One Article Review
| Source | |
|---|---|
| Identifiant | 4726486 |
| Date de publication | 2022-05-21 15:49:50 (vue: 2022-05-21 04:06:22) |
| Titre | Responsible disclosure - another new policy |
| Texte | 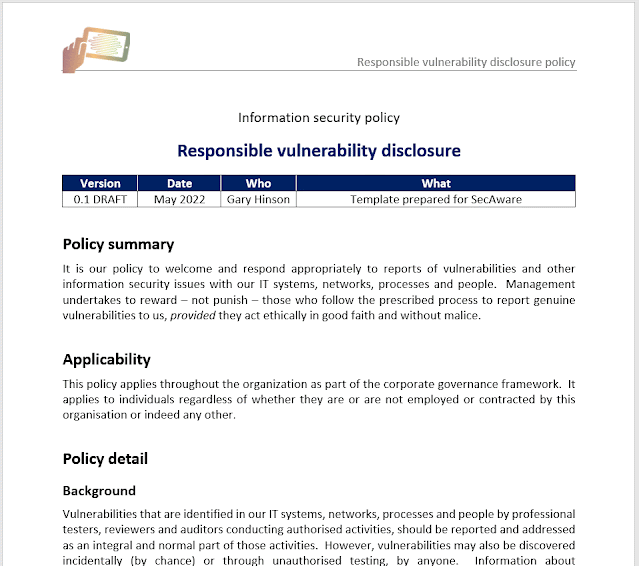 We have just completed and released another topic-specific information security policy template, covering responsible disclosure (of vulnerabilities, mostly).The policy encourages people to report any vulnerabilities or other information security issues they discover with the organisation's IT systems, networks, processes and people. Management undertakes to investigate and address reports using a risk-based approach, reducing the time and effort required for spurious or trivial issues, while ensuring that more significant matters are prioritised. The policy distinguishes authorised from unauthorised security testing, and touches on ethical aspects such as hacking and premature disclosure.It allows for reports to be made or escalated to Internal Audit, acting as a trustworthy, independent function, competent to undertake investigations dispassionately. This is a relief-valve for potentially sensitive or troublesome reports where the reporter is dubious of receiving fair, prompt treatment through the normal reporting mechanism - for instance, reporting on peers or managers.It is primarily intended as an internal/corporate security policy applicable to workers ... but can be used as the basis for something to be published on your website, aimed at 'security researchers' and ethical hackers out there. There are notes about this at the end of the template. To be honest, there are plenty of free examples on the web but few if any are policies covering vulnerability disclosure by workers.All that in just 3 pages, available as an MS Word document for $20 from SecAware.com.I am working on another 2 new topic-specific policies as and when I get the time. Paradoxically, it takes me longer to prepare succcinct policy templates than, say, guidelines or awareness briefings. I have to condense the topic down to its essentials without neglecting anything important. After a fair bit of research and thinking about what those essentials are, the actual drafting is fairly quick, despite the formalities. Preparing new product pages and uploading the templates plus product images then takes a while, especially for policies that relate to several others in the suite - which most do these days as the SecAware policy suite has expanded and matured. As far as I know, SecAware has the broadest coverage of any info/cybersec policy suite on the market.... Talking of which, I plan to package all the topic-specific policies together as a bulk deal before long. Having written them all, I know the suite is internally consistent in terms of the writing style, formatting, approach, coverage and level. It's also externally consistent in the sense of incorporating good security practices from the ISO27k and other standards. We have just completed and released another topic-specific information security policy template, covering responsible disclosure (of vulnerabilities, mostly).The policy encourages people to report any vulnerabilities or other information security issues they discover with the organisation's IT systems, networks, processes and people. Management undertakes to investigate and address reports using a risk-based approach, reducing the time and effort required for spurious or trivial issues, while ensuring that more significant matters are prioritised. The policy distinguishes authorised from unauthorised security testing, and touches on ethical aspects such as hacking and premature disclosure.It allows for reports to be made or escalated to Internal Audit, acting as a trustworthy, independent function, competent to undertake investigations dispassionately. This is a relief-valve for potentially sensitive or troublesome reports where the reporter is dubious of receiving fair, prompt treatment through the normal reporting mechanism - for instance, reporting on peers or managers.It is primarily intended as an internal/corporate security policy applicable to workers ... but can be used as the basis for something to be published on your website, aimed at 'security researchers' and ethical hackers out there. There are notes about this at the end of the template. To be honest, there are plenty of free examples on the web but few if any are policies covering vulnerability disclosure by workers.All that in just 3 pages, available as an MS Word document for $20 from SecAware.com.I am working on another 2 new topic-specific policies as and when I get the time. Paradoxically, it takes me longer to prepare succcinct policy templates than, say, guidelines or awareness briefings. I have to condense the topic down to its essentials without neglecting anything important. After a fair bit of research and thinking about what those essentials are, the actual drafting is fairly quick, despite the formalities. Preparing new product pages and uploading the templates plus product images then takes a while, especially for policies that relate to several others in the suite - which most do these days as the SecAware policy suite has expanded and matured. As far as I know, SecAware has the broadest coverage of any info/cybersec policy suite on the market.... Talking of which, I plan to package all the topic-specific policies together as a bulk deal before long. Having written them all, I know the suite is internally consistent in terms of the writing style, formatting, approach, coverage and level. It's also externally consistent in the sense of incorporating good security practices from the ISO27k and other standards. |
| Envoyé | Oui |
| Condensat | $20 about acting actual address after aimed all allows also another any anything applicable approach are aspects audit authorised available awareness based basis before bit briefings broadest bulk but can com competent completed condense consistent coverage covering days deal despite disclosure discover dispassionately distinguishes document down drafting dubious effort encourages end ensuring escalated especially essentials ethical examples expanded externally fair fairly far formalities formatting free from function get good guidelines hackers hacking has have having honest images important incorporating independent info/cybersec information instance intended internal internal/corporate internally investigate investigations iso27k issues its just know level long longer made management managers market matters matured mechanism more most mostly neglecting networks new normal notes organisation other others out package pages paradoxically peers people plan plenty plus policies policy potentially practices premature prepare preparing primarily prioritised processes product prompt published quick receiving reducing relate released relief report reporter reporting reports required research researchers responsible risk say secaware security sense sensitive several significant something specific spurious standards style succcinct such suite systems takes talking template templates terms testing than them then these thinking those through time together topic touches treatment trivial troublesome trustworthy unauthorised undertake undertakes uploading used using valve vulnerabilities vulnerability web website what when where which without word workers working writing written your |
| Tags | Vulnerability |
| Stories | |
| Notes | |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.