What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2019-05-01 04:54:00 | Why local governments are a hot target for cyberattacks (lien direct) | Over the course of the past few weeks, a seemingly stepped-up wave of malware and ransomware infections has struck a number of municipalities across the U.S. On April 10, the city of Greenville, North Carolina, had to disconnect most city-owned computers from the Internet due to what officials said was a RobinHood ransomware infection, a duplicitous piece of malware that pretends to raise awareness and funds for the people of Yemen. On April 13, Imperial County, California was hit with Ryuk ransomware, which is designed to target enterprise environments, forcing its website to go dark and causing some city systems to malfunction, including a number of departments' phone lines. On the same day Imperial County was infected, the city of Stuart, Florida, was hit by Ryuk ransomware, forcing system shut-downs affecting payroll, utilities and other vital functions, including police and fire departments. On April 18, an unspecified piece of malware, likely ransomware, crippled the city's computer network in Augusta, Maine. On April 21, the municipally owned airport in Cleveland, Ohio, Cleveland Hopkins International airport, was struck by still-unspecified malware, causing the airport's flight and baggage information boards to go dark, an outage that lasted at least five days. [ Find out how 4 deception tools deliver truer network security. | Get the latest from CSO by signing up for our newsletters. ] | Ransomware Malware | |||
| 2019-04-29 03:00:00 | How to evaluate SOC-as-a-service providers (lien direct) | If you don't currently have your own security operations center (SOC), you are probably thinking of ways you can obtain one without building it from scratch. The on-premises version can be pricey, more so once you factor in the staffing costs to man it 24/7. In the past few years, managed security service providers (MSSPs) have come up with cloud-based SOCs that they use to monitor your networks and computing infrastructure and provide a wide range of services such as patching and malware remediation. Let's look at how this SOC-as-a-service (SOCaaS) industry has grown up, what they offer and how to pick the right supplier for your particular needs. | Malware Patching | |||
| 2019-04-17 03:00:00 | How to protect yourself from PC hardware and hardware driver vulnerabilities (lien direct) | PC manufacturer Asus recently announced that from June to November 2018, attackers used its Asus Live Update app, which comes preinstalled on ASUS notebook computers, to install backdoors on targeted computers. Kaspersky indicated that about 57,000 systems installed the backdoored live update software. Asus has acknowledged the introduction of malware into its update process and provided a tool to test your system to see if it has the malicious software installed. | Malware | |||
| 2019-04-15 03:00:00 | Outside-the-box malware is getting more common, security researchers warn (lien direct) | Most malware authors have become lazy in the past few years, copying code and techniques from each other. A few, however, “have invested in really fresh ideas,” building tools that are often difficult to detect by antivirus software and pose challenges to human researchers," Aleksandra Doniec, malware intelligence analyst at Malwarebytes, tells CSO. | Malware | |||
| 2019-04-12 03:00:00 | What is Emotet? And how to guard against this persistent Trojan malware (lien direct) | Emotet is a banking Trojan that started out stealing information from individuals, like credit card details. It has been lurking around since 2014 and has evolved tremendously over the years, becoming major threat that infiltrates corporate networks and spreads other strains of malware.The U.S. Department of Homeland Security published an alert on Emotet in July 2018, describing it as “an advanced, modular banking Trojan that primarily functions as a downloader or dropper of other banking Trojans,” and warning that it's very difficult to combat, capable of evading typical signature-based detection, and determined to spread itself. The alert explains that “Emotet infections have cost SLTT (state, local, tribal, and territorial) governments up to $1 million per incident to remediate.” | Malware Threat | |||
| 2019-04-10 16:59:00 | Group behind TRITON industrial sabotage malware made more victims (lien direct) | Security researchers have uncovered additional attacks attributed to the group behind the TRITON malware framework, one of the few threats found to date that was specifically designed to sabotage industrial equipment. TRITON was first uncovered in 2017 after hitting the systems of a petrochemical plant in Saudi Arabia with the possible goal of causing an explosion. That attack failed because an error made by the attackers triggered an emergency shutdown of critical systems.[ Learn what you need to know about defending critical infrastructure . | Get the latest from CSO by signing up for our newsletters. ] The TRITON malware is capable of reprogramming Triconex safety instrumented system (SIS) controllers made by Schneider Electric. These controllers are part of the last line of defense for avoiding critical failures and possible disasters in industrial facilities. They are designed to automatically shut down equipment and processes if they exceed safe operating parameters. | Malware | |||
| 2019-04-10 12:33:00 | (Déjà vu) You Can Now Get This Award-Winning VPN For Just $1/month (lien direct) | If you use the internet (which you clearly do), you likely know how important it is to protect your data in an increasingly dangerous cyber environment. But like other essential tasks that tend to be tedious (like filing taxes early and brushing your teeth for the full two minutes), most installing and running a VPN can sound unappealing to many: sure, they encrypt your internet traffic and hide your location - but they can also run frustratingly slowly, delaying the way you'd usually use the internet for entertainment and work. That's where Ivacy VPN is different: not only will the speedy service let you browse and stream lag-free, it also offers real-time threat detection technology, removing malware and viruses at the server level. It ensures that all your downloads and devices stay totally secure, so you can stay safe online without being inconvenienced. | Malware Threat | |||
