What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2021-06-21 09:00:56 | Ten years, how time flies. (lien direct) | Ten years, a decade, it's a very long time, and yet passes in the blink of an eye. I joined Tenable ten years ago, and somehow they have not tired of me yet. I had known Ron Gula and Jack Huffard for a few years before I joined, we had tried to find a fit for me at Tenable a few times before, but in 2011 Astaro was being acquired and we decided that there was a good fit for me as the first person to fill the role of product manager at Tenable. In 2011 I joined a company of just over 120 people, big enough and mature enough to be stable and profitable, but small enough that it had the excitement of a startup. It was an amazing team, led by Ron, Jack, and Renaud, including Marcus Ranum, Paul Asadoorian, Carlos Perez, Jon Brody, and many more. Over the years the company evolved, the team was joined by Gavin Millard, Space Rogue, Jeff Man, and other friends who spent some time with us at Tenable. It has been great watching the career progression for all of those who remain at Tenable, and those whose career paths led them elsewhere. Tenable today is much larger, it is a successful publicly traded company, and Tenable still has a great team, led for the past few years by Amit Yoran. There has been a lot of change, but there are still more than a few folks who have been at Tenable longer than I have. It is funny to think of someone as young as Renaud as one of the “old timers”, but that's the tech world. While my role at Tenable has evolved continuously since then, Tenable has always supported my community engagement efforts, and they have always been supportive of me. Life has presented me with a few challenges over the years; Tenable's support, and especially the support of Ron and Jack in the early days, and Amit, Dave Cole, and Gavin more recently, has been nothing short of amazing. I am eternally grateful for their support, individually and as an organization. These days my role is community advocate, a role where I get to dedicate much of my time to working on a wide variety of projects including supporting Security BSides, continuing efforts to address stress and burnout in our communities, the Shoulders of InfoSec history project, and occasional career studies. It is truly a dream job. What about the next ten years? I won't pretend to know what lies ahead, but I am happy to be starting my second decade at Tenable this week. (Note, my usual disclaimer applies here: I rarely speak *for* Tenable, and am not speaking on their behalf now, this is a personal post, but I will always *listen* for Tenable and pass feedback and comments along to the appropriate teams.) | ||||
| 2021-01-25 10:13:55 | Finally, the results of the employer support survey (lien direct) | Delayed by holidays and the madness of the past month, but here it is. | ||||
| 2020-12-01 15:39:14 | Are you getting the support you need? (lien direct) | The second survey is now live, this one is an inquiry into how, and how well, employers are supporting their employees during the pandemic. Anecdotally, I've heard great things about many companies, and sadly some not great things about others. Please take a few minutes, take the survey, and share with others.Answers are anonymous, highlights and details of the results will be shared here.The survey is here | ||||
| 2020-04-07 11:55:51 | Quotable Quotes (lien direct) | Today I'll share a few of the quotes received in the comments section of the survey. Let's start with this commentary on PhD and advanced degrees: "A PhD is a full-time job, not an extension to college/school. During my PhD I've published more papers, gotten more patents & more press coverage, and generally contributed more code, tools, and know-how to the security community then my entire relatively-routine work at my current Top 4 tech company. The distinction between getting a degree and working in the field is not that clear cut while pursuing advanced degrees Note that this is about PhD and equivalent degrees in different countries. A MS degree is indeed an extension to college and it is not an advanced degree." There were a couple of comments on ageism, including this one: "Would like more emphasis pointing to employers not using older workers- definitely ageism that no one seems to be addressing." Here are a couple from women on their challenges: "CISSP and Masters were paid for by employers/grants and/or federal gov assistance program. Had to get Masters cos as a woman my years of experience was irrelevant and ppl wanted to focus on my art degree from 10 yrs+ ago." "I was in SF in the 80s. Nobody had degrees in tech back then. IBM gave free classes to PC-buyers. I just grokked PCs and could write and teach. Male employers wouldn't believe my skills, even when I offered to demo. A decade later, an intelligence agency head hunted me." The topic of who supports and pays for education came up frequently in comments: "It's frustrating how some employers do not support on-going education for their employees, including allowing them to attend security related association meetings and conferences (some of which are low-cost or free). And sadly that good training, like SANS, is getting so costly that many can't afford unless their company is paying. Which many don't." "One of the reasons I'm looking at leaving my current company is because of its extremely limited support for educational/continuing education opportunities." "The cleared defense contractor (CDC) industry in particular continues to deny obligations to train & retain employees... I have worked for multiple companies rating in the top 10 defense contractors, and have yet to experience, influence or benefit from an effective training budget. Lowest Cost, Technically Acceptable criteria seems to always win." "Tuition reimbursement is a great incentive. 3 SANS/GIAC certs thanks to employer. 7 years active military." Speaking of military, there was this comment: "Working for DoD, they were very supportive of my Masters program. My bachelors in music, was earned before I had any notion of an IT career, certainly influenced by family where a college education was strongly expected and encouraged. I don't know if having degrees have helped my career but I learned things in both tech and non-tech programs that have been very useful." Probably the most succinct comment: "The GI Bill was my sugar daddy for my education." Thanks again to everyone who took the survey and helped to spread the word about it. The survey is still open, so please continue to share. Also, thanks to Tenable. I have worked at Tenable for nine years, and they have always been extremely supportive of my community projects and volunteerism, including Security BSides, The Shoulders of InfoSec, The InfoSec Burnout Project, and this exploration of education in our industry. My lawyer would probably like me to add that my community and volunteer work is done through Tiki Tonk, LLC. | ||||
