What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2022-11-17 13:01:13 | Get a Loda This: LodaRAT meets new friends (lien direct) | LodaRAT samples were deployed alongside other malware families, including RedLine and Neshta.Cisco Talos identified several variants and altered versions of LodaRAT with updated functionality have been identified in the wild.Changes in these LodaRAT variants include new functionality allowing proliferation to attached removable storage, a new string encoding algorithm | Malware | |||
| 2022-11-09 13:00:17 | Threat Spotlight: Cyber Criminal Adoption of IPFS for Phishing, Malware Campaigns (lien direct) | The InterPlanetary File System (IPFS) is an emerging Web3 technology that is currently seeing widespread abuse by threat actors.Cisco Talos has observed multiple ongoing campaigns that leverage the IPFS network to host their malware payloads and phishing kit infrastructure while facilitating other attacks.IPFS is often used for legitimate | Malware Threat | |||
| 2022-10-13 08:00:07 | Alchimist: A new attack framework in Chinese for Mac, Linux and Windows (lien direct) |  By Chetan Raghuprasad, Asheer Malhotra and Vitor Ventura, with contributions from Matt Thaxton.Cisco Talos discovered a new attack framework including a command and control (C2) tool called "Alchimist" and a new malware "Insekt" with remote administration capabilities.The Alchimist has a web interface in Simplified Chinese with remote administration features.The attack framework is designed to target Windows, Linux and Mac machines. Alchimist and Insekt binaries are implemented in GoLang.This campaign consists of additional bespoke tools such as a MacOS exploitation tool, a custom backdoor and multiple off-the-shelf tools such as reverse proxies. Cisco Talos has discovered a new single-file command and control (C2) framework the authors call "Alchimist [sic]." Talos researchers found this C2 on a server that had a file listing active on the root directory along with a set of post-exploitation tools.Cisco Talos assesses with moderate-high confidence that this framework is being used in the wild. "Alchimist" is a 64-bit Linux executable written in GoLang and packed with assets including resources for the web interface and Insekt RAT payloads compiled for Windows and Linux. Insekt RAT, a new trojan Cisco Talos discovered, is Alchimist's beacon implant written in GoLang and has a variety of remote access capabilities that can be instrumented by the Alchimist C2 server.Alchimist C2 has a web interface written in Simplified Chinese and can generate a configured payload, establish remote sessions, deploy payload to the remote machines, capture screenshots, perform remote shellcode execution and run arbitrary commands. Among the remaining tools, Cisco Talos found a Mach-O dropper embedded with an exploit to target a known vulnerability CVE-2021-4034, a privilege escalation issue in polkit's pkexec utility, and a Mach-O bind shell backdoor. The Qualys Research Team discovered CVE-2021-4034 in November 2021, and in January 2022, the U.S.'s National Security Agency Cybersecurity Director warned that the vulnerability was being exploited in the wild. The server also contained dual-use tools like psexec and netcat, along with a scanning tool called "fscan," which the author defines as an "intranet scanning tool," essentially all the necessary tools for lateral movement. Alchimist framework The attack framework we discovered during the course of this research consists of a standalone C2 server called "Alchimist" and its corresponding implants the authors call the "Insekt" RAT family.Alchimist isn't the first self-contained framework we've discovered recently, with Manjusaka being another single file-based C2 framework disclosed by Talos recently. Both follow the same design philosophy, albeit implemented in different ways, to the point where they both seem to have the same list of requirements despite being implemented by different programmers. However, Manjusaka and Alchimist have virtually the same set of feat By Chetan Raghuprasad, Asheer Malhotra and Vitor Ventura, with contributions from Matt Thaxton.Cisco Talos discovered a new attack framework including a command and control (C2) tool called "Alchimist" and a new malware "Insekt" with remote administration capabilities.The Alchimist has a web interface in Simplified Chinese with remote administration features.The attack framework is designed to target Windows, Linux and Mac machines. Alchimist and Insekt binaries are implemented in GoLang.This campaign consists of additional bespoke tools such as a MacOS exploitation tool, a custom backdoor and multiple off-the-shelf tools such as reverse proxies. Cisco Talos has discovered a new single-file command and control (C2) framework the authors call "Alchimist [sic]." Talos researchers found this C2 on a server that had a file listing active on the root directory along with a set of post-exploitation tools.Cisco Talos assesses with moderate-high confidence that this framework is being used in the wild. "Alchimist" is a 64-bit Linux executable written in GoLang and packed with assets including resources for the web interface and Insekt RAT payloads compiled for Windows and Linux. Insekt RAT, a new trojan Cisco Talos discovered, is Alchimist's beacon implant written in GoLang and has a variety of remote access capabilities that can be instrumented by the Alchimist C2 server.Alchimist C2 has a web interface written in Simplified Chinese and can generate a configured payload, establish remote sessions, deploy payload to the remote machines, capture screenshots, perform remote shellcode execution and run arbitrary commands. Among the remaining tools, Cisco Talos found a Mach-O dropper embedded with an exploit to target a known vulnerability CVE-2021-4034, a privilege escalation issue in polkit's pkexec utility, and a Mach-O bind shell backdoor. The Qualys Research Team discovered CVE-2021-4034 in November 2021, and in January 2022, the U.S.'s National Security Agency Cybersecurity Director warned that the vulnerability was being exploited in the wild. The server also contained dual-use tools like psexec and netcat, along with a scanning tool called "fscan," which the author defines as an "intranet scanning tool," essentially all the necessary tools for lateral movement. Alchimist framework The attack framework we discovered during the course of this research consists of a standalone C2 server called "Alchimist" and its corresponding implants the authors call the "Insekt" RAT family.Alchimist isn't the first self-contained framework we've discovered recently, with Manjusaka being another single file-based C2 framework disclosed by Talos recently. Both follow the same design philosophy, albeit implemented in different ways, to the point where they both seem to have the same list of requirements despite being implemented by different programmers. However, Manjusaka and Alchimist have virtually the same set of feat |
Malware Tool Vulnerability Threat | |||
| 2022-10-04 08:51:05 | Developer account body snatchers pose risks to the software supply chain (lien direct) |  By Jaeson Schultz.Over the past several years, high-profile software supply chain attacks have increased in frequency. These attacks can be difficult to detect and source code repositories became a key focus of this research.Developer account takeovers present a substantial risk to the software supply chain because attackers who successfully compromise a developer account could conceal malicious code in software packages used by others.Talos analyzed several of the major software repositories to assess the level of developer account security, focusing specifically on whether developer accounts could be recovered by re-registering expired domain names and triggering password resets.Many software repositories have already begun taking steps to enhance the security of developer accounts. Talos has identified additional areas where the security of developer accounts could be improved. Talos worked with vulnerable repositories to resolve issues that we found. Software supply chain attacks, once the exclusive province of sophisticated state-sponsored attackers, have been gaining popularity recently among a broader range of cyber criminals. Attackers everywhere have realized that software supply chain attacks can be very effective, and can result in a large number of compromised victims. Software supply chain attacks more than tripled in 2021 when compared with 2020. Why are software supply chain attacks so effective? Organizations that possess solid cyber defenses may be difficult to attack directly. However, these same organizations are likely vulnerable to a software supply chain attack because they still regularly run/build software obtained from vendors who are trusted.Rather than attacking an entire software repository itself, or identifying an unpatched vulnerability in a software package, compromising the software supply chain can be as simple as attacking the accounts of the package developers and maintainers. Most software repositories track the identities of their software developers using those developers' email addresses. If a cybercriminal somehow gains access to a developer's email account, the attacker can theoretically generate password reset emails at these software repositories a By Jaeson Schultz.Over the past several years, high-profile software supply chain attacks have increased in frequency. These attacks can be difficult to detect and source code repositories became a key focus of this research.Developer account takeovers present a substantial risk to the software supply chain because attackers who successfully compromise a developer account could conceal malicious code in software packages used by others.Talos analyzed several of the major software repositories to assess the level of developer account security, focusing specifically on whether developer accounts could be recovered by re-registering expired domain names and triggering password resets.Many software repositories have already begun taking steps to enhance the security of developer accounts. Talos has identified additional areas where the security of developer accounts could be improved. Talos worked with vulnerable repositories to resolve issues that we found. Software supply chain attacks, once the exclusive province of sophisticated state-sponsored attackers, have been gaining popularity recently among a broader range of cyber criminals. Attackers everywhere have realized that software supply chain attacks can be very effective, and can result in a large number of compromised victims. Software supply chain attacks more than tripled in 2021 when compared with 2020. Why are software supply chain attacks so effective? Organizations that possess solid cyber defenses may be difficult to attack directly. However, these same organizations are likely vulnerable to a software supply chain attack because they still regularly run/build software obtained from vendors who are trusted.Rather than attacking an entire software repository itself, or identifying an unpatched vulnerability in a software package, compromising the software supply chain can be as simple as attacking the accounts of the package developers and maintainers. Most software repositories track the identities of their software developers using those developers' email addresses. If a cybercriminal somehow gains access to a developer's email account, the attacker can theoretically generate password reset emails at these software repositories a |
Malware Vulnerability | |||
