2020-02-24 11:16:26 | (Déjà vu) Lighthouse Pagespeed brought to Firefox (lien direct) | Google has brought its popular Lighthouse extension used by over 400,000 users to Mozilla Firefox so that web developers can test the browser’s performance against submitted web pages. Lighthouse is an open-source tool for testing the performance of web pages through Google’s PageSpeed Insights API and was released as an extension for Google Chrome […] | Tool | |||
| 2020-02-22 15:11:12 | NBlog Feb 22 - the educator virus (lien direct) |  From time to time, people get all excited about micro-learning, the educational equivalent of eating a chocolate elephant - one bite or byte at a time."It's easy", the line goes. "Simply break down large indigestible topics into lots of smaller edible chunks, spreading them out enticingly for people to snack on whenever they feel peckish."I've tried that with our digital awareness content. For some strange reason, nobody was hungry enough to consume the random assortment of ones and zeroes, hundreds and thousands of bits all over the disk.Evidently it's not quite that easy. Education is never easy, if you want it to work well that is. Micro-, milli- and macro-learning, online learning, traditional classroom-based courses, webinars and seminars, conferences, educational events, rote and experiential learning, on-the-job training and demonstration classes, mentoring and so on are neither simple nor universal solutions. They each have their pros and cons. For one thing, they all just tools in the box. For an educator who happens to be a master craftsman, almost any tool will do, but he has preferences and a range of experience. Likewise for the students: some of us like reading and thinking things through in private, or debating the ins-and-outs at length with colleagues. Others need to be shown stuff, just briefly, or put through an intensive boot camp complete with sadistic 'instructors', hard beds and nasty food. Some appear stubbornly resistant to all known edumacational techniques and do their level best to skip class, and we all have our cognitive issues occasionally.The fact that there is such a variety of techniques suggests that none of them is ideal for all learning situations. The advice to use, say, micro-learning could be taken to mean "use ONLY micro-learning" but that would be a mistake, in just the same way as "send them to college" or "gamify it"! It's well-meaning but naive silver bullet advice.Consider how we learn stuff in general. We take classes, go to night school, take driving or diving or cookery lessons, read-up on stuff, watch You Tube vids, read/listen to/watch/contemplate sage advisors, ask someone ... and generally muddle through by ourselves, learning as we go from our successes and failures. From time to time, people get all excited about micro-learning, the educational equivalent of eating a chocolate elephant - one bite or byte at a time."It's easy", the line goes. "Simply break down large indigestible topics into lots of smaller edible chunks, spreading them out enticingly for people to snack on whenever they feel peckish."I've tried that with our digital awareness content. For some strange reason, nobody was hungry enough to consume the random assortment of ones and zeroes, hundreds and thousands of bits all over the disk.Evidently it's not quite that easy. Education is never easy, if you want it to work well that is. Micro-, milli- and macro-learning, online learning, traditional classroom-based courses, webinars and seminars, conferences, educational events, rote and experiential learning, on-the-job training and demonstration classes, mentoring and so on are neither simple nor universal solutions. They each have their pros and cons. For one thing, they all just tools in the box. For an educator who happens to be a master craftsman, almost any tool will do, but he has preferences and a range of experience. Likewise for the students: some of us like reading and thinking things through in private, or debating the ins-and-outs at length with colleagues. Others need to be shown stuff, just briefly, or put through an intensive boot camp complete with sadistic 'instructors', hard beds and nasty food. Some appear stubbornly resistant to all known edumacational techniques and do their level best to skip class, and we all have our cognitive issues occasionally.The fact that there is such a variety of techniques suggests that none of them is ideal for all learning situations. The advice to use, say, micro-learning could be taken to mean "use ONLY micro-learning" but that would be a mistake, in just the same way as "send them to college" or "gamify it"! It's well-meaning but naive silver bullet advice.Consider how we learn stuff in general. We take classes, go to night school, take driving or diving or cookery lessons, read-up on stuff, watch You Tube vids, read/listen to/watch/contemplate sage advisors, ask someone ... and generally muddle through by ourselves, learning as we go from our successes and failures. |
Tool | |||
| 2020-02-21 15:24:51 | Compliance: Veritas tool adds intelligence and analysis to data supervision (lien direct) | A new release leverages machine learning to help companies reduce the search time they need to remain compliant in regulated industries. | Tool | |||
| 2020-02-20 16:30:21 | Security platform tracks rogue wireless devices via real-time map (lien direct) | New security tool from Bastille Networks can help security teams enforce no cell-phone zones. | Tool | |||
| 2020-02-20 13:39:13 | Cisco fixes a static default credential issue in Smart Software Manager tool (lien direct) | Cisco has released security updates to address 17 vulnerabilities affecting its networking and unified communications product lines. Cisco has released security patches to fix 17 vulnerabilities affecting its networking and unified communications product lines. The types of fixed vulnerabilities include remote access and code execution, elevation of privilege, denial of service, and cross-site request forgeries. One of […] | Tool | |||
| 2020-02-19 16:11:19 | Beginners Guide to TShark (Part 2) (lien direct) | In the previous article, we learned about the basic functionalities of this wonderful tool called TShark. If you haven't read it until now. Click here. TL; DR In this part, we will the Statistical Functionalities of TShark. We will understand different ways in which we can sort our traffic capture so that we can analyse... Continue reading → | Tool | |||
| 2020-02-19 15:22:49 | Judas DNS – Nameserver DNS Poisoning Attack Tool (lien direct) |  Judas DNS is a Nameserver DNS Poisoning Attack Tool which functions as a DNS proxy server built to be deployed in place of a taken over nameserver to perform targeted exploitation. Judas works by proxying all DNS queries to the legitimate nameservers for a domain.
