What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2020-02-19 13:00:00 | Understanding cyber attacker motivations to best apply controls (lien direct) | Implementing a risk based security program and appropriate controls against adaptive cyber threat actors can be a complex task for many organizations. With an understanding of the basic motivations that drive cyber-attacks organizations can better identify where their own assets may be at risk and thereby more efficiently and effectively address identified risks. This article will discuss the Rational Actor Model (RAM) as well as the seven primary intrinsic and extrinsic motivations for cyber attackers. Deterrence and security theory fundamentally rely upon the premise that people are rational actors. The RAM is based on the rational choice theory, which posits that humans are rational and will take actions that are in their own best interests. Each decision a person makes is based upon an internal value calculus that weighs the cost versus the benefits of an action. By altering the cost-to-benefit ratios of the decisions, decisions, and therefore behavior can be changed accordingly. It should be noted at this point that ‘rationality’ relies upon a personal calculus of costs and benefits. When speaking about the rational actor model or deterrence, it is critical to understand that ‘rational’ behavior is that which advances the individual’s interests and, as such, behavior may vary among people, groups and situations. For this reason, it is impossible to prevent all crime through deterrence. Some people will simply weigh the pros and cons of committing a crime and determine it is ‘worth the risk’ based upon their personal internal value calculus. While some criminologists dispute RAM in favor of other models, anecdotally it is difficult to argue with the value of the model. It is arguable that even terrorists employ a RAM model, and often select targets where there is fairly good certainty of “success”. This, again, echoes the model of risk management and a rational model of decision-making. The concept repeats in all areas of behavior, including cybercrime. Understanding RAM it is important to explore human motivation. In short there are two types of motivations that drive human behavior. Intrinsic and extrinsic motivation. Intrinsic motivations are those that are driven by internal rewards. It includes motivations that are satisfying to the individual. Eating, climbing a mountain, and watching a great movie are all examples of intrinsically motivated actions. Extrinsic motivations, by contrast, are those behaviors that result in external rewards. Working for a wage, playing the lottery and crime can all be examples of extrinsically motivated behavior. No doubt at this point readers have identified that actions can be both intrinsically and extrinsically motivated. With an understanding of the Rational Actor and Motivation theory it is now possible to discuss the motivations of cyber-attacks. It should be noted that the term ‘crime’ is not used as it is a legal term and an attack may or may not be considered a crime. As such a more generic term of ‘attack’ is used. In general, six different motivations exist for those who attempt a cyber-attack. This has been coined as the Mark Heptad (yes after this author and creator). The six seven motivations are: Financial (extrinsic) – Theft of personally identifiable information (PII), that is then monetized is a classic example of financial motivation of cyberattacks. Primarily perpetrated by organized criminal groups, this motivation represents a large percentage of cyberattacks against retailers and health care providers. | Malware Threat | |||
| 2020-02-18 13:00:00 | Why vendor management is a cornerstone of security (lien direct) | When it comes to building a security program, one of the most frequently overlooked areas is that of vendor management. Organizations focus significant resources on internal security, such as vulnerability scans, centralized log management, or user training, while not extending the same diligence towards their third-parties. Organizations end up trusting the security of their network and data to an unknown and untested third-party. As we all know, a chain is only as strong as its weakest link. If an organization cannot verify the security of its third-parties, then it has introduced the potential for risk and reduced the information assurance of their system. It is essential to realize that even if the cause of a breach is due to a third-party, it is still your company’s name and brand that is at risk. The potential cost associated with a breach can include: Fines Loss of trust Brand damage Data loss What damage can vendors do? Despite the warning above, you may still be thinking, “what damage could my vendors really do?”. The answer to that question will vary based on the access, control, and data you provide to them. For example, if your office caterer was breached the overall risk to the organization is easily contained by simply canceling whatever card you offered them. On the other hand, if you have a third-party accountant or lawyer you could be exposed to much more damage. In this example, you would be releasing highly private and potentially valuable data into unknown systems, with unknown controls and unknown users. This line of thinking can apply to any organization and any vendor, regardless of size or industry, and can help you identify where to focus your efforts. Any vendor that has access to your systems or data is inherently a risk to your company. Every threat or vulnerability you face, your vendors will also face. Are you confident they take these threats as seriously as you do? Or are they even aware of them? Regardless of how confident you may feel, I highly recommend you continue reading! The rest of this article is dedicated to providing tips and advice for building a program to assess, vet, and remediate risks related to your third parties. What can you do? Now that you understand the risks vendors pose to your organization, you need to determine what you can do to help to reduce them. There are a few steps any organization can take to develop a more robust stance on vendor management. It must be noted that to build a truly effective and mature program you must be willing to dedicate the time and resources to do it right. I have broken out the necessary steps below and have provided advice for what these steps should cover. A vendor management program should have, at a minimum, the following components: Policy – A vendor management policy should cover the purpose behind assessing vendors, staff responsibilities, communication channels, and other core components of the overarching program. Procedures – Along with the policy, your organization will need several defined procedures to implement and manage the vendor management program effectively. These procedures can include: Assessment outlines/workflows Documentation management Evidence requirements The processes you create should be relevant to the size and scope of your program and must fit your general operations. Rankings – To provide that resources are used effectively, you must come up with a ranking system to classify your vendors. While there is no ‘right’ answer to ranking vendors, a few metrics you can use to determine criticality are: Sensitivity of data they receive Volume of data they receive Importance of service they provide These can be used by themselves or combined to fo | Vulnerability Threat | ★★★★ | ||
| 2020-02-13 13:00:00 | InfoSec needs a reputation overhaul (lien direct) |
An independent guest blogger wrote this blog.
I was in a medical office the other day, and when the doctor came into the room, he needed to unlock his phone to contact a pharmacy. I couldn’t help but notice that his home screen had a photo of an infant. It was an adorable infant, and I asked “how old is your child?” The doctor reflexively answered, “10 months”, but then became a bit shocked, and asked me ‘how do you know I have a child?"
I confessed that I saw it on his home screen on his phone. I told him that I worked in cybersecurity, to which he responded, “oh, you guys steal everything”. Ouch! Now, the shock was shifted to me. A bit embarrassed, I apologized for being such a snoop, but it certainly made me think: are all of us InfoSec folks like this?
Reflect for a moment on your actions when you enter a room and see computer screens. Do you instinctively try to see what is on the screen? Does something as trivial as an operating system logo make you mentally churn through all the exploitable vulnerabilities? Do your eyes light up when you notice that your local pizza place is still using Windows XP for their ordering terminals?
We have a problem in our community. Our reputation is tarnished. We are not viewed as people who can help, like doctors, nurses, and other first responders. Instead, we are seen as the digital thieves and snoops. We need a reputation overhaul.
Is this because our particular profession is so young, that we feel officiously compelled to point out every vulnerable system, every exploitable action, and every weak security practice? Is this our way of increasing awareness about the perils of the digital world? It is not serving us well. I have pointed out in a previous post that we need to better engage with our clients, as well as how we lack inherited credibility. Yes, soft skills indeed, but look at what we have created by behaving in our current state; “you guys steal everything”.
What is our remedy for this problem? I propose that we InfoSec folks start to think more like the first responders. There is nothing wrong with reserving the ability to act when necessary, but perhaps we need not point out everything we see when we are not being asked to do so. How would you feel if you were cautioned by a nurse every time you ordered something “unhealthy” in a restaurant? Not the most pleasant dining experience. That nurse may be there to rescue you if you start choking, but will not make unsolicited comments about your food preferences prior to that.
My wife is a psychotherapist, and when we attend social events, people often say to her “Oh, I suppose that you are analyzing me”. She has come up with a very funny, but true response; “You ain’t paying me, I ain’t analyzing you”. Perhaps it is time for InfoSec professionals to take the same approach.
|
||||
| 2020-02-11 14:00:00 | New PayPal phishing scam seeks to go beyond login credential information (lien direct) |
 Photo by Kon Karampelas on Unsplash
An independent guest blogger wrote this blog.
Up until now, some of PayPal users’ greatest fears in terms of cybersecurity were phishing scams aimed at obtaining their login credentials. In January of this year, PayPal confirmed a high-severity bug affecting the login form, with PayPal security investigator, Alex Birsan, finding a javascript file with what looked like a CSRF token and a session ID – which makes login information vulnerable to attackers. However, another scam is set to take this vulnerability further, by aiming not only to elicit login details, but also personal information and payment card/bank account details.
Going a step further
The new scam, discovered by researchers at ESET, sends PayPal users an email stating that their account has experienced ‘unusual activity.’ The email then requests that the users take specific steps to protect their security. Once users click onto the page, they are directed to a phishing page on which they are asked to provide various details and verify their account by providing data such as their home address and banking details. Once they have provided the requested data, they are informed that their account is now secure/restored.
Signs of scamming
The scam highlights the importance of knowing basic cybersecurity protocol. This includes being immediately suspicious of any email that leads users to a different URL, and wary of any changes – including misspelled words and odd-looking padlocks. One trend that was prevalent this year involved the use of a fake security certificate and a green padlock. Users should be aware of this and other new tricks by staying up-to-date on new cybersecurity risks, and by being vigilant of suspicious requests for information, addresses, links, and changes in page appearance.
A new PayPal threat from 16Shop phishing gang
If you are aware of current phishing threats, then the name 16Shop Phishing Gang will not be new to you. This gang, whose operators are believed to be located in Southeast Asia, is specifically targeting PayPal, according to researchers at the Zero FOX Alpha Team. The group distributes a phishing kit which aims to obtain as much information as possible from PayPal users. The kit works by sending a POST request to a C2 server, with a password, domain and path. The information illicitly taken is then sent via SMTP to the inbox of the controller. The information can then be used to build phishing pages in a number of different languages – including English and Spanish.
Astounding discoveries
The researchers managed to view traffic between the phishing kit and the command and control server. They found that the system was so easy to negotiate that even amateurs could use it without a hitch. They added that the kit was slick and sophisticated, with features
Photo by Kon Karampelas on Unsplash
An independent guest blogger wrote this blog.
Up until now, some of PayPal users’ greatest fears in terms of cybersecurity were phishing scams aimed at obtaining their login credentials. In January of this year, PayPal confirmed a high-severity bug affecting the login form, with PayPal security investigator, Alex Birsan, finding a javascript file with what looked like a CSRF token and a session ID – which makes login information vulnerable to attackers. However, another scam is set to take this vulnerability further, by aiming not only to elicit login details, but also personal information and payment card/bank account details.
Going a step further
The new scam, discovered by researchers at ESET, sends PayPal users an email stating that their account has experienced ‘unusual activity.’ The email then requests that the users take specific steps to protect their security. Once users click onto the page, they are directed to a phishing page on which they are asked to provide various details and verify their account by providing data such as their home address and banking details. Once they have provided the requested data, they are informed that their account is now secure/restored.
Signs of scamming
The scam highlights the importance of knowing basic cybersecurity protocol. This includes being immediately suspicious of any email that leads users to a different URL, and wary of any changes – including misspelled words and odd-looking padlocks. One trend that was prevalent this year involved the use of a fake security certificate and a green padlock. Users should be aware of this and other new tricks by staying up-to-date on new cybersecurity risks, and by being vigilant of suspicious requests for information, addresses, links, and changes in page appearance.
A new PayPal threat from 16Shop phishing gang
If you are aware of current phishing threats, then the name 16Shop Phishing Gang will not be new to you. This gang, whose operators are believed to be located in Southeast Asia, is specifically targeting PayPal, according to researchers at the Zero FOX Alpha Team. The group distributes a phishing kit which aims to obtain as much information as possible from PayPal users. The kit works by sending a POST request to a C2 server, with a password, domain and path. The information illicitly taken is then sent via SMTP to the inbox of the controller. The information can then be used to build phishing pages in a number of different languages – including English and Spanish.
Astounding discoveries
The researchers managed to view traffic between the phishing kit and the command and control server. They found that the system was so easy to negotiate that even amateurs could use it without a hitch. They added that the kit was slick and sophisticated, with features |
Vulnerability Threat Guideline | |||
| 2020-02-06 14:00:00 | Building comprehensive cybersecurity policies (lien direct) |
 Image Source: Photo by freestocks.org on Unsplash
When you think of cybersecurity, what’s the first thing to come to mind? Most of the time, it might be your business’s IT team, who run around worrying about updates, threats, and computing capacity. The reality is that cybersecurity isn’t just the IT department’s concern — it’s everyone’s.
Research suggests that cybercriminals will steal 33 billion records in the year 2023, and half of all global data breaches will occur in the U.S. If you want a hope of a stopping them from stealing from your business, then you need all hands on deck — from both your administrative team to the sales team to the C-suite.
Why is building a comprehensive cybersecurity policy with features that cover everyone and their devices so important? Because everyone (and their devices) can be a threat. Here’s what you need to know about strengthening your cybersecurity as we head into the new decade.
Why ‘comprehensive’ includes everyone at work
Comprehensive cybersecurity practices usually include items like:
Threat risk analysis
System vulnerability analysis
Impact assessments
Security environment analysis
But, to be totally effective, these need to consider not only the high-value and high-risk processes and procedures but everything in between. Why? Because while it’s true that your security is only as good as your software, you also need to limit the extent to which you expose those systems to threats.
In today’s hyper-connected world, there are millions of opportunities to bare your security infrastructure to the world. Two of the biggest threats actually come down to your employees. First, they now complete the vast majority of their work online, which means both internet security and access are critical to your core processes. As more and more of your work happens in the cloud, you simultaneously create more vulnerabilities.
Second, your employees also carry more internet-connected devices than ever — and they probably access company data on them. The cybersecurity threats created by the Internet of Things (IoT) are stunning: one survey found that 54% of consumers own at least four IoT devices, but only 14% say they know how to secure them.
This is a huge problem because only 31% of employees receive annual cybersecurity training.
Consider the Threat of Internal Sources
To be clear: hackers are a problem. The prevalence of malware, phishing, ransomware, and DDoS attacks has grown year-on-year, and your business could be the next target. What you might not realize, however, is that the biggest threat to your business could already be in
Image Source: Photo by freestocks.org on Unsplash
When you think of cybersecurity, what’s the first thing to come to mind? Most of the time, it might be your business’s IT team, who run around worrying about updates, threats, and computing capacity. The reality is that cybersecurity isn’t just the IT department’s concern — it’s everyone’s.
Research suggests that cybercriminals will steal 33 billion records in the year 2023, and half of all global data breaches will occur in the U.S. If you want a hope of a stopping them from stealing from your business, then you need all hands on deck — from both your administrative team to the sales team to the C-suite.
Why is building a comprehensive cybersecurity policy with features that cover everyone and their devices so important? Because everyone (and their devices) can be a threat. Here’s what you need to know about strengthening your cybersecurity as we head into the new decade.
Why ‘comprehensive’ includes everyone at work
Comprehensive cybersecurity practices usually include items like:
Threat risk analysis
System vulnerability analysis
Impact assessments
Security environment analysis
But, to be totally effective, these need to consider not only the high-value and high-risk processes and procedures but everything in between. Why? Because while it’s true that your security is only as good as your software, you also need to limit the extent to which you expose those systems to threats.
In today’s hyper-connected world, there are millions of opportunities to bare your security infrastructure to the world. Two of the biggest threats actually come down to your employees. First, they now complete the vast majority of their work online, which means both internet security and access are critical to your core processes. As more and more of your work happens in the cloud, you simultaneously create more vulnerabilities.
Second, your employees also carry more internet-connected devices than ever — and they probably access company data on them. The cybersecurity threats created by the Internet of Things (IoT) are stunning: one survey found that 54% of consumers own at least four IoT devices, but only 14% say they know how to secure them.
This is a huge problem because only 31% of employees receive annual cybersecurity training.
Consider the Threat of Internal Sources
To be clear: hackers are a problem. The prevalence of malware, phishing, ransomware, and DDoS attacks has grown year-on-year, and your business could be the next target. What you might not realize, however, is that the biggest threat to your business could already be in |
Vulnerability Threat | |||
| 2020-02-05 14:00:00 | 10 things to know about cybersecurity in 2020 (lien direct) | Cybersecurity talent is elusive, resources are dwindling, but hacks are on the rise. We’re addressing these challenges as “must-haves” as we kick off the year is essential to an organization’s cybersecurity strategy. Here are some of the 10 things to know about cybersecurity in 2020. (If you’re interested in hearing more, register for a Cygilant and AT&T Cybersecurity webinar on the topic February 6). 1. Security-as-a-service fills the talent and recruitment gap. We are already falling into a talent abyss where there isn’t enough cybersecurity or compliance expertise and it’s not changing anytime soon. Getting help from security-as-a-service organizations will become the de-facto standard as the only way to fill the talent and recruitment gap. 2. Navigating vendor noise becomes harder. With so many cybersecurity vendors in the market, it’s tough to make decisions on what will truly help protect a business. This year there needs to be a focused priority in identifying services that provide resources and a full suite of solutions to help turn down the volume, ward off attacks and meet compliance mandates. 3. AI identifies security gaps faster. As we fight to keep up with new hacks, security professionals need to embrace machine learning (ML) and AI technology that works at a much faster cadence to find gaps that could lead to a breach. Using these technologies can help security professionals keep up with hackers. Combined with human expertise, AI and ML can help prevent attacks. 4. Widespread adoption of security visualization in the cloud. We want to see how our apps and data are connecting and where, and if, there are any security gaps. A “must-have” for all security professionals is the ability to see their entire security posture presented in a single, holistic visual dashboard. We will see the widespread adoption of security visualization across all environments. 5. The perimeter is dead; endpoints need protecting. More laptops, desktops, mobile phones, tablets, servers, and virtual environments are connecting to systems. Each one of these endpoints requires security. In 2020, endpoint security will become a “must-have” for all organizations. Perimeter detection is no longer adequate - as your perimeter doesn’t exist. It is anywhere and everywhere. One misconfigured laptop, server or firewall may be the cause of a data breach. 6. More regulations translates to more work. Every year we see an increase in updated guidance or compliance requirements. This trend will continue in 2020 as more regulation is put in place to protect privacy and data. With the floodgates opening, it’s important to have processes and logs in place that prove how security and privacy is handled at your business. 7. More ransomware attacks in 2020. As more people accept that spending on ransomware is the cost of doing business, we’ll see more attacks. Dedicated resources should be spent on prevention by monitoring for suspicious activity, including phishing attempts and ransomware. If you don’t have the internal resources, look to security-as-a-service with security monitoring solutions. 8. Small business aren’t immune. Cybersecurity isn’t just for the enterprises. One breach could be the death of a s | Ransomware Tool Guideline | |||
| 2020-02-03 14:00:00 | NO FATE (lien direct) | “The future is not set, there is no fate but what we make for ourselves.” John Connor, Terminator 2 There is a prevailing viewpoint among security professionals that security breaches are inevitable. They have adopted the mantra, “It is not a matter of if but a matter of when.” As recently as the day I wrote this post, I attended a meeting where this attitude was used to justify accepting easy to mitigate security risks. This attitude is nothing new and it has a name: “fatalism.” Merriam Webster defines fatalism as, “a doctrine that events are fixed in advance so that human beings are powerless to change them.” Ask yourself as you read this, is that the truth? Are you powerless to change events or do you make your own choices? When you make the choice to choose compliance over security, that’s not fatalism but a mixture of choice and will. It’s a decision to be good enough to escape liability without being good enough to escape fate. It’s a trap! Many of the big credit card breaches of the past decade occurred while an organization was PCI compliant. Target was certified PCI compliant weeks before it was hacked in 2013. Verizon has breach data that supports the fact that although companies become compliant they often do so in a way that is unsustainable. Do not take away the wrong lesson. The lesson here is not if Target couldn’t fight the hackers then I can’t either. The lesson is that the culmination of their decisions resulted in an environment that made it possible. You make choices every day that impact your personal and professional destiny. I promise you security is not an expensive goal attainable only by the super-rich. It is far more about the knowledge, dedication, ingenuity, and heart you put into it. As a blog post, I have to keep this short so please forgive me for not addressing every area of focus you need to cover to commit to security. There are four phases to the model I recommend for IT security: identify your environment, categorize your risks, know your enemy, and test your solutions. This model is a cycle designed to repeat itself again and again without end. Each cycle informs upon the information gathered in the last and grows more mature with each revision. Identify your environment Phase one sounds simple. It’s the same advice given by sages, oracles, and war philosophers for thousands of years, know thyself. It is the foundation upon which all else is built. What systems are on the network? What systems are in your inventory? Where is your sensitive data? What is your sensitive data? What is the normal traffic of your network? What is the normal operating usage of your systems? This is a collection of facts, without judgment, about the environment. A single missing piece here may cause your entire security structure to crumble. For example, I did a penetration test for a bank several years ago. They had a secure system for their account data. However, one of their account representatives wanted to do something nice for their clients by recognizing their birthdays. They took the information from the secure database, including the account numbers and safety deposit box information and put it in a spreadsheet. I found that spreadsheet with an unprivileged account sitting on their internal SharePoint platform. They did not know where their data was, and had I not found it they would not have known to address it. Categorize your risks Phase two is about putting those pieces together to figure out what it all means. What do you get when you assess the systems on your network with the systems in your inventory? Rogue device detection and loss prevention. What does it mean that I found account data in SharePoint which itsel | Threat | |||
| 2020-01-31 14:00:00 | A new twist on “Parental consent” (lien direct) |
An independent guest blogger wrote this blog.