| 2019-03-25 13:56:00 | Get a two-year subscription to Ivacy VPN for only $2.03/mo (lien direct) | If you use the internet (which you clearly do), you likely know how important it is to protect your data in an increasingly dangerous cyber environment. But like other essential tasks that tend to be tedious (like filing taxes early and brushing your teeth for the full two minutes), most installing and running a VPN can sound unappealing to many: sure, they encrypt your internet traffic and hide your location - but they can also run frustratingly slowly, delaying the way you'd usually use the internet for entertainment and work. That's where Ivacy VPN is different: not only will the speedy service let you browse and stream lag-free, it also offers real-time threat detection technology, removing malware and viruses at the server level. It ensures that all your downloads and devices stay totally secure, so you can stay safe online without being inconvenienced. | Malware Threat | |||
| 2019-03-20 03:00:00 | What is malvertising? And how to protect against it (lien direct) | Malvertising definition Malvertising, a word that blends malware with advertising, refers to a technique cybercriminals use to target people covertly. Typically, they buy ad space on trustworthy websites, and although their ads appear legitimate, they have malicious code hidden inside them. Bad ads can redirect users to malicious websites or install malware on their computers or mobile devices. [ Get inside the mind of a hacker, learn their motives and their malware. | Sign up for CSO newsletters! ] | Malware | |||
| 2019-03-11 07:07:00 | Hackers use Slack to hide malware communications (lien direct) | A group of hackers is using a previously undocumented backdoor program designed to interact with attackers over Slack. While abusing legitimate services for malware command-and-control purposes is not a new development, this is the first time researchers have seen Slack, a popular enterprise collaboration tool, being used in this way.[ Keep up with 8 hot cyber security trends (and 4 going cold). Give your career a boost with top security certifications: Who they're for, what they cost, and which you need. | Sign up for CSO newsletters. ] The backdoor was detected by security firm Trend Micro in a targeted attack launched from the compromised website of an organization called the Korean American National Coordinating Council that posts articles related to North and South Korean politics. The technique of infecting websites that are of interest to a particular group of individuals or organizations is known as a "watering hole" attack. | Malware | |||
| 2019-03-01 11:17:00 | Qbot malware resurfaces in new attack against businesses (lien direct) | The decade-old Qbot financial malware has resurfaced with an improved version in a new attack against businesses that has infected thousands of systems so far. Researchers from data security solutions provider Varonis have uncovered the attack after a customer alerted them about suspicious activity on a computer. The culprit turned out to be an infection with a new strain of Qbot, also known as Qakbot, that was trying to spread to other systems on the network. [ Get inside the mind of a hacker, learn their motives and their malware. | Sign up for CSO newsletters! ] | Malware | |||
| 2019-02-15 03:00:00 | 10 essential steps to improve your security posture (lien direct) | It has never been easier for cybercriminals to infect your business with malware or ransomware. A vast array of malware tools can be bought on the dark web, complete with helpdesks for hackers, making the barrier to entry low. Most hackers will sit on your network for days, weeks or even months, gathering intelligence to infiltrate your systems and then try to exfiltrate data undetected. | Malware | |||
| 2019-02-14 03:00:00 | Beware of phony or misleading malware rescue web pages (lien direct) | Scammers and adware purveyors have long used the helpful nature of the internet to get more victims. In a world where the top search engines try their best to filter out the chaff, scammers still do their best to encourage victims to install unneeded and sometimes malicious software. They often succeed by using scare tactics and misleading information. My recent experience is an example and can serve as a warning to others. | Malware Guideline | |||
| 2019-01-24 00:05:00 | Multi-vector attacks target cloud-hosted technologies (lien direct) | The push to move everything into the cloud over the past several years has generated a large number of misconfigured and exposed deployments of various software stacks. This has attracted sophisticated attacks that destroy data or abuse server resources for cryptocurrency mining. [ Learn which interview questions to ask cloud security candidates. | Get the latest from CSO by signing up for our newsletters. ] In a new report released today, security researchers from Securonix warn of an increase in the number of multi-vector and multi-platform automated attacks against cloud infrastructure over the past few months. These often combine cryptomining, ransomware and botnet malware all in one. | Malware | |||
| 2019-01-14 03:00:00 | How to protect backups from ransomware (lien direct) | Despite a recent decline in attacks, ransomware still poses significant threats to enterprises, as the attacks against several major newspapers demonstrated this month. It is also becoming more capable. In particular, ransomware writers are aware that backups are an effective defense and are modifying their malware to track down and eliminate the backups. | Ransomware Malware | |||