| 2022-09-30 17:16:47 | Threat Advisory: Microsoft warns of actively exploited vulnerabilities in Exchange Server (lien direct) |  Cisco Talos has released new coverage to detect and prevent the exploitation of two recently disclosed vulnerabilities collectively referred to as "ProxyNotShell," affecting Microsoft Exchange Servers 2013, 2016 and 2019. One of these vulnerabilities could allow an attacker to execute remote code on the targeted server. Limited exploitation of these vulnerabilities in the wild has been reported. CVE-2022-41040 is a Server Side Request Forgery (SSRF) vulnerability, while CVE-2022-41082 enables Remote Code Execution (RCE) when PowerShell is accessible to the attackers. While no fixes or patches are available yet, Microsoft has provided mitigations for on-premises Microsoft Exchange users on Sept. 29, 2022. Even organizations that use Exchange Online may still be affected if they run a hybrid server. Cisco Talos is closely monitoring the recent reports of exploitation attempts against these vulnerabilities and strongly recommends users implement mitigation steps while waiting for security patches for these vulnerabilities. Exchange vulnerabilities have become increasingly popular with threat actors, as they can provide initial access to network environments and are often used to facilitate more effective phishing and malspam campaigns. The Hafnium threat actor exploited several zero-day vulnerabilities in Exchange Server in 2021 to deliver ransomware, and Cisco Talos Incident Response reported that the exploitation of Exchange Server issues was one of the four attacks they saw most often last year.Vulnerability details and ongoing exploitationExploit requests for these vulnerabilities look similar to previously discovered ProxyShell exploitation attempts:autodiscover/autodiscover.json?@evil.com/&Email=autodiscover/autodiscover.json%3f@evil.comSuccessful exploitation of the vulnerabilities observed in the wild leads to preliminary information-gathering operations and the persistence of WebShells for continued access to compromised servers. Open-source reporting indicates that webShells such as Antsword, a popular Chinese language-based open-source webshell, SharPyShell an ASP.NET-based webshell and China Chopper have been deployed on compromised systems consisting of the following artifacts:C:\inetpub\wwwroot\aspnet_client\Xml.ashxC:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\errorEE.aspxC:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\pxh4HG1v.ashxC:\Program Files\Microsoft\Exchange Server\V15 Cisco Talos has released new coverage to detect and prevent the exploitation of two recently disclosed vulnerabilities collectively referred to as "ProxyNotShell," affecting Microsoft Exchange Servers 2013, 2016 and 2019. One of these vulnerabilities could allow an attacker to execute remote code on the targeted server. Limited exploitation of these vulnerabilities in the wild has been reported. CVE-2022-41040 is a Server Side Request Forgery (SSRF) vulnerability, while CVE-2022-41082 enables Remote Code Execution (RCE) when PowerShell is accessible to the attackers. While no fixes or patches are available yet, Microsoft has provided mitigations for on-premises Microsoft Exchange users on Sept. 29, 2022. Even organizations that use Exchange Online may still be affected if they run a hybrid server. Cisco Talos is closely monitoring the recent reports of exploitation attempts against these vulnerabilities and strongly recommends users implement mitigation steps while waiting for security patches for these vulnerabilities. Exchange vulnerabilities have become increasingly popular with threat actors, as they can provide initial access to network environments and are often used to facilitate more effective phishing and malspam campaigns. The Hafnium threat actor exploited several zero-day vulnerabilities in Exchange Server in 2021 to deliver ransomware, and Cisco Talos Incident Response reported that the exploitation of Exchange Server issues was one of the four attacks they saw most often last year.Vulnerability details and ongoing exploitationExploit requests for these vulnerabilities look similar to previously discovered ProxyShell exploitation attempts:autodiscover/autodiscover.json?@evil.com/&Email=autodiscover/autodiscover.json%3f@evil.comSuccessful exploitation of the vulnerabilities observed in the wild leads to preliminary information-gathering operations and the persistence of WebShells for continued access to compromised servers. Open-source reporting indicates that webShells such as Antsword, a popular Chinese language-based open-source webshell, SharPyShell an ASP.NET-based webshell and China Chopper have been deployed on compromised systems consisting of the following artifacts:C:\inetpub\wwwroot\aspnet_client\Xml.ashxC:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\errorEE.aspxC:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\pxh4HG1v.ashxC:\Program Files\Microsoft\Exchange Server\V15 |
Malware Threat Guideline | |||
| 2022-09-28 08:18:45 | New campaign uses government, union-themed lures to deliver Cobalt Strike beacons (lien direct) |  By Chetan Raghuprasad and Vanja Svajcer. Cisco Talos discovered a malicious campaign in August 2022 delivering Cobalt Strike beacons that could be used in later, follow-on attacks.Lure themes in the phishing documents in this campaign are related to the job details of a government organization in the United States and a trade union in New Zealand. The attack involves a multistage and modular infection chain with fileless, malicious scripts. Cisco Talos recently discovered a malicious campaign with a modularised attack technique to deliver Cobalt Strike beacons on infected endpoints. The initial vector of this attack is a phishing email with a malicious Microsoft Word document attachment containing an exploit that attempts to exploit the vulnerability CVE-2017-0199, a remote code execution issue in Microsoft Office. If a victim opens the maldoc, it downloads a malicious Word document template hosted on an attacker-controlled Bitbucket repository. Talos discovered two attack methodologies employed by the attacker in this campaign: One in which the downloaded DOTM template executes an embedded malicious Visual Basic script, which leads to the generation and execution of other obfuscated VB and PowerShell scripts and another that involves the malicious VB downloading and running a Windows executable that executes malicious PowerShell commands to download and implant the payload. The payload discovered is a leaked version of a Cobalt Strike beacon. The beacon configuration contains commands to perform targeted process injection of arbitrary binaries and has a high reputation domain configured, exhibiting the redirection technique to masquerade the beacon's traffic. Although the payload discovered in this campaign is a Cobalt Strike beacon, Talos also observed usage of the Redline information-stealer and Amadey botnet executables as payloads. This campaign is a typical example of a threat actor using the technique of generating and executing malicious scripts in the victim's system memory. Defenders should implement behavioral protection capabilities in the organization's defense to effectively protect them against fileless threats. Organizations should be constantly vigilant on the Cobalt Strike beacons and implement layered defense capabilities to thwart the attacker's attempts in the earlier stage of the attack's infection chain. Initial vectorThe initial infection email is themed to entice the recipient to review the attached Word document and provide some of their personal information. By Chetan Raghuprasad and Vanja Svajcer. Cisco Talos discovered a malicious campaign in August 2022 delivering Cobalt Strike beacons that could be used in later, follow-on attacks.Lure themes in the phishing documents in this campaign are related to the job details of a government organization in the United States and a trade union in New Zealand. The attack involves a multistage and modular infection chain with fileless, malicious scripts. Cisco Talos recently discovered a malicious campaign with a modularised attack technique to deliver Cobalt Strike beacons on infected endpoints. The initial vector of this attack is a phishing email with a malicious Microsoft Word document attachment containing an exploit that attempts to exploit the vulnerability CVE-2017-0199, a remote code execution issue in Microsoft Office. If a victim opens the maldoc, it downloads a malicious Word document template hosted on an attacker-controlled Bitbucket repository. Talos discovered two attack methodologies employed by the attacker in this campaign: One in which the downloaded DOTM template executes an embedded malicious Visual Basic script, which leads to the generation and execution of other obfuscated VB and PowerShell scripts and another that involves the malicious VB downloading and running a Windows executable that executes malicious PowerShell commands to download and implant the payload. The payload discovered is a leaked version of a Cobalt Strike beacon. The beacon configuration contains commands to perform targeted process injection of arbitrary binaries and has a high reputation domain configured, exhibiting the redirection technique to masquerade the beacon's traffic. Although the payload discovered in this campaign is a Cobalt Strike beacon, Talos also observed usage of the Redline information-stealer and Amadey botnet executables as payloads. This campaign is a typical example of a threat actor using the technique of generating and executing malicious scripts in the victim's system memory. Defenders should implement behavioral protection capabilities in the organization's defense to effectively protect them against fileless threats. Organizations should be constantly vigilant on the Cobalt Strike beacons and implement layered defense capabilities to thwart the attacker's attempts in the earlier stage of the attack's infection chain. Initial vectorThe initial infection email is themed to entice the recipient to review the attached Word document and provide some of their personal information.  Initial malicious email message.The maldocs have lures containing text related to the collection of personally identifiable information (PII) which is used to determ Initial malicious email message.The maldocs have lures containing text related to the collection of personally identifiable information (PII) which is used to determ |
Malware Vulnerability Threat Guideline | |||
