One Article Review
| Source | |
|---|---|
| Identifiant | 8641234 |
| Date de publication | 2025-01-17 18:21:00 (vue: 2025-01-22 20:07:55) |
| Titre | Stories from the SOC: Caught in the Trap: Detecting and Defending Against RaccoonO365 Phishing Campaigns |
| Texte | Executive Summary
In September 2024, LevelBlue conducted a comprehensive threat hunt targeting artifacts indicative of Phishing-as-a-Service (PhaaS) activity across our monitored customer fleet. During the investigation, the LevelBlue Managed Detection and Response (MDR) Blue Team discovered a new PhaaS kit, now identified as RaccoonO365. The hunt confirmed true-positive compromises of Office 365 accounts, prompting swift customer notifications and guidance on remediation actions. The initial findings were handed over to the LevelBlue Labs Threat Intelligence team, which further uncovered additional infrastructure and deconstructed the kit’s JavaScript. This analysis provided critical insights into the features and capabilities of the emerging PhaaS kit.
Investigation
An anomalous artifact identified during a customer investigation was escalated to the Threat Hunting team for analysis. Further examination revealed that this artifact was linked to a specific Phishing-as-a-Service (PhaaS) platform known as \'RaccoonO365\'. Promoted as a cutting-edge phishing toolkit, it uses a custom User Agent, domains mimicking Microsoft O365 services, and Cloudflare infrastructure. Including these findings in our threat-hunting queries led to two additional discoveries tallying three total detections across the customer fleet. The two proactive detections identified events received, but no alarms were triggered in the involved customer\'s LevelBlue USM Anywhere instances. The third reactive detection was a confirmed business email compromise (BEC), detected after triggering an alarm. The threat actor utilized the user agent \'RaccoonO365\' prior to the business email compromise detection meaning there was a short period of unauthorized access that went undetected. Each occurrence was triaged individually, and investigations were conducted in all three customer instances referring to the observed activity. Partnering with LevelBlue Labs, a new Correlation Rule was created to search specifically for a RaccoonO365 user agent within associated logs. In addition, the LevelBlue Labs team uncovered additional structural and descriptive features attributed to RaccoonO365, which later was turned into a Pulse Indicator of Compromise (IOC) detection.
Expanded Investigation
Alarm and USMA log review
1. An unrelated potential business email compromise (BEC) alarm was received and triaged by the LevelBlue MDR SOC. The identified user utilized a foreign VPN to successfully log into customer’s Microsoft Office environment. A custom alarm rule was created due to its high probability of being a True Positive. While conducting their investigation, they uncovered a suspicious user agent related to the compromised email address –RaccoonO365.
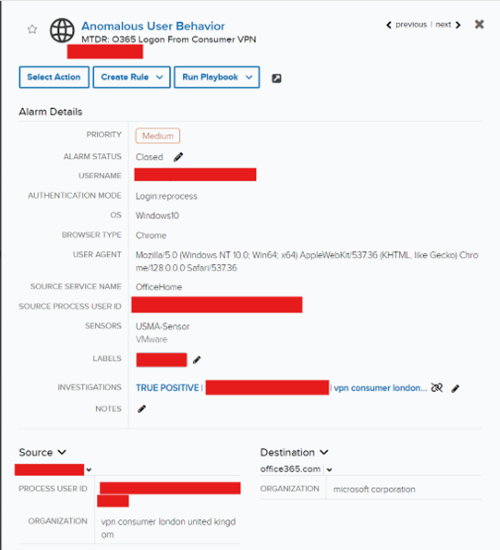 2. Information was passed off to LevelBlue Threat Hunters to conduct further internal and external research for the identified artifact.
2. Information was passed off to LevelBlue Threat Hunters to conduct further internal and external research for the identified artifact.
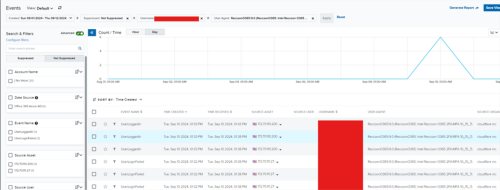 3. A dedicated threat hunter conducted a review of events including the subject user agent. Event logs were compared against each other and the successful logins provided additional key data points.
3. A dedicated threat hunter conducted a review of events including the subject user agent. Event logs were compared against each other and the successful logins provided additional key data points.