| 2019-01-02 08:16:00 | Major US newspapers crippled by Ryuk ransomware attack (lien direct) | Ryuk ransomware is believed to be the culprit behind printing and delivery issues for “all Tribune Publishing newspapers” - as well as newspapers that used to be part of Tribune Publishing.The malware was discovered and later quarantined on Friday, but the security patches failed to hold when the servers were brought back online and the ransomware began to re-infect the network and impact servers used for news production and manufacturing processes. A Tribune spokesperson said the malware “impacted some back-office systems, which are primarily used to publish and produce newspapers across our properties.” | Ransomware Malware | |||
| 2018-12-07 06:55:00 | IDG Contributor Network: A look back at cybercrime in 2018 (lien direct) | Last year IBM's securityintelligence.com predicted that: Internet of things would make the news. Orchestration & Automation would be a top priority. Business would rush to prepare for GDPR These were very accurately predicted as areas of great impact!Symantec's 2018 cybersecurity attacks report reported that IOT experienced a 600% increase in attacks in 2017 over the 2016 period. An astonishing 8500% increase in malware coin miner detections, Coin miners not only slow down devices but can overheat batteries and sometimes render a device useless. These are browser-based attacks so no need to download the malware to a victim's PC. | Malware | |||
| 2018-11-15 12:50:00 | IDG Contributor Network: Small Business Saturday means it\'s time for an annual cyber refresh (lien direct) | As we approach Small Business Saturday, it's a good time of year for small and mid-sized businesses to refresh their thinking around data security and incident response planning. In the same way that we are taught to change the batteries in our smoke detectors twice a year at Daylight Saving Time, Small Business Saturday should trigger an instinctive “cyber refresh” for SMBs everywhere.If the idea of an annual review isn't exactly motivating, think on this. According to the 2018 Verizon DBIR, 58% of malware attack victims were categorized as small businesses. Further, the Poneman 2017 State of Cybersecurity in Small and Medium-Sized Businesses reported that cyberattacks cost small and medium-sized businesses an average of $2,235,000. When you're small, the cost of a cyber event – both in real dollars and in broken trust with your customers – can be devastating. | Malware | |||
| 2018-11-06 08:56:00 | Worst malware and threat actors of 2018 so far (lien direct) | What's the worst malware so far into 2018? The worst botnets and banking trojans, according to Webroot, were Emotet, Trickbot, and Zeus Panda. Crysis/Dharma, GandCrab, and SamSam were the worst among ransomware. The top three in cryptomining/cryptojacking were GhostMiner, Wanna Mine, and Coinhive.And included in the list of top 10 threat actors so far this year, we find Lazarus Group, Sofacy and MuddyWater coming in the top three spots, according to AlienVault. Lazarus Group took the top spot from Sofacy this year. The reported locations for the top 10 threat actors are North Korea, with two groups; Russia, with three groups; Iran, with two groups; China, with two groups; and India, with one. Microsoft Office was the most exploited application, but Adobe Flash, WebLogic, Microsoft Windows, Drupal and GPON routers were also listed in the top 10. | Malware Threat Medical | APT 38 | ||
| 2018-11-04 09:19:00 | (Déjà vu) Meaner, more violent Stuxnet variant reportedly hits Iran (lien direct) | Stuxnet allegedly has a vicious little brother, or perhaps it is a malicious cousin; the complex malware was likened to being similar to Stuxnet but “more violent, more advanced and more sophisticated.”Iran, according to the Times of Israel, admitted that its “infrastructure and strategic networks” were hit by a meaner, leaner version of Stuxnet. A TV news report added that the Iranians are “not admitting, of course, how much damage has been caused.”The report came after Iranian Supreme Leader Ayatollah Ali Khamenei said Iran needed to step up efforts to fight enemy “infiltration.” Reuters also reported that Gholamreza Jalali, the head of Iran's civil defense agency, said, “Recently we discovered a new generation of Stuxnet which consisted of several parts ... and was trying to enter our systems.” Jalali didn't go into more detail. | Malware Guideline | |||
| 2018-11-04 09:19:00 | (Déjà vu) Meaner, more violent Stuxnet variant reportedly hit Iran (lien direct) | Stuxnet allegedly has a vicious little brother, or perhaps it is a malicious cousin; the complex malware was likened to being similar to Stuxnet but “more violent, more advanced and more sophisticated.” Iran, according to the Times of Israel, admitted that its “infrastructure and strategic networks” were hit by a meaner, leaner version of Stuxnet. A TV news report added that the Iranians are “not admitting, of course, how much damage has been caused.”The report came after Iranian Supreme Leader Ayatollah Ali Khamenei said Iran needed to step up efforts to fight enemy “infiltration.” Reuters also reported that Gholamreza Jalali, the head of Iran's civil defense agency, said, “Recently we discovered a new generation of Stuxnet which consisted of several parts ... and was trying to enter our systems.” Jalali didn't go into more detail. | Malware Guideline | |||
| 2018-10-29 03:00:00 | Why the best antivirus software isn\'t enough (and why you still need it) (lien direct) | Traditional signature-based antivirus is notoriously bad at stopping newer threats such as zero-day exploits and ransomware, but it still has a place in the enterprise, experts say, as part of a multi-layer endpoint security protection strategy. The best antivirus products act as the first layer of defense, stopping the vast majority of malware attacks and leaving the broader endpoint protection software with a smaller workload to deal with. | Malware | |||