The magic comes with Judas's rule configurations which allow you to change DNS responses depending on source IP or DNS query type. This allows an attacker to configure a malicious nameserver to do things like selectively re-route inbound email coming from specified source IP ranges (via modified MX records), set extremely long TTLs to keep poisoned records cached, and more.
Read the rest of Judas DNS – Nameserver DNS Poisoning Attack Tool now! Only available at Darknet. Judas DNS is a Nameserver DNS Poisoning Attack Tool which functions as a DNS proxy server built to be deployed in place of a taken over nameserver to perform targeted exploitation. Judas works by proxying all DNS queries to the legitimate nameservers for a domain.
The magic comes with Judas's rule configurations which allow you to change DNS responses depending on source IP or DNS query type. This allows an attacker to configure a malicious nameserver to do things like selectively re-route inbound email coming from specified source IP ranges (via modified MX records), set extremely long TTLs to keep poisoned records cached, and more.
Read the rest of Judas DNS – Nameserver DNS Poisoning Attack Tool now! Only available at Darknet.
|
Tool | |||
| 2020-02-19 14:01:47 | 5 Ways artificial intelligence Is Being Used to Keep Sensitive Information Secure (lien direct) | Artificial intelligence is an immensely helpful tool for businesses and consumers alike, how to use artificial intelligence to secure sensitive Information Artificial intelligence (AI) is an immensely helpful tool for businesses and consumers alike. By processing data quickly and predicting analytics, AI can do everything from automating systems to protecting information. In fact, keeping data […] | Tool | |||
| 2020-02-18 17:45:53 | 12th March – LogPoint: Providing a fair and predictable licensing model for SIEM for the NHS (lien direct) | Security Incident and Event Management (SIEM) is a tool that provides monitoring, detection, and alerting of security events or incidents within an IT environment. It provides a comprehensive and centralized view of the security posture of an IT infrastructure and gives enterprise security professionals insight into the activities within their environment. With legislation such as [...] | Tool | |||
| 2020-02-18 13:00:02 | How to use the Windows 10 Sandbox for safer web surfing (lien direct) | The virtual machine in Windows 10 Sandbox is deployed with Microsoft Edge, which makes this special feature an effective tool for more secure web surfing. | Tool | |||
| 2020-02-17 20:17:51 | How to fix the display bug in Microsoft Windows 10 Sandbox (lien direct) | Windows 10 Sandbox can be a great tool for testing suspicious applications. However, Sandbox has a bug Microsoft has yet to meaningfully address. We have a workaround. | Tool | |||
| 2020-02-14 20:29:48 | How to use the Firefox Performance tool to test site responsiveness (lien direct) | Web developers looking for site performance issues should be using this tool in the Firefox web developers toolkit. | Tool | |||
| 2020-02-13 13:06:03 | Steal Windows Password using FakeLogonScreen (lien direct) | In this article, we are going to focus on a tool that caught my attention. This is a tool that creates a fake Windows Logon Screen and then forces the user to enter the correct credentials and then relay the credentials to the attacker. It can work in different scenarios. This tool was developed by... Continue reading → | Tool | |||
| 2020-02-12 12:00:00 | Can a Database of Animal Viruses Help Predict the Next Pandemic? (lien direct) | A scientist spent years building a tool to identify coronaviruses that can jump species. Then this winter's virus emerged-and put his system to the test. | Tool | |||
| 2020-02-10 17:27:43 | Multiple Ways to Crack WordPress login (lien direct) | In this article, you will be learning how to compromise a WordPress website's credentials using different brute forcing techniques. Table of Content Pre-requisites WPscan Metasploit Burp Suite How to avoid a Brute Force Attack? Pre-requisites: Target: WordPress Attacker: Kali Linux (WPscan) Burp Suite (Intruder) WPscan WPscan is a command-line tool which is used as a black... Continue reading → | Tool | |||
| 2020-02-10 14:05:43 | OWASP Amass – DNS Enumeration, Attack Surface Mapping & External Asset Discovery (lien direct) |  The OWASP Amass Project is a DNS Enumeration, Attack Surface Mapping & External Asset Discovery tool to help information security professionals perform network mapping of attack surfaces and perform external asset discovery using open source information gathering and active reconnaissance techniques.
