What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-06-25 15:02:12 | Mon dernier e-mail avec W. Richard Stevens My Last Email with W. Richard Stevens (lien direct) |
& nbsp; À l'automne 1998, j'ai rejoint l'AFCERT.Je me suis familiarisé avec le livre incroyable TCP / IP Illustrated, Volume 1: The Protocols & nbsp; par W. Richard Stevens.Environ un an plus tard, j'ai échangé des courriels avec M. Stevens.Voici le dernier échange, comme transféré de mon adresse e-mail AFCERT à mon e-mail domestique. De "Capt Richard Bejtlich - Chief en temps réel" LON SEP & NBSP;6 18:27:35 1999 x-mozilla-keys: & nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp;& nbsp; reçu: de kinda.csap.af.mil (kinda.csap.af.mil [192.203.2.250]) & nbsp;& nbsp;& nbsp;& nbsp;& nbsp;par mw4.texas.net (2.4 / 2.4) avec smtp & nbsp;id raa22116 pour ;Lun, 6 septembre 1999 17:27:38 -0500 (CDT) Reçu: par Kinda.csap.af.mil (smail3.1.29.1 # 7) id m11o7ee-000ncwc;Lun, 6 sept. 99 17:27 CDT reçu: de Walt.ip.af.mil (192.168.1.142) par Kinda via SMAP (v1.3) id sma014865;LON SEP & NBSP;6 17:27:36 1999 reçu: de kinda.csap.af.mil by walt.ip.af.mil avec smtp (Smail3.1.29.1 # 6) ID M11O7ED-000VRUC;Lun, 6 sept. 99 22:27 gmt Sender: Bejtlich > Message-id: Date: lun, 06 septembre 1999 22:27:35 +0000 De: Capt Richard Bejtlich - RealTime Chief & nbsp; & nbsp; Organisation: afcert X-Mailer: Mozilla 4.6 [en] (x11; u; Sunos 5.6 Sun4u) X-Accept-Language: en MIME-Version: 1.0 à: bejtlich@texas.net Sujet: [FWD:Re: TCP / IP Illustrated Vol I 2nd ed?] | ★★ | |||
| 2023-06-25 14:36:50 | Radar des compétences et des intérêts Bejtlich à partir de juillet 2005 Bejtlich Skills and Interest Radar from July 2005 (lien direct) |
 C'est unis.J'ai trouvé ce diagramme de "radar d'intérêt" que j'ai créé en juillet 2005. Cela ressemble à ma tentative de capture et de hiérarchise les intérêts techniques.À l'époque, j'étais sur le point de commencer à consulter par moi-même, iirc. Copyright 2003-2020 Richard Bejtlich et Taosecurity (taosecurity.blogspot.com et www.taosecurity.com) C'est unis.J'ai trouvé ce diagramme de "radar d'intérêt" que j'ai créé en juillet 2005. Cela ressemble à ma tentative de capture et de hiérarchise les intérêts techniques.À l'époque, j'étais sur le point de commencer à consulter par moi-même, iirc. Copyright 2003-2020 Richard Bejtlich et Taosecurity (taosecurity.blogspot.com et www.taosecurity.com)
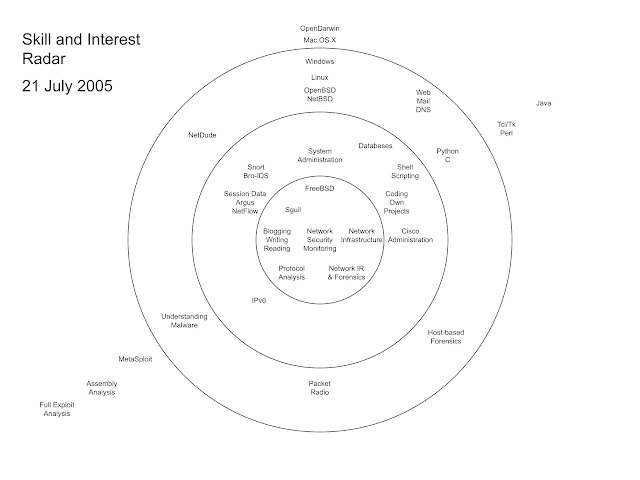 This is unusual. I found this "skills and interest radar" diagram I created in July 2005. It looks like my attempt to capture and prioritize technical interests. At the time I was about to start consulting on my own, IIRC.Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) This is unusual. I found this "skills and interest radar" diagram I created in July 2005. It looks like my attempt to capture and prioritize technical interests. At the time I was about to start consulting on my own, IIRC.Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
★★ | |||
| 2023-06-25 12:23:23 | Questions clés du réseau Key Network Questions (lien direct) |
& nbsp; | Cloud | ★★ | ||
| 2023-06-25 12:17:25 | La cybersécurité est un problème social, politique et méchant Cybersecurity Is a Social, Policy, and Wicked Problem (lien direct) |
★★★ | ||||
| 2023-06-25 12:14:05 | Nais compte d'écriture et de pages Core Writing Word and Page Counts (lien direct) |
 Notez les nombres de mots et de pages dans mes écrits de sécurité principaux. Le tao de la surveillance de la sécurité du réseau /236K MOTS / 833 pages Détection d'extrusion / 113k Mots / 417 pages La pratique de la surveillance de la sécurité du réseau / 97k mots / 380 pages Le meilleur de la taosecurityBlog, Vol 1/84K Words / 357 pages The Best of Taosecurity Blog, Vol 2 / 96K Words / 429 Pages Le Best of Taosecurity Blog, Vol 3 / 89K Words /485 pages Le blog Best of Tosecurity, Vol 4 / 96K Words / 429 pages Le total est 811k mots et 3 330 pages. Copyright 2003-2020 Richard Bejtlich et TaoseCurity (taosecurity.blogspot.com et www.taosecurity.com) Notez les nombres de mots et de pages dans mes écrits de sécurité principaux. Le tao de la surveillance de la sécurité du réseau /236K MOTS / 833 pages Détection d'extrusion / 113k Mots / 417 pages La pratique de la surveillance de la sécurité du réseau / 97k mots / 380 pages Le meilleur de la taosecurityBlog, Vol 1/84K Words / 357 pages The Best of Taosecurity Blog, Vol 2 / 96K Words / 429 Pages Le Best of Taosecurity Blog, Vol 3 / 89K Words /485 pages Le blog Best of Tosecurity, Vol 4 / 96K Words / 429 pages Le total est 811k mots et 3 330 pages. Copyright 2003-2020 Richard Bejtlich et TaoseCurity (taosecurity.blogspot.com et www.taosecurity.com)
 I want to make a note of the numbers of words and pages in my core security writings.The Tao of Network Security Monitoring / 236k words / 833 pagesExtrusion Detection / 113k words / 417 pagesThe Practice of Network Security Monitoring / 97k words / 380 pagesThe Best of TaoSecurity Blog, Vol 1 / 84k words / 357 pagesThe Best of TaoSecurity Blog, Vol 2 / 96k words / 429 pagesThe Best of TaoSecurity Blog, Vol 3 / 89k words / 485 pagesThe Best of TaoSecurity Blog, Vol 4 / 96k words / 429 pagesThe total is 811k words and 3,330 pages.Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) I want to make a note of the numbers of words and pages in my core security writings.The Tao of Network Security Monitoring / 236k words / 833 pagesExtrusion Detection / 113k words / 417 pagesThe Practice of Network Security Monitoring / 97k words / 380 pagesThe Best of TaoSecurity Blog, Vol 1 / 84k words / 357 pagesThe Best of TaoSecurity Blog, Vol 2 / 96k words / 429 pagesThe Best of TaoSecurity Blog, Vol 3 / 89k words / 485 pagesThe Best of TaoSecurity Blog, Vol 4 / 96k words / 429 pagesThe total is 811k words and 3,330 pages.Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
★★ | |||
| 2023-01-08 10:00:00 | Happy 20th Birthday TaoSecurity Blog (lien direct) |  Happy 20th birthday TaoSecurity Blog, born on 8 January 2003. Thank you BloggerBlogger (now part of Google) has continuously hosted this blog for 20 years, for free. I'd like to thank Blogger and Google for providing this platform for two decades. It's tough to find extant self-hosted security content that was born at the same time, or earlier. Bruce Schneier's Schneier on Security is the main one that comes to mind. If not for the wonderful Internet Archive, many blogs from the early days would be lost.StatisticsIn my 15 year post I included some statistics, so here are a few, current as of the evening of 7 January: Happy 20th birthday TaoSecurity Blog, born on 8 January 2003. Thank you BloggerBlogger (now part of Google) has continuously hosted this blog for 20 years, for free. I'd like to thank Blogger and Google for providing this platform for two decades. It's tough to find extant self-hosted security content that was born at the same time, or earlier. Bruce Schneier's Schneier on Security is the main one that comes to mind. If not for the wonderful Internet Archive, many blogs from the early days would be lost.StatisticsIn my 15 year post I included some statistics, so here are a few, current as of the evening of 7 January: I think it's cool to see almost 29 million "all time" views, but that's not the whole story.Here are the so-called "all time" statistics: I think it's cool to see almost 29 million "all time" views, but that's not the whole story.Here are the so-called "all time" statistics: It turns out that Blogger only started capturing these numbers in January 2011. That means I've had almost 29 million views in the last 12 years. I don't know what happened on 20 April 2022, when I had almost 1.5 million views?Top Ten Posts Since January 2011 It turns out that Blogger only started capturing these numbers in January 2011. That means I've had almost 29 million views in the last 12 years. I don't know what happened on 20 April 2022, when I had almost 1.5 million views?Top Ten Posts Since January 2011 |
Ransomware Studies Guideline | Solardwinds | ★★ | |
| 2022-11-20 09:30:10 | Best of TaoSecurity Blog Kindle Edition Sale (lien direct) |  I'm running a #BlackFriday #CyberMonday sale on my four newest #Kindle format books. Volumes 1-4 of The Best of TaoSecurity Blog will be half off starting 9 pm PT Tuesday 22 Nov and ending 9 pm PT Tueday 29 Nov. They are here. There also appears to be a daily deal right now for the paperback of Volume 2, 45% off at $8.96. Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) I'm running a #BlackFriday #CyberMonday sale on my four newest #Kindle format books. Volumes 1-4 of The Best of TaoSecurity Blog will be half off starting 9 pm PT Tuesday 22 Nov and ending 9 pm PT Tueday 29 Nov. They are here. There also appears to be a daily deal right now for the paperback of Volume 2, 45% off at $8.96. Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
||||
| 2022-11-18 15:37:23 | TaoSecurity on Mastodon (lien direct) |  I am now using Mastodon as a replacement for the blue bird. This is my attempt to verify myself via my blog. I am no longer posting to my old bird account.Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) I am now using Mastodon as a replacement for the blue bird. This is my attempt to verify myself via my blog. I am no longer posting to my old bird account.Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
||||
| 2022-08-10 09:30:00 | The Humble Hub (lien direct) |  Over the weekend I organized some old computing equipment. I found this beauty in one of my boxes. It's a Netgear EN104TP hub. I've mentioned this device before, in this blog and my books. This sort of device was the last of the true hubs. In an age where cables seem reserved for data centers or industrial facilities, and wireless rules the home and office, this hub is a relic of days gone past.To give you a sense of how old this device is, the Netgear documentation (still online -- well done) offers a PDF created in August 1998. (Again, well done Netgear, not mucking about with the timestamps.) I'm not sure how old my specific device is. Seeing as I started working in the AFCERT in the fall of 1998, I could see this hub being easily over 20 years old. A hub is a network device that accepts traffic from its ports and repeats the traffic to all other ports. This is different from a switch, which maintains a table identifying which MAC addresses are in use on which ports. Before building this CAM (content addressable memory, IIRC) table, traffic to a new previously unforeseen MAC address will appear on all ports save the sender.This is a "true hub" because all of the ports are 10 Mbps. Yes, that is 100 times "slower" than the Gigabit ports on modern devices, if they have Ethernet ports at all. Starting with 10/100 Mbps devices, they all became switches. I never encountered a 100 Mbps "hub." Every device I ever had hands on was a 10/100 Mbps switch. That meant you were unlikely to see traffic on all ports when using a 10/100 Mbps device or even a 100 Mbps device (which I never saw anyway). There were no Gigabit (1000 Mbps) hubs built. I don't think the specification even supports it.These little boxes were network monitoring enablers. If you wanted to learn, or troubleshoot, or possibly even add monitoring to a production network, you could connect an upstream cable, a downstream cable, and a monitoring cable to the hub. The upstream could be a router and the downstream might be a firewall, and the monitoring would be your NSM server. If you were looking at traffic between two individual computers and needed visibility for a NSM laptop, you would plug all three into the hub, and plug your Internet upstream into the fourth port.I haven't needed this device in years, but I plan to keep it as a physical artifact of a time long past. At least this one still powers on, unlike my first computer, a Timex Sinclair ZX-80.Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) Over the weekend I organized some old computing equipment. I found this beauty in one of my boxes. It's a Netgear EN104TP hub. I've mentioned this device before, in this blog and my books. This sort of device was the last of the true hubs. In an age where cables seem reserved for data centers or industrial facilities, and wireless rules the home and office, this hub is a relic of days gone past.To give you a sense of how old this device is, the Netgear documentation (still online -- well done) offers a PDF created in August 1998. (Again, well done Netgear, not mucking about with the timestamps.) I'm not sure how old my specific device is. Seeing as I started working in the AFCERT in the fall of 1998, I could see this hub being easily over 20 years old. A hub is a network device that accepts traffic from its ports and repeats the traffic to all other ports. This is different from a switch, which maintains a table identifying which MAC addresses are in use on which ports. Before building this CAM (content addressable memory, IIRC) table, traffic to a new previously unforeseen MAC address will appear on all ports save the sender.This is a "true hub" because all of the ports are 10 Mbps. Yes, that is 100 times "slower" than the Gigabit ports on modern devices, if they have Ethernet ports at all. Starting with 10/100 Mbps devices, they all became switches. I never encountered a 100 Mbps "hub." Every device I ever had hands on was a 10/100 Mbps switch. That meant you were unlikely to see traffic on all ports when using a 10/100 Mbps device or even a 100 Mbps device (which I never saw anyway). There were no Gigabit (1000 Mbps) hubs built. I don't think the specification even supports it.These little boxes were network monitoring enablers. If you wanted to learn, or troubleshoot, or possibly even add monitoring to a production network, you could connect an upstream cable, a downstream cable, and a monitoring cable to the hub. The upstream could be a router and the downstream might be a firewall, and the monitoring would be your NSM server. If you were looking at traffic between two individual computers and needed visibility for a NSM laptop, you would plug all three into the hub, and plug your Internet upstream into the fourth port.I haven't needed this device in years, but I plan to keep it as a physical artifact of a time long past. At least this one still powers on, unlike my first computer, a Timex Sinclair ZX-80.Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
||||
| 2021-07-29 14:34:54 | Zeek in Action Videos (lien direct) |  This is a quick note to point blog readers to my Zeek in Action YouTube video series for the Zeek network security monitoring project. Each video addresses a topic that I think might be of interest to people trying to understand their network using Zeek and adjacent tools and approaches, like Suricata, Wireshark, and so on. I am especially pleased with Video 6 on monitoring wireless networks. It took me several weeks to research material for this video. I had to buy new hardware and experiment with a Linux distro that I had not used before -- Parrot. Please like and subscribe, and let me know if there is a topic you think might make a good video.Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) This is a quick note to point blog readers to my Zeek in Action YouTube video series for the Zeek network security monitoring project. Each video addresses a topic that I think might be of interest to people trying to understand their network using Zeek and adjacent tools and approaches, like Suricata, Wireshark, and so on. I am especially pleased with Video 6 on monitoring wireless networks. It took me several weeks to research material for this video. I had to buy new hardware and experiment with a Linux distro that I had not used before -- Parrot. Please like and subscribe, and let me know if there is a topic you think might make a good video.Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
||||
| 2021-04-13 11:00:00 | New Book! The Best of TaoSecurity Blog, Volume 4 (lien direct) |  I've completed the TaoSecurity Blog book series.The new book is The Best of TaoSecurity Blog, Volume 4: Beyond the Blog with Articles, Testimony, and Scholarship. It's available now for Kindle, and I'm working on the print edition. I'm running a 50% off promo on Volumes 1-3 on Kindle through midnight 20 April. Take advantage before the prices go back up. I've completed the TaoSecurity Blog book series.The new book is The Best of TaoSecurity Blog, Volume 4: Beyond the Blog with Articles, Testimony, and Scholarship. It's available now for Kindle, and I'm working on the print edition. I'm running a 50% off promo on Volumes 1-3 on Kindle through midnight 20 April. Take advantage before the prices go back up. I described the new title thus:Go beyond TaoSecurity Blog with this new volume from author Richard Bejtlich.In the first three volumes of the series, Mr. Bejtlich selected and republished the very best entries from 18 years of writing and over 18 million blog views, along with commentaries and additional material. In this title, Mr. Bejtlich collects material that has not been published elsewhere, including articles that are no longer available or are stored in assorted digital or physical archives.Volume 4 offers early white papers that Mr. Bejtlich wrote as a network defender, either for technical or policy audiences. It features posts from other blogs or news outlets, as well as some of his written testimony from eleven Congressional hearings. For the first time, Mr. Bejtlich publishes documents that he wrote as part of his abandoned war studies PhD program. This last batch of content was only available to his advisor, Dr. Thomas Rid, and his review committee at King's College London.Read how the security industry, defensive methodologies, and strategies to improve national security have evolved in this new book, written by one of the authors who has seen it all and survived to blog about it.This will likely be my final collection of writings. I've discovered some documents that may be of interest to historians, so I may contribute those to a national security archive like my friend Jay Healey did a few years ago.The only other work I might do for these four volumes is to record Audible editions. That would take a while, but I'm thinking about it.Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) I described the new title thus:Go beyond TaoSecurity Blog with this new volume from author Richard Bejtlich.In the first three volumes of the series, Mr. Bejtlich selected and republished the very best entries from 18 years of writing and over 18 million blog views, along with commentaries and additional material. In this title, Mr. Bejtlich collects material that has not been published elsewhere, including articles that are no longer available or are stored in assorted digital or physical archives.Volume 4 offers early white papers that Mr. Bejtlich wrote as a network defender, either for technical or policy audiences. It features posts from other blogs or news outlets, as well as some of his written testimony from eleven Congressional hearings. For the first time, Mr. Bejtlich publishes documents that he wrote as part of his abandoned war studies PhD program. This last batch of content was only available to his advisor, Dr. Thomas Rid, and his review committee at King's College London.Read how the security industry, defensive methodologies, and strategies to improve national security have evolved in this new book, written by one of the authors who has seen it all and survived to blog about it.This will likely be my final collection of writings. I've discovered some documents that may be of interest to historians, so I may contribute those to a national security archive like my friend Jay Healey did a few years ago.The only other work I might do for these four volumes is to record Audible editions. That would take a while, but I'm thinking about it.Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
Studies | |||
| 2021-04-01 14:00:00 | The Origins of the Names TaoSecurity and the Unit Formerly Known as TAO (lien direct) |  What are the origins of the names TaoSecurity and the unit formerly known as TAO? IntroductionI've been reading Nicole Perlroth's new book This Is How They Tell Me the World Ends. Her discussion of the group formerly known as Tailored Access Operations, or TAO, reminded me of a controversy that arose in the 2000s. I had heard through back channels that some members of that group were upset that I was operating using the name TaoSeurity. In the 2000s and early 2010s I taught classes under the TaoSecurity brand, and even ran TaoSecurity as a single-person consultancy from 2005-2007. The purpose of this post is to explain why, how, and when I chose the TaoSecurity identity, and to show that it is contemporaneous with the formal naming of the TAO group. The most reliable accounts indicate TaoSecurity predates the TAO brand.TaoSecurity Began with Kung Fu and Taoism What are the origins of the names TaoSecurity and the unit formerly known as TAO? IntroductionI've been reading Nicole Perlroth's new book This Is How They Tell Me the World Ends. Her discussion of the group formerly known as Tailored Access Operations, or TAO, reminded me of a controversy that arose in the 2000s. I had heard through back channels that some members of that group were upset that I was operating using the name TaoSeurity. In the 2000s and early 2010s I taught classes under the TaoSecurity brand, and even ran TaoSecurity as a single-person consultancy from 2005-2007. The purpose of this post is to explain why, how, and when I chose the TaoSecurity identity, and to show that it is contemporaneous with the formal naming of the TAO group. The most reliable accounts indicate TaoSecurity predates the TAO brand.TaoSecurity Began with Kung Fu and Taoism With Sifu Michael Macaris, 21 June 1996In the summer of 1994, after graduating from the Air Force Academy and before beginning my graduate program at what is now called the Harvard Kennedy School, I started watching re-runs of the 1970s David Carradine Kung Fu TV series, created by Ed Spielman. I was so motivated by the philosophical message of the program that I joined a kung fu school in Massachusetts. I trained there for two years, and studied what I could about Chinese history and culture. I learned from the show and that it was based on Taoism (for example) so I bought a copy of the Tao Te Ching by Lao Tzu and devoured it. Visiting China With Sifu Michael Macaris, 21 June 1996In the summer of 1994, after graduating from the Air Force Academy and before beginning my graduate program at what is now called the Harvard Kennedy School, I started watching re-runs of the 1970s David Carradine Kung Fu TV series, created by Ed Spielman. I was so motivated by the philosophical message of the program that I joined a kung fu school in Massachusetts. I trained there for two years, and studied what I could about Chinese history and culture. I learned from the show and that it was based on Taoism (for example) so I bought a copy of the Tao Te Ching by Lao Tzu and devoured it. Visiting China Tai Chi on the Yangtze, May 1999In the spring of 1999 my wife and I took a three week trip to Chin Tai Chi on the Yangtze, May 1999In the spring of 1999 my wife and I took a three week trip to Chin |
Malware Threat | |||
