What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2022-08-29 21:06:12 | Microsoft 365 Business Users Targeted With New DocuSign Phishing Scam (lien direct) | According IT Pro, a new business email compromise (BEC) campaign has been targeting Microsoft 365 organizations in a bid to hack corporate executives' accounts and maliciously divert business payments. Researchers from cyber security firm Mitiga found that the hackers are leveraging inherent weaknesses in 365's multi-factor authentication (MFA), Microsoft Authenticator, as well as Microsoft 365 Identity […] | Hack | |||
| 2022-08-29 15:25:45 | Twilio breach let attackers access Authy two-factor accounts of 93 users (lien direct) | >Threat actors behind the Twilio hack also gained access to the accounts of 93 individual users of its Authy two-factor authentication (2FA) service. Early August, the communications company Twilio discloses a data breach, threat actors had access to the data of some of its customers. The attackers accessed company systems using employee credentials obtained through […] | Hack Threat | |||
| 2022-08-28 13:15:05 | (Déjà vu) Okta one-time MFA passcodes exposed in Twilio cyberattack (lien direct) | The threat actor behind the Twilio hack used their access to steal one-time passwords (OTPs) delivered over SMS to from customers of Okta identity and access management company. [...] | Hack Threat | |||
| 2022-08-28 13:15:05 | Twilio breach let hackers see Okta\'s one-time MFA passwords (lien direct) | The threat actor behind the Twilio hack used their access to steal one-time passwords (OTPs) delivered over SMS to from customers of Okta identity and access management company. [...] | Hack Threat | |||
| 2022-08-27 16:14:51 | Twilio hackers also breached the food delivery firm DoorDash (lien direct) | >Twilio hackers also compromised the food delivery firm DoorDash, the attackers had access to company data, including customer and employee info. On-demand food delivery service DoorDash disclosed a data breach, the threat actors behind the Twilio hack gained access to the company’s data. DoorDash declared that malicious hackers stole credentials from employees of a third-party vendor, then […] | Hack Threat | |||
| 2022-08-26 19:54:39 | The number of companies caught up in the Twilio hack keeps growing (lien direct) | 2FA provider Authy, password manager LastPass, and DoorDash all experienced breaches. | Hack | LastPass | ||
| 2022-08-26 15:30:34 | DoorDash discloses new data breach tied to Twilio hack (lien direct) | Food delivery firm DoorDash has disclosed a data breach exposing customer and employee data that is linked to the recent cyberattack on Twilio. [...] | Data Breach Hack | |||