Information Gathering Techniques Used by OWASP Amass for DNS Enumeration and More
The main functionality of Amass is as follows:
DNS: Basic enumeration, Brute forcing (optional), Reverse DNS sweeping, Subdomain name alterations/permutations, Zone transfers (optional)
Scraping: Ask, Baidu, Bing, DNSDumpster, DNSTable, Dogpile, Exalead, Google, HackerOne, IPv4Info, Netcraft, PTRArchive, Riddler, SiteDossier, ViewDNS, Yahoo
Certificates: Active pulls (optional), Censys, CertSpotter, Crtsh, Entrust, GoogleCT
APIs: AlienVault, BinaryEdge, BufferOver, CIRCL, CommonCrawl, DNSDB, GitHub, HackerTarget, IPToASN, Mnemonic, NetworksDB, PassiveTotal, Pastebin, RADb, Robtex, SecurityTrails, ShadowServer, Shodan, Spyse (CertDB & FindSubdomains), Sublist3rAPI, TeamCymru, ThreatCrowd, Twitter, Umbrella, URLScan, VirusTotal, WhoisXML
Web Archives: ArchiveIt, ArchiveToday, Arquivo, LoCArchive, OpenUKArchive, UKGovArchive, Wayback
Usage of Amass for DNS Enumeration, Attack Surface Mapping & External Asset Discovery
The Amass tool has several subcommands shown below for handling your Internet exposure investigation.
Read the rest of OWASP Amass – DNS Enumeration, Attack Surface Mapping & External Asset Discovery now! Only available at Darknet. The OWASP Amass Project is a DNS Enumeration, Attack Surface Mapping & External Asset Discovery tool to help information security professionals perform network mapping of attack surfaces and perform external asset discovery using open source information gathering and active reconnaissance techniques.
Information Gathering Techniques Used by OWASP Amass for DNS Enumeration and More
The main functionality of Amass is as follows:
DNS: Basic enumeration, Brute forcing (optional), Reverse DNS sweeping, Subdomain name alterations/permutations, Zone transfers (optional)
Scraping: Ask, Baidu, Bing, DNSDumpster, DNSTable, Dogpile, Exalead, Google, HackerOne, IPv4Info, Netcraft, PTRArchive, Riddler, SiteDossier, ViewDNS, Yahoo
Certificates: Active pulls (optional), Censys, CertSpotter, Crtsh, Entrust, GoogleCT
APIs: AlienVault, BinaryEdge, BufferOver, CIRCL, CommonCrawl, DNSDB, GitHub, HackerTarget, IPToASN, Mnemonic, NetworksDB, PassiveTotal, Pastebin, RADb, Robtex, SecurityTrails, ShadowServer, Shodan, Spyse (CertDB & FindSubdomains), Sublist3rAPI, TeamCymru, ThreatCrowd, Twitter, Umbrella, URLScan, VirusTotal, WhoisXML
Web Archives: ArchiveIt, ArchiveToday, Arquivo, LoCArchive, OpenUKArchive, UKGovArchive, Wayback
Usage of Amass for DNS Enumeration, Attack Surface Mapping & External Asset Discovery
The Amass tool has several subcommands shown below for handling your Internet exposure investigation.
Read the rest of OWASP Amass – DNS Enumeration, Attack Surface Mapping & External Asset Discovery now! Only available at Darknet.
