What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2018-07-06 12:08:03 | Former NSO employee steals, flogs Pegasus mobile hacking tool for $50 million (lien direct) | The staff member stole Pegasus spyware code and attempted to sell it in the Dark Web. | Tool | |||
| 2018-07-06 08:32:00 | NSO Group ex-employee arrested for attempting to sell phone Hacking Tool For $50 Million (lien direct) | Ex-employee at the surveillance firm NSO Group has been arrested and charged with stealing phone hacking tools from the company and attempting to sell it. A former employee of one of the most popular surveillance firm, NSO Group, has been arrested and charged with stealing phone hacking tools from the company and attempting to sell […] | Tool | |||
| 2018-07-05 13:08:03 | Baidu no-code EasyDL tool could democratize AI for small businesses, bridge talent gap (lien direct) | The Baidu platform aims to help accelerate enterprise adoption of artificial intelligence. | Tool | |||
| 2018-07-05 12:29:04 | Ex-NSO Employee Caught Selling Stolen Phone Hacking Tool For $50 Million (lien direct) | A former employee of one of the world's most powerful hacking companies NSO Group has been arrested and charged with stealing phone hacking tools from the company and trying to sell it for $50 million on the Darknet secretly.
Israeli hacking firm NSO Group is mostly known for selling high-tech malware capable of remotely cracking into Apple's iPhones and Google's Android devices to
|
Malware Tool | |||
| 2018-07-03 19:04:00 | 8 simple Microsoft Office 365 best practices for making your documents more accessible (lien direct) | Microsoft has updated its Accessibility Checker for Office 365. The tool now suggests accessibility communication best practices for your documents automatically. | Tool | ★★★★★ | ||
| 2018-07-02 18:34:05 | Apple Patches Bug in Swift Programming Language (lien direct) | Apple’s Swift programming language is a useful tool for developers on Mac and iOS platforms due to its versatility and wide-reaching application. Occasionally, though, Apple uncovers issues within Swift that could unintentionally allow bad actors to make inroads towards attack execution. A new Swift module released only a few months ago recently received an update to correct such an issue. In March, Apple introduced a new open source ... | Tool | |||
| 2018-06-30 17:34:02 | 3 Ways Extract Password Hashes from NTDS.dit (lien direct) | Hello friends!! Today we are going to discuss some forensic tool which is quite helpful in penetration testing to obtain NTLM password hashes from inside the host machine. As we know while penetration testing we get lots of stuff from inside the host machine and if you found some files like NTDS.dit and system hive... Continue reading → | Tool | |||
| 2018-06-29 12:55:04 | Twitter shared details about its strategy for fighting spam and bots (lien direct) | Twitter provided some details on new security processes aimed at preventing malicious automation and spam. The tech giant also shared data on the success obtained with the introduction of the new security measures. Social media platform are a privileged tool for psyops and malicious campaign, for this reason, Twitter rolled out new features to detect and […] | Spam Tool | |||
| 2018-06-28 13:12:03 | Inbenta, blamed for Ticketmaster breach, says other sites not affected (lien direct) | The customer service tool blamed a single piece of code, modified by hackers. | Tool | |||
| 2018-06-28 06:35:01 | Talos releases ThanatosDecryptor, a free Thanatos Ransomware decryptor (lien direct) | Experts from Cisco's Talos team released a free decryption tool for the Thanatos ransomware to recover the files without paying the ransom. The Thanatos ransomware first appeared in the threat landscape in February when it was discovered by researchers at the MalwareHunterTeam. The experts from Talos believe the malware is being actively developed, it was being distributed […] | Ransomware Malware Tool Threat | |||
| 2018-06-27 16:37:04 | Free Thanatos Ransomware Decryptor Released (lien direct) | Cisco's Talos team this week announced the availability of a free decryption tool to help victims of the Thanatos ransomware recover their files without paying the ransom. | Ransomware Tool | |||
| 2018-06-27 15:15:04 | Metta – Information Security Adversarial Simulation Tool (lien direct) |  Metta is an information security preparedness tool in Python to help with adversarial simulation, this can help you check various detection and control capabilities within your organisation.
This project uses Redis/Celery, python, and vagrant with virtualbox to do adversarial simulation. This allows you to test (mostly) your host based instrumentation but may also allow you to test any network based detection and controls depending on how you set up your vagrants.
Read the rest of Metta – Information Security Adversarial Simulation Tool now! Only available at Darknet. Metta is an information security preparedness tool in Python to help with adversarial simulation, this can help you check various detection and control capabilities within your organisation.
This project uses Redis/Celery, python, and vagrant with virtualbox to do adversarial simulation. This allows you to test (mostly) your host based instrumentation but may also allow you to test any network based detection and controls depending on how you set up your vagrants.
Read the rest of Metta – Information Security Adversarial Simulation Tool now! Only available at Darknet.
|
Tool | |||
| 2018-06-27 05:30:05 | NSA Exploit "DoublePulsar" Patched to Work on Windows IoT Systems (lien direct) | An infosec researcher who uses the online pseudonym of Capt. Meelo has modified an NSA hacking tool known as DoublePulsar to work on the Windows IoT operating system (formerly known as Windows Embedded). [...] | Tool | |||
| 2018-06-26 21:51:03 | Mozilla Announces Firefox Monitor Tool Testing, Firefox 61 (lien direct) | Mozilla is testing a new tool that securely checks to see if users' accounts have been hacked. | Tool | |||
| 2018-06-26 14:36:00 | \'Have I Been Pwned\' Now Built into Firefox, 1Password (lien direct) | Users can search breach data in a new tool called Firefox Monitor and check if passwords have been exposed in 1Password on the Web. | Tool | |||
| 2018-06-26 12:15:00 | Mozilla\'s new Firefox service can tell users if they\'re a victim of a data breach (lien direct) | Mozilla is integrating with the online tool Have I Been Pwned to alert users if they are at risk following website hacks. | Data Breach Tool | |||
| 2018-06-26 10:44:05 | Free Thanatos Ransomware Decryption Tool Released (lien direct) | If your computer has been infected with Thanatos Ransomware and you are searching for a free ransomware decryption tool to unlock or decrypt your files-your search is over here.