| 2018-10-23 09:00:00 | Burned malware returns, says Cylance report: Is Hacking Team responsible? (lien direct) | Burning malware is like Hercules fighting the nine-headed Hydra. For every head he cuts off, two more grow back in its place. That's the lesson from a new report by Cylance today, and one both enterprise network defenders-and the public at large-should pay attention to.[ Keep up with 8 hot cyber security trends (and 4 going cold). Give your career a boost with top security certifications: Who they're for, what they cost, and which you need. | Sign up for CSO newsletters. ] Cyber mercenaries sell malware to oppressive regimes in the Middle East, which then use that malware to attack their own citizens, research from the Citizen Lab suggested earlier this year. The current regimes in Turkey and Egypt compel local ISPs to run Canadian-made Sandvine/Procera deep packet inspection middleboxes that inject the malware into unencrypted HTTP downloads of popular software like Avast, VLC Player and WinRAR. Large numbers of users in Egypt, Turkey and Syria (near the border with Turkey) are affected. | Malware | |||
| 2018-10-19 11:22:00 | (Déjà vu) Trend Micro shines a light on its new cybersecurity solutions (lien direct) | Last week, Trend Micro came to Boston for its annual Trend Insights industry analyst event. The company provided an overview of its business, products, and strategy. Here are a few of my take-aways: Trend Micro is prepared for the next chapter in endpoint security. To maintain its market leadership, Trend Micro is rolling out Apex One, its newest endpoint security product. Apex One provides more prevention/detection capabilities while consolidating all endpoint security functions onto a single agent. Trend Micro has also decided to swim against the industry tide by including EDR as part of its core commercial endpoint security product (note: EDR requires a licensing change), thus all customers who upgrade will get Trend Micro EDR, alleviating the need to shop elsewhere. Apex One will be an easy decision for existing Trend Micro customers and may be an attractive alternative for CISOs looking for an endpoint security solution will all the bells and whistles. Trend Micro product strategy: Better together. Trend Micro talks about connected threat defense, which brings together several its individual endpoint, network, and cloud products together as an integrated cybersecurity technology architecture. Good timing, as ESG research indicates that 62% of organizations would be willing to buy a majority of their cybersecurity products from a single enterprise-class vendor. For example, TippingPoint IDS/IPS is tightly integrated with Deep Discovery, Trend Micro's malware detection sandbox, while Deep Security, Trend Micro's cloud workload security offering, integrates with both of these products. As part of its business strategy, Trend Micro is working with customers to replace discrete point tools with Trend Micro products and reap integration benefits such as improved threat prevention/detection while streamlining security operations. Moving toward managed services. While Trend Micro engineered its EDR offering for ease of use, it recognizes that many organizations don't have the resources or skills to deploy, learn, or operate detection/response tools on their own. To work with these customers, Trend Micro is rolling out a managed detection and response service (MDR) as a complement to its products. Furthermore, Trend Micro is spinning out a new company called Cysiv, which offers several other advanced managed security services. With these moves, Trend Micro is demonstrating that it wants to play a direct role in the growing market for security services – rather than an indirect role as an arms dealer alone. All in on cloud security. Trend Micro jumped on the server virtualization and cloud computing bandwagons early by forming tight partnerships with VMware, Amazon, and Microsoft. Now that every other established vendor and VC-backed startup is all in on the cloud, Trend Micro is moving beyond basic cloud security support. For example, Trend Micro cloud security products are tightly-coupled with its connected threat defense for prevention/detection. From a cloud perspective, Trend Micro has gotten very familiar with application developers and DevOps to make sure that Trend Micro cloud security products fit seamlessly into a CI/CD pipeline. Trend Micro has also expanded its purview to cover containers micro-services, and even cloud-based application security. In this way, Trend Micro is aligning with cloud innovation and culture – not just hawking security products. More business investment. Over the past five years, Trend Micro business has gone through some significant shifts. For example, a larger percentage of the company's revenue comes from commercial sales rather than consumer sales, while Trend Micro has seen rapid market growth in North America. Trend Micro will hire engineers, expand sales staff, and service channel partners to keep this momentum going. | Malware Threat Guideline | |||
| 2018-10-19 11:22:00 | (Déjà vu) Cybersecurity Trends – With Trend Micro (lien direct) | Last week, Trend Micro came to Boston for its annual Trend Insights industry analyst event. The company provided an overview of its business, products, and strategy. Here are a few of my take-aways: Trend is prepared for the next chapter in endpoint security. To maintain its market leadership, Trend Micro is rolling out ApexOne, its newest endpoint security product. ApexOne provides more prevention/detection capabilities while consolidating all endpoint security functions onto a single agent. Trend has also decided to swim against the industry tide by including EDR as part of its core commercial endpoint security product, thus all customers who upgrade will get Trend EDR, alleviating the need to shop elsewhere. ApexOne will be an easy decision for existing Trend Micro customers and may be an attractive alternative for CISOs looking for an endpoint security solution will all the bells and whistles. Trend product strategy: Better together. Trend talks about connected threat defense which brings