| 2020-03-30 14:51:39 | And here\'s the raw data (lien direct) | As promised, here are the raw data files as of the weekend, somewhat cleaned up: Here's the .xlsx version: https://1drv.ms/x/s!ADU9TlQrSzm4h8cc And here's a .csv https://1drv.ms/u/s!ADU9TlQrSzm4h8cd If you play with the data and decide to do anything with it, please let me know so I can share it here and elsewhere. The survey is still open at https://docs.google.com/forms/d/e/1FAIpQLSfztzGL2ludN9qm7dAcOb6bjUy_Y9WCwHtJd0kg6MlSn4WAHQ/viewform, I will share more data files once the results have grown enough to be significant beyond this set of 438 respondents. | ||||
| 2020-03-30 14:12:50 | A few more numbers, and a "that\'s interesting" or two (lien direct) | Of the 61 respondents who ID as female: 89% have a degree, 11% do not. Compared to the 359 who ID as male: 72% have a degree, 28% do not. Age/degree breakdowns: Under 26, 21 respondents, 43% no degree, 57% degree 26-35, 92 respondents, 24/76% no/yes degree 36-45, 168 respondents, 27/73% no/yes degree 46-55, 121 respondents, 26/74% no/yes degree 56 and up, 34 respondents, 24/76% no/yes degree Age/gender ID breakdown: Under 26, 21/79% ID as female/male 26-35, 22/78% female/male 36-45, 14/86% female/male 46/55, 9/91% female/male 56 and up, 15/85% female/male Of 437 respondents, 6 ID as non-binary (~1%) and 9 preferred not to answer (2%) All demographic data was clearly marked as being optional. I'll let you decide what (if any) of the revelations above warrant a "that's interesting". Up next, more-or-less cleaned up raw data files in .csv and .xlsx formats. | ||||
| 2020-03-25 13:43:49 | Initial Survey Demographics (lien direct) | Here are some initial demographics from the survey. Out of 416 respondents thus far (the survey is still open) results are: Age ranges: 21 are 25 and under (20% of these identify as female) 84 are 26-35 (21% female) 163 are 36-45 (14% female) 113 are 46-55 (10% female) 34 are 56 and over (36% female) Gender: 60 female 341 male 5 non-binary 6 no answer 2 other Race/Ethnicity: 2 American Indian / Alaskan Native 14 Asian 1 Asian;Caucasian / White 12 Black / African 3 Black / African;Caucasian / White 350 Caucasian / White 3 Caucasian / White;American Indian / Alaskan Native 2 Caucasian / White;Hispanic / Latinx 1 Caucasian / White;Hispanic / Latinx;American Indian / Alaskan Native 1 Caucasian / White;Pacific Islander 9 Hispanic / Latinx Two notes: All demographic questions are optional. This is for respondents of this survey only, it may not reflect the industry as a whole. | ||||
| 2020-03-20 14:21:17 | Certifications and self-study (lien direct) | Let's take a quick look at some non-degree data, certifications and self study:What security certifications have you earned (current and/or lapsed)? Please add certs not listed under “Other”.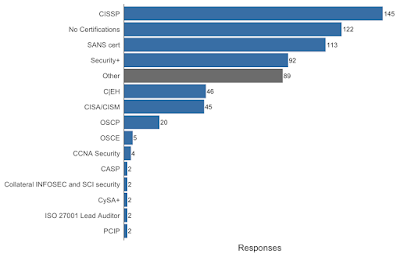 Which non-security certifications have you earned (current or lapsed)? Please add certs not listed under “Other”. Which non-security certifications have you earned (current or lapsed)? Please add certs not listed under “Other”.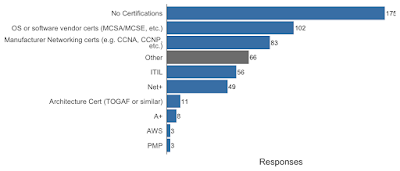 Have you done any of the following self-study or non-traditional training? Please use the “Other” option to add other methods. Have you done any of the following self-study or non-traditional training? Please use the “Other” option to add other methods.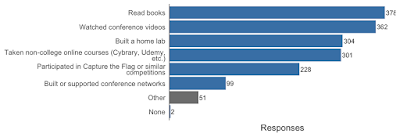 These answer say a lot about many people drawn to the security realm, we study and learn in a wide variety of ways. As the past NOC lead for a hacker con, I am really pleased to see so many folks helping run networks at events, it is a great way to help the community, and to learn in the process. The survey is still open, and the answers keep coming in. Next week we will take a look at demographics. These answer say a lot about many people drawn to the security realm, we study and learn in a wide variety of ways. As the past NOC lead for a hacker con, I am really pleased to see so many folks helping run networks at events, it is a great way to help the community, and to learn in the process. The survey is still open, and the answers keep coming in. Next week we will take a look at demographics. |
Guideline | |||
| 2020-03-20 13:43:52 | Survey Says... (lien direct) | Well, it says a lot of things, and as expected it answers some questions and asks more. First, thank you to everyone who completed the survey and shared it, there are over 400 responses so far and I plan on leaving it open for a few more weeks. I will hold off on sharing my interpretations and opinions, I just want to share some data for now. And yes, raw data will be available as a .CSV in coming weeks, I just want to gather more answers and sanitize it before sharing publicly. Also, thanks to Jay Jacobs of the Cyentia Institute, he has done some data visualization work on the initial data. The first question was "Do you currently work in a security role? (A role where security is the primary focus, whether defensive or offensive: Red team, pentester, SOC analyst, Incident Response, security admin, security support, etc.)"  Question two is "What is the highest level of formal education you have achieved?" Question two is "What is the highest level of formal education you have achieved?" And here Jay has compared the first two questions: And here Jay has compared the first two questions: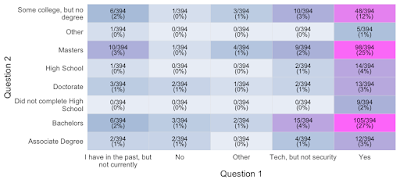 And jumping ahead, question nine is: "If you are a recruiter or hiring manager, do you require degrees for candidates in infosec/cybersecurity roles?" And jumping ahead, question nine is: "If you are a recruiter or hiring manager, do you require degrees for candidates in infosec/cybersecurity roles?" More to come later this week.Note: this post is cross-posted from the project website at https://www.careerstudy.org/ More to come later this week.Note: this post is cross-posted from the project website at https://www.careerstudy.org/ |
||||
| 2020-03-06 08:47:19 | Survey on degrees and education in cybersecurity (lien direct) | I have started a new project to gather information on career topics in information/cyber security. I'm launching with a simple survey on degrees and education in the field. It should take no more than 5-10 minutes to complete, the survey has 14 to 18 questions including optional demographic questions, plus optional additional information and feedback fields. Results will be shared online, including in the blog at careerstudy dot org, and in future presentations. Contact email for this project is: info at careerstudy dot orgPlease take the survey at https://docs.google.com/forms/d/e/1FAIpQLSfztzGL2ludN9qm7dAcOb6bjUy_Y9WCwHtJd0kg6MlSn4WAHQ/viewform And please share the survey with anyone or any group you feel may be appropriate so that we can gather more responses and gain more insights. | ||||