Security researchers at Cisco Talos have discovered a weakness in the Thanatos ransomware code that makes it possible for victims to unlock their Thanatos encrypted files for free without paying any ransom in
|
Ransomware Tool | |||
| 2018-06-25 12:18:03 | Google Earth\'s New Tool Measures The Distance and Area of Locations on Earth (lien direct) | Google released an update to Google Earth today that allows you to measure the distance between two locations or the square feet of an area. Now when you get into an argument with a friend about how far apart two locations are or how large an area is, you can simply go to Google Earth and prove each other wrong. [...] | Tool | |||
| 2018-06-24 19:39:21 | SMB version detection in masscan (lien direct) | My Internet-scale port scanner, masscan, supports "banner checking", grabbing basic information from a service after it connects to a port. It's less comprehensive than nmap's version and scripting checks, but it's better than just recording which ports are open.I recently extended this banner checking to include SMB. It's a complicated protocol so requires a lot more work than just grabbing text banners like you see on FTP. Implementing this, I've found that nmap and smbclient often fail to get version information. They seem focused on getting the information from a standard location in SMBv1 packets, which gives a text string indicating version. There's another place you get get it, from the NTLMSSP pluggable authentication chunks, which gives version numbers in the form of major version, minor version. and build number. Sometimes the SMBv1 information is missing, either because newer Windows version disable SMBv1 by default (supporting only SMBv2) or because they've disabled null/anonymous sessions. They still give NTLMSSP version info, though.For example, running masscan in my local bar, I get the following result:Banner on port 445/tcp on 10.1.10.200: [smb] SMBv1 time=2018-06-24 22:18:13 TZ=+240 domain=SHIPBARBO version=6.1.7601 ntlm-ver=15 domain=SHIPBARBO name=SHIPBARBO domain-dns=SHIPBARBO name-dns=SHIPBARBO os=Windows Embedded Standard 7601 Service Pack 1 ver=Windows Embedded Standard 6.1The top version string comes from NTLMSSP, with 6.1.7601, which means Windows 6.1 (Win7) build number 7601. The bottom version string comes from the SMBv1 packets, which consists of strings.The nmap and smbclient programs will get the SMBv1 part, but not the NTLMSSP part.This seems to be a problem with Rapid7's "National Exposure Index" which tracks SMB exposure (amongst other things). It's missing about 300,000 machines that report NT_STATUS_ACCESS_DENIED from smbclient rather than the numeric version info from NTLMSSP authentication.The smbclient information does have the information internally. For example, you could run the following command to put the debug level at '10' to grab it:$ smbclient -U "" -N -L 10.1.10.95 -d10You'll get something like the following output: It appears to get the Windows 6.1 numbers, though for some reason it's missing the build number.To run masscan to grab this, run:# masscan --banners -p445 10.1.10.95In the above example, I also used the "--hello smbv1" parameter, to grab both the SMBv1 and NTLMSSP version info. Otherwise, it'll default to SMBv2 if available, and only return: It appears to get the Windows 6.1 numbers, though for some reason it's missing the build number.To run masscan to grab this, run:# masscan --banners -p445 10.1.10.95In the above example, I also used the "--hello smbv1" parameter, to grab both the SMBv1 and NTLMSSP version info. Otherwise, it'll default to SMBv2 if available, and only return: |
Tool | |||
| 2018-06-22 13:54:03 | These are the devices that can run Google\'s AR measurement tool (lien direct) | Google's Measure app can virtually measure physical objects, and is now compatible with ARCore phones. | Tool | |||
| 2018-06-18 10:45:00 | Apportez votre propre terre (BYOL) & # 8211;Une nouvelle technique d'équipe rouge Bring Your Own Land (BYOL) – A Novel Red Teaming Technique (lien direct) |
Introduction
L'un des développements récents les plus importants dans les opérations offensives sophistiquées est l'utilisation des techniques de «vivre hors terre» (LOTL) par les attaquants.Ces techniques exploitent des outils légitimes présents sur le système, tels que le langage de script PowerShell, afin d'exécuter des attaques.La popularité de PowerShell en tant qu'outil offensif a abouti au développement de cadres d'équipe rouge entiers basés autour de lui, tels que Empire et Powerspoit .De plus, l'exécution de PowerShell peut être obscurcie grâce à l'utilisation d'outils tels que « invoke-obfuscation ».En réponse, les défenseurs
Introduction One of most significant recent developments in sophisticated offensive operations is the use of “Living off the Land” (LotL) techniques by attackers. These techniques leverage legitimate tools present on the system, such as the PowerShell scripting language, in order to execute attacks. The popularity of PowerShell as an offensive tool culminated in the development of entire Red Team frameworks based around it, such as Empire and PowerSploit. In addition, the execution of PowerShell can be obfuscated through the use of tools such as “Invoke-Obfuscation”. In response, defenders |
Tool Technical | ★★★★ | ||
| 2018-05-29 12:00:00 | Outil d'authentification à distance de géofaisabilité - Geologonalyzer Remote Authentication GeoFeasibility Tool - GeoLogonalyzer (lien direct) |
Les utilisateurs ont longtemps besoin pour accéder aux ressources importantes telles que les réseaux privés virtuels (VPN), les applications Web et les serveurs de courrier de n'importe où dans le monde à tout moment.Bien que la capacité d'accéder à des ressources de n'importe où soit impérative pour les employés, les acteurs de la menace tirent souvent parti des informations d'identification volées pour accéder aux systèmes et aux données.En raison de grands volumes de connexions d'accès à distance, il peut être difficile de faire la distinction entre une connexion légitime et malveillante.
Aujourd'hui, nous sortons Geologonalyzer pour aider les organisations à analyser les journaux pour identifier les connexions malveillantes basées sur la géofasibilité;par exemple
Users have long needed to access important resources such as virtual private networks (VPNs), web applications, and mail servers from anywhere in the world at any time. While the ability to access resources from anywhere is imperative for employees, threat actors often leverage stolen credentials to access systems and data. Due to large volumes of remote access connections, it can be difficult to distinguish between a legitimate and a malicious login. Today, we are releasing GeoLogonalyzer to help organizations analyze logs to identify malicious logins based on GeoFeasibility; for example |
Tool Threat | ★★★★ | ||
| 2018-04-26 11:15:00 | Établir une base de référence pour le protocole de bureau à distance Establishing a Baseline for Remote Desktop Protocol (lien direct) |
Pour le personnel informatique et les utilisateurs de Power Windows, Microsoft Terminal Services Remote Desktop Protocol (RDP) est un outil bénéfique qui permet le Interactive Utilisation ou administration d'un système Windows distant.Cependant, les consultants Mandiant ont également observé des acteurs de menace utilisant le RDP, avec des informations d'identification de domaine compromises, pour se déplacer latéralement sur les réseaux avec une segmentation limitée.
