What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2017-06-13 08:52:00 | Crash Override: Malware that took down a power grid may have been a test run (lien direct) | Two security firms have released reports about the malware which was used in the December 2016 Ukraine power outage, warning that the partial power outage in Kiev may have been test run; the malware could be leveraged against other countries, including the US.The malware, dubbed Crash Override in the Dragos report (pdf) and Industroyer in the ESET report (pdf), has nothing to do with espionage and everything to do with cyber-sabotage.Crash Override, Dragos says, “is the first ever malware framework designed and deployed to attack electric grids.†It could be “leveraged at multiple sites simultaneously.†Dragos founder Robert M. Lee told Reuters, “The malware is capable of causing outages of up to a few days in portions of a nation's grid, but is not potent enough to bring down a country's entire grid.â€To read this article in full or to leave a comment, please click here | ||||
| 2017-06-12 07:36:00 | South Korean web hosting company infected by Erebus ransomware (lien direct) | Nayana, a web hosting company in South Korea, suffered a ransomware attack over the weekend which resulted in more than a hundred Linux servers and thousands of websites being infected with Erebus ransomware. The initial ransom amount was astronomically high.Yesterday, I came across the news that a South Korean web hosting company had been infected by ransomware, but it was extremely short on details. The ransomware was Erebus; the attack occurred on Saturday and thousands of sites were reportedly infected.Today, Aju Business Daily provided more details. Nayana reportedly said 153 of its Linux servers were infected with Erebus. In turn, about 3,400 sites on the web hosting company's servers were also infected.To read this article in full or to leave a comment, please click here | ||||
| 2017-06-11 07:50:00 | Witcher 3 developers won\'t bow to extortion for stolen Cyberpunk 2077 files (lien direct) | With E3 (Electronic Entertainment Expo) starting this week, we can expect a flood of gaming news. It remains to be seen if the person or people trying to extort Polish game developer CD Projekt Red will choose this week to leak stolen Cyberpunk 2077 game files.Instead of staying quiet about an extortion attempt, CD Projekt Red, the developers behind The Witcher 3, got out ahead of any potential leak by tweeting: An unidentified individual or individuals have just informed us they are in possession of a few internal files belonging to CD PROJEKT RED. Among them are documents connected to early designs for the upcoming game, Cyberpunk 2077.To read this article in full or to leave a comment, please click here | ||||
| 2017-06-08 08:15:00 | IDG Contributor Network: Top 5 InfoSec concerns for 2017 (lien direct) | Cloudbleed, WannaCry, ransomware, hackers. Each and every day, it seems, the tech community wakes up to news of another attack on data security and privacy. As IT professionals, we spend our days working to the best of our knowledge and ability to keep company information secure. Some days, however, when news of new attacks hit, it can feel like we'll never get ahead. As soon as we learn one method of protection, the hackers have invented a new workaround.To read this article in full or to leave a comment, please click here | Wannacry | |||
| 2017-06-05 06:52:00 | Hackers leak 8 unaired episodes of ABC\'s Steve Harvey\'s Funderdome TV series (lien direct) | They're back…The Dark Overlord, the hacking group which released 10 of 13 new Orange Is the New Black episodes in late April after Netflix refused to pay a ransom, has now leaked nearly the entire first season of ABC's upcoming Steve Harvey's Funderdome.Back in April, TDO warned ABC, National Geographic, Fox and IFC that the group wasn't playing games anymore. Then on June 2, TDO tweeted, “American Broadcasting Company may be up next, ladies and gentlemen.â€To read this article in full or to leave a comment, please click here | ||||
| 2017-06-02 06:37:00 | OneLogin hack exposed sensitive US customer data and ability to decrypt data (lien direct) | OneLogin, an identity management company which provides a single sign-on platform for logging into multiple apps and sites, was hacked. US customer data was potentially compromised,“including the ability to decrypt encrypted data.â€The company, which claims “over 2000+ enterprise customers in 44 countries across the globe trust OneLogin,†announced the security incident on May 31. It was short on details, primarily saying the unauthorized access it detected had been blocked and law enforcement was notified.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-31 05:26:00 | IDG Contributor Network: Nothing new to (Wanna)Cry about (lien direct) | The WannaCry outbreak has been troubling in many regards – exposing flaws, and opening doors to much finger-pointing and blaming that have gone well beyond the handling and disclosure of nation-state cyber weapon stockpiling.The attackers likely had a good idea of how quickly and widely the attack would spread, evidenced by the fact that their ransom demand was created in 28 languages, suggesting that they had very high expectations of the success of their attack.WannaCry targeted Microsoft systems that were not running the latest patches, and older versions of Windows such as Windows XP, which is still widely deployed in the NHS despite being 16 years old and no longer supported by Microsoft, except under custom contracts.To read this article in full or to leave a comment, please click here | Wannacry | |||