| 2017-12-21 12:47:28 | Blog-ified Tweetstorm (lien direct) | I dumped this on Twitter as a tweetstorm, but it is worth sharing here in one place. Those who have followed me for a while have probably noticed that I rarely get technical here anymore. My world, and world view have changed. I still play with stuff, but it tends to be specific to the nice folks who pay me, or esoteric stuff for personal use. Or for @SecurityBSides networks and labs. I believe that right now I can do more good by supporting our communities and the people in them (that means YOU) than by focusing on technology myself. The past few years have not been fun for me. My wife had a 2.5 year battle with cancer which ended a year ago this Friday, I've spent the past year discovering what it means to be without her after 40 years together. (Also, this "being single" thing is bizarre, now I get what you kids have been complaining about- but that's a story for another day, or a stand-up comedy set) Thank you all for all of your words and acts of kindness, large and small. It has meant a great deal to me. I might not be here now if not for the support of more people than I can thank. Yeah, I said that. There were days when I asked myself the question "Do I want to wake up tomorrow?". And there were times when the answer was "no". I never seriously considered acting on it, but yes, there were ugly days, and not just a few. If I can repay the amazing support and kindness shown to me by making things less bad for others I'm all in. Disclaimer: I am not a psychologist, therapist, doctor, or anything like that. That said, if you need someone to talk/vent/rant/cry to, I'll be here as much as I can. Really. Dealing with stress, burnout, anxiety, illness, or death: I'll do my best to be here for you. I travel a lot and I'm not always available, so don't count on me for immediate responses. But count on me. And if I get overwhelmed, I'll back off until I can resume. I'm not the only one to make an offer like this, find one of us or turn to professionals if you need more than a sympathetic ear. The holidays are a time of happiness and joy for many people. But they are also unpleasant for many of us, so let's take care of each other this holiday season. And the rest of the year, too. Now you smart kids get busy on the technology stuff. Jack | ||||
| 2017-04-04 11:08:36 | Doing it wrong, or “us and them†(lien direct) | I was arguing with the wiring in a little RV over the weekend and it was the typical RV mix of automotive wiring, household wiring, and What The Expletive wiring. I fell back to my auto mechanic days and set about chasing the demons through the wires. Basic diagnostics: separate, isolate, test, reconnect, retest, repeat, until a path becomes clear. In this quest I used an old trick of mine (although I assume many other have used it) in using crimp connectors the “wrong†way. This made me think of being called out for it many years ago, “you're doing it wrong you idiot!†or something like that. I tried to explain that I was just using the common butt connectors in a different way for a different situation, but he wouldn't hear of it. “That's not how you use them†was the answer. This was long before my computer and hacker days, but the mindset is there in many car guys. “You're not supposed to do that†is a warning to most, but an invitation to many of us. I hate to say we can't teach that, but with a lot of folks you either have that curiosity or you don't. I do think a lot more folks have that kind of innate curiosity and desire to test boundaries, but sadly our modern education systems can't handle those characteristics in kids- “do it our way or you are wrong†is great for standardized testing, but terrible for education. And in our little world of cyberthings we really need curious people, people who ask questions like Why? Why not? What if? Hold my beer… OK, the last wasn't a question, but a statement of willingness to try. I don't have the answer, but I have seen a lot of little things which help- hackerspaces, makerspaces, good STEM/STEAM programs, and youth programs at hacker/security cons are great steps, but I fear that these only serve to minimize the damage done by the state of education in the US lately. So yeah, I guess I'm just complaining. Again. Oh, and about using the connectors wrong, normally you put one stripped end of a wire in each end of the connector and create an inline splice. For problem situations I connect wires as shown in the image. This provides a good connection, arguably better than the inline method since the wires are directly touching, but more importantly the open ends of the connectors are shielded to prevent accidental contact, but open to provide handy test points as you chase the demons through the wires. Which reminds me of another story, but that's one for the barstool…  Jack Jack |
||||
| 2017-03-24 13:21:06 | I thought everyone knew this by now (lien direct) | But apparently not. I just saw some “Security Awareness Training†that gave the bad old advice of “look for the padlock†in your web browser. Here's my answer to that:  In a world where most of us face a constant threat from phishing we need to better educate folks, and we need to make it easier to be secure. And since the latter isn't that easy, we need to teach better. Also, “don't click stuff†really defeats the point of the web, so while I understand the sentiment, it is not practical advice. The padlock can mean a variety of things, but what it really signifies is that your web traffic is encrypted. It does not mean that all of the traffic on the page is encrypted, or that it is encrypted well. It also doesn't assure you that the traffic isn't being decrypted, inspected, and re-encrypted. Or maybe it isn't encrypted at all and someone just used a padlock as a favicon on the website (this varies somewhat by web browser). The padlock doesn't prove the identity of the site owner unless it is an EV(extended validation) certificate, and even then the validation is imperfect. When we just say “look for the padlock†we are giving people bad information and a false sense of security. It makes us less secure, so we need to kill this message. Even though it isn't entirely true if we are going to oversimplify this I think we're better off telling folks that the padlock doesn't mean a damn thing anymore, if it ever did. While we're on the subject of browsers, you know the average computer user is just trying to do something, so the warnings they see are mentally translated to “just keep clicking until we let you go where you wantâ€. I did find a few things which made me think of typical