Pour comprendre comment les acteurs de la menace profitent du RDP, considérez l'exemple suivant (et figure 1):
Un membre du personnel du département des ressources humaines travaillant sur son bureau inadvertant une porte dérobée malveillante de
For IT staff and Windows power users, Microsoft Terminal Services Remote Desktop Protocol (RDP) is a beneficial tool that allows for the interactive use or administration of a remote Windows system. However, Mandiant consultants have also observed threat actors using RDP, with compromised domain credentials, to move laterally across networks with limited segmentation. To understand how threat actors take advantage of RDP, consider the following example (and Figure 1): A staff member from the HR department working on his or her desktop inadvertently installs a malicious backdoor by |
Tool Threat | ★★★★ | ||
| 2018-04-23 16:10:10 | Abusing MySQL LOCAL INFILE to read client files (lien direct) | Recently, I was playing the VolgaCTF 2018 CTF with my teammates from TheGoonies and we came across an interesting Web challenge that we didn't manage to solve during the competition. The following day, I read the write-up and learned a cool technique to attack the MySQL client directly via the LOAD DATA INFILE statement.The "Corp Monitoring" task consisted of a Corporate Monitoring API that would test the healthcheck of a given server by connecting and verifying if the FTP, Web and MySQL servers were up. The MySQL user for the connection was restricted and the healthcheck validation was based on a few queries including the "SHOW DATABASE" command.The key to solve the challenge was to identify the "Can Use LOAD DATA LOCAL" client capability and point the API to a Rogue MySQL server that would read arbitrary files from the client via LOAD DATA INFILE statements.After reading about the technique, I decided to check how several libraries, clients and Web Frameworks could be exploited. I also ended up writing a a Bettercap module to abuse this feature in combination with MITM attacks. Previous Research Before I start I would like to point that this technique is not new: it's a known and documented feature from the MySQL clients. I gathered prior posts, tools and presentations and they're all written by Russians - it looks like these techniques are not very widespread outside there.- Database Honeypot by design - Presentation from Yuri Goltsev (August 2013)- Rogue-MySql-Server Tool: MySQL fake server to read files of connected clients (September 2013)- MySQL connect file read - Post from the Russian Security (April 2016)Revisiting MySQL LOAD DATA INFILEAccording to the MySQL documentation, the handshake connection phase performs the following tasks:- Exchange the capabilities of client and server- Setup SSL communication channel if requested- Authenticate the client against the serverAfter the successful authentication, the client sends the query and waits for the server response before actually doing something. The "Client Capabilities" packet includes an entry called "Can Use LOAD DATA LOCAL". Previous Research Before I start I would like to point that this technique is not new: it's a known and documented feature from the MySQL clients. I gathered prior posts, tools and presentations and they're all written by Russians - it looks like these techniques are not very widespread outside there.- Database Honeypot by design - Presentation from Yuri Goltsev (August 2013)- Rogue-MySql-Server Tool: MySQL fake server to read files of connected clients (September 2013)- MySQL connect file read - Post from the Russian Security (April 2016)Revisiting MySQL LOAD DATA INFILEAccording to the MySQL documentation, the handshake connection phase performs the following tasks:- Exchange the capabilities of client and server- Setup SSL communication channel if requested- Authenticate the client against the serverAfter the successful authentication, the client sends the query and waits for the server response before actually doing something. The "Client Capabilities" packet includes an entry called "Can Use LOAD DATA LOCAL". |
Hack Tool Vulnerability | ★★★★ | ||
| 2018-04-23 10:00:00 | Chargement de code de coquille du noyau Loading Kernel Shellcode (lien direct) |
Dans le sillage des récents décharges d'outils de piratage, l'équipe Flare a vu un pic dans des échantillons de logiciels malveillants détonant le shellcode du noyau.Bien que la plupart des échantillons puissent être analysés statiquement, l'équipe Flare débogue parfois ces échantillons pour confirmer des fonctionnalités spécifiques.Le débogage peut être un moyen efficace de contourner l'emballage ou l'obscurcissement et d'identifier rapidement les structures, les routines système et les processus auxquels un échantillon de shellcode de noyau accéde.
Ce message commence une série centrée sur l'analyse des logiciels du noyau et présente un outil qui utilise un pilote de noyau Windows personnalisé pour charger et exécuter le noyau Windows
In the wake of recent hacking tool dumps, the FLARE team saw a spike in malware samples detonating kernel shellcode. Although most samples can be analyzed statically, the FLARE team sometimes debugs these samples to confirm specific functionality. Debugging can be an efficient way to get around packing or obfuscation and quickly identify the structures, system routines, and processes that a kernel shellcode sample is accessing. This post begins a series centered on kernel software analysis, and introduces a tool that uses a custom Windows kernel driver to load and execute Windows kernel |
Malware Tool Technical | ★★★★ | ||
| 2018-04-18 01:00:00 | Comment la montée des crypto-monnaies façonne le paysage de la cybercriminalité: utilisation des infrastructures de blockchain How the Rise of Cryptocurrencies Is Shaping the Cyber Crime Landscape: Blockchain Infrastructure Use (lien direct) |
Mise à jour (31 mai 2018): Une section de la publication sur les IPS OpenNIC couramment utilisées a été supprimée pour éviter toute implication selon laquelle les IPS OpenNIC sont intrinsèquement malveillants, ce qui n'est pas le cas.
Introduction
Les cybercriminels ont toujours été attirés par les crypto-monnaies car il fournit un certain niveau d'anonymat et peut être facilement monétisé.Cet intérêt a augmenté ces dernières années, dépassant bien au-delà du désir d'utiliser simplement les crypto-monnaies comme mode de paiement pour les outils et services illicites.De nombreux acteurs ont également tenté de capitaliser sur la popularité croissante et la montée en puissance ultérieure
UPDATE (May 31, 2018): A section of the post on commonly used OpenNIC IPs has been removed to avoid any implication that the OpenNIC IPs are inherently malicious, which is not the case. Introduction Cyber criminals have always been attracted to cryptocurrencies because it provides a certain level of anonymity and can be easily monetized. This interest has increased in recent years, stemming far beyond the desire to simply use cryptocurrencies as a payment method for illicit tools and services. Many actors have also attempted to capitalize on the growing popularity and subsequent rising |
Tool | ★★★★ | ||
| 2018-04-05 10:00:00 | Fake Software Update Abuses NetSupport Tool à distance Fake Software Update Abuses NetSupport Remote Access Tool (lien direct) |
Au cours des derniers mois, FireEye a suivi une campagne dans la fenêtre qui exploite des sites compromis pour répartir les fausses mises à jour.Dans certains cas, la charge utile était l'outil d'accès à distance (RAT) du gestionnaire Netsupport.Netsupport Manager est un rat disponible dans le commerce qui peut être utilisé légitimement par les administrateurs système pour accéder à distance aux ordinateurs clients.Cependant, les acteurs malveillants abusent de cette application en l'installant aux systèmes des victimes à leur insu pour obtenir un accès non autorisé à leurs machines.Ce blog détaille notre analyse du javascript et des composants utilisés dans
Over the last few months, FireEye has tracked an in-the-wild campaign that leverages compromised sites to spread fake updates. In some cases, the payload was the NetSupport Manager remote access tool (RAT). NetSupport Manager is a commercially available RAT that can be used legitimately by system administrators for remotely accessing client computers. However, malicious actors are abusing this application by installing it to the victims\' systems without their knowledge to gain unauthorized access to their machines. This blog details our analysis of the JavaScript and components used in |
Tool Technical | ★★★★ | ||
| 2018-03-07 18:33:04 | Memcached DDoS Attacks Will Be BIG In 2018 (lien direct) |  So after the massive DDoS attack trend in 2016 it seems like 2018 is going to the year of the Memcached DDoS amplification attack with so many insecure Memcached servers available on the public Internet.
