What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-12-14 18:55:10 | Microsoft ÃĐlimine des domaines vendant de faux comptes Outlook Microsoft Takes Down Domains Selling Fake Outlook Accounts (lien direct) |
Microsoft a annoncÃĐ mercredi qu'il avait saisi des sites Web illicites et des pages de mÃĐdias sociaux appartenant au groupe de cybercriminaux basÃĐ au Vietnam Storm-1152 a crÃĐÃĐ environ 750 millions de comptes d'Outlook frauduleux et a gagnÃĐ des millions de dollars de revenus illÃĐgaux. Le gÃĐant de Redmond appelle Storm-1152, un ÃĐcosystÃĻme de cybercriminalitÃĐ en tant que service (CAAS), ÂŦle vendeur et crÃĐateur numÃĐro un de comptes Microsoft frauduleuxÂŧ qui les a bien vendues en ligne à d'autres cybercriminels pour contourner les logiciels de vÃĐrification d'identitÃĐ Ã travers bien à travers- Plateformes technologiques connues. Ces comptes ont ÃĐtÃĐ utilisÃĐs pour plusieurs activitÃĐs malveillantes, notamment le phishing de masse, le vol d'identitÃĐ et la fraude, et les attaques de dÃĐni de service (DDOS) distribuÃĐes. ÂŦStorm-1152 gÃĻre des sites Web illicites et des pages de mÃĐdias sociaux, vendant des comptes et des outils frauduleux Microsoft pour contourner les logiciels de vÃĐrification d'identitÃĐ sur des plateformes technologiques bien connues.Ces services rÃĐduisent le temps et les efforts nÃĐcessaires pour que les criminels mettent en ligne une multitude de comportements criminels et abusifs Âŧ, Amy Hogan-Burney, directrice gÃĐnÃĐrale de l'unitÃĐ des crimes numÃĐriques de Microsoft \\ (DCU), a ÃĐcrit dans un article de blog. Selon Microsoft, Octo Tempest, ÃĐgalement connu sous le nom de Spanded Spider, est l'un des clients de Storm-1152 \\ qui ont obtenu des comptes de Microsoft frauduleux pour mener des attaques d'ingÃĐnierie sociale visant à l'extorsion financiÃĻre.Outre Octo Tempest, des acteurs de menace tels que Storm-0252, Storm-0455 et d'autres groupes de ransomware ou d'extorsion ont ÃĐgalement achetÃĐ des comptes frauduleux de Storm-1152. Le 7 dÃĐcembre 2023, le gÃĐant de Redmond a obtenu une ordonnance du tribunal du district sud de New York pour saisir l'infrastructure basÃĐe aux Ãtats-Unis de la cybercriminalitÃĐ construite sur l'intelligence recueillie sur les CAA et ses activitÃĐs et infrastructures par Microsoftet la sociÃĐtÃĐ de sÃĐcuritÃĐ et de sÃĐcuritÃĐ des bots Arkose Labs. ÂŦDepuis au moins 2021, les dÃĐfendeurs se sont engagÃĐs dans un plan pour obtenir des millions de comptes de messagerie Microsoft Outlook au nom des utilisateurs fictifs en fonction d'une sÃĐrie de fausses reprÃĐsentations, puis vendent ces comptes frauduleux à des acteurs malveillants pour une utilisationdans divers types de cybercriminalitÃĐ Âŧ, selon le plainte . Sur la base de la commande, Microsoft a repris des domaines tels que Hotmailbox [.] Moi, 1stcaptcha, anycaptcha et non ecaptcha, ainsi que des comptes de mÃĐdias sociaux qui ont ÃĐtÃĐ utilisÃĐs par Storm-1152 pour nuire aux clients de la sociÃĐtÃĐ etcauser des dommages-intÃĐrÊts d'une valeur de centaines de milLions de dollars. La sociÃĐtÃĐ a ÃĐgalement poursuivi trois individus & # 8211;Duong Dinh Tu, Linh Van Nguyen (A / K / A Nguyen Van Linh) et Tai Van Nguyen & # 8211;tous basÃĐs à VIEtnam et censÃĐ ÃŠtre opÃĐrant Storm-1152. "Nos rÃĐsultats montrent que ces personnes ont exploitÃĐ et rÃĐdigÃĐ le code pour les sites Web illicites, publiÃĐ des instructions dÃĐtaillÃĐes ÃĐtape par ÃĐtape sur la façon d'utiliser leurs produits via des didacticiels vidÃĐo et ont fourni des services de chat pour aider ceux qui utilisent leurs services frauduleux", a ajoutÃĐAmy Hogan-Burney. & # 8220; Aujourd'hui, l'action est une continuation de la stratÃĐgie de Microsoft pour viser l'ÃĐcosystÃĻme cybercriminal plus large et cibler les outils que les cybercriminaux utilisent pour lancer leurs attaques.Il s'appuie sur notre exp | Ransomware Malware Tool Threat | â â â | ||
| 2023-12-14 15:46:49 | Dragos rÃĐvÃĻle l'attaque ÃĐlectrique de l'ÃĐlectrum contre l'entitÃĐ ÃĐlectrique ukrainienne à l'aide d'outils personnalisÃĐs, un malware de caddywiper Dragos reveals Electrum October attack on Ukrainian electric entity using custom tools, CaddyWiper malware (lien direct) |
> La sociÃĐtÃĐ de cybersÃĐcuritÃĐ industrielle Dragos a liÃĐ la divulgation rÃĐcente de Mandiant d'un incident cyber-physique à l'acteur de menace liÃĐ Ã la Russie ...
>Industrial cybersecurity company Dragos has linked Mandiant’s recent disclosure of a cyber-physical incident to the Russia-linked threat actor... |
Malware Tool Threat | â â â | ||
| 2023-12-14 12:07:06 | Ce que nos experts en sÃĐcuritÃĐ ont discutÃĐ chez AWS RE: Invent 2023 What Our Security Experts Discussed at AWS re:Invent 2023 (lien direct) |
Le paysage du codage change alors que les dÃĐveloppeurs adoptent l'IA, l'automatisation, les microservices et les bibliothÃĻques tierces pour stimuler la productivitÃĐ.Bien que chaque nouvelle approche amÃĐliore l'efficacitÃĐ, comme une ÃĐpÃĐe à double tranchant, les dÃĐfauts et les vulnÃĐrabilitÃĐs sont ÃĐgalement introduits plus rapidement que les ÃĐquipes ne peuvent les rÃĐparer.DÃĐcouvrez l'une des derniÃĻres innovations qui rÃĐsolvent cela dans un rÃĐcapitulatif de ce que nos experts en sÃĐcuritÃĐ ont discutÃĐ chez AWS RE: Invent 2023.
Veracode Fix: un changeur de jeu en rÃĐgime pour les dÃĐveloppeurs pour les dÃĐveloppeurs
Au cours de leur segment AWS on Air, nos experts, vice-prÃĐsident de la gestion stratÃĐgique des produits, Tim Jarrett, et l'architecte des solutions seniors, Eric Kim, ont partagÃĐ comment Veracode Fix est un nouvel outil de changement de jeu qui aide les dÃĐveloppeurs à rÃĐduire le processus de rÃĐtablissement des dÃĐfauts depuis des moisà quelques minutes.
Tirant la puissance de l'IA, l'outil permet aux dÃĐveloppeurs de rÃĐduire facilement les problÃĻmes de sÃĐcuritÃĐ en gÃĐnÃĐrant des correctifs suggÃĐrÃĐs pour le code existant qui est dÃĐfectueux et vulnÃĐrable.
Alors que de nombreux outils de codage alimentÃĐs par l'IA sont conçus pour aider à ÃĐcrireâĶ
The landscape of coding is changing as developers embrace AI, automation, microservices, and third-party libraries to boost productivity. While each new approach enhances efficiency, like a double-edged sword, flaws and vulnerabilities are also introduced faster than teams can fix them. Learn about one of the latest innovations solving this in a recap of what our security experts discussed at AWS re:Invent 2023. Veracode Fix: A Game Changer in Flaw Remediation for Developers During their AWS on Air segment, our experts, Vice President of Strategic Product Management, Tim Jarrett, and Senior Solutions Architect, Eric Kim, shared how Veracode Fix is a new game-changing tool that helps developers cut down the flaw remediation process from months to minutes. Leveraging the power of AI, the tool allows developers to easily reduce security issues by generating suggested fixes for existing code that is flawed and vulnerable.  While many AI-powered coding tools are designed to help writeâĶ |
Tool Vulnerability | â â â | ||
| 2023-12-14 11:16:00 | Microsoft prend des mesures judiciaires pour rÃĐprimer le rÃĐseau de cybercriminalitÃĐ Storm-1152 \\ Microsoft Takes Legal Action to Crack Down on Storm-1152\\'s Cybercrime Network (lien direct) |
Microsoft a dÃĐclarÃĐ mercredi avoir obtenu une ordonnance du tribunal pour saisir les infrastructures mises en place par un groupe appelÃĐ Storm-1152 qui a colportÃĐ environ 750 millions de comptes et d'outils frauduleux de Microsoft via un rÃĐseau de sites Web de faux et de pages de mÃĐdias sociaux à d'autres acteurs criminels, en les fixant des millions de millions de millions de millions de sites Web et de pages de mÃĐdias sociaux à d'autres acteurs criminels, ce qui en fait des millions de millions de millions de sites de fauxdollars de revenus illicites.