browser warnings: In a world where most of us face a constant threat from phishing we need to better educate folks, and we need to make it easier to be secure. And since the latter isn't that easy, we need to teach better. Also, “don't click stuff†really defeats the point of the web, so while I understand the sentiment, it is not practical advice. The padlock can mean a variety of things, but what it really signifies is that your web traffic is encrypted. It does not mean that all of the traffic on the page is encrypted, or that it is encrypted well. It also doesn't assure you that the traffic isn't being decrypted, inspected, and re-encrypted. Or maybe it isn't encrypted at all and someone just used a padlock as a favicon on the website (this varies somewhat by web browser). The padlock doesn't prove the identity of the site owner unless it is an EV(extended validation) certificate, and even then the validation is imperfect. When we just say “look for the padlock†we are giving people bad information and a false sense of security. It makes us less secure, so we need to kill this message. Even though it isn't entirely true if we are going to oversimplify this I think we're better off telling folks that the padlock doesn't mean a damn thing anymore, if it ever did. While we're on the subject of browsers, you know the average computer user is just trying to do something, so the warnings they see are mentally translated to “just keep clicking until we let you go where you wantâ€. I did find a few things which made me think of typical browser warnings:  This means it's OK to trespass up to this point, but no further? Is that like this website is unsafe? No, because if you look around this sign you can see the end of the pier is missing, if you click past the browser warning you will not fall into the ocean. And this, you know what it means, but what does it say? This means it's OK to trespass up to this point, but no further? Is that like this website is unsafe? No, because if you look around this sign you can see the end of the pier is missing, if you click past the browser warning you will not fall into the ocean. And this, you know what it means, but what does it say?  That's right, it says don't P on the grass. Just because you know what something means does not mean you can assume others do, we need to do a better job of explaining things. Reminding folks of the invention of indoor plumbing when what you want is to keep cars off the grass, sounds like a browser warning to me. That's right, it says don't P on the grass. Just because you know what something means does not mean you can assume others do, we need to do a better job of explaining things. Reminding folks of the invention of indoor plumbing when what you want is to keep cars off the grass, sounds like a browser warning to me. |
APT 32 | |||
| 2017-03-23 13:16:19 | Where\'s Jack? (lien direct) | As I mentioned in a post earlier this year I am traveling extensively this year, connecting and reconnecting with a lot of people. And thanks to a lot of wonderful people inside and out of the hacker and security communities I am doing very well after a rough few months. So, it's time to share my plans and encourage folks to come and chat with me if our paths cross. I know I have a reputation of being a cranky old bastard, one which is well deserved, but I'm really not a miserable person- truly, seek me out and tell me stories, ask questions, whatever. If I can help you I will, or maybe I'll point you to someone who can help if I can't. I meant what I said in my recent post about the loss of Becky Bace and others, they set an example for those of us who knew them and I'm not about to let InfoMom down. So, here's my schedule as it looks from here: Tomorrow, Friday March 24 I'll be speaking at BSidesOK in Tulsa. Yeah, short notice, but there it is. I'll be speaking at the North Florida ISSA meeting in Jacksonville on April 6. I'll also be speaking at BSides Boston on April 15th. BSides Nashville on April 22, I'll be there, not speaking, so I'll have more time to chat. May 2 in Denver I'll be speaking at the EDUCAUSE annual conference. Later that week I'll be attending Thotcon (May 4-5) and probably BurbSecCon (May 6) in Chicago. Then things calm down a little before spending most of June in Europe, but more on that later. See you on the road Jack | ||||
| 2017-03-19 23:06:07 | On loss and responsibility (lien direct) | We have lost more great figures in our world of InfoSec, and we are diminished by their loss. Spaf has written eloquently on the passing of Kevin Ziese, Howard Schmidt, and Becky Bace. I never met Kevin, and I only met Howard a couple of times, but I know of them and their impact on our industry and people in our field. Becky had become a friend over the past several years, and her loss has hit me hard. Becky has a long and storied history in InfoSec and cybersecurity (and damn, could she tell great stories). Becky was instrumental in nurturing the fledgling fields of network analysis and IDS when she was at NSA, but more importantly than her technical work she was a great friend and mentor to so many in our field that it is hard to overstate how many people she touched in her life and career. For a glimpse into what Becky was like, check out Avi's very personal and touching remembrance of meeting Becky. Once again, we take time to remember lost friends. While natural to mourn their passing we must remember that there are still many in our communities who need the kind of friends and mentors that Kevin, Howard, and Becky were to those of us who knew them. It is our responsibility to them and many others we've lost in our young field to remember them, but more importantly to fill those roles of friends and mentors to those who never knew them. Jack | ||||
| 2017-02-01 11:56:53 | What upsets Troy Hunt about conferences (lien direct) | Getting back to my normal territory here- In case you missed it, in late December Troy Hunt posted 10 Ways for a conference to Upset their speakers on his blog. I mostly agree with Troy's list and it adds to my series of rants about conferences from last fall. It's worth a read if you are interested in conferences and speaking and you haven't already read it. Jack | ||||