Unfortunately, it looks like a problem that won't easily go away as there are so many publically exposed, poorly configured Memcached servers online (estimated to be over 100,000).
Honestly, Github handled the 1.3Tbps attack like a champ with only 10 minutes downtime although they did deflect it by moving traffic to Akamai.
Read the rest of Memcached DDoS Attacks Will Be BIG In 2018 now! Only available at Darknet. So after the massive DDoS attack trend in 2016 it seems like 2018 is going to the year of the Memcached DDoS amplification attack with so many insecure Memcached servers available on the public Internet.
Unfortunately, it looks like a problem that won't easily go away as there are so many publically exposed, poorly configured Memcached servers online (estimated to be over 100,000).
Honestly, Github handled the 1.3Tbps attack like a champ with only 10 minutes downtime although they did deflect it by moving traffic to Akamai.
Read the rest of Memcached DDoS Attacks Will Be BIG In 2018 now! Only available at Darknet.
|
Tool | ★★★ | ||
| 2018-03-07 16:30:05 | Sonatype Makes Nexus Firewall Available To 10 Million Developers (lien direct) | The ISBuzz Post: This Post Sonatype Makes Nexus Firewall Available To 10 Million Developers | Tool | ★★ | ||
| 2018-03-07 14:52:00 | Single Photo uniquely identifies Smartphone that took it (lien direct) | Technology developed by researchers at the State University of New York can create a smartphone “fingerprint” from a single photo captured by the device. The technology may clear the way for a new identity verification system that can secure online transactions or protect smartphone owners from identity theft. The technology, developed...Read the whole entry... _!fbztxtlnk!_ https://feeds.feedblitz.com/~/530864124/0/thesecurityledger -->» | Tool | ★★★★ | ||
| 2018-02-07 16:45:00 | Reelphish: un outil de phishing à deux facteurs en temps réel ReelPhish: A Real-Time Two-Factor Phishing Tool (lien direct) |
Ingénierie sociale et authentification à deux facteurs
Les campagnes d'ingénierie sociale sont une menace constante pour les entreprises car elles ciblent la chaîne la plus faible de la sécurité: les gens.Une attaque typique capturerait le nom d'utilisateur et le mot de passe d'une victime et le stockerait pour qu'un attaquant puisse réutiliser plus tard.L'authentification à deux facteurs (2FA) ou l'authentification multi-facteurs (MFA) est couramment considérée comme une solution à ces menaces.
2FA ajoute une couche supplémentaire d'authentification en plus du nom d'utilisateur et du mot de passe typiques.Deux implémentations 2FA courantes sont des mots de passe unique et des notifications push.Les mots de passe uniques sont
Social Engineering and Two-Factor Authentication Social engineering campaigns are a constant threat to businesses because they target the weakest chain in security: people. A typical attack would capture a victim\'s username and password and store it for an attacker to reuse later. Two-Factor Authentication (2FA) or Multi-Factor Authentication (MFA) is commonly seen as a solution to these threats. 2FA adds an extra layer of authentication on top of the typical username and password. Two common 2FA implementations are one-time passwords and push notifications. One-time passwords are |
Tool Threat Technical | ★★★★ | ||
| 2018-01-04 16:30:00 | Débogage de logiciels malveillants complexes qui exécutent du code sur le tas Debugging Complex Malware that Executes Code on the Heap (lien direct) |
Introduction
Dans ce blog, je partagerai une simple tactique de débogage pour créer des «points de sauvegarde» lors du débogage à distance itératif d'échantillons à plusieurs étages complexes qui exécutent du code dans la mémoire du tas à des adresses non déterministes.Je partagerai deux exemples: l'un artificiel, et l'autre un échantillon de logiciel malveillant modulaire complexe (MD5 Hash: 830A09FF05EAC9A5F42897BA5176A36A) d'une famille que nous appelons PoisonPlug.Je me concentrerai sur IDA Pro et Windbg, mais j'expliquerai comment réaliser le même effet avec d'autres outils.Avec cette tactique, vous pouvez également remettre l'exécution du programme entre plusieurs débuggeurs en utilisant
Introduction In this blog, I will share a simple debugging tactic for creating “save points” during iterative remote debugging of complex multi-stage samples that execute code in heap memory at non-deterministic addresses. I\'ll share two examples: one contrived, and the other a complex, modular malware sample (MD5 hash: 830a09ff05eac9a5f42897ba5176a36a) from a family that we call POISONPLUG. I will focus on IDA Pro and WinDbg, but I\'ll explain how to achieve the same effect with other tools as well. With this tactic, you can also hand off program execution between multiple debuggers using |
Malware Tool Technical | ★★★★ | ||
| 2017-11-28 19:00:00 | La variante Ursnif nouvellement observée utilise une technique de rappel TLS malveillante pour réaliser l'injection de processus Newly Observed Ursnif Variant Employs Malicious TLS Callback Technique to Achieve Process Injection (lien direct) |
Introduction
Les rappels TLS (stockage local de thread) sont fournis par le système d'exploitation Windows pour prendre en charge l'initialisation et la terminaison supplémentaires pour les structures de données par thread.
Comme indiqué précédemment, les rappels TLS malveillants, en tant qu'astuce anti-analyse, ont été observés pendant un certain temps et peuvent permettre à des fichiers PE d'inclure des fonctions de rappel TLS malveillantesExécution prévue) dans l'en-tête PE.Essentiellement, les analystes sans méfiance et les outils de sécurité automatisés peuvent manquer le point d'entrée réel à Malcode s'ils
Introduction TLS (Thread Local Storage) callbacks are provided by the Windows operating system to support additional initialization and termination for per-thread data structures. As previously reported, malicious TLS callbacks, as an anti-analysis trick, have been observed for quite some time and can allow for PE files to include malicious TLS callback functions to be executed prior to the AddressOfEntryPoint field (the normal start of intended execution) in the PE header. In essence, unsuspecting analysts and automated security tools can miss the actual entry point to malcode if they |
Tool | ★★★★ | ||
| 2017-10-30 09:00:00 | Présentation de GoCrack: un outil de fissuration de mot de passe géré Introducing GoCrack: A Managed Password Cracking Tool (lien direct) |
L'équipe d'innovation et d'ingénierie personnalisée de Fireeye \\ a publié aujourd'hui un outil appelé gocrack qui permet aux équipes rouges d'effectuer efficacement efficacement efficacementGérez les tâches de craquage de mot de passe sur plusieurs serveurs GPU en fournissant une interface utilisateur en temps réel facile à utiliser (Figure 1 montre le tableau de bord) pour créer, afficher et gérer les tâches.Déployez simplement un serveur GoCrack avec un travailleur sur chaque machine capable GPU / CPU et le système distribuera automatiquement des tâches sur ces machines GPU / CPU.
