What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2022-12-08 05:00:00 | New \'Zombinder\' platform binds Android malware with legitimate apps (lien direct) | A darknet platform dubbed 'Zombinder' allows threat actors to bind malware to legitimate Android apps, causing victims to infect themselves while still having the full functionality of the original app to evade suspicion. [...] | Malware Threat | ★★★ | ||
| 2022-12-08 02:10:30 | (Déjà vu) ASEC Weekly Malware Statistics (November 28th, 2022 – December 4th, 2022) (lien direct) | The ASEC analysis team uses the ASEC automatic analysis system RAPIT to categorize and respond to known malware. This post will list weekly statistics collected from November 28th, 2022 (Monday) to December 4th, 2022 (Sunday). For the main category, Infostealer ranked top with 34.8%, followed by downloader with 28.2%, backdoor with 21.1%, ransomware with 14.6%, and CoinMiner with 0.3%. Top 1 – SmokeLoader SmokeLoader is an infostealer/downloader malware that is distributed via exploit kits. This week, it ranked first place with... | Ransomware Malware | ★★ | ||
| 2022-12-07 15:44:32 | Archives Overtake Office Documents as the Most Popular File Type to Deliver Malware (lien direct) |

|
Malware | ★★★ | ||
| 2022-12-07 14:19:32 | New Zerobot malware has 21 exploits for BIG-IP, Zyxel, D-Link devices (lien direct) | A new Go-based malware named 'Zerobot' has been spotted in mid-November using exploits for almost two dozen vulnerabilities in a variety of devices that include F5 BIG-IP, Zyxel firewalls, Totolink and D-Link routers, and Hikvision cameras. [...] | Malware | ★★ | ||
| 2022-12-07 01:41:18 | Malware Distributed with Disguised Filenames (RIGHT-TO-LEFT OVERRIDE) (lien direct) | In August, the ASEC analysis team made a post on the malware being distributed with filenames that utilize RTLO (Right-To-Left Override). RTLO is a unicode that makes an override from right to left. This type of malware induces users to execute its files by mixing filenames with extensions, with its distribution still being continued to this day. RAT Tool Disguised as Solution File (*.sln) Being Distributed on Github As of November 30th, 2022, when the keywords based on the last... | Malware Tool | ★★★ | ||
| 2022-12-07 01:18:35 | \'Resume.xll\' File Being Distributed in Korea (LockBit 2.0) (lien direct) | In mid-2022, the ASEC analysis team shared that malware with the XLL file format (file extension: .xll) was being distributed via email. The XLL file has a DLL form of a PE (Portable Executable) file but is executed with Microsoft Excel. Since then, this type of malware had not been distributed actively, but for the first time in a long while, we found that it was being distributed with the filename, ‘Resume.xll‘. Post from May 20th, 2022: XLL Malware Distributed... | Malware | ★★★ | ||
| 2022-12-06 18:08:00 | Darknet\'s Largest Mobile Malware Marketplace Threatens Users Worldwide (lien direct) | Cybersecurity researchers have shed light on a darknet marketplace called InTheBox that's designed to specifically cater to mobile malware operators. The actor behind the criminal storefront, believed to be available since at least January 2020, has been offering over 400 custom web injects grouped by geography that can be purchased by other adversaries looking to mount attacks of their own. " | Malware | ★★★ | ||
| 2022-12-06 17:09:00 | Anomali Cyber Watch: Infected Websites Show Different Headers Depending on Search Engine Fingerprinting, 10 Android Platform Certificates Abused in the Wild, Phishing Group Impersonated Major UAE Oil (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, China, In-memory evasion, Infostealers, North Korea, Phishing, Ransomware, Search engine optimization, and Signed malware. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Chinese Gambling Spam Targets World Cup Keywords
(published: December 2, 2022)
Since 2018, a large-scale website infection campaign was affecting up to over 100,000 sites at a given moment. Infected websites, mostly oriented at audiences in China, were modified with additional scripts. Compromised websites were made to redirect users to Chinese gambling sites. Title and Meta tags on the compromised websites were changed to display keywords that the attackers had chosen to abuse search engine optimization (SEO). At the same time, additional scripts were switching the page titles back to the original if the visitor fingerprinting did not show a Chinese search engine from a preset list (such as Baidu).
Analyst Comment: Website owners should keep their systems updated, use unique strong passwords and introduce MFA for all privileged or internet facing resources, and employ server-side scanning to detect unauthorized malicious content. Implement secure storage for website backups.