ÂŦLes comptes en ligne frauduleux agissent comme la passerelle vers une multitude de cybercriminaux,
Microsoft on Wednesday said it obtained a court order to seize infrastructure set up by a group called Storm-1152 that peddled roughly 750 million fraudulent Microsoft accounts and tools through a network of bogus websites and social media pages to other criminal actors, netting them millions of dollars in illicit revenue. "Fraudulent online accounts act as the gateway to a host of cybercrime, |
Tool Legislation | â â â | ||
| 2023-12-14 11:00:00 | ProtÃĐger l'entreprise des fuites de mot de passe Web sombres Protecting the enterprise from dark web password leaks (lien direct) |
Referenced in popular films and television programs, “The Dark Web” has achieved what many cyber security concerns fail to do in that it has entered the public consciousness. It is generally understood that the dark web is a collection of on-line sites and marketplaces, notorious for facilitating illegal activities and harboring stolen information. The details of how this underground economy function, the various levels of sophistication of its participants, and how information ends up in these forums is less broadly understood. The trade in compromised passwords in dark web markets is particularly damaging. Cybercriminals often exploit password leaks to access sensitive data, commit fraud or launch further attacks. Let’s explore the various ways passwords are leaked to the dark web and discuss strategies for using dark web data to protect your organization. Data breaches One of the most common ways passwords are leaked to the dark web is through data breaches. Cybercriminals target organizations and gain unauthorized access to their systems and databases. Once inside, they can steal large volumes of user data, including passwords, which are then sold or traded on the dark web. A “first party” data breach is when that breach occurs in a network you are responsible for (i.e. your company). This is typically a top-of-mind concern for security and IT professionals. However, breaches of third parties that hold information about your users can be equally damaging. Because users often reuse passwords across multiple services, or use slight variations or formulaic passwords, these disclosures are critical. They result in threat actors gaining access to your network or SaaS services by simply logging or through brute forcing a greatly reduced key space which may go unnoticed. Phishing attacks Phishing attacks are another prevalent method used by cybercriminals to obtain passwords. These attacks involve sending deceptive emails, text messages, or social media messages that trick users into revealing their login credentials. Once the attacker has the victim\'s password, they can easily access their accounts or sell the information on the dark web. Keyloggers and malware Keyloggers and malware are stealthy tools used by cybercriminals to record a user\'s keystrokes, including passwords. These can be installed on a victim\'s device through malicious emails, downloads, or infected websites. This is particularly concerning in cases where the endpoints in question are not fully managed by the company. Contractors, network devices provided by service providers, users with BYOD equipment or other semi-public or public devices users might access a cloud service from are all examples of devices which can result in loss of credentials because of malware infection - regardless of the endpoint security measures taken on company owned devices. What is particularly insidious about these infections is that, unless addressed, they continue to report current credentials up to the command-and-control services across password changes and platforms. Insider threats Sometimes, passwords are leaked to the dark web through insider threats. Disgruntled employees, contractors, or other individuals with access to sensitive information may intentionally leak passwords as an act of revenge or for financial gain. Protecting Your Passwords: Best Practices While the risks associated with password leaks on the dark web are real, there are steps you can take to protect your organization from being impacted by these disclosures: Educate users: By now it is difficult to find an organization that doesn’t have a policy and technical controls to enforce the use of strong passwords in their environment. Building on that to train users when it is acceptable to use a company provide email address for service | Data Breach Malware Tool Threat Cloud Technical | â â | ||
| 2023-12-14 09:44:32 | AttÃĐnuation des menaces d'initiÃĐ: 5 meilleures pratiques pour rÃĐduire le risque Insider Threat Mitigation: 5 Best Practices to Reduce Risk (lien direct) |
(This is an updated version of a blog that was originally published on 1/28/21.) Most security teams focus on detecting and preventing external threats. But not all threats come from the outside.  The shift to hybrid work, accelerated cloud adoption and high rates of employee turnover have created a perfect storm for data loss and insider threats over the past several years. Today, insider threats rank amongst the top concerns for security leaders-30% of chief information security officers report that insider threats are their biggest cybersecurity threat over the next 12 months. It\'s easy to understand why. Insider threats have increased 44% since 2020 due to current market dynamics-and security teams are struggling to keep pace. According to the Verizon 2023 Data Breach Investigations Report, 74% of all breaches involve the human element. In short, data doesn\'t lose itself. People lose it. When the cybersecurity risk to your company\'s vital systems and data comes from the inside, finding ways to mitigate it can be daunting. Unlike with tools that combat external threats, security controls for data loss and insider threats can impact users\' daily jobs. However, with the right approach and insider threat management tools, that doesn\'t have to be the case. In this blog post, we\'ll share best practices for insider threat mitigation to help your business reduce risk and overcome common challenges you might face along the way.  What is an insider threat? But first, let\'s define what we mean by an insider threat. In the cybersecurity world, the term âinsiderâ describes anyone with authorized access to a company\'s network, systems or data. In other words, it is someone in a position of trust. Current employees, business partners and third-party contractors can all be defined as insiders.  As part of their day-to-day jobs, insiders have access to valuable data and systems like: Computers and networks Intellectual property (IP) Personal data Company strategy Financial information Customer and partner lists All insiders pose a risk given their position of trust-but not all insiders are threats.  An insider threat occurs when someone with authorized access to critical data or systems misuses that access-either on purpose or by making a mistake. The fallout from an insider threat can be dire for a business, including IP loss, legal liability, financial consequences and reputational damage. The challenge for security firms is to determine which insiders are threats, and what type of threats they are, so they know how to respond. There are three insider threat types: Careless. This type of risky insider is best described as a user with good intentions who makes bad decisions that can lead to data loss. The 2022 Cost of Insider Threats Global Report from Ponemon Institute notes that careless users account for more than half (56%) of all insider-led incidents. Malicious. Some employees-or third parties, like contractors or business partners-are motivated by personal gain. Or they might be intent on harming the business. In either case, these risky users might want to exfiltrate trade secrets or take IP when they leave the company. Industrial espionage and sabotage are examples of malicious insider activity. Ponemon research shows malicious insiders account for 26% of insiders. Compromised. Sometimes, external threat actors steal user login information or other credentials. They then use those credentials to access applications and systems. Ponemon reports that compromised users account for 18% of insiders. Insider threat mitigation best practices Companies can minimize brand and financial damage by detecting and stopping insider threats. How each security team approaches insider threats will vary depending on the industry, maturity and business culture. However, every organization can use the five best practices we\'ve outlined below to improve their insider threat prevention.   1. Identify your risky users Most insiders fall into the âcare | Data Breach Tool Threat Industrial Cloud Technical | â â | ||
| 2023-12-14 09:00:56 | La dÃĐtection de code QR malveillant fait un bond en avant gÃĐant Malicious QR Code Detection Takes a Giant Leap Forward (lien direct) |
Proofpoint introduces inline, pre-delivery QR code detection engine to help protect against imaged-based QR code phishing attacks QR code phishing, also known as quishing, is the latest attack hitting inboxes. This emerging threat is able to get around traditional email defenses and is forging a new way to deliver email attacks directly to users. Along with email phishing, executive impersonation, spear phishing and business email compromise (BEC), this threat has become one of the top concerns for security and IT teams.  In response, Proofpoint has launched new inline sandboxing capabilities to detect and stop suspicious QR code threats. Not only do we support behavioral and sandbox detection engines, but we also provide pre- and post-scanning for risky QR codes. When combined, these capabilities more accurately detect and better protect against this new threat vector. Most API-based email security tools rely on behavioral signals, which means they can only detect a suspicious QR code email after it has been delivered to the user\'s inbox. In contrast, Proofpoint stops attacks pre-delivery, so threats can never make it to users\' inboxes. In this blog post, we\'ll cover what you should know about QR code phishing and detection-and how Proofpoint can help. Why QR codes?  When Microsoft disabled macros to prevent threat actors from exploiting them to deliver malware, threat actors started to test various new attack delivery techniques, such as QR codes. Used by marketers as a quick and easy way to connect with consumers and drive engagement, QR codes have become a part of our daily lives and are now used in retail stores, airline tickets, contactless menus and scan-to-pay, among many others.  While it\'s common knowledge that standard QR codes can be used in malicious ways, a recent Scantrust QR code survey found that âover 80% of US-based QR code users said that they think QR codes are safe.â It\'s this inherent trust of QR codes that threat actors depend on. That and the fact that QR codes do not expose malicious URLs make them very hard detect with traditional email security tools.  What is QR code phishing?  A QR code scam is when a bad actor creates a QR code phishing campaign to trick a user into navigating to a malicious URL. This leads them to a malicious website that then harvests their credentials or downloads malware onto their device. These campaigns include payment scams, package scams, email scams and even donation scams during the holiday season. Because all QR codes look similar, users are easily fooled.  Figure 1: How a QR scam typically works. Why are QR codes getting through?  Legacy email security providers and most API-based email security tools have a very difficult time detecting these attacks. That\'s because these tools scan email messages for known malicious links-they don\'t scan images for links that are hidden inside QR code images.  This attack method also creates a new security blind spot. QR codes are scanned by a separate device, like a smartphone, from where the email is delivered. And smartphones are less likely to have robust security protection, which is needed to detect and prevent these attacks. For this reason, it\'s essential that an email security tool detects and blocks QR code phishing emails before they reach users\' inboxes. When messages are scanned post-delivery, like with API-based tools, there\'s a chance that users will get to them first-before they\'re clawed back. Post-delivery-only detection risks  Post-delivery-only email security tools claim to âdetect and blockâ QR code phishing emails, but they simply cannot. While they may âdetectâ a suspicious QR code email, it\'s only after the threat has been delivered to the user\'s inbox. Moreover, these tools do not sandbox suspicious QR codes. This means they have a high miss rate-which creates more risk for your company. Besides creating more risk, they also create more work for your teams. By relying solely on behavioral anomalies, these tools | Malware Tool Threat Mobile Cloud | â â â | ||
| 2023-12-13 23:13:19 | (Déjà vu) Silent, Yet Powerful Pandora hVNC, The Popular Cybercrime Tool That Flies Under the Radar (lien direct) | Pandora HVNC est un cheval de Troie (rat) à l'accÃĻs à distance qui est annoncÃĐ sur les forums de cybercriminalitÃĐ depuis 2021. Ãtonnamment, il a reçu peu d'attention de la communautÃĐ de la cybersÃĐcuritÃĐ.MalgrÃĐ cela, il reste un outil largement utilisÃĐ et est favorisÃĐ par de nombreux acteurs de menace.Pandora HVNC permet aux attaquants de prendre un contrÃīle secrÃĻte sur l'ordinateur d'une victime.Cet article analysera les caractÃĐristiques de Pandora Hvnc.
-
mise à jour malveillant
Pandora hVNC is a remote access trojan (RAT) that has been advertised on cybercrime forums since 2021. Surprisingly, it has received little attention from the cybersecurity community. Despite this, it remains a widely used tool and is favoured by many threat actors. Pandora hVNC enables attackers to gain covert control over a victim\'s computer. This article will analyse the features of Pandora hVNC. - Malware Update |
Tool Threat | â | ||
| 2023-12-13 19:14:05 | Pandora Hvnc silencieuse, mais puissante, l'outil de cybercriminalitÃĐ populaire qui vole sous le radar Silent, Yet Powerful Pandora hVNC, The Popular Cybercrime Tool That Flies Under the Radar (lien direct) |
> Pandora HVNC est un cheval de Troie (rat) d'accÃĻs à distance qui est annoncÃĐ sur les forums de cybercriminalitÃĐ depuis 2021. Ãtonnamment, il a reçu peu d'attention de la communautÃĐ de la cybersÃĐcuritÃĐ.MalgrÃĐ cela, il reste un outil largement utilisÃĐ et est favorisÃĐ par de nombreux acteurs de menace.Pandora HVNC permet aux attaquants d'obtenir un contrÃīle secrÃĻte sur un ordinateur victime.Ce [& # 8230;]
Le post Silencieux, mais mais encorePuissant Pandora Hvnc, le populaire outil de cybercriminalitÃĐ qui vole sous le radar est apparu pour la premiÃĻre fois sur slashnext .
>Pandora hVNC is a remote access trojan (RAT) that has been advertised on cybercrime forums since 2021. Surprisingly, it has received little attention from the cybersecurity community. Despite this, it remains a widely used tool and is favoured by many threat actors. Pandora hVNC enables attackers to gain covert control over a victim’s computer. This […] The post Silent, Yet Powerful Pandora hVNC, The Popular Cybercrime Tool That Flies Under the Radar first appeared on SlashNext. |
Tool Threat Technical | â â â â | ||
| 2023-12-13 18:45:00 | Google en utilisant les dÃĐsinfeursurs de Clang pour protÃĐger Android contre les vulnÃĐrabilitÃĐs de bande de base cellulaire Google Using Clang Sanitizers to Protect Android Against Cellular Baseband Vulnerabilities (lien direct) |
Google met en ÃĐvidence le rÃīle jouÃĐ par & nbsp; Clang Sanitizers & NBSP; en durcissant la sÃĐcuritÃĐ de la bande de base cellulaire dans le & nbsp; Android Operating System & NBSP; et empÊchant des types de vulnÃĐrabilitÃĐs spÃĐcifiques.
Cela comprend un dÃĐsinfectant de dÃĐbordement entier (INTSAN) et BoundsSanitizer (Boundsan), qui font tous deux partie de UndefinedBehaviorsanitizer (UBSAN), un outil conçu pour attraper divers types de
Google is highlighting the role played by Clang sanitizers in hardening the security of the cellular baseband in the Android operating system and preventing specific kinds of vulnerabilities. This comprises Integer Overflow Sanitizer (IntSan) and BoundsSanitizer (BoundSan), both of which are part of UndefinedBehaviorSanitizer (UBSan), a tool designed to catch various kinds of |
Tool Vulnerability Mobile | â â | ||
| 2023-12-13 17:32:00 | Comment analyser le trafic rÃĐseau de malware \\ dans un bac à sable How to Analyze Malware\\'s Network Traffic in A Sandbox (lien direct) |
L'analyse des logiciels malveillants englobe un large ÃĐventail d'activitÃĐs, notamment en examinant le trafic rÃĐseau des logiciels malveillants.Pour y Être efficace, il est crucial de comprendre les dÃĐfis communs et comment les surmonter.Voici trois problÃĻmes courants que vous pouvez rencontrer et les outils dont vous aurez besoin pour les rÃĐsoudre.
DÃĐcrit le trafic HTTPS
Protocole de transfert hypertexte Secure (HTTPS), le protocole pour sÃĐcuriser
Malware analysis encompasses a broad range of activities, including examining the malware\'s network traffic. To be effective at it, it\'s crucial to understand the common challenges and how to overcome them. Here are three prevalent issues you may encounter and the tools you\'ll need to address them. Decrypting HTTPS traffic Hypertext Transfer Protocol Secure (HTTPS), the protocol for secure |
Malware Tool | â â â | ||
| 2023-12-13 17:00:00 | Floss pour gophers et crabes: extraire les chaÃŪnes de go et les exÃĐcutables de rouille FLOSS for Gophers and Crabs: Extracting Strings from Go and Rust Executables (lien direct) |
|
Tool Technical | â â â â | ||
| 2023-12-13 16:25:00 | Microsoft met en garde contre les pirates exploitant Oauth pour l'extraction et le phishing des crypto-monnaies Microsoft Warns of Hackers Exploiting OAuth for Cryptocurrency Mining and Phishing (lien direct) |
Microsoft a averti que les adversaires utilisent des applications OAuth comme outil d'automatisation pour dÃĐployer des machines virtuelles (VM) pour l'exploitation de crypto-monnaie et le lancement d'attaques de phishing.