| 2017-05-24 06:48:00 | Hackers can use malicious subtitles to remotely take control of your device (lien direct) | Do you use Kodi, Popcorn Time, VLC or Stremio? Do you use subtitles while you watch? If so, then you need to update the platform as Check Point researchers revealed that not all subtitles are benign text files and hackers can remotely take control of any device running vulnerable software via malicious subtitles.The attack is not in the wild, since Check Point developed the proof of concept attack vector; however, with news of the attack vector and an estimated 200 million video players and streaming apps running vulnerable software, attackers might jump on the malicious subtitle wagon to gain remote access to victims' systems.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-23 09:35:00 | IDG Contributor Network: Educating the public about security – are we doing it all wrong? (lien direct) | In 2016 consumers were exposed to a larger number of high profile data breaches than any year previously. According to the Breach Level Index, 1,792 data breaches led to almost 1.4 million data records being compromised worldwide, an increase of 86% compared to 2015. Identity theft was the leading type of data breach last year, accounting for 59% of all data breaches. These numbers have helped raise public awareness around the serious threats to personal data that exist in the modern era, and awareness is also growing for some of the solutions that businesses and individuals can use to minimize the risks from data breaches. But is it enough?To read this article in full or to leave a comment, please click here | Guideline | |||
| 2017-05-18 09:25:00 | How to maintain data oversight to avoid \'shadow data\' (lien direct) | Data at risk Image by George HodanBefore his retirement, an employee of the Office of the Comptroller of the Currency (OCC) uploaded more than 10,000 OCC records onto two removable thumb drives. He retired in November 2015; the agency didn't discover the breach until the following September. That left almost a year between breach and detection. The OCC was not able to recover the thumb drives.To read this article in full or to leave a comment, please click here Image by George HodanBefore his retirement, an employee of the Office of the Comptroller of the Currency (OCC) uploaded more than 10,000 OCC records onto two removable thumb drives. He retired in November 2015; the agency didn't discover the breach until the following September. That left almost a year between breach and detection. The OCC was not able to recover the thumb drives.To read this article in full or to leave a comment, please click here |
||||
| 2017-05-16 08:13:45 | Shadow Brokers teases more Windows exploits and cyberespionage data (lien direct) | A group of hackers that previously leaked alleged U.S. National Security Agency exploits claims to have even more attack tools in its possession and plans to release them in a new subscription-based service.The group also has intelligence gathered by the NSA on foreign banks and ballistic missile programs, it said.The Shadow Brokers was responsible for leaking EternalBlue, the Windows SMB exploit that was used by attackers in recent days to infect hundreds of thousands of computers around the world with the WannaCry ransomware program.To read this article in full or to leave a comment, please click here | Wannacry | |||
| 2017-05-16 07:25:00 | Why WannaCry won\'t change anything (lien direct) | The tally of damage from the WannaCry ransomware attack keeps growing, but it's still not even close to bad enough to force real changes in cybersecurity. According to The New York Times, more than 200,000 machines in more than 150 countries around the world have been infected, but the responses being discussed still center around patches and passwords, updates and antivirus, backups and contingency plans. To read this article in full or to leave a comment, please click here | Wannacry | |||
| 2017-05-16 04:39:00 | Cybercrooks fight over DDoS attack resources (lien direct) | As more groups get into the denial-of-service attack business they're starting to get in each other's way, according to a report released this morning.That translates into a smaller average attack size, said Martin McKeay, senior security advocate at Cambridge, Mass.-based Akamai Technologies Inc.There are only so many devices around that have the kind of vulnerabilities that make them potential targets for a botnet."And other people can come in and take over the device, and take those resources to feed their own botnet," he said. "I'm seeing that over and over."To read this article in full or to leave a comment, please click here | ||||