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] Obfuscated Files or Information - T1027
Tags: SEO hack, HTML entities, Black hat SEO, Fraudulent redirects, Visitor fingerprinting, Gambling, Sports betting, World Cup, China, target-country:CN, JavaScript, Baidu, baiduspider, Sogou, 360spider, Yisou
Leaked Android Platform Certificates Create Risks for Users
(published: December 2, 2022)
On November 30, 2022, Google reported 10 different Android platform certificates that were seen actively abused in the wild to sign malware. Rapid7 researchers found that the reported signed samples are adware, so it is possible that these platform certificates may have been widely available. It is not shared how these platform certificates could have been leaked.
Analyst Comment: Malware signed with a platform certificate can enjoy privileged execution with system permissions, including permissions to access user data. Developers should minimize the number of applications requiring a platform certificate signature.
Tags: Android, Google, Platform certificates, Signed malware, malware-type:Adware
Blowing Cobalt Strike Out of the Water With Memory Analysis
(published: December 2, 2022)
The Cobalt Strike attack framework remains difficult to detect as it works mostly in memory and doesn’t touch the disk much after the initial loader stage. Palo Alto researchers analyzed three types of Cobalt Strike loaders: KoboldLoader which loads an SMB beacon, MagnetLoader loading an HTTPS beacon, and LithiumLoader loading a stager beacon. These beacon samples do not execute in normal sandbox environments and utilize in-me
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Chinese Gambling Spam Targets World Cup Keywords
(published: December 2, 2022)
Since 2018, a large-scale website infection campaign was affecting up to over 100,000 sites at a given moment. Infected websites, mostly oriented at audiences in China, were modified with additional scripts. Compromised websites were made to redirect users to Chinese gambling sites. Title and Meta tags on the compromised websites were changed to display keywords that the attackers had chosen to abuse search engine optimization (SEO). At the same time, additional scripts were switching the page titles back to the original if the visitor fingerprinting did not show a Chinese search engine from a preset list (such as Baidu).
Analyst Comment: Website owners should keep their systems updated, use unique strong passwords and introduce MFA for all privileged or internet facing resources, and employ server-side scanning to detect unauthorized malicious content. Implement secure storage for website backups.
MITRE ATT&CK: [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] Obfuscated Files or Information - T1027
Tags: SEO hack, HTML entities, Black hat SEO, Fraudulent redirects, Visitor fingerprinting, Gambling, Sports betting, World Cup, China, target-country:CN, JavaScript, Baidu, baiduspider, Sogou, 360spider, Yisou
Leaked Android Platform Certificates Create Risks for Users
(published: December 2, 2022)
On November 30, 2022, Google reported 10 different Android platform certificates that were seen actively abused in the wild to sign malware. Rapid7 researchers found that the reported signed samples are adware, so it is possible that these platform certificates may have been widely available. It is not shared how these platform certificates could have been leaked.
Analyst Comment: Malware signed with a platform certificate can enjoy privileged execution with system permissions, including permissions to access user data. Developers should minimize the number of applications requiring a platform certificate signature.
Tags: Android, Google, Platform certificates, Signed malware, malware-type:Adware
Blowing Cobalt Strike Out of the Water With Memory Analysis
(published: December 2, 2022)
The Cobalt Strike attack framework remains difficult to detect as it works mostly in memory and doesn’t touch the disk much after the initial loader stage. Palo Alto researchers analyzed three types of Cobalt Strike loaders: KoboldLoader which loads an SMB beacon, MagnetLoader loading an HTTPS beacon, and LithiumLoader loading a stager beacon. These beacon samples do not execute in normal sandbox environments and utilize in-me |
Spam Malware Tool Threat Medical | APT 38 | ★★★ | |
| 2022-12-06 16:41:01 | ChatGPT shows promise of using AI to write malware (lien direct) | >Large language models pose a major cybersecurity risk, both from the vulnerabilities they risk introducing and the malware they could produce. | Malware | ChatGPT | ★★★★ | |
| 2022-12-06 15:30:10 | Want to detect Cobalt Strike on the network? Look to process memory (lien direct) | Security analysts have tools to spot hard-to-find threat, Unit 42 says Enterprise security pros can detect malware samples in environments that incorporate the highly evasive Cobalt Strike attack code by analyzing artifacts in process memory, according to researchers with Palo Alto Networks' Unit 42 threat intelligence unit.… | Malware Threat | ★★★ | ||
