One Article Review
| Source | |
|---|---|
| Identifiant | 732780 |
| Date de publication | 2018-07-06 14:08:42 (vue: 2018-07-06 15:00:29) |
| Titre | LethalHTA - A new lateral movement technique using DCOM and HTA |
| Texte | The following blog post introduces a new lateral movement technique that combines the power of DCOM and HTA. The research on this technique is partly an outcome of our recent research efforts on COM Marshalling: Marshalling to SYSTEM - An analysis of CVE-2018-0824. Previous Work Several lateral movement techniques using DCOM were discovered in the past by Matt Nelson, Ryan Hanson, Philip Tsukerman and @bohops. A good overview of all the known techniques can be found in the blog post by Philip Tsukerman. Most of the existing techniques execute commands via ShellExecute(Ex). Some COM objects provided by Microsoft Office allow you to execute script code (e.g VBScript) which makes detection and forensics even harder. LethalHTA LethalHTA is based on a very well-known COM object that was used in all the Office Moniker attacks in the past (see FireEys's blog post): ProgID: "htafile" CLSID : "{3050F4D8-98B5-11CF-BB82-00AA00BDCE0B}" AppID : "{40AEEAB6-8FDA-41E3-9A5F-8350D4CFCA91}" Using James Forshaw's OleViewDotNet we get some details on the COM object. The COM object runs as local server.  It has an App ID and default launch and access permissions. Only COM objects having an App ID can be used for lateral movement. It has an App ID and default launch and access permissions. Only COM objects having an App ID can be used for lateral movement. 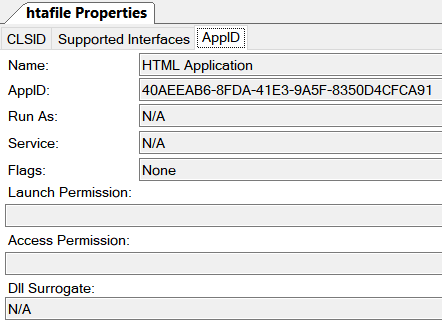 It also implements various interfaces as we can see from OleViewDotNet. It also implements various interfaces as we can see from OleViewDotNet. 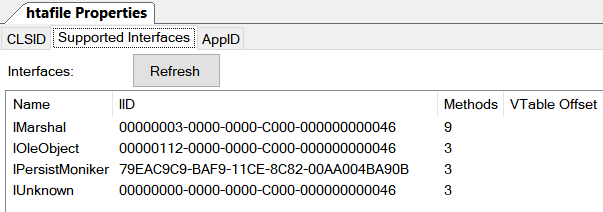 One of the interfaces is IPersistMoniker. This interface is used to save/restore a COM object's state to/from an IMoniker instance. Our initial plan was to create the COM object and restore its state by ca One of the interfaces is IPersistMoniker. This interface is used to save/restore a COM object's state to/from an IMoniker instance. Our initial plan was to create the COM object and restore its state by ca |
| Envoyé | Oui |
| Condensat | able above activexobject addition additional allows also any apparent appdata architecture are attack based beacon beacons before bootstrapping caching can cases class combination config connected connecting containing creating dcom deep delivery delivery/retrieval described detailed detect detected detection determines done dotnettojscript due dynamic dynamically everything exe execute executes explanation exploitation far file files flexibility folder from further furthermore github host hta http implementing included inetcache inside instead internal internet involved lateral lethalhta listener load local memory method microsoft more most movement mshta named need net network new not one only option other payload pipe possible powershell process processes project provides proxy reach same scenarios scloader server shellcode since small smb solution spawned specify staged stageless stealth step steps svchost system system32 systemprofile systems syswow64 takes target teamserver technique techniques terms then through tunnel two used using utilizing vector visit watch where which windir windows within without x64 x86 x86/x64 |
| Tags | |
| Stories | |
| Notes | |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.