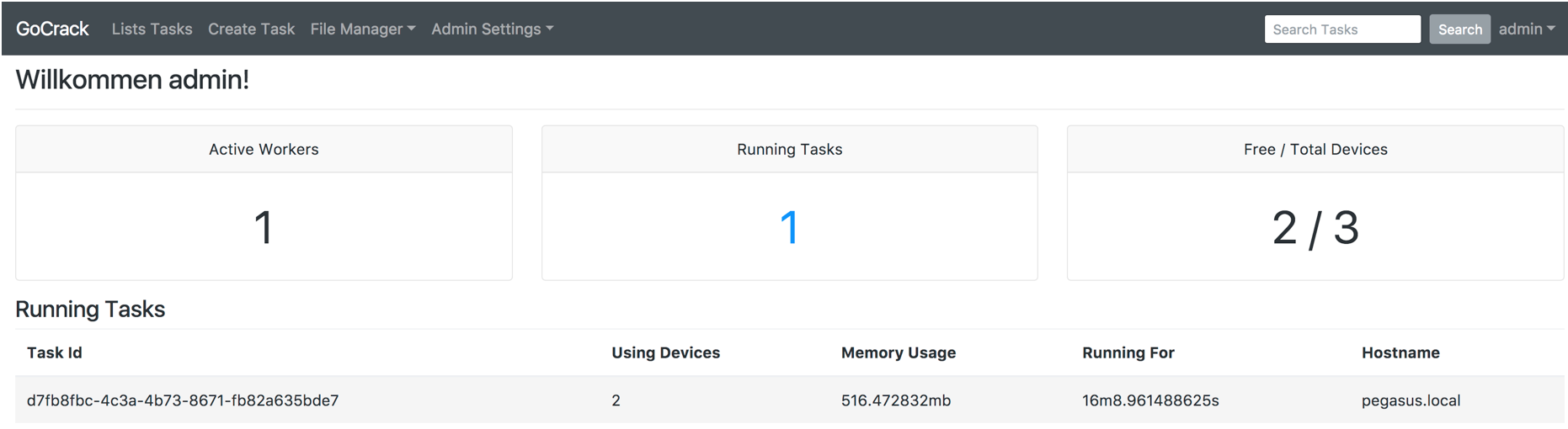 Dashboard Comme les lecteurs de ce blog le savent probablement, les outils de craquage de mot de passe sont un moyen efficace pour les professionnels de la sécurité de tester le mot de passe Dashboard Comme les lecteurs de ce blog le savent probablement, les outils de craquage de mot de passe sont un moyen efficace pour les professionnels de la sécurité de tester le mot de passe
FireEye\'s Innovation and Custom Engineering (ICE) team released a tool today called GoCrack that allows red teams to efficiently manage password cracking tasks across multiple GPU servers by providing an easy-to-use, web-based real-time UI (Figure 1 shows the dashboard) to create, view, and manage tasks. Simply deploy a GoCrack server along with a worker on every GPU/CPU capable machine and the system will automatically distribute tasks across those GPU/CPU machines.  DashboardAs readers of this blog probably know, password cracking tools are an effective way for security professionals to test password DashboardAs readers of this blog probably know, password cracking tools are an effective way for security professionals to test password |
Tool | ★★★★ | ||
| 2017-07-26 11:31:00 | VM Flare: la distribution d'analyse de logiciels malveillants Windows dont vous avez toujours besoin! FLARE VM: The Windows Malware Analysis Distribution You\\'ve Always Needed! (lien direct) |
Mise à jour 3 (5 décembre 2022): La VM Flare a été Mise à jour àêtre plus ouvert et maintenable .
Mise à jour 2 (14 novembre 2018): VM Flare a maintenant un Nouveau processus d'installation, de mise à niveau et de désinstallation , et comprend également de nombreux nouveaux outils tels que IDA 7.0, Radare et Yara.
mise à jour (26 avril 2018): La méthode d'installation Web pour déployer Flare VM est désormais obsolète.Veuillez vous référer à la Readme sur la VM Github le plus à la dateinstructions d'installation.
En tant qu'ingénieur à la recherche de l'équipe Flare, je compte sur une machine virtuelle (VM) personnalisée pour effectuer Analyse des logiciels malveillants .La machine virtuelle est un Windows
UPDATE 3 (Dec. 5, 2022): FLARE VM has been updated to be more open and maintainable. UPDATE 2 (Nov. 14, 2018): FLARE VM now has a new installation, upgrade, and uninstallation process, and also includes many new tools such as IDA 7.0, radare and YARA. UPDATE (April 26, 2018): The web installer method to deploy FLARE VM is now deprecated. Please refer to the README on the FLARE VM GitHub for the most up-to-date installation instructions. As a reverse engineer on the FLARE Team I rely on a customized Virtual Machine (VM) to perform malware analysis. The Virtual Machine is a Windows |
Malware Tool | ★★★★ | ||
| 2017-07-05 10:00:00 | Présentation de la prise en charge de Linux pour Fakennet-NG: outil d'analyse de réseau dynamique de Next Generation de Flare \\ Introducing Linux Support for FakeNet-NG: FLARE\\'s Next Generation Dynamic Network Analysis Tool (lien direct) |
Introduction
En 2016, Flare a présenté FAKENET-NG , un ouvert-Source Outil d'analyse de réseau écrite en python.Fakennet-NG permet aux analystes de sécurité d'observer et d'interagir avec les applications réseau à l'aide de protocoles standard ou personnalisés sur un seul hôte Windows, ce qui est particulièrement utile pour l'analyse des logiciels malveillants et l'ingénierie inverse.Depuis la version de Fakennet-NG \\, Flare a ajouté le support pour des protocoles supplémentaires.Fakennet-ng a maintenant une prise en charge prête à l'emploi pour DNS, HTTP (y compris les bits), FTP, TFTP, IRC, SMTP, POP, TCP et UDP ainsi que SSL.
En s'appuyant sur ce travail, Flare a maintenant amené Fakennet-NG à
Introduction In 2016, FLARE introduced FakeNet-NG, an open-source network analysis tool written in Python. FakeNet-NG allows security analysts to observe and interact with network applications using standard or custom protocols on a single Windows host, which is especially useful for malware analysis and reverse engineering. Since FakeNet-NG\'s release, FLARE has added support for additional protocols. FakeNet-NG now has out-of-the-box support for DNS, HTTP (including BITS), FTP, TFTP, IRC, SMTP, POP, TCP, and UDP as well as SSL. Building on this work, FLARE has now brought FakeNet-NG to |
Malware Tool Technical | ★★★★ | ||
| 2017-04-03 07:00:00 | Dissection de l'une des boursiers WMI et PowerShell sans fichu et PowerShell (Poshspy) Dissecting One of APT29\\'s Fileless WMI and PowerShell Backdoors (POSHSPY) (lien direct) |
Mandiant a observé APT29 en utilisant une porte dérobée furtive que nous appelons poshspy.Poshspy exploite deux des outils que le groupe utilise fréquemment: PowerShell et Windows Management Instrumentation (WMI).Dans les enquêtes que Mandiant a menées, il est apparu qu'APT29 a déployé Poshspy comme porte dérobée secondaire pour une utilisation s'ils perdaient l'accès à leurs possibilités principales.