| 2021-02-18 10:53:39 | Digital Offense Capabilities Are Currently Net Negative for the Security Ecosystem (lien direct) |  PropositionDigital offense capabilities are currently net negative for the security ecosystem.[0]The costs of improved digital offense currently outweigh the benefits. The legitimate benefits of digital offense accrue primarily to the security one percent (#securityonepercent), and to intelligence, military, and law enforcement agencies. The derived defensive benefits depend on the nature of the defender. The entire security ecosystem bears the costs, and in some cases even those who see tangible benefit may suffer costs exceeding those benefits.The ReasonLimitations of scaling are the reason why digital offense capabilities are currently net negative.Consider the case of an actor developing a digital offense capability, and publishing it to the general public. From the target side, limitations on scaling prevent complete mitigation or remediation of the vulnerability.The situation is much different from the offense perspective.Any actor may leverage the offense capability against any Internet-connected target on the planet. The actor can scale that capability across the entire range of vulnerable or exposed targets.The ThreeOnly three sets of actors are able to possibly leverage an offense capability for defensive purposes.First, the organization responsible for developing and maintaining the vulnerable or exposed asset can determine if there is a remedy for the new offense capability. (This is typically a "vendor," but could be a noncommercial entity. As a shorthand, I will use "vendor.") The vendor can try to develop and deploy a patch or mitigation method.Second, major consumers of the vulnerable or exposed asset can take similar steps, usually by implementing the vendor's patch or mitigation.Third, the security one percent can take some defensive measures, either by implementing the vendor's patch or mitigation, or by developing and acting upon detection and response processes.The combination of the actions by these three sets of actors will not completely remediate the digital offense capability. The gap can be small, or it can be exceptionally large, hence the net negative cost to the digital ecosystem. PropositionDigital offense capabilities are currently net negative for the security ecosystem.[0]The costs of improved digital offense currently outweigh the benefits. The legitimate benefits of digital offense accrue primarily to the security one percent (#securityonepercent), and to intelligence, military, and law enforcement agencies. The derived defensive benefits depend on the nature of the defender. The entire security ecosystem bears the costs, and in some cases even those who see tangible benefit may suffer costs exceeding those benefits.The ReasonLimitations of scaling are the reason why digital offense capabilities are currently net negative.Consider the case of an actor developing a digital offense capability, and publishing it to the general public. From the target side, limitations on scaling prevent complete mitigation or remediation of the vulnerability.The situation is much different from the offense perspective.Any actor may leverage the offense capability against any Internet-connected target on the planet. The actor can scale that capability across the entire range of vulnerable or exposed targets.The ThreeOnly three sets of actors are able to possibly leverage an offense capability for defensive purposes.First, the organization responsible for developing and maintaining the vulnerable or exposed asset can determine if there is a remedy for the new offense capability. (This is typically a "vendor," but could be a noncommercial entity. As a shorthand, I will use "vendor.") The vendor can try to develop and deploy a patch or mitigation method.Second, major consumers of the vulnerable or exposed asset can take similar steps, usually by implementing the vendor's patch or mitigation.Third, the security one percent can take some defensive measures, either by implementing the vendor's patch or mitigation, or by developing and acting upon detection and response processes.The combination of the actions by these three sets of actors will not completely remediate the digital offense capability. The gap can be small, or it can be exceptionally large, hence the net negative cost to the digital ecosystem. |
Ransomware Threat | |||
| 2020-11-09 08:30:17 | New Book! The Best of TaoSecurity Blog, Volume 3 (lien direct) |  Introduction I published a new book!The Best of TaoSecurity Blog, Volume 3: Current Events, Law, Wise People, History, and Appendices is the third title in the TaoSecurity Blog series. It's in the Kindle Store, and if you have an Unlimited account, it's free. I also published a print edition, which is 485 pages. Book DescriptionThe book features the following description on the back cover:Since 2003, cybersecurity author Richard Bejtlich has been publishing posts on TaoSecurity Blog, a site with 15 million views since 2011. Now, after re-reading over 3,000 stories and approximately one million words, he has selected and republished the very best entries from 17 years of writing, along with commentaries and additional material. In the third volume of the TaoSecurity Blog series, Mr. Bejtlich addresses the evolution of his security mindset, influenced by current events and advice from his so-called set of "wise people." He talks about why speed is not the key to John Boyd's OODA loop, and why security strategies designed for and by the "security 1%" may be irrelevant at best, or harmful at worst, for the remaining "99%". His history section explores the origins of the terms threat hunting and indicators of compromise, and reveals who really created the quote "there are two types of companies." His chapter on law highlights traps that might catch security teams, with advice to chief information security officers.This volume contains some of Mr. Bejtlich's favorite posts, such as Marcus Ranum's answer to what happens when security teams confront professionals, or how the Internet continues to function despite constant challenges, or reactions to comments by Dan Geer, Bruce Schneier, Marty Roesch, and other security leaders. Mr. Bejtlich has written new commentaries to accompany each post, some of which would qualify as blog entries in their own right. Read how the security industry, defensive methodologies, and strategies to improve national security have evolved in this new book, written by one of the authors who has seen it all and survived to blog about it.Writing the SeriesAlthough I had written and self-published a book in early 2019, I had used Blurb and stayed in print format. Introduction I published a new book!The Best of TaoSecurity Blog, Volume 3: Current Events, Law, Wise People, History, and Appendices is the third title in the TaoSecurity Blog series. It's in the Kindle Store, and if you have an Unlimited account, it's free. I also published a print edition, which is 485 pages. Book DescriptionThe book features the following description on the back cover:Since 2003, cybersecurity author Richard Bejtlich has been publishing posts on TaoSecurity Blog, a site with 15 million views since 2011. Now, after re-reading over 3,000 stories and approximately one million words, he has selected and republished the very best entries from 17 years of writing, along with commentaries and additional material. In the third volume of the TaoSecurity Blog series, Mr. Bejtlich addresses the evolution of his security mindset, influenced by current events and advice from his so-called set of "wise people." He talks about why speed is not the key to John Boyd's OODA loop, and why security strategies designed for and by the "security 1%" may be irrelevant at best, or harmful at worst, for the remaining "99%". His history section explores the origins of the terms threat hunting and indicators of compromise, and reveals who really created the quote "there are two types of companies." His chapter on law highlights traps that might catch security teams, with advice to chief information security officers.This volume contains some of Mr. Bejtlich's favorite posts, such as Marcus Ranum's answer to what happens when security teams confront professionals, or how the Internet continues to function despite constant challenges, or reactions to comments by Dan Geer, Bruce Schneier, Marty Roesch, and other security leaders. Mr. Bejtlich has written new commentaries to accompany each post, some of which would qualify as blog entries in their own right. Read how the security industry, defensive methodologies, and strategies to improve national security have evolved in this new book, written by one of the authors who has seen it all and survived to blog about it.Writing the SeriesAlthough I had written and self-published a book in early 2019, I had used Blurb and stayed in print format. |
Threat Guideline | |||
| 2020-10-31 16:11:10 | Security and the One Percent: A Thought Exercise in Estimation and Consequences (lien direct) | There's a good chance that if you're reading this post, you're the member of an exclusive club. I call it the security one percent, or the security 1%. This is shorthand for the assortment of people and organizations who have the personnel, processes, technology, and support to implement somewhat robust digital security programs, especially those with the detection and response capabilities and not just planning and resistance/"prevention" functions. Introduction This post will estimate the size of the security 1% in the United States. It will then briefly explain how the security strategies of the 1% might be irrelevant at best or damaging at worse to the 99%.A First Cut with FIRSTIt's difficult to measure the size of the security 1%, but not impossible. My goal is to ascertain the correct orders of magnitude. One method is to review entities who are members of the Forum of Incident Response and Security Teams, or FIRST. FIRST is an organization to which high-performing computer incident response teams (CIRTs) may apply once their processes and data handling meet standards set by FIRST. I learned of FIRST when the AFCERT was a member in the late 1990s. I also assisted with FIRST duties when Foundstone was a member in the early 2000s. I helped or sponsored membership when I worked at General Electric in the 2000s and Mandiant in the 2010s. I encourage all capable security teams to join FIRST.Being a FIRST member means having a certain degree of incident response and data handling capability, and it signals to the world and to other FIRST teams that the member entity is serious about incident detection and response.As of the writing of this post, there are 540 FIRST teams worldwide. Slightly more than 100 of them are based in the United States. To put that in perspective, there are less than 4,000 publicly traded companies in the US. That means that even if every single US FIRST member represented a publicly traded company -- and that is not the case -- FIRST representation for US publicly traded companies is only 2.5%. Beyond FIRSTSome of you might claim FIRST membership is no big deal. My current employer, Corelight, isn't a member, you might say. Perhaps you could argue that for every US FIRST member, there are 9 others which have equivalent or better security teams. That would increase the cadre of entities with respectable detection and response capabilities from 100 to 1,000. That would still mean an estimate that says 75% of publicly traded US companies have sub-par or non-existent security programs.Remember that we've only been talking about a population of 4,000 publicly traded US companies. The US Small Business and Entrepreneurship Council estimates that there were 5.6 million employer firms in the United States in 2016. Let's sadly reduce that to 4 million to account for the devastation of Covid. | Threat Guideline | |||
| 2020-10-23 10:12:50 | MITRE ATT&CK Tactics Are Not Tactics (lien direct) |  Just what are "tactics"?IntroductionMITRE ATT&CK is a great resource, but something about it has bothered me since I first heard about it several years ago. It's a minor point, but I wanted to document it in case it confuses anyone else.The MITRE ATT&CK Design and Philosophy document from March 2020 says the following:At a high-level, ATT&CK is a behavioral model that consists of the following core components:• Tactics, denoting short-term, tactical adversary goals during an attack;• Techniques, describing the means by which adversaries achieve tactical goals;• Sub-techniques, describing more specific means by which adversaries achieve tactical goals at a lower level than techniques; and• Documented adversary usage of techniques, their procedures, and other metadata.My concern is with MITRE's definition of "tactics" as "short-term, tactical adversary goals during an attack," which is oddly recursive.The key word in the tactics definition is goals. According to MITRE, "tactics" are "goals."Examples of ATT&CK TacticsATT&CK lists the following as "Enterprise Tactics": Just what are "tactics"?IntroductionMITRE ATT&CK is a great resource, but something about it has bothered me since I first heard about it several years ago. It's a minor point, but I wanted to document it in case it confuses anyone else.The MITRE ATT&CK Design and Philosophy document from March 2020 says the following:At a high-level, ATT&CK is a behavioral model that consists of the following core components:• Tactics, denoting short-term, tactical adversary goals during an attack;• Techniques, describing the means by which adversaries achieve tactical goals;• Sub-techniques, describing more specific means by which adversaries achieve tactical goals at a lower level than techniques; and• Documented adversary usage of techniques, their procedures, and other metadata.My concern is with MITRE's definition of "tactics" as "short-term, tactical adversary goals during an attack," which is oddly recursive.The key word in the tactics definition is goals. According to MITRE, "tactics" are "goals."Examples of ATT&CK TacticsATT&CK lists the following as "Enterprise Tactics": MITRE ATT&CK "Tactics," https://attack.mitre.org/tactics/enterprise/Looking at this list, the first 11 items could indeed be seen as goals. The last item, Impact, is not a goal. That item is an artifact of trying to shoehorn more information into the ATT&CK structure. That's not my primary concern though.Military Theory and DefinitionsAs a service academy graduate who had to sit through many lectures on military theory, and who participated in small unit exercises, the idea of tactics as "goals" does not make any sense. MITRE ATT&CK "Tactics," https://attack.mitre.org/tactics/enterprise/Looking at this list, the first 11 items could indeed be seen as goals. The last item, Impact, is not a goal. That item is an artifact of trying to shoehorn more information into the ATT&CK structure. That's not my primary concern though.Military Theory and DefinitionsAs a service academy graduate who had to sit through many lectures on military theory, and who participated in small unit exercises, the idea of tactics as "goals" does not make any sense. |
Guideline | |||
| 2020-10-10 11:30:12 | Greg Rattray Invented the Term Advanced Persistent Threat (lien direct) | 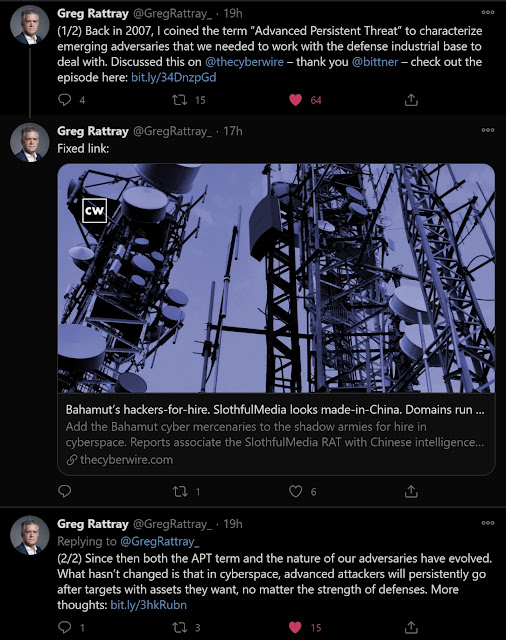 I was so pleased to read this Tweet yesterday from Greg Rattray:"Back in 2007, I coined the term “Advanced Persistent Threat” to characterize emerging adversaries that we needed to work with the defense industrial base to deal with... Since then both the APT term and the nature of our adversaries have evolved. What hasn't changed is that in cyberspace, advanced attackers will persistently go after targets with assets they want, no matter the strength of defenses."BackgroundFirst, some background. Who is Greg Rattray?First, you could call him Colonel or Doctor. I will use Col as that was the last title I used with him, although these days when we chat I call him Greg. Col Rattray served 21 years in the Air Force and also earned his PhD in international security from Tufts University. His thesis formed the content for his 2001 book Strategic Warfare in Cyberspace, which I reviewed in 2002 and rated 4 stars. (Ouch -- I was a bit stingy with the stars back then. I was more of an operator and less of a theorist or historian in those days. Such was my bias I suppose.)Col Rattray is also a 1984 graduate of the Air Force Academy. He studied history and political science there and returned as an assistant professor in the early 1990s. He was one of my instructors when I was a cadet there. (I graduated in 1994 with degrees in history and political science.) Col Rattray then earned a master of public policy degree at Harvard Kennedy School. (I did the same, in 1996.) Do you see a pattern here? He is clearly a role model. Of course, I did not stay in the Air Force as long, earn the same rank, or survive my PhD program!After the Academy, Col Rattray served as commander of the 23rd Information Operations Squadrons on Security Hill in San Antonio, Texas. I was working in the AFCERT at the time. I was so pleased to read this Tweet yesterday from Greg Rattray:"Back in 2007, I coined the term “Advanced Persistent Threat” to characterize emerging adversaries that we needed to work with the defense industrial base to deal with... Since then both the APT term and the nature of our adversaries have evolved. What hasn't changed is that in cyberspace, advanced attackers will persistently go after targets with assets they want, no matter the strength of defenses."BackgroundFirst, some background. Who is Greg Rattray?First, you could call him Colonel or Doctor. I will use Col as that was the last title I used with him, although these days when we chat I call him Greg. Col Rattray served 21 years in the Air Force and also earned his PhD in international security from Tufts University. His thesis formed the content for his 2001 book Strategic Warfare in Cyberspace, which I reviewed in 2002 and rated 4 stars. (Ouch -- I was a bit stingy with the stars back then. I was more of an operator and less of a theorist or historian in those days. Such was my bias I suppose.)Col Rattray is also a 1984 graduate of the Air Force Academy. He studied history and political science there and returned as an assistant professor in the early 1990s. He was one of my instructors when I was a cadet there. (I graduated in 1994 with degrees in history and political science.) Col Rattray then earned a master of public policy degree at Harvard Kennedy School. (I did the same, in 1996.) Do you see a pattern here? He is clearly a role model. Of course, I did not stay in the Air Force as long, earn the same rank, or survive my PhD program!After the Academy, Col Rattray served as commander of the 23rd Information Operations Squadrons on Security Hill in San Antonio, Texas. I was working in the AFCERT at the time. |
Threat Guideline | |||
| 2020-09-03 11:11:10 | The FBI Intrusion Notification Program (lien direct) | The FBI intrusion notification program is one of the most important developments in cyber security during the last 15 years. This program achieved mainstream recognition on 24 March 2014 when Ellen Nakashima reported on it for the Washington Post in her story U.S. notified 3,000 companies in 2013 about cyberattacks. The story noted the following:"Federal agents notified more than 3,000 U.S. companies last year that their computer systems had been hacked, White House officials have told industry executives, marking the first time the government has revealed how often it tipped off the private sector to cyberintrusions...About 2,000 of the notifications were made in person or by phone by the FBI, which has 1,000 people dedicated to cybersecurity investigations among 56 field offices and its headquarters. Some of the notifications were made to the same company for separate intrusions, officials said. Although in-person visits are preferred, resource constraints limit the bureau's ability to do them all that way, former officials said...Officials with the Secret Service, an agency of the Department of Homeland Security that investigates financially motivated cybercrimes, said that they notified companies in 590 criminal cases opened last year, officials said. Some cases involved more than one company."The reason this program is so important is that it shattered the delusion that some executives used to reassure themselves. When the FBI visits your headquarters to tell you that you are compromised, you can't pretend that intrusions are "someone else's problem."It may be difficult for some readers to appreciate how prevalent this mindset was, from the beginnings of IT to about the year 2010.I do not know exactly when the FBI began notifying victims, but I believe the mid-2000's is a safe date. I can personally attest to the program around that time.I was reminded of the importance of this program by Andy Greenberg's new story The FBI Botched Its DNC Hack Warning in 2016-but Says It Won't Next Time. I strongly disagree with this "botched" characterization. Andy writes:"[S]omehow this breach [of the Democratic National Committee] had come as a terrible surprise-despite an FBI agent's warning to [IT staffer Yared] Tamene of potential Russian hacking over a series of phone calls that had begun fully nine months earlier.The FBI agent's warnings had 'never used alarming language,' Tamene would tell the Senate committee, and never reached higher than the DNC's IT director, who dismissed them after a cursory search of the network for signs of foul play."As with all intrusions, criminal responsibility lies with the intruder. However, I do not see why the FBI is supposed to carry the blame for how this intrusion unfolded. According to investigatory documents and this Crowdstrike blog post on their involvement, at least seven months passed from the time the FBI notified the DNC (sometime in September 2015) and when they contacted Crowdstrike (30 April 2015). That is ridiculous. If I received a call from the FBI even hinting at a Russian presence in my network, I would be on the phone with a professional incident response firm right after I briefed the CEO about the call.I'm glad the FBI continues to improve its victim notification procedures, but it doesn't make much of a difference if the individuals running IT and the organization are negligent, either through incompetence or inaction.Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and w | Hack | |||