| 2022-08-26 14:40:34 | DoorDash Data Compromised Following Twilio Hack (lien direct) | Food delivery company DoorDash revealed on Thursday that customer and employee data has been exposed as a result of a recent breach at a third-party vendor. DoorDash said hackers abused a third-party vendor's access to its systems. The attacker abused DoorDash's internal tools and gained access to the information of 'a small percentage of individuals'. | Hack | ★★★★★ | ||
| 2022-08-24 14:56:27 | Plex Confirms Database Breach, Data Theft (lien direct) | Popular streaming media platform Plex is scrambling to reset user passwords after a database hack that included the theft of emails, usernames, and encrypted passwords. | Hack | |||
| 2022-08-24 12:02:07 | CVE-2021-1782, an iOS in-the-wild vulnerability in vouchers (lien direct) | Posted by Ian Beer, Google Project Zero This blog post is my analysis of a vulnerability exploited in the wild and patched in early 2021. Like the writeup published last week looking at an ASN.1 parser bug, this blog post is based on the notes I took as I was analyzing the patch and trying to understand the XNU vouchers subsystem. I hope that this writeup serves as the missing documentation for how some of the internals of the voucher subsystem works and its quirks which lead to this vulnerability. CVE-2021-1782 was fixed in iOS 14.4, as noted by @s1guza on twitter: 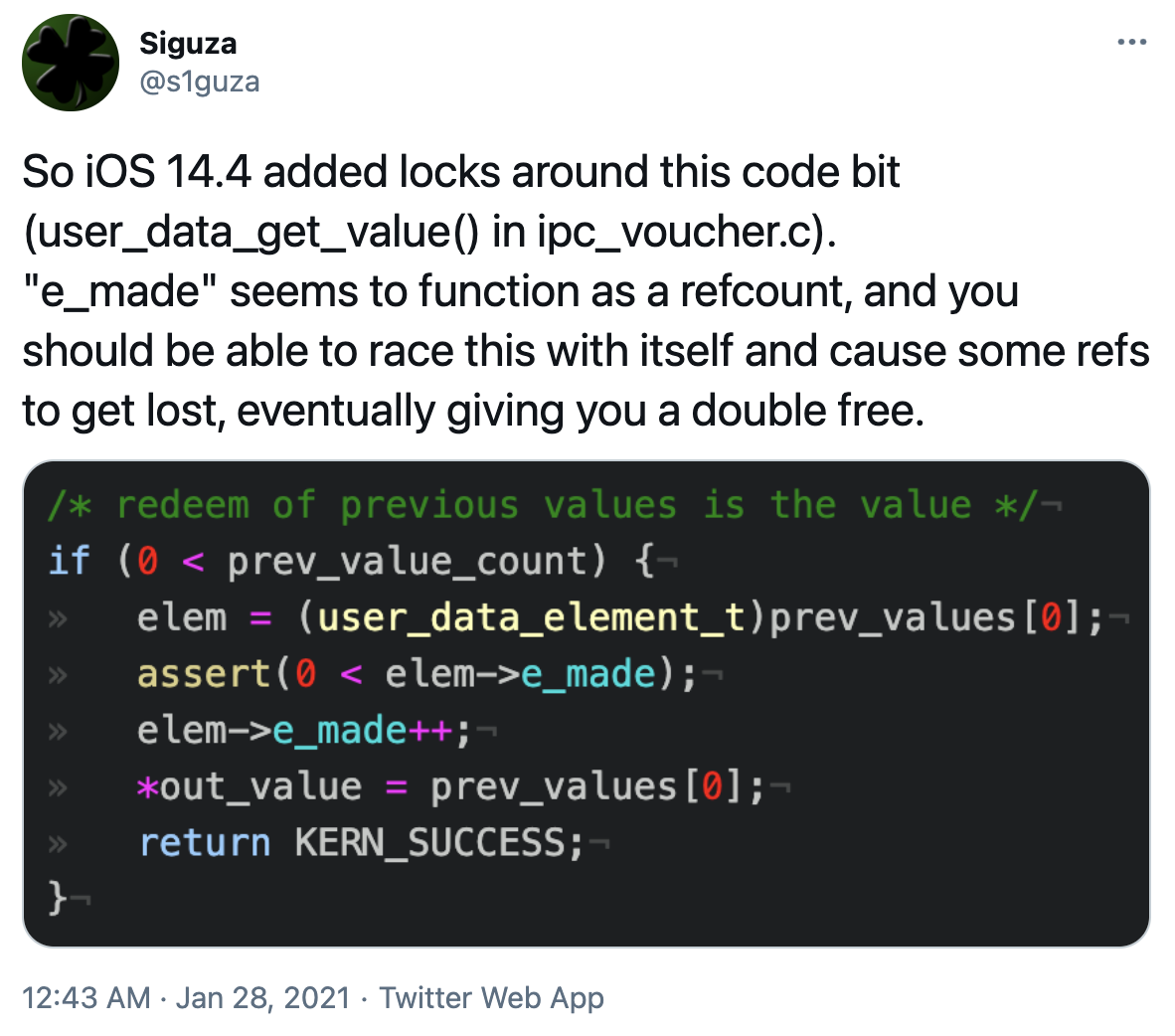 This vulnerability was fixed on January 26th 2021, and Apple updated the iOS 14.4 release notes on May 28th 2021 to indicate that the issue may have been actively exploited: This vulnerability was fixed on January 26th 2021, and Apple updated the iOS 14.4 release notes on May 28th 2021 to indicate that the issue may have been actively exploited: |
Hack Tool Vulnerability Guideline | ★★★ | ||
| 2022-08-24 11:53:36 | Hackers use AiTM attack to monitor Microsoft 365 accounts for BEC scams (lien direct) | A new business email compromise (BEC) campaign has been discovered combining sophisticated spear-phishing with Adversary-in-The-Middle (AiTM) tactics to hack corporate executives' Microsoft 365 accounts, even those protected by MFA. [...] | Hack | |||
| 2022-08-23 14:15:00 | Counterfeit Android Devices Revealed to Contain Backdoor Designed to Hack WhatsApp (lien direct) | At least four different smartphones affected: 'P48pro', 'radmi note 8', 'Note30u' and 'Mate40' | Hack | ★★★★ | ||
| 2022-08-23 13:30:00 | CyberheistNews Vol 12 #34 [Eye Opener] The Cisco Hack Was Caused by Initial Access Broker Phishing (lien direct) |

|
Hack | |||
| 2022-08-23 11:30:40 | Signal Phone Numbers Exposed in Twilio Hack (lien direct) | Twilio was hacked earlier this month, and the phone numbers of 1,900 Signal users were exposed: Here’s what our users need to know: All users can rest assured that their message history, contact lists, profile information, whom they’d blocked, and other personal data remain private and secure and were not affected. For about 1,900 users, an attacker could have attempted to re-register their number to another device or learned that their number was registered to Signal. This attack has since been shut down by Twilio. 1,900 users is a very small percentage of Signal’s total users, meaning that most were not affected... | Hack | |||
