What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-10-23 10:00:00 | Planification de la continuité des activités: en regardant en arrière ou à l'avance Business continuity planning: Looking back or ahead (lien direct) |
In September 2023, cybercriminals launched an extensive ransomware attack that disrupted several major businesses in the Las Vegas Casino Business/District. The attack shook the city and stopped consumer goods and services for several hours. The attack influenced security, visitor services, and financial activities. Businesses lost money and long-term reputational risks ensued. Increasing op tempo A company can keep running after a disruption if it has a comprehensive Business Continuity Plan (BCP) that includes risk assessments, Business Impact Assessments (BIAs), and recovery strategies. A BCP is needed to minimize risk apprehensions, reduce financial loss, and maintain continuous business operations. A business impact analysis (BIA) must be part of Business Continuity Plans (BCPs). The plan sets recovery time and point goals, ranks the most important processes, and figures out how delays will affect business functions. BIAs help organizations figure out what tools and plans they need for recovery. Disaster Recovery Plans, or DRPs, lay out how a business will handle and rebound from a disaster. It includes tools for recovering systems, data, and infrastructure. A complete, well-tested DRP is necessary to keep problems to a minimum and get services back up and running quickly. To stay safe from cyber threats, businesses need to put their operating security footprint at the top of their list of priorities. In this way, networks, systems, apps, and data are kept safe. Data breaches and unauthorized access are less likely to happen with firewalls, intrusion detection systems, and encryption methods. Rearview The ransomware attack on the Las Vegas Casino Business/District in September 2023 shows that current risk management methods need to be looked at and updated. These steps cut down on operational disruptions, keep customer goods and services safe, and speed up the recovery of mission-critical systems. Being operationally ready is important for protecting your business and preparing for the unexpected. The most common way for threat players to take over a company\'s resources, assets, and people is through ransomware attacks. Recent statistics show that strong holding the most sought-after security principles can disrupt present business operations: The State of Ransomware Report in the US says that the average ransomware attack costs $8.1 million and takes 287 days to fix (Emsisoft, 2021). The number of ransom payments made by victims rose by 311% in 2020 (Crypto Crime Report, 2021). Going forward Ransomware attacks affect people all over the world, resulting in huge financial losses costs - compiled worldwide topping $20 billion in 2020. The COVID-19 pandemic has given hackers new avenues and threat vectors to hack, crack, and exploit. It is imperative for businesses to strengthen the home front to gain home-field advantage against cyber threat actors. Having a comprehensive, repeatable, verifiable disaster recovery and business continuity plan minimizes the economic im | Ransomware Tool Vulnerability Threat | ★★ | ||
| 2023-10-23 08:30:00 | Police Dismante Ragnar Locker Ransomware Group Police Dismantle Ragnar Locker Ransomware Group (lien direct) |
Variante prolifique infrastructure fréquemment ciblée
Prolific variant frequently targeted critical infrastructure |
Ransomware | ★★ | ||
| 2023-10-23 02:24:33 | 2023 août & # 8211;Rapport de tendance des menaces sur les statistiques des ransomwares et les problèmes majeurs 2023 Aug – Threat Trend Report on Ransomware Statistics and Major Issues (lien direct) |
Ce rapport fournit des statistiques sur le nombre de nouveaux échantillons de ransomware, des systèmes ciblés et des entreprises ciblées en août 2023, ainsi que des problèmes de ransomware notables en Corée et dans d'autres pays.Tendances clés 1) Tactiques de pression élargies des ransomwares sur les entreprises ciblées 2) Rhysida Ransomware Connection avec la vice Society 3) Monti Ransomware a introduit une nouvelle technique de chiffrement Linux Aug_Thereat Trend Rapport sur les statistiques des ransomwares et les principaux problèmes
This report provides statistics on the number of new ransomware samples, targeted systems, and targeted businesses in August 2023, as well as notable ransomware issues in Korea and other countries. Key Trends 1) CLOP ransomware expanded pressure tactics on targeted businesses 2) Rhysida ransomware connection with Vice Society 3) Monti ransomware introduced new Linux encryption technique Aug_Threat Trend Report on Ransomware Statistics and Major Issues |
Ransomware Threat Prediction | ★★ | ||
| 2023-10-23 02:22:46 | 2023 Jul & # 8211;Rapport sur la tendance des menaces du Web Deep et Dark 2023 Jul – Deep Web and Dark Web Threat Trend Report (lien direct) |
Ce rapport de tendance sur le Web Deep et le Web sombre d'août 2023 est sectionné en ransomware, forums & # & #38;Marchés noirs et acteurs de menace.Nous tenons à dire à l'avance qu'une partie du contenu n'a pas encore été confirmée comme vraie.1) Ransomware (1) Alphv (Blackcat) (2) Lockbit (3) NoEscape (4) Metaencryptor (5) Rhysida 2) Forum & # 38;Black Market (1) Le retour du voleur de raton laveur (2) Anonfiles a fermé (3) violation de données du site Web d'apprentissage des langues étrangères 3) ...