together several its individual endpoint, network, and cloud products together as an integrated cybersecurity technology architecture. Good timing as ESG research indicates that 62% of organizations would be willing to buy a majority of their cybersecurity products from a single enterprise-class vendor. For example, TippingPoint IDS/IPS is tightly integrated with Deep Discovery, Trend's malware detection sandbox while Deep Security, Trend's cloud workload security offering integrates with both of these products. As part of its business strategy, Trend is working with customers to replace discrete point tools with Trend products and reap integration benefits like improved threat prevention/detection while streamlining security operations. Moving toward managed services. While Trend engineered its EDR offering for ease-of-use, it recognizes that many organizations don't have the resources or skills to deploy, learn, or operate detection/response tools on their own. To work with these customers, Trend Micro is rolling out a managed detection and response service (MDR) as a complement to its products. Furthermore, Trend is spinning out a new company called Cysiv which offers several other advanced managed security services. With these moves, Trend is demonstrating that it wants to play a direct role in the growing market for security services – rather than an indirect role as an arms dealer alone. All in on cloud security. Trend Micro jumped on the server virtualization and cloud computing bandwagons early by forming tight partnerships with VMware, Amazon, and Microsoft. Now that every other established vendor and VC-backed startup are all-in on the cloud, Trend is moving beyond basic cloud security support. For example, Trend cloud security products are tightly-coupled with its connected threat defense for prevention/detection. From a cloud perspective, Trend has gotten very familiar with application developers and DevOps to make sure that Trend cloud security products fit seamlessly into a CI/CD pipeline. Trend has also expanded its purview to cover containers micro-services, and even cloud-based application security. In this way, Trend Micro is aligning with cloud innovation and culture – not just hawking security products. More business investment. Over the past 5 years, Trend Micro business has gone through some significant shifts. For example, a larger percentage of the company's revenue comes from commercial sales rather than consumer sales, while Trend has seen rapid market growth in North America. Trend Micro will hire engineers, expand sales staff, and service channel partners to keep this momentum going. In my humble opinion, Trend Micro remains a bit of a diamond in the rough – its security expertise and advanced techno | Malware Threat Guideline | |||
| 2018-10-16 11:47:00 | Best new Windows 10 security features: More patching, updating flexibility (lien direct) | With the new era of Windows as a service, Microsoft is rolling out changes to the operating system twice a year. Many of those changes will allow you to improve your security posture and offer more security choices. You no longer have to wait for a new operating system to deploy new security features. [ Learn how to identify, block and remove malware from Windows PCs. | Get the latest from CSO by signing up for our newsletters. ] Below is a summary of all the new security features and options in Windows 10 version 1809, which features Windows Defender Advanced Threat Protection (ATP) enhancements, more options for enterprises to update and patch Windows, and other security improvements. Bookmark this article, because we will be adding new security features as Microsoft releases future Windows updates. | Malware Threat | |||
| 2018-10-10 09:52:00 | Top cybersecurity facts, figures and statistics for 2018 (lien direct) | Looking for hard numbers to back up your sense of what's happening in the cybersecurity world? We dug into studies and surveys of the industry's landscape to get a sense of the lay of the land-both in terms of what's happening and how your fellow IT pros are reacting to it.Ransomware is down, cryptomining is up With last year's outbreak of NotPetya, ransomware-malicious programs that encrypt your files and demand a ransom payment in bitcoin to restore them-became one of the most talked about forms of malware of 2017. Yet at the same time, the actual rates of malware infection began to plummet around the middle of the year, until by December 2017 it represented only about 10 percent of infections. | Malware Studies | NotPetya | ||
| 2018-10-01 08:14:00 | New vicious Torii IoT botnet discovered (lien direct) | Torii – you might not have heard the name yet, but this new botnet has advanced techniques and persistence and is a threat to nearly every type of computer. Researchers from Avast warned about Torii, which is certainly no spinoff of Mirai. Torii, they said, is an “example of the evolution of IoT malware” and “its sophistication is a level above anything we have seen before.”For starters, Torii can run on almost every modern computer, smartphone, and tablet. Target architectures include x86_64, x86, ARM, MIPS, Motorola 68k, SuperH, PPC and others. Avast security researcher Martin Hron told The Parallax that one server had over 100 versions of malware payloads and supported 15 to 20 architectures. This suggests a “team effort,” as what Torii can do “would be hard for any on person to accomplish.” | Malware Threat | ★★ | ||