| 2022-12-06 12:04:33 | CryWiper Data Wiper Targeting Russian Sites (lien direct) | Kaspersky is reporting on a data wiper masquerading as ransomware that is targeting local Russian government networks. The Trojan corrupts any data that’s not vital for the functioning of the operating system. It doesn’t affect files with extensions .exe, .dll, .lnk, .sys or .msi, and ignores several system folders in the C:\Windows directory. The malware focuses on databases, archives, and user documents. So far, our experts have seen only pinpoint attacks on targets in the Russian Federation. However, as usual, no one can guarantee that the same code won’t be used against other targets... | Ransomware Malware | ★★★ | ||
| 2022-12-06 11:41:00 | Open Source Ransomware Toolkit Cryptonite Turns Into Accidental Wiper Malware (lien direct) | A version of an open source ransomware toolkit called Cryptonite has been observed in the wild with wiper capabilities due to its "weak architecture and programming." Cryptonite, unlike other ransomware strains, is not available for sale on the cybercriminal underground, and was instead offered for free by an actor named CYBERDEVILZ until recently through a GitHub repository. The source code and | Ransomware Malware | ★★★ | ||
| 2022-12-06 09:26:19 | Technical Analysis of the Winbox Payload in WindiGo (lien direct) | >WindiGo is a malware that exploits CVE-2018-14847 to gain access to MikroTik routers, which has been used in several campaigns by multiple actors. This blog provides a technical analysis of WindiGo as well as Indicators of Compromise (IoCs) you can use to detect WindiGo in your network. | Malware | ★★★ | ||
| 2022-12-06 08:28:00 | Flaws in MegaRAC baseband management firmware impact many server brands (lien direct) | Researchers have found three vulnerabilities in AMI MegaRAC, a baseband management controller (BMC) firmware used by multiple server manufacturers. If exploited, the flaws could allow attackers to remotely control servers, deploy malware and firmware implants, or trigger damaging actions that leave them inoperable.BMCs are microcontrollers present on server motherboards that have their own firmware, dedicated memory, power, and network ports and are used for out-of-band management of servers when their main operating systems are shut down. They are essentially small independent computers running inside bigger computers that allow administrators to remotely perform a variety of maintenance and diagnostic tasks including reinstalling operating systems, restarting servers when they're unresponsive, deploying firmware updates and more.To read this article in full, please click here | Malware | ★★★ | ||
| 2022-12-06 00:15:10 | CVE-2022-4173 (lien direct) | A vulnerability within the malware removal functionality of Avast and AVG Antivirus allowed an attacker with write access to the filesystem, to escalate his privileges in certain scenarios. The issue was fixed with Avast and AVG Antivirus version 22.10. | Malware Vulnerability | |||
| 2022-12-05 22:30:13 | Google warns stolen Android keys used to sign info-stealing malware (lien direct) | OEMs including Samsung, LG and Mediatek named and shamed Compromised Android platform certificate keys from device makers including Samsung, LG and Mediatek are being used to sign malware and deploy spyware, among other software nasties.… | Malware | ★★★ | ||
| 2022-12-05 17:54:00 | Russian Courts Targeted by New CryWiper Data Wiper Malware Posing as Ransomware (lien direct) | A new data wiper malware called CryWiper has been found targeting Russian government agencies, including mayor's offices and courts. "Although it disguises itself as a ransomware and extorts money from the victim for 'decrypting' data, [it] does not actually encrypt, but purposefully destroys data in the affected system," Kaspersky researchers Fedor Sinitsyn and Janis Zinchenko said in a | Ransomware Malware Medical | APT 38 | ★★★ | |
| 2022-12-05 17:11:57 | Newly Discovered Trojan Steals 300,000 Facebook Users Details In 4 Year-Long Campaign (lien direct) | It has been reported that a newly discovered Trojan has stolen Facebook logins from over 300,000 users in a campaign lasting four years, according to Zimperium. The security vendor claimed to have found the “Schoolyard Bully” malware hidden in several applications available on both Google Play and third-party app stores. | Malware | ★★ | ||
| 2022-12-05 16:00:00 | North Korean Hackers Spread AppleJeus Malware Disguised as Cryptocurrency Apps (lien direct) | The Lazarus Group threat actor has been observed leveraging fake cryptocurrency apps as a lure to deliver a previously undocumented version of the AppleJeus malware, according to new findings from Volexity. "This activity notably involves a campaign likely targeting cryptocurrency users and organizations with a variant of the AppleJeus malware by way of malicious Microsoft Office documents," | Malware Threat Medical | APT 38 | ★★★ | |
| 2022-12-05 15:00:00 | VM Flare: un flareytale ouvert au public FLARE VM: A FLAREytale Open to the Public (lien direct) |
Flare VM est une collection de scripts d'installations logicielles pour les systèmes Windows qui vous permet de configurer et de maintenir facilement un environnement d'ingénierie inverse sur une machine virtuelle (VM).Des milliers d'ingénieurs inverses, d'analystes de logiciels malveillants et de chercheurs en sécurité comptent sur des VM Flare pour configurer Windows et pour installer une collection d'experts d'outils de sécurité.