| 2017-02-01 06:11:06 | A few words about ovarian cancer (lien direct) | Cancer sucks. The number of people who are touched by cancer is terrifying, it is rare to find someone who hasn't had friends or family attacked by cancer if they've avoided it themselves. Sometimes, as with my bladder cancer, it's not that bad- for me I get a rather uncomfortable exam regularly, and sometimes get a small tumor or two removed, no big deal. That makes me lucky, few who face cancer get to shrug it off as a mere annoyance. Since I've recently learned a lot more about ovarian cancer than I ever expected to know, I'd like to share a few things with everyone. Remember, I'm not a medical professional, these are my observations and ideas formed over the two and a half years of my late wife's struggle with clear cell ovarian cancer. First, routine tests and doctor visits are unlikely to detect it early. Second, it's insidious- many women develop ovarian cancer around the time of menopause, and many of the symptoms of the cancer are also expected conditions that accompany menopause. There is a blood test which looks for a marker, CA 125, which may help detect ovarian cancer but the test is far from perfect. Many people have suggested it should be a regular test, others think it may lead to a false sense of security. Gilda Radner talked about the test in her autobiography before we lost her to ovarian cancer. Here's my take- and keep in mind that I'm not a doctor of anything and this isn't medical advice- I think that CA 125 screening and the symptoms of ovarian cancer are things women should be aware of. I think that routine CA 125 screening probably makes sense for women with a family history of cancer, maybe for a broader population- but only if the test is considered a weak indicator, and is done as part of comprehensive medical care (a low reading does not mean there's no cancer). If you have a healthy relationship with your doctor it should be part of a conversation, as with most tests. I don't think much about my prostate, but I do think about symptoms of prostate problems every time my doctor sends me off for a PSA test. Awareness of symptoms, thinking about them honestly, and having real conversations with your doctors is key to minimizing Bad Things. Note: I was going to prefix this with a note saying this is another personal post with nothing to do with InfoSec, then I realized I'm talking about using weak indicators as component in a comprehensive detection plan, and that sounds pretty familiar. I don't want to watch any more people die of cancer, and neither do you. But we will, so let's try to spread the word and minimize the suffering. Finally, I am not a doctor, psychologist, or anyone else who can provide real help- but if you or a loved one are facing ovarian cancer and want someone to talk to, yell at, or commiserate with- reach out to me. There's email info in the upper right corner of the page. Jack | Guideline | |||
| 2017-01-31 12:42:49 | “Thank you†is not enough (lien direct) | A few weeks ago I made a very personal, and very public announcement- that I had lost my wife to cancer a few days before Christmas. I debated how to share the news, especially since we had largely kept it quiet- she was as private a person as I am public. I decided to share the news on Twitter and Facebook, and the response was overwhelming. Literally overwhelming. The outpouring of love and support I received was humbling and deeply moving. It made me want to be a better person (although a dear friend cautioned me against making any rash decisions). The words “thank you†are not enough, especially tossed out here on my neglected blog, but it is a start. Thank you- to friends old and new, acquaintances, and complete strangers. I am truly humbled by your support. For those who had not heard the news or our story, my wife and I met when she was 14 and I was 15, we started dating a few months later and never stopped. Below is a photo of us from 1976 (and yes, it is one of the last known photos of me without a beard). 2016 was a rough year for many of us and 2017 is presenting us with new challenges, but (forgive my optimism) together we can make things suck less, personally and professionally. For me 2017 is about friends old, new, and as yet unmet. I still love technology, I love abusing technology and solving problems with technology, but this year is about people. I'll be at most of the usual events, and a lot of smaller ones, all around the world. If our paths cross please find me, say hello, maybe share coffee or a cocktail and conversation. I was recently at Shmoocon, it is an event I have always enjoyed and this year it was especially good to reconnect with the Shmoocon crowd as I started my return to being active and engaged on the road. I'll be at BSides San Francisco and RSA in a couple of weeks, after that I'm regrouping before hitting the road again, but more on that later. Thank you Jack 2016 was a rough year for many of us and 2017 is presenting us with new challenges, but (forgive my optimism) together we can make things suck less, personally and professionally. For me 2017 is about friends old, new, and as yet unmet. I still love technology, I love abusing technology and solving problems with technology, but this year is about people. I'll be at most of the usual events, and a lot of smaller ones, all around the world. If our paths cross please find me, say hello, maybe share coffee or a cocktail and conversation. I was recently at Shmoocon, it is an event I have always enjoyed and this year it was especially good to reconnect with the Shmoocon crowd as I started my return to being active and engaged on the road. I'll be at BSides San Francisco and RSA in a couple of weeks, after that I'm regrouping before hitting the road again, but more on that later. Thank you Jack |
||||
| 2016-10-26 13:57:06 | Wrong About Presentations (lien direct) | But first- this series is a bit off-the-cuff and lacking in polish, but I've been meaning to do it for ages and if I wait, well, this blog continues to look abandoned. So please forgive the rambling and read on. Today let's start talking about presentations. I have heard and read that they are all too long, except the ones that are too short. That talks are simultaneously too technical and too high-level. Oh, and all panels suck. Ted-style talks are the best, except that they are hollow, empty, and don't work for highly technical content. And you should never let vendors speak because we're all just sales weasels, except for the events where only “sponsors†get to speak. Let me once again venture into crazy talk: it really depends on who you are and what you want. I don't like vendor sales pitches, but apparently some folks find them a good use of their time. I'd rather avoid those kind of talks, but that's me (and probably you, too, but whatever). If sales presentations are a good use of your time, that's OK with me. I do hope you do some homework before whipping out the old purchase orders, though. I will say that a lot of presentations I've seen could have been delivered better in a shorter timeframe- but that's as much on the events as the speakers. If the only choice is an hour slot, people do an hour talk. I do think the quality of things like Shmoocon Firetalks is in part because people often pare down what they planned to be a longer talk, leaving only the key points and deliver