| 2018-09-25 13:42:00 | BrandPost: Malicious Tactics Have Evolved: Your DNS Needs to, Too (lien direct) | Unfortunately, as cyberthreats have evolved, over 86% of companies that leave DNS unmonitored have not modernized their DNS to help thwart malware before malicious adversaries exploit the glaring hole on the network. This blog looks at the ways threats have evolved to take advantage of legacy DNS, and what organizations should do now to increase their defenses and reduce their attack surface.Remember when cyberattacks were delivered via faxes from Nigerian princes? Although the objective – separating a business from its money – hasn't changed much, the methodologies certainly have. In the 80s and 90s, when enterprise networks were beginning to connect to the internet, DNS was simply the phone book that translated domain name to IP address. Soon enough, bad actors evolved from phreaking to phishing, dropping telephone scams in favor of the rapidly spreading internet, bombarding users with seemingly innocuous emails whose goal was to harvest network account and password information to gain inside access to applications, data, and ultimately money. | Malware | |||
| 2018-09-25 08:20:00 | (Déjà vu) First known malicious cryptomining campaign targeting Kodi discovered (lien direct) | Is your Kodi secretly mining Monero? Yes, sadly some cyber thugs have weaponized the media streaming app by hiding malware in Kodi add-ons. Researchers discovered the first known malicious cryptomining campaign to be launched via the Kodi platform. There are still about 5,000 victims unknowingly mining Monero via their Kodi for the cyber thugs.Ah, man, say it ain't so.Despite Kodi malware scare stories, there's been only one known time that malware was distributed via a Kodi add-on. But that hasn't stopped some anti-piracy groups from claiming Kodi was being used to distribute malware. [ Get inside the mind of a hacker, learn their motives and their malware. | Sign up for CSO newsletters. ] | Malware | |||
| 2018-09-25 08:20:00 | (Déjà vu) First known malicious cryptomining campaign targeting Kodi (lien direct) | Is your Kodi secretly mining Monero? Yes, sadly some cyberthugs have weaponized Kodi by hiding malware in Kodi add-ons. Researchers discovered the first known malicious cryptomining campaign to be launched via the Kodi platform. There are still about 5,000 victims unknowingly mining Monero via their Kodi for the cyberthugs.Ah man, say it ain't so. Despite Kodi malware scare stories, there's been only one known time that malware was distributed via a Kodi add-on. That hasn't stopped some anti-piracy groups from claiming Kodi was being used to distribute malware.For example, after a watching a video interview filmed at RSA about “how malware is growing on the Kodi/XMBC platform,” Torrent Freak scoffed. The group the interviewee worked with had been putting out Kodi-related malware scare stories to promote anti-piracy. Despite the alarming claims made which were short on actual facts, as far as Torrent Freak knew, only one Kodi addon had ever been used for DDoS purposes and that was back in 2017. The XBMC Foundation president had not heard of malware in a video stream and a threat analyst at BitDefender had not seen any malware in a video stream in the wild since in 2005. | Malware Threat | |||
| 2018-09-18 07:44:00 | (Déjà vu) Sophisticated mobile spyware Pegasus found in the US and 44 other countries (lien direct) |
In a new report, Citizen Lab researchers warned that sophisticated mobile spyware, dubbed Pegasus - made and sold by the Israeli company NSO Group - has been found not only on Androids and iPhones in countries with questionable human rights protections, but also in the U.S. The researchers believe this cross-border surveillance likely breaks the law in the U.S. and other countries.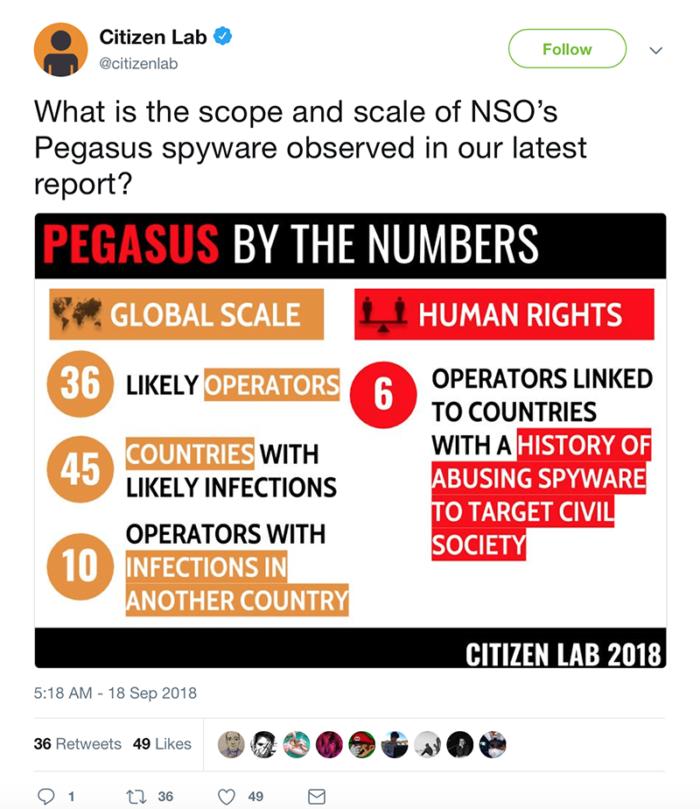 Citizen Lab via Twitter
To become an NSO Pegasus infection victim, the operator has to trick a person into clicking a link that then delivers a chain of zero-day exploits and secretly installs Pegasus on the phone. After the malware installs on the target's iPhone or Android phone without the user's knowledge, it is then capable of spying via the phone's camera and microphone. It can also steal text messages, passwords, photos, contact list, calendar events, and much more. Citizen Lab via Twitter
To become an NSO Pegasus infection victim, the operator has to trick a person into clicking a link that then delivers a chain of zero-day exploits and secretly installs Pegasus on the phone. After the malware installs on the target's iPhone or Android phone without the user's knowledge, it is then capable of spying via the phone's camera and microphone. It can also steal text messages, passwords, photos, contact list, calendar events, and much more. |
Malware | |||
| 2018-09-18 07:44:00 | (Déjà vu) Sophisticated mobile spyware Pegasus found in US and 44 other countries (lien direct) | In a new report, Citizen Lab researchers warned that sophisticated mobile spyware, dubbed Pegasus – made and sold by the Israeli company NSO Group – has been found not only on Androids and iPhones in countries with questionable human rights protections, but also in the US. The researchers believe this cross-border surveillance likely breaks the law in the US and other countries.To become an NSO Pegasus infection victim, the operator has to trick a person into clicking a link which then delivers a chain of zero-day exploits and secretly installs Pegasus on the phone. After the malware installs on the target's iPhone or Android phone without the user's knowledge, it is then capable of spying via the phone's camera and microphone; it can also steal text messages, passwords, photos, contact list, calendar events and much more. | Malware | ★★★★★ | ||
| 2018-09-11 07:00:00 | BrandPost: Cybersecurity Skills Report: Today\'s CISO is Shifting Toward Strategic Business Enablement (lien direct) | Businesses and government agencies of all sizes are experiencing cyber attacks that are growing in both frequency and complexity. Cybercriminals, nation-states, and a host of other bad actors are developing new tactics, tools, and procedures to circumvent modern cybersecurity solutions. We are increasingly seeing targeted attacks employing customized malware and the ready availability of dark web market tools and services covering every aspect of the cyber kill chain. In fact, a recent Fortinet Global Threat Landscape Report shows that virtually no firm is immune, with 96% of firms experiencing at least one severe exploit. | Malware Threat | |||
