What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2024-02-27 11:36:59 | Secteur de la santé et menaces cyber : au-delà des mythes (lien direct) | Secteur de la santé et menaces cyber : au-delà des mythes Par Thomas Segura, spécialiste cybersécurité chez GitGuardian - Points de Vue | Threat | ★★ | ||
| 2024-02-27 11:00:00 | L'évolution du point de terminaison - passant des critères de terminaison traditionnels aux charges de travail cloud ou conteneurisées et les solutions de sécurité pour les protéger The endpoint evolution - Evolving from traditional endpoints to cloud or containerized workloads and the security solutions to protect them (lien direct) |
As organizations grow and more endpoints are added across the enterprise, they create an increasingly broad attack surface sophisticated attackers are looking to compromise. According to the 2019 Endpoint Security Trends Report 70% of breaches originate at the endpoint¹. That is likely because endpoints typically represent the Intersection between humans and machines creating vulnerable points of entry for cybercriminals. This is why it is increasingly important to secure your endpoints.
Growth in endpoints
An endpoint is defined as any computing device that communicates back and forth with a network to which it is connected. Some end user devices serve as an interface with human users while others are servers that communicate with other endpoints on the network. Traditional endpoints began as physical devices including servers, workstations, desktops, and laptops, all connected to a corporate network. When smartphones and tablets became handheld computing devices with access to corporate email, document sharing and collaboration tools the number of endpoints at least doubled.
Then came the rise of the Internet of Things (IoT) including devices like printers, webcams, smartwatches, and thermostats, all of which are connected to the network. Industries like healthcare and manufacturing are using millions of IoT sensors to collect and exchange data. This continued growth in IoT only increases the number of endpoints that need to be protected.
Another contribution to the growth in endpoints is the migration to the cloud. It is estimated that 67% of enterprise infrastructure is cloud-based². This cloud transformation is the evolution from physical devices to virtualization and containerization.
Endpoint virtualization
The cloud is a multi-tenant environment where multiple users run services on the same server hardware. Virtualization and containerization are both virtualization technologies that separate the host operating system from the programs that run in them.
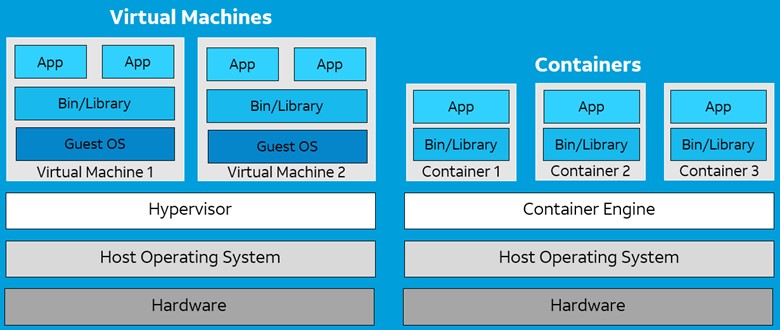 Virtualization is achieved using a hypervisor, which splits CPU, RAM, and storage resources between multiple virtual machines (VMs). Each VM behaves like a separate computer that gets a guest operating system and each VM is independent of each other. This allows organizations to run multiple OS instances on a single server.
Containerization, on the other hand, runs a single host OS instance and uses a container engine to help package applications into container images that can be easily deployed and re-used. By splitting each individual application function or microservice into containers they can operate independently to improve enterprise resilience and scalability. Kubernetes then manages the orchestration of multiple containers. VMs and containers present very different security challenges so let’s look at the evolution of endpoint security and the solutions that meet the needs of complex customer environments.
Securing endpoints
For decades, organizations have heavily relied on antivirus (AV) software to secure endpoints. However, traditional antivirus worked by matching known malicious signatures in a database and can no longer protect against today’s sophisticated threats. Modern endpoint security solutions are less signature-based and much more behavior-based. Endpoint protection platforms (EPP) offer cloud native architectures that provide a layered defense against fileless attacks using machine learning and behavioral AI to protect against malicious activity. Endpoint detection and response (EDR) solutions went beyond protection by recording and storing endpoint-system level behaviors to detect malicious threats.
EDR solutions use data analytics combined with threat intelligence feeds to provide incident responders with the forensic data for completing investigations and threat hunting. In addi
Virtualization is achieved using a hypervisor, which splits CPU, RAM, and storage resources between multiple virtual machines (VMs). Each VM behaves like a separate computer that gets a guest operating system and each VM is independent of each other. This allows organizations to run multiple OS instances on a single server.
Containerization, on the other hand, runs a single host OS instance and uses a container engine to help package applications into container images that can be easily deployed and re-used. By splitting each individual application function or microservice into containers they can operate independently to improve enterprise resilience and scalability. Kubernetes then manages the orchestration of multiple containers. VMs and containers present very different security challenges so let’s look at the evolution of endpoint security and the solutions that meet the needs of complex customer environments.
Securing endpoints
For decades, organizations have heavily relied on antivirus (AV) software to secure endpoints. However, traditional antivirus worked by matching known malicious signatures in a database and can no longer protect against today’s sophisticated threats. Modern endpoint security solutions are less signature-based and much more behavior-based. Endpoint protection platforms (EPP) offer cloud native architectures that provide a layered defense against fileless attacks using machine learning and behavioral AI to protect against malicious activity. Endpoint detection and response (EDR) solutions went beyond protection by recording and storing endpoint-system level behaviors to detect malicious threats.
EDR solutions use data analytics combined with threat intelligence feeds to provide incident responders with the forensic data for completing investigations and threat hunting. In addi |
Malware Tool Vulnerability Threat Mobile Cloud | ★★ | ||
| 2024-02-27 05:00:31 | Risque et ils le savent: 96% des utilisateurs de prise de risque sont conscients des dangers mais le font quand même, 2024 State of the Phish révèle Risky and They Know It: 96% of Risk-Taking Users Aware of the Dangers but Do It Anyway, 2024 State of the Phish Reveals (lien direct) |
We often-and justifiably-associate cyberattacks with technical exploits and ingenious hacks. But the truth is that many breaches occur due to the vulnerabilities of human behavior. That\'s why Proofpoint has gathered new data and expanded the scope of our 2024 State of the Phish report. Traditionally, our annual report covers the threat landscape and the impact of security education. But this time, we\'ve added data on risky user behavior and their attitudes about security. We believe that combining this information will help you to: Advance your cybersecurity strategy Implement a behavior change program Motivate your users to prioritize security This year\'s report compiles data derived from Proofpoint products and research, as well as from additional sources that include: A commissioned survey of 7,500 working adults and 1,050 IT professionals across 15 countries 183 million simulated phishing attacks sent by Proofpoint customers More than 24 million suspicious emails reported by our customers\' end users To get full access to our global findings, you can download your copy of the 2024 State of the Phish report now. Also, be sure to register now for our 2024 State of the Phish webinar on March 5, 2024. Our experts will provide more insights into the key findings and answer your questions in a live session. Meanwhile, let\'s take a sneak peek at some of the data in our new reports. Global findings Here\'s a closer look at a few of the key findings in our tenth annual State of the Phish report. Survey of working adults In our survey of working adults, about 