|
Tool Guideline | Yahoo | ||
| 2020-02-07 16:43:59 | Multipass is a new tool for launching virtual machines (lien direct) | Looking for an easy-to-use VM manage for dev and testing purposes? Look no further than Canonical's Multipass. | Tool | |||
| 2020-02-05 14:00:00 | 10 things to know about cybersecurity in 2020 (lien direct) | Cybersecurity talent is elusive, resources are dwindling, but hacks are on the rise. We’re addressing these challenges as “must-haves” as we kick off the year is essential to an organization’s cybersecurity strategy. Here are some of the 10 things to know about cybersecurity in 2020. (If you’re interested in hearing more, register for a Cygilant and AT&T Cybersecurity webinar on the topic February 6). 1. Security-as-a-service fills the talent and recruitment gap. We are already falling into a talent abyss where there isn’t enough cybersecurity or compliance expertise and it’s not changing anytime soon. Getting help from security-as-a-service organizations will become the de-facto standard as the only way to fill the talent and recruitment gap. 2. Navigating vendor noise becomes harder. With so many cybersecurity vendors in the market, it’s tough to make decisions on what will truly help protect a business. This year there needs to be a focused priority in identifying services that provide resources and a full suite of solutions to help turn down the volume, ward off attacks and meet compliance mandates. 3. AI identifies security gaps faster. As we fight to keep up with new hacks, security professionals need to embrace machine learning (ML) and AI technology that works at a much faster cadence to find gaps that could lead to a breach. Using these technologies can help security professionals keep up with hackers. Combined with human expertise, AI and ML can help prevent attacks. 4. Widespread adoption of security visualization in the cloud. We want to see how our apps and data are connecting and where, and if, there are any security gaps. A “must-have” for all security professionals is the ability to see their entire security posture presented in a single, holistic visual dashboard. We will see the widespread adoption of security visualization across all environments. 5. The perimeter is dead; endpoints need protecting. More laptops, desktops, mobile phones, tablets, servers, and virtual environments are connecting to systems. Each one of these endpoints requires security. In 2020, endpoint security will become a “must-have” for all organizations. Perimeter detection is no longer adequate - as your perimeter doesn’t exist. It is anywhere and everywhere. One misconfigured laptop, server or firewall may be the cause of a data breach. 6. More regulations translates to more work. Every year we see an increase in updated guidance or compliance requirements. This trend will continue in 2020 as more regulation is put in place to protect privacy and data. With the floodgates opening, it’s important to have processes and logs in place that prove how security and privacy is handled at your business. 7. More ransomware attacks in 2020. As more people accept that spending on ransomware is the cost of doing business, we’ll see more attacks. Dedicated resources should be spent on prevention by monitoring for suspicious activity, including phishing attempts and ransomware. If you don’t have the internal resources, look to security-as-a-service with security monitoring solutions. 8. Small business aren’t immune. Cybersecurity isn’t just for the enterprises. One breach could be the death of a s | Ransomware Tool Guideline | |||
| 2020-02-04 18:49:09 | Network data manipulation on the fly (lien direct) | AbstractVarious type of security assessments ranging from regular penetration testing, through red teaming operations up to breaking IoT/ICS devices and SCADA involves playing with binary network protocols what requires intercepting and modification of network data between client and the target. Sniffing of the network traffic is not a big deal as we have tools like Wireshark, Tcpdump or Scapy, however modification is more challenging because we would need to have kind of an interface to read the network data, filter it, modify on the fly and send it back to the target host in almost real time. In addition, it would be perfect if such tool could auto handle multiple connections in parallel and be scriptable.One time I found a tool called maproxy | Tool | |||
| 2020-02-03 17:06:56 | New EmoCheck Tool Checks if You\'re Infected With Emotet (lien direct) | A new utility has been released by Japan CERT (computer emergency response team) that allows Windows users to easily check if they are infected with the Emotet Trojan. [...] | Tool | |||
| 2020-01-29 09:27:23 | Cameradar – Hack RTSP Video Surveillance CCTV Cameras (lien direct) |  Cameradar is a Go-based tool to hack RTSP Video Surveillance CCTV Cameras, it can detect open RTSP hosts, detect device models and launch automated attacks.
The main features of Cameradar are:
Detect open RTSP hosts on any accessible target host
Detect which device model is streaming
Launch automated dictionary attacks to get their stream route (e.g.: /live.sdp)
Launch automated dictionary attacks to get the username and password of the cameras
Retrieve a complete and user-friendly report of the results
Using Cameradar to Hack RTSP Video Cameras
"-t, --targets": Set target.
Read the rest of Cameradar – Hack RTSP Video Surveillance CCTV Cameras now! Only available at Darknet. Cameradar is a Go-based tool to hack RTSP Video Surveillance CCTV Cameras, it can detect open RTSP hosts, detect device models and launch automated attacks.
The main features of Cameradar are:
Detect open RTSP hosts on any accessible target host
Detect which device model is streaming
Launch automated dictionary attacks to get their stream route (e.g.: /live.sdp)
Launch automated dictionary attacks to get the username and password of the cameras
Retrieve a complete and user-friendly report of the results
Using Cameradar to Hack RTSP Video Cameras
"-t, --targets": Set target.