This trend report on the deep web and dark web of August 2023 is sectioned into Ransomware, Forums & Black Markets, and Threat Actors. We would like to state beforehand that some of the content has yet to be confirmed to be true. 1) Ransomware (1) ALPHV (BlackCat) (2) LockBit (3) NoEscape (4) MetaEncryptor (5) Rhysida 2) Forum & Black Market (1) The Return of Raccoon Stealer (2) Anonfiles Shut Down (3) Data Breach of Foreign Language Learning Website 3)... |
Ransomware Data Breach Threat Prediction | ★★ | ||
| 2023-10-21 18:40:00 | Europol démantèle une infrastructure de ransomware Ragnar Locker, développeur NABS Key Europol Dismantles Ragnar Locker Ransomware Infrastructure, Nabs Key Developer (lien direct) |
Vendredi, Europol a annoncé le retrait de l'infrastructure associée aux ransomwares de casier Ragnar, parallèlement à l'arrestation d'une "cible clé" en France.
"Dans une action effectuée entre le 16 et le 20 octobre, des recherches ont été effectuées en Tchéchie, en Espagne et en Lettonie", a indiqué l'agence."L'auteur principal, soupçonné d'être un développeur du groupe Ragnar, a été amené devant l'examen
Europol on Friday announced the takedown of the infrastructure associated with Ragnar Locker ransomware, alongside the arrest of a "key target" in France. "In an action carried out between 16 and 20 October, searches were conducted in Czechia, Spain, and Latvia," the agency said. "The main perpetrator, suspected of being a developer of the Ragnar group, has been brought in front of the examining |
Ransomware | ★★ | ||
| 2023-10-21 11:05:10 | The Week in Ransomware - 20 octobre 2023 - Right Back The Week in Ransomware - October 20th 2023 - Fighting Back (lien direct) |
Ce fut une mauvaise semaine pour les ransomwares, le ransomware Trigona souffrant d'une violation de données et des forces de l'ordre perturbant le fonctionnement du ragnarlocker.[...]
This was a bad week for ransomware, with the Trigona ransomware suffering a data breach and law enforcement disrupting the RagnarLocker ransomware operation. [...] |
Ransomware Data Breach | ★★ | ||
| 2023-10-20 21:35:22 | Gang de ransomware de casser Ragnar Locker Ransomware Gang Dismantled, Key Suspect Arrested, Site Seized (lien direct) |
> Par waqas
Les forces de l'ordre mondiales impliquant 11 pays ont arrêté le gang de ransomware de casier Ragnar.