| 2022-08-23 11:12:43 | (Déjà vu) Counterfeit Phones Found to Contain Backdoor to Hack WhatsApp (lien direct) | Budget Android device models that are counterfeit versions associated with popular smartphone brands contain multiple hidden trojans designed to target WhatsApp and WhatsApp Business messaging app. Doctor Web first came across the malware in July 2022. It was discovered in the system partition of at least four different smartphones: radmi note 8, P48pro, Note30u, and […] | Malware Hack | |||
| 2022-08-23 00:02:06 | Lockbit leak sites hit by mysterious DDoS attack after Entrust hack (lien direct) | >LockBit ransomware gang claims to have hacked the IT giant Entrust and started leaking the stolen files. Entrust Corp., provides software and hardware used to issue financial cards, e-passport production, user authentication for those looking to access secure networks or conduct financial transactions, trust certificated for websites, mobile credentials, and connected devices. The Lockbit ransomware […] | Ransomware Hack | |||
| 2022-08-22 07:28:00 | Researchers Find Counterfeit Phones with Backdoor to Hack WhatsApp Accounts (lien direct) | Budget Android device models that are counterfeit versions associated with popular smartphone brands are harboring multiple trojans designed to target WhatsApp and WhatsApp Business messaging apps. The trojans, which Doctor Web first came across in July 2022, were discovered in the system partition of at least four different smartphones: P48pro, radmi note 8, Note30u, and Mate40, was "These | Hack | |||
| 2022-08-20 13:00:00 | Janet Jackson\'s \'Rhythm Nation\' Can Crash Old Hard Drives (lien direct) | Plus: The Twilio hack snags a reporter, a new tool to check for spyware, and the Canadian weed pipeline gets hit by a cyberattack. | Hack Tool | |||
| 2022-08-19 11:10:55 | Russian APT29 hackers abuse Azure services to hack Microsoft 365 users (lien direct) | The state-backed Russian cyberespionage group Cozy Bear has been particularly prolific in 2022, targeting Microsoft 365 accounts in NATO countries and attempting to access foreign policy information. [...] | Hack | APT 29 | ||
| 2022-08-18 21:37:53 | Encrypted Messaging Service Hack Exposes Phone Numbers (lien direct) | > Many people opt for encrypted messaging services because they like the additional layers of privacy they offer. They allow users...
Many people opt for encrypted messaging services because they like the additional layers of privacy they offer. They allow users...