I was at breakfast the other day with some family friends, and the topic of genealogy came up. Over the past few years, various sites have sprouted up that offer to trace your origins all the way back in time; in some cases, all the way back to the eras of early human development. One of my favorite authors has actually written a book about the results of his test.
The idea behind the test is simple. You order a “kit” online, and when the kit arrives, all you have to do is dribble into a test tube, seal it up with your information, and send it on its way and await the results.
While I was at breakfast with my friends, they were discussing how they were going to send away for their kit to trace their origins. To their knowledge, they were 100% certain of their purely Greek heritage, with no deviations from the bloodlines. It would be fascinating to see if they are distant relatives of some of the great thinkers in human history. This is remarkable, as I cannot boast of such “purity” due to my mutt-like family history.
All was not well with their plan, however. Their son objected to the idea of them participating in what he considered pure folly. He was not so concerned about his past; he was more concerned with his future. He has serious apprehension about the privacy surrounding these tests, as well as the future implications for his life.
I thought about his concern, and he has a valid point. A review of the privacy policy of one of the most popular genealogy sites does nothing to relieve this fear. While they clearly state that they will never share information with an insurance company or medical office, they are, however, legally required to share information if requested by a legitimate law enforcement organization. There is also a warning that “in the event of a breach”, the information may become public knowledge.
Perhaps my young friend has a point? We have seen in the past how data can escape even the most secure organizations. It is one thing to lose control of our financial information, such as our social security numbers. However, what is the remedy if our genetic information becomes public? In this age where we are creating new identification and authentication methods, have we contemplated the future risks of such an event?
The interesting twist here is that we always caution our children to seek parental consent for something as simple as a school trip, or a movie with questionable content. We have childproof caps on all medications, and we worry about our children’s use of social media.
What should we call this new world, where we should seek the consent of our offspring before we responsible adults do something that may affect them in an unknown future? There isn’t even a word in the lexicon for this new phenomenon. Since they are the fruit of our loins, perhaps we can call it “Loinal consent”? Some things may be best if they remain non-public.
|
Heritage | |||
| 2020-01-28 14:00:00 | Do you need certifications to get an InfoSec job? (lien direct) | I’ve seen Tweets and heard many discussions about certifications, like CISSP, CEH, OSCP and so on, in InfoSec. No doubt certifications have value – in many situations hiring managers are quickly going through resumes and certifications are symbolic of at least book-learning, and some degree of dedication to InfoSec. Certifications can be expensive and time consuming so having them clears the bar of at least slightly dedicated. While certifications are arguably a “good thing” inferring a recognized value understood in the InfoSec community, do people really need them to land jobs? After all, job seekers are existentially in need of employment and not likely to want to spend time and money on certifications if they are not necessary. We have published previous blogs on certifications in InfoSec. But I was still curious as to whether certifications are required to get a job in InfoSec. So I decided to do a Twitter poll on my personal Twitter account to gather more data to help write this blog. Is it fair to ask new folks in InfoSec to have to have expensive certifications to be worthy of consideration, given you're a hiring manager? Tagging in @MalwareJake for insights. — Kate Brew (@securitybrew) October 14, 2019 It appears from my Twitter poll, that certifications aren’t an absolute requirement to gain employment in InfoSec, but having them might help candidates get through HR pre-screening. Certificates were viewed as a sort of filter by a few folks. Certs are not a requirement at all. However, without them you're less likely to make it through HR screening at larger shops. You're less impacted at smaller shops because there are fewer steps between resume submission and the hiring authority. 1/2 — Jake Williams (@MalwareJake) October 14, 2019 Given two equally qualified candidates, the one with certifications might have the edge: That said, if I have two equally qualified candidates and one has a cert, I'll take them because some clients ask/care. But there are things more important to me than certs: Conference talks GitHub (more than just college assignments) A blog Thoughtful social media feed 2/2 — Jake Williams (@MalwareJake) October 14, 2019 Several folks were sensitive to the cost of attaining some certifications reaching greater than $1000. They suggested more affordable options. Some certifications are affordable on e | Malware | |||
| 2020-01-27 14:00:00 | How Smart Cards Work (lien direct) | An independent guest blogger wrote this blog. In this modern age, there’s been a significant improvement in the digitization of traditional payment methods. We live in a technologically advanced era, and as such, advancements in payment infrastructures makes life easier, transactions faster, swifter, and smoother. Almost all countries in the world are adopting the cashless economy policy. Smart cards are generally utilized by these countries to implement the cashless economy because they aid the seamless transaction of trade and settlement of other financial instruments. What is a smart card? A smart card is a type of pocket-sized device which looks like a credit card but has an embedded Integrated Circuit (IC) that can process data and allow the user to perform any transaction. The IC chip on the Smart card can be a microprocessor with memory capacity or a simple memory circuit that processes, manipulates exchange, and stores data. Smart cards usually have up to 346 kilobytes of ROM, 8 kilobytes of RAM, a 16-bit microprocessor, and 256 kilobytes of programmable ROM. They are mainly plastic, and the microprocessor cards consist of volatile memory and microprocessor components. How does the smart card work? A smart card reader connected to a host computer, cloud computer, or any controlling terminal collects the information stored on the microprocessor chip of the smart card. Then, it sends such information received from the smart card back to the controlling terminal for immediate processing. The smart card connects to the smart card reader using a unique Radio Frequency ID (RFID) or through a Carrier Sensing Collision Detection (CSCD) system protocol. RFID tags find use in a wide range of applications such as - tracking goods through the supply chain, tracking assets, controlling access into buildings, among other similar applications. The CSCD protocols sense the carrier frequency of the smart card to match its speed. Two-way communication is used when collisions are detected, and the retransmission is based on a priority of detection. Smart cards cannot provide locations using GPS services. This is because the smart card does not have a power source to support continuous operations. Tracking happens by conducting audit trails to pinpoint where an individual used their card. The smart card chip comes in contact with the card reader either directly or indirectly and establishes an electronic interface. This then enables transactions such as payments via Point of Sale to take place. However, some smart cards do not need to come in contact with the reader. They connect using a wireless medium. These types of smart cards are called contactless cards, while those that need contact are known as contact smart cards. Contactless smart cards are increasing in demand due to their ease of use and flexibility. What are the uses of smart cards? Secured storage - Smart card technology provides a secured means of storing data. Users' data is stored securely on the card and not on a central database, and is only accessible with the user giving full consent. E-Commerce - Instead of filling out long forms, smart cards are useful for storing user shopping data and credit card details which are all accessible with a mouse click. Personal finance - Users can use a smart card to conduct business transactions throughout the globe without hassle. Encryption - Smart card technology provides a broad set of encryption capabilities which includes secure key storage, hashing and digital signing. Types of smart cards We can classify the smart cards based on: Their Connection to the Smart card reader Their configuration Types of smart cards base | ||||
| 2020-01-23 14:00:00 | Healthcare security: How can blockchain help? (lien direct) |
 This is part 2 of a blog on healthcare security. For more info, check out part 1. An independent guest blogger wrote this blog.
When it comes to data security, there is no more important place than the healthcare industry. When people go to the doctor, they provide all of their most sensitive information, from their health issues to their phone number, to a doctor they trust. When a medical office or database is hacked or damaged, and that information is released, it can be catastrophic to everyone involved.
Patient security is not only good practice, but it is also the law. Guidelines are in place to protect patient data, and it is up to health professionals and administrators to ensure that proper protections are made. Here are some best practices for now and advanced security platforms to look forward to in the future.
The rise of blockchain technology
While the possibility of losing business and patient data through a system breakdown or employee error is a serious concern, the potential for cybercrime is perhaps the bigger threat. As technology advances, so do the methods that hackers use to infiltrate our systems. The result is a combination of threats from computer viruses to phishing attacks, which trick employees into clicking a link or attachment that opens a door into their computer’s infrastructure. From there, a hacker can sell the personal info that they obtain on the black market or use it to extort money from the unsuspecting patient.
Since criminals have the ability to hack into health systems, an extra layer of security is needed: enter the blockchain. Instead of having patient information listed on an excel spreadsheet or an unsecured platform, this type of technology has information that is encrypted and entered into a chain that cannot be changed, deleted, or tampered with. All new information is verified against a ledger of previous events and cannot be modified unless it is deemed accurate.
In addition to creating better security, blockchain also creates additional transparency for those receiving care. Since a patient would be one of the owners of the blockchain, they are able to monitor when new data is added or changed within their records and have a say in the decision. Blockchain also prevents the leakage of data when emailing or shipping patient records to a new provider, as the new office would need only an access key to view and add their own content.
While this is a relatively new technology, it could prove to be a necessary one in the future.
Safeguarding medical data
Regardless of how data can be lost, it is essential that your medical office is proactive instead of reactive when it comes to a potential breakdown. The first step should always be to create an extensive risk analysis that not only assumes potential risks but also lists a plan of action if the unthinkable were to occur
This is part 2 of a blog on healthcare security. For more info, check out part 1. An independent guest blogger wrote this blog.
When it comes to data security, there is no more important place than the healthcare industry. When people go to the doctor, they provide all of their most sensitive information, from their health issues to their phone number, to a doctor they trust. When a medical office or database is hacked or damaged, and that information is released, it can be catastrophic to everyone involved.
Patient security is not only good practice, but it is also the law. Guidelines are in place to protect patient data, and it is up to health professionals and administrators to ensure that proper protections are made. Here are some best practices for now and advanced security platforms to look forward to in the future.
The rise of blockchain technology
While the possibility of losing business and patient data through a system breakdown or employee error is a serious concern, the potential for cybercrime is perhaps the bigger threat. As technology advances, so do the methods that hackers use to infiltrate our systems. The result is a combination of threats from computer viruses to phishing attacks, which trick employees into clicking a link or attachment that opens a door into their computer’s infrastructure. From there, a hacker can sell the personal info that they obtain on the black market or use it to extort money from the unsuspecting patient.
Since criminals have the ability to hack into health systems, an extra layer of security is needed: enter the blockchain. Instead of having patient information listed on an excel spreadsheet or an unsecured platform, this type of technology has information that is encrypted and entered into a chain that cannot be changed, deleted, or tampered with. All new information is verified against a ledger of previous events and cannot be modified unless it is deemed accurate.
In addition to creating better security, blockchain also creates additional transparency for those receiving care. Since a patient would be one of the owners of the blockchain, they are able to monitor when new data is added or changed within their records and have a say in the decision. Blockchain also prevents the leakage of data when emailing or shipping patient records to a new provider, as the new office would need only an access key to view and add their own content.
While this is a relatively new technology, it could prove to be a necessary one in the future.
Safeguarding medical data
Regardless of how data can be lost, it is essential that your medical office is proactive instead of reactive when it comes to a potential breakdown. The first step should always be to create an extensive risk analysis that not only assumes potential risks but also lists a plan of action if the unthinkable were to occur |
Hack | |||
| 2020-01-22 14:00:00 | It is getting harder for us to prove who we are (lien direct) |
I had an interesting experience the other day. I had to renew my driver’s license.
In previous renewal cycles, this was no big deal. One could just visit the local Department of Motor Vehicles (with a bagged lunch since it was usually a multi-hour wait), read an eye chart, take a horribly unflattering photo, and be on their way with a new license. Now, however there is a new driver’s license being issued in the USA that is required if you want to fly on a domestic flight, and you do not have a valid passport. (In defense of the nation’s motor vehicle offices, it should be mentioned that the license procedure has been streamlined, and the process now takes less than 20 minutes.)
This is an improvement in the identification verification process, as many people do not have a passport, but they do have a driver’s license. The problem I encountered is my ability to prove that I am who I say I am. This was due to the documentation requirements. One of those requirements is possession of a valid passport. However, as stated in the previous paragraph, this new license is supposed to be valid in absence of a passport. I found out that the new license will also be required to enter any Federal Buildings. This made much more sense, as one is often carrying a driver’s license, but it is rare to carry a passport unless you are going to an airport.
The other required proofs of identity include: An original Social Security card, or a tax document that contains your full social security number, and a proof of residence, such as a bank statement.
From a physical security perspective, the idea of carrying all of these documents to the motor vehicle office at the same time is horrifying. These documents represent every form of proof that you are who you say you are. I can think of no other time that I have ever traveled with so many original documents.
There is another security concern that came to mind as I was in the document gathering phase. That is, it is getting more difficult to prove where I live. Most of my utility payments, and financial transactions, are conducted online. In many cases, I have been forced to “Go Paperless”. This means that I do not have a printed document to satisfy the “proof of residency” requirement.
As we proceed more towards a fully online, paperless society, I wonder how we will be able to prove various aspects of our identities? I am not opposed to this new approach, as we need to act to stop the destruction of our environment.
In a previous post, I posited the idea of using a blockchain method for identification. While it seemed a bit crazy, it was certainly less intrusive than an implanted biochip. With the movement of all of our lives to a fully online model, perhaps that identification method is not so crazy after all.
|
||||
| 2020-01-21 14:00:00 | FUD-free analysis: Natural language processing (NLP) (lien direct) | If you follow me on Medium or Twitter, you may already be aware. Still, if you don’t (I assure you that you’re missing out), I have been researching several technologies in preparation for an OPSEC/Anti-OSINT tool that I am crafting. I am using this tool as a means to push myself harder to learn something new that I can apply professionally. I am also doing this to be able to make a positive difference in the world. Notably, I am explicitly trying to learn Machine Learning and Natural Language Processing (NLP) in Python and R. When we hear terms like Advanced Persistent, Next-Generation, Machine Learning, Artificial Intelligence (AI), Machine Learning (ML), Single Pane of Glass, etc. from a vendor, we typically think it’s hype or FUD. Talking about the vendor FUD phrases is ironic because my blog and podcast were called Advanced Persistent Security. Often, we are correct. I set off on the journey to learn about learning to build a tool, but also to understand the technologies. I like to stump salespeople from time to time. Also, if these are the wave of the future, there is no time like the present to get acquainted. So, NLP. What is it? In social engineering circles, it is Neuro-Linguistic Programming. Some (many, if not most) in the scientific community consider it pseudoscience. Regardless, it claims to be able to influence or manipulate people through non-verbal cues from the eyes or touching someone (cringe) or other means. That is not the NLP that I am working on learning. Natural Language Processing, the more scientific NLP, is a marriage of various disciplines: computer science, data science (including AI and ML), and linguistics. NLP allows libraries and code to read the language as it is written or spoken by humans (naturally, hence the name). When applying slang, pidgins, and dialects, it will “learn” to recognize and respond to them. Also adjacent to NLP is OCR or Optical Character Recognition. OCR is the means to read data from a document in a non-text format (i.e., pictures, PDF, or Word documents). Having the ability to read the data allows you to open a PDF with a script (perhaps written in Python) and read it, make sense of it, and act as scripted. Why is this important to InfoSec, and what do we do with it? We could use this in log analysis, network monitoring, analyzing phishing emails, and my personal favorite, OSINT, to name a few. Within log analysis, NLP could be applied to gain further intelligence from logs without writing ridiculously long regular expressions (REGEX) via “learning” the context of the data and what is being sought. This would likely be in parallel with some Machine Learning, but it is a start. From the ML perspective, it would probably need to utilize supervised or semi-supervised learning with online entry vice unsupervised or reinforcement learning. The online means that it would read the data more closely to real-time than by ingesting a defined dataset. The supervision of learning refers to telling the “machine” whether it was correct or not. In some instances of learning logs, unsupervised learning could be useful in determining indicators of compromise or adversarial TTPs based on log data in two sets: breached (event data) and non-breached data. Reinforcement training would be more applicable for tuning and improvement. Back to NLP, the same concepts apply in network monitoring as log analysis, except it would be network traffic and PCAPs being analyzed. PCAP analysis with NLP and ML may be better suited for analyzing a user’s beha | Tool Threat | |||
| 2020-01-17 14:00:00 | Journey to security: Data safety for travelers (lien direct) |
 Image source: Pixabay
Note:This blog was written by an independent guest blogger.
In today’s world, we enjoy incredible mobility that our ancestors could only dream of. In a matter of hours or, at most, days, we can go from one continent to another.
At the same time, our lives depend on the security of all sorts of our private data: from our credit card information to our browsing habits. But if at our homes we can be sure that we have taken sufficient security measures and protected our systems, things get muddier when we travel.
There is no way to tell if cybersecurity employed by an airport or hotel you use is enough to protect your sensitive data. However, there are ways to increase your safety by following several simple tips.
1. Don’t trust public USB charging stations
While their convenience is hard to overestimate when your battery charge is running low, public USB charging stations should not be treated as safe.
The threat when the data on your device is stolen or infected through a USB cord when you connect the device to a charging station is called juice jacking. It may not be the most widespread type of malware injection but it is better to avoid any possibility of it nevertheless.
This threat can be mitigated by getting a USB data blocker that allows charging your device while blocking any data transfer to or from it. Alternatively, just charge your device at a socket.
2. Mind your physical security
It’s not every time when personal information gets stolen that some complex hacking techniques are involved. Quite often, stealing access to sensitive data only requires a more traditional set of criminal skills.
If you travel to a highly-populated city and especially if you use public transportation there, your chances of running into pickpocketers are going to be very high. Therefore, it’s a good idea to take some preemptive measures to battle this possibility.
If your device is small (like a smartphone), try to keep it in an inside pocket, if possible. This way, you will make it almost unreachable to any thief.
On the other hand, if your device is bigger (like a laptop) and you carry it around in a bag, be sure not to put the bag down in any circumstances. Hold it tightly so that no criminal can snatch it from your hands.
3. Be prepared in case your device is stolen
Sadly, no matter what precautions you take, there’s still a possibility that your device may be stolen. It only takes a criminal one lucky attempt to do so while you have to succeed in protecting yourself constantly.
This is why you need to have a plan B.
Set up a screen locker for your smartphone. Ideally, it should be done with a password because those are the hardest to crack but it comes at a price of having to enter it every time you need to access your smartphone. However, in the unfortunate event if your device does get stolen, the perpetrators won’t be able to access it and your personal information.
Another option is setting up a biometric authentication procedure to unlock your phone. In most cases, using your fingerprint is the most convenient route to take.
Similarly, your other devices should also be
Image source: Pixabay
Note:This blog was written by an independent guest blogger.
In today’s world, we enjoy incredible mobility that our ancestors could only dream of. In a matter of hours or, at most, days, we can go from one continent to another.
At the same time, our lives depend on the security of all sorts of our private data: from our credit card information to our browsing habits. But if at our homes we can be sure that we have taken sufficient security measures and protected our systems, things get muddier when we travel.
There is no way to tell if cybersecurity employed by an airport or hotel you use is enough to protect your sensitive data. However, there are ways to increase your safety by following several simple tips.
1. Don’t trust public USB charging stations
While their convenience is hard to overestimate when your battery charge is running low, public USB charging stations should not be treated as safe.
The threat when the data on your device is stolen or infected through a USB cord when you connect the device to a charging station is called juice jacking. It may not be the most widespread type of malware injection but it is better to avoid any possibility of it nevertheless.
This threat can be mitigated by getting a USB data blocker that allows charging your device while blocking any data transfer to or from it. Alternatively, just charge your device at a socket.
2. Mind your physical security
It’s not every time when personal information gets stolen that some complex hacking techniques are involved. Quite often, stealing access to sensitive data only requires a more traditional set of criminal skills.
If you travel to a highly-populated city and especially if you use public transportation there, your chances of running into pickpocketers are going to be very high. Therefore, it’s a good idea to take some preemptive measures to battle this possibility.
If your device is small (like a smartphone), try to keep it in an inside pocket, if possible. This way, you will make it almost unreachable to any thief.
On the other hand, if your device is bigger (like a laptop) and you carry it around in a bag, be sure not to put the bag down in any circumstances. Hold it tightly so that no criminal can snatch it from your hands.
3. Be prepared in case your device is stolen
Sadly, no matter what precautions you take, there’s still a possibility that your device may be stolen. It only takes a criminal one lucky attempt to do so while you have to succeed in protecting yourself constantly.
This is why you need to have a plan B.
Set up a screen locker for your smartphone. Ideally, it should be done with a password because those are the hardest to crack but it comes at a price of having to enter it every time you need to access your smartphone. However, in the unfortunate event if your device does get stolen, the perpetrators won’t be able to access it and your personal information.
Another option is setting up a biometric authentication procedure to unlock your phone. In most cases, using your fingerprint is the most convenient route to take.
Similarly, your other devices should also be |
Malware Threat Patching Guideline | |||
| 2020-01-15 14:00:00 | Alien Labs 2019 Analysis of Threat Groups Molerats and APT-C-37 (lien direct) |
In 2019, several industry analyst reports confused the threat groups Molerats and APT-C-37 due to their similarity, and this has led to some confusion and inaccuracy of attribution.
For example, both groups target the Middle East and North Africa region (with a special emphasis on Palestine territories). And, they both approach victims through the use of phishing emails that contain decoy documents (mostly in Arabic) and contain themes concerning the political situation in the area.
To improve understanding of the differences and similarities of the two groups (as well as the links between them), we at Alien Labs™ are providing an analysis of their 2019 activity.