| 2017-05-15 16:57:38 | Paying the WannaCry ransom will probably get you nothing. Here\'s why. (lien direct) | Last Friday's massive WannaCry ransomware attack means victims around the world are facing a tough question: Should they pay the ransom?Those who do shouldn't expect a quick response -- or any response at all. Even after payment, the ransomware doesn't automatically release your computer and decrypt your files, according to security researchers. Â Instead, victims have to wait and hope WannaCry's developers will remotely free the hostage computer over the internet. It's a process that's entirely manual and contains a serious flaw: The hackers have no way to prove who paid off the ransom."The odds of getting back their files decrypted is very small," said Vikram Thakur, technical director at security firm Symantec. "It's better for [the victims] to save their money and rebuild the affected computers."To read this article in full or to leave a comment, please click here | Wannacry | |||
| 2017-05-15 13:22:00 | 12 ways to improve run-time container security (lien direct) | This vendor-written tech primer has been edited by Network World to eliminate product promotion, but readers should note it will likely favor the submitter's approach.There still really aren't many enterprise run-time security tools for containers available, which has skewed the conversation toward establishing defensive barriers prior to run-time – during the build, integration, and deployment stage.Of course, with rapidly evolving technology like containers, it can be all too easy to overlook the most basic security concerns, so, really, any focus at all is welcome. Efforts pointing out the security advantages of digitally signing container images at build time, and scanning them before they are pushed to the registry, should indeed be heard. The OS should be hardened and attack surfaces should be trimmed where possible. Solutions like Seccomp and AppArmor that introduce security profiles between containers and the host kernel ought to be implemented.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-15 05:06:00 | Incident response is like tracking down a perpetrator (lien direct) | What is incident response? Image by ThinkstockIncident response is like investigating a real burglary. You look for evidence of the intruder at the crime scene, find his targets and his getaway car, and repair any holes. Discover any cuts in your chain link fence. Take a few steps back for more perspective. Find the intruder's targets. What assets are near the compromised fence? Investigate in both directions to find the intruder's target and getaway car. Fix the fence. Resolve any issues and patch vulnerabilities.To read this article in full or to leave a comment, please click here Image by ThinkstockIncident response is like investigating a real burglary. You look for evidence of the intruder at the crime scene, find his targets and his getaway car, and repair any holes. Discover any cuts in your chain link fence. Take a few steps back for more perspective. Find the intruder's targets. What assets are near the compromised fence? Investigate in both directions to find the intruder's target and getaway car. Fix the fence. Resolve any issues and patch vulnerabilities.To read this article in full or to leave a comment, please click here |
||||
| 2017-05-14 20:06:41 | Microsoft blames US stockpiled vulnerability for ransomware attack (lien direct) | Microsoft on Sunday said a software vulnerability stolen from the U.S. National Security Agency has affected customers around the world, and described the spread of the WannaCrypt ransomware on Friday in many countries as yet another example of the problems caused by the stockpiling of vulnerabilities by governments.Referring to the attack as a “wake-up call,†Microsoft's President and Chief Legal Officer, Brad Smith wrote in a blog post that governments have "to consider the damage to civilians that comes from hoarding these vulnerabilities and the use of these exploits."The ransomware, also called WannaCry or Wana Decryptor, works by exploiting a vulnerability in some older versions of Windows. It has been suspected for some time now that the malware came from a cache of hacking tools reportedly stolen by hacking group Shadow Brokers from the NSA and leaked on the internet. WannaCry is said to take advantage of a NSA hacking tool, called EternalBlue, that can make it easy to hijack unpatched older Windows machines.To read this article in full or to leave a comment, please click here | Wannacry | |||
| 2017-05-14 09:17:00 | New WannaCry ransomware variants: Patch old PCs now to avoid becoming a victim (lien direct) | Monday is going to suck for some folks, those who run old, unsupported Windows systems which are vulnerable to WannaCry ransomware, if they didn't put in some weekend time applying security updates.In response to the massive global ransomware attack on Friday, Microsoft took the “highly unusual step of providing a security update for all customers to protect Windows platforms that are in custom support only, including Windows XP, Windows 8, and Windows Server 2003.†Europol chief Rob Wainwright told the BBC, “Companies need to make sure they have updated their systems and 'patched where they should' before staff arrived for work on Monday morning.â€To read this article in full or to leave a comment, please click here | Wannacry | |||