"Les acteurs de la menace compromettent les comptes d'utilisateurs pour crÃĐer, modifier et accorder des privilÃĻges ÃĐlevÃĐs aux applications OAuth qu'ils peuvent abuser pour cacher l'activitÃĐ malveillante", l'ÃĐquipe Microsoft Threat Intelligence & nbsp; a dit & nbsp; dans un
Microsoft has warned that adversaries are using OAuth applications as an automation tool to deploy virtual machines (VMs) for cryptocurrency mining and launch phishing attacks. "Threat actors compromise user accounts to create, modify, and grant high privileges to OAuth applications that they can misuse to hide malicious activity," the Microsoft Threat Intelligence team said in an |
Tool Threat | â â | ||
| 2023-12-13 13:40:53 | Vers une utilisation généralisée de l\'IA, de la consolidation des outils et de l\'OpenTelemetry dans le secteur de l\'observabilité d\'ici 2024 (lien direct) | Les budgets resteront toujours un point d'attention pour les DSI et CTO mais l'observabilité continuera à générer des résultats significatifs avec des analyses qui continueront d'être précieuses. Zoom sur les pratiques en matière d'observabilité qui vont s'accélérer en 2024. | Tool | â â | ||
| 2023-12-13 11:00:00 | Qu'est-ce que la sÃĐcuritÃĐ centrÃĐe sur les donnÃĐes? What is data-centric security? (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Data is the lifeblood of organizations. It drives decision-making, fosters innovation, and underpins business operations. However, this wealth of data is scattered across multiple cloud platforms, making it an attractive target for cybercriminals, and rendering traditional approaches to data protection obsolete. This is where data-centric security comes into play. This article will explore the concept of data-centric security, why businesses need it, and the benefits it offers. Understanding data-centric security Data-centric security is a comprehensive approach to safeguarding sensitive data by focusing on the data itself rather than the network or perimeter. It revolves around protecting data throughout its lifecycle, ensuring that even if security perimeters are breached, the data remains secure. Data-centric security comprises several key components and principles, including: Data discovery and classification: Identifying and categorizing data based on its sensitivity is the first step in protecting it. By knowing what data is most critical, you can allocate resources and protection measures accordingly. Access controls and permissions: Fine-grained access controls and role-based permissions are essential to restrict data access to authorized users and roles, reducing the risk of data exposure. Encryption: Encrypting data at rest and in transit adds an extra layer of protection, making data inaccessible to unauthorized individuals. Activity monitoring: Real-time activity monitoring and auditing capabilities help detect unusual data access or transfer patterns, allowing for immediate response to potential security incidents. Incident response and mitigation: Effective incident response is crucial in case of a breach or unauthorized access, enabling quick identification of the issue and mitigating any damage. Why businesses need data-centric security The amount of data being used by organizations for day-to-day operations is increasing rapidly. The importance of adopting a data-centric approach to data protection can be summarized into three main reasons: 1. Traditional security is insufficient. Businesses leverage multiple cloud environments, and sensitive data, such as personal information or intellectual property, are migrated and sprawled across these platforms, expanding the attack surface. Data vulnerabilities become increasingly common when network perimeters are hard to define in a hybrid work environment. Applying safeguards directly to data is needed to create more barriers that repel unauthorized data distribution. Data-centric security protects data from all kinds of threats, such as external attackers or negligent employees. 2. Apply granular access controls. Data-centric security is a vital approach to protect your data dynamically. It enables you to have more flexibility in managing your systems and networks by providing fine-grained access controls, which are more effective than traditional access controls. This framework is particularly critical in scenarios where not every user should have access to the entire data within their department. 3. Integrate with existing tech stack. Data-centric security is an effective way to protect a company\'s data from cyber threats. It can be added to existing infrastructure without disrupting normal operations or requiring drastic changes. This allows companies to gradually improve their security measures while freeing up resources for other purposes. Benefits of data-centric security As data becomes increasingly valuable as a competitive advantage, organizations have | Data Breach Tool Vulnerability Cloud | â â | ||
| 2023-12-13 10:34:46 | DOE lance des outils Cyote pour une cybersÃĐcuritÃĐ OT amÃĐliorÃĐe, prend en charge la prise de dÃĐcision de cybersÃĐcuritÃĐ axÃĐe sur le risque DOE launches CyOTE tools for enhanced OT cybersecurity, supports risk-informed cybersecurity decision-making (lien direct) |
Le bureau amÃĐricain de l'ÃĐnergie de l'Ãnergie de la cybersÃĐcuritÃĐ, de la sÃĐcuritÃĐ ÃĐnergÃĐtique et des interventions d'urgence (CESER) a introduit un ensemble ...
The U.S. Department of Energy’s Office of Cybersecurity, Energy Security, and Emergency Response (CESER) has introduced a set... |
Tool Industrial | â â | ||
| 2023-12-13 06:39:57 | La guerre ouverte à l\'encontre des VPN (lien direct) | Disparition de plus de 20 outils anti-censure sur GitHub : la main du gouvernement chinois ?... | Tool | â â â | ||
| 2023-12-13 02:48:27 | Conseils pour rÃĐussir avec un audit CIP du NERC Tips for Achieving Success With a NERC CIP Audit (lien direct) |
Les services publics ÃĐlectriques sont responsables de tout ce que nous faisons.Cela prÃĐsente un ÃĐnorme fardeau pour ceux qui exploitent ces services publics.Une façon dont ces organisations offrent l'assurance se font par le biais du processus d'audit.Bien que les audits puissent gÃĐnÃĐrer une anxiÃĐtÃĐ considÃĐrable, une bonne planification et des outils peuvent aider à faire en sorte que l'ensemble du processus se dÃĐroule en douceur.De plus, ceux-ci peuvent ÃĐgalement aider à obtenir des rÃĐsultats positifs.Lors du rÃĐcent groupe de travail sur la conformitÃĐ Tripwire Energy & NERC, nous avons demandÃĐ Ã deux professionnels de longue date de l'industrie comment ils abordent et conquÃĐrir les audits du NERC CIP.Un gestionnaire de la sÃĐcuritÃĐ des infrastructures et un senior ...
Electrical utilities are responsible for just about everything we do. This presents a tremendous burden on those who operate those utilities. One way these organizations offer assurance is through the audit process. While audits can generate tremendous anxiety, good planning, and tools can help make the entire process go smoothly. Moreover, these can also help to achieve positive results. At the recent Tripwire Energy & NERC Compliance Working Group, we asked two long-time industry professionals how they approach and conquer NERC CIP audits. A Manager of Infrastructure Security and a Senior... |
Tool | â â | ||
| 2023-12-12 18:18:34 | Journal d'un ingÃĐnieur de dÃĐtection: soufflÃĐ Ã BitsAdmin Diary of a Detection Engineer: Blown to BITSAdmin (lien direct) |
La combinaison de l'outil BitsAdmin avec Veritas Backup Software a pointÃĐ nos ingÃĐnieurs de dÃĐtection vers une tentative d'attaque de ransomware.
The combination of the BITSAdmin tool with Veritas backup software pointed our detection engineers to an attempted ransomware attack. |
Ransomware Tool | â â â | ||
| 2023-12-12 12:00:09 | Durcissant les bandes de base cellulaire dans Android Hardening cellular basebands in Android (lien direct) |
Posted by Ivan Lozano and Roger Piqueras Jover Android\'s defense-in-depth strategy applies not only to the Android OS running on the Application Processor (AP) but also the firmware that runs on devices. We particularly prioritize hardening the cellular baseband given its unique combination of running in an elevated privilege and parsing untrusted inputs that are remotely delivered into the device. This post covers how to use two high-value sanitizers which can prevent specific classes of vulnerabilities found within the baseband. They are architecture agnostic, suitable for bare-metal deployment, and should be enabled in existing C/C++ code bases to mitigate unknown vulnerabilities. Beyond security, addressing the issues uncovered by these sanitizers improves code health and overall stability, reducing resources spent addressing bugs in the future. An increasingly popular attack surface As we outlined previously, security research focused on the baseband has highlighted a consistent lack of exploit mitigations in firmware. Baseband Remote Code Execution (RCE) exploits have their own categorization in well-known third-party marketplaces with a relatively low payout. This suggests baseband bugs may potentially be abundant and/or not too complex to find and exploit, and their prominent inclusion in the marketplace demonstrates that they are useful. Baseband security and exploitation has been a recurring theme in security conferences for the last decade. Researchers have also made a dent in this area in well-known exploitation contests. Most recently, this area has become prominent enough that it is common to find practical baseband exploitation trainings in top security conferences. Acknowledging this trend, combined with the severity and apparent abundance of these vulnerabilities, last year we introduced updates to the severity guidelines of Android\'s Vulnerability Rewards Program (VRP). For example, we consider vulnerabilities allowing Remote Code Execution (RCE) in the cellular baseband to be of CRITICAL severity. Mitigating Vulnerability Root Causes with Sanitizers Common classes of vulnerabilities can be mitigated through the use of sanitizers provided by Clang-based toolchains. These sanitizers insert runtime checks against common classes of vulnerabilities. GCC-based toolchains may also provide some level of support for these flags as well, but will not be considered further in this post. We encourage you to check your toolchain\'s documentation. Two sanitizers included in Undefine | Tool Vulnerability Threat Mobile Prediction Conference | â â â | ||
| 2023-12-12 11:00:00 | Qu'est-ce que le partage de l'intelligence des menaces de cybersÃĐcuritÃĐ What is Cybersecurity threat intelligence sharing (lien direct) |
Knowledge is power and collaboration is key for organizations to continuously adapt and improve their security measures in order to stay ahead of cybercriminals. An effective way to stay ahead is by enhancing an organization\'s security posture through cybersecurity threat intelligence sharing. By exchanging information about potential and existing cyber threats with other organizations, individuals, or entities, organizations can better understand the threat landscape and make informed decisions about their security strategies. In this article, we will explore what threat intelligence sharing is and provide guidance on starting your own program.
How threat intelligence sharing works
Threat intelligence sharing can be compared to a neighborhood watch program, where community members collaborate and share information about suspicious activities, potential threats, and crime incidents to improve the overall safety and security of the neighborhood.
 Similarly, threat intelligence sharing is a collaborative process that enables organizations to exchange information such as indicators of compromise (IoCs), tactics, techniques, and procedures (TTPs), and vulnerabilities between each other. It involves gathering threat intelligence from various sources, such as internal network logs, security tools, open-source intelligence (OSINT), commercial threat intelligence feeds, and industry-specific sharing communities like Information Sharing and Analysis Centers (ISACs).
The collected data is then analyzed to identify patterns, trends, and actionable insights, which help organizations understand the threat landscape and make informed decisions about their security strategies.
Addressing threat intelligence sharing legal, regulatory, and privacy concerns
To maintain privacy and foster collaboration, organizations should establish clear guidelines and use standardized protocols like Structured Threat Information Expression (STIX) or Trusted Automated eXchange of Indicator Information (TAXII) when sharing threat intelligence outside the company. This collaborative approach will ultimately improve the security posture of all participating organizations.
Also, participating organizations should work closely with legal and compliance teams to understand the requirements and establish guidelines for sharing threat intelligence while adhering to data privacy regulations and industry-specific compliance standards. Guidelines should include sanitization, anonymization, and encryption techniques to protect sensitive information from being publicly disclosed.
How threat intelligence data is structured
Standardized formats and languages, such as STIX or TAXII, are used to structure the data, ensuring consistency, readability, and easy processing by different tools and systems. Organizations share this threat intelligence through various channels, including email, file transfers, web platforms, or automated protocols like STIX and TAXII. Shared intelligence is then consumed, and appropriate countermeasures are implemented based on the insights gained.
Organizations collaboratively and continuously monitor the effectiveness of their threat intelligence sharing efforts, providing feedback to each other and refining their processes to improve the quality and relevance of the shared data.
Benefits of participating in threat intelligence sharing
Just as neighborhood watch programs promote involvement through community building, shared responsibility, and mutual benefit, threat intelligence sharing programs encourage participation by doing the following:
Raising aw
Similarly, threat intelligence sharing is a collaborative process that enables organizations to exchange information such as indicators of compromise (IoCs), tactics, techniques, and procedures (TTPs), and vulnerabilities between each other. It involves gathering threat intelligence from various sources, such as internal network logs, security tools, open-source intelligence (OSINT), commercial threat intelligence feeds, and industry-specific sharing communities like Information Sharing and Analysis Centers (ISACs).
The collected data is then analyzed to identify patterns, trends, and actionable insights, which help organizations understand the threat landscape and make informed decisions about their security strategies.
Addressing threat intelligence sharing legal, regulatory, and privacy concerns
To maintain privacy and foster collaboration, organizations should establish clear guidelines and use standardized protocols like Structured Threat Information Expression (STIX) or Trusted Automated eXchange of Indicator Information (TAXII) when sharing threat intelligence outside the company. This collaborative approach will ultimately improve the security posture of all participating organizations.
Also, participating organizations should work closely with legal and compliance teams to understand the requirements and establish guidelines for sharing threat intelligence while adhering to data privacy regulations and industry-specific compliance standards. Guidelines should include sanitization, anonymization, and encryption techniques to protect sensitive information from being publicly disclosed.
How threat intelligence data is structured
Standardized formats and languages, such as STIX or TAXII, are used to structure the data, ensuring consistency, readability, and easy processing by different tools and systems. Organizations share this threat intelligence through various channels, including email, file transfers, web platforms, or automated protocols like STIX and TAXII. Shared intelligence is then consumed, and appropriate countermeasures are implemented based on the insights gained.
Organizations collaboratively and continuously monitor the effectiveness of their threat intelligence sharing efforts, providing feedback to each other and refining their processes to improve the quality and relevance of the shared data.