 A recent spear-phishing document from Molerats
APT-C-37 Overview
APT-C-37, also known as Pat-Bear or the Syrian Electronic Army (SEA), was first seen in October 2015 targeting members of a terrorist organization. Since 2015, however, APT-C-37 has broadened their objectives to include government agencies, armed forces leadership, media organizations, political activists, and diplomats. The group mostly targets victims in Western countries, with the intent of defacing their websites and social accounts while leaving a public footprint after hacking one of their victims.
In previous attacks, APT-C-37 targeted Windows and Android systems, utilizing popular commercial remote access trojans (RATs) such as DroidJack, SpyNote, njRAT, SSLove, and H-Worm.
Technical Analysis: APT-C-37 2019
June 2019: APT-C-37 released an Android app named after the instant messaging software “WhatsApp” as an espionage tool to reportedly spy on the Syrian opposition forces. The app was capable of installing the SSLove RAT to pull private information from the phone and exfiltrating it to a remote location.
Molerats Overview
Molerats has been present in the cybercriminal landscape since 2012. In an analysis released by the Kaspersky’s GReAT (Global Research & Analysis Team) earlier this year on the Gaza Hacker Team and their various subgroups, Kaspersky concluded that Molerats is Gaza Cybergang “Group1.” The report also concluded that Molerats (i.e. Cybergang Group 1) operates with a lower level of sophistication than other groups within the Gaza Hacker Team. In addition, a 2016 article in Security Week reported that one of Molerats campaigns (October 2016) heavily used popular RATs like NjRat and H-Worm (aka Houdini).
Technical Analysis: Molerats 2019
October 2019: In Molerats’ October operation, the attack was distributed as a phishing campaign in the Middle East. Emails included a Microsoft Word file attachment with the title “Daily report on the most important Palestinian developments for the day 9-9-2019.doc” — content that spoke to the political situation in Palestine. When a victim opened the attachment, the malware performed the following:
Displayed the Microsoft Word doc
A recent spear-phishing document from Molerats
APT-C-37 Overview
APT-C-37, also known as Pat-Bear or the Syrian Electronic Army (SEA), was first seen in October 2015 targeting members of a terrorist organization. Since 2015, however, APT-C-37 has broadened their objectives to include government agencies, armed forces leadership, media organizations, political activists, and diplomats. The group mostly targets victims in Western countries, with the intent of defacing their websites and social accounts while leaving a public footprint after hacking one of their victims.
In previous attacks, APT-C-37 targeted Windows and Android systems, utilizing popular commercial remote access trojans (RATs) such as DroidJack, SpyNote, njRAT, SSLove, and H-Worm.
Technical Analysis: APT-C-37 2019
June 2019: APT-C-37 released an Android app named after the instant messaging software “WhatsApp” as an espionage tool to reportedly spy on the Syrian opposition forces. The app was capable of installing the SSLove RAT to pull private information from the phone and exfiltrating it to a remote location.
Molerats Overview
Molerats has been present in the cybercriminal landscape since 2012. In an analysis released by the Kaspersky’s GReAT (Global Research & Analysis Team) earlier this year on the Gaza Hacker Team and their various subgroups, Kaspersky concluded that Molerats is Gaza Cybergang “Group1.” The report also concluded that Molerats (i.e. Cybergang Group 1) operates with a lower level of sophistication than other groups within the Gaza Hacker Team. In addition, a 2016 article in Security Week reported that one of Molerats campaigns (October 2016) heavily used popular RATs like NjRat and H-Worm (aka Houdini).
Technical Analysis: Molerats 2019
October 2019: In Molerats’ October operation, the attack was distributed as a phishing campaign in the Middle East. Emails included a Microsoft Word file attachment with the title “Daily report on the most important Palestinian developments for the day 9-9-2019.doc” — content that spoke to the political situation in Palestine. When a victim opened the attachment, the malware performed the following:
Displayed the Microsoft Word doc |
Malware Tool Threat Guideline | APT-C-23 | ||
| 2020-01-14 14:00:00 | Running an Eco-friendly IT business (lien direct) |
 (banner image green leaf key Adobe Stock )
As someone in the technology field I follow the steady stream of new and exciting products and gadgets that come out at least twice a year. I am constantly upgrading my tech and my IT work tools in keeping with what is new. I need to have personal experience with the devices and equipment that clients hire me to manage, upgrade and repair for them in my IT Consulting practice. I often think about the effect that my constant upgrading has on the environment.
In 2018, researchers from McMaster University came out with a study in the Journal of Cleaner Production that show that the carbon impact of Information and Communications Industry has tripled since 2007. In 2007 the Information and Communications sector represented 1% of the carbon footprint, by 2018 it was 3% and they project it that the number might climb to 14% by 2040. The impact of the entire transportation industry has a carbon footprint of 7% worldwide.
With numbers like that it is easy to become overwhelmed but, as IT professionals, there is still much we can do to mitigate the effects of e-waste and use our resources more wisely as we encourage our clients to do the same and empower them with solutions. In my practice I think about the services we offer and break down what we can do to adopt more sustainable practices.
We are a team of remote workers who go on-site to clients and our office is a virtual office based in the cloud. No commuting to work for our team of 2-5. That helps a lot. We collaborate over the web, phone and email. Step 1 in making your business more “eco-friendly” might be to re-think the office.
Changing how you run things in an office setting might mean installing a Smart Thermostat and lighting to conserve energy and committing to recycled paper for your printed materials. Not only will you save money, you could earn a Green Business Certification.
Organizations like Green Business Bureau and the American Consumer Council’s Green C Certification recognize and certify companies that are doing their part to conserve energy and reduce waste. Your company will stand out for promoting environmentally responsible practices and create a culture of “green” for others in the industry.
As far as making client services more energy efficient goes, I break it down into the following areas; Device Buyback and Recycling Programs, Municipal Recycling programs, Hosting, Search, Recycled Materials and Office Equipment.
Go to the stores you might buy from to recycle e-waste. You can recycle 3 household items per day at Best Buy Stores - that includes printers, monitors (for a $25 fee), UPS battery backups and surge protectors and many other items used in a typical office. For smaller projects it might be convenient to drop off at a local Best Buy store.
Also, there is the Apple Trade-in Program. Started in 2013, Apple will give you a gift card for trading in qualified devices, computers and Apple accessories. If your devices don’t qualify for a monetary credit, you can still take advantage of Apple’s recycling program, regardless of age. There is an online portal to process your trade in, just answer a few basic questions about your devices and you will get a gift
(banner image green leaf key Adobe Stock )
As someone in the technology field I follow the steady stream of new and exciting products and gadgets that come out at least twice a year. I am constantly upgrading my tech and my IT work tools in keeping with what is new. I need to have personal experience with the devices and equipment that clients hire me to manage, upgrade and repair for them in my IT Consulting practice. I often think about the effect that my constant upgrading has on the environment.
In 2018, researchers from McMaster University came out with a study in the Journal of Cleaner Production that show that the carbon impact of Information and Communications Industry has tripled since 2007. In 2007 the Information and Communications sector represented 1% of the carbon footprint, by 2018 it was 3% and they project it that the number might climb to 14% by 2040. The impact of the entire transportation industry has a carbon footprint of 7% worldwide.
With numbers like that it is easy to become overwhelmed but, as IT professionals, there is still much we can do to mitigate the effects of e-waste and use our resources more wisely as we encourage our clients to do the same and empower them with solutions. In my practice I think about the services we offer and break down what we can do to adopt more sustainable practices.
We are a team of remote workers who go on-site to clients and our office is a virtual office based in the cloud. No commuting to work for our team of 2-5. That helps a lot. We collaborate over the web, phone and email. Step 1 in making your business more “eco-friendly” might be to re-think the office.
Changing how you run things in an office setting might mean installing a Smart Thermostat and lighting to conserve energy and committing to recycled paper for your printed materials. Not only will you save money, you could earn a Green Business Certification.
Organizations like Green Business Bureau and the American Consumer Council’s Green C Certification recognize and certify companies that are doing their part to conserve energy and reduce waste. Your company will stand out for promoting environmentally responsible practices and create a culture of “green” for others in the industry.
As far as making client services more energy efficient goes, I break it down into the following areas; Device Buyback and Recycling Programs, Municipal Recycling programs, Hosting, Search, Recycled Materials and Office Equipment.
Go to the stores you might buy from to recycle e-waste. You can recycle 3 household items per day at Best Buy Stores - that includes printers, monitors (for a $25 fee), UPS battery backups and surge protectors and many other items used in a typical office. For smaller projects it might be convenient to drop off at a local Best Buy store.
Also, there is the Apple Trade-in Program. Started in 2013, Apple will give you a gift card for trading in qualified devices, computers and Apple accessories. If your devices don’t qualify for a monetary credit, you can still take advantage of Apple’s recycling program, regardless of age. There is an online portal to process your trade in, just answer a few basic questions about your devices and you will get a gift |
Guideline | |||
| 2020-01-13 14:00:00 | How to identify phishing emails and what to do (lien direct) |
 Note:This blog was written by an independent guest blogger.
Phishing scams remain one of the most widespread cybercrimes. A phishing scam can be as simple as getting someone to click on a link, attachment, or a picture of cute kittens. I recently received a spam email with the message:
“Old friends post embarrassing pictures of Jason Nelson online; click here to see.”
Seeing my name in the body or subject line of an email is alarming. That is why scammers word these emails this way. They want to alarm you, and in your rush to defend yourself, click the link to see the pictures.
Similar to extortion emails that claim to have videos of “compromising” situations or screen recordings of users on adult websites. These emails work on our fear of embarrassment, rejection, or ruin to get us to let down our guard.
Do not click on anything in these emails. Delete, Delete, DELETE.
But, it does beg the question, where do these emails come from, who is sending them? In this article, we will be looking at the phishing phenomenon and what options we have to defend ourselves.
According to a 2018 report from statistics website Statista, at 11.69%, the majority of spam emails originated in China. But before we in the U.S. pat ourselves on the back, the second-largest amount of spam emails came from the United States at 9.04%.
Since 2018, many of these scams demand some form of a cryptocurrency payment. In an October 8, 2019 report, the cybersecurity company Cofense said that phishing scams are changing their tactics and moving from Bitcoin to one of the so-called altcoins like Litecoin or Monero.
So how do these scammers get our emails? One way and most likely is lax security protocols or a data breach at a service or email provider. HaveIbeenPwned is a website that can help you see if your email is on a compromised site.
But there are other ways as well, including email addresses sold to the highest bidder. A way to minimize our risk of phishing scams is to be mindful of and limit the websites we provide our emails. Also, use a password manager to create more complex passwords. BitWarden, 1Password, and Dashlane are good options.
When deciding on an email address, avoid using your name and or some specific data. For example, janedoe1980@email.com - try to avoid using your actual name and actual year of birth or the last four of your social (for U.S. Citizens).
There is no way to be 100% safe online, but at least we can make it that much harder for cybercriminals.
So let’s look at some steps we can take to protect ourselves from phishing and scam emails:
Check the sender address, even if the message seems legitimate, look at the sending address, if it looks odd, it’s probably spam.
Does the email ask you to click on a link or attachment? Again check the sender address and the rest of the email for anything out of the ordinary.
Did you receive the email out of the blue? A long lost relative is trying to send you money? Delete.
Does the email contain several misspelled words? It could be a phishing email.
Does the email contain some threat (embarrassment, prosecution for example) it’s more than likely a phishing scam.
Lastly, if the email appears to be from someone you know or an organization you do business with, call that person (not from a number on the email) and verify they sent the email. Law Enforcement and the IRS are not known for sending threatening
Note:This blog was written by an independent guest blogger.
Phishing scams remain one of the most widespread cybercrimes. A phishing scam can be as simple as getting someone to click on a link, attachment, or a picture of cute kittens. I recently received a spam email with the message:
“Old friends post embarrassing pictures of Jason Nelson online; click here to see.”
Seeing my name in the body or subject line of an email is alarming. That is why scammers word these emails this way. They want to alarm you, and in your rush to defend yourself, click the link to see the pictures.
Similar to extortion emails that claim to have videos of “compromising” situations or screen recordings of users on adult websites. These emails work on our fear of embarrassment, rejection, or ruin to get us to let down our guard.
Do not click on anything in these emails. Delete, Delete, DELETE.
But, it does beg the question, where do these emails come from, who is sending them? In this article, we will be looking at the phishing phenomenon and what options we have to defend ourselves.
According to a 2018 report from statistics website Statista, at 11.69%, the majority of spam emails originated in China. But before we in the U.S. pat ourselves on the back, the second-largest amount of spam emails came from the United States at 9.04%.
Since 2018, many of these scams demand some form of a cryptocurrency payment. In an October 8, 2019 report, the cybersecurity company Cofense said that phishing scams are changing their tactics and moving from Bitcoin to one of the so-called altcoins like Litecoin or Monero.
So how do these scammers get our emails? One way and most likely is lax security protocols or a data breach at a service or email provider. HaveIbeenPwned is a website that can help you see if your email is on a compromised site.
But there are other ways as well, including email addresses sold to the highest bidder. A way to minimize our risk of phishing scams is to be mindful of and limit the websites we provide our emails. Also, use a password manager to create more complex passwords. BitWarden, 1Password, and Dashlane are good options.
When deciding on an email address, avoid using your name and or some specific data. For example, janedoe1980@email.com - try to avoid using your actual name and actual year of birth or the last four of your social (for U.S. Citizens).
There is no way to be 100% safe online, but at least we can make it that much harder for cybercriminals.
So let’s look at some steps we can take to protect ourselves from phishing and scam emails:
Check the sender address, even if the message seems legitimate, look at the sending address, if it looks odd, it’s probably spam.
Does the email ask you to click on a link or attachment? Again check the sender address and the rest of the email for anything out of the ordinary.
Did you receive the email out of the blue? A long lost relative is trying to send you money? Delete.
Does the email contain several misspelled words? It could be a phishing email.
Does the email contain some threat (embarrassment, prosecution for example) it’s more than likely a phishing scam.
Lastly, if the email appears to be from someone you know or an organization you do business with, call that person (not from a number on the email) and verify they sent the email. Law Enforcement and the IRS are not known for sending threatening |
Data Breach Spam Threat | |||
| 2020-01-10 14:00:00 | Top 10 AT&T Cybersecurity blogs of 2019 (lien direct) |
 Happy New Year! What a year 2019 was in cybersecurity. It was a great year for informative and interesting blogs. Here were the top performing AT&T Cybersecurity blogs written in 2019:
1. The Great Cannon has been deployed again by Chris Doman took the top spot!
2. AT&T Cybersecurity is Born by our CEO, Barmak Meftah was hugely popular.
3. Incident response steps comparison guide for SANS and NIST by Elisha Girkin.
4. There's no such thing as an entry-level job in cybersecurity by the AT&T Chief Security Office.
5. A HIPAA compliance checklist for 2019 by Tawnya Lancaster.
6. Sharepoint vulnerability exploited in the wild by Chris Doman.
7. The ultimate guide to VPN encryption, protocols and ciphers by guest blogger, Callum Tennent.
8. Fileless malware detection: a crash course by Kate Brew.
9. Explaining the cyber kill chain model by Tony DeGonia.
10. Email server security best practices to look out for by guest blogger Kim Crawley.
We look forward to sharing much more helpful information and security research in the rest of 2020!
Happy New Year! What a year 2019 was in cybersecurity. It was a great year for informative and interesting blogs. Here were the top performing AT&T Cybersecurity blogs written in 2019:
1. The Great Cannon has been deployed again by Chris Doman took the top spot!
2. AT&T Cybersecurity is Born by our CEO, Barmak Meftah was hugely popular.
3. Incident response steps comparison guide for SANS and NIST by Elisha Girkin.
4. There's no such thing as an entry-level job in cybersecurity by the AT&T Chief Security Office.
5. A HIPAA compliance checklist for 2019 by Tawnya Lancaster.
6. Sharepoint vulnerability exploited in the wild by Chris Doman.
7. The ultimate guide to VPN encryption, protocols and ciphers by guest blogger, Callum Tennent.
8. Fileless malware detection: a crash course by Kate Brew.
9. Explaining the cyber kill chain model by Tony DeGonia.
10. Email server security best practices to look out for by guest blogger Kim Crawley.
We look forward to sharing much more helpful information and security research in the rest of 2020!
|
Malware Vulnerability | |||
| 2020-01-08 14:00:00 | Security and digital payments – growth finally meeting demand (lien direct) |
 Digital payments are the future of commerce, but security concerns have created a major barrier to their popularity. A study of businesses conducted by the influential PCI Security Standards Council found that 67% of respondents cited a lack of visible security options as a reason for not adopting a digital payments service. A paucity of viable security options, both in terms of product quality and the level of protection that can be offered, has been a stumbling block in the digital payments sector; however, industry indicators suggest that this is beginning to change and good quality products will soon be widespread.
Big businesses tackling fraud
Financial fraud directed at small businesses will have effects felt most acutely the business itself. However, the mechanisms through which businesses reclaim fraud-related losses have impacts on the institutions that provide banking and credit to these businesses. Insurance payouts, charge backs and voided credit transactions all have a significant overall impact on big financial institutions. According to the annual American Express Digital Payments Survey, 82% of businesses feel threatened by fraud via digital payments; as a result, big business has moved forward to provide bespoke security solutions, and have put their name forward for many digital payment platforms to enhance that security. Growing businesses looking towards digital payments can now cater for a huge range of digital payments platforms and the financial security that they offer.
An improving data climate
Front-end security services are the most crucial step in ensuring the viability of integrating digital payments. Promoting an overall culture that values customer private and financial data will promote the long term change that the payments needs to hold customer confidence. This is a factor well recognized, both by regulatory bodies and international governments, and has been exemplified by the roll-out and response to GDPR. Most recently, Forbes have noted the business trend towards data assurance being king, and have advocated for businesses having dedicated specialists to monitor breaches. The move of businesses to becoming more tech savvy is driving innovation in data security products, and crucially creating capacity to deal with the influx of data-related breaches and security complaints.
Future payments
All of this good work is culminating in collaborative efforts, the most recent of which has seen payments giant TAS USA develop security solutions with startup Super Processor. This venture is to pair with the potentially transformative Mastercard CARD 3.0 IE system. According to Bobs Guide, this is a clear signal of how technologists are combining their new and innovative products to the benefit of the customer and the wider industry.
With collaborative efforts will come better technology and better growth for all types of business. Digital payments are clearly the way forward in the super-mobile digital era. Making them safe is the key challenge of this.
Digital payments are the future of commerce, but security concerns have created a major barrier to their popularity. A study of businesses conducted by the influential PCI Security Standards Council found that 67% of respondents cited a lack of visible security options as a reason for not adopting a digital payments service. A paucity of viable security options, both in terms of product quality and the level of protection that can be offered, has been a stumbling block in the digital payments sector; however, industry indicators suggest that this is beginning to change and good quality products will soon be widespread.
Big businesses tackling fraud
Financial fraud directed at small businesses will have effects felt most acutely the business itself. However, the mechanisms through which businesses reclaim fraud-related losses have impacts on the institutions that provide banking and credit to these businesses. Insurance payouts, charge backs and voided credit transactions all have a significant overall impact on big financial institutions. According to the annual American Express Digital Payments Survey, 82% of businesses feel threatened by fraud via digital payments; as a result, big business has moved forward to provide bespoke security solutions, and have put their name forward for many digital payment platforms to enhance that security. Growing businesses looking towards digital payments can now cater for a huge range of digital payments platforms and the financial security that they offer.
An improving data climate
Front-end security services are the most crucial step in ensuring the viability of integrating digital payments. Promoting an overall culture that values customer private and financial data will promote the long term change that the payments needs to hold customer confidence. This is a factor well recognized, both by regulatory bodies and international governments, and has been exemplified by the roll-out and response to GDPR. Most recently, Forbes have noted the business trend towards data assurance being king, and have advocated for businesses having dedicated specialists to monitor breaches. The move of businesses to becoming more tech savvy is driving innovation in data security products, and crucially creating capacity to deal with the influx of data-related breaches and security complaints.
Future payments
All of this good work is culminating in collaborative efforts, the most recent of which has seen payments giant TAS USA develop security solutions with startup Super Processor. This venture is to pair with the potentially transformative Mastercard CARD 3.0 IE system. According to Bobs Guide, this is a clear signal of how technologists are combining their new and innovative products to the benefit of the customer and the wider industry.
With collaborative efforts will come better technology and better growth for all types of business. Digital payments are clearly the way forward in the super-mobile digital era. Making them safe is the key challenge of this.
|
||||
| 2020-01-07 14:00:00 | Healthcare cybersecurity for 2020 and beyond (lien direct) |
An independent guest blogger wrote this blog.
 These days, effective cybersecurity in healthcare is as critical as ever. Last year, more than 32 million patients had their personal and medical information stolen in data breaches across the United States. While moves are being made, the fact remains that healthcare providers still have many holes to plug when it comes to the illegal or accidental outpouring of patient data.
The issue is that current problems need to be solved now before hackers move on to new, more advanced attack strategies. The good news is that there are many methods currently available to mitigate the chances of data leakage if medical professionals are proactive enough to enforce them.
HIPAA on the front lines
When patients visit the doctor, they expect to go to a safe place where their best interests are always the top priority. To foster that confidence, the Health Insurance Portability and Accountability Act was created to protect patient data while also giving the patients control over who can see their information. Along with HIPAA, the Health Information Technology for Economic and Clinical Health (HITECH) Act, encourages medical practices also to ensure that all technology they use is protected to eliminate wrongful data leakage.