Poshspy tire le meilleur parti des fonctionnalités Windows intégrées & # 8211;Ce que l'on appelle «vivre du terrain» & # 8211;pour faire une porte dérobée particulièrement furtive.L'utilisation de WMI de Poshspy \\ pour stocker et persister le code de porte dérobée le rend presque invisible pour quiconque
Mandiant has observed APT29 using a stealthy backdoor that we call POSHSPY. POSHSPY leverages two of the tools the group frequently uses: PowerShell and Windows Management Instrumentation (WMI). In the investigations Mandiant has conducted, it appeared that APT29 deployed POSHSPY as a secondary backdoor for use if they lost access to their primary backdoors. POSHSPY makes the most of using built-in Windows features – so-called “living off the land” – to make an especially stealthy backdoor. POSHSPY\'s use of WMI to both store and persist the backdoor code makes it nearly invisible to anyone |
Tool Technical | APT 29 | ★★★★ | |
| 2017-03-31 09:15:00 | Présentation du moniteur.app pour macOS Introducing Monitor.app for macOS (lien direct) |
Mise à jour 2 (24 octobre 2018): Monitor.App prend maintenant en charge MacOS 10.14 .
mise à jour (4 avril 2018): Monitor.app prend maintenant en charge MacOS 10.13.
En tant qu'analyste de logiciels malveillants ou programmeur de systèmes, avoir une suite d'outils d'analyse dynamique solides est vital pour être rapide et efficace.Ces outils nous permettent de comprendre les capacités de logiciels malveillants et les composants sans papiers du système d'exploitation.Un outil évident qui me vient à l'esprit est procmon de la légendaire Sysinternals Suite de Microsoft.Ces outils ne fonctionnent que sur Windows et nous aimons macOS.
macOS possède un logiciel d'instrumentation dynamique fantastique
UPDATE 2 (Oct. 24, 2018): Monitor.app now supports macOS 10.14. UPDATE (April 4, 2018): Monitor.app now supports macOS 10.13. As a malware analyst or systems programmer, having a suite of solid dynamic analysis tools is vital to being quick and effective. These tools enable us to understand malware capabilities and undocumented components of the operating system. One obvious tool that comes to mind is Procmon from the legendary Sysinternals Suite from Microsoft. Those tools only work on Windows though and we love macOS. macOS has some fantastic dynamic instrumentation software |
Malware Tool | ★★★★ | ||
| 2017-03-08 17:15:00 | Introduction aux applications de cacao en ingénierie inverse Introduction to Reverse Engineering Cocoa Applications (lien direct) |
Bien que cela ne soit pas aussi courant que Windows Malware, un flux constant de logiciels malveillants a été découvert au fil des ans qui s'exécute sur le système d'exploitation OS X, désormais rebaptisé MacOS.Février a vu trois publications particulièrement intéressantes sur le thème des logiciels malveillants MacOS: un application de cacao de trojan qui envoie des informations systèmey compris les données de trousseau à l'attaquant, un version macOS d'APT28\'s xagent malware , et un new-trojan ransomware .
Dans ce blog, l'équipe Flare souhaite introduire deux petits outils qui peuvent aider à la tâche des applications de cacao en ingénierie inverse pour MacOS.Afin de
While not as common as Windows malware, there has been a steady stream of malware discovered over the years that runs on the OS X operating system, now rebranded as macOS. February saw three particularly interesting publications on the topic of macOS malware: a Trojan Cocoa application that sends system information including keychain data back to the attacker, a macOS version of APT28\'s Xagent malware, and a new Trojan ransomware. In this blog, the FLARE team would like to introduce two small tools that can aid in the task of reverse engineering Cocoa applications for macOS. In order to |
Malware Tool | APT 28 | ★★★★ | |
| 2017-03-03 13:00:00 | Évasion antivirus reconstruite & # 8211;Voile 3.0 AntiVirus Evasion Reconstructed – Veil 3.0 (lien direct) |
le Veil Framework est une collection d'outils conçus pour être utilisés lors de tests de sécurité offensive.Lorsque le temps l'appelle, mandiant \\L'équipe rouge utilisera le voile-trame pour atteindre leur objectif.L'outil le plus couramment utilisé est le voile-évasion, qui peut transformer un script arbitraire ou un morceau de shellcode en un exécutable Windows qui échappera aux détections par des produits antivirus courants.