| 2022-09-15 08:02:21 | Gamaredon APT targets Ukrainian government agencies in new campaign (lien direct) |  By Asheer Malhotra and Guilherme Venere.Cisco Talos recently identified a new, ongoing campaign attributed to the Russia-linked Gamaredon APT that infects Ukrainian users with information-stealing malware.The adversary is using phishing documents containing lures related to the Russian invasion of Ukraine.LNK files, PowerShell and VBScript enable initial access, while malicious binaries are deployed in the post-infection phase.We discovered the use of a custom-made information stealer implant that can exfiltrate victim files of interest and deploy additional payloads as directed by the attackers. Cisco Talos discovered Gamaredon APT activity targeting users in Ukraine with malicious LNK files distributed in RAR archives. The campaign, part of an ongoing espionage operation observed as recently as August 2022, aims to deliver information-stealing malware to Ukrainian victim machines and makes heavy use of multiple modular PowerShell and VBScript (VBS) scripts as part of the infection chain. The infostealer is a dual-purpose malware that includes capabilities for exfiltrating specific file types and deploying additional binary and script-based payloads on an infected endpoint. The adversary uses phishing emails to deliver Microsoft Office documents containing remote templates with malicious VBScript macros. These macros download and open RAR archives containing LNK files that subsequently download and activate the next-stage payload on the infected endpoint. We observed considerable overlap between the tactics, techniques and procedures (TTPs), malware artifacts and infrastructure used in this campaign and those used in a series of attacks the Ukraine Computer Emergency Response Team (CERT-UA) recently attributed to Gamaredon.We also observed intrusion attempts against several Ukrainian entities. Based on these observations and Gamaredon's operational history of almost exclusively targeting Ukraine, we assess that this latest campaign is almost certainly directly targeting entities based in Ukraine. By Asheer Malhotra and Guilherme Venere.Cisco Talos recently identified a new, ongoing campaign attributed to the Russia-linked Gamaredon APT that infects Ukrainian users with information-stealing malware.The adversary is using phishing documents containing lures related to the Russian invasion of Ukraine.LNK files, PowerShell and VBScript enable initial access, while malicious binaries are deployed in the post-infection phase.We discovered the use of a custom-made information stealer implant that can exfiltrate victim files of interest and deploy additional payloads as directed by the attackers. Cisco Talos discovered Gamaredon APT activity targeting users in Ukraine with malicious LNK files distributed in RAR archives. The campaign, part of an ongoing espionage operation observed as recently as August 2022, aims to deliver information-stealing malware to Ukrainian victim machines and makes heavy use of multiple modular PowerShell and VBScript (VBS) scripts as part of the infection chain. The infostealer is a dual-purpose malware that includes capabilities for exfiltrating specific file types and deploying additional binary and script-based payloads on an infected endpoint. The adversary uses phishing emails to deliver Microsoft Office documents containing remote templates with malicious VBScript macros. These macros download and open RAR archives containing LNK files that subsequently download and activate the next-stage payload on the infected endpoint. We observed considerable overlap between the tactics, techniques and procedures (TTPs), malware artifacts and infrastructure used in this campaign and those used in a series of attacks the Ukraine Computer Emergency Response Team (CERT-UA) recently attributed to Gamaredon.We also observed intrusion attempts against several Ukrainian entities. Based on these observations and Gamaredon's operational history of almost exclusively targeting Ukraine, we assess that this latest campaign is almost certainly directly targeting entities based in Ukraine. Attack ChainInitial AccessGamaredon APT actors likely gained initial footholds into targeted networks through malicious Microsoft Office documents distributed via email. This is consistent with spear-phishing techniques common to this APT. Malicious VBS macros concealed within remote templates execute when the user opens the document. The macros download RAR archives containing LNK files. The naming convention of the RAR archives in this campaign follows a similar pattern:31.07.2022.rar04.08.2022.rar Attack ChainInitial AccessGamaredon APT actors likely gained initial footholds into targeted networks through malicious Microsoft Office documents distributed via email. This is consistent with spear-phishing techniques common to this APT. Malicious VBS macros concealed within remote templates execute when the user opens the document. The macros download RAR archives containing LNK files. The naming convention of the RAR archives in this campaign follows a similar pattern:31.07.2022.rar04.08.2022.rar |
Malware Threat | |||
| 2022-09-08 08:39:42 | Lazarus and the tale of three RATs (lien direct) |  By Jung soo An, Asheer Malhotra and Vitor Ventura.Cisco Talos has been tracking a new campaign operated by the Lazarus APT group, attributed to North Korea by the United States government. This campaign involved the exploitation of vulnerabilities in VMWare Horizon to gain an initial foothold into targeted organizations.Targeted organizations include energy providers from around the world, including those headquartered in the United States, Canada and Japan. The campaign is meant to infiltrate organizations around the world for establishing long term access and subsequently exfiltrating data of interest to the adversary's nation-state.Talos has discovered the use of two known families of malware in these intrusions - VSingle and YamaBot.Talos has also discovered the use of a recently disclosed implant we're calling "MagicRAT" in this campaign. IntroductionCisco Talos observed North Korean state-sponsored APT Lazarus Group conducting malicious activity between February and July 2022. Lazarus has been previously attributed to the North Korean government by the U.S. Cybersecurity and Infrastructure Security Agency (CISA). The entry vectors involve the successful exploitation of vulnerabilities in VMWare products to establish initial footholds into enterprise networks, followed by the deployment of the group's custom malware implants, VSingle and YamaBot. In addition to these known malware families, we have also discovered the use of a previously unknown malware implant we're calling "MagicRAT."This campaign was previously partially disclosed by other security firms, but our findings reveal more details about the adversary's modus operandi. We have also observed an overlap of command and control (C2) and payload-hosting infrastructure between our findings and the U.S. Cybersecurity and Infrastructure Security Agency's (CISA) June advisory that detailed continued attempts from threat actors to compromise vulnerable VMWare Horizon servers.In this research, we illustrate Lazarus Group's post-exploitation tactics, techniques and procedures (TTPs) to establish a foothold, perform initial reconnaissance, deploy bespoke malware and move laterally across infected enterprises. We also provide details about the activities performed by the attackers when the VSingle backdoor is instrumented on the infected endpoints.In this campaign, Lazarus was primarily targeting energy companies in Canada, the U.S. and Japan. The main goal of these attacks was likely to establish long-term access into victim networks to conduct espionage operations in support of North Korean govern By Jung soo An, Asheer Malhotra and Vitor Ventura.Cisco Talos has been tracking a new campaign operated by the Lazarus APT group, attributed to North Korea by the United States government. This campaign involved the exploitation of vulnerabilities in VMWare Horizon to gain an initial foothold into targeted organizations.Targeted organizations include energy providers from around the world, including those headquartered in the United States, Canada and Japan. The campaign is meant to infiltrate organizations around the world for establishing long term access and subsequently exfiltrating data of interest to the adversary's nation-state.Talos has discovered the use of two known families of malware in these intrusions - VSingle and YamaBot.Talos has also discovered the use of a recently disclosed implant we're calling "MagicRAT" in this campaign. IntroductionCisco Talos observed North Korean state-sponsored APT Lazarus Group conducting malicious activity between February and July 2022. Lazarus has been previously attributed to the North Korean government by the U.S. Cybersecurity and Infrastructure Security Agency (CISA). The entry vectors involve the successful exploitation of vulnerabilities in VMWare products to establish initial footholds into enterprise networks, followed by the deployment of the group's custom malware implants, VSingle and YamaBot. In addition to these known malware families, we have also discovered the use of a previously unknown malware implant we're calling "MagicRAT."This campaign was previously partially disclosed by other security firms, but our findings reveal more details about the adversary's modus operandi. We have also observed an overlap of command and control (C2) and payload-hosting infrastructure between our findings and the U.S. Cybersecurity and Infrastructure Security Agency's (CISA) June advisory that detailed continued attempts from threat actors to compromise vulnerable VMWare Horizon servers.In this research, we illustrate Lazarus Group's post-exploitation tactics, techniques and procedures (TTPs) to establish a foothold, perform initial reconnaissance, deploy bespoke malware and move laterally across infected enterprises. We also provide details about the activities performed by the attackers when the VSingle backdoor is instrumented on the infected endpoints.In this campaign, Lazarus was primarily targeting energy companies in Canada, the U.S. and Japan. The main goal of these attacks was likely to establish long-term access into victim networks to conduct espionage operations in support of North Korean govern |
Malware Tool Vulnerability Threat Medical | APT 38 | ||
| 2022-09-07 08:01:43 | MagicRAT: Lazarus\' latest gateway into victim networks (lien direct) |  By Jung soo An, Asheer Malhotra and Vitor Ventura.Cisco Talos has discovered a new remote access trojan (RAT) we're calling "MagicRAT," developed and operated by the Lazarus APT group, which the U.S. government believes is a North Korean state-sponsored actor.Lazarus deployed MagicRAT after the successful exploitation of vulnerabilities in VMWare Horizon platforms.We've also found links between MagicRAT and another RAT known as "TigerRAT," disclosed and attributed to Lazarus by the Korean Internet & Security Agency (KISA) recently.TigerRAT has evolved over the past year to include new functionalities that we illustrate in this blog. Executive SummaryCisco Talos has discovered a new remote access trojan (RAT), which we are calling "MagicRAT," that we are attributing with moderate to high confidence to the Lazarus threat actor, a state-sponsored APT attributed to North Korea by the U.S. Cyber Security & Infrastructure Agency (CISA). This new RAT was found on victims that had been initially compromised through the exploitation of publicly exposed VMware Horizon platforms. While being a relatively simple RAT capability-wise, it was built with recourse to the Qt Framework, with the sole intent of making human analysis harder, and automated detection through machine learning and heuristics less likely.We have also found evidence to suggest that once MagicRAT is deployed on infected systems, it launches additional payloads such as custom-built port scanners. Additionally, we've found that MagicRAT's C2 infrastructure was also used to host newer variants of known Lazarus implants such as TigerRAT. The discovery of MagicRAT in the wild is an indication of Lazarus' motivations to rapidly build new, bespoke malware to use along with their previously known malware such as TigerRAT to target organizations worldwide.Actor profile By Jung soo An, Asheer Malhotra and Vitor Ventura.Cisco Talos has discovered a new remote access trojan (RAT) we're calling "MagicRAT," developed and operated by the Lazarus APT group, which the U.S. government believes is a North Korean state-sponsored actor.Lazarus deployed MagicRAT after the successful exploitation of vulnerabilities in VMWare Horizon platforms.We've also found links between MagicRAT and another RAT known as "TigerRAT," disclosed and attributed to Lazarus by the Korean Internet & Security Agency (KISA) recently.TigerRAT has evolved over the past year to include new functionalities that we illustrate in this blog. Executive SummaryCisco Talos has discovered a new remote access trojan (RAT), which we are calling "MagicRAT," that we are attributing with moderate to high confidence to the Lazarus threat actor, a state-sponsored APT attributed to North Korea by the U.S. Cyber Security & Infrastructure Agency (CISA). This new RAT was found on victims that had been initially compromised through the exploitation of publicly exposed VMware Horizon platforms. While being a relatively simple RAT capability-wise, it was built with recourse to the Qt Framework, with the sole intent of making human analysis harder, and automated detection through machine learning and heuristics less likely.We have also found evidence to suggest that once MagicRAT is deployed on infected systems, it launches additional payloads such as custom-built port scanners. Additionally, we've found that MagicRAT's C2 infrastructure was also used to host newer variants of known Lazarus implants such as TigerRAT. The discovery of MagicRAT in the wild is an indication of Lazarus' motivations to rapidly build new, bespoke malware to use along with their previously known malware such as TigerRAT to target organizations worldwide.Actor profile |