Nos mises à jour les plus récentes rendent la machine virtuelle Flare plus ouverte et maintenable.Cela permet à la communauté d'ajouter et de mettre à jour facilement les outils et de les rendre rapidement à la disposition de tous.Nous avons travaillé dur pour ouvrir les packages qui détaillent comment installer
FLARE VM is a collection of software installations scripts for Windows systems that allows you to easily setup and maintain a reverse engineering environment on a virtual machine (VM). Thousands of reverse engineers, malware analysts, and security researchers rely on FLARE VM to configure Windows and to install an expert collection of security tools. Our most recent updates make FLARE VM more open and maintainable. This allows the community to easily add and update tools and to make them quickly available to everyone. We\'ve worked hard to open source the packages which detail how to install |
Malware Tool | ★★★ | ||
| 2022-12-05 13:42:01 | Android : téléchargées 2 millions de fois sur le Play Store ces applications cachaient des malwares (lien direct) |  Une dizaine d'applications disponibles au téléchargement sur le Google Play Store embarquaient en réalité des malwares. Elles ont été installées plus de 2 millions de fois. Une dizaine d'applications disponibles au téléchargement sur le Google Play Store embarquaient en réalité des malwares. Elles ont été installées plus de 2 millions de fois. |
Malware | ★★ | ||
| 2022-12-05 13:03:18 | Enhanced Protection - The strongest level of Safe Browsing protection Google Chrome has to offer (lien direct) | Posted by Benjamin Ackerman (Chrome Security and Jonathan Li (Safe Browsing) As a follow-up to a previous blog post about How Hash-Based Safe Browsing Works in Google Chrome, we wanted to provide more details about Safe Browsing's Enhanced Protection mode in Chrome. Specifically, how it came about, the protections that are offered and what it means for your data. Security and privacy have always been top of mind for Chrome. Our goal is to make security effortless for you while browsing the web, so that you can go about your day without having to worry about the links that you click on or the files that you download. This is why Safe Browsing's phishing and malware protections have been a core part of Chrome since 2007. You may have seen these in action if you have ever come across one of our red warning pages. 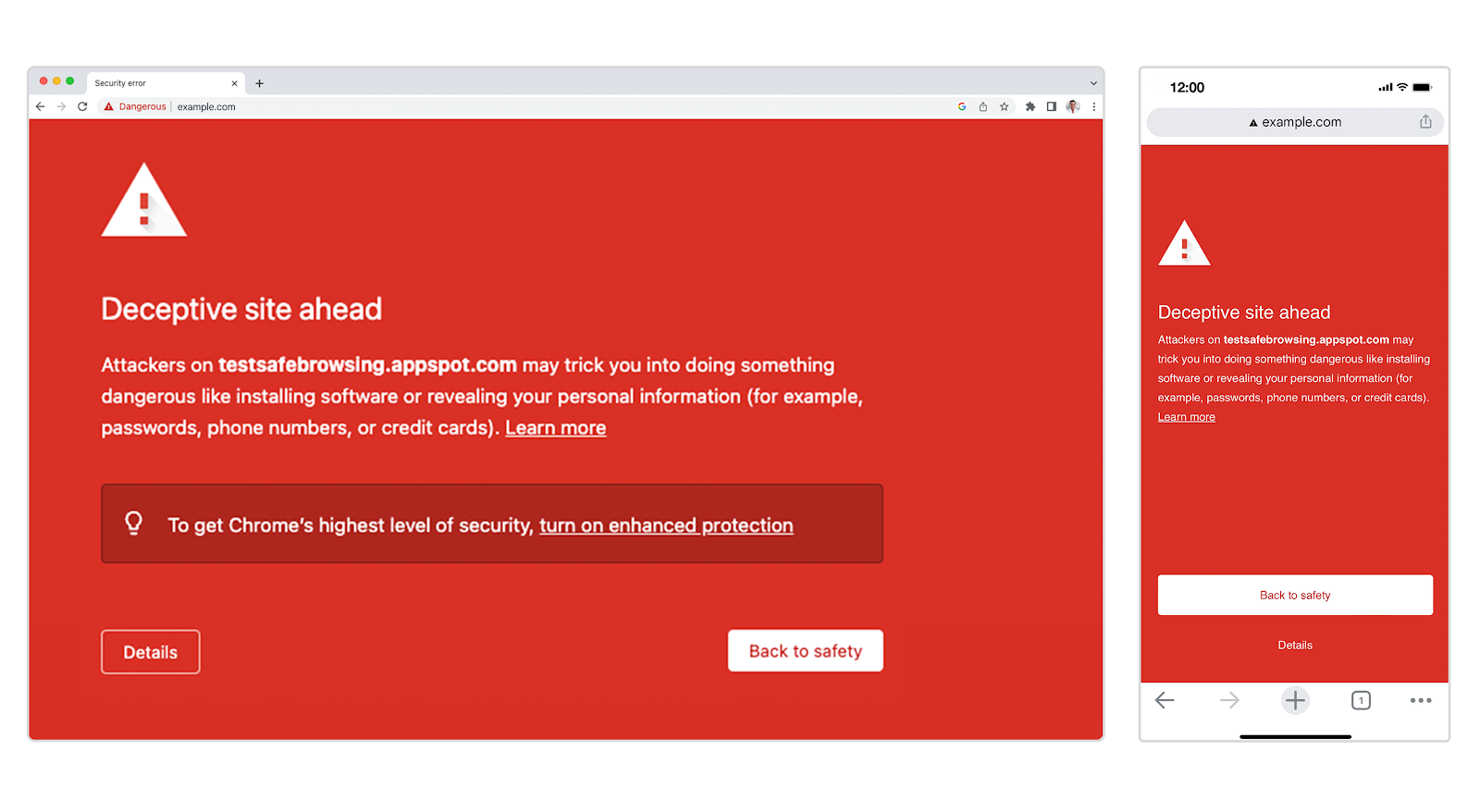 We show these warnings whenever we believe a site that you are trying to visit or file that you are trying to download might put you at risk for an attack. To give you a better understanding of how the Enhanced Protection mode in Safe Browsing provides the strongest level of defense it's useful to know what is offered in Standard Protection. Standard Protection Enabled by default in Chrome, Standard Protection was designed to be privacy preserving at its core by using hash-based checks. This has been effective at protecting users by warning millions of users about dangerous websites. However, hash-based checks are inherently limited as they rely on lookups to a list of known bad sites. We see malicious actors moving fast and constantly evolving their tactics to avoid detection using sophisticated techniques. To counter this, we created a stronger and more customized level of protection that we could offer to users. To this end, we launched Enhanced Protection in 2020, which builds upon the Standard Protection mode in Safe Browsing to keep you safer. Enhanced Protection This is the fastest and strongest level of protection against dangerous sites and downloads that Safe Browsing offers in Chrome. It enables more advanced detection techniques that adapt quickly as malicious activity evolves. As a result, Enhanced Protection users are phished 20-35% less than users on Standard Protection. A few of these features include: Real time URL checks: By checking with Google Safe Browsing's servers in real time before navigating to an uncommon site you're visiting, Chrome provides the best protection against dangerous sites and uses advanced machine learning models to continuously stay up to date. File checks before downloading: In addition to Chrome's standard checks of downloaded