| 2020-09-01 08:30:06 | New Book! The Best of TaoSecurity Blog, Volume 2 (lien direct) |  I published a new book!The Best of TaoSecurity Blog, Volume 2: Network Security Monitoring, Technical Notes, Research, and China and the Advanced Persistent ThreatIt's in the Kindle Store, and if you're Unlimited it's free. Print edition to follow.The book lists as having 413 pages (for the Kindle edition at least) at it's almost 95,000 words. I started working on it in June after finishing Volume 1.Here is the book description:Since 2003, cybersecurity author Richard Bejtlich has been writing posts on TaoSecurity Blog, a site with 15 million views since 2011. Now, after re-reading over 3,000 posts and approximately one million words, he has selected and republished the very best entries from 17 years of writing. In the second volume of the TaoSecurity Blog series, Mr. Bejtlich addresses how to detect and respond to intrusions using third party threat intelligence sources, network data, application and infrastructure data, and endpoint data. He assesses government and private security initiatives and applies counterintelligence and counteradversary mindsets to defend digital assets. He documents the events of the last 20 years of Chinese hacking from the perspective of a defender on the front lines, in the pre- and post-APT era. This volume contains some of Mr. Bejtlich's favorite posts, such as histories of threat hunting, so-called black and white hat budgeting, attribution capabilities and limits, and rating information security incidents. He has written new commentaries to accompany each post, some of which would qualify as blog entries in their own right. Read how the security industry, defensive methodologies, and strategies to improve national security have evolved in this new book, written by one of the authors who has seen it all and survived to blog about it.I have a third volume planned. I will publish it by the end of the year. I published a new book!The Best of TaoSecurity Blog, Volume 2: Network Security Monitoring, Technical Notes, Research, and China and the Advanced Persistent ThreatIt's in the Kindle Store, and if you're Unlimited it's free. Print edition to follow.The book lists as having 413 pages (for the Kindle edition at least) at it's almost 95,000 words. I started working on it in June after finishing Volume 1.Here is the book description:Since 2003, cybersecurity author Richard Bejtlich has been writing posts on TaoSecurity Blog, a site with 15 million views since 2011. Now, after re-reading over 3,000 posts and approximately one million words, he has selected and republished the very best entries from 17 years of writing. In the second volume of the TaoSecurity Blog series, Mr. Bejtlich addresses how to detect and respond to intrusions using third party threat intelligence sources, network data, application and infrastructure data, and endpoint data. He assesses government and private security initiatives and applies counterintelligence and counteradversary mindsets to defend digital assets. He documents the events of the last 20 years of Chinese hacking from the perspective of a defender on the front lines, in the pre- and post-APT era. This volume contains some of Mr. Bejtlich's favorite posts, such as histories of threat hunting, so-called black and white hat budgeting, attribution capabilities and limits, and rating information security incidents. He has written new commentaries to accompany each post, some of which would qualify as blog entries in their own right. Read how the security industry, defensive methodologies, and strategies to improve national security have evolved in this new book, written by one of the authors who has seen it all and survived to blog about it.I have a third volume planned. I will publish it by the end of the year.  If you have any questions about the book, let me know. Currently you can see the table of contents via the "Look Inside" function, and there is a sample that lets you download and read some of the book. Enjoy!Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) If you have any questions about the book, let me know. Currently you can see the table of contents via the "Look Inside" function, and there is a sample that lets you download and read some of the book. Enjoy!Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
Threat | |||
| 2020-08-19 11:17:40 | One Weird Trick for Reviewing Zeek Logs on the Command Line! (lien direct) | Are you a network security monitoring dinosaur like me? Do you prefer to inspect your Zeek logs using the command line instead of a Web-based SIEM?If yes, try this one weird trick!I store my Zeek logs in JSON format. Sometimes I like to view the output using jq.If I need to search directories of logs for a string, like a UID, I might* use something like zgrep with the following syntax:$ zgrep "CLkXf2CMo11hD8FQ5" 2020-08-16/*2020-08-16/conn_20200816_06:00:00-07:00:00+0000.log.gz:{"_path":"conn","_system_name":"ds61","_write_ts":"2020-08-16T06:26:10.266225Z","_node":"worker-01","ts":"2020-08-16T06:26:01.485394Z","uid":"CLkXf2CMo11hD8FQ5","id.orig_h":"192.168.2.76","id.orig_p":53380,"id.resp_h":"196.216.2.24","id.resp_p":21,"proto":"tcp","service":"ftp","duration":3.780829906463623,"orig_bytes":184,"resp_bytes":451,"conn_state":"SF","local_orig":true,"local_resp":false,"missed_bytes":0,"history":"ShAdDafF","orig_pkts":20,"orig_ip_bytes":1232,"resp_pkts":17,"resp_ip_bytes":1343,"community_id":"1:lEESxqaSVYqFZvWNb4OccTa9sTs="}2020-08-16/ftp_20200816_06:26:04-07:00:00+0000.log.gz:{"_path":"ftp","_system_name":"ds61","_write_ts":"2020-08-16T06:26:04.077276Z","_node":"worker-01","ts":"2020-08-16T06:26:03.553287Z","uid":"CLkXf2CMo11hD8FQ5","id.orig_h":"192.168.2.76","id.orig_p":53380,"id.resp_h":"196.216.2.24","id.resp_p":21,"user":"anonymous","password":"ftp@example.com","command":"EPSV","reply_code":229,"reply_msg":"Entering Extended Passive Mode (|||31746|).","data_channel.passive":true,"data_channel.orig_h":"192.168.2.76","data_channel.resp_h":"196.216.2.24","data_channel.resp_p":31746}2020-08-16/ftp_20200816_06:26:04-07:00:00+0000.log.gz:{"_path":"ftp","_system_name":"ds61","_write_ts":"2020-08-16T06:26:05.117287Z","_node":"worker-01","ts":"2020-08-16T06:26:04.597290Z","uid":"CLkXf2CMo11hD8FQ5","id.orig_h":"192.168.2.76","id.orig_p":53380,"id.resp_h":"196.216.2.24","id.resp_p":21,"user":"anonymous","password":"ftp@example.com","command":"RETR","arg":"ftp://196.216.2.24/pub/stats/afrinic/delegated-afrinic-extended-latest.md5","file_size":74,"reply_code":226,"reply_msg":"Transfer complete.","fuid":"FueF95uKPrUuDnMc4"}That is tough on the eyes. I cannot simply pipe that output to Jq however:$ zgrep "CLkXf2CMo11hD8FQ5" 2020-08-16/* | jq .parse error: Invalid numeric literal at line 1, column 28What I need to do is strip out the filename and colon before the JSON. I learned how to use sed to do this thanks to this post. $ zgrep "CLkXf2CMo11hD8FQ5" 2020-08-16/* | sed 's/.*gz://' | jq .{ "_path": "conn", "_system_name": "ds61", "_write_ts": "2020-08-16T06:26:10.266225Z", "_node": "worker-01", | ||||
| 2020-07-16 11:04:59 | I Did Not Write This Book (lien direct) |  Fake Book Someone published a "book" on Amazon and claimed that I wrote it! I had NOTHING to do with this. I am working with Amazon now to remove it, or at least remove my name. Stay away from this garbage!Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) Fake Book Someone published a "book" on Amazon and claimed that I wrote it! I had NOTHING to do with this. I am working with Amazon now to remove it, or at least remove my name. Stay away from this garbage!Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
||||
| 2020-05-04 11:51:25 | New Book! The Best of TaoSecurity Blog, Volume 1 (lien direct) |  I'm very pleased to announce that I've published a new book!It's The Best of TaoSecurity Blog, Volume 1: Milestones, Philosophy and Strategy, Risk, and Advice. It's available now in the Kindle Store, and if you're a member of Kindle Unlimited, it's currently free. I may also publish a print version. If you're interested, please tell me on Twitter. I'm very pleased to announce that I've published a new book!It's The Best of TaoSecurity Blog, Volume 1: Milestones, Philosophy and Strategy, Risk, and Advice. It's available now in the Kindle Store, and if you're a member of Kindle Unlimited, it's currently free. I may also publish a print version. If you're interested, please tell me on Twitter. The book lists at 332 pages and is over 83,000 words. I've been working on it since last year, but I've used the time in isolation to carry the first volume over the finish line.The Amazon.com description says:Since 2003, cybersecurity author Richard Bejtlich has been writing posts on TaoSecurity Blog, a site with 15 million views since 2011. Now, after re-reading over 3,000 posts and approximately one million words, he has selected and republished the very best entries from 17 years of writing.In the first volume of the TaoSecurity Blog series, Bejtlich addresses milestones, philosophy and strategy, risk, and advice. Bejtlich shares his thoughts on leadership, the intruder's dilemma, managing burnout, controls versus assessments, insider versus outsider threats, security return on investment, threats versus vulnerabilities, controls and compliance, the post that got him hired at a Fortune 5 company as their first director of incident response, and much more.He has written new commentaries to accompany each post, some of which would qualify as blog entries in their own right. Read how the security industry, defensive methodologies, and strategies to improve career opportunities have evolved in this new book, written by one of the authors who has seen it all and survived to blog about it.Finally, if you're interested in subsequent volumes, I have two planned. The book lists at 332 pages and is over 83,000 words. I've been working on it since last year, but I've used the time in isolation to carry the first volume over the finish line.The Amazon.com description says:Since 2003, cybersecurity author Richard Bejtlich has been writing posts on TaoSecurity Blog, a site with 15 million views since 2011. Now, after re-reading over 3,000 posts and approximately one million words, he has selected and republished the very best entries from 17 years of writing.In the first volume of the TaoSecurity Blog series, Bejtlich addresses milestones, philosophy and strategy, risk, and advice. Bejtlich shares his thoughts on leadership, the intruder's dilemma, managing burnout, controls versus assessments, insider versus outsider threats, security return on investment, threats versus vulnerabilities, controls and compliance, the post that got him hired at a Fortune 5 company as their first director of incident response, and much more.He has written new commentaries to accompany each post, some of which would qualify as blog entries in their own right. Read how the security industry, defensive methodologies, and strategies to improve career opportunities have evolved in this new book, written by one of the authors who has seen it all and survived to blog about it.Finally, if you're interested in subsequent volumes, I have two planned. I may also have a few other book projects in the pipeline. I'll have more to say on that in the coming weeks.If you have any questions about the book, let me know. Currently you can see the table of contents via the "Look Inside" function, and ther I may also have a few other book projects in the pipeline. I'll have more to say on that in the coming weeks.If you have any questions about the book, let me know. Currently you can see the table of contents via the "Look Inside" function, and ther |
Guideline | |||
| 2020-04-07 11:28:11 | If You Can\'t Patch Your Email Server, You Should Not Be Running It (lien direct) | 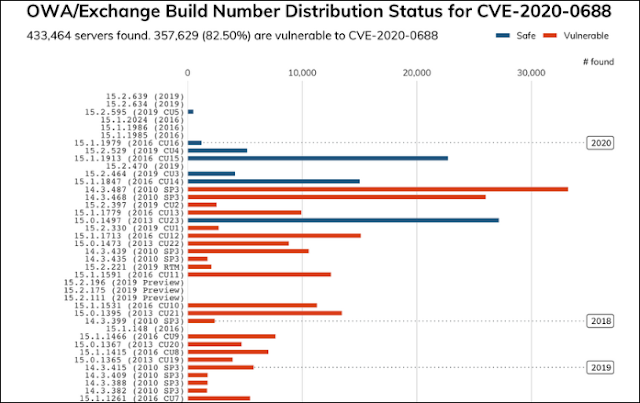 CVE-2020-0688 Scan Results, per Rapid7tl;dr -- it's the title of the post: "If You Can't Patch Your Email Server, You Should Not Be Running It."I read a disturbing story today with the following news:"Starting March 24, Rapid7 used its Project Sonar internet-wide survey tool to discover all publicly-facing Exchange servers on the Internet and the numbers are grim.As they found, 'at least 357,629 (82.5%) of the 433,464 Exchange servers' are still vulnerable to attacks that would exploit the CVE-2020-0688 vulnerability.To make matters even worse, some of the servers that were tagged by Rapid7 as being safe against attacks might still be vulnerable given that 'the related Microsoft update wasn't always updating the build number.'Furthermore, 'there are over 31,000 Exchange 2010 servers that have not been updated since 2012,' as the Rapid7 researchers observed. 'There are nearly 800 Exchange 2010 servers that have never been updated.'They also found 10,731 Exchange 2007 servers and more than 166,321 Exchange 2010 ones, with the former already running End of Support (EoS) software that hasn't received any security updates since 2017 and the latter reaching EoS in October 2020."In case you were wondering, threat actors have already been exploiting these flaws for weeks, if not months.Email is one of, if not the most, sensitive and important systems upon which organizations of all shapes and sizes rely. The are, by virtue of their function, inherently exposed to the Internet, meaning they are within the range of every targeted or opportunistic intruder, worldwide.In this particular case, unpatched servers are also vulnerable to any actor who can download and update Metasploit, which is virtually 100% of them.It is the height of negligence to run such an important system in an unpatched state, when there are much better alternatives -- namely, outsourcing your email to a competent provider, like Google, Microsoft, or several others.I expect some readers are saying "I would never put my email in the hands of those big companies!" That's fine, and I know several highly competent individuals who run their own email infrastructure. The problem is that they represent the small fraction of individuals and organizations who can do so. Even being extremely generous with the numbers, it appears that less than 20%, and probably less than 15% according to other estimates, can even keep their Exchange servers patched, let alone properly configured.If you think it's still worth the risk, and your organization isn't able to patch, because you want to avoid megacorp email providers or government access to your email, you've made a critical miscalculation. You've essentially decided that it's more important for you to keep your email out of megacorp or government hands than it is to keep i CVE-2020-0688 Scan Results, per Rapid7tl;dr -- it's the title of the post: "If You Can't Patch Your Email Server, You Should Not Be Running It."I read a disturbing story today with the following news:"Starting March 24, Rapid7 used its Project Sonar internet-wide survey tool to discover all publicly-facing Exchange servers on the Internet and the numbers are grim.As they found, 'at least 357,629 (82.5%) of the 433,464 Exchange servers' are still vulnerable to attacks that would exploit the CVE-2020-0688 vulnerability.To make matters even worse, some of the servers that were tagged by Rapid7 as being safe against attacks might still be vulnerable given that 'the related Microsoft update wasn't always updating the build number.'Furthermore, 'there are over 31,000 Exchange 2010 servers that have not been updated since 2012,' as the Rapid7 researchers observed. 'There are nearly 800 Exchange 2010 servers that have never been updated.'They also found 10,731 Exchange 2007 servers and more than 166,321 Exchange 2010 ones, with the former already running End of Support (EoS) software that hasn't received any security updates since 2017 and the latter reaching EoS in October 2020."In case you were wondering, threat actors have already been exploiting these flaws for weeks, if not months.Email is one of, if not the most, sensitive and important systems upon which organizations of all shapes and sizes rely. The are, by virtue of their function, inherently exposed to the Internet, meaning they are within the range of every targeted or opportunistic intruder, worldwide.In this particular case, unpatched servers are also vulnerable to any actor who can download and update Metasploit, which is virtually 100% of them.It is the height of negligence to run such an important system in an unpatched state, when there are much better alternatives -- namely, outsourcing your email to a competent provider, like Google, Microsoft, or several others.I expect some readers are saying "I would never put my email in the hands of those big companies!" That's fine, and I know several highly competent individuals who run their own email infrastructure. The problem is that they represent the small fraction of individuals and organizations who can do so. Even being extremely generous with the numbers, it appears that less than 20%, and probably less than 15% according to other estimates, can even keep their Exchange servers patched, let alone properly configured.If you think it's still worth the risk, and your organization isn't able to patch, because you want to avoid megacorp email providers or government access to your email, you've made a critical miscalculation. You've essentially decided that it's more important for you to keep your email out of megacorp or government hands than it is to keep i |
Tool | |||
| 2020-04-02 19:05:11 | Seeing Book Shelves on Virtual Calls (lien direct) |  I have a confession... for me, the best part of virtual calls, or seeing any reporter or commentator working for home, is being able to check out their book shelves. I never use computer video, because I want to preserve the world's bandwidth. That means I don't share what my book shelves look like when I'm on a company call. Therefore, I thought I'd share my book shelves with the world.My big categories of books are martial arts, mixed/miscellaneous, cybersecurity and intelligence, and military and Civil War history. I've cataloged about 400 print books and almost 500 digital titles. Over the years I've leaned towards buying Kindle editions of any book that is mostly print, in order to reduce my footprint.For the last many years, my book shelving has consisted of three units, each with five shelves. Looking at the topic distribution, as of 2020 I have roughly 6 shelves for martial arts, 4 for mixed/miscellaneous, 3 for cybersecurity and intelligence, and 2 for military and Civil War history.This is interesting to me because I can compare my mix from five years ago, when I did an interview for the now defunct Warcouncil Warbooks project. I have a confession... for me, the best part of virtual calls, or seeing any reporter or commentator working for home, is being able to check out their book shelves. I never use computer video, because I want to preserve the world's bandwidth. That means I don't share what my book shelves look like when I'm on a company call. Therefore, I thought I'd share my book shelves with the world.My big categories of books are martial arts, mixed/miscellaneous, cybersecurity and intelligence, and military and Civil War history. I've cataloged about 400 print books and almost 500 digital titles. Over the years I've leaned towards buying Kindle editions of any book that is mostly print, in order to reduce my footprint.For the last many years, my book shelving has consisted of three units, each with five shelves. Looking at the topic distribution, as of 2020 I have roughly 6 shelves for martial arts, 4 for mixed/miscellaneous, 3 for cybersecurity and intelligence, and 2 for military and Civil War history.This is interesting to me because I can compare my mix from five years ago, when I did an interview for the now defunct Warcouncil Warbooks project. |
||||
| 2020-03-27 11:15:36 | Skill Levels in Digital Security (lien direct) |  Two posts in one day? These are certainly unusual times.I was thinking about words to describe different skill levels in digital security. Rather than invent something, I decided to review terms that have established meaning. Thanks to Google Books I found this article in a 1922 edition of the Archives of Psychology that mentioned four key terms:The novice is a (person) who has no trade ability whatever, or at least none that could not be paralleled by practically any intelligent (person).An apprentice has acquired some of the elements of the trade but is not sufficiently skilled to be trusted with any important task.The journey(person) is qualified to perform almost any work done by members of the trade.An expert can perform quickly and with superior skill any work done by (people) in the trade.I believe these four categories can apply to some degree to the needs of the digital security profession.At GE-CIRT we had three levels -- event analyst, incident analyst, and incident handler. We did not hire novices, so those three roles map in some ways to apprentice, journeyperson, and expert. One difference with the classical description applies to how we worked with apprentices. We trusted apprentices, or event analysts, with specific tasks. We thought of this work as important, just as every role on a team is important. It may not have been leading an incident response, but without the work of the event and incident analysts, we may not have discovered many incidents!Crucially, we encouraged event analysts, and incident analysts for that matter, to always be looking to exceed the parameters of their assigned duties.However, we stipulated that if a person was working beyond their assigned duties, they had to have their work product reviewed by the next level of analysis. This enabled mentoring among the various groups. It also helped identify people who were candidates for promotion. If a person consistently worked beyond their assigned duties, and eventually reached a near-perfect or perfect ability to do that work, that proved he or she was ready to assume the next level.This ability to access work beyond assigned duties is one reason I have problems with limiting data by role. I think everyone who works in a CIRT should have access to all of the data, assuming there are no classification, privacy, or active investigation constraints.One of my laws is the following:Analysts are good because they have good data. An expert with bad data is helpless. An apprentice with good data has a chance to do good work.I've said it more eloquently elsewhere but this is the main point. For more information on the apprenticeship model, this article might be useful.Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) Two posts in one day? These are certainly unusual times.I was thinking about words to describe different skill levels in digital security. Rather than invent something, I decided to review terms that have established meaning. Thanks to Google Books I found this article in a 1922 edition of the Archives of Psychology that mentioned four key terms:The novice is a (person) who has no trade ability whatever, or at least none that could not be paralleled by practically any intelligent (person).An apprentice has acquired some of the elements of the trade but is not sufficiently skilled to be trusted with any important task.The journey(person) is qualified to perform almost any work done by members of the trade.An expert can perform quickly and with superior skill any work done by (people) in the trade.I believe these four categories can apply to some degree to the needs of the digital security profession.At GE-CIRT we had three levels -- event analyst, incident analyst, and incident handler. We did not hire novices, so those three roles map in some ways to apprentice, journeyperson, and expert. One difference with the classical description applies to how we worked with apprentices. We trusted apprentices, or event analysts, with specific tasks. We thought of this work as important, just as every role on a team is important. It may not have been leading an incident response, but without the work of the event and incident analysts, we may not have discovered many incidents!Crucially, we encouraged event analysts, and incident analysts for that matter, to always be looking to exceed the parameters of their assigned duties.However, we stipulated that if a person was working beyond their assigned duties, they had to have their work product reviewed by the next level of analysis. This enabled mentoring among the various groups. It also helped identify people who were candidates for promotion. If a person consistently worked beyond their assigned duties, and eventually reached a near-perfect or perfect ability to do that work, that proved he or she was ready to assume the next level.This ability to access work beyond assigned duties is one reason I have problems with limiting data by role. I think everyone who works in a CIRT should have access to all of the data, assuming there are no classification, privacy, or active investigation constraints.One of my laws is the following:Analysts are good because they have good data. An expert with bad data is helpless. An apprentice with good data has a chance to do good work.I've said it more eloquently elsewhere but this is the main point. For more information on the apprenticeship model, this article might be useful.Copyright 2003-2020 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