| 2018-09-04 08:04:00 | (Déjà vu) 7,500 MikroTik routers compromised, traffic forwarded to attackers (lien direct) | If you have a MikroTik router, make sure it is running the latest firmware, as security researchers discovered thousands of compromised MikroTik routers are sending traffic to nine attacker-controlled IPs.Via a honeypot since July, researchers from the China-based Netlab 360 noticed malware exploiting MikroTik routers. Attackers are exploiting the MikroTik CVE-2018-14847 flaw that was patched in April.The critical vulnerability, involving Winbox for MikroTik, “allows remote attackers to bypass authentication and read arbitrary files.” Proof-of-concept exploits have been around for several months. That same vulnerability, the researchers pointed out, was exploited by the CIA's hacking tool Chimay Red, according to WikiLeaks Vault7. | Malware Tool | |||
| 2018-09-04 08:04:00 | (Déjà vu) 7,500 MikroTik routers being eavesdropped, traffic forwarded to attackers (lien direct) | If you have a MikroTik router, then take the time to make sure it is running the latest firmware since security researchers discovered thousands of compromised MikroTik routers are sending traffic to nine attacker-controlled IPs.Via a honeypot since July, researchers from the China-based Netlab 360 noticed malware exploiting MikroTik routers. Attackers are exploiting the MikroTik CVE-2018-14847 flaw which was patched in April. | Malware | |||
| 2018-09-04 07:00:00 | BrandPost: Unidentified Devices Leave Networks Vulnerable (lien direct) | As organizations embrace digital transformation to improve operational efficiency, IoT devices-including industrial and medical IoT-are being deployed at an unprecedented rate. This rapid adoption of IoT is one of the primary reasons why networks are in constant flux. New devices, whether physical or virtual, are continually connecting and disconnecting from the network, and often then reconnecting somewhere else. And to do their job, they need immediate access to applications and networked resources.Internet of Things endpoints are growing at an unprecedented rate, reaching an installed base of several dozen billion units in just a few years. While most people imagine digital cameras, printers, and smart appliances when they think of IoT, it also includes medical IoT (MIoT) devices, such as infusion pumps and heart monitors, and industrial IoT (IIoT), including valve controllers, temperature and pressure monitors, and manufacturing devices. This trend hasn't gone unnoticed by the cybercriminal community. While there continue to be high-profile attacks targeting traditional IoT devices, MIoT and IIoT devices are also increasingly being targeted, such as the recent Triton and VPNFilter malware attacks. | Malware | VPNFilter | ||
| 2018-08-30 11:50:00 | The 6 best password managers (lien direct) | One of the smartest moves you can make to protect yourself online is to use a password manager. It's one of the easiest, too. We'll help you find the best password manager for you. [ Learn how to identify, block and remove malware from Windows PCs. | Get the latest from CSO by signing up for our newsletters. ] A properly designed password manager is an excellent first step in securing your online identity. It generates a unique strong password for every account and application, without requiring you to memorize or write down these random strings of characters. These strong passwords help shield against traditional password attacks such as dictionary, rainbow tables or brute-force attacks. | Malware | |||
| 2018-08-29 09:00:00 | BrandPost: The Evolving Threat Landscape - Swarmbots, Hivenets, Automation in Malware (lien direct) | Over the past several months, the FortiGuard Labs team has been tracking a number of evolving trends related to the FortiGuard 2018 Threat Landscape Predictions article published just before the beginning of the year. This mid-year update provides new details concerning recent advances in some of the techniques and malware tied to those predictions. In particular, the accelerated development of several precursors of Swarmbots and Hivenets are especially worth revisiting. Others include the increased targeting of critical infrastructure, the development of automation in malware exploits, and the use of blockchain technology to anonymize the command and control of botnets. | Malware Threat | |||
| 2018-08-29 07:45:00 | (Déjà vu) Cryptojacking attacks spiked in first half of 2018 (lien direct) | Cryptojacking attacks have skyrocketed, locking in cryptojacking attempts as having the biggest security impact in the first half of 2018. So far this year, there has been a 141 percent increase in cryptocurrency mining detections compared to the previous half year and 47 new cryptocurrency miner malware families detected.The good news, according to Trend Micro's 2018 midyear security roundup report (pdf), is that cyberthugs are relying less on ransomware since ransomware attacks are up only 3 percent from the second half of 2017. | Ransomware Malware | |||
| 2018-08-29 07:45:00 | (Déjà vu) Cryptojacking attacks spiked in first half of 2018, report (lien direct) | Cryptojacking attacks have skyrocketed, locking in cryptojacking attempts as having the biggest security impact in the first half of 2018. So far this year, there has been a 141 percent increase in cryptocurrency mining detections compared to the previous half year and 47 new cryptocurrency miner malware families detected.The good news, according to Trend Micro's 2018 midyear security roundup report (pdf), is that cyberthugs are relying less on ransomware since ransomware attacks are up only 3 percent from the second half of 2017. | Ransomware Malware | ★★★★★ | ||
| 2018-08-27 03:00:00 | What are next generation firewalls? How the cloud and complexity affect them (lien direct) | Traditional firewalls track the domains that traffic is coming from and the ports it's going to. Nextgen firewalls go beyond that -- they also monitor the content of the messages for malware and data exfiltration and can react in real time to stop threats. The newest iterations do even more, adding behavioral analytics, application security, zero-day malware detection, support for cloud and hybrid environments, and even endpoint protection. [ Find out how 4 deception tools deliver truer network security. | Get the latest from CSO by signing up for our newsletters. ] | Malware | ★★★ | ||
