One Article Review
| Source | |
|---|---|
| Identifiant | 8565304 |
| Date de publication | 2024-08-28 10:00:00 (vue: 2024-08-28 10:17:43) |
| Titre | 2024 Cyber Resilience Research: Aligner la cybersécurité du commerce de détail avec les priorités commerciales 2024 Cyber Resilience Research: Aligning Retail Cybersecurity with Business Priorities |
| Texte | New data illuminates how retail leaders can prioritize resilience.
 In today’s retail environment, businesses embrace dynamic computing and other technological innovations to enhance operations and customer experiences. However, as these advancements accelerate, so does the risk of cyber threats.
The 2024 LevelBlue Retail Report reveals a significant challenge for retail leaders: aligning cybersecurity strategies with broader business objectives to ensure a resilient future, especially in securing the increasingly complex supply chain.
Dynamic Computing: Opportunity and Risk
Dynamic computing offers retail businesses unparalleled opportunities to innovate and gain a competitive edge. By processing data closer to the source, retailers can develop groundbreaking services, optimize their supply chains, and deliver more personalized customer experiences. According to the report, 86% of retail executives anticipate that dynamic computing will improve operational performance within the next three years.
However, this optimism comes with a cautionary note—82% of retail respondents also acknowledge that these innovations increase their exposure to cyber risks, particularly within the supply chain. As retail operations become more interconnected and reliant on advanced technologies, the potential for cyber attacks grows, making robust cybersecurity strategies more critical than ever. The complexity of modern supply chains, with their numerous vendors and touchpoints, only amplifies the risk, as each link in the chain could be a potential vulnerability.
Get your complimentary copy of the report.
In today’s retail environment, businesses embrace dynamic computing and other technological innovations to enhance operations and customer experiences. However, as these advancements accelerate, so does the risk of cyber threats.
The 2024 LevelBlue Retail Report reveals a significant challenge for retail leaders: aligning cybersecurity strategies with broader business objectives to ensure a resilient future, especially in securing the increasingly complex supply chain.
Dynamic Computing: Opportunity and Risk
Dynamic computing offers retail businesses unparalleled opportunities to innovate and gain a competitive edge. By processing data closer to the source, retailers can develop groundbreaking services, optimize their supply chains, and deliver more personalized customer experiences. According to the report, 86% of retail executives anticipate that dynamic computing will improve operational performance within the next three years.
However, this optimism comes with a cautionary note—82% of retail respondents also acknowledge that these innovations increase their exposure to cyber risks, particularly within the supply chain. As retail operations become more interconnected and reliant on advanced technologies, the potential for cyber attacks grows, making robust cybersecurity strategies more critical than ever. The complexity of modern supply chains, with their numerous vendors and touchpoints, only amplifies the risk, as each link in the chain could be a potential vulnerability.
Get your complimentary copy of the report.
 The Misalignment Between Business and IT
The Misalignment Between Business and IT
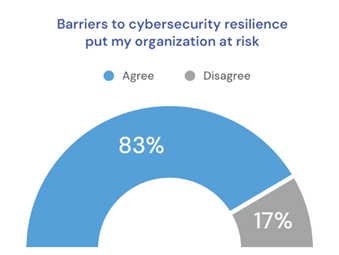 Despite the clear risks associated with technological innovation, there remains a troubling disconnect between business objectives and IT priorities in the retail sector. The report highlights that while business leaders are eager to drive innovation, they often overlook the need to integrate cybersecurity into their strategic planning. This misalignment leaves organizations vulnerable, particularly in their supply chains, as cybersecurity measures are frequently treated as afterthoughts rather than integral components of business success.
One of the most striking findings in the report is that 83% of retail executives do not view cyber resilience as a whole-organization priority. Instead, it is often siloed within IT departments, with limited engagement from other parts of the business. This fragmented approach undermines the effectiveness of cybersecurity efforts and exposes the organization, especially its supply chain, to greater risks.
Strategies for Alignment
To bridge the gap between business objectives and IT priorities, retail leaders must adopt a more integrated approach to cybersecurity, with a particular focus on the supply chain. Here are some key strategies to consider:
1. Proactive Risk Management: Retail executives must involve IT and cybersecurity teams in the early stages of strategic planning. By doing so, they can anticipate potential risks in the supply chain and develop proactive measures to mitigate them rather than reacting to threats after they occur.
2. Cross-Departmental Collaboration: Breaking down silos between IT, supply chain management, and other busines
Despite the clear risks associated with technological innovation, there remains a troubling disconnect between business objectives and IT priorities in the retail sector. The report highlights that while business leaders are eager to drive innovation, they often overlook the need to integrate cybersecurity into their strategic planning. This misalignment leaves organizations vulnerable, particularly in their supply chains, as cybersecurity measures are frequently treated as afterthoughts rather than integral components of business success.
One of the most striking findings in the report is that 83% of retail executives do not view cyber resilience as a whole-organization priority. Instead, it is often siloed within IT departments, with limited engagement from other parts of the business. This fragmented approach undermines the effectiveness of cybersecurity efforts and exposes the organization, especially its supply chain, to greater risks.
Strategies for Alignment
To bridge the gap between business objectives and IT priorities, retail leaders must adopt a more integrated approach to cybersecurity, with a particular focus on the supply chain. Here are some key strategies to consider:
1. Proactive Risk Management: Retail executives must involve IT and cybersecurity teams in the early stages of strategic planning. By doing so, they can anticipate potential risks in the supply chain and develop proactive measures to mitigate them rather than reacting to threats after they occur.
2. Cross-Departmental Collaboration: Breaking down silos between IT, supply chain management, and other busines |
| Notes | ★★★ |
| Envoyé | Oui |
| Condensat | 2024 accelerate according acknowledge across adopt adopting advanced advancements affecting after afterthoughts aligning alignment all also amplifies anticipate approach are associated attacks become becomes been between breaking bridge broader build business businesses can capabilities cautionary chain chains challenge clear closer collaboration collaboration: comes communication competitive complex complexity complimentary components computing computing: concern consider: considered continue continuing copy could critical cross customer cyber cybersecurity data decisions deliver departmental departments despite develop disconnect does doing down download drive dynamic each eager early edge effectiveness efforts element elevating embrace emerging emphasis engagement engaging enhance ensure environment especially essential ever executives experiences expertise: experts explore exposes exposure external findings focus forward foundational fragmented frequently from future futures gain gap get given goals greater groundbreaking grows guidance have help here hesitate higher highlights how however illuminates imperative importance improve including increase increasingly innovate innovation innovations innovative insights instead integral integrate integrated interconnected internal involve its just key leaders leaders: leaves levelblue leveraging limited link links making management management: measures misalignment mitigate modern more most must necessary need never new next not note—82 numerous objectives occur offers often one only operation operational operations opportunities opportunity optimism optimize organization organizations other overlook particular particularly parts performance personalized planning potential priorities prioritize prioritizing priority proactive processing protect provide rather reacting recognized regular reliant remains report research: resilience resilience: resilient resources respondents retail retailers reveals risk risks robust sector secure securing seek services should significant siloed silos solutions some source stages stakes strategic strategies strategy strengthen striking strong success supply support teams technological technologies than them these those threats three today’s touchpoints transforming treated troubling undermines underscores units unparalleled urgent valuable vendors view vulnerability vulnerable where whole will within world years your |
| Tags | Vulnerability |
| Stories | |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.