Medical records contain an abundance of private information that can be used for any number of malicious means. Full medical records can often go for $1000 on the black market where the addresses, social security numbers, and financial information within can be used to create fake identification or take out large loans that can leave the patient in debt. If a hacker catches wind of a patient’s surgery date, they can even attempt to shut down hospital functions until a ransom is paid, like the $14K one paid by Columbia Surgical Specialists.
For these security reasons and to retain the trust of the patients, proper data security is essential, and it starts on the front lines. Nurse leaders should train their staff on how to retain patient confidentiality properly. When discussing the patients near the front desk, only use first names, and conversations should be had behind a closed door or as quietly as possible. Hard copies of patent data should never be left lying around, and your printer should be set to print pages facing down. The last thing you need is to have security precautions in place but still allow a criminal to simply walk up and take private information out of the office.
Proper record keeping
Because hackers have so much to gain from stealing patient data, proper record-keeping is essential. Per HIPAA, medical records are required to be kept between five to 10 years, based on the state and the patient’s last treatment or discharge. If paperwork is to be discarded, it must be properly shredded. If you keep paper records, they must be stored in locked cabinet
These days, effective cybersecurity in healthcare is as critical as ever. Last year, more than 32 million patients had their personal and medical information stolen in data breaches across the United States. While moves are being made, the fact remains that healthcare providers still have many holes to plug when it comes to the illegal or accidental outpouring of patient data.
The issue is that current problems need to be solved now before hackers move on to new, more advanced attack strategies. The good news is that there are many methods currently available to mitigate the chances of data leakage if medical professionals are proactive enough to enforce them.
HIPAA on the front lines
When patients visit the doctor, they expect to go to a safe place where their best interests are always the top priority. To foster that confidence, the Health Insurance Portability and Accountability Act was created to protect patient data while also giving the patients control over who can see their information. Along with HIPAA, the Health Information Technology for Economic and Clinical Health (HITECH) Act, encourages medical practices also to ensure that all technology they use is protected to eliminate wrongful data leakage.
Medical records contain an abundance of private information that can be used for any number of malicious means. Full medical records can often go for $1000 on the black market where the addresses, social security numbers, and financial information within can be used to create fake identification or take out large loans that can leave the patient in debt. If a hacker catches wind of a patient’s surgery date, they can even attempt to shut down hospital functions until a ransom is paid, like the $14K one paid by Columbia Surgical Specialists.
For these security reasons and to retain the trust of the patients, proper data security is essential, and it starts on the front lines. Nurse leaders should train their staff on how to retain patient confidentiality properly. When discussing the patients near the front desk, only use first names, and conversations should be had behind a closed door or as quietly as possible. Hard copies of patent data should never be left lying around, and your printer should be set to print pages facing down. The last thing you need is to have security precautions in place but still allow a criminal to simply walk up and take private information out of the office.
Proper record keeping
Because hackers have so much to gain from stealing patient data, proper record-keeping is essential. Per HIPAA, medical records are required to be kept between five to 10 years, based on the state and the patient’s last treatment or discharge. If paperwork is to be discarded, it must be properly shredded. If you keep paper records, they must be stored in locked cabinet |
Threat Guideline | APT 10 | ||
| 2020-01-06 14:00:00 | Don\'t give away your secret answers (lien direct) | Note:This blog was written by an independent guest blogger. I was watching an interview with an American Congressional member the other night, and I could not help but notice the person’s lack of cybersecurity awareness. As a disclaimer, please note that this is not a piece promoting or denouncing any political party, or view. I do not discuss politics unless it relates to a cybersecurity matter. In two previous posts, I have been misunderstood and thought to be promoting a position, but that isn't my intended purpose - cybersecurity awareness is. In the interview, the Congressional member told an entertaining story about how a site was requesting the creation of a “Security Question”. We have all been subject to these inane questions that require horribly predictable, and sometimes, very publicly known answers. These questions are usually used for password recovery, or password reset functions. In this particular case, the question that was chosen is “What is the name of your dog?” What happened next is where I was mortified at the lack of awareness. The conversation went something like this: Congress member: “So I put in the name of my dog, and the site said that the name was too short.” Did you just perform a face-palm, as I did when I heard that? Let’s review some of the more common short-names for dogs: Rex, Spot, Hero, Bud. I am sure that you can come up with a few others. The problem here is that this Congressional representative just narrowed the search criteria for anyone who wants to guess one of the security questions for a forgotten password. There is no need to use long names in a brute-force attack when it has already been revealed that the dog has a short name. We know for certain that the dog’s name is definitely NOT Alistair, or even Bunsen Honeydew. This also indicates that this Congress person is not using a password manager. One need not search too long to find many resources about how to generate and store random answers for those security questions. As was reported during the “Celebgate” and “TheFappening” nude photo scandals, some celebrities were victims of social engineering that caused them to reveal their security answers. One impressive lesson from this experience is that the web site that was requesting the security answer has made a bit of an effort to prevent easily-guessed, short names. However, to the average person, what are they to do if their dog’s name is simply “Rex”? Should they change their dog’s name to appease a web site? Or, should they create a name to satisfy the question? How are they to remember that fake name? These problems are what cause people to develop a strong disdain for security. Moreover, why are sites still using these horrible pre-defined verification questions? I am no fan of those questions, and even on sites that allow a person to enter a unique question, most folks will use very common questions, and answers. With all the other mechanisms out there, such as mobile authenticators, and multi-factor options, there must be a better way to authenticate a person. In the meantime, please be careful with those security answers. | LastPass | |||
| 2019-12-17 14:00:00 | Top Cybersecurity trends & predictions for 2020 (lien direct) |
It is that time of year again where we look forward to what cyber goodies the New Year brings. 2019 brought new records in data breaches, a rash of ransomware attacks, and a rise in state-sponsored cyber-attacks. Below is a quick list of what me may expect in the 2020.
Cybersecurity will become even more of a strategic priority for companies as the cost, sophistication, and lethality of breaches continue to rise.
The advent of emerging and fused technologies 5G, IoT (and Industrial IoT) will pose significant operational and regulatory challenges. Companies and agencies will look to automation and orchestration technologies such as machine learning, deep learning, artificial intelligence, and other analytic tools to mitigate gaps on ubiquitous platforms.
Threat actors, especially state-sponsored, and criminal enterprises will take advantage of the expanding cyber-attack surface by sing their resources to employ more sophisticated means for discovering target vulnerabilities, automating their phishing attacks, and finding new deceptive paths for infiltrating malware.
For CISOs, enterprise tools such as predictive analytics, machine learning and artificial intelligence will be more readily adapted to expand the effectiveness of mitigation and analysis of threats. The role of the CISO will grow in importance as cybersecurity is not just an IT issue, but a survival and ROI imperative for companies.
Cybersecurity concerns will also continue to be a growing priority for government with strategy, investment, and procurement. This is already evident in the restructuring of government roles and assets. The Department of Defense (DOD), the US Cyber Command, The Army Futures Command, and the Navy and Air Force are already investing in acquisition of new technologies and training of cybersecurity components. Similarly, on the civilian side, the Department of Homeland Security (DHS) has created Cybersecurity Infrastructure Security Agency (CISA) to focus on primarily cybersecurity threats to the critical infrastructure. Look for bigger budgets for agencies t acquire expertise and needed cybersecurity tools.
Protecting the supply chain will continue to be a major area of focus. Supply chain security has been identified both by industry and government as a key vulnerability. A new White House Presidential Executive order was recently issued to help secure the supply chain (both public and commercial) from undue risk of sabotage to or subversion of the design, integrity, manufacturing, production, distribution, installation, operation, or maintenance of information and communications technology or services.
Public Private Partnerships (PPP) will expand throughout the cybersecurity ecosystem. Open collaboration, threat sharing, and cooperative research and development with catalyze innovation and facilitate solutions. PPP will be perceived good news for both industry and government
In 2020, a qualified cybersecurity worker shortage will continue to pose major challenges for both the public and private sectors. The problem grows and automation will be only a partial remedy.
Compliance and digital privacy policy requirements will continue to broaden across industry sectors propelled by government legislation. It will be both policy and consumer privacy driven. GDPR was only a start and is setting the table for others to follow.
2020 also will be the dawn of a new decade that will bring technological transformation that will permeate all aspects of our lives, including cybersecurity. The future has arrived, and we need to be prepared for the uncertainty of what lies ahead in our emerging digital world.
|
Ransomware Threat | |||
| 2019-12-16 01:07:00 | Should cities pay a ransomware demand? (lien direct) | UPDATE: In a “ripped from the headlines” moment, we have real world confirmation of the growing risk discussed in this article. Breaking news over the weekend revealed that both the city of New Orleans and New Jersey's largest hospital network are in the midst of dealing with serious ransomware attacks. When you hear about data breaches and cyberattacks in the news, it's usually in connection with a large company and has affected users across the globe. But that gives the impression that hackers only target huge enterprises when planning their next attack. The truth is just the opposite. Because small organizations, like city and town governments, are forced to work with tight IT budgets but still need to comply with all rules and regulations, they often can't afford to hire cybersecurity experts or invest in expensive software solutions. Hackers know this and focus their efforts on trying to compromise their systems to profit from the damage. In this article, we'll look specifically at the trend of ransomware and how organizations should respond when they are attacked. How ransomware works When a data breach occurs, hackers often seize stolen information from a back-end system and look to sell it on the dark web. But more recently, cybercriminals have realized that they can make money without having to execute a transaction at all. They simply need to hold the stolen data as ransom. Ransomware attacks can begin through a number of different means. Hackers may infiltrate a government's network through social engineering, a phishing scam, or by finding a flaw in access controls. Once inside, they will deploy a form of malware that encrypts all of the files on a local hard drive so that users cannot open, access, or transfer them. These pieces of malware are evolving all the time, which makes it tough for antivirus tools to keep up. For the individuals working in the office, they'll typically see a suspicious screen appear telling them that they have fallen victim to ransomware. The hackers will set a specific financial amount, usually in Bitcoin, to be paid in exchange for releasing the lock on the files. Ransomware isn’t just limited to private companies, public medical infrastructure are common targets of these kinds of attacks. Some companies allow employees to work from home, one access from an unprotected home device that has spy malware installed unknowingly puts the company at risk. Outdated technology is another huge issue. Public hospital systems operate on outdated technology with antiquated data protection software. Even third-party appointment setting software can be targeted to gain access to private health care record and patient databases. The risks of paying Municipal governments rely on their IT systems to sustain operations on a daily basis. Losing access to a server or database can bring everything to a standstill and hurt the citizens who rely on government services. So in the event of a ransomware attack, it's understandable that the organization would seek to resolve the issue quickly, by whatever means necessary, to | Ransomware Data Breach Malware Vulnerability | |||
| 2019-12-12 14:00:00 | Which security certification is for you (if any) (lien direct) | It is hard to look at an information security job posting without seeing some certifications desired. Some make sense and others not so much. I have looked at junior helpdesk positions asking for CISSP, and some of the roles at some of the most respected companies do not ask for any certifications. There are some certifications that in having them demands instant respect: OSCP, OSCE, GXPN, and GREM, to name a few. Dave Kennedy has stated that anyone with an OSCE that applies to TrustedSec will at least get an interview. So, as a n00b, where do you start? Honestly, there is no right or wrong answer. I am sorry to disappoint you. Before you exit this article, I have some insight for you. Let’s start with the discussion of to get certifications or not to get certifications. Off the bat, if you plan to work for the US Department of Defense or Federal Government (as a contractor or civilian), you need certifications. Starting with CompTIA Security+, then EC-Council’s C|EH, then (ISC)2 CISSP, then a variety of other certifications from CompTIA, SANS, etc. DOD Directive 8140.01 mandates this. What about outside the government? There is no specific right or wrong answer, as I stated above. I know this is anti-climactic, but not all jobs require certifications. Some employers/hiring managers will hold some certifications to a high esteem and may hold grudges against others, thus hurting you for having it. In the absence of the job posting saying not to apply if you have insert certification here, there is no way to know. Having a certification should differentiate (not define) you as a candidate. If you are equally experienced and qualified as another person, the certification may put you over the top in getting that offer letter, but there are other factors in play. Regarding certification vendors, not all are created equal. Some focus on non-technical material primarily, others have excruciatingly challenging exams while others are best for entry-level certifications. Some certifications, like the AlienVault Certified Security Engineer (ACSE) or Cisco Certified Networking Associate (CCNA), are focused on a specific vendor. Full Disclosure: I hold the ACSE certification and have previously taught | ||||
| 2019-12-11 14:00:00 | Google Cloud Platform security monitoring with USM Anywhere™ (lien direct) | According to a 2019 Cyber Security Report published by the International Information System Security Certification Consortium, 93 percent of organizations say they are concerned about cloud security and 28 percent admit to having experienced cloud security incidents during the past year. The reality is, most companies lack the specialized knowledge and skills needed to provide that customer data stored in the cloud is protected Cloud service providers (CSPs) do provide extra security layers, such as automating threat detection, with the intent of making their customers feel more confident in the security of the cloud. However, the number of cloud breaches that are being reported shows that CSPs and organizations alike continue to struggle with cloud security. Much of this is due to a lack of unified visibility not just in the cloud, but across an organization’s entire network, siloed teams and technologies, lack of threat intelligence, and partnerships with third-parties whose security controls are not up to snuff. To address these challenges, many in the industry are advocating for organizations to simplify and unify their security approach, i.e. bring as many controls as possible into a single solution in order to break down the silos between security teams and technologies and to give greater visibility across the organization. We at AT&T Cybersecurity help organizations to accomplish this with our Unified Security Management™ (USM) Anywhere platform. Of course, the effectiveness of any security solution is largely determined by the threat intelligence underpinning it. In any environment, we need to identify the common tactics, techniques, and procedures (TTPs) adversaries are using in their attacks. Below, we provide an overview of the latest threat intelligence from Alien Labs™ for Google Cloud Platform (GCP), which helps security practitioners to discover issues in their cloud workloads and detect adversaries exploiting attack vectors commonly seen in cloud environments. Google Cloud Platform integration in USM This summer, AT&T Cybersecurity launched the USM Anywhere™ integration with GCP. Through the USM Anywhere Alien App for GCP, USM can now consume all logging information managed by the Stackdriver utility in a configurable and intuitive way. Google Cloud Platform logs are provided through three major channels: Audit Logs. Record all events impacting objects within the environment. These logs are used to monitor any cloud assets, presenting a solid baseline for security detection. VPC Flow Logs. Half way between resource monitoring and cloud infrastructure security, these logs are the delights of NIDS enthusiasts. Firewall Logs. These help with auditing firewall rules events, and they are useful in detecting risky open ports and other configuration issues. In USM, these channels are processed by different plugins, which extract pieces of intelligence and map them to variables that are easy to steer into orchestration rules. The correlation engine allows for the combination of detections from different channels into a single orchestration rule, scaling GCP security to a new level. To prevent an intrusion from being recorded or triggering a notification, adversaries may try to disable audit logging once they get the necessary permissions. To protect against that, the product has out of the box correlation rules to generate an alert if any of the logging features is disabled. | Tool Threat Guideline | Uber | ||
| 2019-12-10 14:00:00 | Rising to the challenge of delivering more secure elections (lien direct) | As efforts to modernize and digitize outdated and aging elections infrastructure take hold across the U.S., the demand for a revolutionized approach to cybersecurity has become an increasing imperative. Democratic nations rely on public trust in the integrity of their institutions and in a republic with the guiding principles of government “of the people, by the people and for the people.” There is perhaps a no more important system that that of free, fair, and secure elections. As we move deep into the digital era, societies have come to expect innovation in every aspect of their lives. And while governments have often been slower to respond to this reality, innovations to elections systems are beginning to appear, such as mobile vote centers, digital pollbooks, QR code-based ballots, and even remote voting through mobile applications. Adoption of these new technologies has the potential to bring many benefits, including an improved voter experience and increase individual participation in the democratic process through enhanced access to cast a ballot. However, digital-enabled network and cloud-supported architectures introduce new and unique challenges, particularly in the area of cybersecurity. Consider the realities of elections operations that create potential vulnerabilities and opportunities for exploitation: Infrastructure is often stood up rapidly, on-demand and used only for very short intervals of time. Supporting physical and network infrastructure is frequently leased or borrowed from various disparate entities (schools, libraries, government offices) and traffic may be routed across various untrusted networks. Many poll workers and support staff are temporary contractors or volunteers (whose qualifications vary greatly by state) and may be trained insufficiently. Voting machines and supporting infrastructure (routers, switches, firewalls, etc.) can spend significant amounts of time in storage and then are quickly deployed; sometimes passing through multiple hands, creating possible chain-of-custody challenges. Physical safeguards of polling stations are difficult to scale and cost prohibitive. Addressing these and other challenge begins with sound risk management strategies that align government focus, limited budgets, and time constraints to the areas of greatest positive impact. Let’s start with some good framing questions. What are the risks? Vulnerabilities? Threats? Understanding the risks to election operations is key. Unfortunately, all too often public focus is unduly placed or heavily weighted on hackers, external threat actors, and hostile nation states. In reality, one of the biggest threats to an election is a lack of public confidence in the veracity of the results; in other words, perception. Basic security violations can do just as much, if not more, harm than a foreign threat actor and are more likely to occur. To combat these threats, stay focused on building a system that reinforces security fundamentals like integrity, audibility, accountability, non-repudiation and verifiable chain-of-custody. What are the regulatory mandates, and can we go further with security best practices? The Department of Homeland Security (DHS) designates elections systems as critical infrastructure; which mandates a host of regulatory standards and guidelines that must be adhered to or at least evaluated for applicability. It’s important to understand how the NIST guidelines and CIS v7, for example, address the development of your controls and the | Threat | |||
| 2019-12-04 15:28:00 | The “Great Cannon” has been deployed again (lien direct) |
Summary
The Great Cannon is a distributed denial of service tool (“DDoS”) that operates by injecting malicious Javascript into pages served from behind the Great Firewall. These scripts, potentially served to millions of users across the internet, hijack the users’ connections to make multiple requests against the targeted site. These requests consume all the resources of the targeted site, making it unavailable:
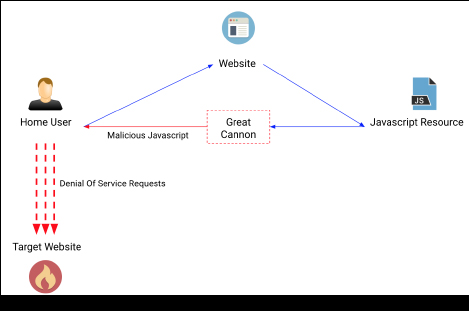 Figure 1: Simplified diagram of how the Great Cannon operates
The Great Cannon was the subject of intense research after it was used to disrupt access to the website Github.com in 2015. Little has been seen of the Great Cannon since 2015. However, we’ve recently observed new attacks, which are detailed below.
Most recent attacks against LIHKG
The Great Cannon is currently attempting to take the website LIHKG offline. LIHKG has been used to organize protests in Hong Kong. Using a simple script that uses data from UrlScan.io, we identified new attacks likely starting Monday November 25th, 2019.
Websites are indirectly serving a malicious javascript file from either:
http://push.zhanzhang.baidu.com/push.js; or
http://js.passport.qihucdn.com/11.0.1.js
Normally these URLs serve standard analytics tracking scripts. However, for a certain percentage of requests, the Great Cannon swaps these on the fly with malicious code:
Figure 1: Simplified diagram of how the Great Cannon operates
The Great Cannon was the subject of intense research after it was used to disrupt access to the website Github.com in 2015. Little has been seen of the Great Cannon since 2015. However, we’ve recently observed new attacks, which are detailed below.
Most recent attacks against LIHKG
The Great Cannon is currently attempting to take the website LIHKG offline. LIHKG has been used to organize protests in Hong Kong. Using a simple script that uses data from UrlScan.io, we identified new attacks likely starting Monday November 25th, 2019.