71%, said they engaged in actions that they knew were risky. Worse, 96% were aware of the potential dangers. About 58% of these users acted in ways that exposed them to common social engineering tactics. The motivations behind these risky actions varied. Many users cited convenience, the desire to save time, and a sense of urgency as their main reasons. This suggests that while users are aware of the risks, they choose convenience. The survey also revealed that nearly all participants (94%) said they\'d pay more attention to security if controls were simplified and more user-friendly. This sentiment reveals a clear demand for security tools that are not only effective but that don\'t get in users\' way. Survey of IT and information security professionals The good news is that last year phishing attacks were down. In 2023, 71% of organizations experienced at least one successful phishing attack compared to 84% in 2022. The bad news is that the consequences of successful attacks were more severe. There was a 144% increase in reports of financial penalties. And there was a 50% increase in reports of damage to their reputation. Another major challenge was ransomware. The survey revealed that 69% of organizations were infected by ransomware (vs. 64% in 2022). However, the rate of ransom payments declined to 54% (vs. 64% in 2022). To address these issues, 46% of surveyed security pros are increasing user training to help change risky behaviors. This is their top strategy for improving cybersecurity. Threat landscape and security awareness data Business email compromise (BEC) is on the rise. And it is now spreading among non-English-speaking countries. On average, Proofpoint detected and blocked 66 million BEC attacks per month. Other threats are also increasing. Proofpoint observed over 1 million multifactor authentication (MFA) bypass attacks using EvilProxy per month. What\'s concerning is that 89% of surveyed security pros think MFA is a “silver bullet” that can protect them against account takeover. When it comes to telephone-oriented attack delivery (TOAD), Proofpoint saw 10 million incidents per month, on average. The peak was in August 2023, which saw 13 million incidents. When looking at industry failure rates for simulated phishing campaigns, the finance industry saw the most improvement. Last year the failure rate was only 9% (vs. 16% in 2022). “Resil | Ransomware Tool Vulnerability Threat Studies Technical | ★★★★ | ||
| 2024-02-27 04:52:59 | Top 5 techniques d'escroquerie: ce que vous devez savoir Top 5 Scam Techniques: What You Need to Know (lien direct) |
Les escrocs sont de plus en plus ingénieux lorsqu'ils proposent des techniques d'arnaque.Mais ils comptent souvent sur des techniques de persuasion de longue date pour que l'arnaque fonctionne.Ainsi, vous pouvez entendre parler d'une nouvelle arnaque qui utilise un nouveau récit, mais il y a de fortes chances que l'arnaque s'appuie sur des techniques d'escroquerie éprouvées une fois que le récit est éliminé.Ces techniques d'arnaque exploitent souvent nos caractéristiques et nos heuristiques, ou des choses qui nous rendent humaines et faillibles.Dans cet article de blog, je couvrirai certaines des techniques d'arnaque les plus courantes et expliquerai comment elles fonctionnent.Évoquant l'influence viscérale des influences viscérales telles que ...
Scammers are increasingly resourceful when coming up with scam techniques. But they often rely on long-standing persuasion techniques for the scam to work. So, you may hear about a new scam that uses a novel narrative, but there is a good chance that the scam relies on proven scam techniques once the narrative is stripped away. These scam techniques often exploit our characteristics and heuristics, or things that make us human and fallible. In this blog post, I will cover some of the most common scam techniques and explain how they work. Evoking visceral influence Visceral influences such as... |
Threat | ★★ | ||
| 2024-02-27 00:12:58 | La Maison Blanche exhorte le passage aux langues sûres de la mémoire White House Urges Switching to Memory Safe Languages (lien direct) |
Le Bureau du Rapport technique du National Cyber Director se concentre sur la réduction des vulnérabilités de sécurité de la mémoire dans les applications et de rendre plus difficile pour les acteurs malveillants de les exploiter.
The Office of the National Cyber Director technical report focuses on reducing memory-safety vulnerabilities in applications and making it harder for malicious actors to exploit them. |
Vulnerability Threat Technical | ★★ | ||
| 2024-02-27 00:00:00 | Les groupes d'acteurs de menace, dont Black Basta, exploitent les vulnérabilités récentes de Screenconnect Threat Actor Groups, Including Black Basta, are Exploiting Recent ScreenConnect Vulnerabilities (lien direct) |
Cette entrée de blog donne une analyse détaillée de ces vulnérabilités récentes de ScreenConnect.Nous discutons également de notre découverte de groupes d'acteurs de menace, notamment Black Basta et Bl00dy Ransomware Gangs, qui exploitent activement CVE-2024-1708 et CVE-2024-1709 sur la base de notre télémétrie.
This blog entry gives a detailed analysis of these recent ScreenConnect vulnerabilities. We also discuss our discovery of threat actor groups, including Black Basta and Bl00dy Ransomware gangs, that are actively exploiting CVE-2024-1708 and CVE-2024-1709 based on our telemetry. |
Ransomware Vulnerability Threat | ★★★ | ||
| 2024-02-26 20:46:17 | Analysis of Nood RAT Used in Attacks Against Linux (Gh0st RAT\'s Variant) (lien direct) | #### Description
Ahnlab Security Intelligence Center (ASEC) a découvert que Nood Rat, une variante de GH0ST RAT qui fonctionne dans Linux, est utilisé dans des attaques de logiciels malveillants.Nood Rat est un malware de porte dérobée qui peut recevoir des commandes du serveur C&C pour effectuer des activités malveillantes telles que le téléchargement de fichiers malveillants, le vol de fichiers internes de systèmes \\ 'et l'exécution de commandes.Bien que simple en forme, il est équipé d'une fonction de chiffrement pour éviter la détection des paquets de réseau.
Nood Rat est développé à l'aide d'un constructeur qui permet à l'acteur de menace de créer du binaire x86 ou x64 basé sur l'architecture et de choisir et d'utiliser le binaire qui correspond au système cible.Le malware a une fonctionnalité qui modifie son nom afin de se déguiser en programme légitime.L'acteur de menace est en mesure de décider du faux nom de processus du malware \\ pendant la phase de développement.
#### URL de référence (s)
1. https://asec.ahnlab.com/en/62144/
#### Date de publication
25 février 2024
#### Auteurs)
Sanseo
#### Description AhnLab Security Intelligence Center (ASEC) has discovered that Nood RAT, a variant of Gh0st RAT that works in Linux, is being used in malware attacks. Nood RAT is a backdoor malware that can receive commands from the C&C server to perform malicious activities such as downloading malicious files, stealing systems\' internal files, and executing commands. Although simple in form, it is equipped with an encryption feature to avoid network packet detection. Nood RAT is developed using a builder that allows the threat actor to create x86 or x64 binary based on the architecture and choose and use the binary that fits the target system. The malware has a feature that changes its name in order to disguise itself as a legitimate program. The threat actor is able to decide the malware\'s fake process name during the development stage. #### Reference URL(s) 1. https://asec.ahnlab.com/en/62144/ #### Publication Date February 25, 2024 #### Author(s) Sanseo |
Malware Threat | ★★ | ||
| 2024-02-26 20:24:00 | Nouvelles attaques de chargeur IDAT en utilisant la stéganographie pour déployer Remcos Rat New IDAT Loader Attacks Using Steganography to Deploy Remcos RAT (lien direct) |
Les entités ukrainiennes basées en Finlande ont été ciblées dans le cadre d'une campagne malveillante distribuant un cheval de Troie à distance commercial connu sous le nom de Remcos Rat à l'aide d'un chargeur de logiciels malveillants appelée IDAT Loader.
L'attaque a été attribuée à un acteur de menace suivi par l'équipe d'intervention d'urgence informatique d'Ukraine (CERT-UA) en vertu du surnom UAC-0184.