Benefits of participating in threat intelligence sharing
Just as neighborhood watch programs promote involvement through community building, shared responsibility, and mutual benefit, threat intelligence sharing programs encourage participation by doing the following:
Raising aw |
Tool Vulnerability Threat Commercial | â â â | ||
| 2023-12-12 10:37:13 | Android iMessage App Beeper publie la mise à jour de travail de l'outil Blue Bubbled Android iMessage app Beeper releases working update of blue-bubbled tool (lien direct) |
Dev prÃĐtend avoir rÃĐsolu le problÃĻme \\ 'qui a fait que les messages ne sont pas envoyÃĐs ou reçus \' Le dÃĐveloppeur derriÃĻre Beeper Mini vient de publier une version mise à jour de l'application Android autonome qui, selon les utilisateurs, peutCasquez le bloc Apple mis en place pendant le week-end.âĶ
Dev claims to have fixed \'issue that caused messages not to be sent or received\' The developer behind Beeper Mini just released an updated version of the standalone Android app that users say can sidestep the block Apple put in place over the weekend.âĶ |
Tool Mobile | â â â | ||
| 2023-12-12 05:00:00 | MÃĐmoire de sÃĐcuritÃĐ: TA4557 cible les recruteurs directement par e-mail Security Brief: TA4557 Targets Recruiters Directly via Email (lien direct) |
What happened Since at least October 2023, TA4557 began using a new technique of targeting recruiters with direct emails that ultimately lead to malware delivery. The initial emails are benign and express interest in an open role. If the target replies, the attack chain commences.  Previously, throughout most of 2022 and 2023, TA4557 typically applied to existing open job listings purporting to be a job applicant. The actor included malicious URLs, or files containing malicious URLs, in the application. Notably, the URLs were not hyperlinked and the user would have to copy and paste the URL text to visit the website. The legitimate job hosting sites would then generate and send email notifications to the prospective employers who posted the positions. In recently observed campaigns, TA4557 used both the new method of emailing recruiters directly as well as the older technique of applying to jobs posted on public job boards to commence the attack chain. Specifically in the attack chain that uses the new direct email technique, once the recipient replies to the initial email, the actor was observed responding with a URL linking to an actor-controlled website posing as a candidate resume. Alternatively, the actor was observed replying with a PDF or Word attachment containing instructions to visit the fake resume website. Example initial outreach email by TA4557 to inquire about a job posting. Example follow up email containing a URL linking to a fake resume website. Very notably, in campaigns observed in early November 2023, Proofpoint observed TA4557 direct the recipient to ârefer to the domain name of my email address to access my portfolioâ in the initial email instead of sending the resume website URL directly in a follow up response. This is likely a further attempt to evade automated detection of suspicious domains. Email purporting to be from a candidate directing the recipient to visit the domain in an email address. If the potential victims visit the âpersonal websiteâ as directed by the threat actor, the page mimics a candidate\'s resume or job site for the candidate (TA4557) applying for a posted role. The website uses filtering to determine whether to direct the user to the next stage of the attack chain. Example of a fake candidate website operated by TA4557 that leads to download of a zip attachment.  If the potential victim does not pass the filtering checks, they are directed to a page containing a resume in plain text. Alternatively, if they pass the filtering checks, they are directed to the candidate website. The candidate website uses a CAPTCHA which, if completed, will initiate the download of a zip file containing a shortcut file (LNK). The LNK, if executed, abuses legitimate software functions in "ie4uinit.exe" to download and execute a scriptlet from a location stored in the "ie4uinit.inf" file. This technique is commonly referred to as "Living Off The Land" (LOTL).  The scriptlet decrypts and drops a DLL in the %APPDATA%\Microsoft folder. Next, it attempts to create a new regsrv32 process to execute the DLL using Windows Management Instrumentation (WMI) and, if that fails, tries an alternative approach using the ActiveX Object Run method. The DLL employs anti-sandbox and anti-analysis techniques. It incorporates a loop specifically designed to retrieve the RC4 key necessary for deciphering the More_Eggs backdoor. This loop is strategically crafted to extend its execution time, enhancing its evasion capabilities within a sandbox environment. Furthermore, the DLL employs multiple checks to determine if it is currently being debugged, utilizing the NtQueryInformationProcess function. The DLL drops the More_Eggs backdoor along with the MSXSL executable. Subsequently, it initiates the creation of the MSXSL process using the WMI service. Once completed, the DLL deletes itself. More_Eggs can be used to establish persistence, profile the machine, and drop additional payloads. Attribution Proofpoint has been tracking TA4557 since 2018 as a | Malware Tool Threat | â â â | ||
| 2023-12-11 16:53:06 | EntitÃĐ ÃĐlectrique ukrainienne ciblÃĐe d'ÃĐlectrum à l'aide d'outils personnalisÃĐs et de logiciels malveillants CaddyWiper, octobre 2022 ELECTRUM Targeted Ukrainian Electric Entity Using Custom Tools and CaddyWiper Malware, October 2022 (lien direct) |
> Le 9 novembre 2023, Mandiant a publiÃĐ de nouveaux dÃĐtails des enquÊtes mÃĐdico-lÃĐgales à la suite d'une attaque perturbatrice contre l'Ukraine Electric Sondat qui ...
Le post Electrum Electric Ukrainian Electric à l'aide d'outils personnalisÃĐs et de malware de caddywiper, octobre octobre, octobre2022 est apparu pour la premiÃĻre fois sur dragos .
>On November 9, 2023, Mandiant released new details from forensic investigations following a disruptive attack against Ukraine electric substation which... The post ELECTRUM Targeted Ukrainian Electric Entity Using Custom Tools and CaddyWiper Malware, October 2022 first appeared on Dragos. |
Malware Tool Industrial | â â â | ||
| 2023-12-11 13:00:22 | Autonomiser les dÃĐfenses de la cybersÃĐcuritÃĐ avec Horizon IOC Empower Cyber Security Defenses with Horizon IOC (lien direct) |
> Les menaces de cybersÃĐcuritÃĐ se dÃĐplacent rapidement, donc avoir une solution robuste et centralisÃĐe pour gÃĐrer les indicateurs de compromis (CIO) est crucial.Check Point prÃĐsente Horizon IOC, une plate-forme innovante conçue pour rationaliser la gestion du CIO dans l'entreprise.Gestion centralisÃĐe du CIO pour Horizon Control Horizon sans couture sert de plate-forme centralisÃĐe, intÃĐgrant de maniÃĻre transparente les sources de donnÃĐes à partir de produits de contrÃīle, d'ÃĐquipes SOC et de points de vente externes.Cet outil convivial permet aux organisations en consolidant divers flux de donnÃĐes dans une seule interface de gestion unifiÃĐe.L'application immÃĐdiate des politiques dans les politiques d'entreprise dÃĐfinies au sein du directeur de l'IOC Horizon ne sont pas seulement des directives thÃĐoriques;Ils sont immÃĐdiatement appliquÃĐs à travers [& # 8230;]
>Cyber security threats move fast, so having a robust and centralized solution for managing Indicators of Compromise (IOCs) is crucial. Check Point introduces Horizon IOC, an innovative platform designed to streamline IOC management across the enterprise. Centralized IOC Management for Seamless Control Horizon IOC serves as a centralized platform, seamlessly integrating data sources from Check Point products, SOC teams, and external outlets. This user-friendly tool empowers organizations by consolidating diverse data streams into one unified management interface. Immediate Policy Enforcement Across the Enterprise Policies set within the Horizon IOC manager are not just theoretical guidelines; they are immediately enforced across […] |
Tool | â â | ||
| 2023-12-11 11:00:00 | Avez-vous pris en compte les risques d'IA dans votre cadre de gestion des risques Have you accounted for AI risk in your risk management framework (lien direct) |
L'intelligence artificielle (IA) est sur le point d'influencer considÃĐrablement diverses facettes de la sociÃĐtÃĐ, couvrant les soins de santÃĐ, le transport, la finance et la sÃĐcuritÃĐ nationale.Les praticiens de l'industrie et les citoyens dans l'ensemble envisagent et discutent activement des innombrables façons d'IA pourraient Être utilisÃĐes ou devraient Être appliquÃĐes. Il est crucial de comprendre et de traiter soigneusement les consÃĐquences rÃĐelles du dÃĐploiement de l'IA, d'aller au-delà des suggestions pour votre prochaine vidÃĐo en streaming ou des prÃĐdictions pour vos prÃĐfÃĐrences d'achat.NÃĐanmoins, une question centrale de notre ÃĐpoque tourne autour de la façon dont nous pouvons exploiter le pouvoir de l'IA pour le plus grand bien de la sociÃĐtÃĐ, visant à amÃĐliorer la vie.L'espace entre l'introduction de la technologie innovante et son potentiel d'utilisation abusive se rÃĐtrÃĐcit rapidement.Alors que nous embrassons avec enthousiasme les capacitÃĐs de l'IA, il est crucial de nous prÃĐparer à des risques technologiques accrus, allant des prÃĐjugÃĐs aux menaces de sÃĐcuritÃĐ. Dans cette ÃĻre numÃĐrique, oÃđ les problÃĻmes de cybersÃĐcuritÃĐ sont dÃĐjà en augmentation, l'IA introduit un nouvel ensemble de vulnÃĐrabilitÃĐs.Cependant, comme nous affronterons ces dÃĐfis, il est crucial de ne pas perdre de vue la situation dans son ensemble.Le monde de l'IA englobe à la fois des aspects positifs et nÃĐgatifs, et il ÃĐvolue rapidement.Pour suivre le rythme, nous devons simultanÃĐment conduire l'adoption de l'IA, dÃĐfendre contre ses risques associÃĐs et assurer une utilisation responsable.Ce n'est qu'alors que nous pouvons dÃĐbloquer le plein potentiel de l'IA pour les progrÃĻs rÃĐvolutionnaires sans compromettre nos progrÃĻs en cours. Aperçu du cadre de gestion des risques d'intelligence artificielle NIST Le cadre de gestion des risques de l'IA NIST (AI RMF) est une directive complÃĻte dÃĐveloppÃĐe par le NIST, en collaboration avec diverses parties prenantes et en alignant les efforts lÃĐgislatifs, pour aider les organisations à gÃĐrer les risques associÃĐs aux systÃĻmes d'IA.Il vise à amÃĐliorer la fiabilitÃĐ et à minimiser les dommages potentiels des technologies de l'IA.Le cadre est divisÃĐ en deux parties principales: Planification et comprÃĐhension: cette partie se concentre sur l'hiver les organisations pour ÃĐvaluer les risques et les avantages de l'IA, dÃĐfinissant les critÃĻres des systÃĻmes d'IA dignes de confiance.La fiabilitÃĐ est mesurÃĐe en fonction de facteurs tels que la validitÃĐ, la fiabilitÃĐ, la sÃĐcuritÃĐ, la rÃĐsilience, la responsabilitÃĐ, la transparence, l'explication, l'amÃĐlioration de la confidentialitÃĐ et l'ÃĐquitÃĐ avec les biais gÃĐrÃĐs. Guidance exploitable: cette section, connue sous le nom de noyau du cadre, dÃĐcrit quatre ÃĐtapes clÃĐs - gouverner, mapper, mesurer et gÃĐrer.Ces ÃĐtapes sont intÃĐgrÃĐes dans le processus de dÃĐveloppement du systÃĻme d'IA pour ÃĐtablir une culture de gestion des risques, identifier et ÃĐvaluer les risques et mettre en Åuvre des stratÃĐgies d'attÃĐnuation efficaces. Gassement d'informations: collectionner des donnÃĐes essentielles sur les systÃĻmes d'IA, tels que les dÃĐtails du projet et les dÃĐlais. Gover: Ãtablir une forte culture de gouvernance pour la gestion des risques de l'IA dans toute l'organisation. MAP: Framer les risques dans le contexte du systÃĻme d'IA pour amÃĐliorer l'identification des risques. Mesure: en utilisant diverses mÃĐthodes pour analyser et surveiller les risques d'IA et leurs impacts. GÃĐrer: appliquer des pratiques systÃĐmatiques pour traiter les risques identifiÃĐs, en se concentrant sur le traitement des risques et la planification des rÃĐponses. L'IA RMF est un excellent outil pour aider les organisations à crÃĐer un programme de gouvernance solide et à gÃĐrer les risques associÃĐs à leurs systÃĻmes d'IA.MÊme s'il n'est pas obligatoire en vertu des lois proposà | Tool Vulnerability Guideline | â â â | ||
| 2023-12-11 08:00:00 | Pixi – Pour créer des environnements de dev aux petits oignons (lien direct) | Pixi, un projet écrit en Rust, est un gestionnaire de paquets fonctionnant sur l'écosystème Conda, supportant plusieurs langages de programmation et permettant d'installer toutes les bibliothèques et outils nécessaires pour vos projets. Il crée automatiquement des lockfiles pour reproduire des environnements identiques entre les systèmes d'exploitation sans Docker. Pixi est également capable de créer des packages Conda prêts à être déployés. | Tool | â â | ||
| 2023-12-10 08:00:00 | Comment installer Windows 11 ARM sur VMware Fusion – Apple Silicon (lien direct) | Après avoir réussi à installer un Windows 11 ARM sur son iMac M3 ARM64, l'auteur explique le processus : télécharger l'image de Windows 11 ARM, convertir le fichier .VHDX inutile pour VMware en .VMDK via l'outil vdiskmanager de VMware, puis créer une nouvelle VM dans VMware. Il faut ensuite sélectionner Windows 11 ARM comme OS, activer le 'Démarrage sécurisé UEFI', et choisir l'image VMDK comme disque virtuel. L'installation de Windows se fait sans support réseau, grâce à la commande 'OOBE\BYPASSNRO'. Pour activer le réseau, il faut lancer un Powershell en admin, entrer la commande 'Set-ExecutionPolicy RemoteSigned', et installer les Vmware Tools. | Tool | â â | ||
| 2023-12-08 22:00:00 | CISA ajoute des bogues Qlik au catalogue des vulnÃĐrabilitÃĐs exploitÃĐes CISA adds Qlik bugs to exploited vulnerabilities catalog (lien direct) |