Websites are indirectly serving a malicious javascript file from either:
http://push.zhanzhang.baidu.com/push.js; or
http://js.passport.qihucdn.com/11.0.1.js
Normally these URLs serve standard analytics tracking scripts. However, for a certain percentage of requests, the Great Cannon swaps these on the fly with malicious code:
 Figure 2: Malicious code served from the Great Cannon
The code attempts to repeatedly request the following resources, in order to overwhelm websites and prevent them from being accessible:
http://lihkg.com/
https://i.loli.net/2019/09/29/hXHglbYpykUGIJu.gif?t=
https://na.cx/i/XibbJAS.gif?t=
https://na.cx/i/UHr3Dtk.gif?t=
https://na.cx/i/9hjf7rg.gif?t=
https://na.cx/i/qKE4P2C.gif?t=
https://na.cx/i/0Dp4P29.gif?t=
https://na.cx/i/mUkDptW.gif?t=
https://na.cx/i/ekL74Sn.gif?t=
https://i.ibb.co/ZBDcP9K/LcSzXUb.gif?t=
https://66.media.tumblr.com/e06eda7617fb1b98cbaca0edf9a427a8/tumblr_oqrv3wHXoz1sehac7o1_540.gif?t=
https://na.cx/i/6hxp6x9.gif?t=
https://live.staticflickr.com/65535/48978420208_76b67bec15_o.gif?t=
https://i.lihkg.com/540/https://img.eservice-hk.net/upload/2018/08/09/181951_60e1e9bedea42535801bc785b6f48e7a.gif?t=
https://na.cx/i/E3sYryo.gif?t=
https://na.cx/i/ZbShS2F.gif?t=
https://na.cx/i/LBppBac.gif?t=
http://i.imgur.com/5qrZMPn.gif?t=
https://na.cx/i/J3q35jw.gif?t=
https://na.cx/i/QR7JjSJ.gif?t=
https://na.cx/i/haUzqxN.gif?t=
https://na.cx/i/3hS5xcW.gif?t=
https://na.cx/i/z340DGp.gif?t=
https://luna.komica
Figure 2: Malicious code served from the Great Cannon
The code attempts to repeatedly request the following resources, in order to overwhelm websites and prevent them from being accessible:
http://lihkg.com/
https://i.loli.net/2019/09/29/hXHglbYpykUGIJu.gif?t=
https://na.cx/i/XibbJAS.gif?t=
https://na.cx/i/UHr3Dtk.gif?t=
https://na.cx/i/9hjf7rg.gif?t=
https://na.cx/i/qKE4P2C.gif?t=
https://na.cx/i/0Dp4P29.gif?t=
https://na.cx/i/mUkDptW.gif?t=
https://na.cx/i/ekL74Sn.gif?t=
https://i.ibb.co/ZBDcP9K/LcSzXUb.gif?t=
https://66.media.tumblr.com/e06eda7617fb1b98cbaca0edf9a427a8/tumblr_oqrv3wHXoz1sehac7o1_540.gif?t=
https://na.cx/i/6hxp6x9.gif?t=
https://live.staticflickr.com/65535/48978420208_76b67bec15_o.gif?t=
https://i.lihkg.com/540/https://img.eservice-hk.net/upload/2018/08/09/181951_60e1e9bedea42535801bc785b6f48e7a.gif?t=
https://na.cx/i/E3sYryo.gif?t=
https://na.cx/i/ZbShS2F.gif?t=
https://na.cx/i/LBppBac.gif?t=
http://i.imgur.com/5qrZMPn.gif?t=
https://na.cx/i/J3q35jw.gif?t=
https://na.cx/i/QR7JjSJ.gif?t=
https://na.cx/i/haUzqxN.gif?t=
https://na.cx/i/3hS5xcW.gif?t=
https://na.cx/i/z340DGp.gif?t=
https://luna.komica |
Tool Threat | |||
| 2019-11-22 14:00:00 | 5G is coming, are you prepared? (lien direct) |
5G technologies and networks are bringing exciting new possibilities for the enterprise. Many organizations are taking a proactive stance by anticipating the security requirements that will come with the new technology. Given the multifaceted nature of 5G and security, it’s critical for organizations to understand the magnitude of this undertaking.
You can check out a recent blog with some of the results of a recent study we conducted with 451 Group: AT&T Cybersecurity Insights™ Report: Security at the Speed of 5G. But wouldn’t a webinar be more fun? Great news - one is coming up soon: Wednesday December 4th at 12:00 PM CST.
In the webinar, we’ll cover:
• How 5G will transform the network with such things as Multi-edge Computing (MEC) and IoT
• Where 5G may present new security challenges and where it offers security benefits with a shared security model
• Which security controls will become most critical in the 5G future
• What security practitioners should focus on to get a head start on 5G
I’ll be the host – hope you can join us! REGISTER HERE.
|
||||
| 2019-11-21 14:00:00 | Why CJIS mobile compliance might be easier than you think (lien direct) |
Guest blog By Andrew King, AT&T Global Account Director, MobileIron
Although we just wrapped up National Cybersecurity Awareness Month in October, security professionals never take a break — because cybercriminals don’t either. That’s especially true for folks who work in law enforcement. Every day they are on the front lines helping to protect the public and solve crimes using Criminal Justice Information (CJI) such as crime reports and fingerprints. Protecting this information is extremely important, which is why Criminal Justice Information Services (CJIS) was created in 1992 to outline best-practice security requirements.
You may already know about CJIS, but did you also know that CJIS guidelines include a section about mobile device security?
This section outlines recommendations that various agencies can use to meet CJIS compliance and prevent data from falling into the wrong hands. Although agencies can follow a number of steps to achieve CJIS compliance on their own, mobile device management (MDM) solutions can make the process much faster and easier.
MobileIron provides a complete MDM solution that supports key best practices needed for CJIS compliance. These include the ability to:
Lock down and wipe data from lost, stolen, or compromised devices.
Enforce device security settings that users can’t delete or modify.
Prevent unsecured devices from accessing CJI.
Provide that CJI can only be shared between authorized apps on the device.
MobileIron actually goes beyond these minimum recommendations for CJIS compliance. Our mobile-centric, zero trust platform protects devices from sophisticated mobile threats, eliminates the need for passwords with zero sign-on authentication, and provides that only trusted users and devices can access cloud-based apps and services.
It’s why more than 19,000 customers, including law enforcement agencies, have chosen MobileIron as their trusted security partner.
Want to learn more? Review this brief CJIS Compliance Mobile Checklist for more insight into best practices and recommendations.
|
||||
| 2019-11-19 14:00:00 | The surprising truth about cybersecurity and autism (lien direct) | This is a guest blog by Kim Crawley. I’ve worked in cybersecurity for about a decade, but I’ve been autistic for my entire life. Careers usually start in adulthood, but autism is something children are born with. And contrary to what some people assume, autism doesn’t disappear at age 18. Autism is for life. Unfortunately, once autistic people become adults, services become a lot less plentiful. For each professional who diagnoses autism in adults, there are dozens or possibly hundreds of professionals who only diagnose autism in children. There exists an entire industry of supposed treatments for autistic children. Some of those supposed treatments are obviously harmful and should be illegal, like bleach-based snake oil (“Miracle Mineral Supplement” or “Miracle Mineral Solution”) to be administered to children orally or... through a different anatomical vector. Others, like Applied Behavioral Analysis, are widely condemned by autistic adults. Righfully so! Forcing autistic children to pretend to be neurotypical doesn’t cure them of autism and will ultimately backfire in PTSD and depression. I suspect treatments for autistic adults are few and far between because there’s little money to be made there. An autistic adult like myself can usually deny consent to a supposed treatment, whereas children usually cannot. Autistic people need support to manage life in a neurotypical world, and acceptance for harmless traits such as hand flapping and obsessive focus on topics of interest. There are symptoms of my autism that can be difficult, such as my hypersensitivity to the sound of vacuum cleaners and the feel of chalk on my hands, and my dyspraxia (a medical term for clumsiness.) But my autism comes with many positive traits too. The psychologist who diagnosed me with Autism Spectrum Disorder 1 in April says I have exceptional long-term memory. And when I’m interested in something, my thirst for knowledge is immense. I’m certain that I wouldn’t be a successful cybersecurity blogger if it weren’t for my autism. Research is my life’s work, and I can do so with remarkable intensity. Like most autistic adults, I would refuse a hypothetical cure for autism because if it weren’t for my autism, I just wouldn’t be myself. Everyone on Earth has strengths and weaknesses. It’s best to simply manage my weaknesses so I don’t lose my strengths. Not all, but many autistic teenagers and adults have a natural talent for computer technology. In fact, an obsession with computers is a part of many autism stereotypes. Computers are logical. If a computer malfunctions, there’s a clear reason for it that can be discovered with proper troubleshooting. Computers don’t demand uncomfortable eye contact unless you’re using iris scanning biometrics. Computers and the Internet are a gateway to a massive and ever-growing collection of knowledge. Computers facilitate social media, online chat, and email, so you can socialize with other people without their physical presence and without possibly misinterpreted body language. Some autistics, especially those with high support needs, are nonverbal or selectively mute. Many autistic children and adults with high support needs or intellectual disabilities are assumed to lack the ability to communicate with language until they’re given PCs, phones, or Augmentative and Alternative Communication (AAC) devices. With access to technology as an alternative to verbal speech, neurotypical people in their lives are shocked to learn that autistics who are assumed to be unintelligent because they don’t speak have been capable of sophisticated intelligence all along. Imagine how frustrating it is to not have a means of communication! Computer technology can make it possible. The affinity most autistics have for computers have clear and simple reasons. The world is going to need more and more cybersecurity professionals as | Hack Guideline | |||
| 2019-11-18 14:00:00 | How website security and SEO are intimately connected (lien direct) | Learning how to optimize your website can be a challenge. At one time, it was only about figuring out what Google wanted, which was largely keywords. Now, it’s much more complex. Google is focused on not only delivering high-quality, relevant search results, but also on protecting people from malware and unscrupulous websites. Not only that, a hack of your website by others can give Google false information that directly impacts your rankings. That’s why it’s vital for your website to have strong web security if you want to do well in SEO. How security can directly impact SEO Hacks, or attempts at hacks, can keep Google’s bots from accessing your site and assessing your content and keywords. Your server may report missing pages to Google because of a web scraper or hacker impacting your website. Why would someone hack your site? Usually it’s to do back-door SEO. For instance, a hacker wants to put a link on your site, or add a web page. Sometimes they even target your domain and redirect it to another site altogether. Sucuri has an excellent example of a common hack they see on WordPress sites. These hacks make your website look like an untrustworthy page, or may even draw penalties from Google that cause your site to be blacklisted. Sometimes, no matter how much effort you put into SEO, failures in cybersecurity can drastically impact how Google sees your site, therefore also impacting your place in the SERPs. The First Step in Security to Boost SEO One of the first things you need to do to protect your website and boost your Google ranking is to install HTTPS. Google named this security protocol a ranking signal several years ago, so it’s obvious that your SEO results will be tied to it. You’ll need to make sure you have a proper certificate and allow indexing so that Google can still read your website. However, this is only the beginning. An HTTPS setup does not secure a website, it only secures the connection and encrypts data that is sent. That means that communication between your server and the web browser a visitor is using is secure and data — like a credit card number used for purchase — cannot be stolen. Other Important Security Steps Information security, or keeping your stored data secure, is another important part of keeping your website secure and helping it rank well, and the good news is that this security requires the same vigilance that SEO does. As a result, you can monitor both simultaneously. Platform Security Be sure you’ve chosen a good web host that has strong security on their end. Use security software or plugins as appropriate. For smaller websites using WordPress, you can use Wordfence, iThemes Security, or Bulletproof Security, for example. Overall, you want plugins that address the known security issues in the platform you use. All websites can also benefit from using SiteLock, which not only closes security loopholes but also monitors your website daily for malware, viruses, and more. Secure Passwords Believe it or not, the | Malware Hack | APT 19 | ||
| 2019-11-14 14:00:00 | Cybersecurity: top of mind Q and A (lien direct) | I really enjoy Shira Rubinoff's videos, and captured one of them in case you prefer reading to watching videos. Please find snippets of this commentary in the AT&T Cybersecurity video series with Shira Rubinoff interviewing me recently. Episode #6 - @attcyber Video Series With @twaskelis AVP @attcyber Discuscussing:Issues we are facing in #CyberSecurity today Full video��https://t.co/1GxIQVAeJ0#ai #attinfluencer #Security@sstoesser @BinduSundaresan @BJWebb4 @saritasayso @MoKatibeh @eisaiah_e @ChuckDBrooks pic.twitter.com/VuJfAsoSYH — Shira Rubinoff (@Shirastweet) October 24, 2019 Q1: How will CISO’s investments change in 2019? What areas of cybersecurity do they see receiving more funding? Many large and mid-size businesses are recognizing security requires more than just a technology investment. Service organizations bring technology, expertise, and resources to the table in a way that may be a more cost-effective alternative to trying to manage all this internally Lack of resources as a major challenge along with keeping up with advancements in cybersecurity technology by utilizing outside service providers rather than hire, retain, and manage staff For the CISO, this translates to set a big picture of priorities such as maintaining customer trust and keeping the organizations name out of the headlines. In order to accomplish these priorities, there are essential areas where security executives will spend their time, and money in 2019 Develop a culture of security: The culture must go together with policies and best practices. Every single person within the organization has some responsibility for security Security and Risk Management: Governance and resource requirements, security frameworks, data protection, training and awareness, insider threats, third-party security practices as outsourcing increases Cloud Services: Cloud strategy, proper selection of services and deployment models. Scalable and | Threat | |||
| 2019-11-13 14:00:00 | The future job market for cybersecurity professionals (lien direct) | If you work in IT – and even if you don’t – you’re probably aware of the huge shortage of cybersecurity professionals. Most companies are desperate for analysts trained to protect their valuable data from theft. On the surface, then, the future of the job market for cybersecurity seems bright. Look a little deeper, though, and you’ll see that this headline hides a lot of complexity. At the moment, there are very few educational programs that are designed to give cybersecurity pros the skills they need to succeed in the industry. And then there is the fact that ‘cybersecurity’ is not one job, but many. In reality, though the job market is full of unfilled positions, many of these require specific skills that jobseekers only rarely have. The shortage of cybersecurity professionals First of all, let's take a closer look at the apparent shortage of cybersecurity professionals. The Bureau of Labor Statistics claims, for instance, that the rate of growth for jobs in information security is projected at 37% from 2012–2022, and that there are currently 2.2 million unfilled cybersecurity roles. These numbers are not actually that helpful, however. Cybersecurity is a huge, diverse, and relatively new industry, and statistical agencies typically don't understand it very well. As a result, it's very difficult to find out how many of these unfilled positions relate to IoT solutions, for instance, or how many require training in forensics. Unfortunately, this lack of understanding is also a feature of the educational programs that are designed to churn out IT professionals. Despite the importance of security for all aspects of systems development and maintenance, cybersecurity is still not taught to students studying relevant and parallel subjects. This has started to change, but very slowly. It's been almost 20 years now since the NSA launched the National Centers of Academic Excellence in Information program, but only now are we seeing a rise in the number of college-level cybersecurity majors. Diversity and segmentation When it comes to the immediate future of the jobs market for cybersecurity professionals, there are two key principles to keep in mind. One is that the market is likely to become even more diverse over the coming years. The second is that, as systems grow ever more complex, there will be an increased segregation of roles even between employees who sit (nominally) within a 'security' team. These trends will likely have two effects on the job market. The first is that employees seeking cybersecurity roles are going to need to be trained in more depth (and for longer) than has been customary in the industry. This extra training is likely to be delivered through on-the-job training programs, however, rather that postgraduate programs, simply due to the specificity of the systems that cybersecurity pros now have to work with. The second outcome of these trends is that cybersecurity pros who are already in the industry will need to continuously develop their skills in order to stay up to date with the latest systems and threats. This requirement can be difficult for established professionals to achieve, particularly given existing workloads in the industry, but will be critical. As Diana Burley, a professor at George Washington University, | Threat Guideline | |||
| 2019-11-12 14:00:00 | Can Google now guess your password in under 4 minutes? (lien direct) | In a recent story that appeared on multiple news sites, as well as the Google AI Blog, it was announced that Google has achieved “Quantum Supremacy” with its 54-Qubit processor, named “Sycamore”. This is a monumental leap forward in computing capabilities. (Yes, I had to resist calling it a quantum leap forward, because that does not nearly sum up this accomplishment). This is huge! The question exactly is, how huge? What exactly do you know about quantum computing? After watching this video, produced by IBM and WIRED, I realized that I know about as much as a 15-year old child. Sad, but true. My knowledge of quantum supremacy is equally lacking. Google is asserting that this quantum chip can solve a computational task in 200 seconds, whereas, it would take a classical computer 10,000 years. There are two amazing thoughts being proposed here, and a third not-so-amazing ponderance. First, trying to understand the reality of 10,000 years is almost beyond human comprehension. The humans of Stonehenge existed 5,000 years ago. The humans of 10,000 years ago were just exiting the Stone Age. Imagine those humans who roamed the Earth 10,000 years ago trying to solve a riddle, and that riddle only gets solved today. 10,000 years is an amazing temporal, as well as intellectual distance. Second, did you realize that the computer on which you are reading this article is now a “classical” computer? If this was an aptitude test, the answer to the analogy section would be: Your computer is to Mozart as the Google computer is to the latest Rap artist. Third, what does this all mean to the average person? Let’s consider password strength. Does this new super-computing power mean that there is a computer that can crack your extremely complex password in under 4 minutes? As I have stated in previous posts, if you are still using a password governed by rules that were devised in 1985, (minimum of 8-characters, upper-case, lower-case, numbers, special characters) you might as well be living in the stone age. Even a classical computer is capable of cracking an 8-character password in less than a few minutes. Now, however, even a password such as Gr8tpassword is trivial for most home machines to crack. Fortunately, as Doctors Gershon and Girvin mention in the video, the ability of the quantum computer to crack passwords is still many years away, as is its ability to break the classical encryption algorithms. Regardless of that, you can take action right now by doing these simple steps to make sure that your password is secure enough to withstand the quantum apocalypse: Get a password manager Use multi-factor authentication wherever possible. Wishing you the best in password supremacy. | Guideline | |||
| 2019-11-11 14:00:00 | AT&T Cybersecurity Insights™ Report: Security at the Speed of 5G (lien direct) |
While some enterprises appear to be getting an early jump on the security implications of 5G, many are struggling with the implications to the business and the changing security model. This is based on a survey AT&T Cybersecurity conducted with 451 Research of 704 cybersecurity professionals in North America, India, Australia and UK in August - September 2019. Participating organizations spanned 13 industry verticals and each had more than 500 employees.
Here are excerpts from those surveyed in the AT&T Cybersecurity Insights on their progress in making security changes required by 5G:
Timeframe to implement security changes
 5G is more than an increase in speed – it’s not a “faster 4G". It provides new features such as network slicing, which allows for isolated domains for traffic. 5G service providers can assign slices to users with customizable quality of service and bandwidth.
Sporting innovative built-in security measures, 5G can allow for stronger over-the-air encryption, subscriber identity protection and reduced risk of eavesdropping.
At AT&T, we believe that 5G will encourage a shared security model akin to the public cloud. The beauty of this is it shifts some security functions to the 5G service provider, freeing up enterprises from some concerns. The anticipated shared security model of 5G does require security pros to think differently, which will take time. However, in the end the shifting of some security functions to the 5G service provider may provide great benefits for enterprises.
With the large number of devices associated with 5G, authentication and identity need to be considered in the scope of security, similar to the public cloud. The 5G service provider can help confirm device identity as well, because the network will know a device’s physical location. In a way, the 5G service provider uses the network itself as a security tool.
Introducing 5G networking impacts many technical areas, but also provides an opportunity and motivation to modernize security approaches. Software Defined Network (SDN) and virtualization technologies should be considered by enterprises preparing for 5G due to its sheer scale. In parallel, security should be virtualized and automated.
From the survey we learned the top security concerns cited were due to the increased attack surface. Have a look at what companies had to say:
Top 3 security concerns
5G is more than an increase in speed – it’s not a “faster 4G". It provides new features such as network slicing, which allows for isolated domains for traffic. 5G service providers can assign slices to users with customizable quality of service and bandwidth.
Sporting innovative built-in security measures, 5G can allow for stronger over-the-air encryption, subscriber identity protection and reduced risk of eavesdropping.
At AT&T, we believe that 5G will encourage a shared security model akin to the public cloud. The beauty of this is it shifts some security functions to the 5G service provider, freeing up enterprises from some concerns. The anticipated shared security model of 5G does require security pros to think differently, which will take time. However, in the end the shifting of some security functions to the 5G service provider may provide great benefits for enterprises.
With the large number of devices associated with 5G, authentication and identity need to be considered in the scope of security, similar to the public cloud. The 5G service provider can help confirm device identity as well, because the network will know a device’s physical location. In a way, the 5G service provider uses the network itself as a security tool.
Introducing 5G networking impacts many technical areas, but also provides an opportunity and motivation to modernize security approaches. Software Defined Network (SDN) and virtualization technologies should be considered by enterprises preparing for 5G due to its sheer scale. In parallel, security should be virtualized and automated.
From the survey we learned the top security concerns cited were due to the increased attack surface. Have a look at what companies had to say:
Top 3 security concerns
 Conclusion
5G has the potential to bring significantly more devices onto the network, expanding the attack surfaces and increasing the possibility of new threats. Security organizations relying on manual security approaches likely will have a hard time keeping up. Security that is dynamic and automated will be able to quickly and effectively address the new security threats of 5G networks, and virtualization can help provide flexibility to respond to unknown future threats.
The research in this report reveals that organizations should do more to prepare their cybersecurity practices for 5G. Preparations that should be made include security virtualization, automation, and SDN, enhanced measures for identity and authentication, and planning for a shared security model. Be proactive and improve your security posture now, while 5G is still in its early stages of deployment and adoption.
Read the whole report.
Conclusion
5G has the potential to bring significantly more devices onto the network, expanding the attack surfaces and increasing the possibility of new threats. Security organizations relying on manual security approaches likely will have a hard time keeping up. Security that is dynamic and automated will be able to quickly and effectively address the new security threats of 5G networks, and virtualization can help provide flexibility to respond to unknown future threats.
The research in this report reveals that organizations should do more to prepare their cybersecurity practices for 5G. Preparations that should be made include security virtualization, automation, and SDN, enhanced measures for identity and authentication, and planning for a shared security model. Be proactive and improve your security posture now, while 5G is still in its early stages of deployment and adoption.