Guideline | |||
| 2020-03-27 08:59:19 | When You Should Blog and When You Should Tweet (lien direct) |  I saw my like-minded, friend-that-I've-never-met Andrew Thompson Tweet a poll, posted above.I was about to reply with the following Tweet:"If I'm struggling to figure out how to capture a thought in just 1 Tweet, that's a sign that a blog post might be appropriate. I only use a thread, and no more than 2, and hardly ever 3 (good Lord), when I know I've got nothing more to say. "1/10," "1/n," etc. are not for me."Then I realized I had something more to say, namely, other reasons blog posts are better than Tweets. For the briefest moment I considered adding a second Tweet, making, horror of horrors, a THREAD, and then I realized I would be breaking my own guidance.Here are three reasons to consider blogging over Tweeting.1. If you find yourself trying to pack your thoughts into a 280 character limit, then you should write a blog post. You might have a good idea, and instead of expressing it properly, you're falling into the trap of letting the medium define the message, aka the PowerPoint trap. I learned this from Edward Tufte: let the message define the medium, not the other way around.2. Twitter threads lose the elegance and readability of the English language as our ancestors created it, for our benefit. They gave us structures, like sentences, lists, indentation, paragraphs, chapters, and so on. What does Twitter provide? 280 character chunks. Sure, you can apply feeble "1/n" annotations, but you've lost all that structure and readability, and for what?3. In the event you're writing a Tweet thread that's really worth reading, writing it via Twitter virtually guarantees that it's lost to history. Twitter is an abomination for citation, search, and future reference. In the hierarchy of delivering content for current researchers and future generations, the hierarchy is the following, from lowest to highest:"Transient," "bite-sized" social media, e.g., Twitter, Instagram, Facebook, etc. postsBlog postsWhitepapersAcademic papers in "electronic" journalsElectronic (e.g., Kindle) only formatted booksPrint books (that may be stand-alone works, or which may contain journal articles)Print book are the apex communication medium because we have such references going back hundreds of years. Hundreds of years from now, I doubt the first five formats above will be easily accessible, or accessible at all. However, in a library or personal collection somewhere, printed books will endure.The bottom line is that if you think what you're writing is important enough to start a "1/n" Tweet thread, you've already demonstrated that Twitter is the wrong medium.The natural follow-on might be: what is Twitter good for? Here are my suggestions:Announcing a link to another, in-depth news resource, like a news article, blog post, whitepaper, etc.Offering a comment on an in-depth news resource, or replying to another person's announcement.Asking a poll question.Asking for help on a topic.Engaging in a short exchange with another user. Long exchanges on hot topics typically devolve into a confusing mess of messages and replies, that delivery of which Twitter has never really managed to figure out.I understand the seduction of Twitter. I use it every da I saw my like-minded, friend-that-I've-never-met Andrew Thompson Tweet a poll, posted above.I was about to reply with the following Tweet:"If I'm struggling to figure out how to capture a thought in just 1 Tweet, that's a sign that a blog post might be appropriate. I only use a thread, and no more than 2, and hardly ever 3 (good Lord), when I know I've got nothing more to say. "1/10," "1/n," etc. are not for me."Then I realized I had something more to say, namely, other reasons blog posts are better than Tweets. For the briefest moment I considered adding a second Tweet, making, horror of horrors, a THREAD, and then I realized I would be breaking my own guidance.Here are three reasons to consider blogging over Tweeting.1. If you find yourself trying to pack your thoughts into a 280 character limit, then you should write a blog post. You might have a good idea, and instead of expressing it properly, you're falling into the trap of letting the medium define the message, aka the PowerPoint trap. I learned this from Edward Tufte: let the message define the medium, not the other way around.2. Twitter threads lose the elegance and readability of the English language as our ancestors created it, for our benefit. They gave us structures, like sentences, lists, indentation, paragraphs, chapters, and so on. What does Twitter provide? 280 character chunks. Sure, you can apply feeble "1/n" annotations, but you've lost all that structure and readability, and for what?3. In the event you're writing a Tweet thread that's really worth reading, writing it via Twitter virtually guarantees that it's lost to history. Twitter is an abomination for citation, search, and future reference. In the hierarchy of delivering content for current researchers and future generations, the hierarchy is the following, from lowest to highest:"Transient," "bite-sized" social media, e.g., Twitter, Instagram, Facebook, etc. postsBlog postsWhitepapersAcademic papers in "electronic" journalsElectronic (e.g., Kindle) only formatted booksPrint books (that may be stand-alone works, or which may contain journal articles)Print book are the apex communication medium because we have such references going back hundreds of years. Hundreds of years from now, I doubt the first five formats above will be easily accessible, or accessible at all. However, in a library or personal collection somewhere, printed books will endure.The bottom line is that if you think what you're writing is important enough to start a "1/n" Tweet thread, you've already demonstrated that Twitter is the wrong medium.The natural follow-on might be: what is Twitter good for? Here are my suggestions:Announcing a link to another, in-depth news resource, like a news article, blog post, whitepaper, etc.Offering a comment on an in-depth news resource, or replying to another person's announcement.Asking a poll question.Asking for help on a topic.Engaging in a short exchange with another user. Long exchanges on hot topics typically devolve into a confusing mess of messages and replies, that delivery of which Twitter has never really managed to figure out.I understand the seduction of Twitter. I use it every da |
||||
| 2020-03-12 09:29:36 | COVID-19 Phishing Tests: WRONG (lien direct) | Malware Jake Tweeted a poll last night which asked the following:"I have an interesting ethical quandary. Is it ethically okay to use COVID-19 themed phishing emails for assessments and user awareness training right now? Please read the thread before responding and RT for visibility. 1/"Ultimately he decided:"My gut feeling is to not use COVID-19 themed emails in assessments/training, but to TELL users to expect them, though I understand even that might discourage consumption of legitimate information, endangering public health. 6/"I responded by saying this was the right answer.Thankfully there were many people who agreed, despite the fact that voting itself was skewed towards the "yes" answer.There were an uncomfortable number of responses to the Tweet that said there's nothing wrong with red teams phishing users with COVID-19 emails. For example:"Do criminals abide by ethics? Nope. Neither should testing.""Yes. If it's in scope for the badguys [sic], it's in scope for you.""Attackers will use it. So I think it is fair game."Those are the wrong answers. As a few others outlined well in their responses, the fact that a criminal or intruder employs a tactic does not mean that it's appropriate for an offensive security team to use it too.I could imagine several COVID-19 phishing lures that could target school districts and probably cause high double-digit click-through rates. What's the point of that? For a "community" that supposedly considers fear, uncertainty, and doubt (FUD) to be anathema, why introduce FUD via a phishing test?I've grown increasingly concerned over the past few years that there's a "cult of the offensive" that justifies its activities with the rationale that "intruders do it, so we should too." This is directly observable in the replies to Jake's Tweet. It's a thin veneer that covers bad behavior, outweighing the small benefit accrued to high-end, 1% security shops against the massive costs suffered by the vast majority of networked global organizations.The is a selfish, insular mindset that is reinforced by the echo chamber of the so-called "infosec community." This "tribe" is detached from the concerns and ethics of the larger society. It tells itself that what it is doing is right, oblivious or unconcerned with the costs imposed on the organizations they are supposedly "protecting" with their backwards actions.We need people with feet in both worlds to tell this group that their approach is not welcome in the broader human community, because the costs it imposes vastly outweigh the benefits.I've written here about ethics before, usually in connection with the only real value I saw in the CISSP -- its code of ethics. Reviewing the "code," as it appears now, shows the following:"There are only four mandatory canons in the Code. By necessity, such high-level guidance is not intended to be a substitute for the ethical judgment of the professional.Code of Ethics Preamble:The safety and welfare of society and the common good, duty to our principals, and to each other, requires that we adhere, and be seen to adhere, to the highest ethical standards of behavior.Therefore, strict adherence to this Code is a condition of certification.Code of Ethics Canons:Protect society, the common good, necessary public trust and confidence, and the infrastructure.Act honorably, honestly, justly, responsibly, and legally.Provide diligent and competent service to principals.Advance and protect the profession."This is | Malware | |||
| 2019-11-06 16:12:52 | Seven Security Strategies, Summarized (lien direct) | This is the sort of story that starts as a comment on Twitter, then becomes a blog post when I realize I can't fit all the ideas into one or two Tweets. (You know how much I hate Tweet threads, and how I encourage everyone to capture deep thoughts in blog posts!)In the interest of capturing the thought, and not in the interest of thinking too deeply or comprehensively (at least right now), I offer seven security strategies, summarized.When I mention the risk equation, I'm talking about the idea that one can conceptually image the risk of some negative event using this "formula": Risk (of something) is the product of some measurements of Vulnerability X Threat X Asset Value, or R = V x T x A.Denial and/or ignorance. This strategy assumes the risk due to loss is low, because those managing the risk assume that one or more of the elements of the risk equation are zero or almost zero, or they are apathetic to the cost.Loss acceptance. This strategy may assume the risk due to loss is low, or more likely those managing the risk assume that the cost of risk realization is low. In other words, incidents will occur, but the cost of the incident is acceptable to the organization.Loss transferal. This strategy may also assume the risk due to loss is low, but in contrast with risk acceptance, the organization believes it can buy an insurance policy which will cover the cost of an incident, and the cost of the policy is cheaper than alternative strategies.Vulnerability elimination. This strategy focuses on driving the vulnerability element of the risk equation to zero or almost zero, through secure coding, proper configuration, patching, and similar methods.Threat elimination. This strategy focuses on driving the threat element of the risk equation to zero or almost zero, through deterrence, dissuasion, co-option, bribery, conversion, incarceration, incapacitation, or other methods that change the intent and/or capabilities of threat actors. Asset value elimination. This strategy focuses on driving the threat element of the risk equation to zero or almost zero, through minimizing data or resources that might be valued by adversaries.Interdiction. This is a hybrid strategy which welcomes contributions from vulnerability elimination, primarily, but is open to assistance from loss transferal, threat elimination, and asset value elimination. Interdiction assumes that prevention eventually fails, but that security teams can detect and respond to incidents post-compromise and pre-breach. In other words, some classes of intruders will indeed compromise an organization, but it is possible to detect and respond to the attack before the adversary completes his mission.As you might expect, I am most closely associated with the interdiction strategy. I believe the denial and/or ignorance and loss acceptance strategies are irresponsible.I believe the loss transferal strategy continues to gain momentum with the growth of cybersecurity breach insurance policies. I believe the vulnerability elimination strategy is important but ultimately, on its own, ineffective and historically shown to be impossible. When used in concert with other strategies, it is absolutely helpful.I believe the threat elimination strategy is generally beyond the scope of private organizations. As the state retains the monopoly on the use of force, usually only law enforcement, military, and sometimes intelligence agencies can truly eliminate or mitigate threats. (Threats are not vulnerabilities.)I believe asset value elimination is powerful but has not gained the ground I would like to see. This is my " | Vulnerability Threat | |||
| 2019-09-13 11:00:00 | Five Thoughts on the Internet Freedom League (lien direct) |  In the September/October issue of Foreign Affairs magazine, Richard Clarke and Rob Knake published an article titled "The Internet Freedom League: How to Push Back Against the Authoritarian Assault on the Web," based on their recent book The Fifth Domain. The article proposes the following:The United States and its allies and partners should stop worrying about the risk of authoritarians splitting the Internet. Instead, they should split it themselves, by creating a digital bloc within which data, services, and products can flow freely, excluding countries that do not respect freedom of expression or privacy rights, engage in disruptive activity, or provide safe havens to cybercriminals...The league would not raise a digital Iron Curtain; at least initially, most Internet traffic would still flow between members and nonmembers, and the league would primarily block companies and organizations that aid and abet cybercrime, rather than entire countries. Governments that fundamentally accept the idea of an open, tolerant, and democratic Internet but that struggle to live up to such a vision would have an incentive to improve their enforcement efforts in order join the league and secure connectivity for their companies and citizens. Of course, authoritarian regimes in China, Russia, and elsewhere will probably continue to reject that vision. Instead of begging and pleading with such governments to play nice, from now on, the United States and its allies should lay down the law: follow the rules, or get cut off.My initial reaction to this line of thought was not encouraging. Rather than continue exchanging Twitter messages, Rob and I had a very pleasant phone conversation to help each other understand our points of view. Rob asked me to document my thoughts in a blog post, so this is the result.Rob explained that the main goal of the IFL is to create leverage to influence those who do not implement an open, tolerant, and democratic Internet (summarized below as OTDI). I agree that leverage is certainly lacking, but I wondered if the IFL would accomplish that goal. My reservations included the following.1. Many countries that currently reject the OTDI might only be too happy to be cut off from the Western Internet. These countries do not want their citizens accessing the OTDI. Currently dissidents and others seeking news beyond their local borders must often use virtual private networks and other means to access the OTDI. If the IFL went live, those dissidents and others would be cut off, thanks to their government's resistance to OTDI principles.2. Elites in anti-OTDI countries would still find ways to access the Western Internet, either for personal, business, political, military, or intelligence reasons. The common person would be mostly likely to suffer.3. Segregating the OTDI would increase the incentives for "network traffic smuggling," whereby anti-OTDI elites would compromise, bribe, or otherwise corrupt Western Internet resources to establish surreptitious methods to access the OTDI. This would increase the intrusion pressure upon o In the September/October issue of Foreign Affairs magazine, Richard Clarke and Rob Knake published an article titled "The Internet Freedom League: How to Push Back Against the Authoritarian Assault on the Web," based on their recent book The Fifth Domain. The article proposes the following:The United States and its allies and partners should stop worrying about the risk of authoritarians splitting the Internet. Instead, they should split it themselves, by creating a digital bloc within which data, services, and products can flow freely, excluding countries that do not respect freedom of expression or privacy rights, engage in disruptive activity, or provide safe havens to cybercriminals...The league would not raise a digital Iron Curtain; at least initially, most Internet traffic would still flow between members and nonmembers, and the league would primarily block companies and organizations that aid and abet cybercrime, rather than entire countries. Governments that fundamentally accept the idea of an open, tolerant, and democratic Internet but that struggle to live up to such a vision would have an incentive to improve their enforcement efforts in order join the league and secure connectivity for their companies and citizens. Of course, authoritarian regimes in China, Russia, and elsewhere will probably continue to reject that vision. Instead of begging and pleading with such governments to play nice, from now on, the United States and its allies should lay down the law: follow the rules, or get cut off.My initial reaction to this line of thought was not encouraging. Rather than continue exchanging Twitter messages, Rob and I had a very pleasant phone conversation to help each other understand our points of view. Rob asked me to document my thoughts in a blog post, so this is the result.Rob explained that the main goal of the IFL is to create leverage to influence those who do not implement an open, tolerant, and democratic Internet (summarized below as OTDI). I agree that leverage is certainly lacking, but I wondered if the IFL would accomplish that goal. My reservations included the following.1. Many countries that currently reject the OTDI might only be too happy to be cut off from the Western Internet. These countries do not want their citizens accessing the OTDI. Currently dissidents and others seeking news beyond their local borders must often use virtual private networks and other means to access the OTDI. If the IFL went live, those dissidents and others would be cut off, thanks to their government's resistance to OTDI principles.2. Elites in anti-OTDI countries would still find ways to access the Western Internet, either for personal, business, political, military, or intelligence reasons. The common person would be mostly likely to suffer.3. Segregating the OTDI would increase the incentives for "network traffic smuggling," whereby anti-OTDI elites would compromise, bribe, or otherwise corrupt Western Internet resources to establish surreptitious methods to access the OTDI. This would increase the intrusion pressure upon o |
Guideline | |||
| 2019-07-01 10:00:03 | Happy Birthday TaoSecurity.com (lien direct) |  Nineteen years ago this week I registered the domain taosecurity.com:Creation Date: 2000-07-04T02:20:16ZThis was 2 1/2 years before I started blogging, so I don't have much information from that era. I did create the first taosecurity.com Web site shortly thereafter.I first started hosting it on space provided by my then-ISP, Road Runner of San Antonio, TX. According to archive.org, it looked like this in February 2002. Nineteen years ago this week I registered the domain taosecurity.com:Creation Date: 2000-07-04T02:20:16ZThis was 2 1/2 years before I started blogging, so I don't have much information from that era. I did create the first taosecurity.com Web site shortly thereafter.I first started hosting it on space provided by my then-ISP, Road Runner of San Antonio, TX. According to archive.org, it looked like this in February 2002. That is some fine-looking vintage hand-crafted HTML. Because I lived in Texas I apparently reached for the desert theme with the light tan background. Unfortunately I didn't have the "under construction" gif working for me.As I got deeper into the security scene, I decided to simplify and adopt a dark look. By this time I had left Texas and was in the DC area, working for Foundstone. According to archive.org, the site look like this in April 2003. That is some fine-looking vintage hand-crafted HTML. Because I lived in Texas I apparently reached for the desert theme with the light tan background. Unfortunately I didn't have the "under construction" gif working for me.As I got deeper into the security scene, I decided to simplify and adopt a dark look. By this time I had left Texas and was in the DC area, working for Foundstone. According to archive.org, the site look like this in April 2003. Notice I've replaced the oh-so-cool picture of me doing American Kenpo in the upper-left-hand corner with the classic Bruce Lee photo from the cover of The Tao of Jeet Kune Do. This version marks the first appearance of my classic TaoSecurity logo.A little more than two years later, I decided to pursue TaoSecurity as an independent consultant. To launch my services, I painstakingly created more hand-written HTML and graphics to deliver this beauty. According to archive.org, the site looked like this in May 2005. Notice I've replaced the oh-so-cool picture of me doing American Kenpo in the upper-left-hand corner with the classic Bruce Lee photo from the cover of The Tao of Jeet Kune Do. This version marks the first appearance of my classic TaoSecurity logo.A little more than two years later, I decided to pursue TaoSecurity as an independent consultant. To launch my services, I painstakingly created more hand-written HTML and graphics to deliver this beauty. According to archive.org, the site looked like this in May 2005. |