|
Hack | |||
| 2022-08-18 15:49:45 | Apple releases Safari 15.6.1 to fix zero-day bug used in attacks (lien direct) | Apple has released Safari 15.6.1 for macOS Big Sur and Catalina to fix a zero-day vulnerability exploited in the wild to hack Macs. [...] | Hack Vulnerability | |||
| 2022-08-18 12:00:00 | How a Hacked Tractor Added Fuel to the Right-to-Repair Movement (lien direct) | This week, we discuss the latest John Deere tractor hack and its broader implications for repair rights advocates. | Hack | |||
| 2022-08-18 10:00:00 | (Déjà vu) Urgent update for macOS and iOS! Two actively exploited zero-days fixed (lien direct) | >Categories: Exploits and vulnerabilitiesCategories: NewsTags: macOS Tags: iOS Tags: CVE-2022-32894 Tags: CVE-2022-32893 Tags: kernel privileges Tags: WebKit Tags: actively exploited Tags: watering hole Tags: exploit kit Apple has released emergency security updates to fix two zero-day vulnerabilities previously exploited by attackers to hack iPhones, iPads, or Macs. (Read more...) | Hack | |||
| 2022-08-17 18:35:26 | Apple security updates fix 2 zero-days used to hack iPhones, Macs (lien direct) | Apple has released emergency security updates today to fix two zero-day vulnerabilities previously exploited by attackers to hack iPhones, iPads, or Macs. [...] | Hack | |||
| 2022-08-17 09:33:15 | (Déjà vu) Job Seekers Targeted in Lazarus Group Hack (lien direct) | The North Korea state-backed Lazarus Group has been observed to be targeting job seekers with malware capable of executing on Apple Macs with Intel and M1 chipsets. ESET, a Slovak cybersecurity firm, linked these events to a campaign dubbed “Operation In(ter)ception” that was first disclosed in June 2020 and involved using social engineering tactics to […] | Malware Hack Medical | APT 38 | ||
| 2022-08-16 14:15:00 | New Attack Weaponizes PLCs to Hack Enterprise and OT Networks (lien direct) | The research resulted in proof-of-concept exploits against seven market-leading automation firms | Hack Guideline | |||
| 2022-08-16 13:53:13 | Ransomware Group Claims Access to SCADA in Confusing UK Water Company Hack (lien direct) | A ransomware group has hit at least one water company in the United Kingdom, but there is some confusion over whose systems were actually breached. | Ransomware Hack | |||
| 2022-08-16 13:34:25 | (Déjà vu) CyberheistNews Vol 12 #33 [Eye Opener] Recent Cisco Hack by Ransomware Group Started Because of a Phishing Attack (lien direct) |

|
Ransomware Hack | |||
| 2022-08-16 13:30:00 | #DEFCON: How US Teen RickRolled His High School District (lien direct) | American teenager explains how he was able to hack his local high school district | Hack | |||
| 2022-08-16 11:30:27 | Il a hacké un tracteur John Deere… et a installé Doom (lien direct) | > Au delà du jeu vidéo, ce hack permettrait aux utilisateurs de regagner le contrôle des équipements agricoles qu'ils possèdent et de ne plus être obligés de passer par un concessionnaire pour les mises à jour.
L'article Il a hacké un tracteur John Deere… et a installé Doom est à retrouver sur 01net.com.
Au delà du jeu vidéo, ce hack permettrait aux utilisateurs de regagner le contrôle des équipements agricoles qu'ils possèdent et de ne plus être obligés de passer par un concessionnaire pour les mises à jour.
L'article Il a hacké un tracteur John Deere… et a installé Doom est à retrouver sur 01net.com. |
Hack | |||
| 2022-08-16 11:09:42 | Signal Discloses Impact From Twilio Hack (lien direct) | Secure communications services provider Signal on Monday disclosed impact from the recent Twilio hack, after threat actors attempted to re-register the phone numbers of some of its users to new devices. | Hack Threat | |||
| 2022-08-15 22:42:11 | Nearly 1,900 Signal Messenger Accounts Potentially Compromised in Twilio Hack (lien direct) | Popular end-to-end encrypted messaging service Signal on Monday disclosed the cyberattack aimed at Twilio earlier this month may have exposed the phone numbers of roughly 1,900 users. "For about 1,900 users, an attacker could have attempted to re-register their number to another device or learned that their number was registered to Signal," the company said. "All users can rest assured that | Hack | |||
| 2022-08-15 17:46:24 | Twilio hack exposed Signal phone numbers of 1,900 users (lien direct) | Phone numbers of close to 1,900 Signal users were exposed in the data breach Twilio cloud communications company suffered at the beginning of the month. [...] | Data Breach Hack | |||