Malware Threat Medical | APT 38 | ★★★ | |
| 2022-09-06 08:00:00 | Researcher Spotlight: How Asheer Malhotra looks for \'instant gratification\' in threat hunting (lien direct) | The India native has transitioned from a reverse-engineer hobbyist to a public speaker in just a few years By Jon Munshaw. Ninety percent of Asheer Malhotra's work will never see the light of day. But it's that 10 percent that keeps him motivated to keep looking for something new. The Talos Outreach researcher spends most of his days looking into potential new threats. Many times, that leads to dead ends of threats that have already been discovered and blocked or don't have any additional threads to pull on. But eventually, the “lightbulb goes off,” as he puts it, which indicates something is a new threat the wider public needs to know about. During his time at Talos, Malhotra has spent much of his time looking into cyber attacks and state-sponsored threat actors in Asia, like the Transparent Tribe group he's written about several times. “At some point, I say 'Hey, I don't think I've seen this before.' I start analyzing public disclosures, and slowly start gaining confidence and being able to craft a narrative around the motivations and tactics around a specific threat actor or malware campaign,” he said. In the case of Transparent Tribe, Malhotra's tracked their growth as a major player in the threat landscape in Asia, as they've added several remote access trojans to their arsenal, targeted high-profile government-adjacent entities in India and expanded their scope across the region. When he's not threat hunting, Malhotra also speaks to Cisco customers about the current state of cybersecurity in briefings and delivers presentations at conferences around the world (mainly virtually during the COVID-19 pandemic).  “I always try to find the latest and new stuff to talk about. … I've been honing my skills and trying to speak more confidently publicly, but the confidence is backed up with the right kind of knowledge and the threat intelligence, that's what helps me succeed,” he said. Malhotra is a native of India and spent most of his life there before coming to the U.S. for his master's degree at Mississippi State University. Mississippi was a far cry from everything else he had known up until that point, but he quickly adjusted. “That was the 'Deep South,'” he said. “So there was a culture shock, but the southern hospitality is such a real thing, and it felt very normal there.” Growing up, Malhotra always knew he wanted to work with computers, starting out as a teenager reverse-engineering exploits he'd see others talk about on the internet or just poking at smaller applications. His additional interest in politics and national security made it natural for him to combine the two and focus his research on state-sponsored actors. He enjoys continuing his research in the Indian subcontinent and sees many parallels between the state of security in India and the U.S. “Th “I always try to find the latest and new stuff to talk about. … I've been honing my skills and trying to speak more confidently publicly, but the confidence is backed up with the right kind of knowledge and the threat intelligence, that's what helps me succeed,” he said. Malhotra is a native of India and spent most of his life there before coming to the U.S. for his master's degree at Mississippi State University. Mississippi was a far cry from everything else he had known up until that point, but he quickly adjusted. “That was the 'Deep South,'” he said. “So there was a culture shock, but the southern hospitality is such a real thing, and it felt very normal there.” Growing up, Malhotra always knew he wanted to work with computers, starting out as a teenager reverse-engineering exploits he'd see others talk about on the internet or just poking at smaller applications. His additional interest in politics and national security made it natural for him to combine the two and focus his research on state-sponsored actors. He enjoys continuing his research in the Indian subcontinent and sees many parallels between the state of security in India and the U.S. “Th |
Ransomware Malware Threat Guideline | APT 36 | ||
| 2022-08-30 08:00:09 | ModernLoader delivers multiple stealers, cryptominers and RATs (lien direct) |  By Vanja SvajcerCisco Talos recently observed three separate, but related, campaigns between March and June 2022 delivering a variety of threats, including the ModernLoader bot, RedLine information-stealer and cryptocurrency-mining malware to victims. The actors use PowerShell, .NET assemblies, and HTA and VBS files to spread across a targeted network, eventually dropping other pieces of malware, such as the SystemBC trojan and DCRAT, to enable various stages of their operations. The attackers' use of a variety of off-the-shelf tools makes it difficult to attribute this activity to a specific adversary.The final payload appears to be ModernLoader, which acts as a remote access trojan (RAT) by collecting system information and deploying various modules. In the earlier campaigns from March, we also observed the attackers delivering the cryptocurrency mining malware XMRig. The March campaigns appeared to be targeting Eastern European users, as the constructor utility we analyzed had predefined script templates written in Bulgarian, Polish, Hungarian and Russian.The actors are attempting to compromise vulnerable web applications to serve malware and deliver threats via files masquerading as fake Amazon gift cards. Technical detailsInitial findingsIn June 2022, Cisco Talos identified an unusual command line execution in our telemetry. The decoded base64 command is below: By Vanja SvajcerCisco Talos recently observed three separate, but related, campaigns between March and June 2022 delivering a variety of threats, including the ModernLoader bot, RedLine information-stealer and cryptocurrency-mining malware to victims. The actors use PowerShell, .NET assemblies, and HTA and VBS files to spread across a targeted network, eventually dropping other pieces of malware, such as the SystemBC trojan and DCRAT, to enable various stages of their operations. The attackers' use of a variety of off-the-shelf tools makes it difficult to attribute this activity to a specific adversary.The final payload appears to be ModernLoader, which acts as a remote access trojan (RAT) by collecting system information and deploying various modules. In the earlier campaigns from March, we also observed the attackers delivering the cryptocurrency mining malware XMRig. The March campaigns appeared to be targeting Eastern European users, as the constructor utility we analyzed had predefined script templates written in Bulgarian, Polish, Hungarian and Russian.The actors are attempting to compromise vulnerable web applications to serve malware and deliver threats via files masquerading as fake Amazon gift cards. Technical detailsInitial findingsIn June 2022, Cisco Talos identified an unusual command line execution in our telemetry. The decoded base64 command is below: Initial finding: A command executed on the system.The 31.41.244[.]231 IP is a Russian IP and hosts several other URLs with similar naming conventions. Autostart commandFollowing the discovery of the initial command, we identified two other command lines. They are a result of an autorun registered executable and the execution of a scheduled task. Initial finding: A command executed on the system.The 31.41.244[.]231 IP is a Russian IP and hosts several other URLs with similar naming conventions. Autostart commandFollowing the discovery of the initial command, we identified two other command lines. They are a result of an autorun registered executable and the execution of a scheduled task. |
Malware Tool Threat | Yahoo | ||
| 2022-08-24 12:50:34 | Ukraine Independence Day: Talos update (lien direct) | On Independence Day for Ukraine, Aug. 24, 2022, Cisco Talos provided a live update on its continued support for the region. Six months since the invasion of Russia's invasion of Ukraine, Dmytro Korzhevin, a senior threat intelligence researcher, JJ Cummings, Talos' national intelligence principal, and Ashlee Benge, a strategic intelligence lead, provided insights into their past few months of work in the region.The discussion primarily focused on the resiliency of Ukrainians, who have worked tirelessly over the years to transform their cybersecurity capabilities. Ukrainian infrastructure has largely stayed operational and, in most cases, exceeded expectations. It seems to have baffled most pundits, but for those that have spent years working in Ukraine, it's no surprise about the levels of dedication and commitment to protecting their critical infrastructure from those that would do it harm. The team also covered how groundwork laid years ago is paying dividends now during the war, as well as an update on the types of cyber threats we're observing, including the deployment of the GoMet backdoor. At the beginning of the broadcast, Korzhevin shared what Independence Day of Ukraine means for him. "Independence is not an extra day off, but a value that should be used for the benefit of every citizen of our country," he added after the stream. "Independence is the will. Independence lives in every person. If we are independent, it means that we are free. That is, we live, not exist. The same goes for the state. Independence of Ukraine is when we have the possibility to develop the state as we want it and not as we are told when we have a real own history and not a twisted one when we speak our native language and not a hostile one. And now that there is a war in Ukraine, the most important task of our people is to preserve Independence. So that we, our children, grandchildren and all future generations of Ukrainians could live and build our state based on national traditions and core democratic values. Independence is primarily a way, not a condition. I believe that we will overcome all the difficulties in this way."Bengee added that Cisco and Talos have several resources available to any organizations in Ukraine that are in need of assistance. "If you are an organization in Ukraine who is interested in having Talos' help, and you would like to participate in our threat hunting program, please reach out via our social channels," she said. "We are offering our security products for free to Ukrainian organizations, as it's important to us to continue to support Ukraine throughout the duration of the conflict."A recording of the broadcast is available here and above.In our continued efforts to support Ukraine the following blogs have been translated into Ukrainian: Current executive guidance for ongoing cyberattacks in Ukraine Talos on the developing situation in Ukraine Cisco stands on guard with our customers in Ukraine Threat Advisory: Opportunistic | Malware Threat Guideline | ★★★★ | ||