||||
| 2019-07-01 08:00:07 | Reference: TaoSecurity News (lien direct) | I started speaking publicly about digital security in 2000. I used to provide this information on my Web site, but since I don't keep that page up-to-date anymore, I decided to publish it here. 2017 Mr. Bejtlich led a podcast titled Threat Hunting: Past, Present, and Future, in early July 2017. He interviewed four of the original six GE-CIRT incident handlers. The audio is posted on YouTube. Thank you to Sqrrl for making the reunion possible. Mr. Bejtlich's latest book was inducted into the Cybersecurity Canon. Mr. Bejtlich is doing limited security consulting. See this blog post for details. 2016 Mr. Bejtlich organized and hosted the Management track (now "Executive track") at the 7th annual Mandiant MIRCon (now "FireEye Cyber Defense Summit") on 29-30 November 2016. Mr. Bejtlich delivered the keynote to the 2016 Air Force Senior Leaders Orientation Conference at Joint Base Andrews on 29 July 2016. Mr. Bejtlich delivered the keynote to the FireEye Cyber Defense Live Tokyo event in Tokyo on 12 July 2016. Mr. Bejtlich delivered the keynote to the New Zealand Cyber Security Summit in Auckland on 6 May 2016. Mr. Bejtlich delivered the keynote to the Lexpo Summit in Amsterdam on 21 April 2016. Video posted here. Mr. Bejtlich discussed cyber security campaigns at the 2016 War Studies Cumberland Lodge Conference near London on 30 March 2016. Mr. Bejtlich offered a guest lecture to the Wilson Center Congressional Cybersecurity Lab on 5 February 2016. Mr. Bejtlich delivered the keynote to the SANS Cyber Threat Intelligence Summit on 4 February 2016. Slides and video available. 2015 Mr. Bejtlich spoke on a panel at the DefenseOne Summit on 2 November 2015. Mr. Bejtlich spoke on a panel at the AEI Internet Strategy event on 27 October 2015. Mr. Bejtlich organized and hosted the Management track at the 6th annual Mandiant MIRCon on 13-14 October 2015. Mr. Bejtlich testified to the House Foreign Affairs Committee on 7 October 2015. Mr. Bejtlich testified to the House Armed Services Committee on 30 September 2015. Mr. Bejtlich delivered a keynote at the 2015 Army Cyber Institute Cyber Talks on 22 September 2015 in Washington, DC. Mr. Bejtlich delivered a keynote at the 2015 Security Onion Conference on 11 September 2015 in Augusta, GA. Mr. Bejtlich delivered a keynote at the 2015 World Services Group Conference on 10 S | Guideline | APT 1 | ||
| 2019-07-01 08:00:04 | Reference: TaoSecurity Research (lien direct) | I started publishing my thoughts and findings on digital security in 1999. I used to provide this information on my Web site, but since I don't keep that page up-to-date anymore, I decided to publish it here.2015 and later: Please visit Academia.edu for Mr. Bejtlich's most recent research.2014 and earlier: Seven Tips for Small Business Security, in the Huffington Post, 18 June 2014Strategy, Not Speed: What Today's Digital Defenders Must Learn From Cybersecurity's Early Thinkers, for the Brookings Institution, 7 May 2014What Federal Cyber Breach Notifications Really Mean for Business, for the Brookings Institution, 25 March 2014Don't Underestimate Cyber Spies: How Virtual Espionage Can Lead to Actual Destruction in Foreign Affairs, 2 May 2013Become a Hunter in the targeted-threat-centric Information Security Magzine, July-August 2011 (.pdf) Directions in Incident Detection and Response (.pdf) in the January/February 2011 issue of IEEE Security and Privacy magazineUnderstanding the Advanced Persistent Threat in Information Security Magazine, July 2010Traffic Talk issues 1, 2, 3, 4, 5, 6, 7, 8, 9, 10Snort Report issues 1, 2, 3, 4, 5, 6, | Guideline | |||
| 2019-07-01 08:00:01 | Reference: TaoSecurity Press (lien direct) | I started appearing in media reports in 2000. I used to provide this information on my Web site, but since I don't keep that page up-to-date anymore, I decided to publish it here. As of 2017, Mr. Bejtlich generally denies press inquiries on cybersecurity matters, including those on background.2016Mr. Bejtlich was cited in the Forture story Meet the US's First Ever Cyber Chief, published 8 September 2016.Mr. Bejtlich was interviewed for the NPR story Cybersecurity: Who's Vulnerable To Attack?, aired 30 July 2016.Mr. Bejtlich was interviewed for the Washington Post story It's not just the DNC; we all send emails we probably shouldn't, published 25 July 2016.Mr. Bejtlich was interviewed for the New Scientist story NATO says the internet is now a war zone – what does that mean?, published 22 June 2016.Mr. Bejtlich was interviewed for the Military Times story The Pentagon's controversial plan to hire military leaders off the street, published 19 June 2016.Mr. Bejtlich was interviewed for the Idealog story Idealog talks with a cyber-war expert, published 6 May 2016.Mr. Bejtlich was cited in the New Zealand Herald story Cyber-attacks part of doing business with China - experts, published 5 May 2016.Mr. Bejtlich was cited in the Christian Science Monitor story Iran hacking indictment highlights US naming and shaming strategy, published 30 March 2016.Mr. Bejtlich was cited in the Financial Times story Defence groups take aim at cyber security, published 28 March 2016.Mr. Bejtlich was interviewed for the Security Management story A Chinese New Year, published 4 January 2016.2015Mr. Bejtlich was cited in the AP story US Advised to Examine "Hack Back" Options against China, published 17 November 2015.Mr. Bejtlich was cited in the Reuters story Data from US agency cyber breach not on black market - researcher, published 2 November 2015.Mr. Bejtlich was cited in the NextGov story Creative, Audacious or Destructive: The Different Personalities of Nation-State Hackers, published 2 November 2015.Mr. Bejtlich was cited in the Baltimore Sun story As more devices go online, hackers hunt for vulnerabilities, published 24 October 2015.Mr. Bejtlich was cited in the Atlantic story Can Campus Networks Ever Be Secure?, published 12 October 2015.Mr. Bejtlich was cited in the Info Security story | Guideline | Yahoo | ||
| 2019-05-29 09:55:00 | Know Your Limitations (lien direct) |  At the end of the 1973 Clint Eastwood movie Magnum Force, after Dirty Harry watches his corrupt police captain explode in a car, he says "a man's got to know his limitations."I thought of this quote today as the debate rages about compromising municipalities and other information technology-constrained yet personal information-rich organizations.Several years ago I wrote If You Can't Protect It, Don't Collect It. I argued that if you are unable to defend personal information, then you should not gather and store it.In a similar spirit, here I argue that if you are unable to securely operate information technology that matters, then you should not be supporting that IT.You should outsource it to a trustworthy cloud provider, and concentrate on managing secure access to those services.If you cannot outsource it, and you remain incapable of defending it natively, then you should integrate a capable managed security provider.It's clear to me that a large portion of those running PI-processing IT are simply not capable of doing so in secure manner, and they do not bear the full cost of PI breaches.They have too many assets, with too many vulnerabilities, and are targeted by too many threat actors.These organizations lack sufficient people, processes, and technologies to mitigate the risk.They have successes, but they are generally due to the heroics of individual IT and security professionals, who often feel out-gunned by their adversaries.If you can't patch a two-year-old vulnerability prior to exploitation, or detect an intrusion and respond to the adversary before he completes his mission, then you are demonstrating that you need to change your entire approach to information technology.The security industry seems to think that throwing more people at the problem is the answer, yet year after year we read about several million job openings that remain unfilled. This is a sign that we need to change the way we are doing business. The fact is that those organziations that cannot defend themselves need to recognize their limitations and change their game.I recognize that outsourcing is not a panacea. Note that I emphasized "IT" in my recommendation. I do not see how one could outsource the critical technology running on-premise in the industrial control system (ICS) world, for example. Those operations may need to rely more on outsourced security providers, if they cannot sufficiently detect and respond to intrusions using in-house capabilities.Remember that the vast majority of organizations do not exist to run IT. They run IT to support their lines of business. Many older organizations have indeed been migrating legacy applications to the cloud, and most new organizations are cloud-native. These are hopeful signs, as the older organizations could potentially "age-out" over time.This puts a burden on the cloud providers, who fall into the "managed service provider" category that I wrote about in my recent Corelight blog. However, the more trustworthy providers have the people, proc At the end of the 1973 Clint Eastwood movie Magnum Force, after Dirty Harry watches his corrupt police captain explode in a car, he says "a man's got to know his limitations."I thought of this quote today as the debate rages about compromising municipalities and other information technology-constrained yet personal information-rich organizations.Several years ago I wrote If You Can't Protect It, Don't Collect It. I argued that if you are unable to defend personal information, then you should not gather and store it.In a similar spirit, here I argue that if you are unable to securely operate information technology that matters, then you should not be supporting that IT.You should outsource it to a trustworthy cloud provider, and concentrate on managing secure access to those services.If you cannot outsource it, and you remain incapable of defending it natively, then you should integrate a capable managed security provider.It's clear to me that a large portion of those running PI-processing IT are simply not capable of doing so in secure manner, and they do not bear the full cost of PI breaches.They have too many assets, with too many vulnerabilities, and are targeted by too many threat actors.These organizations lack sufficient people, processes, and technologies to mitigate the risk.They have successes, but they are generally due to the heroics of individual IT and security professionals, who often feel out-gunned by their adversaries.If you can't patch a two-year-old vulnerability prior to exploitation, or detect an intrusion and respond to the adversary before he completes his mission, then you are demonstrating that you need to change your entire approach to information technology.The security industry seems to think that throwing more people at the problem is the answer, yet year after year we read about several million job openings that remain unfilled. This is a sign that we need to change the way we are doing business. The fact is that those organziations that cannot defend themselves need to recognize their limitations and change their game.I recognize that outsourcing is not a panacea. Note that I emphasized "IT" in my recommendation. I do not see how one could outsource the critical technology running on-premise in the industrial control system (ICS) world, for example. Those operations may need to rely more on outsourced security providers, if they cannot sufficiently detect and respond to intrusions using in-house capabilities.Remember that the vast majority of organizations do not exist to run IT. They run IT to support their lines of business. Many older organizations have indeed been migrating legacy applications to the cloud, and most new organizations are cloud-native. These are hopeful signs, as the older organizations could potentially "age-out" over time.This puts a burden on the cloud providers, who fall into the "managed service provider" category that I wrote about in my recent Corelight blog. However, the more trustworthy providers have the people, proc |
Vulnerability Threat | |||
| 2019-05-09 10:30:01 | Dissecting Weird Packets (lien direct) | I was investigating traffic in my home lab yesterday, and noticed that about 1% of the traffic was weird. Before I describe the weird, let me show you a normal frame for comparison's sake. This is a normal frame with Ethernet II encapsulation. It begins with 6 bytes of the destination MAC address, 6 bytes of the source MAC address, and 2 bytes of an Ethertype, which in this case is 0x0800, indicating an IP packet follows the Ethernet header. There is no TCP payload as this is an ACK segment.You can also see this in Tshark.$ tshark -Vx -r frame4238.pcapFrame 1: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) Encapsulation type: Ethernet (1) Arrival Time: May 7, 2019 18:19:10.071831000 UTC [Time shift for this packet: 0.000000000 seconds] Epoch Time: 1557253150.071831000 seconds [Time delta from previous captured frame: 0.000000000 seconds] [Time delta from previous displayed frame: 0.000000000 seconds] [Time since reference or first frame: 0.000000000 seconds] Frame Number: 1 Frame Length: 66 bytes (528 bits) Capture Length: 66 bytes (528 bits) [Frame is marked: False] [Frame is ignored: False] [Protocols in frame: eth:ethertype:ip:tcp]Ethernet II, Src: IntelCor_12:7d:bb (38:ba:f8:12:7d:bb), Dst: Ubiquiti_49:e0:10 (fc:ec:da:49:e0:10) Destination: Ubiquiti_49:e0:10 (fc:ec:da:49:e0:10) Address: Ubiquiti_49:e0:10 (fc:ec:da:49:e0:10) .... ..0. .... .... .... .... = LG bit: Globally unique address (factory default) .... ...0 .... .... .... .... = IG bit: Individual address (unicast) This is a normal frame with Ethernet II encapsulation. It begins with 6 bytes of the destination MAC address, 6 bytes of the source MAC address, and 2 bytes of an Ethertype, which in this case is 0x0800, indicating an IP packet follows the Ethernet header. There is no TCP payload as this is an ACK segment.You can also see this in Tshark.$ tshark -Vx -r frame4238.pcapFrame 1: 66 bytes on wire (528 bits), 66 bytes captured (528 bits) Encapsulation type: Ethernet (1) Arrival Time: May 7, 2019 18:19:10.071831000 UTC [Time shift for this packet: 0.000000000 seconds] Epoch Time: 1557253150.071831000 seconds [Time delta from previous captured frame: 0.000000000 seconds] [Time delta from previous displayed frame: 0.000000000 seconds] [Time since reference or first frame: 0.000000000 seconds] Frame Number: 1 Frame Length: 66 bytes (528 bits) Capture Length: 66 bytes (528 bits) [Frame is marked: False] [Frame is ignored: False] [Protocols in frame: eth:ethertype:ip:tcp]Ethernet II, Src: IntelCor_12:7d:bb (38:ba:f8:12:7d:bb), Dst: Ubiquiti_49:e0:10 (fc:ec:da:49:e0:10) Destination: Ubiquiti_49:e0:10 (fc:ec:da:49:e0:10) Address: Ubiquiti_49:e0:10 (fc:ec:da:49:e0:10) .... ..0. .... .... .... .... = LG bit: Globally unique address (factory default) .... ...0 .... .... .... .... = IG bit: Individual address (unicast) |
||||
| 2019-04-08 16:56:12 | Troubleshooting NSM Virtualization Problems with Linux and VirtualBox (lien direct) |  I spent a chunk of the day troubleshooting a network security monitoring (NSM) problem. I thought I would share the problem and my investigation in the hopes that it might help others. The specifics are probably less important than the general approach.It began with ja3. You may know ja3 as a set of Zeek scripts developed by the Salesforce engineering team to profile client and server TLS parameters.I was reviewing Zeek logs captured by my Corelight appliance and by one of my lab sensors running Security Onion. I had coverage of the same endpoint in both sensors.I noticed that the SO Zeek logs did not have ja3 hashes in the ssl.log entries. Both sensors did have ja3s hashes. My first thought was that SO was misconfigured somehow to not record ja3 hashes. I quickly dismissed that, because it made no sense. Besides, verifying that intution required me to start troubleshooting near the top of the software stack.I decided to start at the bottom, or close to the bottom. I had a sinking suspicion that, for some reason, Zeek was only seeing traffic sent from remote systems, and not traffic originating from my network. That would account for the creation of ja3s hashes, for traffic sent by remote systems, but not ja3 hashes, as Zeek was not seeing traffic sent by local clients.I was running SO in VirtualBox 6.0.4 on Ubuntu 18.04. I started sniffing TCP network traffic on the SO monitoring interface using Tcpdump. As I feared, it didn't look right. I ran a new capture with filters for ICMP and a remote IP address. On another system I tried pinging the remote IP address. Sure enough, I only saw ICMP echo replies, and no ICMP echoes. Oddly, I also saw doubles and triples of some of the ICMP echo replies. That worried me, because unpredictable behavior like that could indicate some sort of software problem.My next step was to "get under" the VM guest and determine if the VM host could see traffic properly. I ran Tcpdump on the Ubuntu 18.04 host on the monitoring interface and repeated my ICMP tests. It saw everything properly. That meant I did not need to bother checking the switch span port that was feeding traffic to the VirtualBox system.It seemed I had a problem somewhere between the VM host and guest. On the same VM host I was also running an instance of RockNSM. I ran my ICMP tests on the RockNSM VM and, sadly, I got the same one-sided traffic as seen on SO.Now I was worried. If the problem had only been present in SO, then I could fix SO. If the problem is present in both SO and RockNSM, then the problem had to be with VirtualBox -- and I might not be able to fix it.I reviewed my configurations in VirtualBox, ensuring that the "Promiscuous Mode" under the Advanced options was set to "Allow All". At this point I worried that there was a bug in VirtualBox. I did some Google searches and reviewed some forum posts, but I did not see anyone reporting issues with sniffing traffic inside VMs. Still, my use case might have been weird enough to not have been reported.I decided to try a different approach. I wondered if running VirtualBox with elevated privileges might make a difference. I did not want to take ownership of my user VMs, so I decided to install a new VM and run it with elevated privileges.Let me stop here to note that I am breaking one of the rules of troubleshooting. I'm introducing two new variables, when I should I spent a chunk of the day troubleshooting a network security monitoring (NSM) problem. I thought I would share the problem and my investigation in the hopes that it might help others. The specifics are probably less important than the general approach.It began with ja3. You may know ja3 as a set of Zeek scripts developed by the Salesforce engineering team to profile client and server TLS parameters.I was reviewing Zeek logs captured by my Corelight appliance and by one of my lab sensors running Security Onion. I had coverage of the same endpoint in both sensors.I noticed that the SO Zeek logs did not have ja3 hashes in the ssl.log entries. Both sensors did have ja3s hashes. My first thought was that SO was misconfigured somehow to not record ja3 hashes. I quickly dismissed that, because it made no sense. Besides, verifying that intution required me to start troubleshooting near the top of the software stack.I decided to start at the bottom, or close to the bottom. I had a sinking suspicion that, for some reason, Zeek was only seeing traffic sent from remote systems, and not traffic originating from my network. That would account for the creation of ja3s hashes, for traffic sent by remote systems, but not ja3 hashes, as Zeek was not seeing traffic sent by local clients.I was running SO in VirtualBox 6.0.4 on Ubuntu 18.04. I started sniffing TCP network traffic on the SO monitoring interface using Tcpdump. As I feared, it didn't look right. I ran a new capture with filters for ICMP and a remote IP address. On another system I tried pinging the remote IP address. Sure enough, I only saw ICMP echo replies, and no ICMP echoes. Oddly, I also saw doubles and triples of some of the ICMP echo replies. That worried me, because unpredictable behavior like that could indicate some sort of software problem.My next step was to "get under" the VM guest and determine if the VM host could see traffic properly. I ran Tcpdump on the Ubuntu 18.04 host on the monitoring interface and repeated my ICMP tests. It saw everything properly. That meant I did not need to bother checking the switch span port that was feeding traffic to the VirtualBox system.It seemed I had a problem somewhere between the VM host and guest. On the same VM host I was also running an instance of RockNSM. I ran my ICMP tests on the RockNSM VM and, sadly, I got the same one-sided traffic as seen on SO.Now I was worried. If the problem had only been present in SO, then I could fix SO. If the problem is present in both SO and RockNSM, then the problem had to be with VirtualBox -- and I might not be able to fix it.I reviewed my configurations in VirtualBox, ensuring that the "Promiscuous Mode" under the Advanced options was set to "Allow All". At this point I worried that there was a bug in VirtualBox. I did some Google searches and reviewed some forum posts, but I did not see anyone reporting issues with sniffing traffic inside VMs. Still, my use case might have been weird enough to not have been reported.I decided to try a different approach. I wondered if running VirtualBox with elevated privileges might make a difference. I did not want to take ownership of my user VMs, so I decided to install a new VM and run it with elevated privileges.Let me stop here to note that I am breaking one of the rules of troubleshooting. I'm introducing two new variables, when I should |
||||