Read the rest of Cameradar – Hack RTSP Video Surveillance CCTV Cameras now! Only available at Darknet.
|
Hack Tool | |||
| 2020-01-28 14:24:42 | How to decrypt WhatsApp end-to-end media files (lien direct) | At the center of the "Saudis hacked Bezos" story is a mysterious video file investigators couldn't decrypt, sent by Saudi Crown Prince MBS to Bezos via WhatsApp. In this blog post, I show how to decrypt it. Once decrypted, we'll either have a smoking gun proving the Saudi's guilt, or exoneration showing that nothing in the report implicated the Saudis. I show how everyone can replicate this on their own iPhones.The steps are simple:backup the phone to your computer (macOS or Windows), using one of many freely available tools, such as Apple's own iTunes appextract the database containing WhatsApp messages from that backup, using one of many freely available tools, or just hunt for the specific file yourselfgrab the .enc file and decryption key from that database, using one of many freely available SQL toolsdecrypt the video, using a tool I just created on GitHubEnd-to-end encrypted downloaderThe FTI report says that within hours of receiving a suspicious video that Bezos's iPhone began behaving strangely. The report says:...analysis revealed that the suspect video had been delivered via an encrypted downloader host on WhatsApp's media server. Due to WhatsApp's end-to-end encryption, the contents of the downloader cannot be practically determined. The phrase "encrypted downloader" is not a technical term but something the investigators invented. It sounds like a term we use in malware/viruses, where a first stage downloads later stages using encryption. But that's not what happened here.Instead, the file in question is simply the video itself, encrypted, with a few extra bytes due to encryption overhead (10 bytes of checksum at the start, up to 15 bytes of padding at the end).Now let's talk about "end-to-end encryption". This only means that those in middle can't decrypt the file, not even WhatsApp's servers. But those on the ends can -- and that's what we have here, one of the ends. Bezos can upgrade his old iPhone X to a new iPhone XS by backing up the old phone and restoring onto the new phone and still decrypt the video. That means the decryption key is somewhere in the backup.Specifically, the decryption key is in the file named 7c7fba66680ef796b916b067077cc246adacf01d in the backup, in the table named ZWAMDIAITEM, as the first protobuf field in the field named ZMEDIAKEY. These details are explained below.WhatsApp end-to-end encryption of videoLet's discuss how videos are transmitted using text messages.We'll start with SMS, the old messaging system built into the phone system that predates modern apps. It can only send short text messages of a few hundred bytes at a time. These messages are too small to hold a complete video many megabytes in size. They are sent through the phone system itself, not via the Internet.When you send a video via SMS what happens is that the video is uploaded to the phone company's servers via HTTP. Then, a text message is sent with a URL link to the video. When the recipient gets the message, their phone downloads the video from the URL. The text messages going through the phone system just contain the URL, an Internet connection is used to transfer the video.This happens transparently to the user. The user just sees the video and not the URL. They'll only notice a difference when using ancient 2G mobile phones that can get the SMS messages but which can't actually connect to the Internet.A similar thing happens with WhatsApp, only with encryption added.The sender first encryp | Malware Hack Tool | |||
| 2020-01-28 14:10:00 | Android Flash Tool Lets You Install Android Using a Browser (lien direct) | Google announced the release of a web-based tool that can be used by developers to install Android Open Source Project (AOSP) builds on recent Pixel phones and some Android development devices from the web browser, without building and flashing manually. [...] | Tool | |||
| 2020-01-28 10:37:16 | Cyber Threat Trends Dashboard (lien direct) | Marco Ramilli published the Cyber Threat Trends Dashboard, a useful tool that will allow us to better understand most active threats in real time. Introduction Information sharing is one of the most important activity that cybersecurity researchers do on daily basis. Thanks to “infosharing” activities it is possible to block or, in specific cases, to […] | Tool Threat | |||
| 2020-01-27 13:00:00 | Tinder Swipes Right on AI to Help Stop Harassment (lien direct) | The dating app says its new machine learning tool can help flag potentially offensive messages and encourage more users to report inappropriate behavior. | Tool | |||
| 2020-01-24 13:20:30 | Google: Flaws in Apple\'s privacy tool could enable tracking (lien direct) | Safari's anti-tracking feature could apparently give access to users' browsing habits | Tool | |||
| 2020-01-23 20:47:00 | Glassdoor offers new mobile device tool for job seekers (lien direct) | Mobile job applications are on the rise, and this new feature makes it easier to do from smartphones. | Tool | |||