| 2022-08-10 15:44:23 | Cisco Talos shares insights related to recent cyber attack on Cisco (lien direct) | Executive summaryOn May 24, 2022, Cisco became aware of a potential compromise. Since that point, Cisco Security Incident Response (CSIRT) and Cisco Talos have been working to remediate. During the investigation, it was determined that a Cisco employee's credentials were compromised after an attacker gained control of a personal Google account where credentials saved in the victim's browser were being synchronized. The attacker conducted a series of sophisticated voice phishing attacks under the guise of various trusted organizations attempting to convince the victim to accept multi-factor authentication (MFA) push notifications initiated by the attacker. The attacker ultimately succeeded in achieving an MFA push acceptance, granting them access to VPN in the context of the targeted user. CSIRT and Talos are responding to the event and we have not identified any evidence suggesting that the attacker gained access to critical internal systems, such as those related to product development, code signing, etc. After obtaining initial access, the threat actor conducted a variety of activities to maintain access, minimize forensic artifacts, and increase their level of access to systems within the environment. The threat actor was successfully removed from the environment and displayed persistence, repeatedly attempting to regain access in the weeks following the attack; however, these attempts were unsuccessful. We assess with moderate to high confidence that this attack was conducted by an adversary that has been previously identified as an initial access broker (IAB) with ties to the UNC2447 cybercrime gang, Lapsus$ threat actor group, and Yanluowang ransomware operators. For further information see the Cisco Response page here. Initial vectorInitial access to the Cisco VPN was achieved via the successful compromise of a Cisco employee's personal Google account. The user had enabled password syncing via Google Chrome and had stored their Cisco credentials in their browser, enabling that information to synchronize to their Google account. After obtaining the user's credentials, the attacker attempted to bypass multifactor authentication (MFA) using a variety of techniques, including voice phishing (aka "vishing") and MFA fatigue, the process of sending a high volume of push requests to the target's mobile device until the user accepts, either accidentally or simply to attempt to silence the repeated push notifications they are receiving. Vishing is an increasingly common social engineering technique whereby attackers try to trick employees into divulging sensitive information over the phone. In this instance, an employee reported that they received multiple calls over several days in which the callers – who spoke in English with various international accents and dialects – purported to be associated with support organizations trusted by the user. Once the attacker had obtained initial access, they enrolled a series of new devices for MFA and authenticated successfully to the Cisco VPN. The attacker then escalated to administrative privileges, allowing them to login to multiple systems, which alerted our Cisco Security Incident Response Team (CSIRT), who subsequently responded to the incident. The actor in question dropped a variety of tools, including remote access tools like LogMeIn and TeamViewer, offensive security tools such as Cobalt Strike, PowerSploit, Mimikatz, and Impacket, and added their own backdoor accounts and persistence mechanisms. | Ransomware Malware Threat Guideline | |||
| 2022-08-08 08:42:23 | Small-time cybercrime is about to explode - We aren\'t ready (lien direct) |  By Nick Biasini.The cybersecurity industry tends to focus on extremely large-scale or sophisticated, state-sponsored attacks. Rightfully so, as it can be the most interesting, technically speaking. When most people think of cybercrime they think of large-scale breaches because that's what dominates the headlines. However, the problem is much bigger. In 2021, the Internet Crime Complaint Center (IC3) received a staggering 847,376 complaints, with each victim losing a little more than $8,000 on average. Once you account for the high-value breaches, the true impact is even lower. The average person is far more likely to have their identity stolen or fall victim to some other sort of scam than be directly affected by a large-scale breach - and business is booming.A deeper look at the data from IC3 shows that the amount of complaints and revenue being generated from cybercrime continues to rise. Interestingly there is a huge jump in cybercrime during the pandemic with a staggering increase of more than 60% in complaints between 2019 and 2020, with it increasing further in 2021. It's clear that cybercrime is on the rise, but what's driving it? By Nick Biasini.The cybersecurity industry tends to focus on extremely large-scale or sophisticated, state-sponsored attacks. Rightfully so, as it can be the most interesting, technically speaking. When most people think of cybercrime they think of large-scale breaches because that's what dominates the headlines. However, the problem is much bigger. In 2021, the Internet Crime Complaint Center (IC3) received a staggering 847,376 complaints, with each victim losing a little more than $8,000 on average. Once you account for the high-value breaches, the true impact is even lower. The average person is far more likely to have their identity stolen or fall victim to some other sort of scam than be directly affected by a large-scale breach - and business is booming.A deeper look at the data from IC3 shows that the amount of complaints and revenue being generated from cybercrime continues to rise. Interestingly there is a huge jump in cybercrime during the pandemic with a staggering increase of more than 60% in complaints between 2019 and 2020, with it increasing further in 2021. It's clear that cybercrime is on the rise, but what's driving it? There have been a variety of reports that criminals are turning increasingly to cybercrime instead of traditional drug crimes, with which they were commonly associated in the past. This is both a blessing and a curse - it removes a lot of violence and crime from the streets but is adding a significant amount of pressure on local law enforcement. This is an international problem. Several recent reports highlight that this is also an issue in Italy and Spain.There are cybercriminals everywhere and the U.S. is no exception. What's changed is who is involved. Historically, cybercrime was considered white-collar criminal behavior perpetrated by those that were knowledgeable and turned bad. Now, technology has become such an integral part of our lives that anyone with a smartphone and desire can get started in cybercrime. The growth of cryptocurrencies and associated anonymity, whether legitimate or not, has garnered the attention of criminals that formerly operated in traditional criminal enterprises and have now shifted to cybercrime and identity theft.Cybercrime is a local law enforcement problemFor cybercrime to get the attention of national law enforcement, There have been a variety of reports that criminals are turning increasingly to cybercrime instead of traditional drug crimes, with which they were commonly associated in the past. This is both a blessing and a curse - it removes a lot of violence and crime from the streets but is adding a significant amount of pressure on local law enforcement. This is an international problem. Several recent reports highlight that this is also an issue in Italy and Spain.There are cybercriminals everywhere and the U.S. is no exception. What's changed is who is involved. Historically, cybercrime was considered white-collar criminal behavior perpetrated by those that were knowledgeable and turned bad. Now, technology has become such an integral part of our lives that anyone with a smartphone and desire can get started in cybercrime. The growth of cryptocurrencies and associated anonymity, whether legitimate or not, has garnered the attention of criminals that formerly operated in traditional criminal enterprises and have now shifted to cybercrime and identity theft.Cybercrime is a local law enforcement problemFor cybercrime to get the attention of national law enforcement, |
Ransomware Malware Guideline | |||
| 2022-08-04 08:00:13 | Attackers leveraging Dark Utilities "C2aaS" platform in malware campaigns (lien direct) |  By Edmund Brumaghin, Azim Khodjibaev and Matt Thaxton, with contributions from Arnaud Zobec.Executive SummaryDark Utilities, released in early 2022, is a platform that provides full-featured C2 capabilities to adversaries.It is marketed as a means to enable remote access, command execution, distributed denial-of-service (DDoS) attacks and cryptocurrency mining operations on infected systems.Payloads provided by the platform support Windows, Linux and Python-based implementations and are hosted within the Interplanetary File System (IPFS), making them resilient to content moderation or law enforcement intervention.Since its initial release, we've observed malware samples in the wild leveraging it to facilitate remote access and cryptocurrency mining.What is "Dark Utilities?"In early 2022, a new C2 platform called "Dark Utilities" was established, offering a variety of services such as remote system access, DDoS capabilities and cryptocurrency mining. The operators of the service also established Discord and Telegram communities where they provide technical support and assistance for customers on the platform. By Edmund Brumaghin, Azim Khodjibaev and Matt Thaxton, with contributions from Arnaud Zobec.Executive SummaryDark Utilities, released in early 2022, is a platform that provides full-featured C2 capabilities to adversaries.It is marketed as a means to enable remote access, command execution, distributed denial-of-service (DDoS) attacks and cryptocurrency mining operations on infected systems.Payloads provided by the platform support Windows, Linux and Python-based implementations and are hosted within the Interplanetary File System (IPFS), making them resilient to content moderation or law enforcement intervention.Since its initial release, we've observed malware samples in the wild leveraging it to facilitate remote access and cryptocurrency mining.What is "Dark Utilities?"In early 2022, a new C2 platform called "Dark Utilities" was established, offering a variety of services such as remote system access, DDoS capabilities and cryptocurrency mining. The operators of the service also established Discord and Telegram communities where they provide technical support and assistance for customers on the platform.  Dark Utilities provides payloads consisting of code that is executed on victim systems, allowing them to be registered with the service and establish a command and control (C2) communications channel. The platform currently supports Windows, Linux and Python-based payloads, allowing adversaries to target multiple architectures without requiring significant development resources. During our analysis, we observed efforts underway to expand OS and system architecture support as the platform continues to see ongoing develo Dark Utilities provides payloads consisting of code that is executed on victim systems, allowing them to be registered with the service and establish a command and control (C2) communications channel. The platform currently supports Windows, Linux and Python-based payloads, allowing adversaries to target multiple architectures without requiring significant development resources. During our analysis, we observed efforts underway to expand OS and system architecture support as the platform continues to see ongoing develo |