"L'attaque, dans le cadre du chargeur IDAT, a utilisé
Ukrainian entities based in Finland have been targeted as part of a malicious campaign distributing a commercial remote access trojan known as Remcos RAT using a malware loader called IDAT Loader. The attack has been attributed to a threat actor tracked by the Computer Emergency Response Team of Ukraine (CERT-UA) under the moniker UAC-0184. "The attack, as part of the IDAT Loader, used |
Malware Threat Commercial | ★★ | ||
| 2024-02-26 15:45:57 | 26 février & # 8211;Rapport de renseignement sur les menaces 26th February – Threat Intelligence Report (lien direct) |
> Pour les dernières découvertes en cyberLes meilleures attaques et violation des écoles publiques du comté de Prince George américain (PGCP) ont connu une attaque de ransomware qui a compromis les données personnelles de près de 100 000 personnes.L'attaque exposée aux individus \\ 'Noms complets, informations sur le compte financier et social [& # 8230;]
>For the latest discoveries in cyber research for the week of 26th February, please download our Threat_Intelligence Bulletin. TOP ATTACKS AND BREACHES The American Prince George’s County Public Schools (PGCPS) has experienced a ransomware attack that compromised the personal data of nearly 100K individuals. The attack exposed individuals\' full names, financial account information, and Social […] |
Ransomware Threat | ★★ | ||
| 2024-02-26 15:17:44 | Étapes pratiques pour prévenir les vulnérabilités d'injection SQL Practical Steps to Prevent SQL Injection Vulnerabilities (lien direct) |
Dans le paysage numérique d'aujourd'hui, les applications Web et les API sont constamment menacées par des acteurs malveillants qui cherchent à exploiter les vulnérabilités.Une attaque commune et dangereuse est une injection SQL.
Dans ce blog, nous explorerons les vulnérabilités et les attaques de l'injection de SQL, comprendrons leur niveau de gravité et fournirons des étapes pratiques pour les empêcher.En mettant en œuvre ces meilleures pratiques, vous pouvez améliorer la sécurité de vos applications Web et API.
Comprendre les vulnérabilités et les attaques de l'injection SQL
Les attaques d'injection SQL se produisent lorsque les pirates manipulent les requêtes SQL d'une application \\ pour obtenir un accès non autorisé, altérer la base de données ou perturber la fonctionnalité de l'application \\.Ces attaques peuvent entraîner une usurpation d'identité, un accès aux données non autorisé et des attaques enchaînées.
L'injection SQL est une technique où les pirates injectent des requêtes SQL malveillantes dans la base de données backend d'une application Web.Cette vulnérabilité survient lorsque l'application accepte la saisie de l'utilisateur comme une instruction SQL que la base de données…
In today\'s digital landscape, web applications and APIs are constantly under threat from malicious actors looking to exploit vulnerabilities. A common and dangerous attack is a SQL injection. In this blog, we will explore SQL injection vulnerabilities and attacks, understand their severity levels, and provide practical steps to prevent them. By implementing these best practices, you can enhance the security of your web applications and APIs. Understanding SQL Injection Vulnerabilities and Attacks SQL injection attacks occur when hackers manipulate an application\'s SQL queries to gain unauthorized access, tamper with the database, or disrupt the application\'s functionality. These attacks can lead to identity spoofing, unauthorized data access, and chained attacks. SQL injection is a technique where hackers inject malicious SQL queries into a web application\'s backend database. This vulnerability arises when the application accepts user input as a SQL statement that the database… |
Vulnerability Threat Guideline Technical | ★★★ | ||
| 2024-02-26 14:41:25 | Groupe parrainé par l'État blâmé pour le changement de violation des soins de santé State-Sponsored Group Blamed for Change Healthcare Breach (lien direct) |
> UnitedHealth Group blâme un acteur de menace parrainé par l'État pour une cyberattaque perturbatrice sur sa filiale Change Healthcare.
>UnitedHealth Group is blaming a state-sponsored threat actor for a disruptive cyberattack on its subsidiary Change Healthcare. |
Threat | ★★ | ||
| 2024-02-26 13:56:26 | Russie Cyber Spies derrière Solarwinds Breach adoptant de nouvelles tactiques, avertissez cinq agences Eyes Russia cyber spies behind SolarWinds breach adopting new tactics, warn Five Eyes agencies (lien direct) |
 Les cyber-espions russes derrière la violation de Solarwinds adaptent leurs techniques pour pirater des organisations qui ont déplacé leurs réseaux dans des environnements hébergés dans le cloud, les responsables occidentaux avertissent.L'hébergement cloud a posé un défi pour les pirates, car il a effectivement réduit la surface d'attaque en termes de capacité à exploiter les vulnérabilités logicielles que les organisations
Les cyber-espions russes derrière la violation de Solarwinds adaptent leurs techniques pour pirater des organisations qui ont déplacé leurs réseaux dans des environnements hébergés dans le cloud, les responsables occidentaux avertissent.L'hébergement cloud a posé un défi pour les pirates, car il a effectivement réduit la surface d'attaque en termes de capacité à exploiter les vulnérabilités logicielles que les organisations
 The Russian cyber spies behind the SolarWinds breach are adapting their techniques to hack into organizations that have moved their networks into cloud-hosted environments, Western officials are warning. Cloud hosting has posed a challenge to hackers because it has effectively reduced the attack surface in terms of their ability to exploit software vulnerabilities that organizations
The Russian cyber spies behind the SolarWinds breach are adapting their techniques to hack into organizations that have moved their networks into cloud-hosted environments, Western officials are warning. Cloud hosting has posed a challenge to hackers because it has effectively reduced the attack surface in terms of their ability to exploit software vulnerabilities that organizations |
Hack Vulnerability Threat Cloud | ★★★ | ||
| 2024-02-26 11:00:00 | Construire une cyber-résilience contre l'ingénierie sociale alimentée par l'IA Building Cyber resilience against AI-powered social engineering (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Exploring advanced AI tactics in social engineering and effective strategies for cyber defense Long-standing as a significant threat in the business world, social engineering attacks constitute a major portion of global cyberattacks. An average business regularly faces a substantial number of such attacks every year. These attacks manifest in various forms, from intricate phishing emails to complex interactions designed to deceive employees, often leading to grave outcomes. This alarming reality is further underscored by the following statistics: · Social engineering is implicated in 98% of all cyberattacks · Approximately 90% of malicious data breaches occur due to social engineering · The typical organization faces over 700 social engineering attacks each year · The average cost incurred from a social engineering attack is about $130,000 | Malware Tool Vulnerability Threat | ★★ | ||
| 2024-02-26 10:27:00 | Lockbit Ransomware Group refait surface après le retrait des forces de l'ordre LockBit Ransomware Group Resurfaces After Law Enforcement Takedown (lien direct) |
Les acteurs de la menace derrière l'opération Ransomware de Lockbit ont refait surface sur le Web Dark en utilisant une nouvelle infrastructure, quelques jours après un exercice international d'application de la loi et NBSP; Control saisi & NBSP; de ses serveurs.
À cette fin, le groupe notoire a déplacé son portail de fuite de données vers une nouvelle adresse .onion sur le réseau Tor, répertoriant 12 nouvelles victimes à partir de l'écriture.
L'administrateur derrière Lockbit, dans A &
The threat actors behind the LockBit ransomware operation have resurfaced on the dark web using new infrastructure, days after an international law enforcement exercise seized control of its servers. To that end, the notorious group has moved its data leak portal to a new .onion address on the TOR network, listing 12 new victims as of writing. The administrator behind LockBit, in a& |
Ransomware Threat | ★★★ | ||
| 2024-02-26 08:00:20 | Le paysage des menaces de logiciels malveillants mobiles en 2023 The mobile malware threat landscape in 2023 (lien direct) |
Ce rapport détaille les statistiques et les tendances clés associées aux logiciels malveillants mobiles: Google Play Trojans, Malicents Messaging App Mods et autres.