| 2019-03-28 16:40:01 | Thoughts on OSSEC Con 2019 (lien direct) |  Last week I attended my first OSSEC conference. I first blogged about OSSEC in 2007, and wrote other posts about it in the following years.OSSEC is a host-based intrusion detection and log analysis system with correlation and active response features. It is cross-platform, such that I can run it on my Windows and Linux systems. The moving force behind the conference was a company local to me called Atomicorp.In brief, I really enjoyed this one-day event. (I had planned to attend the workshop on the second day but my schedule did not cooperate.) The talks were almost uniformly excellent and informative. I even had a chance to talk jiu-jitsu with OSSEC creator Daniel Cid, who despite hurting his leg managed to travel across the country to deliver the keynote.I'd like to share a few highlights from my notes.First, I had been worried that OSSEC was in some ways dead. I saw that the Security Onion project had replaced OSSEC with a fork called Wazuh, which I learned is apparently pronounced "wazoo." To my delight, I learned OSSEC is decidedly not dead, and that Wazuh has been suffering stability problems. OSSEC has a lot of interesting development ahead of it, which you can track on their Github repo.For example, the development roadmap includes eliminating Logstash from the pipeline used by many OSSEC users. OSSEC would feed directly into Elasticsearch. One speaker noted that Logstash has a 1.7 GB memory footprint, which astounded me.On a related note, the OSSEC team is planning to create a new Web console, with a design goal to have it run in an "AWS t2.micro" instance. The team noted that instance offers 2 GB memory, which doesn't match what AWS says. Perhaps they meant t2.micro and 1 GB memory, or t2.small with 2 GB memory. I think they mean t2.micro with 1 GB RAM, as that is the free tier. Either way, I'm excited to see this later in 2019.Second, I thought the presentation by security personnel from USA Today offered an interesting insight. One design goal they had for monitoring their Google Cloud Platform (GCP) was to not install OSSEC on every container or on Kubernetes worker nodes. Several times during the conference, speakers noted that the transient nature of cloud infrastructure is directly antithetical to standard OSSEC usage, whereby OSSEC is installed on servers with long uptime and years of service. Instead, USA Today used OSSEC to monitor HTTP logs from the GCP load balancer, logs from Google Kubernetes Engine, and monitored processes by watching output from successive kubectl invocations.Third, a speaker from Red Hat brought my attention to an aspect of containers that I had not considered. Docker and containers had made software testing and deployment a lot easier for everyone. However, those who provide containers have effectively become Linux distribution maintainers. In other words, who is responsible when a security or configuration vulnerability in a Linux component is discovered? Will the container maintainers be responsive?Another speaker emphasized the difference between "security of the cloud," offered by cloud providers, and "security in the cloud," which is supposed to be the customer\ Last week I attended my first OSSEC conference. I first blogged about OSSEC in 2007, and wrote other posts about it in the following years.OSSEC is a host-based intrusion detection and log analysis system with correlation and active response features. It is cross-platform, such that I can run it on my Windows and Linux systems. The moving force behind the conference was a company local to me called Atomicorp.In brief, I really enjoyed this one-day event. (I had planned to attend the workshop on the second day but my schedule did not cooperate.) The talks were almost uniformly excellent and informative. I even had a chance to talk jiu-jitsu with OSSEC creator Daniel Cid, who despite hurting his leg managed to travel across the country to deliver the keynote.I'd like to share a few highlights from my notes.First, I had been worried that OSSEC was in some ways dead. I saw that the Security Onion project had replaced OSSEC with a fork called Wazuh, which I learned is apparently pronounced "wazoo." To my delight, I learned OSSEC is decidedly not dead, and that Wazuh has been suffering stability problems. OSSEC has a lot of interesting development ahead of it, which you can track on their Github repo.For example, the development roadmap includes eliminating Logstash from the pipeline used by many OSSEC users. OSSEC would feed directly into Elasticsearch. One speaker noted that Logstash has a 1.7 GB memory footprint, which astounded me.On a related note, the OSSEC team is planning to create a new Web console, with a design goal to have it run in an "AWS t2.micro" instance. The team noted that instance offers 2 GB memory, which doesn't match what AWS says. Perhaps they meant t2.micro and 1 GB memory, or t2.small with 2 GB memory. I think they mean t2.micro with 1 GB RAM, as that is the free tier. Either way, I'm excited to see this later in 2019.Second, I thought the presentation by security personnel from USA Today offered an interesting insight. One design goal they had for monitoring their Google Cloud Platform (GCP) was to not install OSSEC on every container or on Kubernetes worker nodes. Several times during the conference, speakers noted that the transient nature of cloud infrastructure is directly antithetical to standard OSSEC usage, whereby OSSEC is installed on servers with long uptime and years of service. Instead, USA Today used OSSEC to monitor HTTP logs from the GCP load balancer, logs from Google Kubernetes Engine, and monitored processes by watching output from successive kubectl invocations.Third, a speaker from Red Hat brought my attention to an aspect of containers that I had not considered. Docker and containers had made software testing and deployment a lot easier for everyone. However, those who provide containers have effectively become Linux distribution maintainers. In other words, who is responsible when a security or configuration vulnerability in a Linux component is discovered? Will the container maintainers be responsive?Another speaker emphasized the difference between "security of the cloud," offered by cloud providers, and "security in the cloud," which is supposed to be the customer\ |
Vulnerability | Uber | ||
| 2019-03-13 16:15:01 | Thoughts on Cloud Security (lien direct) |  Recently I've been reading about cloud security and security with respect to DevOps. I'll say more about the excellent book I'm reading, but I had a moment of déjà vu during one section.The book described how cloud security is a big change from enterprise security because it relies less on IP-address-centric controls and more on users and groups. The book talked about creating security groups, and adding users to those groups in order to control their access and capabilities.As I read that passage, it reminded me of a time long ago, in the late 1990s, when I was studying for the MCSE, then called the Microsoft Certified Systems Engineer. I read the book at left, Windows NT Security Handbook, published in 1996 by Tom Sheldon. It described the exact same security process of creating security groups and adding users. This was core to the new NT 4 role based access control (RBAC) implementation.Now, fast forward a few years, or all the way to today, and consider the security challenges facing the majority of legacy enterprises: securing Windows assets and the data they store and access. How could this wonderful security model, based on decades of experience (from the 1960s and 1970s no less), have failed to work in operational environments?There are many reasons one could cite, but I think the following are at least worthy of mention.The systems enforcing the security model are exposed to intruders.Furthermore:Intruders are generally able to gain code execution on systems participating in the security model.Finally:Intruders have access to the network traffic which partially contains elements of the security model.From these weaknesses, a large portion of the security countermeasures of the last two decades have been derived as compensating controls and visibility requirements.The question then becomes:Does this change with the cloud?In brief, I believe the answer is largely "yes," thankfully. Generally, the systems upon which the security model is being enforced are not able to access the enforcement mechanism, thanks to the wonders of virtualization.Should an intruder find a way to escape from their restricted cloud platform and gain hypervisor or management network access, then they find themselves in a situation similar to the average Windows domain network.This realization puts a heavy burden on the cloud infrastructure operators. They major players are likely able to acquire and apply the expertise and resources to make their infrastructure far more resilient and survivable than their enterprise counterparts.The weakness will likely be their personnel.Once the compute and network components are sufficiently robust from externally sourced compromise, then internal threats become the next most cost-effective and return-producing vectors for dedicated intruders.Is there anything users can do as they hand their compute and data assets to cloud operators?I suggest four moves.First, small- to mid-sized cloud infrastructure users will likely have to piggyback or free-ride on the initiatives and influence of the largest cloud customers, who have the clout and hopefully the expertise to hold the cloud operators responsible for the security of everyone's data.Second, lawmakers may also need imp Recently I've been reading about cloud security and security with respect to DevOps. I'll say more about the excellent book I'm reading, but I had a moment of déjà vu during one section.The book described how cloud security is a big change from enterprise security because it relies less on IP-address-centric controls and more on users and groups. The book talked about creating security groups, and adding users to those groups in order to control their access and capabilities.As I read that passage, it reminded me of a time long ago, in the late 1990s, when I was studying for the MCSE, then called the Microsoft Certified Systems Engineer. I read the book at left, Windows NT Security Handbook, published in 1996 by Tom Sheldon. It described the exact same security process of creating security groups and adding users. This was core to the new NT 4 role based access control (RBAC) implementation.Now, fast forward a few years, or all the way to today, and consider the security challenges facing the majority of legacy enterprises: securing Windows assets and the data they store and access. How could this wonderful security model, based on decades of experience (from the 1960s and 1970s no less), have failed to work in operational environments?There are many reasons one could cite, but I think the following are at least worthy of mention.The systems enforcing the security model are exposed to intruders.Furthermore:Intruders are generally able to gain code execution on systems participating in the security model.Finally:Intruders have access to the network traffic which partially contains elements of the security model.From these weaknesses, a large portion of the security countermeasures of the last two decades have been derived as compensating controls and visibility requirements.The question then becomes:Does this change with the cloud?In brief, I believe the answer is largely "yes," thankfully. Generally, the systems upon which the security model is being enforced are not able to access the enforcement mechanism, thanks to the wonders of virtualization.Should an intruder find a way to escape from their restricted cloud platform and gain hypervisor or management network access, then they find themselves in a situation similar to the average Windows domain network.This realization puts a heavy burden on the cloud infrastructure operators. They major players are likely able to acquire and apply the expertise and resources to make their infrastructure far more resilient and survivable than their enterprise counterparts.The weakness will likely be their personnel.Once the compute and network components are sufficiently robust from externally sourced compromise, then internal threats become the next most cost-effective and return-producing vectors for dedicated intruders.Is there anything users can do as they hand their compute and data assets to cloud operators?I suggest four moves.First, small- to mid-sized cloud infrastructure users will likely have to piggyback or free-ride on the initiatives and influence of the largest cloud customers, who have the clout and hopefully the expertise to hold the cloud operators responsible for the security of everyone's data.Second, lawmakers may also need imp |
||||
| 2019-02-09 09:30:04 | Forcing the Adversary to Pursue Insider Theft (lien direct) |  Jack Crook pointed me toward a story by Christopher Burgess about intellectual property theft by "Hongjin Tan, a 35 year old Chinese national and U.S. legal permanent resident... [who] was arrested on December 20 and charged with theft of trade secrets. Tan is alleged to have stolen the trade secrets from his employer, a U.S. petroleum company," according to the criminal complaint filed by the US DoJ.Tan's former employer and the FBI allege that Tan "downloaded restricted files to a personal thumb drive." I could not tell from the complaint if Tan downloaded the files at work or at home, but the thumb drive ended up at Tan's home. His employer asked Tan to bring it to their office, which Tan did. However, he had deleted all the files from the drive. Tan's employer recovered the files using commercially available forensic software.This incident, by definition, involves an "insider threat." Tan was an employee who appears to have copied information that was outside the scope of his work responsibilities, resigned from his employer, and was planning to return to China to work for a competitor, having delivered his former employer's intellectual property.When I started GE-CIRT in 2008 (officially "initial operating capability" on 1 January 2009), one of the strategies we pursued involved insider threats. I've written about insiders on this blog before but I couldn't find a description of the strategy we implemented via GE-CIRT.We sought to make digital intrusions more expensive than physical intrusions.In other words, we wanted to make it easier for the adversary to accomplish his mission using insiders. We wanted to make it more difficult for the adversary to accomplish his mission using our network.In a cynical sense, this makes security someone else's problem. Suddenly the physical security team is dealing with the worst of the worst!This is a win for everyone, however. Consider the many advantages the physical security team has over the digital security team.The physical security team can work with human resources during the hiring process. HR can run background checks and identify suspicious job applicants prior to granting employment and access.Employees are far more exposed than remote intruders. Employees, even under cover, expose their appearance, likely residence, and personalities to the company and its workers.Employees can be subject to far more intensive monitoring than remote intruders. Employee endpoints can be instrumented. Employee workspaces are instrumented via access cards, cameras at entry and exit points, and other measures.Employers can cooperate with law enforcement to investigate and prosecute employees. They can control and deter theft and other activities.In brief, insider theft, like all "close access" activities, is incredibly risky for the adversary. It is a win for everyone when the adversary must resort to using insiders to accomplish their mission. Digital and physical security must cooperate t Jack Crook pointed me toward a story by Christopher Burgess about intellectual property theft by "Hongjin Tan, a 35 year old Chinese national and U.S. legal permanent resident... [who] was arrested on December 20 and charged with theft of trade secrets. Tan is alleged to have stolen the trade secrets from his employer, a U.S. petroleum company," according to the criminal complaint filed by the US DoJ.Tan's former employer and the FBI allege that Tan "downloaded restricted files to a personal thumb drive." I could not tell from the complaint if Tan downloaded the files at work or at home, but the thumb drive ended up at Tan's home. His employer asked Tan to bring it to their office, which Tan did. However, he had deleted all the files from the drive. Tan's employer recovered the files using commercially available forensic software.This incident, by definition, involves an "insider threat." Tan was an employee who appears to have copied information that was outside the scope of his work responsibilities, resigned from his employer, and was planning to return to China to work for a competitor, having delivered his former employer's intellectual property.When I started GE-CIRT in 2008 (officially "initial operating capability" on 1 January 2009), one of the strategies we pursued involved insider threats. I've written about insiders on this blog before but I couldn't find a description of the strategy we implemented via GE-CIRT.We sought to make digital intrusions more expensive than physical intrusions.In other words, we wanted to make it easier for the adversary to accomplish his mission using insiders. We wanted to make it more difficult for the adversary to accomplish his mission using our network.In a cynical sense, this makes security someone else's problem. Suddenly the physical security team is dealing with the worst of the worst!This is a win for everyone, however. Consider the many advantages the physical security team has over the digital security team.The physical security team can work with human resources during the hiring process. HR can run background checks and identify suspicious job applicants prior to granting employment and access.Employees are far more exposed than remote intruders. Employees, even under cover, expose their appearance, likely residence, and personalities to the company and its workers.Employees can be subject to far more intensive monitoring than remote intruders. Employee endpoints can be instrumented. Employee workspaces are instrumented via access cards, cameras at entry and exit points, and other measures.Employers can cooperate with law enforcement to investigate and prosecute employees. They can control and deter theft and other activities.In brief, insider theft, like all "close access" activities, is incredibly risky for the adversary. It is a win for everyone when the adversary must resort to using insiders to accomplish their mission. Digital and physical security must cooperate t |
||||
| 2019-01-29 15:30:05 | Fixing Virtualbox RDP Server with DetectionLab (lien direct) | Yesterday I posted about DetectionLab, but noted that I was having trouble with the RDP servers offered by Virtualbox. If you remember, DetectionLab builds four virtual machines:root@LAPTOP-HT4TGVCP C:\Users\root>"c:\Program Files\Oracle\VirtualBox\VBoxManage" list runningvms"logger" {3da9fffb-4b02-4e57-a592-dd2322f14245}"dc.windomain.local" {ef32d493-845c-45dc-aff7-3a86d9c590cd}"wef.windomain.local" {7cd008b7-c6e0-421d-9655-8f92ec98d9d7}"win10.windomain.local" {acf413fb-6358-44df-ab9f-cc7767ed32bd}I was having a problem with two of the VMs sharing the same port for the RDP server offered by Virtualbox. This meant I could not access one of them. (Below, port 5932 has the conflict.)root@LAPTOP-HT4TGVCP C:\Users\root\git\detectionlab\DetectionLab\Vagrant>"c:\Program Files\Oracle\VirtualBox\VBoxManage" showvminfo logger | findstr /I vrde | findstr /I addressVRDE: enabled (Address 0.0.0.0, Ports 5955, MultiConn: off, ReuseSingleConn: off, Authentication type: null)VRDE property : TCP/Address = "0.0.0.0"root@LAPTOP-HT4TGVCP C:\Users\root\git\detectionlab\DetectionLab\Vagrant>"c:\Program Files\Oracle\VirtualBox\VBoxManage" showvminfo dc.windomain.local | findstr /I vrde | findstr /I addressVRDE: enabled (Address 0.0.0.0, Ports 5932, MultiConn: off, ReuseSingleConn: off, Authentication type: null)VRDE property : TCP/Address = "0.0.0.0"root@LAPTOP-HT4TGVCP C:\Users\root\git\detectionlab\DetectionLab\Vagrant>"c:\Program Files\Oracle\VirtualBox\VBoxManage" showvminfo wef.windomain.local | findstr /I vrde | findstr /I addressVRDE: enabled (Address 0.0.0.0, Ports 5932, MultiConn: off, ReuseSingleConn: off, Authentication type: null)VRDE property : TCP/Address = "0.0.0.0"root@LAPTOP-HT4TGVCP C:\Users\root\git\detectionlab\DetectionLab\Vagrant>"c:\Program Files\Oracle\VirtualBox\VBoxManage" showvminfo win10.windomain.local | | ||||
| 2019-01-28 16:00:00 | Trying DetectionLab (lien direct) |  Many security professionals run personal labs. Trying to create an environment that includes fairly modern Windows systems can be a challenge. In the age of "infrastructure as code," there should be a simpler way to deploy systems in a repeatable, virtualized way -- right?Enter DetectionLab, a project by Chris Long. Briefly, Chris built a project that uses Packer and Vagrant to create an instrumented lab environment. Chris explained the project in late 2017 in a Medium post, which I recommend reading.I can't even begin to describe all the functionality packed into this project. So much of it is new, but this is a great way to learn about it. In this post, I would like to show how I got a version of DetectionLab running.My build environment included a modern laptop with 16 GB RAM and Windows 10 professional. I had already installed Virtualbox 6.0 with the appropriate VirtualBox Extension Pack. I had also enabled the native OpenSSH server and performed all DetectionLab installation functions over an OpenSSH session.Install ChocolateyMy first step was to install Chocolatey, a package manager for Windows. I wanted to use this to install the Git client I wanted to use to clone the DetectionLab repo. Commands I typed at each stage are in bold below.root@LAPTOP-HT4TGVCP C:\Users\root>@"%SystemRoot%\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -InputFormat None -ExecutionPolicy Bypass -Command "iex ((New-Object System.Net.WebClient).DownloadString('https://chocolatey.org/install.ps1'))" && SET "PATH=%PATH%;%ALLUSERSPROFILE%\chocolatey\bin"Getting latest version of the Chocolatey package for download.Getting Chocolatey from https://chocolatey.org/api/v2/package/chocolatey/0.10.11.Downloading 7-Zip commandline tool prior to extraction.Extracting C:\Users\root\AppData\Local\Temp\chocolatey\chocInstall\chocolatey.zip to C:\Users\root\AppData\Local\Temp\chocolatey\chocInstall...Installing chocolatey on this machineCreating ChocolateyInstall as an environment variable (targeting 'Machine') Setting ChocolateyInstall to 'C:\ProgramData\chocolatey'WARNING: It's very likely you will need to close and reopen your shell before you can use choco. Many security professionals run personal labs. Trying to create an environment that includes fairly modern Windows systems can be a challenge. In the age of "infrastructure as code," there should be a simpler way to deploy systems in a repeatable, virtualized way -- right?Enter DetectionLab, a project by Chris Long. Briefly, Chris built a project that uses Packer and Vagrant to create an instrumented lab environment. Chris explained the project in late 2017 in a Medium post, which I recommend reading.I can't even begin to describe all the functionality packed into this project. So much of it is new, but this is a great way to learn about it. In this post, I would like to show how I got a version of DetectionLab running.My build environment included a modern laptop with 16 GB RAM and Windows 10 professional. I had already installed Virtualbox 6.0 with the appropriate VirtualBox Extension Pack. I had also enabled the native OpenSSH server and performed all DetectionLab installation functions over an OpenSSH session.Install ChocolateyMy first step was to install Chocolatey, a package manager for Windows. I wanted to use this to install the Git client I wanted to use to clone the DetectionLab repo. Commands I typed at each stage are in bold below.root@LAPTOP-HT4TGVCP C:\Users\root>@"%SystemRoot%\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -InputFormat None -ExecutionPolicy Bypass -Command "iex ((New-Object System.Net.WebClient).DownloadString('https://chocolatey.org/install.ps1'))" && SET "PATH=%PATH%;%ALLUSERSPROFILE%\chocolatey\bin"Getting latest version of the Chocolatey package for download.Getting Chocolatey from https://chocolatey.org/api/v2/package/chocolatey/0.10.11.Downloading 7-Zip commandline tool prior to extraction.Extracting C:\Users\root\AppData\Local\Temp\chocolatey\chocInstall\chocolatey.zip to C:\Users\root\AppData\Local\Temp\chocolatey\chocInstall...Installing chocolatey on this machineCreating ChocolateyInstall as an environment variable (targeting 'Machine') Setting ChocolateyInstall to 'C:\ProgramData\chocolatey'WARNING: It's very likely you will need to close and reopen your shell before you can use choco. |