Veil 2.0 a été rendu public le 17 juin 2013 et le cadre principal est resté largement inchangé depuis cette date.Il y a eu quelques modifications dans le cadre lui-même, mais ceux-ci ont
The Veil Framework is a collection of tools designed for use during offensive security testing. When the time calls for it, Mandiant\'s Red Team will use the Veil-Framework to help achieve their objective. The most commonly used tool is Veil-Evasion, which can turn an arbitrary script or piece of shellcode into a Windows executable that will evade detections by common antivirus products. Veil 2.0 was made publicly available on June 17, 2013, and the core framework has remained largely unchanged since that date. There have been some modifications to the framework itself, but these have |
Tool Technical | ★★★★ | ||
| 2017-02-22 12:20:20 | Techniques de phishing de lance utilisées dans les attaques ciblant le gouvernement mongol Spear Phishing Techniques Used in Attacks Targeting the Mongolian Government (lien direct) |
Introduction
Fireeye a récemment observé une campagne sophistiquée ciblant les individus au sein du gouvernement mongol.Les individus ciblés qui ont activé les macros dans un document Microsoft Word malveillant peuvent avoir été infectés par poison ivy , un outil d'accès à distance populaire (rat) qui est utilisé depuis près d'une décennie pour la journalisation clé, la capture d'écran et de vidéo, les transferts de fichiers, le vol de mot de passe, l'administration du système, le traficrelais, et plus encore.Les acteurs de la menace derrière cette attaque ont démontré des techniques intéressantes, notamment:
Évasion personnalisée basée sur le profil de la victime & # 8211;La campagne a utilisé un
Introduction FireEye recently observed a sophisticated campaign targeting individuals within the Mongolian government. Targeted individuals that enabled macros in a malicious Microsoft Word document may have been infected with Poison Ivy, a popular remote access tool (RAT) that has been used for nearly a decade for key logging, screen and video capture, file transfers, password theft, system administration, traffic relaying, and more. The threat actors behind this attack demonstrated some interesting techniques, including: Customized evasion based on victim profile – The campaign used a |
Tool Threat | ★★★ | ||
| 2016-12-01 18:15:55 | LuaBot: Malware targeting cable modems (lien direct) | During mid-2015 I disclosed some vulnerabilities affecting multiple ARRIS cable modems. I wrote a blogpost about ARRIS' nested backdoor and detailed some of my cable modem research during the 2015 edition from NullByte Security Conference.CERT/CC released the Vulnerability Note VU#419568 and it got lots of media coverage. I did not provide any POC's during that time because I was pretty sure that those vulnerabilities were easily wormable... And guess what? Someone is actively exploiting those devices since May/2016.The malware targets Puma 5 (ARM/Big Endian) cable modems, including the ARRIS TG862 family. The infection happens in multiple stages and the dropper is very similar to many common worm that targets embedded devices from multiple architectures. The final stage is an ARMEB version from the LuaBot Malware.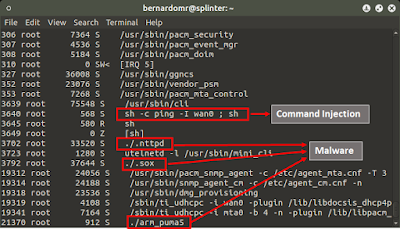 The ARMEL version from the LuaBot Malware was dissected on a blogpost from Malware Must Die, but this specific ARMEB was still unknown/undetected for the time being. The malware was initially sent to VirusTotal on 2016-05-26 and it still has a 0/0 detection rate. The ARMEL version from the LuaBot Malware was dissected on a blogpost from Malware Must Die, but this specific ARMEB was still unknown/undetected for the time being. The malware was initially sent to VirusTotal on 2016-05-26 and it still has a 0/0 detection rate. |
Malware Tool Vulnerability | ★★★★ | ||
| 2016-08-03 03:30:00 | FAKENET-NG: outil d'analyse de réseau dynamique de prochaine génération FakeNet-NG: Next Generation Dynamic Network Analysis Tool (lien direct) |
En tant qu'équipe insensée dans l'équipe Flare (Fireeye Labs Advanced Inverse Engineering), j'effectue régulièrement une analyse dynamique de base des échantillons de logiciels malveillants.L'objectif est d'observer rapidement les caractéristiques d'exécution en exécutant des binaires dans un environnement sûr.Une tâche importante lors de l'analyse dynamique consiste à imiter l'environnement réseau et à inciter les logiciels malveillants à penser qu'il est connecté à Internet.Une fois bien fait, le logiciel malveillant révèle ses signatures de réseau telles que les noms de domaine de commande et de contrôle (C2), les chaînes d'agent utilisateur, les URL interrogées, etc.
Un outil de choix est Fakennet.Dans ce blog, je
As a reverse engineer on the FLARE (FireEye Labs Advanced Reverse Engineering) team, I regularly perform basic dynamic analysis of malware samples. The goal is to quickly observe runtime characteristics by running binaries in a safe environment. One important task during dynamic analysis is to emulate the network environment and trick the malware into thinking it is connected to the Internet. When done right, the malware reveals its network signatures such as command and control (C2) domain names, User-Agent strings, URLs queried, and so on. One tool of choice is FakeNet. In this blog, I |
Malware Tool Technical | ★★★★ | ||
| 2015-12-09 01:03:30 | Hack.lu 2015 CTF Write Up: Dr. Bob (Forensic 150) (lien direct) | Hack.lu 2015 CTF was organised by fluxfingers during October 20-22. It's one of the coolest CTFs around, the only drawback is that it runs during week days (hey guys patch this for the next years). My team TheGoonies ranked #59th, which is not bad considering we only played part-time.The task Dr. Bob was the one I found most interesting as it included disk forensics, memory forensics and basic crypto tasks.Task: Dr. Bob (Forensic 150)There are elections at the moment for the representative of the students and the winner will be announced tomorrow by the head of elections Dr. Bob. The local schoolyard gang is gambling on the winner and you could really use that extra cash. Luckily, you are able to hack into the mainframe of the school and get a copy of the virtual machine that is used by Dr. Bob to store the results. The desired information is in the file /home/bob/flag.txt, easy as that.Download: dr_bob_e22538fa166acecc68fa17ac148dcbe2.tar.gzThe file provided is a VirtualBox image in a saved state. According to the challenge instructions, we have to retrieve the flag from the user home folder. The VM starts on a login terminal of what seems to be a Linux distro.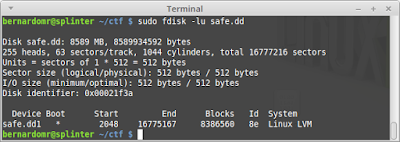 sudo losetup -o 1048576 /dev/loop0 safe.ddsudo lvmdiskscan sudo losetup -o 1048576 /dev/loop0 safe.ddsudo lvmdiskscan There are two interesting devices: /dev/vg/root and /dev/vg/home, let's 1 - mount the home folder, 2 - grab the flag and 3 - PROFIT!!! There are two interesting devices: /dev/vg/root and /dev/vg/home, let's 1 - mount the home folder, 2 - grab the flag and 3 - PROFIT!!! |
Hack Tool | ★★★★ | ||
| 2015-05-04 23:57:38 | Firmware Forensics: Diffs, Timelines, ELFs and Backdoors (lien direct) | This post covers some common techniques that I use to analyze and reverse firmware images. These techniques are particularly useful to dissect malicious firmwares, spot backdoors and detect unwanted modifications.Backdooring and re-flashing firmware images is becoming mainstream: malicious guys are infecting embedded devices and inserting trojans in order to achieve persistence. Recent articles covered the increasing number of trojanized android firmwares and routers that are being permanently modified.Attackers with a privileged network position may MITM your requests and forge fake updates containing malicious firmwares. Writing Evilgrade modules for this is really simple, as most vendors keep failing to deliver updates securely, right ASUS? Valid signature -> nvram_set("rsasign_check", "1")NoConName 2014 CTF Finals: VodkaI'll keep my tradition of writing posts based on CTF challenges because everybody upvotes CTF posts on reddit it's cool.The challenge "Vodka", from NoConName 2014 CTF Finals was created by @MarioVilas, who kindly provided the files here (thanks dude!).I did not participate on the CTF finals, but I found the challenge really interesting because there were many different ways to solve it, summarizing the actions needed to audit a compromised f Valid signature -> nvram_set("rsasign_check", "1")NoConName 2014 CTF Finals: VodkaI'll keep my tradition of writing posts based on CTF challenges because everybody upvotes CTF posts on reddit it's cool.The challenge "Vodka", from NoConName 2014 CTF Finals was created by @MarioVilas, who kindly provided the files here (thanks dude!).I did not participate on the CTF finals, but I found the challenge really interesting because there were many different ways to solve it, summarizing the actions needed to audit a compromised f |
Malware Hack Tool | ★★★★ | ||
| 2015-04-17 09:00:00 | Flare Ida Pro Script Series: Application des prototypes de fonction aux appels indirects FLARE IDA Pro Script Series: Applying Function Prototypes to Indirect Calls (lien direct) |
intro
L'équipe Advanced Insinerering (Flare) de FireEye Labs Travelding Fireeye Labs souhaite présenter le prochain épisode de notre série de blogs IDA Pro Script afin de partager les connaissances et les outils avec la communauté.Tous les scripts et plug-ins sont disponibles à partir de notre référentiel github .
