One Article Review
| Source | |
|---|---|
| Identifiant | 1501619 |
| Date de publication | 2020-01-17 10:32:23 (vue: 2020-01-17 11:05:40) |
| Titre | CVE-2019-19470: Rumble in the Pipe |
| Texte | This blog post describes an interesting privilege escalation from a local user to SYSTEM for a well-known local firewall solution called TinyWall in versions prior to 2.1.13. Besides a .NET deserialization flaw through Named Pipe communication, an authentication bypass is explained as well. Introduction TinyWall is a local firewall written in .NET. It consists of a single executable that runs once as SYSTEM and once in the user context to configure it. The server listens on a Named Pipe for messages that are transmitted in the form of serialized object streams using the well-known and beloved BinaryFormatter. However, there is an additional authentication check that we found interesting to examine and that we want to elaborate here a little more closely as it may also be used by other products to protect themselves from unauthorized access. For the sake of simplicity the remaining article will use the terms Server for the receiving SYSTEM process and Client for the sending process within an authenticated user context, respectively. Keep in mind that the authenticated user does not need any special privileges (e.g. SeDebugPrivilege) to exploit this vulnerability described.Named Pipe Communication Many (security) products use Named Pipes for inter-process communication (e.g. see Anti Virus products). One of the advantages of Named Pipes is that a Server process has access to additional information on the sender like the origin Process ID, Security Context etc. through Windows' Authentication model. Access to Named Pipes from a programmatic perspective is provided through Windows API calls but can also be achieved e.g. via direct filesystem access. The Named Pipe filessystem (NPFS) is accessible via the Named Pipe's name with a prefix \\.\pipe\.The screenshot below confirms that a Named Pipe "TinyWallController" exists and could be accessed and written into by any authenticated user. Talking to SYSTEMFirst of all, let's look how the Named Pipe is created and used. When TinyWall starts, a PipeServerWorker method takes care of a proper Named Pipe setup. For this the Windows API provides System.IO.Pipes.NamedPipeServerStream with one of it's constructors taking a parameter of System.IO.Pipes.PipeSecurity. This allows for fine-grained access control via System.IO.PipeAccessRule objects using SecurityIdentifiers and alike. Well, as one can observe from the first screenshot above, the only restriction seems to be that the Client process has to be executed in an authenticated user context which doesn't seem to be a hard restriction after all. Talking to SYSTEMFirst of all, let's look how the Named Pipe is created and used. When TinyWall starts, a PipeServerWorker method takes care of a proper Named Pipe setup. For this the Windows API provides System.IO.Pipes.NamedPipeServerStream with one of it's constructors taking a parameter of System.IO.Pipes.PipeSecurity. This allows for fine-grained access control via System.IO.PipeAccessRule objects using SecurityIdentifiers and alike. Well, as one can observe from the first screenshot above, the only restriction seems to be that the Client process has to be executed in an authenticated user context which doesn't seem to be a hard restriction after all.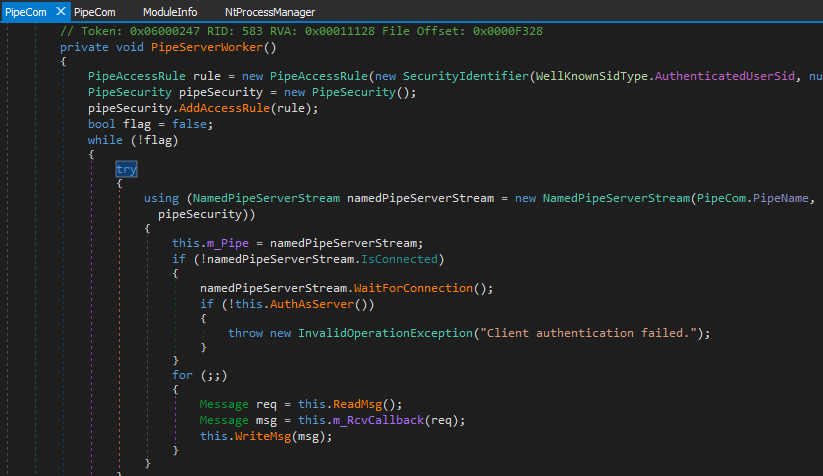 But as it turned out But as it turned out |
| Envoyé | Oui |
| Condensat | introduction 19470: 2007 2019 @fuzzysec above access accessed accessible accordingly achieved additional adjust advantages after again alike all allow allows already also anti any api approach are arguments article ask assumption attaching attributes authasserver authenticated authentication automatically automation available based basedllname been before beginning behind being beloved below besides binary binaryformatter block blog boonen both breakpoint brought built but bypass bypassed:the calc calcimplementing call called calls can candidate care case cast change check checking chose client closely code colleague combined commandline communication concept configure confirmed confirms connecting consists constructors containing content context control convert core could count created creating current cve data debugger debugging defined described describes deserialization deserializationthus deserializing design detail details developers diagnostics did direct disclosurethe dll dnspy does doesn double elaborate enabled entries environment equality escalation etc even exactly examine exe executable executed exercise existing exists explained explaining explicit exploit explorer expressing expression extended failed fails fake faked faking fed filename filenameafter filessystem filesystem final finally fine firewall first fixed flaw flow following form forshaw fortunately forward found from frombase64string fulfill full fulldllname further gadget get getmodulefilenameex getnamedpipeclientprocessid grained great had handle hard has have here hit hopefully how however idea identifier ids imagepathname immediately implementation implemented imported information instance inter interesting invalidcastexceptions invalidoperationexception invoked invoking its james keep kind known late lazy ldr left let like linked list listens little local look made mainmodule malicious management many markus masquerade match matching may member memory mentioned message messages method mind model modification modified moduleinfo more name named namedpipeclientstream namedpipeserverstream namely native need net nice not now npfs ntprocessmanager ntqueryinformationprocess object objects observe once one only operates origin original other ourselves out over overwrite owner parameter parameters passed path peb perspective phrack pipe pipeaccessrule pipeclient pipes pipesecurity pipeserverworker pipestream pksoft place pop popping ported possible post powershell ppeb prefix prior privilege privileges process processmodule processparameters products programmatic proof proper property protect provided provides prtl ps1 psapi put quickly reach read reader reading readmsg receive received receiving released releasing relevant remaining replace requirement research respectively responsible restriction result resulted retrieved retrieves rid right ruben rumble running runs sake same screenshot script scripts security securityidentifiers sedebugprivilege see seem seems send sender sending sent serialize serialized server session set setting setup several should simplicity since single slight solution some somehow special specified starting starts straight streams strings struct structure structures such support sysinternals system systemfirst take taken takes taking talking terms test testing thanks themselves therefore these though through thrown tinywall tinywallcontroller together took tool topics transition transmitted triggered trusted turned typeconfusedelegate unauthorized under underlying unicode untrusted use used user userland using value variable verified verify version versions very virus vulnerability want well what when where which will windows with ysoserial within without work world would writeable writecore writes written wulftange |
| Tags | Tool Vulnerability |
| Stories | |
| Notes | |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.