This report details statistics and key trends associated with mobile malware: Google Play Trojans, malicious messaging app mods, and others. |
Malware Threat Studies Mobile | ★★★★ | ||
| 2024-02-26 05:03:36 | Les tenants et aboutissants de la confidentialité des données, partie 2: confidentialité par conception en protection de l'information The Ins and Outs of Data Privacy, Part 2: Privacy by Design in Information Protection (lien direct) |
This is the second blog in a two-part series about data privacy. In our previous post, we discussed how data privacy has become increasingly important. And we covered why data loss protection (DLP) and insider threat management (ITM) tools are critical to ensuring data privacy. The shift to “work from anywhere” and the increase in cloud adoption have caused a rise in data loss and insider threats. To defend data from careless, malicious and compromised insiders-and the harm that they cause-security teams must implement data security tools like data loss prevention (DLP) and insider threat management (ITM) platforms. These tools monitor and control how employees interact with data. At the same time, companies are collecting more and more data about employees themselves, like protected health information (PHI). The abundance of all this data-which is being collected and processed in the cloud-creates a critical challenge for security teams. They must protect employee privacy without impeding productivity. In this post, we\'ll explore the topic of privacy by design, which aims to strike a balance between these two challenges. We\'ll cover why it\'s so important. And we\'ll discuss how Proofpoint Information Protection can help you build a modern DLP program and comply with data privacy laws. Why privacy by design matters for DLP and ITM Privacy by design is a framework that embeds privacy into the design of IT systems, infrastructure and business processes. Privacy is not an afterthought. It is considered right from the start-in the initial design phase. What\'s more, it\'s a core component that integrates visibility, transparency and user-centricity into its design. In short, privacy by design ensures that everything is built with the user in mind. Privacy by design is important to DLP and ITM because it helps to: Protect employee rights. Personal data is sacred. Employees expect their personal data to be safe and their rights protected. When a company takes a proactive, transparent approach to data privacy, it helps maintain trust with employees. Comply with privacy laws. Data privacy laws protect people by requiring businesses to keep their data safe and avoid sharing it unethically with third parties. These laws often require companies to tell users exactly how their data is used and collected, and to notify them in the event of a data breach. Failure to comply can lead to hefty fines and penalties, which can damage a firm\'s finances and brand image. Prevent bias in investigations. When user data is kept secure and private, it ensures insider threat investigations maintain their integrity and objectivity. If a user is identified, it could influence a security analyst\'s response to an incident. User privacy helps take emotion and subjectivity out of the picture. Ensure data privacy with Proofpoint DLP and ITM Proofpoint Information Protection includes administration and access controls. These controls can help your business keep data private and meet compliance requirements. Data residency and storage Proofpoint uses regional data centers in the U.S., Europe, Australia and Japan to meet data privacy and data residency requirements. You can control exactly where your data is stored at all of these data centers. For example, you can group your endpoints and map each group to a regional data center. This ensures that data on all those endpoints are stored in that regional center. So, a U.S. realm can manage U.S. endpoint data, which is sent to the U.S. data center. Attribute-based access controls Attribute-based access controls give you a flexible and easy way to manage access to data. You can use these controls to ensure that security analysts have visibility into data on a need-to-know basis only. For instance, you can write granular policies and assign access so that a U.S.-based security analyst can only see U.S. data. They cannot see data in Europe or the Asia-Pacific region. And when an analyst needs to access a specific user\'s data for an | Data Breach Tool Threat Cloud | ★★ | ||
| 2024-02-26 02:45:39 | Plonger dans le nouveau guide de cybersécurité SMB de NCSC \\ Delving into NCSC\\'s New SMB Cybersecurity Guide (lien direct) |
Bien que les attaques contre les petites et moyennes entreprises (PME) aient rarement fait la une des journaux, elles restent une menace sérieuse.Contrairement à leurs homologues d'entreprise, de nombreuses PME n'ont pas les outils, les compétences et les services d'atténuation dont ils ont besoin pour lutter contre les menaces modernes.Comprenant que les prévenus ont été prévenus, le National Cyber Security Center (NCSC) a récemment fait ses débuts sur un guide destiné aux petites entreprises qui manquent de personnel informatique ou de soutien dédié appelé «utilisant des services en ligne en toute sécurité».Son objectif est d'aider les petits joueurs à renforcer leurs défenses de cybersécurité et à atténuer l'impact potentiel des attaques contre les entreprises ...
Although attacks on small and medium-sized businesses (SMBs) rarely hit the headlines, they remain a serious threat. Unlike their corporate counterparts, many SMBs lack the tools, skills, and mitigation services they need to combat modern threats. Understanding that forewarned is forearmed, the National Cyber Security Centre (NCSC) recently debuted a guide aimed at smaller companies that lack dedicated IT or support staff called “ Using Online Services Safely ”. Its purpose is to help smaller players bolster their cybersecurity defenses and mitigate the potential impact of attacks on companies... |
Tool Threat | ★★ | ||
| 2024-02-25 14:23:00 | Les autorités affirment que l'administrateur Lockbit "Lockbitsupp" s'est engagé avec les forces de l'ordre Authorities Claim LockBit Admin "LockBitSupp" Has Engaged with Law Enforcement (lien direct) |
Lockbitsupp, le ou les individus derrière le personnage représentant le service de ransomware de lockbit sur des forums de cybercriminalité tels que Exploit et XSS ", a engagé les forces de l'ordre", ont déclaré les autorités.
Le développement vient après le & nbsp; Takedown & nbsp; de l'opération prolifique des ransomwares en tant que service (RAAS) dans le cadre d'une opération internationale coordonnée, nommé Cronos.Plus de 14 000 voyous
LockBitSupp, the individual(s) behind the persona representing the LockBit ransomware service on cybercrime forums such as Exploit and XSS, "has engaged with law enforcement," authorities said. The development comes following the takedown of the prolific ransomware-as-a-service (RaaS) operation as part of a coordinated international operation codenamed Cronos. Over 14,000 rogue |
Ransomware Threat | ★★ | ||
| 2024-02-23 20:51:22 | Astaroth, Mekotio & Ousaban abusant Google Cloud Run dans les campagnes de logiciels malveillants axés sur LATAM Astaroth, Mekotio & Ousaban Abusing Google Cloud Run in LATAM-Focused Malware Campaigns (lien direct) |
#### Description
Depuis septembre 2023, Cisco Talos a observé une augmentation significative du volume de courriels malveillants tirant parti du service Google Cloud Run pour infecter les victimes potentielles avec des chevaux de Troie bancaires.
Les chaînes d'infection associées à ces familles de logiciels malveillants présentent l'utilisation de installateurs Microsoft malveillants (MSIS) qui fonctionnent comme des gouttes ou des téléchargeurs pour la charge utile des logiciels malveillants finaux.Les campagnes de distribution pour ces familles de logiciels malveillants sont liées, Astaroth et Mekotio distribués sous le même projet Google Cloud et Google Cloud Storage Bucket.Ousaban est également abandonné dans le cadre du processus d'infection Astaroth.
Le malware est distribué par e-mails qui sont envoyés à l'aide de thèmes liés aux factures ou aux documents financiers et fiscaux, et se présentent parfois comme étant envoyés par l'agence fiscale du gouvernement local dans le pays ciblé.Les e-mails contiennent des hyperliens vers Google Cloud Run, qui peuvent être identifiés en raison de l'utilisation de l'application Run [.] Comme domaine de niveau supérieur (TLD).Lorsque les victimes accèdent à ces hyperliens, elles sont redirigées vers les services Web d'exécution du cloud déployés par les acteurs de la menace et ont livré les composants nécessaires pour initier le processus d'infection.