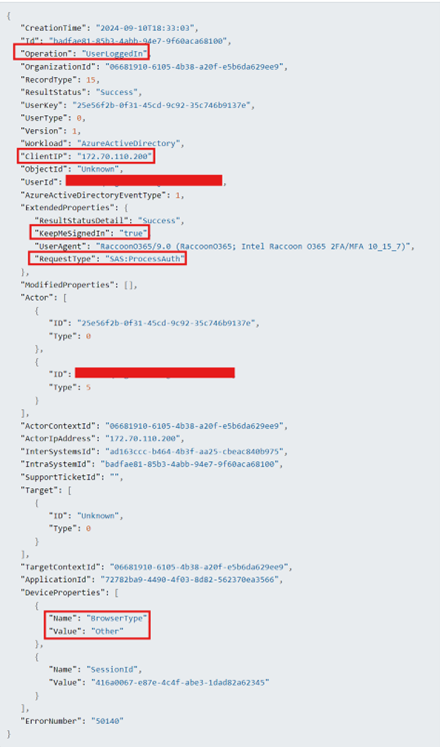 Shared Access Signature (SAS) authentication
"SAS authentication" refers to a method of user access control using a "Shared Access Signature" (SAS) token, which essentially grants temporary, limited access to specific resources within a cloud platform like Azure. This allows users to access data without directly sharing the full account access
Shared Access Signature (SAS) authentication
"SAS authentication" refers to a method of user access control using a "Shared Access Signature" (SAS) token, which essentially grants temporary, limited access to specific resources within a cloud platform like Azure. This allows users to access data without directly sharing the full account access |
| Notes | ★★★ |
| Envoyé | Oui |
| Condensat | $175 $250 $450—significantly $50 $75 $external $home “raccoono365/9 ‘azure ‘office ‘sign alert type –although –no –raccoono365 10: 10; 11: 12: 13: 14: 172 17th 2024 2fa/mfa 365 a’s aadsts50074 aadsts50097 aadsts50158 able access access/crawl accessibility accessible accessing account accounted accounting accounts across acted actions active activity activity’ actor actor’s adding addition additional address addressed admin administered adversary affected after against agent agent; agents aims aitm alarm alarms all allows alongside also alternate among analyses analysis ancillary anomalous another anti any anywhere appear appears application are artifact artifacts as13335 asn associated attack attack; attempting attempts attributed audit’ authenticate authentication automated available azure back base64 based bec become been behalf behaviors behind being below benefit between block blog blue bot bots broad browser budgets business but bypass campaign campaigns can capabilities captcha caught challenge challenges changed channel check checks checkvisitstatus chrome claiming classtype:web clicked closely cloud cloudflare cloudflare’s code collaboration collaborative com com com/ com/blog/raccoono365paas; common company compared completing comprehensive compromise compromised compromises concerned conduct conducted conducting config configuration confirmed consulted contain containing content: continue contributed control cookie cookies correlation corresponding coverage crafted created critical cryptographic curl custom customer customer’s customers cutting cybercriminals data day days debugging deceive decoded deconstructed deconstructing dedicated defending defenses denied dependent description descriptive designed detailing detect detected detecting detection detections developments device deviceauthenticationrequired devices did directly discounted discovered discoveries displays doc doccloudonedrivefiles docsoffice365 domain domains down drive due durations during dynamic dynamically each ecloud eclouddrivesharedfiles ecloudfileshare edge effective effectively either email emerging enabled encodedcontent encoding end enhance ensure enter enterprises entire enumerate environment escalated essentially event events evolution examination example executive expanded expanding expected expiration expires expiry external externalsecuritychallenge eyes factor failed failure fake false far fastpass features fenableshowresendcode figure file files filter filtering final findings firefox first fleet flow:established flows flows: focusing following foreign found free from full function functionality functions further generating gets give goal googlebot granted grants greatness growing guidance had handed handles hardcoded has help hex high highlighted hijacking hosted how however html html/javascript http https://ig3thack3d4u https://passwordreset human hunt hunter hunters hunters’ hunting identified identify ids image impersonate implement implemented in’ include included including incorporating increasingly indicate indicated indicative indicator indicators individually information infrastructure initial initially insightful insights instance instances intel intelligence internal investigation investigations involved ioc iocs ip/domain ips ishowresendcodedelay isp its javascript justification justifications key keywords kit kit’s kits known labs landing last later learning led legitimacy legitimate less levelblue leveraging license like limited link linked list listed lists loads log logging login logins logs longer longevity looks machine main makers making malicious manage managed many mdr meaning message metadata:created method mfa microsoft microsoftonline middle mimicking mitigate mobile model models monitored monitoring month months morado more msg: multi name names net network new newly not notblocked notifications notorious now o365 obfuscation observed occurrence occurrences off offering offerings offic |
| Tags | Tool Threat Mobile Cloud |
| Stories | |
| Move | 

|
L'article ne semble pas avoir été repris aprés sa publication.
L'article ne semble pas avoir été repris sur un précédent.