||||
| 2019-01-08 09:03:39 | Happy 16th Birthday TaoSecurity Blog (lien direct) |  Today, 8 January 2019, is TaoSecurity Blog's 16th birthday! This is also my 3,041st blog post.I wrote my first post on 8 January 2003 while working as an incident response consultant for Foundstone.Here are a few statistics on the blog. Blogger started providing statistics in May 2010, so these apply to roughly the past 9 years only.As of today, since May 2010 the blog has nearly 9.4 million all time page views, up from 7.7 million a year ago.Here are the most popular posts of the last 9 years, as of today: Today, 8 January 2019, is TaoSecurity Blog's 16th birthday! This is also my 3,041st blog post.I wrote my first post on 8 January 2003 while working as an incident response consultant for Foundstone.Here are a few statistics on the blog. Blogger started providing statistics in May 2010, so these apply to roughly the past 9 years only.As of today, since May 2010 the blog has nearly 9.4 million all time page views, up from 7.7 million a year ago.Here are the most popular posts of the last 9 years, as of today: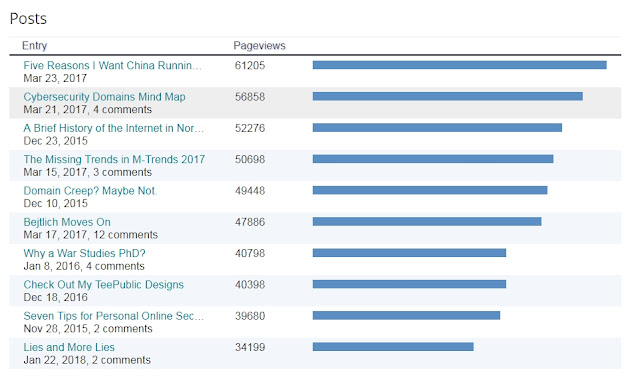 I'm blogging a bit more recently, with 22 posts in 2018 -- more than my total for 2016 and 2017 combined, but still not half as much as 2015, which saw 55 posts.Twitter continues to play a role in the way I communicate. Last year @taosecurity had nearly 49,000 followers with less than 18,000 Tweets. Today I have nearly 53,000 followers with 19,000 Tweets.My rule is generally this: if I start wondering how to fit an idea in 280 characters on Twitter, then a blog post is a better idea. If I start a Twitter "thread," then I really need to write a blog post!I continue to blog about martial arts and related topics at Rejoining the Tao, which incidentally will be three years old later this month, and is currently 11 posts shy of 100. You can see that during my burnout period I shifted my writing and creativity outside of security.Thank you to everyone who has been part of this blog's journey since 2003!Copyright 2003-2018 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) I'm blogging a bit more recently, with 22 posts in 2018 -- more than my total for 2016 and 2017 combined, but still not half as much as 2015, which saw 55 posts.Twitter continues to play a role in the way I communicate. Last year @taosecurity had nearly 49,000 followers with less than 18,000 Tweets. Today I have nearly 53,000 followers with 19,000 Tweets.My rule is generally this: if I start wondering how to fit an idea in 280 characters on Twitter, then a blog post is a better idea. If I start a Twitter "thread," then I really need to write a blog post!I continue to blog about martial arts and related topics at Rejoining the Tao, which incidentally will be three years old later this month, and is currently 11 posts shy of 100. You can see that during my burnout period I shifted my writing and creativity outside of security.Thank you to everyone who has been part of this blog's journey since 2003!Copyright 2003-2018 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com) |
||||
| 2018-12-31 17:46:00 | Notes on Self-Publishing a Book (lien direct) |  In this post I would like to share a few thoughts on self-publishing a book, in case anyone is considering that option.As I mentioned in my post on burnout, one of my goals was to publish a book on a subject other than cyber security. A friend from my Krav Maga school, Anna Wonsley, learned that I had published several books, and asked if we might collaborate on a book about stretching. The timing was right, so I agreed.I published my first book with Pearson and Addison-Wesley in 2004, and my last with No Starch in 2013. 14 years is an eternity in the publishing world, and even in the last 5 years the economics and structure of book publishing have changed quite a bit.To better understand the changes, I had dinner with one of the finest technical authors around, Michael W. Lucas. We met prior to my interest in this book, because I had wondered about publishing books on my own. MWL started in traditional publishing like me, but has since become a full-time author and independent publisher. He explained the pros and cons of going it alone, which I carefully considered.By the end of 2017, Anna and I were ready to begin work on the book. I believe our first "commits" occurred in December 2017.For this stretching book project, I knew my strengths included organization, project management, writing to express another person's message, editing, and access to a skilled lead photographer. I learned that my co-author's strengths included subject matter expertise, a willingness to be photographed for the book's many pictures, and friends who would also be willing to be photographed.None of us was very familiar with the process of transforming a raw manuscript and photos into a finished product. When I had published with Pearson and No Starch, they took care of that process, as well as copy-editing. In this post I would like to share a few thoughts on self-publishing a book, in case anyone is considering that option.As I mentioned in my post on burnout, one of my goals was to publish a book on a subject other than cyber security. A friend from my Krav Maga school, Anna Wonsley, learned that I had published several books, and asked if we might collaborate on a book about stretching. The timing was right, so I agreed.I published my first book with Pearson and Addison-Wesley in 2004, and my last with No Starch in 2013. 14 years is an eternity in the publishing world, and even in the last 5 years the economics and structure of book publishing have changed quite a bit.To better understand the changes, I had dinner with one of the finest technical authors around, Michael W. Lucas. We met prior to my interest in this book, because I had wondered about publishing books on my own. MWL started in traditional publishing like me, but has since become a full-time author and independent publisher. He explained the pros and cons of going it alone, which I carefully considered.By the end of 2017, Anna and I were ready to begin work on the book. I believe our first "commits" occurred in December 2017.For this stretching book project, I knew my strengths included organization, project management, writing to express another person's message, editing, and access to a skilled lead photographer. I learned that my co-author's strengths included subject matter expertise, a willingness to be photographed for the book's many pictures, and friends who would also be willing to be photographed.None of us was very familiar with the process of transforming a raw manuscript and photos into a finished product. When I had published with Pearson and No Starch, they took care of that process, as well as copy-editing. Beyond turning manuscript and photos into a book, I also had to identify a publication platform. Early on we decided to self-publish using one of the many newer companies offering that service. We wanted a company that could get our book into Amazon, and possibly physical book stores as well. We did not want to try working with a traditional publisher, as we felt that we could manage most aspects of the publishing process ourselves, and augment with specialized help where needed.After a lot of research we chose Blurb. One of the most attractive aspects of Blurb was their expert ecosystem. We decided that we would hire one of these experts to handle th Beyond turning manuscript and photos into a book, I also had to identify a publication platform. Early on we decided to self-publish using one of the many newer companies offering that service. We wanted a company that could get our book into Amazon, and possibly physical book stores as well. We did not want to try working with a traditional publisher, as we felt that we could manage most aspects of the publishing process ourselves, and augment with specialized help where needed.After a lot of research we chose Blurb. One of the most attractive aspects of Blurb was their expert ecosystem. We decided that we would hire one of these experts to handle th |
Guideline | |||
| 2018-12-21 16:30:11 | Managing Burnout (lien direct) |  This is not strictly an information security post, but the topic likely affects a decent proportion of my readership.Within the last few years I experienced a profound professional "burnout." I've privately mentioned this to colleagues in the industry, and heard similar stories or requests for advice on how to handle burnout.I want to share my story in the hopes that it helps others in the security scene, either by coping with existing burnout or preparing for a possible burnout.How did burnout manifest for me? It began with FireEye's acquisition of Mandiant, almost exactly five years ago. 2013 was a big year for Mandiant, starting with the APT1 report in early 2013 and concluding with the acquisition in December.The prospect of becoming part of a Silicon Valley software company initially seemed exciting, because we would presumably have greater resources to battle intruders. Soon, however, I found myself at odds with FireEye's culture and managerial habits, and I wondered what I was doing inside such a different company.(It's important to note that the appointment of Kevin Mandia as CEO in June 2016 began a cultural and managerial shift. I give Kevin and his lieutenants credit for helping transform the company since then. Kevin's appointment was too late for me, but I applaud the work he has done over the last few years.)Starting in late 2014 and progressing in 2015, I became less interested in security. I was aggravated every time I saw the same old topics arise in social or public media. I did not see the point of continuing to debate issues which were never solved. I was demoralized and frustrated.At this time I was also working on my PhD with King's College London. I had added this stress myself, but I felt like I could manage it. I had earned two major and two minor degrees in four years as an Air Force Academy cadet. Surely I could write a thesis!Late in 2015 I realized that I needed to balance the very cerebral art of information security with a more physical activity. I took a Krav Maga class the first week of January 2016. It was invigorating and I began a new blog, Rejoining the Tao, that month. I began to consider options outside of informations security.In early 2016 my wife began considering ways to rejoin the W-2 workforce, after having stayed home with our kids for 12 years. We discussed the possibility of me leaving my W-2 job and taking a primary role with the kids. By mid-2016 she had a new job and I was open to departing FireEye.By late 2016 I also realized that I was not cut out to be a PhD candidate. Although I had written several books, I did not have the right mindset or attitude to continue writing my thesis. After two years I quit my PhD program. This was the first time I had quit anything significant in my life, and it was the right decision for me. (The Churchill "never, never, never give up" speech is fine advice when defending your nation's existence, but it's stupid advice if you're not happy with the path you're following.)In March 2017 I posted Bejtlich Moves On, where I said I was leaving FireEye. I would offer security consulting in the short term, and would open a Krav Maga school in the long-term. This was my break with the security This is not strictly an information security post, but the topic likely affects a decent proportion of my readership.Within the last few years I experienced a profound professional "burnout." I've privately mentioned this to colleagues in the industry, and heard similar stories or requests for advice on how to handle burnout.I want to share my story in the hopes that it helps others in the security scene, either by coping with existing burnout or preparing for a possible burnout.How did burnout manifest for me? It began with FireEye's acquisition of Mandiant, almost exactly five years ago. 2013 was a big year for Mandiant, starting with the APT1 report in early 2013 and concluding with the acquisition in December.The prospect of becoming part of a Silicon Valley software company initially seemed exciting, because we would presumably have greater resources to battle intruders. Soon, however, I found myself at odds with FireEye's culture and managerial habits, and I wondered what I was doing inside such a different company.(It's important to note that the appointment of Kevin Mandia as CEO in June 2016 began a cultural and managerial shift. I give Kevin and his lieutenants credit for helping transform the company since then. Kevin's appointment was too late for me, but I applaud the work he has done over the last few years.)Starting in late 2014 and progressing in 2015, I became less interested in security. I was aggravated every time I saw the same old topics arise in social or public media. I did not see the point of continuing to debate issues which were never solved. I was demoralized and frustrated.At this time I was also working on my PhD with King's College London. I had added this stress myself, but I felt like I could manage it. I had earned two major and two minor degrees in four years as an Air Force Academy cadet. Surely I could write a thesis!Late in 2015 I realized that I needed to balance the very cerebral art of information security with a more physical activity. I took a Krav Maga class the first week of January 2016. It was invigorating and I began a new blog, Rejoining the Tao, that month. I began to consider options outside of informations security.In early 2016 my wife began considering ways to rejoin the W-2 workforce, after having stayed home with our kids for 12 years. We discussed the possibility of me leaving my W-2 job and taking a primary role with the kids. By mid-2016 she had a new job and I was open to departing FireEye.By late 2016 I also realized that I was not cut out to be a PhD candidate. Although I had written several books, I did not have the right mindset or attitude to continue writing my thesis. After two years I quit my PhD program. This was the first time I had quit anything significant in my life, and it was the right decision for me. (The Churchill "never, never, never give up" speech is fine advice when defending your nation's existence, but it's stupid advice if you're not happy with the path you're following.)In March 2017 I posted Bejtlich Moves On, where I said I was leaving FireEye. I would offer security consulting in the short term, and would open a Krav Maga school in the long-term. This was my break with the security |
APT 1 | |||
| 2018-12-18 11:22:26 | The Origin of the Quote "There Are Two Types of Companies" (lien direct) |  While listening to a webcast this morning, I heard the speaker mentionThere are two types of companies: those who have been hacked, and those who don't yet know they have been hacked.He credited Cisco CEO John Chambers but didn't provide any source.That didn't sound right to me. I could think of two possible antecedents. so I did some research. I confirmed my memory and would like to present what I found here.John Chambers did indeed offer the previous quote, in a January 2015 post for the World Economic Forum titled What does the Internet of Everything mean for security? Unfortunately, neither Mr Chambers nor the person who likely wrote the article for him decided to credit the author of this quote.Before providing proper credit for this quote, we need to decide what the quote actually says. As noted in this October 2015 article by Frank Johnson titled Are there really only “two kinds of enterprises”?, there are really (at least) two versions of this quote:A popular meme in the information security industry is, “There are only two types of companies: those that know they've been compromised, and those that don't know.”And the second is like unto it: “There are only two kinds of companies: those that have been hacked, and those that will be.”We see that the first is a version of what Mr Chambers said. Let's call that 2-KNOW. The second is different. Let's call that 2-BE.The first version, 2-KNOW, can be easily traced and credited to Dmitri Alperovitch. He stated this proposition as part of the publicity around his Shady RAT report, written while he worked at McAfee. For example, this 3 August 2011 story by Ars Technica, Operation Shady RAT: five-year hack attack hit 14 countries, quotes Dmitri in the following:So widespread are the attacks that Dmitri Alperovitch, McAfee Vice President of Threat Research, said that the only companies not at risk are those who have nothing worth taking, and that of the world's biggest firms, there are just two kinds: those that know they've been compromised, and those that still haven't realized they've been compromised.Dmitri used slightly different language in this popular Vanity Fair article from September 2011, titled Enter the Cyber-Dragon:Dmitri Alperovitch, who discovered Operation Shady rat, draws a stark lesson: “There are only two types of companies-those that know they've been compromised, and those that don't know. If you have anything that may be valuable to a competitor, you will be targeted, and almost certainly compromised.”No doubt former FBI Director Mueller read this report (and probably spoke with Dmitri). He delivered a speech at RSA on 1 March 2012 that introduced question 2-BE into the lexicon, plus a little more:For it is no longer a question of “if,” but “when” and While listening to a webcast this morning, I heard the speaker mentionThere are two types of companies: those who have been hacked, and those who don't yet know they have been hacked.He credited Cisco CEO John Chambers but didn't provide any source.That didn't sound right to me. I could think of two possible antecedents. so I did some research. I confirmed my memory and would like to present what I found here.John Chambers did indeed offer the previous quote, in a January 2015 post for the World Economic Forum titled What does the Internet of Everything mean for security? Unfortunately, neither Mr Chambers nor the person who likely wrote the article for him decided to credit the author of this quote.Before providing proper credit for this quote, we need to decide what the quote actually says. As noted in this October 2015 article by Frank Johnson titled Are there really only “two kinds of enterprises”?, there are really (at least) two versions of this quote:A popular meme in the information security industry is, “There are only two types of companies: those that know they've been compromised, and those that don't know.”And the second is like unto it: “There are only two kinds of companies: those that have been hacked, and those that will be.”We see that the first is a version of what Mr Chambers said. Let's call that 2-KNOW. The second is different. Let's call that 2-BE.The first version, 2-KNOW, can be easily traced and credited to Dmitri Alperovitch. He stated this proposition as part of the publicity around his Shady RAT report, written while he worked at McAfee. For example, this 3 August 2011 story by Ars Technica, Operation Shady RAT: five-year hack attack hit 14 countries, quotes Dmitri in the following:So widespread are the attacks that Dmitri Alperovitch, McAfee Vice President of Threat Research, said that the only companies not at risk are those who have nothing worth taking, and that of the world's biggest firms, there are just two kinds: those that know they've been compromised, and those that still haven't realized they've been compromised.Dmitri used slightly different language in this popular Vanity Fair article from September 2011, titled Enter the Cyber-Dragon:Dmitri Alperovitch, who discovered Operation Shady rat, draws a stark lesson: “There are only two types of companies-those that know they've been compromised, and those that don't know. If you have anything that may be valuable to a competitor, you will be targeted, and almost certainly compromised.”No doubt former FBI Director Mueller read this report (and probably spoke with Dmitri). He delivered a speech at RSA on 1 March 2012 that introduced question 2-BE into the lexicon, plus a little more:For it is no longer a question of “if,” but “when” and |
Hack Threat | |||
| 2018-11-25 15:48:54 | The Origin of the Term Indicators of Compromise (IOCs) (lien direct) |  I am an historian. I practice digital security, but I earned a bachelor's of science degree in history from the United States Air Force Academy. (1)Historians create products by analyzing artifacts, among which the most significant is the written word.In my last post, I talked about IOCs, or indicators of compromise. Do you know the origin of the term? I thought I did, but I wanted to rely on my historian's methodology to invalidate or confirm my understanding.I became aware of the term "indicator" as an element of indications and warning (I&W), when I attended Air Force Intelligence Officer's school in 1996-1997. I will return to this shortly, but I did not encounter the term "indicator" in a digital security context until I encountered the work of Kevin Mandia.In August 2001, shortly after its publication, I read Incident Response: Investigating Computer Crime, by Kevin Mandia, Chris Prosise, and Matt Pepe (Osborne/McGraw-Hill). I was so impressed by this work that I managed to secure a job with their company, Foundstone, by April 2002. I joined the Foundstone incident response team, which was led by Kevin and consisted of Matt Pepe, Keith Jones, Julie Darmstadt, and me.I Tweeted earlier today that Kevin invented the term "indicator" (in the IR context) in that 2001 edition, but a quick review of the hard copy in my library does not show its usage, at least not prominently. I believe we were using the term in the office but that it had not appeared in the 2001 book. Documentation would seem to confirm that, as Kevin was working on the second edition of the IR book (to which I contributed), and that version, published in 2003, features the term "indicator" in multiple locations.In fact, the earliest use of the term "indicators of compromise," appearing in print in a digital security context, appears on page 280 in Incident Response & Computer Forensics, 2nd Edition. I am an historian. I practice digital security, but I earned a bachelor's of science degree in history from the United States Air Force Academy. (1)Historians create products by analyzing artifacts, among which the most significant is the written word.In my last post, I talked about IOCs, or indicators of compromise. Do you know the origin of the term? I thought I did, but I wanted to rely on my historian's methodology to invalidate or confirm my understanding.I became aware of the term "indicator" as an element of indications and warning (I&W), when I attended Air Force Intelligence Officer's school in 1996-1997. I will return to this shortly, but I did not encounter the term "indicator" in a digital security context until I encountered the work of Kevin Mandia.In August 2001, shortly after its publication, I read Incident Response: Investigating Computer Crime, by Kevin Mandia, Chris Prosise, and Matt Pepe (Osborne/McGraw-Hill). I was so impressed by this work that I managed to secure a job with their company, Foundstone, by April 2002. I joined the Foundstone incident response team, which was led by Kevin and consisted of Matt Pepe, Keith Jones, Julie Darmstadt, and me.I Tweeted earlier today that Kevin invented the term "indicator" (in the IR context) in that 2001 edition, but a quick review of the hard copy in my library does not show its usage, at least not prominently. I believe we were using the term in the office but that it had not appeared in the 2001 book. Documentation would seem to confirm that, as Kevin was working on the second edition of the IR book (to which I contributed), and that version, published in 2003, features the term "indicator" in multiple locations.In fact, the earliest use of the term "indicators of compromise," appearing in print in a digital security context, appears on page 280 in Incident Response & Computer Forensics, 2nd Edition. From other uses of the term "indicators" in that IR book, you can observe that IOC wasn't a formal, independent concept at this point, in 2003. In the same excerpt above you see "indicators of attack" mentioned.The first citation of the term "indicators" in the 2003 book shows it is meant as an investigative lead or tip: From other uses of the term "indicators" in that IR book, you can observe that IOC wasn't a formal, independent concept at this point, in 2003. In the same excerpt above you see "indicators of attack" mentioned.The first citation of the term "indicators" in the 2003 book shows it is meant as an investigative lead or tip: |