them in a short time. Scheduling talks of different lengths does pose real logistical challenges for conference organizers, but I think it would be good to make it easy for people to do shorter talks. Of course, speaker ego can be an issue, we need to make it clear that the quality of the talk is not tied to the length of the talk. I also thing that shorter talks make it easier to get new things in front of an audience. Presentation style, there's a topic sure to inflame absolutists. The style has to match the speaker and the topic. You will never do a good Ted-style talk that walks through the code of your new project or steps through disassembly of malware. Conversely, a code walk isn't the way to explain big picture issues. Lately my presentations weave the ideas and information together via storytelling, in a style that sometimes borders on stand-up comedy. And it works for me and the less technical topics I've covered in the past few years, but it certainly won't work for everyone or every topic. I know there are disciples of some books and styles such as Presentation Zen and Slide:ology, I think they are great resources but as always there is no One True Way. Do what works for your audience and for you. As far as panels, many are indeed often a lazy attempt at getting on the schedule, they're frequently poorly moderated and wander off topic into incoherent ramblings. It is also true that well-run panels can showcase display a diverse set of opinions and experiences and add nuance to complicated topics. Panels do not suck, bad panels suck. And no, this series isn't over, I'm just getting warmed up. Jack | ||||
| 2016-10-13 14:08:46 | Relevant to my rants (lien direct) | Before I resume my rambling on conferences and presentations, here's a great article I came across via Tales of the Cocktail, a site you would expect me to link to from my, ahem, travel blog. This article is specifically about submitting a cocktail seminar to Tales of the Cocktail, but several points in the list of seventeen items apply to a wide variety of events, regardless of topic or venue. Also, it has been said many times by many people and in many ways- one of the best tips for getting your proposal accepted at any event is to follow the rules. Really, read the rules/guidelines for submission, and follow them. Also, submit early. Most event reviewers are volunteers and do it in their spare time, something which gets scarce when the deadline approaches. Submit early and you're more likely to get non-bloodshot eyes looking at your paper. Jack | ||||
| 2016-10-07 13:46:06 | Wrong About Conferences, part 3 (lien direct) | Thought I'd get tired of this topic? No way, I'm just getting warmed up. Today's installment continues on the events themselves: A lot of people complain about the commercialization, the sales pitches, the circus-like atmosphere of some vendor areas. I'm not a big fan of these things myself (OK, I loathe them), I prefer to engage with vendors in a rational manner- but whether you are buying antivirus, SIEM, a new car, or a washing machine, expect the sales hype. If you are like me you'll ignore the excesses and gravitate towards the companies who bring engineers and maybe even support personnel to accompany the sales and marketing teams to shows so that they can answer hard questions and help existing customers. And if you aren't buying, or curious about the tech, avoid those parts of the events altogether (or as much as the venue allows). The same events which have the big vendorfests are often the best for meeting people for quiet meaningful conversations- not at the show but nearby, away from the mayhem. If thousands of people go to the event, there may be folks there you want to talk to, you don't have to meet at the conference. If you are going to do this, make appointments. You will not just run into folks and have time to chat. And “I'll meet you in the lobby†isn't good enough, especially at sprawling complexes like the Moscone Center in San Francisco, the Las Vegas Convention Center, and other huge venues. The flip side of over commercialization are the community events with little or no advertising and sales. They are a great relief to many of us who suffer the excesses at commercial shows, but they don't generate leads for the sponsors so it can be hard to pull in the funding needed for the event. These events often get funded primarily through ticket sales because someone has to pay. A lot of companies will provide sponsorship for visibility and the good of the community, but there are a lot of community conferences and not enough money for all of them. The realms of for-profit, not-for-profit, and non-profit are too convoluted a topic for this series, bet whether people want to make money from an event or not, they want people to like the event. It is also worth mentioning the size of events. Everyone want to go to the cool events, and so some grow until they aren't what they used to be, and a lot of folks complain about this. When I hear such complaints I am reminded of what the sage Yogi Berra said many years ago about Rigazzi's in St. Louis: “Nobody goes there anymore, it's too crowded†But if events cap attendance and demand continues to grow they get accused of being exclusionary by some. What's a conference organizer to do? You'll note I've avoided naming specific events, although I'm sure most of you have assigned names to several things I've mentioned. I would, however, like to use one specific group as an example, an example that could be applied to many other groups and events. DC303, the Denver area DEF CON group, is well known and very active, and I've heard them accused of being “cliquish†and excluding people from activities and events. I would like to make two points abut DC303 (note, I am *not* a 303 member): First, as with most organizations, some things are limited to members. I can't expect to toss my kayak in the bay and be welcomed down at the yacht club. Some things are more open than others- and some do require an invitation, which leads to my second point: My first interaction with the 303 crew was in July of 2009, at the first BSides Las Vegas. I knew almost no one other than from a few online exchanges, they certianly didn't know me. And it didn't matter, I showed up and got to work as did several others- and many of us became friends. That's it, th | Guideline | |||
