One Article Review
| Source | |
|---|---|
| Identifiant | 8615221 |
| Date de publication | 2024-11-21 07:00:00 (vue: 2024-11-21 07:07:56) |
| Titre | Stories from the SOC: Registry Clues to PDF Blues: A Tale of PUA Persistence |
| Texte | Executive Summary
Establishing persistence on a system allows a threat actor continued access or process execution across system restarts or other changes. For this reason, monitoring for and investigating persistence indicators are key components of any robust cybersecurity platform.
Two common persistence techniques are using AutoStart Execution of programs during system boot or logon (T1547) and abusing scheduled task functions (T1053). However, legitimate application activity also frequently involves AutoStart Execution and scheduled task functions, so defending against these techniques requires not only detection monitoring but also analysis by a cybersecurity professional.
During a recent incident involving a LevelBlue MDR SOC customer, an alarm that triggered for a Windows Autorun registry key for persistence was traced back to a potentially unwanted application (PUA). The PUA purportedly was acting as a PDF conversion application. A review of the initial alarm and relevant events revealed that the application had established a double layer of persistence by using both Scheduled Task creation and Autorun registry keys to execute JavaScript under the guise of a Chrome browser extension. Additional open-source intelligence (OSINT) tools identified the application as either a PUA or a potentially malicious file. An investigation was created for the customer with remediation recommendations and ultimately it was confirmed that the application was neither expected nor authorized within the customer’s environment, and it was removed.
The same application was later detected in another customer’s environment, but in this case, the customer had added a related file hash to an exclusion list. Because the LevelBlue MDR SOC analyst had recently investigated the application and identified it as potentially malicious, they were able to recommend removing the hash from the exclusion list and instead adding it to a blocklist.
Investigation
Initial Alarm Review
The investigation began with the LevelBlue analyst receiving an alarm that a Windows Autorun registry key named “ChromeBrowserAutoLaunch” had been added on an endpoint in the customer environment. While at first glance this appeared to be a key set to auto-launch Chrome with a browser extension loaded, analysis of the source process command line revealed several items that warranted further investigation.
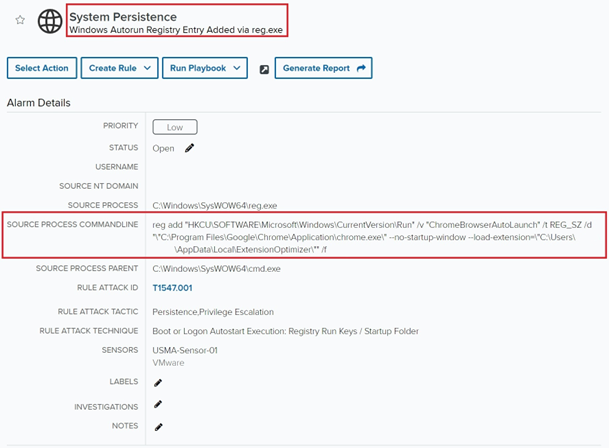 Figure 1: The initial alarm for the autorun registry key creation
The “–no-startup-window” option: although this is commonly used for legitimate purposes, it can also indicate an attempt to hide activity from the end user. The pathway of the extension being loaded showed it was not an extension that the user had installed from the Chrome webstore. The expected pathway for extensions from the webstore would be “C:\Users\\AppData\Local\Google\Chrome\User Data\Default\Extensions”. While a sideloaded extension could still be legitimate, this gave additional cause to identify the origin of the registry key and extension.
No verifiable browser extension with the name “Extension Optimizer” was found in OSINT queries.
Abuse of browser extensions (T1176) is a known technique and malicious extensions have a history of being used for infostealing, adware, and browser hijack or redirect behaviors.
Expanded Investigation
Events Search
The analyst conducted an event search to identify the origin of the browser extension “ExtensionOptimizer”. This search returned pro
Figure 1: The initial alarm for the autorun registry key creation
The “–no-startup-window” option: although this is commonly used for legitimate purposes, it can also indicate an attempt to hide activity from the end user. The pathway of the extension being loaded showed it was not an extension that the user had installed from the Chrome webstore. The expected pathway for extensions from the webstore would be “C:\Users\\AppData\Local\Google\Chrome\User Data\Default\Extensions”. While a sideloaded extension could still be legitimate, this gave additional cause to identify the origin of the registry key and extension.
No verifiable browser extension with the name “Extension Optimizer” was found in OSINT queries.
Abuse of browser extensions (T1176) is a known technique and malicious extensions have a history of being used for infostealing, adware, and browser hijack or redirect behaviors.
Expanded Investigation
Events Search
The analyst conducted an event search to identify the origin of the browser extension “ExtensionOptimizer”. This search returned pro |
| Notes | ★★ |
| Envoyé | Oui |
| Condensat | “–no “c: “eclipse “extension “extensionoptimizer “freepdf “malicious “node “pdfflex “pdftool an –check 0” 1208 202 49402039 6:deep 9c5d756045fd479a742b81241ccf439d02fc668581a3002913811a341278de43 able about abuse abusing access across acting action activity activity” actor add added adding addition additional adware after against alarm alarms alerting allowed allows along also alternate although analysis analyst analyst’s anomalous another any apparent appdata appeared application application’s applications are artifacts associated attempt authorized auto autorun autostart back based because been began behavior behaviors being blocklist blues: boot both browser building but can case cause changes chrome classified cloud clues command common commonly components conclusion conducted configured confirm confirmed context continued conversion could create created creating creation critical customer customer’s cybersecurity daily data day days deep default defending desired detailed detected detection did different dive domain double downloads due during each either elected end endpoint endpoints environment environment: established establishing event events exclusion exe exe” execute executing execution executive exhibiting expanded expected expert extension extensions extensions” figure file filename findings first flagged folder folders fortinet found frequently from functions further gave glance global google guise had hash have having hide highlights hijack history however identified identify inc inc” incident incidents including indicate indicated indicators inform information infostealing initial initially installation installed installer instead intelligence interaction investigated investigating investigation involves involving io” items its javascript key keys knowledge known later launch layer legitimacy legitimate levelblue leveraged likely line list load loaded loading local logged logon malicious manual manually matched mdr media monitoring msi msi” multiple name named nature need needed negative neither node nor not observed obtain obtained one only open optimizer” option: origin osint other outright pathway pdf pdfflex performed persistence persistently platform points potential potentially presence previously prior process professional programs protect protecting proved provided pua pua/pup publisher purportedly purposes queries reason receiving recent recently recommend recommendation recommendations recommended redirect regarding registered registry reimage related relevant remediation remove removed removing replace report reports requires research researching response responsible restarts returned revealed review risks robust run same sandbox sandboxing scheduled search searched searches security seen sentinelone service set several sha256 shortly should showed showing sideloaded signed signer similarly soc soc: sophos source startup stories such summary system t1053 t1176 t1547 tale task tasks team’s technique techniques them then these threat threats thus time together tool tools traced trigger triggered two ultimately uncovered under understand unverified unwanted update update” use used user user’s users using value vendors verdict verifiable verify version virustotal visibility warranted web webstore what which whois window” windows within would |
| Tags | Tool Threat Cloud |
| Stories | |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.