Spam Malware Hack Tool Threat Guideline | APT 19 | ||
| 2022-08-02 08:00:14 | Manjusaka: A Chinese sibling of Sliver and Cobalt Strike (lien direct) |  By Asheer Malhotra and Vitor Ventura.Cisco Talos recently discovered a new attack framework called "Manjusaka" being used in the wild that has the potential to become prevalent across the threat landscape. This framework is advertised as an imitation of the Cobalt Strike framework.The implants for the new malware family are written in the Rust language for Windows and Linux.A fully functional version of the command and control (C2), written in GoLang with a User Interface in Simplified Chinese, is freely available and can generate new implants with custom configurations with ease, increasing the likelihood of wider adoption of this framework by malicious actors.We recently discovered a campaign in the wild using lure documents themed around COVID-19 and the Haixi Mongol and Tibetan Autonomous Prefecture, Qinghai Province. These maldocs ultimately led to the delivery of Cobalt Strike beacons on infected endpoints.We have observed the same threat actor using the Cobalt Strike beacon and implants from the Manjusaka framework.IntroductionCisco Talos has discovered a relatively new attack framework called "Manjusaka" (which can be translated to "cow flower" from the Simplified Chinese writing) by their authors, being used in the wild.As defenders, it is important to keep track of offensive frameworks such as Cobalt Strike and Sliver so that enterprises can effectively defend against attacks employing these tools. Although we haven't observed widespread usage of this framework in the wild, it has the potential to be adopted by threat actors all over the world. This disclosure from Talos intends to provide early notification of the usage of Manjusaka. We also detail the framework's capabilities and the campaign that led to the discovery of this attack framework in the wild.The research started with a malicious Microsoft Word document (maldoc) that contained a Cobalt Strike (CS) beacon. The lure on this document mentioned a COVID-19 outbreak in Golmud City, one of the largest cities in the Haixi Mongol and Tibetan Autonomous Prefecture, Qinghai Province. During the investigation, Cisco Talos found no direct link between the campaign and the framework developers, aside from the usage of the framework (which is freely available on GitHub). However, we could not find any data that could support victimology definition. This is justifiable considering there's a low number of victims, indicating the early stages of the campaign, further supported by the maldoc metadata that indicates it was created in the second half of June 2022.While investigating the maldoc infection chain, we found an implant used to instrument Manjusaka infections, contacting the same IP address as the CS beacon. This implant is written in the Rust programming language and we found samples for Windows and Linux operating systems. The Windows implant included test samples, which had non-internet-routable IP addresses as command and control (C2). Talos also discovered the Manjusaka C2 executable - a fully functional C2 ELF binary written in GoLang with a User Interface in Simplified Chinese - on GitHub. While analyzing the C2, we generated implants by specifying our configurations. The developer advertises it has an advers By Asheer Malhotra and Vitor Ventura.Cisco Talos recently discovered a new attack framework called "Manjusaka" being used in the wild that has the potential to become prevalent across the threat landscape. This framework is advertised as an imitation of the Cobalt Strike framework.The implants for the new malware family are written in the Rust language for Windows and Linux.A fully functional version of the command and control (C2), written in GoLang with a User Interface in Simplified Chinese, is freely available and can generate new implants with custom configurations with ease, increasing the likelihood of wider adoption of this framework by malicious actors.We recently discovered a campaign in the wild using lure documents themed around COVID-19 and the Haixi Mongol and Tibetan Autonomous Prefecture, Qinghai Province. These maldocs ultimately led to the delivery of Cobalt Strike beacons on infected endpoints.We have observed the same threat actor using the Cobalt Strike beacon and implants from the Manjusaka framework.IntroductionCisco Talos has discovered a relatively new attack framework called "Manjusaka" (which can be translated to "cow flower" from the Simplified Chinese writing) by their authors, being used in the wild.As defenders, it is important to keep track of offensive frameworks such as Cobalt Strike and Sliver so that enterprises can effectively defend against attacks employing these tools. Although we haven't observed widespread usage of this framework in the wild, it has the potential to be adopted by threat actors all over the world. This disclosure from Talos intends to provide early notification of the usage of Manjusaka. We also detail the framework's capabilities and the campaign that led to the discovery of this attack framework in the wild.The research started with a malicious Microsoft Word document (maldoc) that contained a Cobalt Strike (CS) beacon. The lure on this document mentioned a COVID-19 outbreak in Golmud City, one of the largest cities in the Haixi Mongol and Tibetan Autonomous Prefecture, Qinghai Province. During the investigation, Cisco Talos found no direct link between the campaign and the framework developers, aside from the usage of the framework (which is freely available on GitHub). However, we could not find any data that could support victimology definition. This is justifiable considering there's a low number of victims, indicating the early stages of the campaign, further supported by the maldoc metadata that indicates it was created in the second half of June 2022.While investigating the maldoc infection chain, we found an implant used to instrument Manjusaka infections, contacting the same IP address as the CS beacon. This implant is written in the Rust programming language and we found samples for Windows and Linux operating systems. The Windows implant included test samples, which had non-internet-routable IP addresses as command and control (C2). Talos also discovered the Manjusaka C2 executable - a fully functional C2 ELF binary written in GoLang with a User Interface in Simplified Chinese - on GitHub. While analyzing the C2, we generated implants by specifying our configurations. The developer advertises it has an advers |
Malware Threat Guideline | APT 19 | ||
| 2022-07-27 08:00:00 | What Talos Incident Response learned from a recent Qakbot attack hijacking old email threads (lien direct) |  By Nate Pors and Terryn Valikodath. Executive summary In a recent malspam campaign delivering the Qakbot banking trojan, Cisco Talos Incident Response (CTIR) observed the adversary using aggregated, old email threads from multiple organizations that we assess were likely harvested during the 2021 ProxyLogon-related compromises targeting vulnerable Microsoft Exchange servers. This campaign relies on external thread hijacking, whereby the adversary is likely using a bulk aggregation of multiple organizations' harvested emails to launch focused phishing campaigns against previously uncompromised organizations. This differs from the more common approach to thread hijacking, in which attackers use a single compromised organization's emails to deliver their threat. This many-to-one approach is unique from what we have generally observed in the past and is likely an indirect effect of the widespread compromises and exfiltration of large volumes of email from 2020 and 2021. Understanding the difference between external and single-victim thread hijacking is essential for detecting these threats. Below, we have several tips for defenders on how to identify key indicators of this activity. External thread hijacking Cisco Talos has observed threat actors using external thread hijacking, a method by which attackers weaponize emails previously harvested from other organizations. This differs from the more common approach to thread hijacking, in which adversaries compromise the victim organization's Exchange server to obtain email threads that are then weaponized. We recently observed this in June 2022 as part of a broader campaign that delivered the Qakbot banking trojan. In this threat activity, the attackers used old emails harvested months to years ago during the 2021 ProxyLogon campaign, tracked as CVE-2021-26855, targeting vulnerable Exchange servers. External thread hijacking is not dependent on the threat actor gaining initial access to the victim environment. This is notable from a digital forensics and incident response (DFIR) perspective because the target organization only saw inbound phishing emails with its own legitimate emails as the source material, with multiple external organizations represented in the email threads. Our assessment of the adversary's use of emails obtained from the ProxyLogon compromises is based on a number of observations, including the timing of the emails and research into publicly acknowledged ProxyLogon compromises. The attackers selectively used these emails to target senders or recipients from the target organization. In the external thread hijacking attack observed by CTIR, the adversary likely took the following steps: The attacker took control of multiple third-party organizations' Exchange servers or individual inboxes and exported emails for later use. The adversary selected the emails relevant to the target organization By Nate Pors and Terryn Valikodath. Executive summary In a recent malspam campaign delivering the Qakbot banking trojan, Cisco Talos Incident Response (CTIR) observed the adversary using aggregated, old email threads from multiple organizations that we assess were likely harvested during the 2021 ProxyLogon-related compromises targeting vulnerable Microsoft Exchange servers. This campaign relies on external thread hijacking, whereby the adversary is likely using a bulk aggregation of multiple organizations' harvested emails to launch focused phishing campaigns against previously uncompromised organizations. This differs from the more common approach to thread hijacking, in which attackers use a single compromised organization's emails to deliver their threat. This many-to-one approach is unique from what we have generally observed in the past and is likely an indirect effect of the widespread compromises and exfiltration of large volumes of email from 2020 and 2021. Understanding the difference between external and single-victim thread hijacking is essential for detecting these threats. Below, we have several tips for defenders on how to identify key indicators of this activity. External thread hijacking Cisco Talos has observed threat actors using external thread hijacking, a method by which attackers weaponize emails previously harvested from other organizations. This differs from the more common approach to thread hijacking, in which adversaries compromise the victim organization's Exchange server to obtain email threads that are then weaponized. We recently observed this in June 2022 as part of a broader campaign that delivered the Qakbot banking trojan. In this threat activity, the attackers used old emails harvested months to years ago during the 2021 ProxyLogon campaign, tracked as CVE-2021-26855, targeting vulnerable Exchange servers. External thread hijacking is not dependent on the threat actor gaining initial access to the victim environment. This is notable from a digital forensics and incident response (DFIR) perspective because the target organization only saw inbound phishing emails with its own legitimate emails as the source material, with multiple external organizations represented in the email threads. Our assessment of the adversary's use of emails obtained from the ProxyLogon compromises is based on a number of observations, including the timing of the emails and research into publicly acknowledged ProxyLogon compromises. The attackers selectively used these emails to target senders or recipients from the target organization. In the external thread hijacking attack observed by CTIR, the adversary likely took the following steps: The attacker took control of multiple third-party organizations' Exchange servers or individual inboxes and exported emails for later use. The adversary selected the emails relevant to the target organization |