| 2017-05-13 12:14:00 | Old Windows PCs can stop WannaCry ransomware with new Microsoft patch (lien direct) | Users of old Windows systems can now download a patch to protect them from this week's massive ransomware attack.In a rare step, Microsoft published a patch for Windows XP, Windows Server 2003 and Windows 8 -- all of them operating systems for which it no longer provides mainstream support.Users can download and find more information about the patches in Microsoft's blog post about Friday's attack from the WannaCry ransomware.The ransomware, which has spread globally, has been infecting computers by exploiting a Windows vulnerability involving the Server Message Block protocol, a file-sharing feature.To read this article in full or to leave a comment, please click here | Wannacry | |||
| 2017-05-12 18:24:53 | A \'kill switch\' is slowing the spread of WannaCry ransomware (lien direct) | Friday's unprecedented ransomware attack may have stopped spreading to new machines -- at least briefly -- thanks to a "kill switch" that a security researcher has activated.The ransomware, called Wana Decryptor or WannaCry, has been found infecting machines across the globe. It works by exploiting a Windows vulnerability that the U.S. National Security Agency may have used for spying.The malware encrypts data on a PC and shows users a note demanding $300 in bitcoin to have their data decrypted. Images of the ransom note have been circulating on Twitter. Security experts have detected tens of thousands of attacks, apparently spreading over LANs and the internet like a computer worm.To read this article in full or to leave a comment, please click here | Wannacry | |||
| 2017-05-12 10:22:12 | A ransomware attack is spreading worldwide, using alleged NSA exploit (lien direct) | A ransomware attack appears to be spreading around the world, leveraging a hacking tool that may have come from the U.S. National Security Agency.The ransomware, called Wanna Decryptor, struck hospitals at the U.K.'s National Health Service on Friday, taking down some of their network.Spain's computer response team CCN-CERT has also warned of a "massive attack" from the ransomware strain, amid reports that local telecommunications firm Telefonica was hit.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-12 09:53:00 | England hospitals hit by coordinated ransomware attack (lien direct) | Hospitals across England have fallen victim to what appears to be a coordinated ransomware attack that has affected facilities diverting patients to hospitals not hit by the malware.The attackers are asking for $300 in Bitcoin to decrypt affected machines, payable within 24 hours or the ransom doubles. If the victims don't pay within seven days, they lose the option to have the files decrypted, according to U.K. press reports.While multiple healthcare facilities have been hit, the country's health service says other types of groups have also fallen victim.According to The Register, a spokesperson for the country's National Health Service's digital division said: "The investigation is at an early stage but we believe the malware variant is Wanna Decryptor.†The spokesperson said the attack was not specifically targeted at the NHS, but affects organizations across a range of sectors, but didn't specify which.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-11 09:26:36 | Latest firmware updates for Asus routers fix CSRF security flaws (lien direct) | Users of Asus RT-N and RT-AC series routers should install the latest firmware updates released for their models because they address vulnerabilities that could allow attackers to hijack router settings.The flaws were discovered by researchers from security consultancy outfit Nightwatch Cybersecurity and leave many Asus router models exposed to cross-site request forgery (CSRF) attacks.CSRF is an attack technique that involves hijacking a user's browser when visiting a specially crafted website and forcing it to send unauthorized requests to a different website -- or in this case, the router web-based administration interface accessible over the local area network (LAN).To read this article in full or to leave a comment, please click here | ||||
| 2017-05-09 15:53:27 | How to protect your Google and Facebook accounts with a security key (lien direct) |
In late March when I got an unsettling message on my Gmail account: "Warning: Google may have detected government-backed attackers trying to steal your password."Google sends them out when it detects a "government-backed attacker" has attempted to hack an account through phishing or malware.Last time I saw one, I added two-factor authentication to many of my accounts. This time it prompted me to ask: Can I do even better?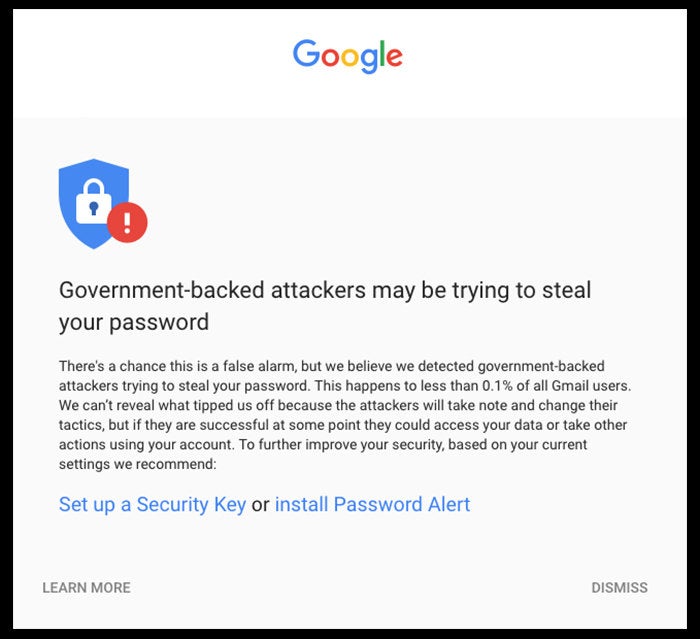 Martyn Williams/IDGNS
A security warning message displayed by Google.To read this article in full or to leave a comment, please click here Martyn Williams/IDGNS
A security warning message displayed by Google.To read this article in full or to leave a comment, please click here |
||||
