One Article Review
| Source | |
|---|---|
| Identifiant | 8221932 |
| Date de publication | 2022-08-24 12:02:07 (vue: 2022-11-25 18:05:33) |
| Titre | CVE-2021-1782, an iOS in-the-wild vulnerability in vouchers |
| Texte | Posted by Ian Beer, Google Project Zero This blog post is my analysis of a vulnerability exploited in the wild and patched in early 2021. Like the writeup published last week looking at an ASN.1 parser bug, this blog post is based on the notes I took as I was analyzing the patch and trying to understand the XNU vouchers subsystem. I hope that this writeup serves as the missing documentation for how some of the internals of the voucher subsystem works and its quirks which lead to this vulnerability. CVE-2021-1782 was fixed in iOS 14.4, as noted by @s1guza on twitter: 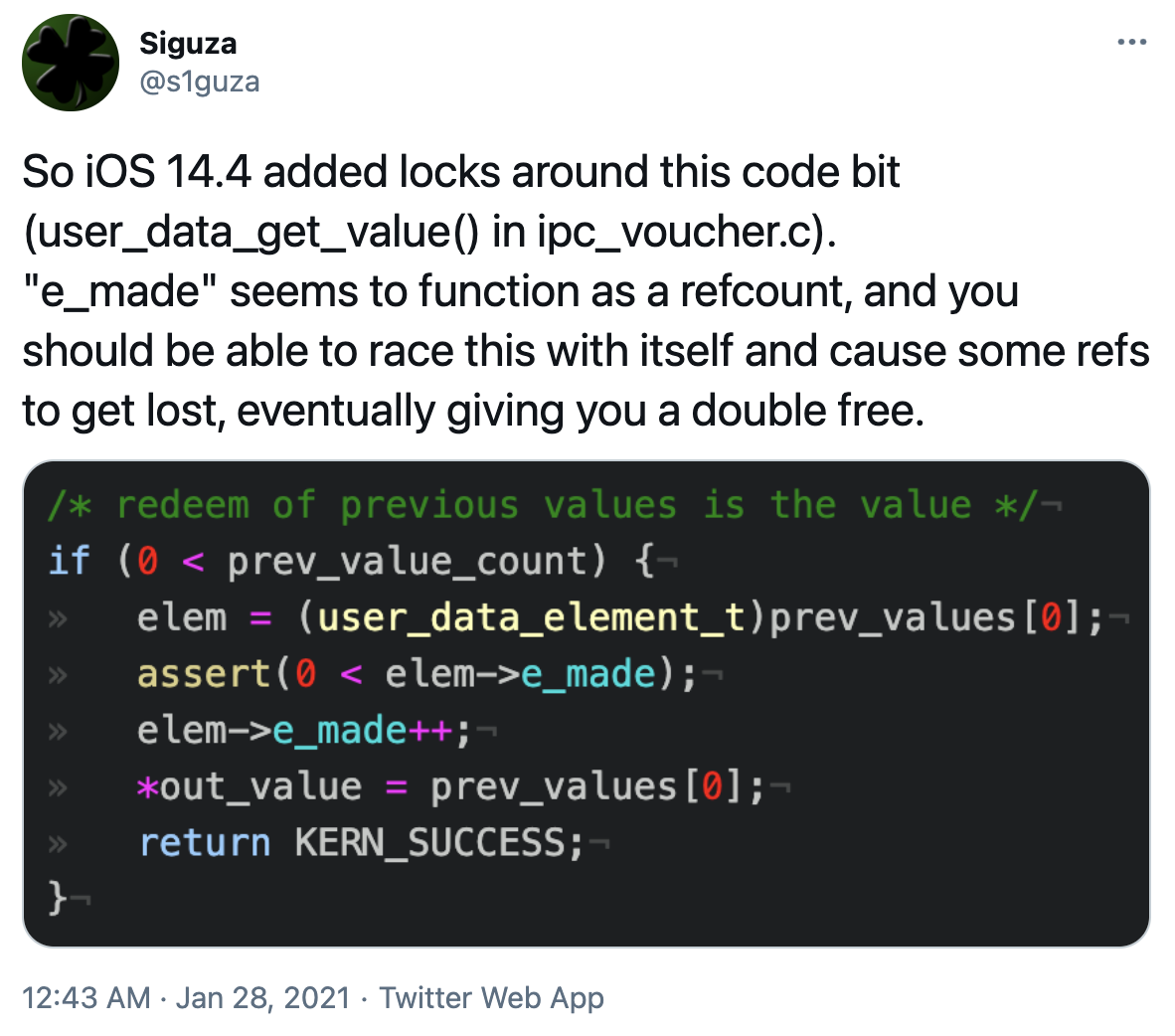 This vulnerability was fixed on January 26th 2021, and Apple updated the iOS 14.4 release notes on May 28th 2021 to indicate that the issue may have been actively exploited: This vulnerability was fixed on January 26th 2021, and Apple updated the iOS 14.4 release notes on May 28th 2021 to indicate that the issue may have been actively exploited: |
| Envoyé | Oui |
| Condensat | #define iv #define mach #include && elem & mach &new &recipes &redeem &single &user &voucher &ivac &ivam &new &previous &redeem &single * */ *out + content + elem + sub /* 0x41 1 2040 : = = arc4random = ivace = reference = value alloc and boolean buf char** argv command content count e elem false flag if ipc iter iv ivac ivace ivaceu ivam ivgte key len mach made new null pointers prev previous recipe s3threadfunc size sizeof so sub template the true user userdata val value values voucher you *alloc *count *elem *index* into user *new *new* *out *prev *sub *template *voucher + len +8; += 7; += sizeof +sizeof 0 0 elem 0 ivace 0 prev 0 recipe 0 == content 0 == ivace 0x41 16kb 1782 1:1 2*sizeof 2021 232 increments 26th 28th 5260 : false; = = &ivac = 0; = 0; i = 0x41414141; = 100000; = 1; = alloc = calloc = content = create = elem = false; = hash; = host = index = index; = ipc = iv = ivac = ivace = kern = key = kr = len; = mach = made = made; = new = null; = pointer = prev = recipe = reference = sizeof = sub = sum; = true; = user = value; == alloc == content == elem == hash == index == ivac == ivace == ivam == key == kr == manager == prev == sum == value == voucher > 0 >command >content >iv >ivac >ivace >ivam >key >previous >recipe @i41nbeer @s1guza able about above absolute abstract abstracted accessed accessing accounted acquired across actively actual actually add added addition address adds after afternoon again against agnostic aid align alive all alloc allocate allocated allocated: allocates allocation allocator allocator; allow allowed allows allusions almost already also although always always get analysis analyzing another answer any anything apple apply arbitrary arc4random are are: aren arg; arguably argument; around array array; so ask asn assert associated assume assuming atm atomic atrr attack attacker attempting attr attribute attribute; attributes attrs attrs in auditing auto away back back; background bad band bank bank: based because been beer before before any behind being believe below better between bit blog boolean both bottom branch break; briefly bucket bucket hash bucket hashtable buckets buf buffer buffers bug bug: build built bunch but byte bytes bytes: cache caches calculate call called called: caller calling callout calls callsite: can cannot cant capability; captures case case mach case: cases: cast casts cause causes certainly chain chained changed chats: check checks checksum choose chooses circumstances claim clear clients; code code: code; codebase coffee collection collide combine/evaluate comes command command are command function command is command mig command which command; commands comment comments compare compared complete completely completeness complex complicated concept concise conclusions concretely condition conditions confusing; confusion connection consequences consisting const struct ipc construction consume consumed consumes containing contains content content content is content voucher content; contents continue continue; continues continues: contribution control contr |
| Tags | Hack Tool Vulnerability Guideline |
| Stories | |
| Notes | ★★★ |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.