| 2020-01-23 11:40:45 | A free tool for detecting Shitrix-related compromises on your business network (lien direct) | Citrix has announced that it has teamed up with security researchers at FireEye to produce a free forensic tool which can help your business hunt for potential Indicators of Compromise related to the CVE-2019-19781 vulnerability. | Tool | |||
| 2020-01-22 12:01:57 | (Déjà vu) Panorays And Hysolate Comment On New NIST 1.0 Privacy Framework (lien direct) | The National Institute of Standards and Technology (NIST) just released its first version of its privacy framework, a tool to give organizations guidance on how to manage risks and be in compliance with new privacy laws. The ISBuzz Post: This Post Panorays And Hysolate Comment On New NIST 1.0 Privacy Framework | Tool | |||
| 2020-01-21 14:00:00 | FUD-free analysis: Natural language processing (NLP) (lien direct) | If you follow me on Medium or Twitter, you may already be aware. Still, if you don’t (I assure you that you’re missing out), I have been researching several technologies in preparation for an OPSEC/Anti-OSINT tool that I am crafting. I am using this tool as a means to push myself harder to learn something new that I can apply professionally. I am also doing this to be able to make a positive difference in the world. Notably, I am explicitly trying to learn Machine Learning and Natural Language Processing (NLP) in Python and R. When we hear terms like Advanced Persistent, Next-Generation, Machine Learning, Artificial Intelligence (AI), Machine Learning (ML), Single Pane of Glass, etc. from a vendor, we typically think it’s hype or FUD. Talking about the vendor FUD phrases is ironic because my blog and podcast were called Advanced Persistent Security. Often, we are correct. I set off on the journey to learn about learning to build a tool, but also to understand the technologies. I like to stump salespeople from time to time. Also, if these are the wave of the future, there is no time like the present to get acquainted. So, NLP. What is it? In social engineering circles, it is Neuro-Linguistic Programming. Some (many, if not most) in the scientific community consider it pseudoscience. Regardless, it claims to be able to influence or manipulate people through non-verbal cues from the eyes or touching someone (cringe) or other means. That is not the NLP that I am working on learning. Natural Language Processing, the more scientific NLP, is a marriage of various disciplines: computer science, data science (including AI and ML), and linguistics. NLP allows libraries and code to read the language as it is written or spoken by humans (naturally, hence the name). When applying slang, pidgins, and dialects, it will “learn” to recognize and respond to them. Also adjacent to NLP is OCR or Optical Character Recognition. OCR is the means to read data from a document in a non-text format (i.e., pictures, PDF, or Word documents). Having the ability to read the data allows you to open a PDF with a script (perhaps written in Python) and read it, make sense of it, and act as scripted. Why is this important to InfoSec, and what do we do with it? We could use this in log analysis, network monitoring, analyzing phishing emails, and my personal favorite, OSINT, to name a few. Within log analysis, NLP could be applied to gain further intelligence from logs without writing ridiculously long regular expressions (REGEX) via “learning” the context of the data and what is being sought. This would likely be in parallel with some Machine Learning, but it is a start. From the ML perspective, it would probably need to utilize supervised or semi-supervised learning with online entry vice unsupervised or reinforcement learning. The online means that it would read the data more closely to real-time than by ingesting a defined dataset. The supervision of learning refers to telling the “machine” whether it was correct or not. In some instances of learning logs, unsupervised learning could be useful in determining indicators of compromise or adversarial TTPs based on log data in two sets: breached (event data) and non-breached data. Reinforcement training would be more applicable for tuning and improvement. Back to NLP, the same concepts apply in network monitoring as log analysis, except it would be network traffic and PCAPs being analyzed. PCAP analysis with NLP and ML may be better suited for analyzing a user’s beha | Tool Threat | |||
| 2020-01-21 07:13:59 | NIST releases version 1.0 of the Privacy Framework (lien direct) | The NIST released version 1.0 of Privacy Framework, it is a tool designed to help organizations to manage privacy risks. The National Institute of Standards and Technology (NIST) has published the release version 1.0 of its privacy framework. The Framework is a voluntary tool that can be used by organizations to manage risks in compliance […] | Tool | |||
| 2020-01-20 04:22:32 | Evaluating Your Security Controls? Be Sure to Ask the Right Questions (lien direct) | Testing security controls is the only way to know if they are truly defending your organization. With many different testing frameworks and tools to choose from, you have lots of options.
But what do you specifically want to know? And how are the findings relevant to the threat landscape you face at this moment?