| 2017-05-09 07:26:55 | Microsoft fixes remote hacking flaw in Windows Malware Protection Engine (lien direct) | Microsoft has released an update for the malware scanning engine bundled with most of its Windows security products in order to fix a highly critical vulnerability that could allow attackers to hack computers.The vulnerability was discovered by Google Project Zero researchers Tavis Ormandy and Natalie Silvanovich on Saturday and was serious enough for Microsoft to create and release a patch by Monday. This was an unusually fast response for the company, which typically releases security updates on the second Tuesday of every month and rarely breaks out of that cycle.Ormandy announced Saturday on Twitter that he and his colleague found a "crazy bad" vulnerability in Windows and described it as "the worst Windows remote code execution in recent memory."To read this article in full or to leave a comment, please click here | ||||
| 2017-05-08 08:04:45 | Supply chain attack hits Mac users of HandBrake video converter app (lien direct) | Hackers compromised a download server for HandBrake, a popular open-source program for converting video files, and used it to distribute a macOSÂ version of the application that contained malware.The HandBrake development team posted a security warning on the project's website and support forum on Saturday, alerting Mac users who downloaded and installed the program from May 2 to May 6 to check their computers for malware.The attackers compromised only a download mirror hosted under download.handbrake.fr, with the primary download server remaining unaffected. Because of this, users who downloaded HandBrake-1.0.7.dmg during the period in question have a 50/50 chance of having received a malicious version of the file, the HandBreak team said.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-07 09:25:00 | HandBrake mirror server hacked to serve up Proton RAT for Macs (lien direct) | If you recently downloaded the HandBrake app for Mac, then there's a good chance your system is infected with a nasty Remote Access Trojan (RAT).On Saturday, the HandBrake team posted a security alert after learning one of the mirror download servers was hacked. The attacker replaced the Mac version of the HandBrake client with a malicious version.In case you don't know, HandBrake is an open source video transcoder app which allows users to convert video to other formats.The HandBrake team said an attacker compromised the download mirror server at download.handbrake.fr and replaced the HandBrake-1.0.7.dmg installer file with a version infected with a new variant of the Proton RAT.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-05 17:59:08 | Email dump hits French candidate Macron ahead of election (lien direct) | Another political campaign has been hit by an email dump. This time, the target is French presidential candidate Emmanuel Macron.On Friday, his campaign said a massive and coordinated hack had breached the email inboxes of several staffers. This came after a mysterious user named “EMLEAKS†apparently dumped the stolen data through torrent files on text storage site Pastebin.It's unclear if the information in the dump is genuine. Allegedly, the dump contains a 9GB trove of emails and photos. The torrent files, which were hosted on Archive.org, are no longer available there.But Macron's campaign said the leaked files have been spreading over social media as the country prepares to vote for a new president on Sunday.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-04 16:20:18 | Google Docs phishing attack underscores OAuth security risks (lien direct) | Google has stopped Wednesday's clever email phishing scheme, but the attack may very well make a comeback.One security researcher has already managed to replicate it, even as Google is trying to protect users from such attacks.“It looks exactly like the original spoof,†said Matt Austin, director of security research at Contrast Security.The phishing scheme -- which may have circulated to 1 million Gmail users -- is particularly effective because it fooled users with a dummy app that looked like Google Docs.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-04 06:00:04 | The BlackBerry KeyOne - a surprising phone with a hardware keyboard (lien direct) | Here's a surprise: BlackBerry is back with a new handset and it's pretty good.I know, I know, you've heard this before. Several times over the last few years BlackBerry has attempted to make a comeback and each time it's come to nothing, so what's different now?For the first time the iconic BlackBerry hardware keyboard has been married with Android in the BlackBerry KeyOne. Combine those with several software apps from BlackBerry and the KeyOne is worth a look if you're shopping for a new smartphone, particularly if you spend a lot of time on email, social media or messaging.The handset is produced by TCL, a Chinese phone maker that recently acquired rights to the BlackBerry brand for smartphones. BlackBerry, based in Canada, is still responsible for the software.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-03 17:28:53 | Sneaky Gmail phishing attack fools with fake Google Docs app (lien direct) |
