One Article Review
| Source | |
|---|---|
| Identifiant | 8601741 |
| Date de publication | 2024-10-25 10:30:02 (vue: 2024-10-25 18:06:02) |
| Titre | The Windows Registry Adventure # 4: Hives and the Registry Mayout The Windows Registry Adventure #4: Hives and the registry layout |
| Texte | Posted by Mateusz Jurczyk, Google Project Zero
To a normal user or even a Win32 application developer, the registry layout may seem simple: there are five root keys that we know from Regedit (abbreviated as HKCR, HKLM, HKCU, HKU and HKCC), and each of them contains a nested tree structure that serves a specific role in the system. But as one tries to dig deeper and understand how the registry really works internally, things may get confusing really fast. What are hives? How do they map or relate to the top-level keys? Why are some HKEY root keys pointing inside of other root keys (e.g. HKCU being located under HKU)? These are all valid questions, but they are difficult to answer without fully understanding the interactions between the user-mode Registry API and the kernel-mode registry interface, so let\'s start there.The high-level view
A simplified diagram of the execution flow taken when an application creates a registry key is shown below:
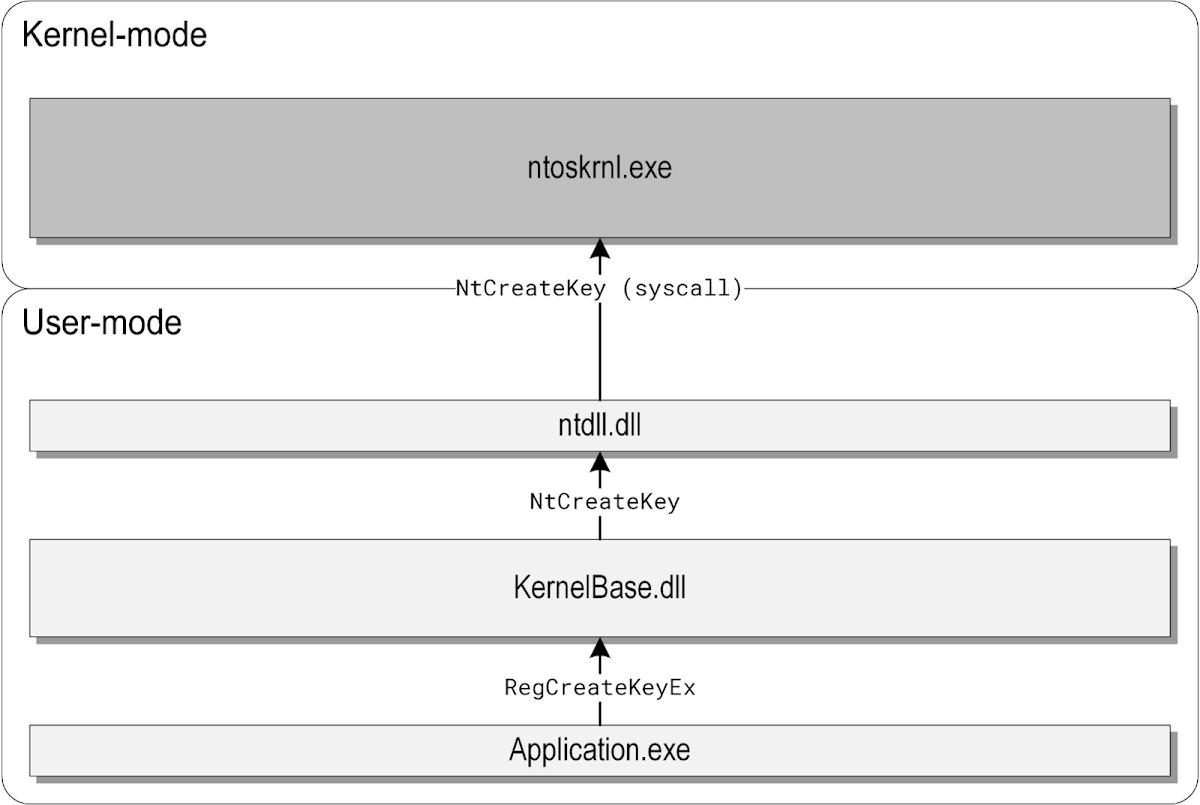 In this example, Application.exe is a desktop program calling the documented RegCreateKeyEx function, which is exported by KernelBase.dll. The KernelBase.dll library implements RegCreateKeyEx by translating the high-level API parameters passed by the caller (paths, flags, etc.) to internal ones understood by the kernel. It then invokes the NtCreateKey system call through a thin wrapper provided by ntdll.dll, and the execution finally reaches the Windows kernel, where all of the actual work on the internal registry representation is performed.