| 2016-10-06 12:11:14 | Wrong About Conferences, part 2 (lien direct) | Today let's start with a look at the conferences and events themselves. One of the cyclical things I see is dismissing events people don't like as irrelevant or worse. “The big commercial cons are irrelevant…†as tens of thousands of people go to them, learn, share and yes, do the business of InfoSec. The business of InfoSec, it's so ugly and dirty, oh, and pays tens of thousands of us a living while funding an amazing amount of research. Maybe they aren't the places for cutting edge research, especially offensive security stuff, but that's not their core audience. Are there excesses? Sure there are. Are they valuable to a lot of people? Of course they are. And very few people are forced to go unless they are paid to do so. Don't like it? Not your scene? Cool, don't go. “That's just a hacker con, full of criminals…†as thousands or even tens of thousands of people gather to learn, share, and (gasp) maybe even do a little business. Yeah, we're all a bunch of criminals, right. No, almost all of us at hacker cons are trying to make the world more secure. You may disagree with some methods and opinions, but hacker cons help make us more secure. Some may not be the best places to learn a lot about policy and compliance issues, or securing global enterprises, but that's not what they're about- and some “hacker†cons do cover these topics well. Are there excesses? Sure there are. Are they valuable to a lot of people? Of course they are. And very few people are forced to go unless they are paid to do so. Don't like it? Not your scene? Cool, don't go. Fifty years ago buffalo Springfield sang “Nobody's right if everybody's wrongâ€, and that sums up the way I feel about a lot of the con noise, hype, and drama. Find the events that work for you, contribute to making them better, and avoid the ones that don't work for you. There are plenty of things I don't like about a lot of events, I'm a cranky old man. I do, however, understand that different events serve different needs and audiences. That doesn't excuse hype, lies, and bullshit but no event has a monopoly on that. More on events in the next few posts. Jack | ||||
| 2016-10-05 13:34:12 | Everyone is wrong about conferences (lien direct) | In the past couple of years there have been many blog posts and articles on the topics of what's wrong with InfoSec and hacker conferences, which events are or are not relevant, and what's wrong with the talks and panels at those conferences. A lot of good points have been raised, and some great ideas have been floated. But they are all wrong. Many of them aren't just wrong, they're also symptomatic of some of the things wrong with InfoSec, a failure to understand the importance of context and perspective. Let's start with this simple fact: Your experience is unique, it is not not universal. Your perspective is therefore not a universal perspective. As with anyone offering The One True Answer to any question, allow me to suggest that It Isn't That Simple. In upcoming posts I'll dig into a few of theses topics, not to give The One True Answer, but to share some of my experiences and perspectives, and float a few ideas of my own. I don't claim to be an expert on conferences or presentations (or much of anything else), but I am and have been involved in a lot of conferences- as an attendee, participant, program committee member, organizer, volunteer, vendor booth staff, speaker, and even bartender. I also participate in events large and small, commercial and community, business- and hacker-centric. And I have opinions. You may have noticed. Stay tuned. Jack But they are all wrong. Many of them aren't just wrong, they're also symptomatic of some of the things wrong with InfoSec, a failure to understand the importance of context and perspective. Let's start with this simple fact: Your experience is unique, it is not not universal. Your perspective is therefore not a universal perspective. As with anyone offering The One True Answer to any question, allow me to suggest that It Isn't That Simple. In upcoming posts I'll dig into a few of theses topics, not to give The One True Answer, but to share some of my experiences and perspectives, and float a few ideas of my own. I don't claim to be an expert on conferences or presentations (or much of anything else), but I am and have been involved in a lot of conferences- as an attendee, participant, program committee member, organizer, volunteer, vendor booth staff, speaker, and even bartender. I also participate in events large and small, commercial and community, business- and hacker-centric. And I have opinions. You may have noticed. Stay tuned. Jack |
||||
| 2016-09-30 06:45:19 | Debunking fuel in the gas tank, case closed. (lien direct) | Picking up from yesterday's post: Imagine a time when carburetors ruled the earth (or at least car's fuel systems), and a time before emissions controls extended to evaporating fuel vapor, say perhaps in the 70s when I began my career as a mechanic, working on cars of that era and older. Back then, in ye olden days, fuel systems were open to the environment, both in cars and in the tanks at gas stations. That meant that water vapor could condense in the fuel tanks and drip or run down the sides and pool at the bottom of the tanks. This is why the fuel pickups in gas stations' underground tanks were a few inches above the bottom, and why we always used water-detecting paste on the giant tank sticks used to measure the amount of fuel in the ground. An inch or two of water at the bottom of the tank and no one cared as long as the amount didn't increase rapidly- it would stay down there harmlessly. Unless, of course, you got a fuel delivery which churned up everything on the bottom of the tanks, water, sediment, whatever. Still, it would eventually settle back down- but if you happened fill up your car while the much was stirred up you could get the nasties, including water, into your car's tank. And no, most stations didn't have great fuel filtration between the tank and the pumps. To this day I avoid filling up my vehicles if I see a fuel truck in the gas station lot- I had to deal with too many dirty fuel systems to take the chance. And even if you didn't get water from a bad gas station fill up you could build up water from condensation on the roof of your fuel tank settling to the bottom. Now we have a couple of paths to getting water into your car's gas tank, where does that take the sugar myth? It doesn't take a lot of water to dissolve sugar that finds its way into the tank, especially given the constant vibration and sloshing that happens in a moving vehicle, so now we can move the sugar solution along with the gasoline towards the engine. We still have a fuel filter to deal with, but they were generally simple paper filters designed to stop solids, not liquids, so our mix of gasoline and sugar water wouldn't get stopped there. This assumes that the vehicle has a fuel filter at all- which is not a safe assumption if you go far enough back in time, or if you happen to be dealing with someone who bypassed their fuel filter “because it kept clogging upâ€. (If you think no one would ever do something that dumb, you have probably never worked a helpdesk). And