Ceci est un article de HackRead.com Lire la publication originale: Ragnar Locker Ransomware Gang démantelé, clé suspecte arrêtée, site saisi
>By Waqas Global law enforcement involving 11 countries has shuts down Ragnar Locker ransomware gang. This is a post from HackRead.com Read the original post: Ragnar Locker Ransomware Gang Dismantled, Key Suspect Arrested, Site Seized |
Ransomware | ★★★ | ||
| 2023-10-20 17:28:00 | Europol: \\ 'cible clé \\' dans l'opération de ransomware de casier Ragnar arrêté à Paris Europol: \\'Key target\\' in Ragnar Locker ransomware operation arrested in Paris (lien direct) |
 Une «cible clé» qui aurait été impliquée dans le Ragnar Locker Ransomware Group a été arrêtée lundi à Paris, selon des responsables d'Europol.Le annonce , fait vendredi, est le premier mot officiel des forces de l'ordre après que le site de fuite du gang \\ était Remplacé par une bannière mettant en vedette les insignes de plusieurs agences jeudi.Europol a déclaré la loi
Une «cible clé» qui aurait été impliquée dans le Ragnar Locker Ransomware Group a été arrêtée lundi à Paris, selon des responsables d'Europol.Le annonce , fait vendredi, est le premier mot officiel des forces de l'ordre après que le site de fuite du gang \\ était Remplacé par une bannière mettant en vedette les insignes de plusieurs agences jeudi.Europol a déclaré la loi
 A “key target” allegedly involved with the Ragnar Locker ransomware group was arrested in Paris on Monday, according to officials at Europol. The announcement, made Friday, is the first official word from law enforcement after the gang\'s leak site was replaced with a banner featuring the insignias of several agencies on Thursday. Europol said law
A “key target” allegedly involved with the Ragnar Locker ransomware group was arrested in Paris on Monday, according to officials at Europol. The announcement, made Friday, is the first official word from law enforcement after the gang\'s leak site was replaced with a banner featuring the insignias of several agencies on Thursday. Europol said law |
Ransomware | ★★ | ||
| 2023-10-20 15:00:32 | Sélection de l'éducation: Marple Newtown School District s'associe à Check Point pour protéger les étudiants et les employés Safeguarding Education: Marple Newtown School District Partners with Check Point to Protect Students and Employees (lien direct) |
> Alors que les écoles des États-Unis commencent une nouvelle année académique, la menace imminente des cyberattaques jette une ombre sur l'industrie de l'éducation.Selon Check Point Research, le secteur de l'éducation est l'une des industries les plus attaquées par les ransomwares.Le ransomware peut entraîner la perte de données sensibles et personnelles des élèves et des enseignants.Et selon le US Government Accountability Office, les cyberattaques peuvent également entraîner une perte de temps d'apprentissage allant de trois jours à trois semaines, en plus des pertes financières pour les districts scolaires entre 50 000 $ et 1 million de dollars.Protéger les informations sensibles des cyberattaquants est [& # 8230;]
>As schools across the United States are beginning a new academic year, the looming threat of cyberattacks casts a shadow over the education industry. According to Check Point Research, the education sector is one of the most attacked industries by ransomware. Ransomware can lead to the loss of sensitive and personal data from students and teachers. And according to the U.S. Government Accountability Office, cyber-attacks can also cause a loss of learning time ranging from three days to three weeks, in addition to financial losses for school districts between $50,000 to $1 million. Protecting sensitive information from cyber attackers is […] |
Ransomware Threat | ★★ | ||
| 2023-10-20 14:32:22 | Les autorités prennent le contrôle du site Web sombre du ragnarlocker ransomware Authorities Seize Control of RagnarLocker Ransomware Dark Web Site (lien direct) |
> Le site de fuite du groupe sombre du Ransomware Group du Ragnarlocker a été saisi dans une opération coordonnée d'application de la loi.
>The RagnarLocker ransomware group\'s dark web leak site has been seized in a coordinated law enforcement operation. |
Ransomware | ★★ | ||
| 2023-10-19 19:33:00 | Europol Strike Wounds Ragnar Locker Ransomware Group (lien direct) | Plusieurs pays d'Europe ainsi que des États-Unis et du Japon ont participé à l'opération, qui vise à défangler l'un des plus grands noms du ransomware.