files, Enhanced Protection users can choose to upload suspicious files to be scanned by Google Safe Browsing's full suite of malware detection technology before opening the file. This helps catch brand new malware that Safe Browsing has not scanned bef We show these warnings whenever we believe a site that you are trying to visit or file that you are trying to download might put you at risk for an attack. To give you a better understanding of how the Enhanced Protection mode in Safe Browsing provides the strongest level of defense it's useful to know what is offered in Standard Protection. Standard Protection Enabled by default in Chrome, Standard Protection was designed to be privacy preserving at its core by using hash-based checks. This has been effective at protecting users by warning millions of users about dangerous websites. However, hash-based checks are inherently limited as they rely on lookups to a list of known bad sites. We see malicious actors moving fast and constantly evolving their tactics to avoid detection using sophisticated techniques. To counter this, we created a stronger and more customized level of protection that we could offer to users. To this end, we launched Enhanced Protection in 2020, which builds upon the Standard Protection mode in Safe Browsing to keep you safer. Enhanced Protection This is the fastest and strongest level of protection against dangerous sites and downloads that Safe Browsing offers in Chrome. It enables more advanced detection techniques that adapt quickly as malicious activity evolves. As a result, Enhanced Protection users are phished 20-35% less than users on Standard Protection. A few of these features include: Real time URL checks: By checking with Google Safe Browsing's servers in real time before navigating to an uncommon site you're visiting, Chrome provides the best protection against dangerous sites and uses advanced machine learning models to continuously stay up to date. File checks before downloading: In addition to Chrome's standard checks of downloaded files, Enhanced Protection users can choose to upload suspicious files to be scanned by Google Safe Browsing's full suite of malware detection technology before opening the file. This helps catch brand new malware that Safe Browsing has not scanned bef |
Malware | ★★★ | ||
| 2022-12-04 10:11:22 | Android malware apps with 2 million installs spotted on Google Play (lien direct) | A new set of Android malware, phishing, and adware apps have infiltrated the Google Play store, tricking over two million people into installing them. [...] | Malware Mobile | ★★★ | ||
| 2022-12-03 10:12:06 | Hackers use new, fake crypto app to breach networks, steal cryptocurrency (lien direct) | The North Korean 'Lazarus' hacking group is linked to a new attack spreading fake cryptocurrency apps under the made-up brand, "BloxHolder," to install the AppleJeus malware for initial access to networks and steal crypto assets. [...] | Malware | APT 38 | ★★★ | |
| 2022-12-02 21:13:04 | Samsung\'s Android app-signing key has leaked, is being used to sign malware (lien direct) | The cryptographic key proves an update is legit, assuming your OEM doesn't lose it. | Malware | ★★★ | ||
| 2022-12-02 19:19:31 | Android Phone Makers\' Encryption Keys Stolen and Used in Malware (lien direct) | Device manufacturers use “platform certificates” to verify an app's authenticity, making them particularly dangerous in the wrong hands. | Malware | ★★ | ||
| 2022-12-02 16:00:00 | Hackers Use Archive Files and HTML Smuggling to Bypass Detection Tools (lien direct) | HP's latest report suggests 44% of malware was delivered via archive files in Q3 2022 | Malware | ★★★ | ||
| 2022-12-02 12:29:48 | New CryWiper malware wipes data in attack against Russian org (lien direct) | A previously undocumented data wiper named CryWiper is masquerading as ransomware, extorting victims to pay for a decrypter, but in reality, it just destroys data beyond recovery. [...] | Malware | ★★★ | ||