"Decide what you want to know and then choose the best tool for the job." |
Tool Threat | |||
| 2020-01-17 10:32:23 | CVE-2019-19470: Rumble in the Pipe (lien direct) | This blog post describes an interesting privilege escalation from a local user to SYSTEM for a well-known local firewall solution called TinyWall in versions prior to 2.1.13. Besides a .NET deserialization flaw through Named Pipe communication, an authentication bypass is explained as well. Introduction TinyWall is a local firewall written in .NET. It consists of a single executable that runs once as SYSTEM and once in the user context to configure it. The server listens on a Named Pipe for messages that are transmitted in the form of serialized object streams using the well-known and beloved BinaryFormatter. However, there is an additional authentication check that we found interesting to examine and that we want to elaborate here a little more closely as it may also be used by other products to protect themselves from unauthorized access. For the sake of simplicity the remaining article will use the terms Server for the receiving SYSTEM process and Client for the sending process within an authenticated user context, respectively. Keep in mind that the authenticated user does not need any special privileges (e.g. SeDebugPrivilege) to exploit this vulnerability described.Named Pipe Communication Many (security) products use Named Pipes for inter-process communication (e.g. see Anti Virus products). One of the advantages of Named Pipes is that a Server process has access to additional information on the sender like the origin Process ID, Security Context etc. through Windows' Authentication model. Access to Named Pipes from a programmatic perspective is provided through Windows API calls but can also be achieved e.g. via direct filesystem access. The Named Pipe filessystem (NPFS) is accessible via the Named Pipe's name with a prefix \\.\pipe\.The screenshot below confirms that a Named Pipe "TinyWallController" exists and could be accessed and written into by any authenticated user. Talking to SYSTEMFirst of all, let's look how the Named Pipe is created and used. When TinyWall starts, a PipeServerWorker method takes care of a proper Named Pipe setup. For this the Windows API provides System.IO.Pipes.NamedPipeServerStream with one of it's constructors taking a parameter of System.IO.Pipes.PipeSecurity. This allows for fine-grained access control via System.IO.PipeAccessRule objects using SecurityIdentifiers and alike. Well, as one can observe from the first screenshot above, the only restriction seems to be that the Client process has to be executed in an authenticated user context which doesn't seem to be a hard restriction after all. Talking to SYSTEMFirst of all, let's look how the Named Pipe is created and used. When TinyWall starts, a PipeServerWorker method takes care of a proper Named Pipe setup. For this the Windows API provides System.IO.Pipes.NamedPipeServerStream with one of it's constructors taking a parameter of System.IO.Pipes.PipeSecurity. This allows for fine-grained access control via System.IO.PipeAccessRule objects using SecurityIdentifiers and alike. Well, as one can observe from the first screenshot above, the only restriction seems to be that the Client process has to be executed in an authenticated user context which doesn't seem to be a hard restriction after all.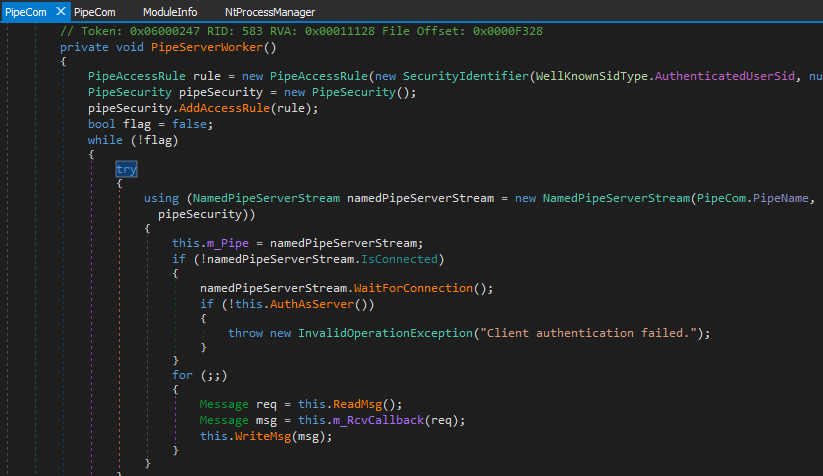 But as it turned out But as it turned out |
Tool Vulnerability | |||
| 2020-01-16 13:00:56 | Use the Correct Tool for the Job: Mobile Management Solutions are Not Security! (lien direct) | By Yael Macias, Product Marketing Manager, Threat Prevention In the past decade, the world went mobile. And businesses had to catch up and adapt to this trend, by allowing their employees to access corporate assets and seamlessly work from their mobile devices. For several years now, organizations have used mobile management solutions (UEM, EMM, MDM,… | Tool Threat | |||
| 2020-01-16 10:07:24 | Broadening the Scope: A Comprehensive View of Pen Testing (lien direct) | Penetration tests have long been known as a critical security tool that exposes security weaknesses through simulated attacks on an organization's IT environments. These test results can help prioritize weaknesses, providing a road-map towards remediation.
However, the results are also capable of doing even more. They identify and quantify security risk, and can be used as a keystone in |
Tool | |||
| 2020-01-16 00:01:45 | Smashing Security #161: Love, lucky dips, and 23andMe (lien direct) | The man who hacked the UK National Lottery didn’t end up a winner, Japanese Love hotel booking tool suffers a data breach, and just what is 23andMe planning to do with your DNA? All this and much more is discussed in the latest edition of the award-winning “Smashing Security” podcast by computer security veterans Graham Cluley and Carole Theriault, joined this week by Thom Langford. | Tool | ★★★★★ | ||
| 2020-01-15 14:00:00 | Alien Labs 2019 Analysis of Threat Groups Molerats and APT-C-37 (lien direct) |
In 2019, several industry analyst reports confused the threat groups Molerats and APT-C-37 due to their similarity, and this has led to some confusion and inaccuracy of attribution.