Several countries in Europe as well as the United States and Japan were involved in the operation, which is aimed at defanging one of the bigger names in ransomware. |
Ransomware | ★★★ | ||
| 2023-10-19 19:15:00 | Les préoccupations se développent à mesure que les imitations de verrouillage ciblent de plus en plus les vulnérabilités populaires Concerns grow as LockBit knockoffs increasingly target popular vulnerabilities (lien direct) |
 Les pirates utilisent une boîte à outils divulguée utilisée pour créer des versions de bricolage du ransomware de verrouillage populaires, ce qui facilite même les cybercriminels amateurs pour cibler les vulnérabilités communes.Le Gang de ransomware de verrouillage , qui a attaqué des milliers d'organisations à travers le monde, a fait divulguer la boîte à outils en septembre 2022 par un affilié à tristesse .Les experts ont immédiatement exprimé des préoccupations
Les pirates utilisent une boîte à outils divulguée utilisée pour créer des versions de bricolage du ransomware de verrouillage populaires, ce qui facilite même les cybercriminels amateurs pour cibler les vulnérabilités communes.Le Gang de ransomware de verrouillage , qui a attaqué des milliers d'organisations à travers le monde, a fait divulguer la boîte à outils en septembre 2022 par un affilié à tristesse .Les experts ont immédiatement exprimé des préoccupations
 Hackers are using a leaked toolkit used to create do-it-yourself versions of the popular LockBit ransomware, making it easy for even amateur cybercriminals to target common vulnerabilities. The LockBit ransomware gang, which has attacked thousands of organizations across the world, had the toolkit leaked in September 2022 by a disgruntled affiliate. Experts immediately expressed concerns
Hackers are using a leaked toolkit used to create do-it-yourself versions of the popular LockBit ransomware, making it easy for even amateur cybercriminals to target common vulnerabilities. The LockBit ransomware gang, which has attacked thousands of organizations across the world, had the toolkit leaked in September 2022 by a disgruntled affiliate. Experts immediately expressed concerns |
Ransomware Vulnerability | ★★ | ||
| 2023-10-19 16:30:08 | Europol frappe le Ragnarlocker hors ligne dans le deuxième grand buste des ransomwares cette année Europol knocks RagnarLocker offline in second major ransomware bust this year (lien direct) |
Le groupe restera dans les mémoires comme un négociateur fidèle et un intimidateur d'infrastructures critiques orgs Les organismes d'application de la loi ont repris le site de fuite de Ransomware Group de Ragnarlocker dans un Takedown coordonné internationalement.…
Group will be remembered as staunch negotiator and a bullier of critical infrastructure orgs Law enforcement agencies have taken over RagnarLocker ransomware group\'s leak site in an internationally coordinated takedown.… |
Ransomware | ★★ | ||
| 2023-10-19 16:15:00 | Site de ransomware Ragnar Locker Ransomware par le FBI, Europol Ragnar Locker ransomware site taken down by FBI, Europol (lien direct) |
 Le site de fuite du gang ransomware prolifique Ragnar Locker a été remplacé par un avis de retrait du FBI, d'Europol et de plusieurs organismes d'application de la loi en Europe jeudi.Dans une déclaration à Recred Future News, un porte-parole d'Europol a déclaré qu'ils ne pouvaient pas divulguer plus d'informations sur l'opération parce que «un certain nombre d'actions sont toujours
Le site de fuite du gang ransomware prolifique Ragnar Locker a été remplacé par un avis de retrait du FBI, d'Europol et de plusieurs organismes d'application de la loi en Europe jeudi.Dans une déclaration à Recred Future News, un porte-parole d'Europol a déclaré qu'ils ne pouvaient pas divulguer plus d'informations sur l'opération parce que «un certain nombre d'actions sont toujours
 The leak site of the prolific ransomware gang Ragnar Locker was replaced with a takedown notice from the FBI, Europol and several law enforcement agencies in Europe on Thursday. In a statement to Recorded Future News, a Europol spokesperson said they cannot release more information about the operation because “a number of actions are still