| 2022-12-02 12:00:49 | Les smartphones de Samsung et LG sont menacés par des malwares à cause d\'une fuite de certificats (lien direct) |  La fuite de plusieurs certificats de plate-forme Android appartenant à LG, Samsung et MediaTek peut permettre à des pirates de signer des applications malveillantes pour qu'elles soient acceptées par le système et disposent de privilèges élevés. La fuite de plusieurs certificats de plate-forme Android appartenant à LG, Samsung et MediaTek peut permettre à des pirates de signer des applications malveillantes pour qu'elles soient acceptées par le système et disposent de privilèges élevés. |
Malware | ★★★ | ||
| 2022-12-02 09:30:51 | Mozilla, Microsoft drop TrustCor as root certificate authority (lien direct) | 'There is no evidence to suggest that TrustCor violated conduct, policy, or procedure' says biz Mozilla and Microsoft have taken action against a certificate authority accused of having close ties to a US military contractor that allegedly paid software developers to embed data-harvesting malware in mobile apps.… | Malware | ★★★★★ | ||
| 2022-12-02 08:56:00 | Hackers Sign Android Malware Apps with Compromised Platform Certificates (lien direct) | Platform certificates used by Android smartphone vendors like Samsung, LG, and MediaTek have been found to be abused to sign malicious apps. The findings were first discovered and reported by Google reverse engineer Łukasz Siewierski on Thursday. "A platform certificate is the application signing certificate used to sign the 'android' application on the system image," a report filed through the | Malware | ★★ | ||
| 2022-12-02 06:09:00 | Hackers Exploiting Redis Vulnerability to Deploy New Redigo Malware on Servers (lien direct) | A previously undocumented Go-based malware is targeting Redis servers with the goal of taking control of the infected systems and likely building a botnet network. The attacks involve taking advantage of a critical security vulnerability in the open source, in-memory, key-value store that was disclosed earlier this year to deploy Redigo, according to cloud security firm Aqua. | Malware Vulnerability | ★★ | ||
| 2022-12-02 00:54:11 | (Déjà vu) ASEC Weekly Malware Statistics (November 21st, 2022 – November 27th, 2022) (lien direct) | The ASEC analysis team is using the ASEC automatic analysis system RAPIT to categorize and respond to known malware. This post will list weekly statistics collected from November 21st, 2022 (Monday) to November 27th (Sunday). For the main category, downloader ranked top with 40.3%, followed by Infostealer with 35.8%, backdoor with 16.3%, ransomware with 7.2%, and CoinMiner with 0.4%. Top 1 – AgentTesla AgentTesla is an Infostealer that ranked first place with 17.3%. It leaks user credentials saved in web... | Ransomware Malware | ★★ | ||
| 2022-12-01 22:39:51 | New Go-based Redigo malware targets Redis servers (lien direct) | >Redigo is a new Go-based malware employed in attacks against Redis servers affected by the CVE-2022-0543 vulnerability. Researchers from security firm AquaSec discovered a new Go-based malware that is used in a campaign targeting Redis servers. Threat actors are exploiting a critical vulnerability, tracked as CVE-2022-0543, in Redis (Remote Dictionary Server) servers. Redis (remote dictionary server) […] | Malware Threat | ★★★ | ||
| 2022-12-01 21:43:44 | (Déjà vu) Samsung, LG, Mediatek certificates compromised to sign Android malware (lien direct) | Multiple platform certificates used by Android OEM device vendors to digitally sign core system applications have also been used to sign Android apps containing malware. [...] | Malware | ★★★★★ | ||
| 2022-12-01 21:43:44 | Compromised OEM Android platform certificates used to sign malware (lien direct) | Multiple platform certificates used by Android OEM device vendors to digitally sign core system applications were utilized by threat actors to sign apps containing malware. [...] | Malware Threat | ★★★ | ||
| 2022-12-01 20:41:19 | ₿Uyer ₿eware: fausses applications de crypto-monnaie servant de front pour les logiciels malveillants d'Applejeus ₿uyer ₿eware: Fake Cryptocurrency Applications Serving as Front for AppleJeus Malware (lien direct) |