Google Docs was pulled into a sneaky email phishing attack on Tuesday that was designed to trick users into giving up access to their Gmail accounts.The phishing emails, which circulated for about three hours before Google stopped them, invited the recipient to open what appeared to be a Google Doc. The teaser was a blue box that said, “Open in Docs.â€In reality, the link led to a dummy app that asked users for permission to access their Gmail account. Reddit
An example of the phishing email that circulated on Tuesday.To read this article in full or to leave a comment, please click here Reddit
An example of the phishing email that circulated on Tuesday.To read this article in full or to leave a comment, please click here |
||||
| 2017-05-03 05:00:00 | IDG Contributor Network: Healthcare data breaches skyrocket, but is there good news coming? (lien direct) | In 2016, 328 individual healthcare breaches occurred, surpassing the previous record of 268 in 2015, according to Bitglass' recent Healthcare Breach Report. As a direct result of the breaches, records of approximately 16.6 million Americans were exposed due to hacks, lost or stolen devices, unauthorized disclosure and more.The good news, however, is that the overall number of compromised records has declined for the second year in a row, and early indications suggest that those numbers will continue to decline in 2017.+ Also on Network World:Â Healthcare records for sale on Dark Web + The report aggregates data from the U.S. Department of Health and Human Services' Wall of Shame-a database of breach disclosures required as part of the Health Insurance Portability and Accountability Act (HIPAA)-to identify the most common causes of data leakage.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-03 04:47:00 | False positives still cause threat alert fatigue (lien direct) | It is commonly referred to as information overload. An infosec professional throws out a wide net in hopes of stopping malware before it gets too deep into the network, but like a motion-sensor light, sometimes the alert catches a squirrel instead of a burglar.Rob Kerr, chief technology officer at Haystax Technology, cited the 2013 breach at Target, as an example in which thieves stole some 40 million Target credit cards by accessing data on point of sale (POS) systems. Target later revised that number to include theft of private data for 70 million customers.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-02 14:36:04 | Shodan search engine starts unmasking malware command-and-control servers (lien direct) | There's now a new tool that could allow companies to quickly block communications between malware programs and their frequently changing command-and-control servers.Threat intelligence company Recorded Future has partnered with Shodan, a search engine for internet-connected devices and services, to create a new online crawler called Malware Hunter.The new service continuously scans the internet to find control panels for over ten different remote access Trojan (RAT) programs, including Gh0st RAT, DarkComet, njRAT, ZeroAccess and XtremeRAT. These are commercial malware tools sold on underground forums and are used by cybercriminals to take complete control of compromised computers.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-02 08:34:24 | Android gets patches for critical flaws in media handling, hardware drivers (lien direct) | Android is getting security fixes for more than 100 vulnerabilities, including 29 critical flaws in the media processing server, hardware-specific drivers and other components.Android's monthly security bulletin, published Monday, was split into two "patch levels," which are represented as date strings on the "About" page of Android devices.The 2017-05-01 security patch level covers fixes for vulnerabilities that are common to all Android devices while the 2017-05-05 level covers additional fixes for hardware drivers and kernel components that are present only in some devices.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-02 04:37:00 | SMBs continue to be a target of cybercriminals (lien direct) | Because they don't see themselves as targets, small-to-midsize businesses (SMB) have for a long time believed that their security programs are good enough. They have a firewall, antivirus, maybe they even use two-factor authentication.The mistake is believing that this is enough because they have nothing of value to an attacker. While they may have a smaller attack surface, they are no less vulnerable than a major enterprise.Not only are small businesses growing as the favored targets for ransomware attacks, they are also the most impacted, with 60 percent shutting down within six months of a breach, according to the US National Cyber Security Alliance.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-01 17:36:57 | Vulnerability hits Intel enterprise PCs going back 10 years (lien direct) | Intel is reporting a firmware vulnerability that could let attackers take over remote management functions on computers built over nearly the past decade.The vulnerability, disclosed on Monday, affects features in Intel firmware that are designed for enterprise IT management. Â Enterprises using Intel Active Management Technology, Intel Small Business Technology and Intel Standard Manageability on their systems should patch them as soon as possible, the company says.The vulnerable firmware features can be found in some current Core processors and all the way back to Intel's first-generation Core, called Nehalem, which shipped in 2008. They're part of versions 6.0 through 11.6 of Intel's manageability firmware.