| 2022-08-15 10:46:06 | Weaponized PLCs Can Hack Engineering Workstations in Attacks on Industrial Orgs (lien direct) | Researchers have shown how hackers could weaponize programmable logic controllers (PLCs) and use them to exploit engineering workstations running software from several major industrial automation companies. | Hack | |||
| 2022-08-12 10:43:09 | Zero-Day Vulnerability Exploited to Hack Over 1,000 Zimbra Email Servers (lien direct) | A new zero-day vulnerability affecting Zimbra has been exploited to hack more than 1,000 enterprise email servers, according to incident response firm Volexity. | Hack Vulnerability | |||
| 2022-08-12 08:00:43 | Experts warn of mass exploitation of an RCE flaw in Zimbra Collaboration Suite (lien direct) | >Threat actors are exploiting an authentication bypass Zimbra flaw, tracked as CVE-2022-27925, to hack Zimbra Collaboration Suite email servers worldwide. An authentication bypass affecting Zimbra Collaboration Suite, tracked as CVE-2022-27925, is actively exploited to hack ZCS email servers worldwide. Zimbra is an email and collaboration platform used by more than 200,000 businesses from over 140 countries. Yesterday, August 11, CISA has […] | Hack | |||
| 2022-08-11 12:59:06 | Recent Cisco Hack by Ransomware Group Started Because of a Phishing Attack (lien direct) |

|
Ransomware Hack | |||
| 2022-08-11 03:53:00 | Cisco admits hack on IT network, links attacker to LAPSUS$ threat group (lien direct) | IT, networking, and cybersecurity solutions giant Cisco has admitted suffering a security incident targeting its corporate IT infrastructure in late May 2022. On August 10, the firm stated that an employee's credentials were compromised after an attacker gained control of a personal Google account where credentials saved in the victim's browser were being synchronized. Bad actors published a list of files from this security incident to the dark web, Cisco added.“The incident was contained to the corporate IT environment and Cisco did not identify any impact to any Cisco products or services, sensitive customer data or employee information, Cisco intellectual property, or supply chain operations,” the company said. Cisco claimed it took immediate action to contain and eradicate the bad actor, which it has linked to notorious threat group LAPSUS$. It also said that it has taken the decision to publicly announce the incident now as it was previously actively collecting information about the bad actor to help protect the security community.To read this article in full, please click here | Hack Threat | |||
| 2022-08-11 03:24:07 | What the Zola Hack Can Teach Us About Password Security (lien direct) | Password security is only as strong as the password itself. Unfortunately, we are often reminded of the danger of weak, reused, and compromised passwords with major cybersecurity breaches that start with stolen credentials. For example, in May 2022, the popular wedding planning site, Zola, was the victim of a significant cybersecurity breach where hackers used an attack known as credential | Hack | |||
| 2022-08-10 16:05:00 | Cyber-criminals Shift From Macros to Shortcut Files to Hack Business PCs, HP Report (lien direct) | The report shows an 11% rise in archive files containing malware, including LNK files | Hack | ★★ | ||
| 2022-08-10 12:00:24 | Making Linux Kernel Exploit Cooking Harder (lien direct) | Posted by Eduardo Vela, Exploit Critic |
Hack | Uber | ||
| 2022-08-08 16:28:03 | Twilio, a texting platform popular with political campaigns, reports breach (lien direct) | >The company says it became aware of the hack on Aug. 4 but it declined to say how many customers were affected by the incident. | Hack | |||
| 2022-08-08 13:49:02 | How You Can Hack Your Senses to Work Better (lien direct) | Cybersecurity has never been a low-stress field. The industry attracts dedicated, highly-skilled perfectionists who are all too willing to shoulder the burden of a company's cybersecurity without complaint. Yet, increased threats of ransomware and cyberattacks are creating an anxiety filled workplace. The current technological skills gap means there is frequently too much work for too […] | Ransomware Hack | |||
| 2022-08-08 07:00:00 | KMSpico explained: No, KMS is not "kill Microsoft" (lien direct) | >Categories: ExplainedA hack tool called KMSPico is hailed as the go-to tool when it comes to activiating Windows. But is it safe? (Read more...) | Hack Tool | |||
| 2022-08-05 21:30:37 | (Déjà vu) Cyberattack on Albanian government suggests new Iranian aggression (lien direct) | Tehran-linked hack of a NATO member is a significant escalation. | Hack | |||
| 2022-08-05 14:20:00 | (Déjà vu) How To Hack Web Applications in 2022: Part 2 (lien direct) | Tehran-linked hack of a NATO member is a significant escalation. | Hack | |||