> Au cours des derniers mois, la volexité a observé une nouvelle activité liée à un acteur de menace nord-coréen, IT suit largement le groupe Lazare.Cette activité implique notamment une campagne ciblant probablement les utilisateurs et les organisations de crypto-monnaie avec une variante du malware d'Applejeus par le biais de documents malveillants Microsoft Office.L'analyse de Volexity \\ de cette campagne a révélé un site Web en direct sur le thème de la crypto-monnaie avec le contenu volé à un autre site Web légitime.Une analyse technique supplémentaire du logiciel malveillant Applejeus déployé a révélé une nouvelle variation de chargement latérale DLL que la volexité n'a pas été documentée précédemment comme dans la nature.Ce blog décrit les nouvelles techniques utilisées par le groupe Lazare, analyse les récentes variantes de logiciels malveillants d'Applejeus, partage des indicateurs d'autres versions de ce malware, ainsi que des liens entre cette activité et les campagnes historiques.La fin de la publication comprend des possibilités de détection et d'atténuation pour les particuliers ou les organisations susceptibles d'être ciblées par [& # 8230;]
>Over the last few months, Volexity has observed new activity tied to a North Korean threat actor it tracks that is widely referred to as the Lazarus Group. This activity notably involves a campaign likely targeting cryptocurrency users and organizations with a variant of the AppleJeus malware by way of malicious Microsoft Office documents. Volexity\'s analysis of this campaign uncovered a live cryptocurrency-themed website with contents stolen from another legitimate website. Further technical analysis of the deployed AppleJeus malware uncovered a new variation of DLL side-loading that Volexity has not seen previously documented as in the wild. This blog outlines new techniques used by the Lazarus Group, analyzes recent AppleJeus malware variants, shares indicators from other versions of this malware, as well as outlines links between this activity and historic campaigns. The end of the post includes detection and mitigation opportunities for individuals or organizations likely to be targeted by […] |
Malware Threat | APT 38 | ★★★ | |
| 2022-12-01 17:17:52 | Wipers Are Widening: Here\'s Why That Matters (lien direct) | In the first half of this year, researchers saw a rising trend of wiper malware being deployed in parallel with the Russia-Ukraine war. However, those wipers haven't stayed in one place – they're emerging globally, which underscores the fact that cybercrime knows no borders. | Malware | ★★★ | ||
| 2022-12-01 17:00:20 | Checklist 305: Dangers in the Latest Thing (lien direct) | >We look at Mastodon security and privacy; a TikTok malware scam; and why we still need to talk about passwords. | Malware | ★★ | ||
| 2022-12-01 15:52:29 | Android malware infected 300,000 devices to steal Facebook accounts (lien direct) | An Android malware campaign masquerading as reading and education apps has been underway since 2018, attempting to steal Facebook account credentials from infected devices. [...] | Malware | ★★★ | ||
| 2022-12-01 15:37:00 | Schoolyard Bully Trojan Apps Stole Facebook Credentials from Over 300,000 Android Users (lien direct) | More than 300,000 users across 71 countries have been victimized by a new Android threat campaign called the Schoolyard Bully Trojan. Mainly designed to steal Facebook credentials, the malware is camouflaged as legitimate education-themed applications to lure unsuspecting users into downloading them. The apps, which were available for download from the official Google Play Store, have now been | Malware Threat | ★★ | ||
| 2022-12-01 13:45:32 | (Déjà vu) New Redigo malware drops stealthy backdoor on Redis servers (lien direct) | A new Go-based malware threat that researchers call Redigo has been targeting Redis servers vulnerable to CVE-2022-0543 to plant a stealthy backdoor and allow command execution. [...] | Malware Threat | ★★★ | ||
| 2022-12-01 11:19:46 | New DuckLogs malware service claims having thousands of \'customers\' (lien direct) | A new malware-as-a-service (MaaS) operation named 'DuckLogs' has emerged, giving low-skilled attackers easy access to multiple modules to steal information, log key strokes, access clipboard data, and remote access to the compromised host. [...] | Malware | ★★★ | ||