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-01 12:45:00 | IDG Contributor Network: Data breaches: It\'s still personal (lien direct) | In a blog post last September, I highlighted how data breaches for the first half of 2016 shifted from stolen credit card data and financial information to the theft of something much more personal-identities. Unsurprisingly, this trend continued throughout the remainder of the year.According to the recently released Breach Level Index, 1,792 data breaches led to almost 1.4 million data records being compromised worldwide, an increase of 86 percent compared to 2015. Once again, identity theft was the leading type of data breach last year, accounting for 59 percent of all data breaches. To read this article in full or to leave a comment, please click here | Guideline | |||
| 2017-05-01 11:16:33 | Trump seeks to upgrade US government IT services (lien direct) | President Donald Trump is launching a special council to upgrade the U.S. government's IT services at a time when some systems more than 50 years old. Americans deserve better digital services from their government,†the"Americans deserve better digital services from their government," said an executive order from Trump, released on Monday.The order seeks to "promote the secure, efficient and economical use" of IT. As part of that goal, Trump is establishing the American Technology Council, which he will chair.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-01 10:36:00 | Report: Bad policies and practices put data at risk [Infographic] (lien direct) | Almost every company has data stored in its systems that is overexposed and at risk. That's the finding of the recently released 2017 Varonis Data Risk Report. The report is based on assessments that Varonis conducts for its customers and prospects to determine which data is at risk. The report data is aggregated and anonymized. download 2017 Varonis Data Risk Report Highlights Varonis What this year's report revealed is that much of the risk is due to bad policy or failure to follow an established policy. For example, files were accessible to people who should not have access, complex permissions rules negatively impacted enforceability, and some companies fail to properly audit data for risk. The report also found that these risks were consistent across geographies and industries.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-01 09:03:00 | (Déjà vu) The differences among the white, grey, and black hats (lien direct) | The infographic below provides good, entertaining definitions of the terms white hat, grey hat and black hat hackers courtesy of Exigent Networks. As the infographic explains, there are some, well, grey areas between categories-for example, there is sometimes a fine line between grey hats and black hats.Some might also disagree with the choices of white hat hacker examples. The telecom industry, for example, might consider Steve Wozniak's early hacking exploits theft of services rather than hacking for the greater good. And Julian Assange's qualifications will be tinted by whatever political lens through which an individual judges his actions.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-01 07:11:00 | Facebook able to target emotionally vulnerable teens for ads (lien direct) | Facebook is so proud of its algorithms that it conducted research about exploiting posts by kids as young as 14 to show how its algorithms could help advertisers pinpoint emotionally vulnerable moments for the purpose of targeted ads.The Australian (paywall) got its hands on a 23-page Facebook document, dated in 2017, marked as “Confidential: Internal Only,†and authored by two Australian Facebook executives, Andy Sinn and David Fernandez. While no screenshots were included, the report allegedly explained how Facebook could analyze posts, photos and interactions to help determine the emotional states of 6.4 million “high schoolers,†“tertiary†(college) students and “young Australians and New Zealanders ... in the workforce.â€To read this article in full or to leave a comment, please click here | ||||
| 2017-05-01 07:07:02 | NSA suggests using virtualization to secure smartphones (lien direct) | The U.S. National Security Agency is now suggesting government departments and businesses buy smartphones secured using virtualization, a technology it currently requires only on tablets and laptopsThe change comes about with the arrival of the first virtualization-based smartphone security system on the U.S. Commercial Solutions for Classified list.CSFC is a program developed by the NSA to help U.S. government agencies and the businesses that serve them to quickly build layered secure systems from approved components.An HTC A9 smartphone security-hardened by Cog Systems using its D4 virtualization platform is now on that list, alongside devices without virtualization from Samsung Electronics, LG Electronics, and BlackBerry.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-01 05:22:00 | Career Watch: Be wary of IT employment contracts (lien direct) | Jeffrey Scolaro, an attorney at Daley Mohan Groble PC in Chicago and a member of Legal Services Link, answers questions about employment contracts.Are employment contracts for IT workers negotiable, or are they one-size-fits-all? The axiom that “everything is negotiable†should be where all IT professionals begin their assessment of proposed employment contracts. However, the IT industry in particular can be especially rigid in its collective enforcement of employment agreements.To read this article in full or to leave a comment, please click here | APT 17 | |||