lorsque les choses fonctionnent correctement
L'analyse de pile Ida \\ et la propagation des informations de type est extrêmement utile lorsque les logiciels malveillants de l'ingénierie inverse.Hex Rays fournit plusieurs fichiers .til avec IDA qui contiennent le type de données et les déclarations de fonction pour une gamme de compilateurs et d'API.Ils fournissent également un outil supplémentaire nommé tilib
Intro The FireEye Labs Advanced Reverse Engineering (FLARE) Team would like to introduce the next installment of our IDA Pro Script series of blog posts in order to share knowledge and tools with the community. All scripts and plug-ins are available from our GitHub repository. When Things Work Right IDA\'s stack analysis and propagation of type information is extremely useful when reverse engineering malware. Hex-Rays provides several .til files with IDA that contain data type and function declarations for a range of compilers and APIs. They also provide an additional tool named tilib |
Tool | ★★★ | ||
| 2015-04-01 15:17:27 | Microsoft Word Intruder (MWI): un nouveau kit d'exploitation de documents Word Microsoft Word Intruder (MWI): A New Word Document Exploit Kit (lien direct) |
Les outils utilisés pour créer des documents malveillants qui exploitent les vulnérabilités dans Microsoft Word sont désormais annoncés dans des forums underground et un nouvel outil a émergé qui offre la possibilité de suivre l'efficacité des campagnes.Le constructeur, Microsoft Word Intruder (MWI), est annoncé comme un outil «APT» à utiliser dans les attaques ciblées.Il s'accompagne d'un ensemble de statistiques appelé «Mwistat» qui permet aux opérateurs de suivre diverses campagnes.
Selon l'auteur, l'utilisation de MWI en collaboration avec le spam est interdite, et ceux qui ignorent ce risque pour que leur permis soit révoquée.Dans
The tools used to create malicious documents that exploit vulnerabilities in Microsoft Word are now being advertised in underground forums and one new tool has emerged that provides the ability to track the effectiveness of campaigns. The builder, Microsoft Word Intruder (MWI), is advertised as an “APT” tool to be used in targeted attacks. It is accompanied by a statistics package known as “MWISTAT” that allows operators to track various campaigns. According to the author, the use of MWI in conjunction with spam is forbidden, and those who ignore this risk having their license revoked. In |
Spam Tool Vulnerability Technical | ★★★★ | ||
| 2015-02-27 00:56:54 | Extracting RAW pictures from memory dumps (lien direct) | IntroductionEarlier today, while reading my Twitter timeline, I saw some Infosec folks discussing about scripts/tools to identify RAW pictures in memory dumps. I decided, then, to write this blog post and share a small hack that I use to visualize data (including memory dumps). Memory DumpsThe first thing you will want to do is to narrow the analysis to the process containing interesting images/pictures. I'm going to use three different memory dumps here:Remote Desktop Client - Windows 7 x64 (mstsc.exe)Let's use the Windows built-in RDP client to connect to an external server and dump the processmemory using procdump: Memory DumpsThe first thing you will want to do is to narrow the analysis to the process containing interesting images/pictures. I'm going to use three different memory dumps here:Remote Desktop Client - Windows 7 x64 (mstsc.exe)Let's use the Windows built-in RDP client to connect to an external server and dump the processmemory using procdump: |
Hack Tool | ★★★★ | ||
| 2015-01-08 20:39:00 | Flare Ida Pro Script Series: Génération de modèles de fonction Flair Using Idapython FLARE IDA Pro Script Series: Generating FLAIR function patterns using IDAPython (lien direct) |
L'équipe Advanced Insidering (Flare) de FireEye Labs continue de partager les connaissances et les outils avec la communauté.Ceci est le troisième script Ida Pro que nous avons publié via ce blog et nous continuerons à publier ces scripts ici .
Résumé
Ce blog décrit un script idapython pour aider à l'ingénierie inverse de logiciels malveillants.Les signatures de flirt aident Ida Pro reconnaître les fonctions communes dans les programmes compilés et les renommer automatiquement pour l'ingénieur inverse.Le script idapython idb2pat.py génère des modèles IDA Pro Flair à partir des fichiers IDB existants.Vous pouvez l'utiliser pour générer des signatures de flirt pour
The FireEye Labs Advanced Reverse Engineering (FLARE) Team continues to share knowledge and tools with the community. This is the third IDA Pro script we\'ve released via this blog and we\'ll continue to release these scripts here. Summary This blog describes an IDAPython script to assist with malware reverse engineering. FLIRT signatures help IDA Pro recognize common functions in compiled programs and automatically rename them for the reverse engineer. The IDAPython script idb2pat.py generates IDA Pro FLAIR patterns from existing IDB files. You can use it to generate FLIRT signatures for |
Malware Tool Technical | ★★★★ | ||
| 2014-09-11 09:00:00 | Flare Ida Pro Script Series: MSDN Annotations Plugin for Malware Analysis (lien direct) | L'équipe Advanced Insidering (Flare) de FireEye Labs continue de partager les connaissances et les outils avec la communauté.Nous avons commencé cette série de blogs avec un script pour Récupération automatique des chaînes construites dans les logiciels malveillants .Comme toujours, vous pouvez Téléchargez ces scripts sur notre page github .Nous espérons que vous trouverez tous ces scripts aussi utiles que nous.
motivation
Au cours de mon stage d'été avec l'équipe Flare, mon objectif était de développer des plug-ins idapython qui accélèrent le flux de travail ingénieur en inverse dans IDA Pro.Tout en analysant des échantillons de logiciels malveillants avec l'équipe, j'ai réalisé que beaucoup de temps est passé à chercher
The FireEye Labs Advanced Reverse Engineering (FLARE) Team continues to share knowledge and tools with the community. We started this blog series with a script for Automatic Recovery of Constructed Strings in Malware. As always, you can download these scripts at our Github page. We hope you find all these scripts as useful as we do. Motivation During my summer internship with the FLARE team, my goal was to develop IDAPython plug-ins that speed up the reverse engineering workflow in IDA Pro. While analyzing malware samples with the team, I realized that a lot of time is spent looking up |
Malware Tool | ★★★ |
To see everything:
Our RSS (filtrered)