#### URL de référence (s)
1. https://blog.talosintelligence.com/google-cloud-run-abuse/
#### Date de publication
20 février 2024
#### Auteurs)
Edmund Brumaghin
Ashley Shen
Holger Unterbrink
Guilherme Veree
#### Description Since September 2023, Cisco Talos have observed a significant increase in the volume of malicious emails leveraging the Google Cloud Run service to infect potential victims with banking trojans. The infection chains associated with these malware families feature the use of malicious Microsoft Installers (MSIs) that function as droppers or downloaders for the final malware payload(s). The distribution campaigns for these malware families are related, with Astaroth and Mekotio being distributed under the same Google Cloud Project and Google Cloud storage bucket. Ousaban is also being dropped as part of the Astaroth infection process. The malware is being distributed via emails that are being sent using themes related to invoices or financial and tax documents, and sometimes pose as being sent from the local government tax agency in the country being targeted. The emails contain hyperlinks to Google Cloud Run, which can be identified due to the use of run[.]app as the top-level domain (TLD). When victims access these hyperlinks, they are redirected to the Cloud Run web services deployed by the threat actors and delivered the components necessary to initiate the infection process. #### Reference URL(s) 1. https://blog.talosintelligence.com/google-cloud-run-abuse/ #### Publication Date February 20, 2024 #### Author(s) Edmund Brumaghin Ashley Shen Holger Unterbrink Guilherme Venere |
Malware Threat Cloud | ★★ | ||
| 2024-02-23 19:20:39 | Repeindre le réseau pour repousser les tactiques de vie Redesigning the Network to Fend Off Living-Off-the-Land Tactics (lien direct) |
La menace croissante de tactiques de vie à la terre nécessite une repense de la visibilité du trafic réseau pour empêcher ces types d'attaques
The growing threat of living-off-the-land tactics requires a rethink of network traffic visibility to prevent these types of attacks |
Threat | ★★ | ||
| 2024-02-23 16:11:24 | Le département de l'immigration du Malawi interrompre les services de passeport au milieu de la cyberattaque Malawi Immigration Dept. Halts Passport Services Amid Cyberattack (lien direct) |
Le président du Malawi promet de ne pas payer la rançon pour "apaiser les criminels".
President of Malawi vows not to pay ransom to "appease criminals." |
Threat | ★★★ | ||
| 2024-02-23 15:00:00 | Favoriser la collaboration pour une enquête sur les menaces standardisée & amp;Réponse Fostering Collaboration for Standardized Threat Investigation & Response (lien direct) |
Travailler ensemble peut apporter une confiance indispensable à l'industrie et aider à protéger les personnes, les organisations et le gouvernement - maintenant et à l'avenir.
Working together can bring much-needed trust to the industry and help safeguard people, organizations, and government - now and in the future. |
Threat | ★★ | ||
| 2024-02-23 14:02:47 | Près d'une cyberattaque sur trois en 2023 a impliqué l'abus de comptes valides Nearly One in Three Cyber Attacks In 2023 Involved The Abuse of Valid Accounts (lien direct) |
 Trente pour cent de tous les cyber-incidents en 2023 impliquaient des abus de références valides, selon le dernier indice de renseignement sur les menaces d'IBM X-Force.Cela représente une augmentation de soixante et onze pour cent par rapport à 2022.
Trente pour cent de tous les cyber-incidents en 2023 impliquaient des abus de références valides, selon le dernier indice de renseignement sur les menaces d'IBM X-Force.Cela représente une augmentation de soixante et onze pour cent par rapport à 2022.
 Thirty percent of all cyber incidents in 2023 involved abuse of valid credentials, according to IBM X-Force\'s latest Threat Intelligence Index. This represents a seventy-one percent increase compared to 2022.
Thirty percent of all cyber incidents in 2023 involved abuse of valid credentials, according to IBM X-Force\'s latest Threat Intelligence Index. This represents a seventy-one percent increase compared to 2022. |
Threat Studies | ★★★ | ||
| 2024-02-23 13:11:11 | Dans d'autres nouvelles: arrêt des vendeurs de logiciels espions, Settlement Freenom-Meta, 232 groupes de menaces In Other News: Spyware Vendor Shutdown, Freenom-Meta Settlement, 232 Threat Groups (lien direct) |
> Des histoires remarquables qui auraient pu glisser sous le radar: le vendeur de logiciels espions Varonis s'arrête, Crowdsstrike Tracks 232 Acteurs de la menace, Meta et Freenom Reach Settlement.
>Noteworthy stories that might have slipped under the radar: Spyware vendor Varonis is shutting down, Crowdstrike tracks 232 threat actors, Meta and Freenom reach settlement. |
Threat | ★★★ | ||
| 2024-02-23 12:53:03 | Groupes de cybercrimins exploitant activement \\ 'Catastrophic \\' Screenconnect Bogue Cybercriminal groups actively exploiting \\'catastrophic\\' ScreenConnect bug (lien direct) |
 Une vulnérabilité de sécurité dans un outil d'accès à distance disponible dans le commerce est exploitée par des criminels de ransomware quelques jours seulement après la première fois.La vulnérabilité spécifique, affectant certaines versions du produit ScreenConnect de ConnectWise \\, a reçu le maximum score CVSS de 10 , indiquantqu'il représente une menace critique pour les organisations qui n'ont pas corrigé leur logiciel.
Une vulnérabilité de sécurité dans un outil d'accès à distance disponible dans le commerce est exploitée par des criminels de ransomware quelques jours seulement après la première fois.La vulnérabilité spécifique, affectant certaines versions du produit ScreenConnect de ConnectWise \\, a reçu le maximum score CVSS de 10 , indiquantqu'il représente une menace critique pour les organisations qui n'ont pas corrigé leur logiciel.
 A security vulnerability in a commercially available remote access tool is being exploited by ransomware criminals just days after first being disclosed. The specific vulnerability, affecting some versions of ConnectWise\'s ScreenConnect product, has been given the maximum CVSS score of 10, indicating that it poses a critical threat to organizations that haven\'t patched their software.
A security vulnerability in a commercially available remote access tool is being exploited by ransomware criminals just days after first being disclosed. The specific vulnerability, affecting some versions of ConnectWise\'s ScreenConnect product, has been given the maximum CVSS score of 10, indicating that it poses a critical threat to organizations that haven\'t patched their software. |
Ransomware Tool Vulnerability Threat | ★★ | ||
| 2024-02-23 12:35:02 | Menace DeepFake: un contenu trompeur de 2 $ sape l'intégrité des élections Deepfake Threat: $2 Deceptive Content Undermines Election Integrity (lien direct) |
> Par deeba ahmed
En 2024, plus de 60 pays à travers le monde organisent des élections.La menace la plus importante pour l'intégrité de ces élections?Des vidéos DeepFake, facilement accessibles sur le Dark Web and Telegram, avec des prix allant de 2 $ à 100 $
Ceci est un article de HackRead.com Lire le post original: Menace profonde: 2 $ Le contenu trompeur sape l'intégrité des élections
>By Deeba Ahmed In 2024, over 60 countries worldwide are holding elections. The most significant threat to the integrity of these elections? Deepfake videos, readily accessible on the dark web and Telegram, with prices ranging from as low as $2 to $100. This is a post from HackRead.com Read the original post: Deepfake Threat: $2 Deceptive Content Undermines Election Integrity |
Threat | ★★★ | ||
| 2024-02-23 11:00:00 | Détection des connexions anormales O365 et des techniques d'évasion Detecting anomalous O365 logins and evasion techniques (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Summary Businesses across multiple industries, regardless of size, are at risk of being targeted with Microsoft 365 phishing campaigns. These campaigns trick users into visiting fake Microsoft login page where threat actors capture the user’s credentials. Even accounts with MFA can be victim to these types of attacks. There are several ways in which MFA is being bypassed with these types of campaigns. MFA Fatigue is one of the ways threat actors are bypassing MFA and this method attempts to exploit human error by repeatedly logging in with the stolen credentials causing an overwhelming number of MFA prompts in attempts to get the user to approve the login. Another MFA bypass technique is SIM Swapping. A SIM card is a small chip that your mobile carrier uses to hold identification information to tie your phone to you and your mobile carrier. Threat actors have found a weakness in this because there are scenarios where a customer may need a new SIM card (for example, they lost their phone). Carriers can transfer your identification information from your old SIM card to new one. SIM Swapping is when a threat actor abuses this feature and impersonates you to convince your mobile carrier to switch your phone number to a SIM card that is in the threat actor’s possession. This then allows the threat actor to receive MFA codes sent to your number via phone call or SMS. | Tool Threat Mobile Cloud | ★★★ | ||
| 2024-02-23 10:52:00 | 78% des organisations subissent des attaques de ransomwares répétées après avoir payé 78% of Organizations Suffer Repeat Ransomware Attacks After Paying (lien direct) |
Cybearon a constaté que 78% des organisations qui ont payé une demande de rançon ont été touchées par une deuxième attaque de ransomware, souvent par le même acteur de menace
Cybereason found that 78% of organizations who paid a ransom demand were hit by a second ransomware attack, often by the same threat actor |
Ransomware Threat | ★★★ | ||
| 2024-02-23 10:47:31 | Armis acquiert CTCI pour créer un système d'alerte d'attaque d'alerte précoce pour les gouvernements, les entreprises Armis acquires CTCI to create early warning attack alert system for governments, enterprises (lien direct) |
> La société de cybersécurité des renseignements d'actifs Armis a récemment annoncé qu'elle avait accepté d'acquérir CTCI (Cyber Threat Cognitive Intelligence), ...