In this example, Application.exe is a desktop program calling the documented RegCreateKeyEx function, which is exported by KernelBase.dll. The KernelBase.dll library implements RegCreateKeyEx by translating the high-level API parameters passed by the caller (paths, flags, etc.) to internal ones understood by the kernel. It then invokes the NtCreateKey system call through a thin wrapper provided by ntdll.dll, and the execution finally reaches the Windows kernel, where all of the actual work on the internal registry representation is performed.
|
| Notes | ★★★ |
| Envoyé | Oui |
| Condensat | #2047 #2048 #2297 #2366 #2378 #2419 #2445 + #2445 and #2452 #2479: #2492 #2492 #4: #865 and #870 discovered #define diff #define hkey #define reg // 0 00 0000000000000000 03 10000 19 1c000 2 24000 28700000 287001ff 28700200 287003ff 28700400 287005ff 28700600 287007ff 28700800 287009ff 28700a00 28700bff 28700c00 28700dff 28700e00 28700fff 28701000 287011ff 28701200 287013ff 28701400 2870147f 28701480 2870167f 28701680 2870187f 28701880 2870197f 2877fca0 2877fe9f 2877fea0 2877feaf 2877feb0 2877ff2f 2877ff30 2877ff3f 2877ff40 2877ff4f 2f000 3 30000 4 41000 48 4c4b000 4e 5 6 68 72000 74000 78000 a0 and blog bundle cid: commit dwoptions ffff8f818ba623a0 ffff8f818ba883a0 ffff8f818bada024 ffff8f818bb873a0 ffff8f818c75b3a0 ffff8f818e7733a0 ffff8f818ec683a0 ffff8f81903703a0 ffff8f8190b98000 h handlecount: hbin key lpcwstr lpfile lpcwstr lpsubkey lpdwdisposition lpsubkey newstoreroot objecttable: optional parentcid: peb: phkresult reserved this use | **** /* +0x00 */handle hjob; /* +0x08 */dword unused1; /* +0x0c */dword diffhiveflags; /* +0x10 */dword loadflags; /* +0x14 */word /* +0x16 */word /* +0x18 */word /* +0x1a */word /* +0x1c */dword unused3; /* +0x20 */handle htoken; /* +0x28 */wchar buffer 0000 00000000 00000287`7fea1000 00000287`7fea1010 00000287`7fea1020 00000287`7fea1030 00000287`7fea1040 00000287`7fea1050 00000287`7fea1060 00000287`7fea1070 0004 001ae002 0040 02db7002 0x00000001l 0x00000002l 0x00000004l 0x00000008l 0x00000010l 0x00000020l 0x00000040l 0x00000080l 0x00000100l 0x00000200l 0x00000400l 0x00000800l 0x00001000l 0x00002000l 0x00004000l 0x00008000l 0x1 0x10 0x100 0x1000 0x2000 0x220008 0x220018 0x220020 0x2877fea0000 0x2877fea1000 0x2877fea1000: 0x2877feaffff 0x4 0x40 0x400 0x4000 0x800 0x80000000 0x80000001 0x80000002 0x80000003 0x80000004 0x80000005 0x80000006 0x80000007 0x80000050 0x80000060 0xb 0xc 0xebb0 1000 114 11: 128 1607 18 – 19 – 19b000 1f3000 2 of 20 – 2000 2003 2016 2023 2024 26181 2cf000 3193 330000 35356 35633 4000 5n1h2txyewy 7000 8000 8192 9000 ;ntstatus a is abbreviated ability able about above above: access accessed accessible accommodate accompanied according accordingly account accounts achieved acknowledged across actions activationstore active actively actual actually add added adding addition additional additionally address addresses adds adequate admin administer administrative administrators admittedly advanced advancements advantage adventure affected after against agree all allocated allow allowed allows almost already also alternatively although always amcache analysis and/or anniversary another answer anti any anything anyway anywhere api app appcompat appdata apphive appinfo appkey flag application applications applies applying approach apps arbitrary are aren argon arguments around arranged array article articles aspects assignments associated associations assumed attack attacker attacks attempting attributes attributes lpsecurityattributes automatically available awareness back backed backedunloaded: a background backing base based baselayerpathlength; baseregqueryandmergevalues and basic bbi bcd bcd00000000 bcdedit command because become becomes becoming been before behalf behavior behaviors being below below: better bet |
| Tags | Tool Vulnerability Threat Legislation Technical |
| Stories | APT 17 |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.