Read the whole report.
|
||||
| 2019-10-31 13:00:00 | Data breach: how to prevent it (lien direct) | We are living in the era of the digital economy where companies are collecting and storing lots of valuable customer data on a daily basis. As it has turned out, data is an important input in the competitiveness, growth, and revenue generation for any company across industries. But every valuable resource has its vulnerabilities, and data is not left out in this unfortunate fact. A notable vulnerability of sensitive data that has left many IT departments scratching their heads is data breaching. What does “Data Breach” mean? When unauthorized people gain access to confidential data, either by stealing it from a company database or through leakage from an insider, that action is known as a data breach. How is data stolen? Well, hackers have mastered the art of infiltrating data security systems for both small and big businesses and copying sensitive data, often without being noticed or traced. In other cases, staff members maliciously or accidentally leak important information to data spies. Think of a case where a staff member leaves their unlocked computer or an unencrypted external hard drive at home or at a public place, and then a malicious person copies data from the device. That is an accidental data breach. The device can also be stolen. Common data breach methods As sophisticated as data thieves try to be, they aren’t too creative with their methods. Experienced data security experts are sometimes able to track them down by establishing the vulnerable areas through which they entered into the system. In most cases, malicious actors take advantage of failed software updates and reckless end-user practices to phish data. Here are more possible data breach methods: 1. Fabricated or stolen credentials If your company uses weak credentials to establish the identity of staff members, hackers can easily fabricate those credentials and enter your database unsuspected. Think of a case where a user’s username is his email and his initials or date of birth his password; a data thief can easily guess such login credentials. Also, hackers can steal user credentials from their PC. 2. BYOD Bring your own devices (BYOD) has its perks, e.g. increasing employee efficiency, but it is now growing to become a serious workplace data threat. Most of these employee devices aren’t encrypted, and some even have malware-laden apps installed. Any important files and emails in such a device can easily be retrieved by a hacker. This is highly risky for recruitment agencies, especially when they outsource work to employees overseas. 3. Card fraud There have been cases of data thieves gaining access to ATM machines and gas pumps and attaching spying malware that copies credit card data from anyone who swipes his/her card in the machine. And because many people recycle pins and passwords, the malware uses the stolen credit card information to guess usernames and passwords and later use them to access company and private employee emails. How to prevent data breach 1. Invest in strong cybersecurity Recent cases of a data breach show that businesses can no longer rely on firewalls, antivirus software, and intrusion detection software to protect their data from a possible data breaches. It is important to install multi-layered cybersecurity systems that do not only thwart possible infiltration attempts but also identify possible vulnerabilities before hackers do. 2. Remote data backup If your company has remote employees, it is important that you invest in a strong remote data backup system. It is time to get rid of backup tapes as they can easily be lost, stolen, or mishandled before they reach the main office. A good backup system should enable you to backup data a | Data Breach Malware Vulnerability | |||
| 2019-10-30 13:00:00 | Physical threats to Cybersecurity that you must address (lien direct) |
 Photo by Nahel Abdul Hadi on Unsplash
Over 90% of data breach is attributed to human error costing a company anywhere from $1.25 million to $8.19 million. Tackling cybersecurity does not only entail non-physical risks, but also includes an assessment of physical threats such as human, internal, and external hazards. Only then can an appropriate and effective security plan to dissuade hackers and thieves be devised.
Internal and External Risks
Internal dangers may include fire or unstable power supply. Another risk is humidity which can cause the appearance of mold that will damage data and equipment. Mold remediation and regular maintenance of the heating, ventilation, and air-conditioning (HVAC) system are necessary to ensure that equipment is stored properly.
While lightning, flood, and earthquakes are difficult to predict, preparing a comprehensive risk assessment is the first step. A detailed plan on what to do if disaster strikes should be done including personnel training. For example, you can install back up power and lightning protection systems to secure computer rooms.
Theft, vandalism, and accidental or intentional errors can be averted by putting a security system. Surveillance cameras and continuous monitoring ensure that there are no intruders on the premises who can physically harm data and infrastructure. Video and event recordings offer valuable data to monitor sensitive locations.
Secure the Premises
Of essence is the protection of your physical security system to keep hackers and intruders away. An assessment of the risks and threats that might arise if the security system is compromised will prove useful.
To illustrate, intruders might take control of the door lock and CCTV systems or turn off video recordings. Should the situation arise, make sure that your company has a backup plan to keep data systems safe or add another layer of security by hosting servers in different parts of the building.
Train Staff and Increase Retention
Staff training is very important to deter possible internal and external threats. Informing them what to do if there are incidents or any physical threat reduces work disruptions. Training also indicates that they are appreciated and will improve retention. According to the 2018 Workforce Learning Report, 94% of employees would stay at a company if it invested in their careers.
Each worker must follow a strict protocol when it comes to data handling and educating employees on cyber literacy helps in preventing data breach. Phishing scams and other attacks may be caused by human error such as downloading a malicious file unintentionally.
A comprehensive cybersecurity plan takes into account internal, external, and human risks. Without a profound understanding of every possible threat, any preventive action to avoid hacks and leaks is useless.
Photo by Nahel Abdul Hadi on Unsplash
Over 90% of data breach is attributed to human error costing a company anywhere from $1.25 million to $8.19 million. Tackling cybersecurity does not only entail non-physical risks, but also includes an assessment of physical threats such as human, internal, and external hazards. Only then can an appropriate and effective security plan to dissuade hackers and thieves be devised.
Internal and External Risks
Internal dangers may include fire or unstable power supply. Another risk is humidity which can cause the appearance of mold that will damage data and equipment. Mold remediation and regular maintenance of the heating, ventilation, and air-conditioning (HVAC) system are necessary to ensure that equipment is stored properly.
While lightning, flood, and earthquakes are difficult to predict, preparing a comprehensive risk assessment is the first step. A detailed plan on what to do if disaster strikes should be done including personnel training. For example, you can install back up power and lightning protection systems to secure computer rooms.
Theft, vandalism, and accidental or intentional errors can be averted by putting a security system. Surveillance cameras and continuous monitoring ensure that there are no intruders on the premises who can physically harm data and infrastructure. Video and event recordings offer valuable data to monitor sensitive locations.
Secure the Premises
Of essence is the protection of your physical security system to keep hackers and intruders away. An assessment of the risks and threats that might arise if the security system is compromised will prove useful.
To illustrate, intruders might take control of the door lock and CCTV systems or turn off video recordings. Should the situation arise, make sure that your company has a backup plan to keep data systems safe or add another layer of security by hosting servers in different parts of the building.
Train Staff and Increase Retention
Staff training is very important to deter possible internal and external threats. Informing them what to do if there are incidents or any physical threat reduces work disruptions. Training also indicates that they are appreciated and will improve retention. According to the 2018 Workforce Learning Report, 94% of employees would stay at a company if it invested in their careers.
Each worker must follow a strict protocol when it comes to data handling and educating employees on cyber literacy helps in preventing data breach. Phishing scams and other attacks may be caused by human error such as downloading a malicious file unintentionally.
A comprehensive cybersecurity plan takes into account internal, external, and human risks. Without a profound understanding of every possible threat, any preventive action to avoid hacks and leaks is useless.
|
Threat | |||
| 2019-10-29 13:00:00 | Was the largest breach in history a misconfiguration problem? (lien direct) |
Earlier this week, I heard a fascinating interview with the former Chief Information Officer of Equifax, Graeme Payne. If you are unfamiliar with Graeme, he was the scapegoat for the Equifax breach; described in Congressional testimony as “the human error” that caused the breach. Graeme, however, is a true gentleman who is very gracious about his situation. He explained that the servers that were breached were “under his watch”, so it makes sense that he was the person who was ultimately held responsible for the breach.
In Graeme’s recently published a book, The New Era of Cybersecurity Breaches, Graeme describes the events of the Equifax breach and offers practical steps to secure a company from the same fate that was suffered by Equifax. The only reason I have not yet read the book is because I did not know it existed. Now, it is on my wish list, and, if the description lives up to the book contents, I anticipate an excellent read!
One item that struck me as peculiar during Graeme’s interview was that he stated, contrary to all the reports about the breach, that the breached server was patched against the Apache Struts. To be clear, all of the news reports indicated that Equifax received notice of the vulnerability, the available patch, yet did nothing to prevent it.
I asked the following question: Didn’t you scan the servers after the patches were applied? (It is excellent that BrightTalk offers interactive webcasts like this.) Graeme responded that they scanned the servers for vulnerabilities, and the patch was reported as successfully applied to the server. How is that possible?
A further discussion ensued, in which the importance of authenticated versus unauthenticated scans was mentioned. It even drifted into the idea that a company should use two different scanners! We are not all the size of an Equifax corporation. Running two scanners is simply unmanageable for many medium sized enterprises.
I posted a follow-up question: How did the vendor of the vulnerability scanner respond once the breach occurred. Unfortunately, Graeme was not at liberty to discuss that. (If you are unfamiliar with the legal system, it probably means that the terms of his dismissal are confidential, and he cannot discuss various topics, such as any impending action against a vendor.)
Whatever the vendor’s response, it doesn’t matter. What matters is that the largest breach in history (to date), may not have been the result of human error or negligence. It may have been just another case of a misconfiguration problem, this time, with a vulnerability scanner.
Given the recent breaches that have involved cloud misconfigurations, it is important to remember that these problems can still exist within the cozy confines of an organization.
Graeme seems to be doing fine in his new existence, not as a scapegoat, but as a Phoenix. I empathize with how he was treated, and I am confident that I speak for all the security community by saying, we wish him well.
|
Vulnerability | Equifax | ||
| 2019-10-28 13:00:00 | Lessons learned conducting an information security risk assessment (lien direct) |
In an age where businesses are relying more than ever on the rapid advancements in technology to drive innovation, strategy, growth and competitive advantage, it is clear the prevalence of technology is not slowing down. But the increase in new devices and systems that utilize connectivity, as well as the transition to the network of devices and systems that were traditionally air-gapped, brings with it an increased cybersecurity risk.
Organizations large and small are attempting to defend against a constant barrage of potentially damaging cybersecurity attacks and struggling to keep up. Increasingly, they are finding that the best approach is taking a proactive, risk-based approach. By repeatedly conducting risk assessments, a holistic understanding of the organization’s risk landscape can be developed, and gaps that exist between people, processes and technology can be utilized to develop a prioritized roadmap for managing and tracking risk over time. The organizations gain the ability to make informed business decisions and move away from a reactive, whack-a-mole approach to cybersecurity.[endif]---->
 Policies and procedures are the foundation
Strong cybersecurity policies and procedures are the foundation of a robust security program. A risk assessor can glean a significant amount of insight into the maturity of an organization’s cybersecurity program simply by looking at a few key areas of cybersecurity policies and procedures, such as those areas identified in the graphic below. They allow the assessor to gain valuable insight on the culture of cybersecurity within the organization, the reporting structure within the organization, the types of technologies present within the organization, and ultimately allows the assessor to drive discovery of information efficiently. This quick and efficient information discovery is especially important for external assessors or those that don’t already have an intimate understanding of the organization.
Policies and procedures are the foundation
Strong cybersecurity policies and procedures are the foundation of a robust security program. A risk assessor can glean a significant amount of insight into the maturity of an organization’s cybersecurity program simply by looking at a few key areas of cybersecurity policies and procedures, such as those areas identified in the graphic below. They allow the assessor to gain valuable insight on the culture of cybersecurity within the organization, the reporting structure within the organization, the types of technologies present within the organization, and ultimately allows the assessor to drive discovery of information efficiently. This quick and efficient information discovery is especially important for external assessors or those that don’t already have an intimate understanding of the organization.
 Documentation is not implementation
Having a strong cybersecurity posture on paper does not mean much if it is not implemented. It’s why conducting interviews of personnel is so important in a risk assessment and why the phrase “Trust but verify” is often half-facetiously repeated by cybersecurity professionals.
When seeking to verify through conducting interviews, it’s tempting to simply go down a list of specific and tailored questions, likely from a framework or compliance standard. Questions like “Does your organization implement a cybersecurity training and awareness training program?”, are to the point, brief, and answer the question asked by the assessment framework, but are not the best way to conduct interviews. Risk assessments are not audits and getting a yes/no answer to a question is not nearly as valuable as taking the time to develop a comprehensive understanding. By having a guided cybersecurity conversation and not simply going through a list of questions, an assessor is able to glean more information on an organization’s risk and develop more valuable findings and recommendations.
Start broad and go narrow
When conducting interviews, start at a ten-thousand-foot level of the topic being discussed, then use the framework as a general guide to steer the conversation and narrow down on specifics. As seen in the below example, the risk assessor should first ask open-ended questions that allow the interviewee a chance to explain the topic in-depth. This allows for a less restrictive and narrow-minded conversation and gives a potential view into how the topic at hand fits into the entire business.
Documentation is not implementation
Having a strong cybersecurity posture on paper does not mean much if it is not implemented. It’s why conducting interviews of personnel is so important in a risk assessment and why the phrase “Trust but verify” is often half-facetiously repeated by cybersecurity professionals.
When seeking to verify through conducting interviews, it’s tempting to simply go down a list of specific and tailored questions, likely from a framework or compliance standard. Questions like “Does your organization implement a cybersecurity training and awareness training program?”, are to the point, brief, and answer the question asked by the assessment framework, but are not the best way to conduct interviews. Risk assessments are not audits and getting a yes/no answer to a question is not nearly as valuable as taking the time to develop a comprehensive understanding. By having a guided cybersecurity conversation and not simply going through a list of questions, an assessor is able to glean more information on an organization’s risk and develop more valuable findings and recommendations.
Start broad and go narrow
When conducting interviews, start at a ten-thousand-foot level of the topic being discussed, then use the framework as a general guide to steer the conversation and narrow down on specifics. As seen in the below example, the risk assessor should first ask open-ended questions that allow the interviewee a chance to explain the topic in-depth. This allows for a less restrictive and narrow-minded conversation and gives a potential view into how the topic at hand fits into the entire business.
|
Tool | |||
| 2019-10-23 13:00:00 | Data Governance….at the heart of security, privacy, and risk (lien direct) | Security, privacy, and risk does not have to be scary… but with GDPR, CCPA, and organizations moving to a risk-based approach to security rather than focusing on only compliance, it has become a daunting challenge. What is typically at the heart of organizations? Data and information. The common denominator that makes security, privacy and risk more effective and dare I say, easier?….data governance. What is data governance? Data governance is the capability within an organization to help provide for and protect for high quality data throughout the lifecycle of that data. This includes data integrity, data security, availability, and consistency. Data governance includes people, processes, and technology that help enable appropriate handling of the data across the organization. Data governance program policies include: Delineating accountability for those responsible for data and data assets Assigning responsibility to appropriate levels in the organization for managing and protecting the data Determining who can take what actions, with what data, under what circumstances, using what methods (see Data Governance Institute for details.) Identifying safeguards to protect data Providing integrity controls to provide for the quality and accuracy of data How does data governance help with privacy management? You have to know what data you have, where it is, how it is used, and who it is shared with to comply with applicable privacy regulations, and have the processes to obtain appropriate consents, access and delete it. Privacy regulations are basically a business case for data governance. Imagine if organizations had already done extensive data mapping exercises prior to GDPR? Imagine if they knew where, why, what, and how about the data prior to GDPR being passed? The transition to GDPR would have been far less painful. How does data governance help cybersecurity? In order to protect against threats, organizations need to know what data to protect and how to help keep it protected.. Information protection is at the core of security, but how can you protect it if you do not know what data you have, where your data is, how it is used, who it is shared with (and how it is shared)? Businesses can no longer have perimeter protections in place and call it a day….the perimeter has expanded to suppliers, cloud vendors, partners, and so on. So managing your data in a structured, responsible, and law-abiding way will make it more efficient for security professionals to protect it. How does data governance help an organization manage information risk? You need to know the most sensitive and critical data to your organization – your most valuable information - so that you can allocate more resources to protecting that data. No organization will be 100% secure and very few organizations have unlimited resources – people and financial – to implement, operate, and improve cybersecurity measures. Therefore, businesses must take a risk-based approach and focus on the most sensitive data assets. Times are changing. Is it easy to design and implement a data governance program? No, or organizations would have them in place today. However, given the privacy regulations, the evolving threat landscape, the age of digitization, and the expanding organizational boundaries, data governance is no longer a choice for organizations that need quality data, protected from cybercriminals, and in compliance with data protection laws. | Threat | |||
| 2019-10-21 13:00:00 | Reviewing best practices for IT asset management in the cloud (lien direct) |
 It used to be that businesses needing their own large computer networks had to do everything themselves. They had to buy all of their servers, all of their networking appliances. They needed the physical space on premises for all of their datacenters, the HVAC people to keep everything cool, and the massive electricity bills to keep all of that going.
But in the past several years, the growth of cloud services has been exponential. It’s great for the enterprise because depending on a business’s specific needs, they can either have everything but their local area network on the cloud, or they can have some hybrid of their own on premises network and a cloud provider or two, fully integrated. Either way, they can put at least some of their networking needs in the hands of a cloud provider such as AWS, Microsoft Azure, or Google Cloud. That can save a company a lot of time, labor, space, and money. Plus, the agility and flexibility that cloud providers offer is great! Do you need to double the data capacity of your network as soon as possible? It’s much quicker and easier to change your cloud provider plan and do some adjustments on your end than it is to double the size of your on prem network. The cloud can be a lifesaver, but your IT people still need to know how to manage their computing assets there, especially when it comes to cybersecurity. Cloud asset management is a special matter, and it’s absolutely vital to understand.
What is cloud asset management?
Your IT assets are the hardware, software, and networking entities that your company has as tools and resources for their objectives. An excellent example of an IT asset is a database. Databases are very important, particularly in the backend of your applications.
With the implementation of cloud networks, these IT assets become cloud assets too. So instead of having your MySQL databases entirely on your on premises servers and data storage, you can have them run from the server and data storage capacity that your cloud provider offers your business.
But making sure your cloud-hosted assets function well and maintain security is its own area of knowledge: cloud asset management. There are challenges involved in cloud asset management which differ from managing assets on your own infrastructure. For instance, developers and administrators often don’t use the security tools that their cloud providers offer them. Also, visibility into your assets can be more difficult in the cloud. You can’t secure what you can’t see!
Cloud asset management best practices
There’s a lot to learn when it comes to cloud asset management. It can seem overwhelming to start. Thankfully, there are some best practices to keep in mind which will provide you with a strong foundation for properly handling the cloud.
Monitor your cloud as thoroughly as possible
As I mentioned, visibility in cloud networks can be a special challenge. There’s also the everyday performance of your network to consider. You won’t be physically inside of your cloud provider’s datacenter, so you’ll need to be able to see as much as possible with monitoring tools. This isn’t all directly security related. You need to make sure that your provider honors your Service Level Agreement. Watch your bandwidth and make sure that it suits your organization’s needs at all times. Make sure all of your cloud assets have excellent availability, as much uptime as possible. You could have thousands of users depending on your cloud at any given second. Monitor thoroughly and constantly to make sure that your cloud is always capable and reliable.
Redundancy and automation are your friends
Redundancy goes a long way when it comes to keeping good uptime and everything working properly. There should be as few single points of failure as possible, preferably no
It used to be that businesses needing their own large computer networks had to do everything themselves. They had to buy all of their servers, all of their networking appliances. They needed the physical space on premises for all of their datacenters, the HVAC people to keep everything cool, and the massive electricity bills to keep all of that going.
But in the past several years, the growth of cloud services has been exponential. It’s great for the enterprise because depending on a business’s specific needs, they can either have everything but their local area network on the cloud, or they can have some hybrid of their own on premises network and a cloud provider or two, fully integrated. Either way, they can put at least some of their networking needs in the hands of a cloud provider such as AWS, Microsoft Azure, or Google Cloud. That can save a company a lot of time, labor, space, and money. Plus, the agility and flexibility that cloud providers offer is great! Do you need to double the data capacity of your network as soon as possible? It’s much quicker and easier to change your cloud provider plan and do some adjustments on your end than it is to double the size of your on prem network. The cloud can be a lifesaver, but your IT people still need to know how to manage their computing assets there, especially when it comes to cybersecurity. Cloud asset management is a special matter, and it’s absolutely vital to understand.
What is cloud asset management?
Your IT assets are the hardware, software, and networking entities that your company has as tools and resources for their objectives. An excellent example of an IT asset is a database. Databases are very important, particularly in the backend of your applications.
With the implementation of cloud networks, these IT assets become cloud assets too. So instead of having your MySQL databases entirely on your on premises servers and data storage, you can have them run from the server and data storage capacity that your cloud provider offers your business.
But making sure your cloud-hosted assets function well and maintain security is its own area of knowledge: cloud asset management. There are challenges involved in cloud asset management which differ from managing assets on your own infrastructure. For instance, developers and administrators often don’t use the security tools that their cloud providers offer them. Also, visibility into your assets can be more difficult in the cloud. You can’t secure what you can’t see!
Cloud asset management best practices
There’s a lot to learn when it comes to cloud asset management. It can seem overwhelming to start. Thankfully, there are some best practices to keep in mind which will provide you with a strong foundation for properly handling the cloud.