>Asset intelligence cybersecurity firm Armis recently announced that it has agreed to acquire CTCI (Cyber Threat Cognitive Intelligence),... |
Threat | ★★ | ||
| 2024-02-23 10:01:03 | Les garanties de l'IA défensive contre les cyber-menaces émergentes, explique GlobalData Defensive AI safeguards against emerging cyber threats, says GlobalData (lien direct) |
L'annonce récente de Google \\ d'une initiative de cyber-défense de l'intelligence artificielle (AI) pour améliorer la cybersécurité mondiale souligne l'importance de la défense contre les cyber-menaces de plus en plus sophistiquées et omniprésentes.L'IA devrait jouer un rôle central dans la collecte, le traitement et la neutralisation des menaces, transformant la façon dont les organisations combattent les cyber-risques, observe GlobalData.
En regardant la technologie de détection des cyber-menaces de l'IA à travers l'objectif de l'innovation à l'aide de GlobalData \'s (...)
-
rapports spéciaux
Google\'s recent announcement of an artificial intelligence (AI) Cyber Defense Initiative to enhance global cybersecurity underscores the importance of defending against increasingly sophisticated and pervasive cyber threats. AI is expected to play a pivotal role in collecting, processing, and neutralizing threats, transforming the way organizations combat cyber risks, observes GlobalData. Looking at AI cyber threat detection technology through the lens of innovation using GlobalData\'s (...) - Special Reports |
Threat | ★★ | ||
| 2024-02-22 23:49:35 | Les retards de pharmacie aux États-Unis sont imputés aux pirates d'État-nation Pharmacy Delays Across US Blamed on Nation-State Hackers (lien direct) |
Le fournisseur de technologies de santé Change Healthcare affirme qu'un acteur présumé de la menace nationale a violé ses systèmes, provoquant des retards de transaction en pharmacie à l'échelle nationale.
Healthcare tech provider Change Healthcare says a suspected nation-state threat actor breached its systems, causing pharmacy transaction delays nationwide. |
Threat | ★★★★ | ||
| 2024-02-22 21:55:00 | Apple dévoile le protocole PQ3 - cryptage post-quantal pour iMessage Apple Unveils PQ3 Protocol - Post-Quantum Encryption for iMessage (lien direct) |
Apple a annoncé un nouveau protocole cryptographique post-Quantum appelé & nbsp; pq3 & nbsp; qui, selon lui, sera intégré à iMessage pour sécuriser la plate-forme de messagerie contre les futures attaques résultant de la menace d'un ordinateur quantique pratique.
"Avec un cryptage résilient aux compromis et des défenses étendues contre les attaques quantiques même très sophistiquées, PQ3 est le premier protocole de messagerie à atteindre
Apple has announced a new post-quantum cryptographic protocol called PQ3 that it said will be integrated into iMessage to secure the messaging platform against future attacks arising from the threat of a practical quantum computer. "With compromise-resilient encryption and extensive defenses against even highly sophisticated quantum attacks, PQ3 is the first messaging protocol to reach |
Threat | ★★ | ||
| 2024-02-22 19:57:30 | La fuite montre une alarme au Congrès sur une menace russe \\ 'mention \\' est une véritable anomalie Leak Shows Alarm in Congress Over a Russian \\'Threat\\' Is a Real Anomaly (lien direct) |
Le Congrès américain se préparait à voter sur un programme clé de surveillance étrangère la semaine dernière.Puis une menace russe sauvage est apparue.
The US Congress was preparing to vote on a key foreign surveillance program last week. Then a wild Russian threat appeared. |
Threat | ★★★ | ||
| 2024-02-22 16:14:00 | Les cybercriminels ont armé l'outil SSH-Ssh-Sake open source pour les attaques de réseau Cybercriminals Weaponizing Open-Source SSH-Snake Tool for Network Attacks (lien direct) |
Un outil de cartographie de réseau récemment open open appelé & nbsp; ssh-snake & nbsp; a été réutilisé par des acteurs de la menace pour mener des activités malveillantes.
"SSH-Snake est un ver auto-modifiant qui exploite les informations d'identification SSH découvertes sur un système compromis pour commencer à se propager dans tout le réseau", a déclaré le chercheur de Sysdig, Miguel Hern & Aacute; Ndez & Nbsp.
"Le ver recherche automatiquement les informations d'identification connues
A recently open-sourced network mapping tool called SSH-Snake has been repurposed by threat actors to conduct malicious activities. "SSH-Snake is a self-modifying worm that leverages SSH credentials discovered on a compromised system to start spreading itself throughout the network," Sysdig researcher Miguel Hernández said. "The worm automatically searches through known credential |
Tool Threat | ★★ | ||
| 2024-02-22 14:52:59 | Tenable: les professionnels de la cybersécurité devraient s'inquiéter des cyberattaques parrainées par l'État Tenable: Cyber Security Pros Should Worry About State-Sponsored Cyber Attacks (lien direct) |
La sortie de l'acteur de menace soutenu par la Chine Volt Typhoon et du compromis de Microsoft \\ par la blizzard de minuit soutenue par la Russie fournissent d'importantes leçons de stratégie de cybersécurité pour l'Australie, explique Tenable.
The outing of China-backed threat actor Volt Typhoon and Microsoft\'s compromise by Russia-backed Midnight Blizzard provide important cyber security strategy lessons for Australia, says Tenable. |
Threat | Guam | ★★★ | |
| 2024-02-22 13:00:00 | Voltzite Threat Group \\ est sous le cyber-espionnage radar sur les systèmes critiques américains VOLTZITE Threat Group\\'s Under the Radar Cyber Espionage on U.S. Critical Systems (lien direct) |
> Voltzite est un groupe de menaces actif suivi par Dragos Intelligence.Ce groupe partage des chevauchements avec Volt Typhoon (Microsoft) et le ...
The Post groupe de menaces voltzite \\Sous le cyber-espionnage radar sur les systèmes critiques américains est apparu pour la première fois sur dragos .