| 2022-08-04 21:30:27 | An Attack on Albanian Government Suggests New Iranian Aggression (lien direct) | A Tehran-linked hack of a NATO member marks a significant escalation against the backdrop of US-Iran nuclear talks. | Hack | |||
| 2022-08-04 08:00:13 | Attackers leveraging Dark Utilities "C2aaS" platform in malware campaigns (lien direct) |  By Edmund Brumaghin, Azim Khodjibaev and Matt Thaxton, with contributions from Arnaud Zobec.Executive SummaryDark Utilities, released in early 2022, is a platform that provides full-featured C2 capabilities to adversaries.It is marketed as a means to enable remote access, command execution, distributed denial-of-service (DDoS) attacks and cryptocurrency mining operations on infected systems.Payloads provided by the platform support Windows, Linux and Python-based implementations and are hosted within the Interplanetary File System (IPFS), making them resilient to content moderation or law enforcement intervention.Since its initial release, we've observed malware samples in the wild leveraging it to facilitate remote access and cryptocurrency mining.What is "Dark Utilities?"In early 2022, a new C2 platform called "Dark Utilities" was established, offering a variety of services such as remote system access, DDoS capabilities and cryptocurrency mining. The operators of the service also established Discord and Telegram communities where they provide technical support and assistance for customers on the platform. By Edmund Brumaghin, Azim Khodjibaev and Matt Thaxton, with contributions from Arnaud Zobec.Executive SummaryDark Utilities, released in early 2022, is a platform that provides full-featured C2 capabilities to adversaries.It is marketed as a means to enable remote access, command execution, distributed denial-of-service (DDoS) attacks and cryptocurrency mining operations on infected systems.Payloads provided by the platform support Windows, Linux and Python-based implementations and are hosted within the Interplanetary File System (IPFS), making them resilient to content moderation or law enforcement intervention.Since its initial release, we've observed malware samples in the wild leveraging it to facilitate remote access and cryptocurrency mining.What is "Dark Utilities?"In early 2022, a new C2 platform called "Dark Utilities" was established, offering a variety of services such as remote system access, DDoS capabilities and cryptocurrency mining. The operators of the service also established Discord and Telegram communities where they provide technical support and assistance for customers on the platform.  Dark Utilities provides payloads consisting of code that is executed on victim systems, allowing them to be registered with the service and establish a command and control (C2) communications channel. The platform currently supports Windows, Linux and Python-based payloads, allowing adversaries to target multiple architectures without requiring significant development resources. During our analysis, we observed efforts underway to expand OS and system architecture support as the platform continues to see ongoing develo Dark Utilities provides payloads consisting of code that is executed on victim systems, allowing them to be registered with the service and establish a command and control (C2) communications channel. The platform currently supports Windows, Linux and Python-based payloads, allowing adversaries to target multiple architectures without requiring significant development resources. During our analysis, we observed efforts underway to expand OS and system architecture support as the platform continues to see ongoing develo |
Spam Malware Hack Tool Threat Guideline | APT 19 | ||
| 2022-08-03 13:51:03 | Analyse de Chainalysis concernant le hack de Nomad Bridge (lien direct) | À la suite du récent hack de Nomad, voici une analyse de Chainalysis, la plateforme des données des blockchains. Selon Chainalysis, le bridge cross-chain Nomad, qui permet de connecter deux blockchains entre elles, a perdu plus de 2 milliards de dollars en cryptomonnaies au cours des 13 piratages subis depuis début 2022. Chainalysis revient en détail sur les protocoles des bridges cross-chain, expose leurs vulnérabilités et recommande des actions que l'industrie peut entreprendre afin d'assurer (...) - Malwares | Hack | |||
| 2022-08-03 13:26:39 | Solana hack wipes more than 7,000 wallets, totaling nearly $5 million in losses (lien direct) | >The apparent software-based attack stands out among other major cryptocurrency hacks that have totaled nearly $2 billion so far in 2022. | Hack |
To see everything:
Our RSS (filtrered)