 Deux vulnÃĐrabilitÃĐs affectant un outil d'analyse de donnÃĐes populaires ont ÃĐtÃĐ ajoutÃĐes à la liste des bogues exploitÃĐs de la Cybersecurity and Infrastructure Security Agency \\ Agency (CISA).Jeudi, cisa ajoutÃĐ CVE-2023-41265 et CVE-2023-41266 à son catalogue, donnant le fÃĐdÃĐralagences civiles jusqu'au 28 dÃĐcembre pour corriger les problÃĻmes.Les deux bogues ÃĐtaient TrouvÃĐCet ÃĐtÃĐ au sens Qlik -
Deux vulnÃĐrabilitÃĐs affectant un outil d'analyse de donnÃĐes populaires ont ÃĐtÃĐ ajoutÃĐes à la liste des bogues exploitÃĐs de la Cybersecurity and Infrastructure Security Agency \\ Agency (CISA).Jeudi, cisa ajoutÃĐ CVE-2023-41265 et CVE-2023-41266 à son catalogue, donnant le fÃĐdÃĐralagences civiles jusqu'au 28 dÃĐcembre pour corriger les problÃĻmes.Les deux bogues ÃĐtaient TrouvÃĐCet ÃĐtÃĐ au sens Qlik -
 Two vulnerabilities affecting a popular data analytics tool were added to the Cybersecurity and Infrastructure Security Agency\'s (CISA) list of exploited bugs this week. On Thursday, CISA added CVE-2023-41265 and CVE-2023-41266 to its catalog, giving federal civilian agencies until December 28 to patch the issues. Both bugs were found this summer in Qlik Sense -
Two vulnerabilities affecting a popular data analytics tool were added to the Cybersecurity and Infrastructure Security Agency\'s (CISA) list of exploited bugs this week. On Thursday, CISA added CVE-2023-41265 and CVE-2023-41266 to its catalog, giving federal civilian agencies until December 28 to patch the issues. Both bugs were found this summer in Qlik Sense - |
Tool Vulnerability | â â â | ||
| 2023-12-08 06:00:37 | ProtÃĐger les identitÃĐs: comment ITDR complÃĻte EDR et XDR pour garder les entreprises plus en sÃĐcuritÃĐ Protecting identities: How ITDR Complements EDR and XDR to Keep Companies Safer (lien direct) |
Defenders who want to proactively protect their company\'s identities have no shortage of security tools to choose from. There are so many, in fact, that it seems like a new category of tool is invented every few months just to help keep them all straight. Because most security teams are finding it increasingly difficult to stop attackers as they use identity vulnerabilities to escalate privilege and move laterally across their organization\'s IT environment, some of today\'s newest tools focus on this middle part of the attack chain. Endpoint detection and response (EDR) and extended detection and response (XDR) are two tools that claim to cover this specialized area of defense. But unfortunately, because of their fundamental architecture and core capabilities, that\'s not really what they do best. That\'s why a new category of tool-identity threat detection and response (ITDR)-is emerging to fill the gaps. In this blog post, we\'ll explain the difference between EDR, XDR and ITDR so that you can understand how these tools complement and reinforce each other. They each have strengths, and when they\'re combined they provide even better security coverage. But first, let\'s rewind the cybersecurity evolution timeline back to the 1980s to understand why ITDR has emerged as a critical defense measure in today\'s threat landscape. The rise of antivirus software and firewalls We\'re starting in the 1980s because that\'s the decade that saw the advent of computer networks and the proliferation of personal computers. It also saw the rapid rise of new threats due to adversaries taking advantage of both trends. There were notable computer threats prior to this decade, of course. The âCreeperâ self-replicating program in 1971 and the ANIMAL Trojan in 1975 are two examples. But the pace of development picked up considerably during the 1980s as personal computing and computer networking spread, and bad actors and other mischief-makers sought to profit from or simply break into (or break) devices and systems. In 1987, the aptly named Bernd Robert Fix, a German computer security expert, developed a software program to stop a virus known as Vienna. This virus destroyed random files on the computers it infected. Fix\'s program worked-and the antivirus software industry was born. However, while early antivirus tools were useful, they could only detect and remove known viruses from infected systems. The introduction of firewalls to monitor and control network traffic is another security advancement from the decade. Early ânetwork layerâ firewalls were designed to judge âpacketsâ (small chunks of data) based on simple information like the source, destination and connection type. If the packets passed muster, they were sent to the system requesting the data; if not, they were discarded. The internet explosion-and the escalation of cybercrime The late 1990s and early 2000s witnessed the explosive growth of the internet as a key business platform, kicking off an era of tremendous change. It brought new opportunities but also many new security risks and threats. Cybercrime expanded and became a more formalized and global industry during this time. Bad actors focused on developing malware and other threats. Email with malicious attachments and crafty social engineering strategies quickly became favorite tools for adversaries looking to distribute their innovations and employ unsuspecting users in helping to activate their criminal campaigns. As cyberthreats became more sophisticated, defenders evolved traditional detective security tools to feature: Signature-based detection to identify known malware Heuristic analysis to detect previously difficult to detect threats based on suspicious behavioral patterns All of these methods were effective to a degree. But once again, they could not keep in step with cybercriminal innovation and tended to generate a lot of false positives and false negatives. Enter the SIEM Around 2005, security information and event management (SIEM) tools emerged to enhance | Ransomware Malware Tool Vulnerability Threat Studies Cloud | â â â | ||
| 2023-12-07 07:28:54 | La cyberattaque la plus avancÃĐe de l'Iran \\ Iran\\'s Most Advanced Cyber Attack Yet (lien direct) |
> Depuis des annÃĐes maintenant, les pirates parrainÃĐs par l'Ãtat d'Iran ont ÃĐtÃĐ parmi les plus prolifiques au monde.Mais prolifique ne signifie pas nÃĐcessairement sophistiquÃĐ & # 8212;Ses attaques ne sont pas trÃĻs impressionnÃĐes dans la façon dont les Ãtats-Unis, la Russie et la Chine.Mais dans une campagne rÃĐcemment dÃĐcouverte par Checkpoint, un APT iranien a dÃĐclenchÃĐ des outils et des tactiques contrairement à [& # 8230;]
>For years now, Iran\'s state-sponsored hackers have been some of the most prolific in the world. But prolific does not necessarily mean sophisticated — its attacks haven\'t quite impressed in the way that the U.S., Russia, and China\'s do. But in a campaign recently uncovered by CheckPoint, one Iranian APT unleashed tools and tactics unlike […] |
Tool | â â â | ||
| 2023-12-07 00:04:10 | Chatgpt Builder aide à crÃĐer des campagnes d'arnaque et de piratage ChatGPT builder helps create scam and hack campaigns (lien direct) |
Un outil de pointe de l'IA ouverte semble mal modÃĐrÃĐ, ce qui lui permet d'Être abusÃĐ par les cybercriminels.
A cutting-edge tool from Open AI appears to be poorly moderated, allowing it to be abused by cyber-criminals. |
Hack Tool | ChatGPT | â â | |
| 2023-12-07 00:00:00 | L'outil DFIR intÃĐgrÃĐ peut simplifier et accÃĐlÃĐrer la cyber-criminalistique Integrated DFIR Tool Can Simplify and Accelerate Cyber Forensics (lien direct) |
Explorez des cas d'utilisation rÃĐels dÃĐmontrant l'impact transformateur de Trend Vision One âĒ & # 8211;Pays -cent-chef, un outil intÃĐgrÃĐ de la criminalistique numÃĐrique et de la rÃĐponse aux incidents (DFIR)
Explore real use cases demonstrating the transformative impact of Trend Vision OneâĒ – Forensics, an integrated Digital Forensics and Incident Response (DFIR) tool |
Tool Prediction | â â â | ||
| 2023-12-06 22:30:00 | Les dirigeants du CongrÃĻs cherchent à ÃĐtendre le programme de surveillance contestÃĐ jusqu'en avril Congressional leaders seek to extend contested surveillance program until April (lien direct) |
 La vie des outils d'espionnage ÃĐtrangers qui devrait expirer dans quelques semaines pourrait Être briÃĻvement prolongÃĐe jusqu'au 19 avril aprÃĻs que les dirigeants du CongrÃĻs ont insÃĐrÃĐ un renouvellement à court terme dans le projet de loi annuel sur la politique de dÃĐfense.La dÃĐcision d'attacher un renouvellement temporaire de l'article 702 de la Foreign Intelligence Surveillance Act au plan de politique massive vient
La vie des outils d'espionnage ÃĐtrangers qui devrait expirer dans quelques semaines pourrait Être briÃĻvement prolongÃĐe jusqu'au 19 avril aprÃĻs que les dirigeants du CongrÃĻs ont insÃĐrÃĐ un renouvellement à court terme dans le projet de loi annuel sur la politique de dÃĐfense.La dÃĐcision d'attacher un renouvellement temporaire de l'article 702 de la Foreign Intelligence Surveillance Act au plan de politique massive vient
 The life of foreign spying tools set to expire in a few weeks could be briefly extended until April 19 after congressional leaders inserted a short-term renewal into the annual defense policy bill. The decision to attach a temporary renewal of Section 702 of the Foreign Intelligence Surveillance Act to the massive policy blueprint comes
The life of foreign spying tools set to expire in a few weeks could be briefly extended until April 19 after congressional leaders inserted a short-term renewal into the annual defense policy bill. The decision to attach a temporary renewal of Section 702 of the Foreign Intelligence Surveillance Act to the massive policy blueprint comes |
Tool | â â | ||
| 2023-12-06 20:55:10 | Le cyber stellaire lance un programme universitaire ÃĐprouvÃĐ sur le terrain Stellar Cyber Launches Field-Proven University Program (lien direct) |
Getting that first job after completing a university degree can be challenging. This is true even for cybersecurity - an industry with millions of available roles. Anecdotally, it can take 6 months or up to a year for a graduate to land their first job in cybersecurity. Sometimes, they have to settle for different roles that will eventually help them advance to the one they initially wanted. There are several reasons why new graduates can\'t find a job in cybersecurity. First, they don\'t have someone to guarantee for them yet. Companies would rather hire someone who has a proven track record - and real-life experience. Entry-level positions are scarce in cybersecurity. After you read the job description, you also realize that most job postings aren\'t really for someone who is just getting started in the industry. Since the last year was marked by a lot of layoffs, those who recently graduated are competing for jobs against highly skilled experts (in specific areas). At the heart of the problem is this: Most freshly graduated students don\'t have real-life experience to back up their theoretical knowledge. How does the OpenXDR innovator Stellar Cyber open up opportunities for future security professionals with its first and invite-only Stellar Cyber University Program? Skills Gap Created in University Graduates struggle to find opportunities because there is a gap between what the university teaches and the skills that are genuinely needed for the job. Companies often look for someone who has specialized knowledge and practical experience in a particular segment of security operations. This is where the skill gap is most evident in the IT industry. Therefore, the skills gap starts at university. While universities might want to provide students with practical experiences, most are limited by their funding and time constraints. We\'re talking about a quickly evolving industry that would require frequent alterations to the curriculum. It\'s not possible for universities to change the curriculum or even to provide training. They\'d have to cover the training, tools, and people to coach the students. This is why it\'s important for security vendors and universities that are teaching the next generation of security experts to collaborate and complete the theory with practice. Stellar Cyber\'s new program helps the universities do just that for free. âStellar Cyber is proud to offer this comprehensive, collaborative education program free of charge for those training our cyber warriors of the future,â said Jim O’Hara, Chief Revenue Officer at Stellar Cyber. âWe are honored to do our part to help shrink the worldwide cybersecurity skills gap and provide security services to communities in need. It\'s our objective to scale as broadly as possible and to assist universities as they prepare their graduates to enter the cybersecurity workforce.â Technology, Mentorship, and Training | Tool | â â â | ||
| 2023-12-06 18:15:00 | Le pouvoir judiciaire de la Chambre efface facilement le projet de loi pour renouveler les outils de surveillance avec mandat de mandat House Judiciary easily clears bill to renew surveillance tools with warrant mandate (lien direct) |
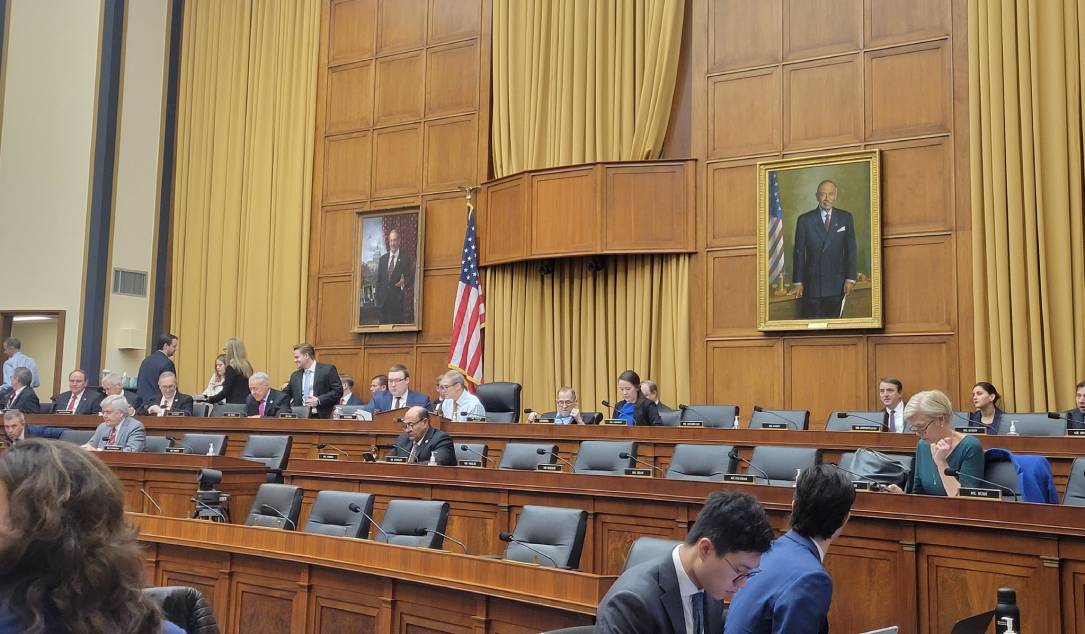 Mercredi, le comitÃĐ judiciaire de la Chambre a approuvÃĐ une massification massivement un projet de loi bipartite qui obligerait toutes les agences de renseignement aux Ãtats-Unis pour obtenir un mandat judiciaire avant de rechercher des informations sur les AmÃĐricains rÃĐcupÃĐrÃĐs par de puissants outils d'espionnage ÃĐlectronique.Les lÃĐgislateurs ont votÃĐ 35 Ã 2 en faveur du ProtÃĐger la libertÃĐ et finir la loi de surveillance sans mandat