Monitor your cloud as thoroughly as possible
As I mentioned, visibility in cloud networks can be a special challenge. There’s also the everyday performance of your network to consider. You won’t be physically inside of your cloud provider’s datacenter, so you’ll need to be able to see as much as possible with monitoring tools. This isn’t all directly security related. You need to make sure that your provider honors your Service Level Agreement. Watch your bandwidth and make sure that it suits your organization’s needs at all times. Make sure all of your cloud assets have excellent availability, as much uptime as possible. You could have thousands of users depending on your cloud at any given second. Monitor thoroughly and constantly to make sure that your cloud is always capable and reliable.
Redundancy and automation are your friends
Redundancy goes a long way when it comes to keeping good uptime and everything working properly. There should be as few single points of failure as possible, preferably no |
Tool Guideline | ★★★★★ | ||
| 2019-10-16 13:00:00 | Are smart homes really safe from hackers? (lien direct) |
 Image Source: Pexels
There are a number of smart devices becoming commonplace in homes around the world, leading us closer and closer to the reality of smart homes, or houses that depend primarily on interconnected smart tech. Heating, lighting, and common appliances like doorbells, alarms, and entertainment devices are now increasingly being designed to operate on the internet of things (IoT).
However, some experts have expressed valid security concerns regarding smart technology, believing that these systems are specifically vulnerable to cybercriminals. Some may argue that implementing smart systems isn’t worth the time it takes unless the security bugs are worked out.
This points to the fact that smart home cybersecurity is often overlooked. If you’re thinking about using a variety of smart home devices in your home and have never thought about this, now may be the time. Below are some things to consider that will help you make a more informed choice regarding smart tech in your home.
The risks of IoT
The truth is that IoT-based devices are growing in popularity at a faster rate than their security measures can keep up with. This could have some extremely serious consequences for those who have filled everyday lives with multiple interconnected smart devices. While these things may be convenient for a home, IoT technology itself comes with a cost.
As Javvad Malik suggested in his article “IoT: Usability Dream or Privacy Nightmare?”, imagine what might happen if a hacker got control of your smart thermostat. They could hold your temperature for ransom unless you paid them in bitcoin, Malik argued. This is a real concern with the growing popularity of IoT smart homes because, frankly, they’re not designed to defend themselves against cyberattacks.
The risks of IoT systems have been well documented, specifically by the Open Web Application Security (OWASP) Project. Each year they cover concerns about the IoT in their “IoT project.” In their most recent update, they included the following things with the most major concerns in the implementation of IoT:
Insecure network services.
Lack of secure update mechanisms.
Insecure data transfer and storage.
Insufficient privacy protection.
Lack of device management.
Lack of secure default settings.
The importance and trustworthiness of testing
Smart devices can be tested for cybersecurity, but these tests aren’t foolproof. A common type of test is penetration (or “pen”) testing, and is used to check how easy it is to hack into a network. In general, they’re very helpful. But for IoT, they are harder to perform successfully. This was best summed up in a rhetorical example put forth by Ryan Francis, a contributor to Network World,
Penetration testing was much like taking a battering ram to the door of the fortress. Keep pounding away and maybe find a secret backdoor to enter through
Image Source: Pexels
There are a number of smart devices becoming commonplace in homes around the world, leading us closer and closer to the reality of smart homes, or houses that depend primarily on interconnected smart tech. Heating, lighting, and common appliances like doorbells, alarms, and entertainment devices are now increasingly being designed to operate on the internet of things (IoT).
However, some experts have expressed valid security concerns regarding smart technology, believing that these systems are specifically vulnerable to cybercriminals. Some may argue that implementing smart systems isn’t worth the time it takes unless the security bugs are worked out.
This points to the fact that smart home cybersecurity is often overlooked. If you’re thinking about using a variety of smart home devices in your home and have never thought about this, now may be the time. Below are some things to consider that will help you make a more informed choice regarding smart tech in your home.
The risks of IoT
The truth is that IoT-based devices are growing in popularity at a faster rate than their security measures can keep up with. This could have some extremely serious consequences for those who have filled everyday lives with multiple interconnected smart devices. While these things may be convenient for a home, IoT technology itself comes with a cost.
As Javvad Malik suggested in his article “IoT: Usability Dream or Privacy Nightmare?”, imagine what might happen if a hacker got control of your smart thermostat. They could hold your temperature for ransom unless you paid them in bitcoin, Malik argued. This is a real concern with the growing popularity of IoT smart homes because, frankly, they’re not designed to defend themselves against cyberattacks.
The risks of IoT systems have been well documented, specifically by the Open Web Application Security (OWASP) Project. Each year they cover concerns about the IoT in their “IoT project.” In their most recent update, they included the following things with the most major concerns in the implementation of IoT:
Insecure network services.
Lack of secure update mechanisms.
Insecure data transfer and storage.
Insufficient privacy protection.
Lack of device management.
Lack of secure default settings.
The importance and trustworthiness of testing
Smart devices can be tested for cybersecurity, but these tests aren’t foolproof. A common type of test is penetration (or “pen”) testing, and is used to check how easy it is to hack into a network. In general, they’re very helpful. But for IoT, they are harder to perform successfully. This was best summed up in a rhetorical example put forth by Ryan Francis, a contributor to Network World,
Penetration testing was much like taking a battering ram to the door of the fortress. Keep pounding away and maybe find a secret backdoor to enter through |
Hack Guideline | |||
| 2019-10-10 13:00:00 | Love your enemies before you destroy them (lien direct) |
 Photo by Volkan Olmez on Unsplash
“In the moment when I truly understand my enemy, understand him well enough to defeat him, then in that very moment I also love him. I think it’s impossible to really understand somebody, what they want, what they believe, and not love them the way they love themselves. And then, in that very moment when I love them.... I destroy them.”
Orson Scott Card, Enders Game
The cutting edge of cybersecurity is moving away from a reactive defense. Instead of analysts waiting for a threat to happen, they are proactively searching out attackers in their environment. Attackers are dynamic. They are always changing and improving their capabilities, which means that defenders needs to lean in and adapt even faster to keep up. Proactive defense is about predicting, understanding, and preventing as many moves as possible that an attacker could make against you. You have to stay a step ahead of the enemy and lure them into a trap of your own.
In the cybersecurity space, this is why we red team. A group of red teamers takes on the characteristics of an adversary to challenge an organization to improve its defenses. They eat, sleep, and breathe adversary behavior ...legally.
Red teaming is a well-regarded and crucial part of defense in cybersecurity. It has its place and it makes an impact, but it is solely targeted at improving defenses. What if we took this idea of understanding the enemy one step further, outside of defense?
Anonymous, WIkiLeaks, and nation-state threat actors use open-source intelligence (OSINT) and espionage campaigns to drill down into the lives of targeted individuals. They use hacker techniques, tactics, and procedures to aggressively target individuals as a means of control. Once they have access to this information, they can do any number of bad things with it, from sabotage to assassination. But what if we took these adversary methods of OSINT and used them for the greater good? Must these techniques be used solely for evil?
As a society, we have gone from outright shunning of hacker culture, stereotyping hackers as hoodie-wearing teenagers in the basement, to the beginnings of acceptance and appreciation of hackers. We have started to recognize that many hackers are curious individuals that want to try something new. They are the puzzle solvers of the Internet age. Moreover, they are necessary for the cyber-resilience of the technology industry. Much like being a germaphobe puts you at more risk of becoming ill, not appreciating and adopting a hacker mindset results in weakly secured systems. As part of the revolution of acceptance ar
Photo by Volkan Olmez on Unsplash
“In the moment when I truly understand my enemy, understand him well enough to defeat him, then in that very moment I also love him. I think it’s impossible to really understand somebody, what they want, what they believe, and not love them the way they love themselves. And then, in that very moment when I love them.... I destroy them.”
Orson Scott Card, Enders Game
The cutting edge of cybersecurity is moving away from a reactive defense. Instead of analysts waiting for a threat to happen, they are proactively searching out attackers in their environment. Attackers are dynamic. They are always changing and improving their capabilities, which means that defenders needs to lean in and adapt even faster to keep up. Proactive defense is about predicting, understanding, and preventing as many moves as possible that an attacker could make against you. You have to stay a step ahead of the enemy and lure them into a trap of your own.
In the cybersecurity space, this is why we red team. A group of red teamers takes on the characteristics of an adversary to challenge an organization to improve its defenses. They eat, sleep, and breathe adversary behavior ...legally.
Red teaming is a well-regarded and crucial part of defense in cybersecurity. It has its place and it makes an impact, but it is solely targeted at improving defenses. What if we took this idea of understanding the enemy one step further, outside of defense?
Anonymous, WIkiLeaks, and nation-state threat actors use open-source intelligence (OSINT) and espionage campaigns to drill down into the lives of targeted individuals. They use hacker techniques, tactics, and procedures to aggressively target individuals as a means of control. Once they have access to this information, they can do any number of bad things with it, from sabotage to assassination. But what if we took these adversary methods of OSINT and used them for the greater good? Must these techniques be used solely for evil?
As a society, we have gone from outright shunning of hacker culture, stereotyping hackers as hoodie-wearing teenagers in the basement, to the beginnings of acceptance and appreciation of hackers. We have started to recognize that many hackers are curious individuals that want to try something new. They are the puzzle solvers of the Internet age. Moreover, they are necessary for the cyber-resilience of the technology industry. Much like being a germaphobe puts you at more risk of becoming ill, not appreciating and adopting a hacker mindset results in weakly secured systems. As part of the revolution of acceptance ar |
Threat | |||
| 2019-10-09 13:00:00 | What\'s new in OTX (lien direct) |
Alien Labs and the Open Threat Exchange (OTX) development team have been hard at work, continuing our development of the OTX platform. As some of you may have noticed, we’ve added some exciting new features and capabilities this last year to improve understanding within the OTX community of evolving and emerging threats.
Malware analysis to benefit all
The biggest (and latest) new feature within OTX is the ability to submit samples to be analyzed in our backend Alien Labs systems. (Alien Labs is the threat intelligence unit of AT&T Cybersecurity.) You can now upload files and URLs for analysis, with access to results within minutes. Submissions can be made through the OTX portal (as shown below) or programmatically through the API.
 From the Submit Sample page, you’ll be able to see all of your submissions with a link to the results. And, if you’re concerned about a sample containing sensitive information, OTX gives you the ability to make your submitted files and URLs private by using the Traffic Light Protocol (TLP).
Pulse creation enhancements
But it doesn’t stop there! You can easily add the resulting indicator to a new pulse with the click of a button. In fact, you can utilize the new “Add to Pulse” button from any indicator details page.
From the Submit Sample page, you’ll be able to see all of your submissions with a link to the results. And, if you’re concerned about a sample containing sensitive information, OTX gives you the ability to make your submitted files and URLs private by using the Traffic Light Protocol (TLP).
Pulse creation enhancements
But it doesn’t stop there! You can easily add the resulting indicator to a new pulse with the click of a button. In fact, you can utilize the new “Add to Pulse” button from any indicator details page.
 And, speaking of pulses, we’ve added to the list of file types that OTX can automatically extract IOCs from, which now includes PCAPs and emails.
And, speaking of pulses, we’ve added to the list of file types that OTX can automatically extract IOCs from, which now includes PCAPs and emails.
 You can also edit multiple indicators at once, making pulse creation even easier.
You can also edit multiple indicators at once, making pulse creation even easier.
 We’ve also made it simpler to add more details to pulses with auto-suggestions for malware family and threat actor. Simply start typing in the associated fields, and OTX will provide a list of suggestions. Additionally, OTX will now identify MITRE ATT&CK IDs from a resource, such as a blog or threat report, and automatically add this information to the pulse.
We’ve also made it simpler to add more details to pulses with auto-suggestions for malware family and threat actor. Simply start typing in the associated fields, and OTX will provide a list of suggestions. Additionally, OTX will now identify MITRE ATT&CK IDs from a resource, such as a blog or threat report, and automatically add this information to the pulse.
 CVSS v3 Severity Scores
We’ve also added support for CVSS v3, so you can now easily reference both CVSS v2 and v3 severity information.
CVSS v3 Severity Scores
We’ve also added support for CVSS v3, so you can now easily reference both CVSS v2 and v3 severity information.
 And more!
We’ve also made improvements to Passive DNS data, as well as added Linux sandbox support for ARM, x86, and x64.
What’s coming next...
We’re currently working on:
Redesign and enhancements to file indicator detail pages
Improved search capabilities for IoCs
Ability to kick-off an endpoint scan from pulse emails
Stay tuned because we have a lot more great stuff coming!
We'd love to hear any feedback or thoughts you might have around how to improve OTX. There's a survey you can fill out, or just drop us an email.
Join OTX today and start taking advantage of all these new capabilities and more -- for FREE!
And more!
We’ve also made improvements to Passive DNS data, as well as added Linux sandbox support for ARM, x86, and x64.
What’s coming next...
We’re currently working on:
Redesign and enhancements to file indicator detail pages
Improved search capabilities for IoCs
Ability to kick-off an endpoint scan from pulse emails
Stay tuned because we have a lot more great stuff coming!
We'd love to hear any feedback or thoughts you might have around how to improve OTX. There's a survey you can fill out, or just drop us an email.
Join OTX today and start taking advantage of all these new capabilities and more -- for FREE!
|
Malware Threat | |||
| 2019-10-08 13:00:00 | Workplace design tips to help deter hackers (lien direct) |
 Photo by ROOM on Unsplash
31 percent of companies in the USA have been subjected to cyber attacks and 43 percent of those attacks were aimed at small businesses. When workplaces are designed with cybersecurity in mind, the odds of breaches will decrease. This is good news, because some breaches have the capacity to put companies out of business. These workplace design tips will make it simpler to keep hackers out of workplace networks. With a little smart planning and implementation, a workplace that is designed to provide top-notch data security can be an attractive and functional place.
Invest in ultra-modern hardware
A lot of modern hardware, such as brand-new mainframes, have cybersecurity software baked right in. If hardware at your business is out-of-date, it may be time to make a capital investment in new hardware that is inherently more secure. This doesn’t mean that you’ll be able to let your guard down. You’ll still need centralized security monitoring of cloud devices and networks, onsite and in remote places, which assist you with finding threats. As a bonus, new hardware, from PCs to printers and beyond, improve the look of a workplace and send a message of success.
Avoid open plan office design
To ensure the highest level of cybersecurity, avoid an open plan office, in favor of private offices or offices with cubicle walls. Open plan offices create data security risks, because a lot of people have access to unlocked computers and papers which might contain sensitive information about computer systems. To make a VIP's private office feel warm and cozy, consider adding a fireplace, which will make guests relax while adding a touch of luxury.
For a cubicle-based workplace, put a few bean bag chairs in an empty corner. The corner will become a comfortable lounge area for rest breaks or collaboration, which is a safe distance away from computers and papers. Mixing modern and old-fashioned design elements is a good way to add eclecticism, without sacrificing cybersecurity. Non-smart design elements, such as fireplaces and retro bean bag chairs, don’t need to be monitored for data security purposes and they help to create a positive company culture.
Create a safe room for sensitive conversations
When designing a workplace with data security in mind, there should be a room that is set aside for private business conversations.
Photo by ROOM on Unsplash
31 percent of companies in the USA have been subjected to cyber attacks and 43 percent of those attacks were aimed at small businesses. When workplaces are designed with cybersecurity in mind, the odds of breaches will decrease. This is good news, because some breaches have the capacity to put companies out of business. These workplace design tips will make it simpler to keep hackers out of workplace networks. With a little smart planning and implementation, a workplace that is designed to provide top-notch data security can be an attractive and functional place.
Invest in ultra-modern hardware
A lot of modern hardware, such as brand-new mainframes, have cybersecurity software baked right in. If hardware at your business is out-of-date, it may be time to make a capital investment in new hardware that is inherently more secure. This doesn’t mean that you’ll be able to let your guard down. You’ll still need centralized security monitoring of cloud devices and networks, onsite and in remote places, which assist you with finding threats. As a bonus, new hardware, from PCs to printers and beyond, improve the look of a workplace and send a message of success.
Avoid open plan office design
To ensure the highest level of cybersecurity, avoid an open plan office, in favor of private offices or offices with cubicle walls. Open plan offices create data security risks, because a lot of people have access to unlocked computers and papers which might contain sensitive information about computer systems. To make a VIP's private office feel warm and cozy, consider adding a fireplace, which will make guests relax while adding a touch of luxury.
For a cubicle-based workplace, put a few bean bag chairs in an empty corner. The corner will become a comfortable lounge area for rest breaks or collaboration, which is a safe distance away from computers and papers. Mixing modern and old-fashioned design elements is a good way to add eclecticism, without sacrificing cybersecurity. Non-smart design elements, such as fireplaces and retro bean bag chairs, don’t need to be monitored for data security purposes and they help to create a positive company culture.
Create a safe room for sensitive conversations
When designing a workplace with data security in mind, there should be a room that is set aside for private business conversations. |
||||
| 2019-10-02 13:00:00 | How to avoid becoming a victim of cybercrime: 5 tips (lien direct) |
 Description: Do you want to avoid cybercrime? Online identity theft and fraud, webcam hackers, ransomware cyber-attacks, phishing, and other scams are a threat to all of us. Keep reading to protect your data and privacy and save your files and finances from fraudsters.
How to avoid cybercrime
The cyber definition relates to the field of digital technology, and today is often associated with cybercrime. You might say that it doesn’t matter to you as you’re not a big cheese in the business world. Big mistake - since all individuals save data on their computers that is potentially profitable for scammers.
Unfortunately, plenty of people are reckless when dealing with cybercrime. For example, up to 73% of users reuse passwords in their online accounts. The following tips can protect you from cybercrime.
Cybercrime – types of threats
A definition of cybersecurity is the integrated protection of internet-connected systems – hardware, software, and data from attacks. What are the types of cyber-attacks that lie in our virtual path?
Webcam cybercrime means that scammers can hack web cameras to spy on you when using Trojan horse attacks.
Screenshot managers do cybercrime when they make a snapshot of your PC when you click a doubtful link or download a file from a suspicious source.
Cybercrime occurs when the ad clickers display ads and motivate you to click them, for example, when you are reading gadgets and electronic reviews and let end up with malware instead
DDoS attacks were developed to disrupt business/e-commerce websites to by directing tons of traffic from numerous sources, and disrupt business operations.
There are plenty of other attacks in the modern web world. For example, online identity cybercrime means that a hacker gets unauthorized access to your personal data. It can happen if you provide somebody with private information when communicating with a scammer via email or by the phone. Fraudsters can even deliver you (or themselves) a credit card that you’ve never applied for.
5 tips to stay safe online
Cybercrime is an everyday danger, and sometimes cyber police are unable to help. So, it’s arguably easier to prevent cybercrime than to deal with the consequences. How to achieve that?
Install a current antivirus system and accept updates when getting official notifications/
Never use the same passwords on several websites. Try to complicate them with symbols and numbers. Don’t choose your name or date of birth for a password.
Cyber-attacks today are not a joke, so you should strengthen your security system with a firewall to protect yourself from unwanted traffic.
Pay attention to the web camera LED indicators (they’re red on external devices and blue on laptops).
Be cautious with strangers. Don’t talk to them online and don’t accept offline tech help if you’re not sure it’s credible. A stranger from an unknown company can offer you computer support and then do cybercrime and spy on you remotely.
Description: Do you want to avoid cybercrime? Online identity theft and fraud, webcam hackers, ransomware cyber-attacks, phishing, and other scams are a threat to all of us. Keep reading to protect your data and privacy and save your files and finances from fraudsters.
How to avoid cybercrime
The cyber definition relates to the field of digital technology, and today is often associated with cybercrime. You might say that it doesn’t matter to you as you’re not a big cheese in the business world. Big mistake - since all individuals save data on their computers that is potentially profitable for scammers.
Unfortunately, plenty of people are reckless when dealing with cybercrime. For example, up to 73% of users reuse passwords in their online accounts. The following tips can protect you from cybercrime.
Cybercrime – types of threats
A definition of cybersecurity is the integrated protection of internet-connected systems – hardware, software, and data from attacks. What are the types of cyber-attacks that lie in our virtual path?
Webcam cybercrime means that scammers can hack web cameras to spy on you when using Trojan horse attacks.
Screenshot managers do cybercrime when they make a snapshot of your PC when you click a doubtful link or download a file from a suspicious source.
Cybercrime occurs when the ad clickers display ads and motivate you to click them, for example, when you are reading gadgets and electronic reviews and let end up with malware instead
DDoS attacks were developed to disrupt business/e-commerce websites to by directing tons of traffic from numerous sources, and disrupt business operations.
There are plenty of other attacks in the modern web world. For example, online identity cybercrime means that a hacker gets unauthorized access to your personal data. It can happen if you provide somebody with private information when communicating with a scammer via email or by the phone. Fraudsters can even deliver you (or themselves) a credit card that you’ve never applied for.
5 tips to stay safe online
Cybercrime is an everyday danger, and sometimes cyber police are unable to help. So, it’s arguably easier to prevent cybercrime than to deal with the consequences. How to achieve that?
Install a current antivirus system and accept updates when getting official notifications/
Never use the same passwords on several websites. Try to complicate them with symbols and numbers. Don’t choose your name or date of birth for a password.
Cyber-attacks today are not a joke, so you should strengthen your security system with a firewall to protect yourself from unwanted traffic.