>VOLTZITE is an active threat group tracked by Dragos Intelligence. This group shares overlaps with Volt Typhoon (Microsoft) and the... The post VOLTZITE Threat Group\'s Under the Radar Cyber Espionage on U.S. Critical Systems first appeared on Dragos. |
Threat Industrial | Guam | ★★ | |
| 2024-02-22 11:47:19 | (Déjà vu) Les données sur la menace de Sonicwall expose les profondeurs des cyberattaques;Propulse le besoin de fournisseurs de services gérés SonicWall Threat Data Exposes Depths of Cyberattacks; Propels the Need for Managed Service Providers (lien direct) |
Les données sur la menace de Sonicwall expose les profondeurs des cyberattaques;Propulse le besoin de fournisseurs de services gérés (MSPS)
• Les tentatives globales d'intrusion grimpent (+ 20%), alors que les acteurs de la menace diversifient les tactiques - augmentation des attaques à travers le monde
• Le ransomware s'intensifie tout au long de l'année (+ 27% en 2h) au pic pendant les mois d'été (+ 37%)
• Volume total de cryptojacking & # 8211;pics + 659% mondialement
• IoT exploit (+ 15%) et menaces cryptées (+ 117%) également sur la montée
• Sonicwall a découvert 293 989 \\ 'never-befre-vis \' malware variantes & # 8211;805 par jour
-
rapports spéciaux
SonicWall Threat Data Exposes Depths of Cyberattacks; Propels the Need for Managed Service Providers (MSPs) • Overall intrusion attempts climb (+20%), as threat actors diversify tactics - increase in attacks around the globe • Ransomware intensifies through the year (+27% in 2H) peaking during the summer months (+37%) • Total cryptojacking volume – spikes +659% globally • IoT exploit (+15%) and encrypted threats (+117%) also on the rise • SonicWall discovered 293,989 \'never-before-seen\' malware variants – 805 a day - Special Reports |
Malware Threat | ★★ | ||
| 2024-02-22 11:00:00 | L'importance de la cybersécurité dans les services bancaires en ligne The importance of Cybersecurity in online banking (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. In our digitized world, online banking has become an integral part of managing your finances, offering unparalleled convenience. However, with this convenience comes an increasing need for robust cybersecurity measures. As you embrace the ease of handling your financial affairs online, understanding the importance of cybersecurity becomes paramount. This article delves into the critical role of cybersecurity in safeguarding your financial assets and personal information from the evolving risks associated with online banking. Risks associated with online banking Engaging in online banking exposes you to various risks that demand your vigilance. Financial data breaches, where cybercriminals exploit vulnerabilities to gain unauthorized access to sensitive information, pose a significant threat. Phishing attacks, disguised as legitimate communications, aim to trick you into disclosing personal details. Additionally, identity theft, a direct consequence of these breaches, can lead to severe financial implications. Recognizing these risks is the first step in fortifying your online banking experience and ensuring the protection of your valuable information. Beyond individual concerns, these risks reverberate through financial institutions, impacting their reputation. Financial losses and unauthorized activities not only harm individuals but also erode the trust customers place in their banks and reputational damage becomes a looming threat for financial institutions, highlighting the critical need for comprehensive cybersecurity measures. Offshore banking risks Offshore banking, while offering financial privacy and potential tax advantages, poses certain risks that individuals should be aware of. One significant concern is the potential for increased susceptibility to financial fraud and money laundering due to the less stringent regulations in some offshore jurisdictions. Additionally, the lack of transparency in offshore banking systems may create challenges in recovering funds in the event of disputes or legal issues. It\'s crucial for individuals engaging in offshore banking to carefully evaluate the regulatory environment, conduct thorough due diligence on financial institutions, and be aware of the potential risks associated with this financial strategy. The impact of cyber-attacks on individuals and financial institutions The fallout from cyber-attacks extends far beyond individual victims, leaving lasting effects on financial institutions. Instances of financial losses and unauthorized activities not only harm individuals but also erode the trust customers place in their banks. The repercussions of cyber-attacks reverberate through the broader financial landscape, extending well beyond the immediate impact on individual victims. It is sobering to consider that when a financial institution falls victim to a cyber-attack, the consequences are felt on a systemic level. Instances of financial losses and unauthorized activities create a ripple effect, compromising the overall integrity of the affected institution. The fallout includes not only the immediate financial implications | Vulnerability Threat | ★★ | ||
| 2024-02-22 09:54:37 | Les données sur les menaces de SonicWall révèlent la profondeur des cyberattaques et renforcent la nécessité de recourir à des fournisseurs de services managés (MSP) (lien direct) | Les données sur les menaces de SonicWall révèlent la profondeur des cyberattaques et renforcent la nécessité de recourir à des fournisseurs de services managés (MSP) • Les tentatives d'intrusion augmentent (+20 %), les auteurs de menaces diversifiant leurs tactiques : les attaques progressent dans le monde entier • Les ransomwares s'intensifient tout au long de l'année (+27 % au 2e semestre) avec un pic pendant les mois d'été (+37 %) • Volume total de cryptojacking : +659 % au niveau mondial • Les exploits IoT (+15 %) et les menaces chiffrées (+117 %) sont également en hausse • SonicWall a découvert 293 989 variantes de logiciels malveillants encore inconnues, soit 805 par jour - Investigations | Threat | ★★ | ||
| 2024-02-22 09:44:38 | TEHTRIS dévoile son rapport Threat Intelligence et donne un aperçu de l\'évolution des principales cybermenaces de 2023 (lien direct) | >TEHTRIS, entreprise spécialisée dans la neutralisation automatique en temps réel et sans action humaine des cyberattaques, vient de publier son rapport annuel de Threat Intelligence, analysant les menaces cyber de l'année écoulée et celles qui façonneront les mois venir. Ce rapport souligne notamment une accélération des cyberattaques au cours du second semestre 2023, avec une […] The post TEHTRIS dévoile son rapport Threat Intelligence et donne un aperçu de l'évolution des principales cybermenaces de 2023 first appeared on UnderNews. | Threat | ★★★★ | ||
| 2024-02-22 08:28:44 | Renforcement de la cyber-résilience ICS / OT: Apprentissage des incidents de cybersécurité de 2023 à partir de Dragos \\ 'Rapport Strengthening ICS/OT Cyber Resilience: Learning from 2023\\'s Cybersecurity Incidents from Dragos\\' Report (lien direct) |
> Introduction: Comprendre le paysage des menaces en évolution de la cybersécurité industrielle 2023 a été un moment de bassin versant pour la cybersécurité industrielle, ...
>Introduction: Understanding the Evolving Threat Landscape in Industrial Cybersecurity 2023 has been a watershed moment for industrial cybersecurity,... |
Threat Studies Industrial | ★★★★ | ||
| 2024-02-22 05:00:00 | Les menaces continues ont besoin d'une gestion continue Continuous Threats Need Continuous Management (lien direct) |
Un explicateur principal des parties prenantes pour la cybersécurité continue de la gestion de l'exposition aux menaces (CTEM) à l'ère des menaces continues: l'affaire ...
A senior stakeholder explainer for Continuous Threat Exposure Management (CTEM) Cybersecurity in the Era of Continuous Threats: The Case... |
Threat | ★★★ | ||
| 2024-02-21 20:24:47 | Dot, la Maison Blanche s'attaque à la menace chinoise pour la sécurité portuaire américaine DoT, White House Tackle the Chinese Threat to US Port Security (lien direct) |
Les nouveaux investissements et l'autorité de la Garde côtière visent à limiter la menace présumée que les vendeurs chinois représentent la sécurité maritime américaine.
New investments and Coast Guard authority aim to curb the alleged threat that Chinese vendors pose to American maritime security. |
Threat | ★★ | ||
| 2024-02-21 18:33:00 | Mustang Panda cible l'Asie avec des variantes avancées Doplugs Mustang Panda Targets Asia with Advanced PlugX Variant DOPLUGS (lien direct) |
L'acteur de menace lié à la Chine connue sous le nom de Mustang Panda a ciblé divers pays asiatiques à l'aide d'une variante de la porte dérobée Plugx (AKA Korplug) surnommée Doplugs.