| 2018-08-14 09:08:00 | Security flaws in police body cameras open the devices to attack (lien direct) | Police body cameras are riddled with security vulnerabilities that could allow a hacker to remotely tweak or delete footage, track the cops wearing them, or weaponize the bodycam by installing malware such as ransomware that could be spread to other devices in a police station.Josh Mitchell, aka @bx_lr, a consultant at the security firm Nuix, pointed out a plethora of critical security issues with police body cameras during his presentation at Def Con. After analyzing bodycams by Vievu, Patrol Eyes, Fire Cam, Digital Ally, and CeeSc, Mitchell said some of the vulnerabilities that could be remotely exploited were appalling. | Ransomware Malware | ★★★★ | ||
| 2018-08-09 02:56:00 | What is malware? Viruses, worms, trojans, and beyond (lien direct) | Malware-a blanket term for viruses, worms, trojans, and other harmful computer programs-has been with us since the early days of computing. But malware is constantly evolving and hackers use it to wreak destruction and gain access to sensitive information; fighting malware takes up much of the day-to-day work of infosec professionals.Malware definition Malware is short for malicious software, and, as Microsoft puts it, "is a catch-all term to refer to any software designed to cause damage to a single computer, server, or computer network." In other words, software is identified as malware based on its intended use, rather than a particular technique or technology used to build it. | Malware | |||
| 2018-08-08 07:45:00 | (Déjà vu) Weaponized AI and facial recognition enter the hacking world (lien direct) | Meet Social Mapper, a facial recognition tool that searches for targets across numerous social networks, and the highly evasive and highly targeted AI-powered malware DeepLocker.Open-source Social Mapper face recognition tool The open-source intelligence-gathering tool Social Mapper uses facial recognition to automatically search for targets across eight social media sites: Facebook, Twitter, LinkedIn, Instagram, Google+, the Russian social networking service VKontakte, and the Chinese social networking sites Weibo and Douban. | Malware Tool | |||
| 2018-08-08 07:45:00 | (Déjà vu) AI-powered DeepLocker malware attacks and face recognition Social Mapper tracking tool (lien direct) | Meet Social Mapper, a facial recognition tool that searches for targets across numerous social networks, and the highly evasive and highly targeted AI-powered malware DeepLocker.Open-source Social Mapper face recognition toolThe open-source intelligence-gathering tool Social Mapper uses facial recognition to automatically search for targets across eight social media sites: Facebook, Twitter, LinkedIn, Instagram, Google+, the Russian social networking service VKontakte and the Chinese social networking sites Weibo and Douban. | Malware Tool | |||
| 2018-07-24 03:48:00 | 8 types of malware and how to recognize them (lien direct) | People tend to play fast and loose with security terminology. However, it's important to get your malware classifications straight because knowing how various types of malware spread is vital to containing and removing them.This concise malware bestiary will help you get your malware terms right when you hang out with geeks. [ Next-generation endpoint security tools are ready to replace antivirus. | Get the latest from CSO by signing up for our newsletters. ] | Malware | |||
| 2018-07-23 02:58:00 | Review: Zero tolerance malware and code blocking with Solebit (lien direct) | The one thing that all malware has in common is that it's comprised of computer code. But in cybersecurity, so is everything else. Lots of companies have tried to make the distinction between good and bad code, whether by comparing samples to the signatures of bad files, setting programs into a sandbox and seeing what they do, or applying artificial intelligence and machine learning to behavioral analytics while examining how a file acts. None of those methods has been entirely successful, and some, like signature-based protection, are almost completely outflanked by today's most advanced malware. | Malware | |||
| 2018-07-19 11:16:00 | IDG Contributor Network: The router of all evil (lien direct) | We spend a lot of time researching and highlighting the dangers of IoT devices. Cameras, DVRs, thermostats, light bulbs, and even refrigerators, connected to the internet may be vulnerable to attacks and exploits.Still, there's one IoT device that everyone owns and, I'll wager, the vast majority of people forget about: the router.“The box,” as my parents call it, typically is happily blinking away in a forgotten corner of the house and left alone for years. These home routers recently became the target of a Russian malware campaign using what is known as “VPNfilter” malware. | Malware | VPNFilter | ||
| 2018-07-19 06:00:00 | BrandPost: The Value of Third Party Testing (lien direct) | We all wrestle with the challenges of security in today's digital marketplace. The security landscape and potential attack surfaces continue to expand, and malware and exploits continue to become more sophisticated. However, one of the most significant security challenges that organizations face is simply deciding which solutions they want to incorporate into their security strategy. Vendors are multiplying at a dizzying pace, and anyone who has even been partway around the block knows that data sheets and marketing materials aren't nearly as reliable as they could be. Moreover, given time and resource constraints, setting up a testbed and evaluating all potential solutions by hand is rarely a viable option. | Malware |
To see everything:
Our RSS (filtrered)