| 2017-05-01 05:18:00 | How the insurance industry could change the game for security (lien direct) | The recent growth in the cyber insurance market is already improving cybersecurity in some industry segments, and has the potential to do more -- if the industry is able to address its data problem.One area where cyber insurance has already made an impact is in the retail space, said David White, founder and COO at Axio Global, a cyber risk company.After the 2013 Target breach, it became very difficult for retailers to get a decent price for cyber insurance unless they had completely switched over to end-to-end encryption, or had a definite plan in place for doing that.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-01 03:51:00 | Network monitoring tools: Features users love and hate (lien direct) | Managing the health of the corporate network will directly affect the productivity of every user of that network. So network administrators need a robust network monitoring tool that helps them manage the network, identify problems before they cause downtime, and quickly resolve issues when something goes wrong.Five of the top network monitoring products on the market, according to users in the IT Central Station community, are CA Unified Infrastructure Management, SevOne, Microsoft System Center Operations Manager (SCOM), SolarWinds Network Performance Monitor (NPM), and CA Spectrum.To read this article in full or to leave a comment, please click here | ||||
| 2017-05-01 02:17:00 | (Déjà vu) New products of the week 5.1.17 (lien direct) | New products of the week Image by HPEOur roundup of intriguing new products. Read how to submit an entry to Network World's products of the week slideshow.Bluescape visual collaboration software Image by HPEOur roundup of intriguing new products. Read how to submit an entry to Network World's products of the week slideshow.Bluescape visual collaboration software Image by bluescapeTo read this article in full or to leave a comment, please click here Image by bluescapeTo read this article in full or to leave a comment, please click here |
||||
| 2017-04-30 08:25:00 | Hackers leak 10 new Orange Is the New Black episodes after Netflix failed to pay ransom (lien direct) | On Saturday, the hacking group The Dark Overlord followed through with threats to release 10 of 13 new Orange Is the New Black episodes that it had in its possession after Netflix failed to pay a ransom. The Dark Overlord, or TDO, allegedly has tried to extort money from other big networks as well and used the leak to threaten those networks.TDO tweeted: “Who is next on the list? FOX, IFC, NAT GEO, and ABC. Oh, what fun we're all going to have. We're not playing games anymore.†Who is next on the list? FOX, IFC, NAT GEO, and ABC. Oh, what fun we're all going to have. We're not playing any games anymore.To read this article in full or to leave a comment, please click here | ||||
| 2017-04-28 16:23:58 | NSA ends surveillance tactic that pulled in citizens\' emails, texts (lien direct) | The U.S. National Security Agency will no longer sift through emails, texts and other internet communications that mention targets of surveillance.The change, which the NSA announced on Friday, stops a controversial tactic that critics said violated U.S. citizens' privacy rights.The practice involved flagging communications where a foreign surveillance target was mentioned, even if that target wasn't involved in the conversation. Friday's announcement means the NSA will stop collecting this data.“Instead, this surveillance will now be limited to only those communications that are directly 'to' or 'from' a foreign intelligence target,†the NSA said in a statement.To read this article in full or to leave a comment, please click here | ||||
| 2017-04-28 13:33:10 | Stealthy Mac malware spies on encrypted browser traffic (lien direct) | A new malware program that targets macOS users is capable of spying on encrypted browser traffic to steal sensitive information.The new program, dubbed OSX/Dok by researchers from Check Point Software Technologies, was distributed via email phishing campaigns to users in Europe.One of the rogue emails was crafted to look as if it was sent by a Swiss government agency warning recipients about apparent errors in their tax returns. The malware was attached to the email as a file called Dokument.zip.What makes OSX/Dok interesting is that it was digitally signed with a valid Apple developer certificate. These certificates are issued by Apple to members of its developer program and are needed to publish applications in the official Mac App Store.To read this article in full or to leave a comment, please click here |
To see everything:
Our RSS (filtrered)