Malware Threat | |||
| 2022-07-26 10:11:15 | Quarterly Report: Incident Response Trends in Q2 2022 (lien direct) | Commodity malware usage surpasses ransomware by narrow margin  By Caitlin Huey.For the first time in more than a year, ransomware was not the top threat Cisco Talos Incident Response (CTIR) responded to this quarter, as commodity malware surpassed ransomware by a narrow margin. This is likely due to several factors, including the closure of several ransomware groups, whether it be of their own volition or the actions of global law enforcement agencies and governments. By Caitlin Huey.For the first time in more than a year, ransomware was not the top threat Cisco Talos Incident Response (CTIR) responded to this quarter, as commodity malware surpassed ransomware by a narrow margin. This is likely due to several factors, including the closure of several ransomware groups, whether it be of their own volition or the actions of global law enforcement agencies and governments. 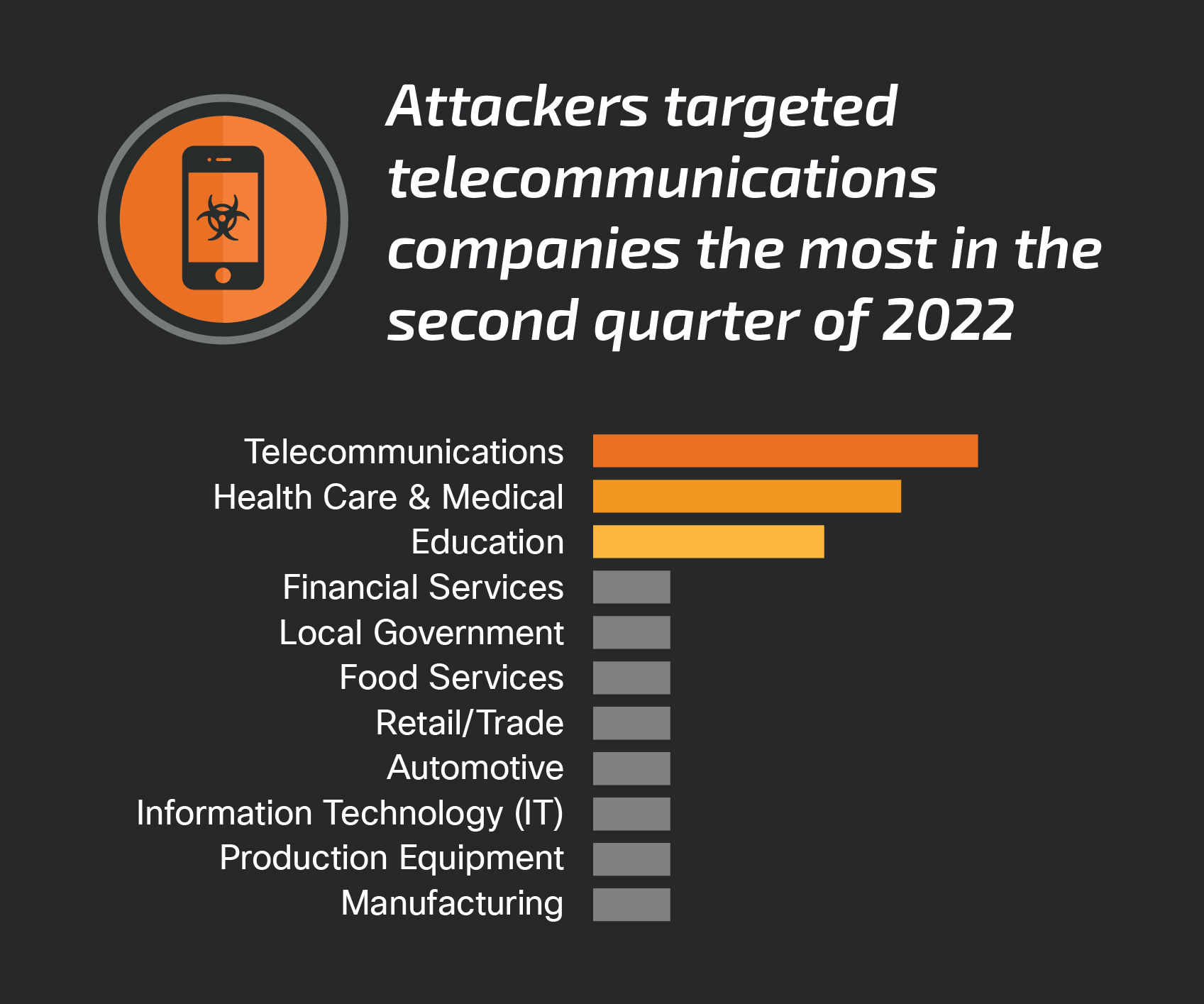 Commodity malwareThis quarter saw a notable increase in commodity malware threats compared to previous quarters. Commodity Commodity malwareThis quarter saw a notable increase in commodity malware threats compared to previous quarters. Commodity |
Ransomware Spam Malware Threat | |||
| 2022-07-21 08:00:05 | Attackers target Ukraine using GoMet backdoor (lien direct) |  Executive summarySince the Russian invasion of Ukraine began, Ukrainians have been under a nearly constant barrage of cyber attacks. Working jointly with Ukrainian organizations, Cisco Talos has discovered a fairly uncommon piece of malware targeting Ukraine - this time aimed at a large software development company whose software is used in various state organizations within Ukraine. We believe that this campaign is likely sourced by Russian state-sponsored actors or those acting in their interests. As this firm is involved in software development, we cannot ignore the possibility that the perpetrating threat actor's intent was to gain access to source a supply chain-style attack, though at this time we do not have any evidence that they were successful. Cisco Talos confirmed that the malware is a slightly modified version of the open-source backdoor named "GoMet." The malware was first observed on March 28, 2022. GoMet backdoorThe story of this backdoor is rather curious - there are two documented cases of its usage by sophisticated threat actors. First, in 2020, attackers were deploying this malware after the successful exploitation of CVE-2020-5902, a vulnerability in F5 BIG-IP so severe that USCYBERCOM posted a tweet urging all users to patch the application. The second is more recent and involved the successful exploitation of CVE-2022-1040, a remote code execution vulnerability in Sophos Firewall. Both cases are very similar. They both start with the exploitation of a public vulnerability on appliances where the malicious actors then dropped GoMet as a backdoor. As of publishing time, Cisco Talos has no reason to believe these cases are related to the usage of this backdoor in Ukraine. The original GoMet author posted the code on GitHub on March 31, 2019 and had commits until April 2, 2019. The commits didn't add any features but did fix some code convention aesthetics. The backdoor itself is a rather simple piece of software written in the Go programming language. It contains nearly all the usual functions an attacker might want in a remotely controlled agent. Agents can be deployed on a variety of operating systems (OS) or architectures (amd64, arm, etc.). GoMet supports job scheduling (via Cron or task scheduler depending on the OS), single command execution, file download, file upload or opening a shell. An additional notable feature of GoMet lies in its ability to daisy chain - whereby the attackers gain access to a network or machine and then use that same information to gain access to multiple networks and computers - connections from one implanted host to another. Such a feature could allow for communication out to the internet from otherwise completely "isolated" hosts.This version was changed by malicious actors, in the original code, the cronjob is configured to be executed once every hour on the hour. In our samples, the cronjob is configured to run every two seconds. This change makes the sample slightly more noisy since it executes every two seconds, but also prevents an hour-long sleep if the connection fails which would Executive summarySince the Russian invasion of Ukraine began, Ukrainians have been under a nearly constant barrage of cyber attacks. Working jointly with Ukrainian organizations, Cisco Talos has discovered a fairly uncommon piece of malware targeting Ukraine - this time aimed at a large software development company whose software is used in various state organizations within Ukraine. We believe that this campaign is likely sourced by Russian state-sponsored actors or those acting in their interests. As this firm is involved in software development, we cannot ignore the possibility that the perpetrating threat actor's intent was to gain access to source a supply chain-style attack, though at this time we do not have any evidence that they were successful. Cisco Talos confirmed that the malware is a slightly modified version of the open-source backdoor named "GoMet." The malware was first observed on March 28, 2022. GoMet backdoorThe story of this backdoor is rather curious - there are two documented cases of its usage by sophisticated threat actors. First, in 2020, attackers were deploying this malware after the successful exploitation of CVE-2020-5902, a vulnerability in F5 BIG-IP so severe that USCYBERCOM posted a tweet urging all users to patch the application. The second is more recent and involved the successful exploitation of CVE-2022-1040, a remote code execution vulnerability in Sophos Firewall. Both cases are very similar. They both start with the exploitation of a public vulnerability on appliances where the malicious actors then dropped GoMet as a backdoor. As of publishing time, Cisco Talos has no reason to believe these cases are related to the usage of this backdoor in Ukraine. The original GoMet author posted the code on GitHub on March 31, 2019 and had commits until April 2, 2019. The commits didn't add any features but did fix some code convention aesthetics. The backdoor itself is a rather simple piece of software written in the Go programming language. It contains nearly all the usual functions an attacker might want in a remotely controlled agent. Agents can be deployed on a variety of operating systems (OS) or architectures (amd64, arm, etc.). GoMet supports job scheduling (via Cron or task scheduler depending on the OS), single command execution, file download, file upload or opening a shell. An additional notable feature of GoMet lies in its ability to daisy chain - whereby the attackers gain access to a network or machine and then use that same information to gain access to multiple networks and computers - connections from one implanted host to another. Such a feature could allow for communication out to the internet from otherwise completely "isolated" hosts.This version was changed by malicious actors, in the original code, the cronjob is configured to be executed once every hour on the hour. In our samples, the cronjob is configured to run every two seconds. This change makes the sample slightly more noisy since it executes every two seconds, but also prevents an hour-long sleep if the connection fails which would |
Malware Vulnerability Threat | |||
| 2022-07-05 04:00:00 | Researcher Spotlight: Around the security world and back again with Nick Biasini (lien direct) | By Jon Munshaw. Nick Biasini's seen it all. Going on a nearly 20-year security career, he's been a part of some of Cisco Talos' largest undertakings in the company's history. From an attack on the global Olympic Games, to a wireless router malware that affected hundreds of... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Malware | |||
| 2022-05-13 05:00:00 | EMEAR Monthly Talos Update: Wiper malware (lien direct) | Cisco Talos and Cisco Secure are launching a new video series to fill you in on the latest cybersecurity trends. We're thrilled to launch our first video in the new Talos Threat Update series, which you can watch above or over at this link, where Martin Lee and Hazel Burton talk about wiper... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Malware Threat | |||
| 2022-05-05 05:01:44 | Mustang Panda deploys a new wave of malware targeting Europe (lien direct) | By Jung soo An, Asheer Malhotra and Justin Thattil, with contributions from Aliza Berk and Kendall McKay. In February 2022, corresponding roughly with the start of the Russian Invasion of Ukraine, Cisco Talos began observing the China-based threat actor Mustang Panda conducting phishing campaigns... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Malware Threat | |||
| 2022-04-05 05:00:32 | Threat Spotlight: AsyncRAT campaigns feature new version of 3LOSH crypter (lien direct) | By Edmund Brumaghin, with contributions from Alex Karkins. Ongoing malware distribution campaigns are using ISO disk images to deliver AsyncRAT, LimeRAT and other commodity malware to victims.The infections leverage process injection to evade detection by endpoint security software.These campaigns... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Malware | |||
| 2022-03-29 05:02:08 | Transparent Tribe campaign uses new bespoke malware to target Indian government officials (lien direct) | By Asheer Malhotra and Justin Thattil with contributions from Kendall McKay. Cisco Talos has observed a new Transparent Tribe campaign targeting Indian government and military entities. While the actors are infecting victims with CrimsonRAT, their well-known malware of choice, they are also using... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Malware | APT 36 | ||
| 2022-03-09 11:46:39 | Threat advisory: Cybercriminals compromise users with malware disguised as pro-Ukraine cyber tools (lien direct) | Executive summary Opportunistic cybercriminals are attempting to exploit Ukrainian sympathizers by offering malware purporting to be offensive cyber tools to target Russian entities. Once downloaded, these files infect unwitting users rather than delivering the tools originally advertised.In one... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Malware | |||
| 2022-02-24 15:03:29 | Threat Advisory: Cyclops Blink (lien direct) | Cisco Talos is aware of the recent reporting around a new modular malware family, Cyclops Blink, that targets small and home office (SOHO) devices, similar to previously observed threats like VPNFilter. This malware is designed to run on Linux systems and is compiled specifically for 32-bit PowerPC... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Malware | VPNFilter | ||