For example, both groups target the Middle East and North Africa region (with a special emphasis on Palestine territories). And, they both approach victims through the use of phishing emails that contain decoy documents (mostly in Arabic) and contain themes concerning the political situation in the area.
To improve understanding of the differences and similarities of the two groups (as well as the links between them), we at Alien Labs™ are providing an analysis of their 2019 activity.
 A recent spear-phishing document from Molerats
APT-C-37 Overview
APT-C-37, also known as Pat-Bear or the Syrian Electronic Army (SEA), was first seen in October 2015 targeting members of a terrorist organization. Since 2015, however, APT-C-37 has broadened their objectives to include government agencies, armed forces leadership, media organizations, political activists, and diplomats. The group mostly targets victims in Western countries, with the intent of defacing their websites and social accounts while leaving a public footprint after hacking one of their victims.
In previous attacks, APT-C-37 targeted Windows and Android systems, utilizing popular commercial remote access trojans (RATs) such as DroidJack, SpyNote, njRAT, SSLove, and H-Worm.
Technical Analysis: APT-C-37 2019
June 2019: APT-C-37 released an Android app named after the instant messaging software “WhatsApp” as an espionage tool to reportedly spy on the Syrian opposition forces. The app was capable of installing the SSLove RAT to pull private information from the phone and exfiltrating it to a remote location.
Molerats Overview
Molerats has been present in the cybercriminal landscape since 2012. In an analysis released by the Kaspersky’s GReAT (Global Research & Analysis Team) earlier this year on the Gaza Hacker Team and their various subgroups, Kaspersky concluded that Molerats is Gaza Cybergang “Group1.” The report also concluded that Molerats (i.e. Cybergang Group 1) operates with a lower level of sophistication than other groups within the Gaza Hacker Team. In addition, a 2016 article in Security Week reported that one of Molerats campaigns (October 2016) heavily used popular RATs like NjRat and H-Worm (aka Houdini).
Technical Analysis: Molerats 2019
October 2019: In Molerats’ October operation, the attack was distributed as a phishing campaign in the Middle East. Emails included a Microsoft Word file attachment with the title “Daily report on the most important Palestinian developments for the day 9-9-2019.doc” — content that spoke to the political situation in Palestine. When a victim opened the attachment, the malware performed the following:
Displayed the Microsoft Word doc
A recent spear-phishing document from Molerats
APT-C-37 Overview
APT-C-37, also known as Pat-Bear or the Syrian Electronic Army (SEA), was first seen in October 2015 targeting members of a terrorist organization. Since 2015, however, APT-C-37 has broadened their objectives to include government agencies, armed forces leadership, media organizations, political activists, and diplomats. The group mostly targets victims in Western countries, with the intent of defacing their websites and social accounts while leaving a public footprint after hacking one of their victims.
In previous attacks, APT-C-37 targeted Windows and Android systems, utilizing popular commercial remote access trojans (RATs) such as DroidJack, SpyNote, njRAT, SSLove, and H-Worm.
Technical Analysis: APT-C-37 2019
June 2019: APT-C-37 released an Android app named after the instant messaging software “WhatsApp” as an espionage tool to reportedly spy on the Syrian opposition forces. The app was capable of installing the SSLove RAT to pull private information from the phone and exfiltrating it to a remote location.
Molerats Overview
Molerats has been present in the cybercriminal landscape since 2012. In an analysis released by the Kaspersky’s GReAT (Global Research & Analysis Team) earlier this year on the Gaza Hacker Team and their various subgroups, Kaspersky concluded that Molerats is Gaza Cybergang “Group1.” The report also concluded that Molerats (i.e. Cybergang Group 1) operates with a lower level of sophistication than other groups within the Gaza Hacker Team. In addition, a 2016 article in Security Week reported that one of Molerats campaigns (October 2016) heavily used popular RATs like NjRat and H-Worm (aka Houdini).
Technical Analysis: Molerats 2019
October 2019: In Molerats’ October operation, the attack was distributed as a phishing campaign in the Middle East. Emails included a Microsoft Word file attachment with the title “Daily report on the most important Palestinian developments for the day 9-9-2019.doc” — content that spoke to the political situation in Palestine. When a victim opened the attachment, the malware performed the following:
Displayed the Microsoft Word doc |
Malware Tool Threat Guideline | APT-C-23 |
To see everything:
Our RSS (filtrered)