now the fuel hits the carburetor, where a little bowl acts as a reservoir for fuel before it finds its way into the intake system. Carburetors are full of tiny orifices, the kind that don't like dirt, or much of anything other than clean gasoline and clean air. Sugar water can gum things up, block holes, or settle out into the bottom of the fuel bowl- and that's where things are no longer theoretical. I had to clean out a few carburetors with sticky goo in them in my “gas station mechanic†days, and I recall one where we dropped the gas tank and found an ugly mess in the tank. Sugar in the tank could, under some circumstances, be annoying. Not catastrophic but mildly disruptive, and a genuinely unpleasant thing to do to someone. What's the moral of the story? I don't think there is one, other than exaggeration and hyperbole feed urban legends whether they're based on complete nonsense or a tiny grain of truth. Bottom line, don't put sugar in gas tanks. Not just because it won't work, but because it's a rotten thing to do. Jack | ||||
| 2016-09-29 14:37:24 | Debunked debunking, part 2 (lien direct) | Another “debunked†automotive urban legend is the “Sugar in the gas tank will destroy your engine!!!11!†story. Let's take a look at this tale, and look at a few angles folks often miss when discussing it. This myth has been thoroughly debunked, by people both smart and not-so-smart, but let's look at it again. First and foremost, sugar does not dissolve in gasoline. You might be able to stir it into some kind of suspension, but it won't really dissolve. (Sugar doesn't dissolve well in alcohol, either, but that's a topic for my other blog.) That would seem to thoroughly debunk the story by itself, and in modern vehicles in good condition it pretty much does. Modern, good condition… I just opened two interesting views into one angle to the tale. Second, modern (there's that word again) vehicles have very thorough fuel filtering which will prevent sugar granules from making it anywhere near the engine. And finally for this post, even if sugar did dissolve in gas (which it doesn't) and sugar made it through the filter(s) (which it won't), the sugared fuel would only flow through the fuel, intake, and exhaust systems. I suppose it might make it into the lower parts of the engine if the pistons/rings/cylinder walls were junk but then the engine is already trashed. Let's talk about what could happen in the scenario above, assuming sugar did dissolve in gas and/or filtration didn't stop it. It is a safe bet that fuel injectors wouldn't like it, they might gum up eventually as the sugar burned (caramelized?) due to engine heat. I suppose, since we're suspending disbelief, that sugar could build up on the valves and contribute to burned valves- but the operating temperatures of modern valves are extremely high and since they're designed to function at such temperatures that I doubt it would be a problem as the sugar would burn off without building up. Continuing with the fantasy, maybe turbochargers and catalytic converters wouldn't enjoy the sugar solution- but again the extreme heat would burn the sugar somewhere in the process and probably burn it cleanly with no significant ill effects. So there we have it, thoroughly debunked. Except maybe not. What if we scale back the expected damage from catastrophic to annoying, and go back in time? In the first post on debunking going back in time was also a key to understanding the battery myth. The rest of this story comes tomorrow (really). Jack | ||||
| 2016-06-14 19:31:09 | Bad analogy, bad. No biscuit. (lien direct) | If you use the “If I leave my door unlocked you don;t have the right to walk in…†analogy when discussing web disclosures, you really need to stop. Bad analogies are bad. You know the cases, folks find things on the Internet that people didn't mean to make public, and a storm ensues and all kinds of people say all kinds of naïve stuff, including people who should know better. Your website is not a house, and not just because of the physical vs. virtual difference. If we have to use this analogy, let's at least get it more accurate. You live on a road, it may be public, or it may be private, but either way it is open to the public- in fact public use is encouraged. That's why you put your house there, because of good access in and out to the rest of the world. You put sensitive data on signs in your yard, visible from the road. There might even be a sign that says “only read your own dataâ€, but it is all visible. Someone drives by and reads someone else's sign from the road. Maybe they take pictures of the signs. Still imperfect, but much more accurate. And so convoluted it doesn't help make any point. These issues are not simple and misrepresenting them and oversimplifying things does not help. Note that I have not made any judgements about who exposed what where, and who drove by and looked at it. If it is your house and you post my data in an irresponsible manner, you are being irresponsible. If someone feels the need to copy everything to prove a point, that causes problems, even when their intentions are good. Without picking any specific cases, most of the ones that make the news are a combination of errors on both sides. You should act like sensitive data is, I don't know, sensitive. And when you stumble across things like that (and you will if you use the Internet and pay attention), you should think about how folks will react, and keep the CFAA in mind. Right or wrong, that's the world we live in. I think the CFAA is horrible and horribly out of date, as is the DMCA- but while they are the law and enforced, ignore them at your peril. It is worth considering that when people find stuff that shouldn't be posted publicly, it generally doesn't require downloading the entire dataset to report the problem, in fact that is likely to create problems for everyone. And yes, that's a gross oversimplification from me in a post where I decry gross oversimplification. Literary license or something. And because I actually care about this mess we're in, I'll make an offer I hope I don't regret: if you stumble across things which are exposed and you really don't know how to handle it please pause and reach out to me. I'll ask friends in law enforcement for guidance for you if you wish to remain anonymous, or I'll try to help you find the right folks to work with. If you are outside of the US, I'm unlikely to be if much help, but I'll still make inquiries. Note that if you are on any side of one of these situations and act like a dumbass, I reserve the right to call you a dumbass. I'll still try to help, but I'm calling you a dumbass if you deserve it. That's as close to idealistic as you'll get from me. Jack |
1
We have: 26 articles.
We have: 26 articles.
To see everything:
Our RSS (filtrered)