The leak site of the prolific ransomware gang Ragnar Locker was replaced with a takedown notice from the FBI, Europol and several law enforcement agencies in Europe on Thursday. In a statement to Recorded Future News, a Europol spokesperson said they cannot release more information about the operation because “a number of actions are still |
Ransomware | ★★★ | ||
| 2023-10-19 14:17:19 | Piratage du leader de la plaisance mondiale : Brunswick s\'explique (lien direct) | Juin 2023, des pirates informatiques s'invitent dès les serveurs du leader mondial de la navigation de plaisance. Cinq mois plus tard, Brunswick revient sur sa fuite de données.... | Ransomware | ★★★ | ||
| 2023-10-19 10:39:39 | Les sites d'extorsion Web sombres de Ragnar Locker Ransomware ont été saisis par la police Ragnar Locker ransomware\\'s dark web extortion sites seized by police (lien direct) |
Le Ragnar Locker Ransomware Operation \'s TOR La négociation et les sites de fuite de données ont été saisis jeudi matin dans le cadre d'une opération internationale d'application de la loi.[...]
The Ragnar Locker ransomware operation\'s Tor negotiation and data leak sites were seized Thursday morning as part of an international law enforcement operation. [...] |
Ransomware | ★ | ||
| 2023-10-19 10:00:00 | Pourquoi les organisations ne détectent-elles pas les menaces de cybersécurité? Why are organizations failing to detect cybersecurity threats? (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. With the changing security landscape, the most daunting task for the CISO and CIO is to fight an ongoing battle against hackers and cybercriminals. Bad actors stay ahead of the defenders and are always looking to find new vulnerabilities and loopholes to exploit and enter the business network. Failing to address these threats promptly can have catastrophic consequences for the organization. A survey finds that, on average, it takes more than five months to detect and remediate cyber threats. This is a significant amount of time, as a delayed response to cyber threats can result in a possible cyber-attack. One can never forget the devastating impacts of the Equifax breach in 2017 and the Target breach in 2013 due to delayed detection and response. This is concerning and highlights the need for proactive cybersecurity measures to detect and mitigate rising cyber threats. Amidst this, it\'s also crucial to look into why it is challenging to detect cyber threats. Why do organizations fail to detect cyber threats? Security teams are dealing with more cyber threats than before. A report also confirmed that global cyber attacks increased by 38% in 2022 compared to the previous year. The increasing number and complexity of cyber-attacks make it challenging for organizations to detect them. Hackers use sophisticated techniques to bypass security systems and solutions - like zero-day vulnerabilities, phishing attacks, business email compromises (BEC), supply chain attacks, and Internet of Things (IoT) attacks. Some organizations are unaware of the latest cyber threat trends and lack the skills and resources to detect them. For instance, hackers offer professional services like ransomware-as-a-service (RaaS) to launch ransomware attacks. Surprisingly, two out of three ransomware attacks are facilitated by the RaaS setup, but still, companies fail to have a defensive strategy against them. Enterprises relying on legacy devices and outdated software programs are no longer effective at recognizing certain malicious activities, leaving the network vulnerable to potential threats. Additionally, the lack of trained staff, insider threats, and human errors are other reasons why many organizations suffer at the hands of threat actors. Besides this, much of the company\'s data is hidden as dark data. As the defensive teams and employees may be unaware of it, the hackers take complete advantage of dark data and either replicate it or use it to fulfill their malicious intentions. Moreover, cloud migration has rapidly increased in recent years, putting cybersecurity at significant risk. The complexity of the cloud environments, poorly secured remote and hybrid work environments, and sharing security responsibilities between cloud service providers and clients have complicated the situation. In addition, cloud vulnerabilities, which have risen to 194% from the previous year, have highlighted the need for organizations to look out for ways to strengthen their security infrastructure. Security measures to consider to prevent cyber threats Since businesses face complex cyber threats, mitigating them require | Ransomware Data Breach Tool Vulnerability Threat Cloud | Equifax | ★★ | |