Malware Tool Guideline | |||
| 2018-11-24 15:23:09 | Even More on Threat Hunting (lien direct) |  In response to my post More on Threat Hunting, Rob Lee asked:[D]o you consider detection through ID'ing/“matching” TTPs not hunting?To answer this question, we must begin by clarifying "TTPs." Most readers know TTPs to mean tactics, techniques and procedures, defined by David Bianco in his Pyramid of Pain post as:How the adversary goes about accomplishing their mission, from reconnaissance all the way through data exfiltration and at every step in between.In case you've forgotten David's pyramid, it looks like this. In response to my post More on Threat Hunting, Rob Lee asked:[D]o you consider detection through ID'ing/“matching” TTPs not hunting?To answer this question, we must begin by clarifying "TTPs." Most readers know TTPs to mean tactics, techniques and procedures, defined by David Bianco in his Pyramid of Pain post as:How the adversary goes about accomplishing their mission, from reconnaissance all the way through data exfiltration and at every step in between.In case you've forgotten David's pyramid, it looks like this. It's important to recognize that the pyramid consists of indicators of compromise (IOCs). David uses the term "indicator" in his original post, but his follow-up post from his time at Sqrrl makes this clear:There are a wide variety of IoCs ranging from basic file hashes to hacking Tactics, Techniques and Procedures (TTPs). Sqrrl Security Architect, David Bianco, uses a concept called the Pyramid of Pain to categorize IoCs. At this point it should be clear that I consider TTPs to be one form of IOC.In The Practice of Network Security Monitoring, I included the following workflow: It's important to recognize that the pyramid consists of indicators of compromise (IOCs). David uses the term "indicator" in his original post, but his follow-up post from his time at Sqrrl makes this clear:There are a wide variety of IoCs ranging from basic file hashes to hacking Tactics, Techniques and Procedures (TTPs). Sqrrl Security Architect, David Bianco, uses a concept called the Pyramid of Pain to categorize IoCs. At this point it should be clear that I consider TTPs to be one form of IOC.In The Practice of Network Security Monitoring, I included the following workflow: |
Malware Threat | |||
| 2018-11-23 12:36:47 | More on Threat Hunting (lien direct) |  Earlier this week hellor00t asked via Twitter:Where would you place your security researchers/hunt team?I replied:For me, "hunt" is just a form of detection. I don't see the need to build a "hunt" team. IR teams detect intruders using two major modes: matching and hunting. Junior people spend more time matching. Senior people spend more time hunting. Both can and should do both functions.This inspired Rob Lee to blog a response, from which I extract his core argument:[Hunting] really isn't, to me, about detecting threats...Hunting is a hypothesis-led approach to testing your environment for threats. The purpose, to me, is not in finding threats but in determining what gaps you have in your ability to detect and respond to them...In short, hunting, to me, is a way to assess your security (people, process, and technology) against threats while extending your automation footprint to better be prepared in the future. Or simply stated, it's incident response without the incident that's done with a purpose and contributes something. As background for my answer, I recommend my March 2017 post The Origin of Threat Hunting, which cites my article "Become a Hunter," published in the July-August 2011 issue of Information Security Magazine. I wrote it in the spring of 2011, when I was director of incident response for GE-CIRT.For the term "hunting," I give credit to briefers from the Air Force and NSA who, in the mid-2000s briefed "hunter-killer" missions to the Red Team/Blue Team Symposium at the Johns Hopkins University Applied Physics Lab in Laurel, MD.As a comment to that post, Tony Sager, who ran NSA VAO at the time I was briefed at ReBl, described hunting thus:[Hunting] was an active and sustained search for Attackers...For us, "Hunt" meant a very planned and sustained search, taking advantage of the existing infrastructure of Red/Blue Teams and COMSEC Monitoring, as well as intelligence information to guide the search. For the practice of hunting, as I experienced it, I give credit to our GE-CIRT incident handlers -- David Bianco, Ken Bradley, Tim Crothers, Tyler Hudak, Bamm Visscher, and Aaron Wade -- who took junior analysts on "hunting trips," starting in 2008-2009.It is very clear, to me, that hunting has always been associated with detecting an adversary, not "determining what gaps you have in your ability to detect and respond to them," as characterized by Rob.For me, Rob is describing the job of an enterprise visibility architect, which I described in a 2007 post:[W]e are stuck with numerous platforms, operating systems, applications, and data (POAD) for which we have zero visibility. I suggest that enterprises consider hiring or assigning a new role -- Enterprise Visibility Architect. The role of the EVA is to identify visibility deficiencies in existing and future POAD and Earlier this week hellor00t asked via Twitter:Where would you place your security researchers/hunt team?I replied:For me, "hunt" is just a form of detection. I don't see the need to build a "hunt" team. IR teams detect intruders using two major modes: matching and hunting. Junior people spend more time matching. Senior people spend more time hunting. Both can and should do both functions.This inspired Rob Lee to blog a response, from which I extract his core argument:[Hunting] really isn't, to me, about detecting threats...Hunting is a hypothesis-led approach to testing your environment for threats. The purpose, to me, is not in finding threats but in determining what gaps you have in your ability to detect and respond to them...In short, hunting, to me, is a way to assess your security (people, process, and technology) against threats while extending your automation footprint to better be prepared in the future. Or simply stated, it's incident response without the incident that's done with a purpose and contributes something. As background for my answer, I recommend my March 2017 post The Origin of Threat Hunting, which cites my article "Become a Hunter," published in the July-August 2011 issue of Information Security Magazine. I wrote it in the spring of 2011, when I was director of incident response for GE-CIRT.For the term "hunting," I give credit to briefers from the Air Force and NSA who, in the mid-2000s briefed "hunter-killer" missions to the Red Team/Blue Team Symposium at the Johns Hopkins University Applied Physics Lab in Laurel, MD.As a comment to that post, Tony Sager, who ran NSA VAO at the time I was briefed at ReBl, described hunting thus:[Hunting] was an active and sustained search for Attackers...For us, "Hunt" meant a very planned and sustained search, taking advantage of the existing infrastructure of Red/Blue Teams and COMSEC Monitoring, as well as intelligence information to guide the search. For the practice of hunting, as I experienced it, I give credit to our GE-CIRT incident handlers -- David Bianco, Ken Bradley, Tim Crothers, Tyler Hudak, Bamm Visscher, and Aaron Wade -- who took junior analysts on "hunting trips," starting in 2008-2009.It is very clear, to me, that hunting has always been associated with detecting an adversary, not "determining what gaps you have in your ability to detect and respond to them," as characterized by Rob.For me, Rob is describing the job of an enterprise visibility architect, which I described in a 2007 post:[W]e are stuck with numerous platforms, operating systems, applications, and data (POAD) for which we have zero visibility. I suggest that enterprises consider hiring or assigning a new role -- Enterprise Visibility Architect. The role of the EVA is to identify visibility deficiencies in existing and future POAD and |
Threat | |||
| 2018-11-02 09:20:23 | Cybersecurity and Class M Planets (lien direct) |  I was considering another debate about appropriate cybersecurity measures and I had the following thought: not all networks are the same. Profound, right? This is so obvious, yet so obviously forgotten.Too often when confronting a proposed defensive measure, an audience approaches the concept from their own preconceived notion of what assets need to be protected.Some think about an information technology enterprise organization with endpoints, servers, and infrastructure. Others think about an industrial organization with manufacturing equipment. Others imagine an environment with no network at all, where constituents access cloud-hosted resources. Still others think in terms of being that cloud hosting environment itself.Beyond those elements, we need to consider the number of assets, their geographic diversity, their relative value, and many other aspects that you can no doubt imagine.This made me wonder if we need some sort of easy reference term to capture the essential nature of these sorts of diverse environments. I thought immediately of the term "class M planet," from Star Trek. From the Wikipedia entry:[An] Earth-like planet, the Class M designation is similar to the real-world astronomical theory of life-supporting planets within the habitable zone... Class M planets are said to possess an atmosphere composed of nitrogen and oxygen as well as an abundance of liquid water necessary for carbon-based life to exist. Extensive plant and animal life often flourishes; often, a sentient race is also present. In contrast, consider a class Y planet:Class Y planets are referred to as "demon" worlds, where surface conditions do not fall into any other recognized category. Such worlds are usually hostile and lethal to humanoid life. If life forms develop on these worlds they usually take on many bizarre forms, like living crystal or rock, liquid or gaseous physical states, or incorporeal, dimensional, or energy-based states. Given their work providing names for various offensive security activities in ATT&CK, I wonder if MITRE might consider creating a naming scheme to capture this idea? For example, a "class M" network might be an enterprise organization with endpoints, servers, and infrastructure, of a certain size. Or perhaps M1 might be "small," M2 "medium," and M3 "large," where each is associated with a user count.Perhaps an environment with no network at all, where constituents access cloud-hosted resources, would be a class C network. (I'm not sure "network" is even the right term, if there is no "network" for which the organization is responsible.)With such a scheme in place, we could begin a cybersecurity discussion by asking, "given a class M network, what defensive processes, people, or technology are appropriate," versus "given a class C network, what defensive processes, people, or technology are appropriate."This is only an idea, and I'd be happy if something was already created to address this problem. Comments below are welcome (pending moderation to repel trolls and spammers.) Alternatively, reply to my announcement of this post via @taosecurity on Twitter.Copyright 2003-2018 Richard Bejtlich and TaoSecurity (taosecuri I was considering another debate about appropriate cybersecurity measures and I had the following thought: not all networks are the same. Profound, right? This is so obvious, yet so obviously forgotten.Too often when confronting a proposed defensive measure, an audience approaches the concept from their own preconceived notion of what assets need to be protected.Some think about an information technology enterprise organization with endpoints, servers, and infrastructure. Others think about an industrial organization with manufacturing equipment. Others imagine an environment with no network at all, where constituents access cloud-hosted resources. Still others think in terms of being that cloud hosting environment itself.Beyond those elements, we need to consider the number of assets, their geographic diversity, their relative value, and many other aspects that you can no doubt imagine.This made me wonder if we need some sort of easy reference term to capture the essential nature of these sorts of diverse environments. I thought immediately of the term "class M planet," from Star Trek. From the Wikipedia entry:[An] Earth-like planet, the Class M designation is similar to the real-world astronomical theory of life-supporting planets within the habitable zone... Class M planets are said to possess an atmosphere composed of nitrogen and oxygen as well as an abundance of liquid water necessary for carbon-based life to exist. Extensive plant and animal life often flourishes; often, a sentient race is also present. In contrast, consider a class Y planet:Class Y planets are referred to as "demon" worlds, where surface conditions do not fall into any other recognized category. Such worlds are usually hostile and lethal to humanoid life. If life forms develop on these worlds they usually take on many bizarre forms, like living crystal or rock, liquid or gaseous physical states, or incorporeal, dimensional, or energy-based states. Given their work providing names for various offensive security activities in ATT&CK, I wonder if MITRE might consider creating a naming scheme to capture this idea? For example, a "class M" network might be an enterprise organization with endpoints, servers, and infrastructure, of a certain size. Or perhaps M1 might be "small," M2 "medium," and M3 "large," where each is associated with a user count.Perhaps an environment with no network at all, where constituents access cloud-hosted resources, would be a class C network. (I'm not sure "network" is even the right term, if there is no "network" for which the organization is responsible.)With such a scheme in place, we could begin a cybersecurity discussion by asking, "given a class M network, what defensive processes, people, or technology are appropriate," versus "given a class C network, what defensive processes, people, or technology are appropriate."This is only an idea, and I'd be happy if something was already created to address this problem. Comments below are welcome (pending moderation to repel trolls and spammers.) Alternatively, reply to my announcement of this post via @taosecurity on Twitter.Copyright 2003-2018 Richard Bejtlich and TaoSecurity (taosecuri |
||||
| 2018-10-25 10:31:27 | Have Network, Need Network Security Monitoring (lien direct) |  I have been associated with network security monitoring my entire cybersecurity career, so I am obviously biased towards network-centric security strategies and technologies. I also work for a network security monitoring company (Corelight), but I am not writing this post in any corporate capacity.There is a tendency in many aspects of the security operations community to shy away from network-centric approaches. The rise of encryption and cloud platforms, the argument goes, makes methodologies like NSM less relevant. The natural response seems to be migration towards the endpoint, because it is still possible to deploy agents on general purpose computing devices in order to instrument and interdict on the endpoint itself.It occurred to me this morning that this tendency ignores the fact that the trend in computing is toward closed computing devices. Mobile platforms, especially those running Apple's iOS, are not friendly to introducing third party code for the purpose of "security." In fact, one could argue that iOS is one of, if not the, most security platform, thanks to this architectural decision. (Timely and regular updates, a policed applications store, and other choices are undoubtedly part of the security success of iOS, to be sure.)How is the endpoint-centric security strategy going to work when security teams are no longer able to install third party endpoint agents? The answer is -- it will not. What will security teams be left with?The answer is probably application logging, i.e., usage and activity reports from the software with which users interact. Most of this will likely be hosted in the cloud. Therefore, security teams responsible for protecting work-anywhere-but-remote-intensive users, accessing cloud-hosted assets, will have really only cloud-provided data to analyze and escalate.It's possible that the endpoint providers themselves might assume a greater security role. In other words, Apple and other manufacturers provide security information directly to users. This could be like Chase asking if I really made a purchase. This model tends to break down when one is using a potentially compromised asset to ask the user if that asset is compromised.In any case, this vision of the future ignores the fact that someone will still be providing network services. My contention is that if you are responsible for a network, you are responsible for monitoring it.It is negligent to provide network services but ignore abuse of that service.If you disagree and cite the "common carrier" exception, I would agree to a certain extent. However, one cannot easily fall back on that defense in an age where Facebook, Twitter, and other platforms are being told to police their infrastructure or face ever more government regulation.At the end of the day, using modern Internet services means, by definition, using someone's network. Whoever is providing that network will need to instrument it, if only to avoid the liability associated with misuse. Therefore, anyone operating a network would do well to continue to deploy and operate network security monitoring capabilities.We may be in a golden age of endpoint visibility, but closure of those platforms will end the endpoint's viability as a source of security logging. So long as there are networks, we will need network security monitoring.Copyright 2003-2018 Richard Bejtlich and TaoSec I have been associated with network security monitoring my entire cybersecurity career, so I am obviously biased towards network-centric security strategies and technologies. I also work for a network security monitoring company (Corelight), but I am not writing this post in any corporate capacity.There is a tendency in many aspects of the security operations community to shy away from network-centric approaches. The rise of encryption and cloud platforms, the argument goes, makes methodologies like NSM less relevant. The natural response seems to be migration towards the endpoint, because it is still possible to deploy agents on general purpose computing devices in order to instrument and interdict on the endpoint itself.It occurred to me this morning that this tendency ignores the fact that the trend in computing is toward closed computing devices. Mobile platforms, especially those running Apple's iOS, are not friendly to introducing third party code for the purpose of "security." In fact, one could argue that iOS is one of, if not the, most security platform, thanks to this architectural decision. (Timely and regular updates, a policed applications store, and other choices are undoubtedly part of the security success of iOS, to be sure.)How is the endpoint-centric security strategy going to work when security teams are no longer able to install third party endpoint agents? The answer is -- it will not. What will security teams be left with?The answer is probably application logging, i.e., usage and activity reports from the software with which users interact. Most of this will likely be hosted in the cloud. Therefore, security teams responsible for protecting work-anywhere-but-remote-intensive users, accessing cloud-hosted assets, will have really only cloud-provided data to analyze and escalate.It's possible that the endpoint providers themselves might assume a greater security role. In other words, Apple and other manufacturers provide security information directly to users. This could be like Chase asking if I really made a purchase. This model tends to break down when one is using a potentially compromised asset to ask the user if that asset is compromised.In any case, this vision of the future ignores the fact that someone will still be providing network services. My contention is that if you are responsible for a network, you are responsible for monitoring it.It is negligent to provide network services but ignore abuse of that service.If you disagree and cite the "common carrier" exception, I would agree to a certain extent. However, one cannot easily fall back on that defense in an age where Facebook, Twitter, and other platforms are being told to police their infrastructure or face ever more government regulation.At the end of the day, using modern Internet services means, by definition, using someone's network. Whoever is providing that network will need to instrument it, if only to avoid the liability associated with misuse. Therefore, anyone operating a network would do well to continue to deploy and operate network security monitoring capabilities.We may be in a golden age of endpoint visibility, but closure of those platforms will end the endpoint's viability as a source of security logging. So long as there are networks, we will need network security monitoring.Copyright 2003-2018 Richard Bejtlich and TaoSec |
To see everything:
Our RSS (filtrered)