Pay attention to the web camera LED indicators (they’re red on external devices and blue on laptops).
Be cautious with strangers. Don’t talk to them online and don’t accept offline tech help if you’re not sure it’s credible. A stranger from an unknown company can offer you computer support and then do cybercrime and spy on you remotely.
|
Ransomware Malware Hack Threat | |||
| 2019-10-01 13:00:00 | What you need to know about PII security in 2019 (lien direct) |
 As a society we have always relied on personal identifiers, commonly known as personally identifiable information (PII). Defining and protecting PII has recently become much more important as a component of personal privacy now that advances in computing and communications technology, including the internet, has made it easier to collect and process vast amounts of information.
The protection of PII and overall privacy of information are concerns both for individuals whose personal information is at stake and for organizations that may be liable or have their reputations damaged should such PII be inappropriately accessed, used, or disclosed. Without question, 2019 has been an eventful year for organizations across the different industries, with massive data breaches that have had major impacts to organizations as well as consumers. A number of these breaches have exposed PII and heightened the awareness around privacy regulations such as GDPR.
PII data security best practices
Here are some foundational steps to get started with an information protection framework that helps think of the key dimensions associated with protecting PII.
Understand the data: identify and classify it by source, type, sensitivity and criticality to the business.
Understand the threats they are exposed to: due to the constantly changing nature of the threat landscape, a review of the threat exposure should be performed on a regular basis.
Provide that the data’s protection is commensurate with the threat: this means that the controls that composed the Security Framework need to be adapted to each case so the risks are adequately mitigated.
Identify Your PII
Due to the wide range of definitions of what exactly comprises PII, each organization is responsible for determining what defines PII in its jurisdiction and which statutes, industry standards, etc., are in scope for compliance. One of the most important steps in protecting PII involves the identification of PII. The types of information that should be considered PII are well known.
Once the types of information considered PII are understood, there remains the challenge of determining where this information is located and stored. The information generally resides in either structured data sources such as databases, or in unstructured information such as electronic documents, emails and other file types.
Unstructured information poses the greater challenge as it can travel anywhere – from desktop computer to tablet to server to mobile phone. Organizations must determine how to identify which unstructured information contains PII, and how to make their employees, contractors, and partners aware that certain files contain PII.
PII is typically stored in a myriad of locations, both in electronic and hard copy form. Perform a review to identify PII and focus on:
Policies and procedures to protect PII and other private data in any of its forms and storage locations, including the deployment and effectiveness of an organization-wide data classification scheme
Policies and procedures relating to action needed after a breach of PII confidentiality
Training and awareness of employees in the handling and processing of PII and data privacy
Educate and Build Awareness of PII
Organizations should develop comprehensive policies and procedures for handling PII at the organization level, the program or component level, and where appropriate, at the system level.
Well-crafted PII handling policies and procedures are unlikely to succeed if the organization does not involve its information creators in the protection of PII as part of their standard way of doing business.
Awareness and training for end user
As a society we have always relied on personal identifiers, commonly known as personally identifiable information (PII). Defining and protecting PII has recently become much more important as a component of personal privacy now that advances in computing and communications technology, including the internet, has made it easier to collect and process vast amounts of information.
The protection of PII and overall privacy of information are concerns both for individuals whose personal information is at stake and for organizations that may be liable or have their reputations damaged should such PII be inappropriately accessed, used, or disclosed. Without question, 2019 has been an eventful year for organizations across the different industries, with massive data breaches that have had major impacts to organizations as well as consumers. A number of these breaches have exposed PII and heightened the awareness around privacy regulations such as GDPR.
PII data security best practices
Here are some foundational steps to get started with an information protection framework that helps think of the key dimensions associated with protecting PII.
Understand the data: identify and classify it by source, type, sensitivity and criticality to the business.
Understand the threats they are exposed to: due to the constantly changing nature of the threat landscape, a review of the threat exposure should be performed on a regular basis.
Provide that the data’s protection is commensurate with the threat: this means that the controls that composed the Security Framework need to be adapted to each case so the risks are adequately mitigated.
Identify Your PII
Due to the wide range of definitions of what exactly comprises PII, each organization is responsible for determining what defines PII in its jurisdiction and which statutes, industry standards, etc., are in scope for compliance. One of the most important steps in protecting PII involves the identification of PII. The types of information that should be considered PII are well known.
Once the types of information considered PII are understood, there remains the challenge of determining where this information is located and stored. The information generally resides in either structured data sources such as databases, or in unstructured information such as electronic documents, emails and other file types.
Unstructured information poses the greater challenge as it can travel anywhere – from desktop computer to tablet to server to mobile phone. Organizations must determine how to identify which unstructured information contains PII, and how to make their employees, contractors, and partners aware that certain files contain PII.
PII is typically stored in a myriad of locations, both in electronic and hard copy form. Perform a review to identify PII and focus on:
Policies and procedures to protect PII and other private data in any of its forms and storage locations, including the deployment and effectiveness of an organization-wide data classification scheme
Policies and procedures relating to action needed after a breach of PII confidentiality
Training and awareness of employees in the handling and processing of PII and data privacy
Educate and Build Awareness of PII
Organizations should develop comprehensive policies and procedures for handling PII at the organization level, the program or component level, and where appropriate, at the system level.
Well-crafted PII handling policies and procedures are unlikely to succeed if the organization does not involve its information creators in the protection of PII as part of their standard way of doing business.
Awareness and training for end user |
Threat | |||
| 2019-09-30 13:00:00 | GootKit malware bypasses Windows Defender | AT&T ThreatTraq (lien direct) |
 Photo by Christopher Beddies on Unsplash
Every week the AT&T Chief Security Office produces a series called ThreatTraq with helpful information and news commentary for InfoSec practitioners and researchers. I really enjoy them; you can subscribe to the Youtube channel to stay updated. This is a transcript of a recent feature on ThreatTraq. The video features Andy Benavides, Professional - Technology Security, AT&T, Stan Nurilov, Lead Member of Technical Staff, AT&T and Mike Klepper, Principal Architect, AT&T Cybersecurity Services. Mike has written blogs here in the past.
Andy: You can't defend what you can't scan. GootKit malware bypasses user access control (UAC).
Mike: So, Andy, I guess we're going to continue with the malware theme today with your story, right?
Andy: Yes, we're going to be talking about GootKit a little bit. G-O-O-T, Kit - it's kind of hard to say. But for those who don't know, GootKit is a banking Trojan whose goal is to steal your banking credentials, and it does that by recording your screen or by redirecting you to fake banking login pages. That's how it works.
A security researcher by the name of Vitali Kremez found that GootKit actually attacks Windows Defender by adding itself, by adding the directory that the malware lives in. It avoids detection by adding it to the scan exclusion list. So, it basically tells Windows Defender, "Don't scan this directory that my malware's in." And the key to doing that is through the use of the good old fodhelper.exe.
For those who don't know, fodhelper.exe is a Windows 10 management tool. It was found to allow UAC bypass in 2017 by a researcher by the name of Christian B. That's all that's known about him. Essentially, what happens is when an application wants to perform a task, because that requires administrative purposes, it brings up a prompt on your screen and it asks you for that permission. It says, "Hey, I want to do something as Admin." And you say yes or you say no. Bypassing that means that you can run things in the background as Admin without the user knowing. So that's kind of a big problem.
What Christian B. found was that fodhelper.exe actually runs with the auto-elevate attributes set to true, which means it can run itself with a higher privilege on its own when it deems it's necessary. Which means it can do things without bringing up that control prompt, letting the user know that something is happening in the background. What Christian B. was able to figure out was that the fodhelper.exe works by first checking for a few registry keys that strangely enough don't exist by default in Windows 10.
Stan: That's actually kind of normal.
Andy: Is it really?
Stan: Yes. That's how they do a lot of GPO policies later. They like to produce certain registry keys. And if you have them, then whatever, you can apply that setting.
Andy: Okay. So it checks for some registry keys that don't exist by default in Windows 10. When it finds those, then it does other things. What Christian B. was able to figure out is if you create the keys that it's looking for, one of the keys actually lets you dictate it and enter in furth
Photo by Christopher Beddies on Unsplash
Every week the AT&T Chief Security Office produces a series called ThreatTraq with helpful information and news commentary for InfoSec practitioners and researchers. I really enjoy them; you can subscribe to the Youtube channel to stay updated. This is a transcript of a recent feature on ThreatTraq. The video features Andy Benavides, Professional - Technology Security, AT&T, Stan Nurilov, Lead Member of Technical Staff, AT&T and Mike Klepper, Principal Architect, AT&T Cybersecurity Services. Mike has written blogs here in the past.
Andy: You can't defend what you can't scan. GootKit malware bypasses user access control (UAC).
Mike: So, Andy, I guess we're going to continue with the malware theme today with your story, right?
Andy: Yes, we're going to be talking about GootKit a little bit. G-O-O-T, Kit - it's kind of hard to say. But for those who don't know, GootKit is a banking Trojan whose goal is to steal your banking credentials, and it does that by recording your screen or by redirecting you to fake banking login pages. That's how it works.
A security researcher by the name of Vitali Kremez found that GootKit actually attacks Windows Defender by adding itself, by adding the directory that the malware lives in. It avoids detection by adding it to the scan exclusion list. So, it basically tells Windows Defender, "Don't scan this directory that my malware's in." And the key to doing that is through the use of the good old fodhelper.exe.
For those who don't know, fodhelper.exe is a Windows 10 management tool. It was found to allow UAC bypass in 2017 by a researcher by the name of Christian B. That's all that's known about him. Essentially, what happens is when an application wants to perform a task, because that requires administrative purposes, it brings up a prompt on your screen and it asks you for that permission. It says, "Hey, I want to do something as Admin." And you say yes or you say no. Bypassing that means that you can run things in the background as Admin without the user knowing. So that's kind of a big problem.
What Christian B. found was that fodhelper.exe actually runs with the auto-elevate attributes set to true, which means it can run itself with a higher privilege on its own when it deems it's necessary. Which means it can do things without bringing up that control prompt, letting the user know that something is happening in the background. What Christian B. was able to figure out was that the fodhelper.exe works by first checking for a few registry keys that strangely enough don't exist by default in Windows 10.
Stan: That's actually kind of normal.
Andy: Is it really?
Stan: Yes. That's how they do a lot of GPO policies later. They like to produce certain registry keys. And if you have them, then whatever, you can apply that setting.
Andy: Okay. So it checks for some registry keys that don't exist by default in Windows 10. When it finds those, then it does other things. What Christian B. was able to figure out is if you create the keys that it's looking for, one of the keys actually lets you dictate it and enter in furth |
Malware Guideline | |||
| 2019-09-27 13:00:00 | Why security monitoring falls short and what can be done about it (lien direct) |
 Photo by Emmanuel on Unsplash
There are parts of every business considered to be critical to its ability to function. Email, accounting, and customer service are a few. Indeed, if email went down, accounts receivable stopped, or customers couldn’t talk to anyone, the business would suffer. There is another critical function of business that isn’t widely viewed as such: security monitoring.
If you’re not “hands on” with security day-to-day, you might have just read that and thought, “…whaaaatever.”
Yet, what would happen if your company was hacked and you suffered a critical, prolonged outage? Or if your company was featured in the next credit card breach headline? Would you reconsider the importance of security monitoring in the aftermath of these events?
Yes, security monitoring is a critical business function because it is a vital element of any meaningful cyber security strategy. Without a doubt, a sound monitoring capability can prevent and minimize loss of revenue, data, value, and trust associated with a breach. Why then, is it one of the most under-funded and under-resourced functions in many businesses?
More often than not, it is because organizations fail to approach it with the rigor and discipline applied to other core business functions. And when you fail to take that approach, there will be inevitable shortcomings in the implementation and operation of the security monitoring program. This is part of the reason so many businesses continue to fall victim to cyberthreats, costing immense losses every year.
Frequently, we’re called into a company because a breach has already occurred. In those moments, budgets are out the window, as all hands are on deck to assess and contain the threat, and to recover critical business operations. In the aftermath of damage control, the focus shifts to an introspective post-mortem. We seek to understand the vulnerabilities, gaps, and even attitudes that gave way to such havoc, and to implement the necessary practices to help prevent such a breach from happening again.
Almost always, we find that the prior security monitoring effort could much better be defined as a “concept” rather than a “program” or “capability”. We routinely see clients with a few generalists from their IT or security departments overseeing the effort, but not full time, and with little (if any) training in the practice. Security monitoring is a specialty, and it requires well-trained analysts to perform the job correctly.
There are countless manifestations of threat activity that a seasoned analyst knows how to spot and investigate. This ability comes with training, experience, and often the support of a broader team that can provide their own insights and guidance. Even then, these folks need standardized processes to ensure the consistency and effectiveness of the operation.
No matter how capable they may be, even the most skilled generalist is at a constant disadvantage in knowing what to look for, how to investigate it, and getting it right time-after-time. Moreover, budget constraints and competing priorities dictate that these individuals are seldom provided ample time to perform their work thoughtfully and thoroughly. Given these realities, most organizations will find that building a strong monitoring program in-house is an uphill battle.
Unless you are among the fortunate few who can afford to acquire, train, and retain the talent to staff a SOC, you may want to consider a partner who can bring the SOC function to you.
Want to learn more? Join Alagen’s webinar on September 30 to hear me talk about the benefits — performance and financial — of hiring a managed securit
Photo by Emmanuel on Unsplash
There are parts of every business considered to be critical to its ability to function. Email, accounting, and customer service are a few. Indeed, if email went down, accounts receivable stopped, or customers couldn’t talk to anyone, the business would suffer. There is another critical function of business that isn’t widely viewed as such: security monitoring.
If you’re not “hands on” with security day-to-day, you might have just read that and thought, “…whaaaatever.”
Yet, what would happen if your company was hacked and you suffered a critical, prolonged outage? Or if your company was featured in the next credit card breach headline? Would you reconsider the importance of security monitoring in the aftermath of these events?
Yes, security monitoring is a critical business function because it is a vital element of any meaningful cyber security strategy. Without a doubt, a sound monitoring capability can prevent and minimize loss of revenue, data, value, and trust associated with a breach. Why then, is it one of the most under-funded and under-resourced functions in many businesses?
More often than not, it is because organizations fail to approach it with the rigor and discipline applied to other core business functions. And when you fail to take that approach, there will be inevitable shortcomings in the implementation and operation of the security monitoring program. This is part of the reason so many businesses continue to fall victim to cyberthreats, costing immense losses every year.
Frequently, we’re called into a company because a breach has already occurred. In those moments, budgets are out the window, as all hands are on deck to assess and contain the threat, and to recover critical business operations. In the aftermath of damage control, the focus shifts to an introspective post-mortem. We seek to understand the vulnerabilities, gaps, and even attitudes that gave way to such havoc, and to implement the necessary practices to help prevent such a breach from happening again.
Almost always, we find that the prior security monitoring effort could much better be defined as a “concept” rather than a “program” or “capability”. We routinely see clients with a few generalists from their IT or security departments overseeing the effort, but not full time, and with little (if any) training in the practice. Security monitoring is a specialty, and it requires well-trained analysts to perform the job correctly.
There are countless manifestations of threat activity that a seasoned analyst knows how to spot and investigate. This ability comes with training, experience, and often the support of a broader team that can provide their own insights and guidance. Even then, these folks need standardized processes to ensure the consistency and effectiveness of the operation.
No matter how capable they may be, even the most skilled generalist is at a constant disadvantage in knowing what to look for, how to investigate it, and getting it right time-after-time. Moreover, budget constraints and competing priorities dictate that these individuals are seldom provided ample time to perform their work thoughtfully and thoroughly. Given these realities, most organizations will find that building a strong monitoring program in-house is an uphill battle.
Unless you are among the fortunate few who can afford to acquire, train, and retain the talent to staff a SOC, you may want to consider a partner who can bring the SOC function to you.
Want to learn more? Join Alagen’s webinar on September 30 to hear me talk about the benefits — performance and financial — of hiring a managed securit |
Threat | |||
| 2019-09-26 13:00:00 | How to manage Internet of Things (IoT) security in 2019 (lien direct) |
 Photo by BENCE BOROS on Unsplash
The challenges of IoT security
Welcome to the world of Internet of Things (IoT) and a glimpse into the future. The IoT is where the physical world merges with the digital world. Soon, we expect the world IoT population to outnumber the human population tenfold—perhaps as many as 80 billion connected devices by 2025.
As you witness the accelerating global and economic growth of IoT you are probably wondering how you and your business will connect and take part in the multi-trillion dollar opportunities that will be created by it.
It means different things to everyone—from a connected car to a smart lamppost, a wearable health monitor, or a robot on the assembly line of a factory floor. It might even be ‘connected dirt’—with swarms of small, solar-powered sensors on the fields of a farm.
No matter which way you do it, there’s a daunting task ahead: the acceleration of IoT, combined with the diversity of these devices, their different capabilities, and the many places and ways they can be deployed—make security a unique challenge.
What you need is a consistent way to establish and maintain security for all aspects of the IoT deployments you envision for the future of your business.
This is within your reach, by adopting a holistic, multi-layered approach to protect your IoT ecosystem, your other valuable assets they connect to, as well as the physical world they reside in.
Solutions for your Internet of Things security needs
Protect your IoT with a layered approach.
Every IoT ecosystem has its own distinct security needs. Even for a single client, seemingly similar IoT deployments may have different underlying designs. For example, a factory built today may have a radically different design from the one built just a few years ago. This means a combination of different solutions may be needed to help provide security for each of them.
A thorough security assessment of IoT is a multi-layered process. Every layer needs care and attention. Some endpoint devices are complex, with multiple ways to access the internal functions of the device. Others are simple, years behind smart phones with regard to security. Do you know your devices’ security capabilities?
Endpoints may connect with each other, to and through gateways, to other networks, on the Internet, and to the cloud. They may use connections that include wired, wireless, short-range, cellular, and satellite. What could potentially disrupt them from communicating?
To make your IoT deployment successful, data from your devices must be acquired, transported, processed, and consumed. How are you providing for trust and appropriate access to your vital data and applications?
Realize that some IoT ecosystems can vary wildly from a traditional IT environment. Industrial IoT deployments use operational technology which flips the script on the classic model for information security. Availability and integrity are the priority, while confidentiality isn’t typically a consideration. This requires specialized passive scanning tools to perform assessments. Slight disruption to manufacturing or utility processes turn into massive financial loss. An example of this is a factory that produces a pickup truck every minute—it cannot afford downtime. Life-sensitive devices will affect remediation and response plans. So for example, a connected healthcare device like an insulin pump—even if you think someone is accessing the data, you wouldn’t want to disable the device.
What’s your formal plan for handling threats to your devices? Have you tested it
Photo by BENCE BOROS on Unsplash
The challenges of IoT security
Welcome to the world of Internet of Things (IoT) and a glimpse into the future. The IoT is where the physical world merges with the digital world. Soon, we expect the world IoT population to outnumber the human population tenfold—perhaps as many as 80 billion connected devices by 2025.
As you witness the accelerating global and economic growth of IoT you are probably wondering how you and your business will connect and take part in the multi-trillion dollar opportunities that will be created by it.
It means different things to everyone—from a connected car to a smart lamppost, a wearable health monitor, or a robot on the assembly line of a factory floor. It might even be ‘connected dirt’—with swarms of small, solar-powered sensors on the fields of a farm.
No matter which way you do it, there’s a daunting task ahead: the acceleration of IoT, combined with the diversity of these devices, their different capabilities, and the many places and ways they can be deployed—make security a unique challenge.
What you need is a consistent way to establish and maintain security for all aspects of the IoT deployments you envision for the future of your business.
This is within your reach, by adopting a holistic, multi-layered approach to protect your IoT ecosystem, your other valuable assets they connect to, as well as the physical world they reside in.
Solutions for your Internet of Things security needs
Protect your IoT with a layered approach.
Every IoT ecosystem has its own distinct security needs. Even for a single client, seemingly similar IoT deployments may have different underlying designs. For example, a factory built today may have a radically different design from the one built just a few years ago. This means a combination of different solutions may be needed to help provide security for each of them.
A thorough security assessment of IoT is a multi-layered process. Every layer needs care and attention. Some endpoint devices are complex, with multiple ways to access the internal functions of the device. Others are simple, years behind smart phones with regard to security. Do you know your devices’ security capabilities?
Endpoints may connect with each other, to and through gateways, to other networks, on the Internet, and to the cloud. They may use connections that include wired, wireless, short-range, cellular, and satellite. What could potentially disrupt them from communicating?
To make your IoT deployment successful, data from your devices must be acquired, transported, processed, and consumed. How are you providing for trust and appropriate access to your vital data and applications?
Realize that some IoT ecosystems can vary wildly from a traditional IT environment. Industrial IoT deployments use operational technology which flips the script on the classic model for information security. Availability and integrity are the priority, while confidentiality isn’t typically a consideration. This requires specialized passive scanning tools to perform assessments. Slight disruption to manufacturing or utility processes turn into massive financial loss. An example of this is a factory that produces a pickup truck every minute—it cannot afford downtime. Life-sensitive devices will affect remediation and response plans. So for example, a connected healthcare device like an insulin pump—even if you think someone is accessing the data, you wouldn’t want to disable the device.
What’s your formal plan for handling threats to your devices? Have you tested it |
Hack |
To see everything:
Our RSS (filtrered)