| 2022-12-01 09:29:27 | Over 95% of all new malware threats discovered in 2022 are aimed at Windows (lien direct) | Over 95% of all new malware threats discovered in 2022 are aimed at Windows Windows is the most popular operating system among desktop and laptop users. It occupies around 30% of the OS market share worldwide. This may be one of the reasons why it is also the most targeted by malware. - Special Reports | Malware | ★★★★ | ||
| 2022-11-30 19:14:00 | Researchers Find a Way Malicious NPM Libraries Can Evade Vulnerability Detection (lien direct) | New findings from cybersecurity firm JFrog show that malware targeting the npm ecosystem can evade security checks by taking advantage of an "unexpected behavior" in the npm command line interface (CLI) tool. npm CLI's install and audit commands have built-in capabilities to check a package and all of its dependencies for known vulnerabilities, effectively acting as a warning mechanism for | Malware Vulnerability | ★★★ | ||
| 2022-11-30 17:00:00 | China-Based Hackers Target Southeast Asia With USB-Based Malware (lien direct) | UNC4191 operations have affected several entities in Southeast Asia but also in the US, Europe and Asia Pacific Japan | Malware | ★★★ | ||
| 2022-11-30 15:51:29 | New Windows malware scans victims\' mobile phones for data to steal (lien direct) | Security researchers found a previously unknown backdoor they call Dophin that's been used by North Korean hackers in highly targeted operations for more than a year to steal files and send them to Google Drive storage. [...] | Malware | ★★★ | ||
| 2022-11-30 15:13:54 | Surfshark launches a browser extension upgrade with a CleanWeb 2.0 (lien direct) | Surfshark launches a browser extension upgrade with a CleanWeb 2.0 Cybersecurity company Surfshark released a significant browser extension upgrade. The new extension has its own dashboard, where users will find upgraded CleanWeb 2.0 with four essential features – ad blocker, pop-up blocker, data breach alert, and malware alert. - Product Reviews | Data Breach Malware | ★★★ | ||
| 2022-11-30 13:59:28 | ESET Research : un groupe de pirates lié à la Corée du Nord vole des fichiers de valeur en s\'appuyant sur Google Drive (lien direct) | ESET Research : un groupe de pirates lié à la Corée du Nord vole des fichiers de valeur en s'appuyant sur Google Drive ● Les chercheurs d'ESET ont analysé Dolphin, une porte dérobée jusqu'à présent inconnue, utilisée par le groupe de pirates ScarCruft. ● Dolphin possède de nombreuses fonctionnalités d'espionnage, notamment de surveillance des lecteurs et des appareils portables, d'exfiltration de fichiers d'intérêt, d'enregistrement des frappes de clavier, de capture d'écran et de vol d'identifiants dans les navigateurs. ● Elle est uniquement déployée sur des cibles sélectionnées. Elle parcourt les lecteurs des systèmes compromis à la recherche de fichiers intéressants et les exfiltre vers Google Drive. ● ScarCruft, également connu sous le nom d'APT37 ou Reaper, est un groupe d'espionnage qui opère depuis au moins 2012. Il se concentre principalement sur la Corée du Sud. Les cibles de ScarCruft semblent être liées aux intérêts de la Corée du Nord. ● La porte dérobée est le malware final d'une attaque menée en plusieurs étapes au début de l'année 2021, qui se compose d'une attaque dite de " point d'eau " sur un journal en ligne sud-coréen, l'exploitation d'une vulnérabilité d'Internet Explorer, et une autre porte dérobée de ScarCruft appelée BLUELIGHT. ● Depuis la découverte initiale de Dolphin en avril 2021, les chercheurs d'ESET ont observé de multiples versions et améliorations de cette porte dérobée, dont l'ajout de techniques pour échapper à sa détection. ● La possibilité de modifier les paramètres des comptes Google et Gmail connectés des victimes afin d'en réduire la sécurité est une caractéristique notable des versions antérieures de Dolphin. - Malwares | Malware Cloud | APT 37 | ★★★ | |
| 2022-11-30 11:07:46 | Self-Replicating Malware Used by Chinese Cyberspies Spreads via USB Drives (lien direct) | A China-linked cyberespionage group tracked as UNC4191 has been observed using self-replicating malware on USB drives to infect targets, and the technique could allow them to steal data from air-gapped systems, Google-owned Mandiant reports. | Malware | ★★★ |
To see everything:
Our RSS (filtrered)