Mercredi, le comitÃĐ judiciaire de la Chambre a approuvÃĐ une massification massivement un projet de loi bipartite qui obligerait toutes les agences de renseignement aux Ãtats-Unis pour obtenir un mandat judiciaire avant de rechercher des informations sur les AmÃĐricains rÃĐcupÃĐrÃĐs par de puissants outils d'espionnage ÃĐlectronique.Les lÃĐgislateurs ont votÃĐ 35 Ã 2 en faveur du ProtÃĐger la libertÃĐ et finir la loi de surveillance sans mandat
 The House Judiciary Committee on Wednesday overwhelmingly approved a bipartisan bill that would require all U.S. intelligence agencies to obtain a court warrant before searching for information about Americans retrieved by powerful electronic spying tools. Lawmakers voted 35 to 2 in favor of the Protect Liberty and End Warrantless Surveillance Act that would amend and
The House Judiciary Committee on Wednesday overwhelmingly approved a bipartisan bill that would require all U.S. intelligence agencies to obtain a court warrant before searching for information about Americans retrieved by powerful electronic spying tools. Lawmakers voted 35 to 2 in favor of the Protect Liberty and End Warrantless Surveillance Act that would amend and |
Tool | â â â | ||
| 2023-12-06 11:00:00 | Les 29 meilleures pratiques de sÃĐcuritÃĐ des donnÃĐes pour votre entreprise Top 29 data security best practices for your enterprise (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. In this digital era, as data is produced and gathered more than ever before, the importance of data security has surged. Given the widespread use of social media, e-commerce, and other online services, individuals are sharing their personal details with numerous entities. In this blog, we\'ll explore the key concepts of data security and highlight the best practices across various sectors. Many of these safeguarding measures are also mandated by data security legislation and standards. Without any further ado, let\'s start discussing data security, its importance, benefits and steps to make your data more secure. What is data security? Data security refers to the practice of protecting digital data from unauthorized access, corruption, theft, or loss. It encompasses a wide range of techniques, tools, and measures that ensure data is safe from various threats. Data security is crucial for individuals, businesses, and governments, as it ensures the confidentiality, integrity, and availability of data. Benefits of data security Following are the key benefits of data security. Protect your data - Ensuring your information is safe from both inside and outside threats offers peace of mind. This means you can focus more on advancing your business plans and less on potential data breaches. Boost your credibility - Companies aiming for lasting collaborations often scrutinize the reputation of their prospective partners. Demonstrating solid data protection practices can also build trust with your clientele. Meet data security standards - Adopting stringent security protocols ensures you adhere to data protection standards, helping you steer clear of hefty non-compliance penalties. Minimize legal costs - Proactively securing data is far more cost-effective than addressing the aftermath of a breach. Investing in data security now can save significant expenses related to potential incidents later. Ensure operational consistency - Strong data security measures pave the way for smooth business operations, decreasing the chances of interruptions that could impact profitability. Top 29 data security best practices for your organization Data discovery: Begin by identifying the types and sensitivity of the data your organization holds. This helps determine which data is critical and which must adhere to specific security regulations. By doing this, you\'ll have a clear understanding of how to prioritize your data protection. Limit sensitive data access: All employees don\'t require access to all information. Broad access increases the risk of internal breaches and data theft. Embrace the principle of least privilege (PoLP): Minimize risks by ensuring new accounts start with minimal data access, which can be expanded based on roles, needs, and seniority. This way, sensitive data is less exposed, even if a cyber attacker breaches an account. Data encryption: With a surge in cyber threats, it\'s essential to shield personal data. Encrypting data transforms readable information into coded text, challenging unauthorized users. Equip with anti-malware: To guard against data breaches from malware, equip your devices with reliable anti-malware software. Regular vulnerability checks: Since data resides on computers, it\'s continuously exposed to potential threats. Keep data safe by routinely assessing and updating your software, mitigating risks of breaches. E | Malware Tool Vulnerability Legislation Cloud | â â â | ||
| 2023-12-06 08:01:35 | Conscience de sÃĐcuritÃĐ et renseignement sur la sÃĐcuritÃĐ: le jumelage parfait Proofpoint Security Awareness and Threat Intelligence: The Perfect Pairing (lien direct) |
Just like peanut butter and chocolate, when you add threat intelligence to a security awareness program, it\'s the perfect pairing. Together, they can help you efficiently train one of your most important yet most attacked lines of defense-your people. A robust security awareness program that is tailored, defined and driven by real-world threat insights and context is one of the strongest defenses you can implement.  Every week, the Proofpoint Security Awareness team gets regular updates about new and emerging threats and social engineering trends from the Proofpoint Threat Intelligence Services team. This helps drive the development of our security awareness platform. Likewise, our customers can generate daily, weekly, monthly and ad-hoc threat intelligence reports to boost the efficacy of their security awareness programs. In this blog, we will discuss some ways that security awareness teams (SATs) can use threat intelligence from Proofpoint to supercharge their awareness programs.  Tailor your program to defend against the latest threats Not all people within a company see the same threats. And the response to threats differs greatly across teams-even within the same business. That\'s why security awareness programs shouldn\'t a take one-size-fits-all approach.  Here\'s where Proofpoint Threat Intelligence Services can help. Our team regularly briefs customers about which threat actors are targeting their business and industry, who within their company is clicking, which users and departments are attacked most, and what threats they\'re being targeted with.  Proofpoint gives SAT teams the data they need so they can tailor the modules, training and phishing simulations to match those that their users face. Threats in the wild are converted to valuable, tailored awareness materials.  Use cases  Our threat intelligence services team analyzes exactly what threat actors are targeting when they go after a customer-both in terms of volume, but also at a granular department level. We regularly observe that it\'s more common for specific actors to target users within a specific department.  Are threat actors targeting a specific department?  This is a good example of how SAT teams can use threat intelligence to identify departments that are at risk and help keep them safe. In this case study, Proofpoint Threat Intelligence Services revealed that TA578-an initial access broker-was frequently targeting marketing and corporate communications departments with a standard copyright violation message lure. We highlighted this trend for a particular customer as we reviewed their TAP data. This Proofpoint threat actor victimology report shows that TA578 is targeting a marketing address. Proofpoint Threat Intelligence Services identified what was happening and also provided additional context about the threat actor, including: Tactics, techniques and procedures (TTPs)  Malware payloads Attack chains Specific examples of message lures and landing pages Plus, Proofpoint offered recommendations for remediation and proactive, layered protection.  Proofpoint Threat Intelligence Services report on TA578. The SAT team used this information in its Proofpoint Security Awareness program to train the marketing department about specific message lures. The team also created a phishing simulation that used a similar-style lure and content to educate those users about this unique threat. Are threat actors targeting specific people?  Another use case for Proofpoint Threat Intelligence Services is that it can help SAT teams understand who at their company is clicking-and what types of message themes they are clicking on.  Proofpoint Threat Intelligence Services report for a large healthcare customer.  Proofpoint Threat Intelligence Services report shows which users are repeat clickers. This data is compiled from real threats that users have clicked on. SAT teams can use it to prioritize these users for additional awareness training. They can also pi | Tool Threat Studies Prediction | â â â | ||
| 2023-12-06 00:00:00 | Le rapport du Threat Lab de WatchGuard révèle une augmentation du nombre d\'acteurs malveillants exploitant les logiciels d\'accès à distance (lien direct) | PARIS – 6 décembre 2023 – WatchGuard® Technologies, leader mondial de la cybersécurité unifiée, publie les conclusions de son dernier rapport sur la sécurité Internet, détaillant les principales tendances en matière de malwares et de menaces pour la sécurité des réseaux et des endpoints, analysées par les chercheurs du Threat Lab de WatchGuard. Les principales conclusions tirées des données révèlent une augmentation des cas d'utilisation abusive des logiciels d'accès à distance, la montée en puissance des cyberattaquants qui utilisent des voleurs de mots de passe et de données pour s'emparer d'informations d'identification précieuses, et le recours par les acteurs malveillants non plus à des scripts, mais à des techniques de type " living off the land " pour lancer une attaque sur les endpoints. " Les acteurs malveillants emploient sans cesse de nouveaux outils et méthodes pour mener leurs campagnes d'attaque. Il est donc essentiel que les entreprises se tiennent au courant des dernières tactiques afin de renforcer leur stratégie de sécurité ", souligne Corey Nachreiner, Chief Security Officer chez WatchGuard. " Les plateformes de sécurité modernes, qui intègrent des pare-feux et des logiciels de protection des endpoints, peuvent renforcer la protection des réseaux et des appareils. En revanche, lorsque les attaques font appel à des tactiques d'ingénierie sociale, l'utilisateur final représente la dernière ligne de défense pour empêcher les acteurs malveillants de s'infiltrer dans les entreprises. Il est important que celles-ci dispensent une formation sur l'ingénierie sociale et adoptent une approche de sécurité unifiée mettant en place des couches de défense pouvant être administrées efficacement par des fournisseurs de services managés. " Parmi les principales conclusions, le dernier rapport sur la sécurité Internet basé sur des données du troisième trimestre 2023 révèle les éléments suivants : Les acteurs malveillants utilisent de plus en plus d'outils et de logiciels de gestion à distance pour contourner la détection des malwares, ce que le FBI et la CISA ont tous deux reconnu. En étudiant les principaux domaines du phishing, le Threat Lab a par exemple observé une escroquerie à l'assistance technique qui conduisait la victime à télécharger une version préconfigurée et non autorisée de TeamViewer, ce qui permettait au pirate d'accéder à distance à l'intégralité de son ordinateur. Une variante du ransomware Medusa fait son apparition au troisième trimestre, entraînant une augmentation de 89 % du nombre d'attaques de ransomwares sur les endpoints. De prime abord, les détections de ransomwares sur les endpoints semblent avoir diminué au cours du troisième trimestre. Pourtant, la variante du ransomware Medusa, qui figure pour la première fois dans le Top 10 des menaces liées aux malwares, a été détectée à l'aide d'une signature générique provenant du moteur de signatures automatisé du Threat Lab. Si l'on tient compte des détections de Medusa, les attaques par ransomware ont augmenté de 89 % d'un trimestre par rapport à l'autre. Les acteurs malveillants cessent d'utiliser des attaques basées sur des scripts et recourent de plus en plus à d'autres techniques de type " living off the land ". Le vecteur d'attaque que constituent les scripts malveillants a connu une baisse de 11 % au troisième trimestre, après avoir chut&eacut | Ransomware Malware Tool Threat | â â | ||
| 2023-12-05 23:30:00 | BUG BYTES # 218 & # 8211;Avent of Cyber, RCES et Hacking Poems Bug Bytes #218 – Advent of Cyber, RCEs and hacking poems (lien direct) |
> Bug Bytes est une newsletter hebdomadaire organisÃĐe par les membres de la communautÃĐ Bug Bounty.La deuxiÃĻme sÃĐrie est organisÃĐe par InsiderPhd.Chaque semaine, elle nous tient à jour avec une liste complÃĻte des articles, des outils, des tutoriels et des ressources.Ce numÃĐro couvre les semaines du 19 novembre au 3 dÃĐcembre Intigriti News de mon cahier
>Bug Bytes is a weekly newsletter curated by members of the bug bounty community. The second series is curated by InsiderPhD. Every week, she keeps us up to date with a comprehensive list of write-ups, tools, tutorials and resources. This issue covers the weeks from November 19th to December 3rd Intigriti News From my notebook |
Tool | â â â | ||
| 2023-12-05 16:59:00 | SÃĐcuritÃĐ gÃĐnÃĐrative de l'IA: prÃĐvention de l'exposition aux donnÃĐes de Microsoft Copilot Generative AI Security: Preventing Microsoft Copilot Data Exposure (lien direct) |
Microsoft Copilot a ÃĐtÃĐ appelÃĐ l'un des outils de productivitÃĐ les plus puissants de la planÃĻte.