"Le jeu de malware Plugx personnalisé est différent du type général du malware Plugx qui contient un module de commande de porte dérobée terminé, et que le premier n'est utilisé que pour télécharger le second", Trend Micro Researchs Sunny Lu
The China-linked threat actor known as Mustang Panda has targeted various Asian countries using a variant of the PlugX (aka Korplug) backdoor dubbed DOPLUGS. "The piece of customized PlugX malware is dissimilar to the general type of the PlugX malware that contains a completed backdoor command module, and that the former is only used for downloading the latter," Trend Micro researchers Sunny Lu |
Malware Threat Prediction | ★★★ | ||
| 2024-02-21 15:58:44 | Rapport 2024 Incident Response - Unit 42/Palo Alto Networks (lien direct) | Rapport 2024 Incident Response - Unit 42/Palo Alto Networks Dans le paysage des menaces de cybersécurité en constante évolution, il est plus que jamais crucial de garder une longueur d'avance sur les acteurs malveillants. Pour cela, il faut comprendre leurs comportements, connaître leurs techniques et outils. - Investigations | Tool Threat Studies | ★★★ | ||
| 2024-02-21 15:00:00 | Comment les Cisos équilibrent la croissance des entreprises, la sécurité dans le paysage cyber-menace How CISOs Balance Business Growth, Security in Cyber-Threat Landscape (lien direct) |
La collaboration, les soins et la planification proactive doivent faire partie des boîtes à outils CISO, car l'aggravation des environnements de menaces devient la nouvelle normale.Les CISO doivent ajuster les processus afin que l'innovation commerciale puisse se poursuivre.
Collaboration, care, and proactive planning need to be part of CISO toolboxes as worsening threat environments become the new normal. CISOs need to adjust processes so business innovation can continue. |
Threat | ★★★ | ||
| 2024-02-21 14:50:00 | Cybersécurité pour les soins de santé diagnostiquant le paysage de la menace et prescrivant des solutions de reprise Cybersecurity for Healthcare-Diagnosing the Threat Landscape and Prescribing Solutions for Recovery (lien direct) |
Le jour de Thanksgiving 2023, alors que de nombreux Américains célébraient, les hôpitaux des États-Unis faisaient tout le contraire.Les systèmes échouaient.Les ambulances ont été détournées.Les soins ont été altérés.Les hôpitaux de trois États ont été & nbsp; frappés par une attaque de ransomware, et à ce moment-là, les répercussions du monde réel sont venues à la lumière, ce n'était pas juste des réseaux informatiques qui ont été mis en garde
On Thanksgiving Day 2023, while many Americans were celebrating, hospitals across the U.S. were doing quite the opposite. Systems were failing. Ambulances were diverted. Care was impaired. Hospitals in three states were hit by a ransomware attack, and in that moment, the real-world repercussions came to light-it wasn\'t just computer networks that were brought to a halt, but actual patient |
Ransomware Threat Medical | ★★★ | ||
| 2024-02-21 14:37:16 | Browser en entreprise: la passerelle vers la sécurisation de toutes les identités Enterprise Browser: The Gateway to Securing All Identities (lien direct) |
Avec de nouvelles identités, environnements et méthodes d'attaque dominant le paysage des menaces d'aujourd'hui, les chefs de cybersécurité sont hyper concentrés sur la sécurisation des identités pour protéger les entreprises.Cependant, il existe un écart de sécurité flagrant et élevé que les acteurs de menace exploitent activement pour voler ...
With new identities, environments and attack methods dominating today\'s threat landscape, cybersecurity leaders are hyper-focused on securing identities to safeguard enterprises. However, a glaring, high-touch security gap exists that threat actors actively exploit to steal... |
Threat | ★★ | ||
| 2024-02-21 14:03:25 | Les nouveaux logiciels malveillants SSH-Sake volent les clés SSH pour se propager sur le réseau New SSH-Snake malware steals SSH keys to spread across the network (lien direct) |
Un acteur de menace utilise un outil de cartographie de réseau open source nommé SSH-Snake pour rechercher des clés privées non détectées et se déplacer latéralement sur l'infrastructure de victime.[...]
A threat actor is using an open-source network mapping tool named SSH-Snake to look for private keys undetected and move laterally on the victim infrastructure. [...] |
Malware Tool Threat | ★★ | ||
| 2024-02-21 13:46:06 | Comprendre la loi UE AI: implications pour les agents de conformité des communications Understanding the EU AI Act: Implications for Communications Compliance Officers (lien direct) |
The European Union\'s Artificial Intelligence Act (EU AI Act) is set to reshape the landscape of AI regulation in Europe-with profound implications. The European Council and Parliament recently agreed on a deal to harmonize AI rules and will soon bring forward the final text. The parliament will then pass the EU AI Act into law. After that, the law is expected to become fully effective in 2026. The EU AI Act is part of the EU\'s digital strategy. When the act goes into effect, it will be the first legislation of its kind. And it is destined to become the “gold standard” for other countries in the same way that the EU\'s General Data Protection Regulation (GDPR) became the gold standard for privacy legislation. Compliance and IT executives will be responsible for the AI models that their firms develop and deploy. And they will need to be very clear about the risks these models present as well as the governance and the oversight that they will apply to these models when they are operated. In this blog post, we\'ll provide an overview of the EU AI Act and how it may impact your communications practices in the future. The scope and purpose of the EU AI Act The EU AI Act establishes a harmonized framework for the development, deployment and oversight of AI systems across the EU. Any AI that is in use in the EU falls under the scope of the act. The phrase “in use in the EU” does not limit the law to models that are physically executed within the EU. The model and the servers that it operates on could be located anywhere. What matters is where the human who interacts with the AI is located. The EU AI Act\'s primary goal is to ensure that AI used in the EU market is safe and respects the fundamental rights and values of the EU and its citizens. That includes privacy, transparency and ethical considerations. The legislation will use a “risk-based” approach to regulate AI, which considers a given AI system\'s ability to cause harm. The higher the risk, the stricter the legislation. For example, certain AI activities, such as profiling, are prohibited. The act also lays out governance expectations, particularly for high-risk or systemic-risk systems. As all machine learning (ML) is a subset of AI, any ML activity will need to be evaluated from a risk perspective as well. The EU AI Act also aims to foster AI investment and innovation in the EU by providing unified operational guidance across the EU. There are exemptions for: Research and innovation purposes Those using AI for non-professional reasons Systems whose purpose is linked to national security, military, defense and policing The EU AI Act places a strong emphasis on ethical AI development. Companies must consider the societal impacts of their AI systems, including potential discrimination and bias. And their compliance officers will need to satisfy regulators (and themselves) that the AI models have been produced and operate within the Act\'s guidelines. To achieve this, businesses will need to engage with their technology partners and understand the models those partners have produced. They will also need to confirm that they are satisfied with how those models are created and how they operate. What\'s more, compliance officers should collaborate with data scientists and developers to implement ethical guidelines in AI development projects within their company. Requirements of the EU AI Act The EU AI Act categorizes AI systems into four risk levels: Unacceptable risk High risk Limited risk Minimal risk Particular attention must be paid to AI systems that fall into the “high-risk” category. These systems are subject to the most stringent requirements and scrutiny. Some will need to be registered in the EU database for high-risk AI systems as well. Systems that fall into the “unacceptable risk” category will be prohibited. In the case of general AI and foundation models, the regulations focus on the transparency of models and the data used and avoiding the introduction of system | Vulnerability Threat Legislation | ★★ |
To see everything:
Our RSS (filtrered)