| 2022-02-24 15:01:17 | Threat Advisory: HermeticWiper (lien direct) | Cisco Talos is aware of a second wave of wiper attacks ongoing inside Ukraine, leveraging a new wiper that has been dubbed "HermeticWiper." Deployment of the destructive malware began on Feb. 23, 2022. HermeticWiper features behavioral characteristics similar to what was observed during the... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Malware | |||
| 2022-02-09 05:06:14 | What\'s with the shared VBA code between Transparent Tribe and other threat actors? (lien direct) | By Vanja Svajcer and Vitor Ventura. Recently, we've been researching several threat actors operating in South Asia: Transparent Tribe, SideCopy, etc., that deploy a range of remote access trojans (RATs). After a hunting session in our malware sample repositories and VirusTotal while looking into... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Malware Threat | APT 36 | ||
| 2022-02-02 05:04:10 | Arid Viper APT targets Palestine with new wave of politically themed phishing attacks, malware (lien direct) | By Asheer Malhotra and Vitor Ventura. Cisco Talos has observed a new wave of Delphi malware called Micropsia developed and operated by the Arid Viper APT group since 2017.This campaign targets Palestinian entities and activists using politically themed lures.The latest iteration of the implant... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Malware | APT-C-23 | ||
| 2022-01-21 12:19:42 | Ukraine Campaign Delivers Defacement and Wipers, in Continued Escalation (lien direct) | Authored by Nick Biasini and Chris Neal with Contributions from Dmytro Korzhevin. Several cyber attacks against Ukrainian government websites - including website defacements and destructive wiper malware - have made headlines over the past few weeks as military tensions along the Russian/Ukrainian... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Malware | |||
| 2022-01-13 11:00:00 | Threat Source Newsletter (Jan. 13, 2022) (lien direct) | Newsletter compiled by Jon Munshaw.Good afternoon, Talos readers. Move out of the way, Log4j! Traditional malware is back with a bang in 2022. While Log4j is likely still occupying many defenders' minds, the bad guys are still out there doing not-Log4j things. We have new research out... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Malware | |||
| 2021-12-27 06:00:00 | 2021: Looking back on the year in malware and cyber attacks, from SolarWinds to Log4j (lien direct) | By Jon Munshaw. It seems like we were just recovering from the aftermath of the massive SolarWinds campaign a month or two ago. And now suddenly, it's been a year since one of the largest cyber attacks in history and moving onto another threat that could last for years. That just seemed to be... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Malware Threat | |||
| 2021-12-02 05:00:01 | Magnat campaigns use malvertising to deliver information stealer, backdoor and malicious Chrome extension (lien direct) | By Tiago Pereira. Talos recently observed a malicious campaign offering fake installers of popular software as bait to get users to execute malware on their systems. This campaign includes a set of malware distribution campaigns that started in late 2018 and have targeted mainly Canada, along... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Malware | |||
| 2021-11-22 05:01:13 | Back from the dead: Emotet re-emerges, begins rebuilding to wrap up 2021 (lien direct) | Executive summary Emotet has been one of the most widely distributed threats over the past several years. It has typically been observed being distributed via malicious spam email campaigns, and often leads to additional malware infections as it provides threat actors with an initial foothold in an... [[ This is only the beginning! Please visit the blog for the complete entry ]] | Spam Malware Threat Guideline | |||
| 2021-11-10 14:11:03 | North Korean attackers use malicious blogs to deliver malware to high-profile South Korean targets (lien direct) |
By Jung soo An and Asheer Malhotra, with contributions from Kendall McKay.
Cisco Talos has observed a new malware campaign operated by the Kimsuky APT group since June 2021.Kimsuky, also known as Thallium and Black Banshee, is a North Korean state-sponsored advanced...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Malware Cloud | APT 37 | ||
| 2021-10-26 05:01:17 | SQUIRRELWAFFLE Leverages malspam to deliver Qakbot, Cobalt Strike (lien direct) | By Edmund Brumaghin, Mariano Graziano and Nick Mavis.
Executive summary
Recently, a new threat, referred to as "SQUIRRELWAFFLE" is being spread more widely via spam campaigns, infecting systems with a new malware loader. This is a malware family that's been spread with increasing regularity and...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Spam Malware | |||
| 2021-09-30 06:22:57 | A wolf in sheep\'s clothing: Actors spread malware by leveraging trust in Amnesty International and fear of Pegasus (lien direct) | By Vitor Ventura and Arnaud Zobec.
Threat actors are impersonating the group Amnesty International and promising to protect against the Pegasus spyware as part of a scheme to deliver malware.
Amnesty International recently made international headlines when it released a groundbreaking report on...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Malware | |||
| 2021-09-21 05:11:17 | TinyTurla - Turla deploys new malware to keep a secret backdoor on victim machines (lien direct) | News summary Cisco Talos recently discovered a new backdoor used by the Russian Turla APT group.We have seen infections in the U.S., Germany and, more recently, in Afghanistan. It is likely used as a stealth second-chance backdoor to keep access to infected devicesIt can be used to download, upload...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Malware | |||
| 2021-09-17 07:39:44 | Talos Takes Ep. #68: The various pivots and pitfalls in a malware investigation (lien direct) | By Jon Munshaw.
The latest episode of Talos Takes is available now. Download this episode and subscribe to Talos Takes using the buttons below, or visit the Talos Takes page.
On this week's episode, Vitor Ventura from our research team walks through his recent work on connecting several...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Malware | |||
| 2021-09-16 05:04:10 | Operation Layover: How we tracked an attack on the aviation industry to five years of compromise (lien direct) | By Tiago Pereira and Vitor Ventura.
Cisco Talos linked the recent aviation targeting campaigns to an actor who has been targeting the aviation industry for two years.The same actor has been running successful malware campaigns for more than five years.Although always using commodity malware, the...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Malware | |||
| 2021-08-19 04:58:51 | Malicious Campaign Targets Latin America: The seller, The operator and a curious link (lien direct) | By Asheer Malhotra and Vitor Ventura, with contributions from Vanja Svajcer.
Cisco Talos has observed a new malware campaign delivering commodity RATs, including njRAT and AsyncRAT.The campaign targets travel and hospitality organizations in Latin America.Techniques utilized in this campaign bear...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Malware | |||
| 2021-08-11 05:00:00 | Talos Incident Response quarterly threat report - The top malware families and TTPs used in Q2 2021 (lien direct) | By David Liebenberg and Caitlin Huey.
Last quarter, ransomware was not the most dominant threat for the first time since we began compiling these reports. We theorized that this was due to a huge uptick in Microsoft Exchange exploitation, which temporarily became a primary focus for Cisco...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Ransomware Malware Threat | |||
| 2021-07-29 10:05:54 | Threat Spotlight: Solarmarker (lien direct) | By Andrew Windsor, with contributions from Chris Neal.
Executive summaryCisco Talos has observed new activity from Solarmarker, a highly modular .NET-based information stealer and keylogger.A previous staging module, "d.m," used with this malware has been replaced by a new module dubbed...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Malware | |||
| 2021-06-22 04:56:28 | Attackers in Executive Clothing - BEC continues to separate orgs from their money (lien direct) | By Nick Biasini.
In today's world of threat research, the focus tends to be on the overtly malicious practice of distributing and installing malware on end systems. But this is far from the complete picture of what threats organizations face. One of the most, if not the most, costly is something...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Malware Threat | |||
| 2021-06-03 11:00:00 | Threat Source newsletter (June 3, 2021) (lien direct) | Newsletter compiled by Jon Munshaw.Good afternoon, Talos readers.
If you didn't catch us live yesterday, we've uploaded the full version of our stream on Discord and Slack malware to our YouTube page. Chris Neal from Talos Outreach walked through his recent research into these campaigns...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Malware | |||
| 2021-06-03 05:00:05 | Necro Python bot adds new exploits and Tezos mining to its bag of tricks (lien direct) | By Vanja Svajcer, with contributions from Caitlin Huey and Kendall McKay.
News summarySome malware families stay static in terms of their functionality. But a newly discovered malware campaign utilizing the Necro Python bot shows this actor is adding new functionality and improving its chances of...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Malware | |||
| 2021-05-13 05:09:57 | Transparent Tribe APT expands its Windows malware arsenal (lien direct) | By Asheer Malhotra, Justin Thattil and Kendall McKay.
Transparent Tribe, also known as APT36 and Mythic Leopard, continues to create fake domains mimicking legitimate military and defense organizations as a core component of their operations. Cisco Talos' previous research has mainly linked this...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Malware | APT 36 | ||
| 2021-04-21 05:04:42 | A year of Fajan evolution and Bloomberg themed campaigns (lien direct) | By Vanja Svajcer.
News summarySome malware campaigns are designed to spread malware to as many people as possible - while some others carefully choose their targets. Cisco Talos recently discovered a malware campaign that does not fit in any of the two categories. This actor has a relatively low...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Malware | |||
| 2021-04-12 06:32:04 | Recording: Analyzing Android Malware - From triage to reverse-engineering (lien direct) | It's easy to get wrapped up worry about large-scale ransomware attacks on the threat landscape. These are the types of attacks that make headlines and strike fear into the hearts of CISOs everywhere. But if you want to defend the truly prolific and widespread threats that target some of the devices...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Ransomware Malware Threat | |||
| 2021-03-31 06:29:41 | Cheating the cheater: How adversaries are using backdoored video game cheat engines and modding tools (lien direct) | By Nick Lister and Holger Unterbrink, with contributions from Vanja Svajcer.
News summary Cisco Talos recently discovered a new campaign targeting video game players and other PC modders.Talos detected a new cryptor used in several different malware campaigns hidden in seemingly legitimate files...
[[ This is only the beginning! Please visit the blog for the complete entry ]] |
Malware |
To see everything:
Our RSS (filtrered)