Copilot est un assistant AI qui vit à l'intÃĐrieur de chacune de vos applications Microsoft 365 - Word, Excel, PowerPoint, Teams, Outlook, etc.Le rÊve de Microsoft est de retirer la corvÃĐe du travail quotidien et de laisser les humains se concentrer sur le fait d'Être des rÃĐsolveurs de problÃĻmes crÃĐatifs.
Ce qui fait de Copilot une bÊte diffÃĐrente de celle du chatte et
Microsoft Copilot has been called one of the most powerful productivity tools on the planet. Copilot is an AI assistant that lives inside each of your Microsoft 365 apps - Word, Excel, PowerPoint, Teams, Outlook, and so on. Microsoft\'s dream is to take the drudgery out of daily work and let humans focus on being creative problem-solvers. What makes Copilot a different beast than ChatGPT and |
Tool | ChatGPT | â â â | |
| 2023-12-05 15:25:00 | Le panneau de maison cherche à sauter les autres sur FISA alors que la Maison Blanche fait un plaidoyer frais pour le renouvellement House panel looks to leapfrog others on FISA as White House makes fresh plea for renewal (lien direct) |
 Le dernier projet de loi de la Chambre pour renouveler un outil de sÃĐcuritÃĐ nationale controversÃĐ proposerait les restrictions les plus serrÃĐes sur le programme de surveillance gouvernementale.Le comitÃĐ judiciaire de la Chambre lundi a dÃĐvoilÃĐ sa propre lÃĐgislation pour rÃĐautoriser L'article 702 de la Foreign Intelligence Surveillance Act, qui expirera dans quelques semaines sans approbation du CongrÃĻs, pour trois autres
Le dernier projet de loi de la Chambre pour renouveler un outil de sÃĐcuritÃĐ nationale controversÃĐ proposerait les restrictions les plus serrÃĐes sur le programme de surveillance gouvernementale.Le comitÃĐ judiciaire de la Chambre lundi a dÃĐvoilÃĐ sa propre lÃĐgislation pour rÃĐautoriser L'article 702 de la Foreign Intelligence Surveillance Act, qui expirera dans quelques semaines sans approbation du CongrÃĻs, pour trois autres
 The latest House bill to renew a controversial national security tool would propose the tightest restrictions yet on the government surveillance program. The House Judiciary Committee on Monday unveiled its own legislation to reauthorize Section 702 of the Foreign Intelligence Surveillance Act, which will expire in a few weeks without congressional approval, for another three
The latest House bill to renew a controversial national security tool would propose the tightest restrictions yet on the government surveillance program. The House Judiciary Committee on Monday unveiled its own legislation to reauthorize Section 702 of the Foreign Intelligence Surveillance Act, which will expire in a few weeks without congressional approval, for another three |
Tool Legislation | â â â | ||
| 2023-12-05 12:01:49 | Comment fonctionne la machine de dÃĐsinformation et comment 400 $ peuvent l'arrÊter How The Disinformation Machine Works, And How $400 Can Stop It (lien direct) |
 Plus prÃĐcisÃĐment, lorsque les guerres ÃĐclatent, la dÃĐsinformation passe à la vitesse supÃĐrieure. & NBSP; à la suite de l'attaque du 7 octobre, Internet a ÃĐtÃĐ submergÃĐ par un dÃĐluge de dÃĐsinformation.Ce phÃĐnomÃĻne ne consiste pas à rÃĐpandre des mensonges;C'est une tentative systÃĐmatique d'amplifier les fausses nouvelles et de dÃĐtourner des sources d'information crÃĐdibles pour la guerre de dÃĐsinformation. & nbsp; Nouvelle tempÊte de dÃĐsinformation: un casAnalyse Depuis le 7 octobre, une augmentation de la dÃĐsinformation, allant de subtilement trompeuse à une fausse fausse, a ÃĐtÃĐ dÃĐchaÃŪnÃĐe.Il montre une utilisation sophistiquÃĐe des tactiques couramment utilisÃĐes dans les opÃĐrations d'influence parrainÃĐes par l'Ãtat et privÃĐe.Ces mÃĐthodes se concentrent particuliÃĻrement sur le mini-jeu ou le refus carrÃĐment de la participation du Hamas dans les ÃĐvÃĐnements surLa bordure de Gaza. BBC VÃĐrifie l'ÃĐchelle de la dÃĐsinformation BBC Verify \'s Disinformation Expert, Shayan Sardarizadeh,dÃĐcrit le pic initial de dÃĐsinformation comme sans prÃĐcÃĐdent.Le conflit entre IsraÃŦl et le Hamas s'est immÃĐdiatement ÃĐtendu dans le domaine de l'information et de la guerre psychologique.Selon Sardarizadeh, le rÃĐcit dÃĐni que ÂŦc'est IsraÃŦl qui a tuÃĐ ses propres civils le 7 octobre, pas le HamasÂŧ, est devenu terriblement rÃĐpandu en ligne.Les campagnes de dÃĐsinformation comprennent la propagation des thÃĐories du complot et l'utilisation abusive du contenu de divers autres conflits, de maniÃĻre inexacte prÃĐsentÃĐe comme ÃĐtant liÃĐe à la bande de Gaza.De telles tactiques du livre de jeu KGB sont ingÃĐnierie sociale à grande ÃĐchelle. & Nbsp; AI et dÃĐsinformation: une liaison dangereuse Un dÃĐveloppement particuliÃĻrement alarmant est l'utilisation des technologies d'IA dans ces campagnes de dÃĐsinformation.De Deepfakes aux faux comptes automatisÃĐs, ces outils reprÃĐsentent une escalade significative dans la sophistication de ces opÃĐrations.La campagne russe, par exemple, a fait de profondeurs les soldats des Tsahal et des postes gÃĐnÃĐrÃĐs par ordinateur pour une armÃĐe de faux comptes ouverts automatiquement. Coopting CredibilitÃĐ de co-option: Le PlayBook of Disinformation Les acteurs malignes ciblent souvent des sources d'information ÃĐtablies pour donner l'authenticitÃĐ Ã leurs rÃĐcits.En dÃĐnaturant la dÃĐclaration des points de vente crÃĐdibles, ils visent à crÃĐer une base pour les thÃĐories du dÃĐni et du complot d'atrocitÃĐ.Une instance notable de ceci est la manipulation des rapports à partir de
Plus prÃĐcisÃĐment, lorsque les guerres ÃĐclatent, la dÃĐsinformation passe à la vitesse supÃĐrieure. & NBSP; à la suite de l'attaque du 7 octobre, Internet a ÃĐtÃĐ submergÃĐ par un dÃĐluge de dÃĐsinformation.Ce phÃĐnomÃĻne ne consiste pas à rÃĐpandre des mensonges;C'est une tentative systÃĐmatique d'amplifier les fausses nouvelles et de dÃĐtourner des sources d'information crÃĐdibles pour la guerre de dÃĐsinformation. & nbsp; Nouvelle tempÊte de dÃĐsinformation: un casAnalyse Depuis le 7 octobre, une augmentation de la dÃĐsinformation, allant de subtilement trompeuse à une fausse fausse, a ÃĐtÃĐ dÃĐchaÃŪnÃĐe.Il montre une utilisation sophistiquÃĐe des tactiques couramment utilisÃĐes dans les opÃĐrations d'influence parrainÃĐes par l'Ãtat et privÃĐe.Ces mÃĐthodes se concentrent particuliÃĻrement sur le mini-jeu ou le refus carrÃĐment de la participation du Hamas dans les ÃĐvÃĐnements surLa bordure de Gaza. BBC VÃĐrifie l'ÃĐchelle de la dÃĐsinformation BBC Verify \'s Disinformation Expert, Shayan Sardarizadeh,dÃĐcrit le pic initial de dÃĐsinformation comme sans prÃĐcÃĐdent.Le conflit entre IsraÃŦl et le Hamas s'est immÃĐdiatement ÃĐtendu dans le domaine de l'information et de la guerre psychologique.Selon Sardarizadeh, le rÃĐcit dÃĐni que ÂŦc'est IsraÃŦl qui a tuÃĐ ses propres civils le 7 octobre, pas le HamasÂŧ, est devenu terriblement rÃĐpandu en ligne.Les campagnes de dÃĐsinformation comprennent la propagation des thÃĐories du complot et l'utilisation abusive du contenu de divers autres conflits, de maniÃĻre inexacte prÃĐsentÃĐe comme ÃĐtant liÃĐe à la bande de Gaza.De telles tactiques du livre de jeu KGB sont ingÃĐnierie sociale à grande ÃĐchelle. & Nbsp; AI et dÃĐsinformation: une liaison dangereuse Un dÃĐveloppement particuliÃĻrement alarmant est l'utilisation des technologies d'IA dans ces campagnes de dÃĐsinformation.De Deepfakes aux faux comptes automatisÃĐs, ces outils reprÃĐsentent une escalade significative dans la sophistication de ces opÃĐrations.La campagne russe, par exemple, a fait de profondeurs les soldats des Tsahal et des postes gÃĐnÃĐrÃĐs par ordinateur pour une armÃĐe de faux comptes ouverts automatiquement. Coopting CredibilitÃĐ de co-option: Le PlayBook of Disinformation Les acteurs malignes ciblent souvent des sources d'information ÃĐtablies pour donner l'authenticitÃĐ Ã leurs rÃĐcits.En dÃĐnaturant la dÃĐclaration des points de vente crÃĐdibles, ils visent à crÃĐer une base pour les thÃĐories du dÃĐni et du complot d'atrocitÃĐ.Une instance notable de ceci est la manipulation des rapports à partir de |
Tool | â â â | ||
| 2023-12-05 11:00:00 | Aperçu des systÃĻmes de dÃĐtection de fraude modernes Insights into modern fraud detection systems (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Information security requirements and standards are in a constant state of evolution. Recent issues, such as COVID-19 and the growing global reliance on mobile devices and remote work solutions, have played important roles in this ongoing transformation. At the same time, the increasing sophistication of cyber attackers has added new layers of complexity to the cybersecurity landscape. In this article, I will explore the importance of implementing fraud detection systems as a crucial measure to mitigate the impact of both traditional and emerging fraudulent schemes. Challenges faced by financial institutions The landscape of user behavior has undergone significant shifts, primarily driven by external factors such as the COVID-19 pandemic. This factor led to an increase in online transactions, coupled with reduced income streams for many individuals, resulting in decreased spending in specific user categories. Additionally, local conflicts, like the war in Ukraine and Israel, influence spending patterns in particular regions. The implementation of restrictive measures and the resulting increase in stress levels have provided cyber crooks with more opportunities to exploit social engineering techniques through acts of intimidation. One prevalent scam involves fraudsters posing as bank security officials to deceive unsuspecting individuals. Another concerning trend is the rise of legitimate channels that drive people to scam schemes via mainstream advertising platforms like Google and Facebook. Furthermore, the economic hardships some people face have led them to seek alternative income sources, driving them to engage in various forms of online criminal activities. Some individuals become involved in schemes where they act as money mules or work in illegal call centers. It is challenging for financial institutions to guarantee absolute safety. Malicious individuals can present counterfeit identification to authorize transactions that were initially denied by the anti-fraud system. While financial institutions strive to know as much as possible about their clients and run transactions carefully, they are constrained by data retention limitations (typically several months) and the need to respond within seconds, as stipulated by Service Level Agreements. So, again, achieving complete certainty about every transaction remains a huge problem. Detecting suspicious activities becomes even more challenging when malicious employees request details about a specific client or transaction, as this falls within their routine work tasks. Some fraud detection systems use computer webcams or video surveillance cameras to monitor employee behavior. Modern surveillance systems have become more intelligent, leveraging artificial intelligence and historical data to perform comprehensive risk assessments and take action when unusual employee behavior is detected. However, these cameras may not always be effective in identifying deceitful behavior when employees remain almost motionless. Understanding fraud detection systems Fraud detection systems are designed to detect and prevent various forms of fraudulent activities, ranging from account hijacking and | Tool Threat Mobile Prediction Technical | â â â | ||
| 2023-12-05 10:43:56 | La CISA prÃĐvoit une contribution sur l'outil d'ÃĐvaluation de la cybersÃĐcuritÃĐ fondamentale pour les entitÃĐs SLTT CISA calls for input on foundational cybersecurity assessment tool for SLTT entities (lien direct) |
> L'Agence amÃĐricaine de sÃĐcuritÃĐ de la cybersÃĐcuritÃĐ et de l'infrastructure (CISA) a publiÃĐ une soumission pour une nouvelle demande de collecte (ICR) ...
>The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has published a submission for a new collection request (ICR)... |
Tool | â â â | ||
| 2023-12-05 02:56:27 | Cinq choses que vous devez savoir sur les erreurs de sÃĐcuritÃĐ Five Things You Need to Know About Security Misconfigurations (lien direct) |
Il est facile de supposer que les outils de sÃĐcuritÃĐ sont efficacement configurÃĐs dÃĻs la sortie de la boÃŪte, pour ainsi dire.Ce scÃĐnario est trop courant et peut entraÃŪner de graves consÃĐquences, telles que les violations de donnÃĐes si une organisation implÃĐmente des solutions logicielles avec de mauvaises configurations de sÃĐcuritÃĐ.Une erreur de configuration est ÂŦune configuration incorrecte ou sous-optimale d'un systÃĻme d'information ou d'un composant systÃĻme qui peut conduire à des vulnÃĐrabilitÃĐsÂŧ, telle que dÃĐfinie par l'Institut national des normes et de la technologie (NIST).Afin d'ÃĐviter les erreurs de configuration et les incidents de sÃĐcuritÃĐ qui peuvent en dÃĐcouler, c'est ...
It is easy to assume that security tools are effectively configured right out of the box, so to speak. This scenario is all too common and can lead to severe consequences, such as data breaches if an organization implements software solutions with improper security configurations. A misconfiguration is âan incorrect or suboptimal configuration of an information system or system component that may lead to vulnerabilities,â as defined by the National Institute of Standards and Technology (NIST). In order to prevent misconfigurations and the security incidents that can arise from them, it is... |
Tool Vulnerability | â â â | ||
| 2023-12-04 11:49:08 | Applications de santÃĐ mentale: peuvent-ils faire confiance? Mental Health Apps: Can They Be Trusted? (lien direct) |
In the past few years, mental health apps have witnessed massive growth thanks to their potential to fix a multitude of mental health-related problems.
That said, they are not the best when it comes to managing and securing highly sensitive personal data.
Mental health apps with millions of downloads have been found guilty of selling, misusing, and leaking sensitive data of their users.
In this article, we have shared everything you need to know about the countless privacy concerns associated with mental health apps.
Let’s see if you can trust any mainstream mental health app or if they are all the same.
What Are Mental Health Apps? The name says it all, mental health apps offer tools, activities, and support to help cure serious problems like anxiety, depression, ADHD, Bipolar Disorder, substance abuse, and many more. While mental health apps can’t replace an actual doctor, they have been found to be quite effective in multiple instances.  On the surface, mental health apps seem to be quite useful for the well-being of users, but you will be surprised to know that the research from Private Internet Access revealed that many mainstream apps fail to protect the privacy and security of their users.
Let’s get into details and discuss all of the problems associated with mental health apps and see how they have become the biggest data-harvesting machines.
On the surface, mental health apps seem to be quite useful for the well-being of users, but you will be surprised to know that the research from Private Internet Access revealed that many mainstream apps fail to protect the privacy and security of their users.
Let’s get into details and discuss all of the problems associated with mental health apps and see how they have become the biggest data-harvesting machines.
Are Mental Health Apps Spying on You? Unlike other mainstream apps, mental health apps require substantially more information about their users for the app to function properly. |
Data Breach Tool Threat Medical | â â â | ||
| 2023-12-04 11:00:00 | Comment les outils de collaboration d'ÃĐquipe et la cybersÃĐcuritÃĐ peuvent protÃĐger les effectifs hybrides How team collaboration tools and Cybersecurity can safeguard hybrid workforces (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Hybrid operations are becoming an increasingly prevalent part of the business landscape. Certainly, this offers some fantastic opportunities for companies to reduce overhead costs and gain access to international talent. Yet, there are some distinct challenges hybrid workforces face, too. Key among these is the potential for cybersecurity issues to arise. When you have some employees working from the office and others operating remotely, a range of vulnerabilities may arise — not to mention that there may be hurdles to staff interacting effectively. So, let’s take a look at how team collaboration tools and cybersecurity measures can safeguard your hybrid workforce. Identifying and addressing relevant threats There are few businesses today that aren’t vulnerable to some form of cyber threat. However, the risks tend to depend on the specific business model. As a result, it’s important to first gain an understanding of the prevalent risks related to hybrid workplaces. This enables you to more effectively collaborate and develop safeguards. For hybrid businesses, a range of network security threats have the potential to disrupt operations and cause data breaches. These include: Malware. These malicious software or firmware programs usually enter a network when a person unintentionally downloads them after clicking a link or attachment. Depending on the type of malware, this can give hackers remote access to networks or capture data about network activity, alongside infecting other devices on the network. It’s important to ensure hybrid staff have malware detection software on both business and personal devices that they use to connect to company networks. In addition, you must give them training on how to avoid triggering malware downloads. Phishing. Social engineering attacks, like phishing, can be a challenging issue. These tactics are designed to skirt your security software by getting information or network access directly from your human workers. This may involve criminals posing as legitimate businesses or official entities and directing workers to cloned websites where they’ll be requested to enter sensitive information. You can mitigate this type of issue by monitoring network traffic to spot unusual activity, as well as educating staff on the details of these methods. Even if criminals gain passwords by these methods, setting up multi-factor authentication can limit how useful they are to hackers. That said, alongside the common threats, it’s important to get to know and address the issues with your specific hybrid business. Talk to your staff about their day-to-day working practices and the potential points of vulnerability. Discuss remote workers’ home network setups to establish whether there are end-to-end safeguards in place to prevent unauthorized access to networks. You can then collaborate on arranging additional equipment or protocols — such as access to an encrypted virtual private network (VPN) — that protect both the business and workers’ home equipment. Utilizing collaborative tools Effective collaboration is essential for all hybrid businesses. This isn’t just a matter of maintaining productivity. When employees have the right tools in place to wo | Malware Tool Vulnerability Threat Cloud | â â | ||
| 2023-12-04 10:39:37 | Comment l'analyse dynamique vous aide à amÃĐliorer l'automatisation des DevSecops How Dynamic Analysis Helps You Enhance Automation for DevSecOps (lien direct) |
DevSecops, ÃĐgalement connu sous le nom de DevOps sÃĐcurisÃĐ, reprÃĐsente un ÃĐtat d'esprit dans le dÃĐveloppement de logiciels qui maintient tout le monde responsable de la sÃĐcuritÃĐ des applications.En favorisant la collaboration entre les dÃĐveloppeurs et les opÃĐrations informatiques et en dirigeant les efforts collectifs vers une meilleure prise de dÃĐcision de sÃĐcuritÃĐ, les ÃĐquipes de dÃĐveloppement peuvent fournir des logiciels plus sÃŧrs avec une plus grande vitesse et une plus grande efficacitÃĐ.
MalgrÃĐ ses avantages, la mise en Åuvre de DevSecops peut introduire des frictions dans le processus de dÃĐveloppement.Les outils traditionnels pour tester le code et ÃĐvaluer le risque de sÃĐcuritÃĐ des applications n'ont tout simplement pas ÃĐtÃĐ conçu pour la vitesse dont les tests DevOps ont besoin.
Pour naviguer dans ces dÃĐfis, les ÃĐquipes de dÃĐveloppement doivent commencer avec des outils de test automatisÃĐs, car le fait de s'appuyer sur les processus manuels ne peut pas suivre le rythme des dÃĐlais de dÃĐveloppement accÃĐlÃĐrÃĐs.L'automatisation est considÃĐrÃĐe comme clÃĐ pour l'intÃĐgration continue de l'analyse de la sÃĐcuritÃĐ et l'attÃĐnuation des menaces des flux de travail dynamiques.En tant qu'extension des principes DevOps, DevSecops Automation aide à intÃĐgrer les tests de sÃĐcuritÃĐâĶ
DevSecOps, also known as secure DevOps, represents a mindset in software development that holds everyone accountable for application security. By fostering collaboration between developers and IT operations and directing collective efforts towards better security decision-making, development teams can deliver safer software with greater speed and efficiency. Despite its merits, implementing DevSecOps can introduce friction into the development process. Traditional tools for testing code and assessing application security risk simply weren\'t built for the speed that DevOps testing requires. To navigate these challenges, development teams need to start with automated testing tools, as relying on manual processes can\'t possibly keep pace with accelerated development timelines. Automation is considered key to continuous integration of security analysis and threat mitigation of dynamic workflows. As an extension of DevOps principles, DevSecOps automation helps integrate security testingâĶ |
Tool Threat | â â â | ||
| 2023-12-04 07:10:47 | ArrÊt de cybersÃĐcuritÃĐ du mois: Utilisation de l'IA comportementale pour ÃĐcraser le dÃĐtournement de la paie Cybersecurity Stop of the Month: Using Behavioral AI to Squash Payroll Diversion (lien direct) |
This blog post is part of a monthly series exploring the ever-evolving tactics of today\'s cybercriminals. Cybersecurity Stop of the Month focuses on the critical first steps in the attack chain – stopping the initial compromise-in the context of email threats. The series is designed to help you understand how to fortify your defenses to protect people and defend data against emerging threats in today\'s dynamic threat landscape. The first three steps of the attack chain: stop the initial compromise. In our previous posts, we have covered these attack types:âŊ Supplier compromiseâŊ EvilProxyâŊ SocGholishâŊ E-signature phishing QR code phishing Telephone-oriented attack delivery (TOAD)âŊâŊ In this installment we examine a payroll diversion threat that Proofpoint detected during a recent threat assessment. We also cover the typical attack sequence of payroll fraud and explain how Proofpoint uses multiple signals to detect and prevent these threats for our customers. Background Business email compromise (BEC) continues to grow in popularity and sophistication. The 2022 FBI Internet Crime Report notes that BEC attacks cost U.S. businesses $2.7 billion last year. The global figure is no doubt much higher. Ransomware victims, in contrast, lost just $34 million. Payroll diversion is a form of BEC. Typically, employees who have direct access to fulfilling payroll-related requests are prime targets. In these attacks, a bad actor pretends to be an employee who needs to update their direct deposit information. The new information is for an account that the bad actor owns. Once the fraudulent request is complete, the lost funds cannot be retrieved by the business. Payroll diversion fraud isn\'t a new form of BEC, but the frequency of this type of attack is on the rise. Proofpoint continues to see this type of threat getting through the defenses of other email security tools. Across all of our October 2023 threat assessments, we found that more than 400 of these threats got past 12 other email security tools.  There are a few reasons why it\'s difficult for a lot of email security tools to detect or remediate these threats. The primary reason is because they don\'t usually carry malicious payloads like attachments or URLs. They also tend to be sent from personal email services-like Google, Yahoo and iCloud-and target specific users.  Notably, API-based email security tools that scan for threats post-delivery are the most susceptible to not being able to detect or remediate this type of threat. This partly comes down to how they work. In order for them to be effective, they need security and IT teams to manually populate them with a dictionary of possible display names of all employees, which is a very time-consuming effort that is hard to scale.  To avoid this, many organizations simply choose to enable display name prevention for their senior executives only. But bad actors behind payroll diversion don\'t just impersonate executives, they target anyone in the organization who can access corporate funds.  In our example below, an attacker took advantage of this exact weakness. The scenario Proofpoint detected a payroll diversion attempt where the attacker posed as a non-executive employee. The email was sent to the director of human resources (HR) at a 300-person company in the energy and utilities industry. The company\'s incumbent email security tool delivered the message, and its API-based post-delivery remediation tool failed to detect and retract it. The threat: How did the attack happen? Here is a closer look at how this payroll diversion scam unfolded: 1. The deceptive message: The attacker sent a request to update their direct deposit information from an account that appeared to be a legitimate employee\'s personal email account. The original malicious message delivered to the recipient\'s inbox. 2. Payroll diversion attack sequence: If the recipient had engaged, the attacker\'s goal would have been to convince them to trans | Ransomware Tool Threat | Yahoo | â â |
To see everything:
Our RSS (filtrered)