| 2023-10-19 09:30:00 | Groupe de pirate GhostSec dévoile l'implant de ransomware de nouvelle génération Hacker Group GhostSec Unveils New Generation Ransomware Implant (lien direct) |
Le groupe ex-hacktiviste est désormais pleinement impliqué dans le marché des ransomwares en tant que service
The ex-hacktivist group is now fully involved with the ransomware-as-a-service market |
Ransomware | ★★★ | ||
| 2023-10-19 02:00:00 | Startup de sécurité AirGap Networks apporte des technologies de télécommunications au LAN Security startup Airgap Networks brings telco technologies to the LAN (lien direct) |
Les logiciels malveillants générateurs de l'AI, l'usurpation de faux identité profonde et les ransomwares parrainés par l'État ne sont que quelques-unes des dernières méthodes que les attaquants utilisent pour contourner les outils de cybersécurité traditionnels.Ritesh Agrawal, PDG de Cybersecurity Startup AirGap Networks, a remarqué que de nombreuses attaques qui compromettent les réseaux d'entreprise ne parviennent pas à pénétrer les réseaux de télécommunications et de prestataires de services. «Même s'ils déploient les mêmes routeurs, les mêmes routeurs, les commutateurs, et des pare-feu, il y a quelque chose de fondamentalement différent dans les réseaux de télécommunications qui les protègent de nombreuses menaces pour les Lans d'entreprise », a déclaré Argawal.Agrawal a 20 ans d'expérience avec la cybersécurité, le réseautage d'entreprise et le cloud computing, la plupart du temps passé avec les réseaux de genévriers en se concentrant sur les télécommunications et les grands clients d'entreprise. Pour lire cet article en totalité, veuillez cliquer ici
AI-generating malware, deep fake identity spoofing, and state-sponsored ransomware are just a few of the latest methods that attackers are using to bypass traditional cybersecurity tools. Ritesh Agrawal, CEO of cybersecurity startup Airgap Networks, noticed that many of the attacks that compromise enterprise networks fail to penetrate telco and service provider networks.“Even though they\'re deploying the same routers, switches, and firewalls, there\'s something fundamentally different about telco networks that shields them from many threats to enterprise LANs,” Argawal said. Agrawal has 20 years of experience with cybersecurity, enterprise networking, and cloud computing, most of that time spent with Juniper Networks focusing on telco and large enterprise clients.To read this article in full, please click here |
Ransomware Malware Tool Cloud | ★★ | ||
| 2023-10-18 19:17:43 | Les militants ukrainiens piratent le gang de ransomware Trigona, les serveurs essuyés Ukrainian activists hack Trigona ransomware gang, wipe servers (lien direct) |
Un groupe de cyber-activistes sous la bannière ukrainienne de la cyber-alliance a piraté les serveurs du gang de ransomware Trigona et les a essuyés après avoir copier toutes les informations disponibles.[...]
A group of cyber activists under the Ukrainian Cyber Alliance banner has hacked the servers of the Trigona ransomware gang and wiped them clean after copying all the information available. [...] |
Ransomware Hack | ★★★★ | ||
| 2023-10-18 16:37:41 | Ghostlocker: une nouvelle génération de ransomwares en tant que service (RAAS) GhostLocker: A New Generation of Ransomware as a Service (RaaS) (lien direct) |
Ces derniers temps, nous avons assisté à une forte augmentation des attaques de ransomwares, une tendance déconcertante ...
In recent times, we have witnessed a sharp uptick in ransomware attacks, a disconcerting trend... |
Ransomware | ★★ | ||
| 2023-10-18 15:45:00 | Le groupe pro-ukraine dit qu'il a abattu le site Web de Ransomware Trigona Pro-Ukraine group says it took down Trigona ransomware website (lien direct) |
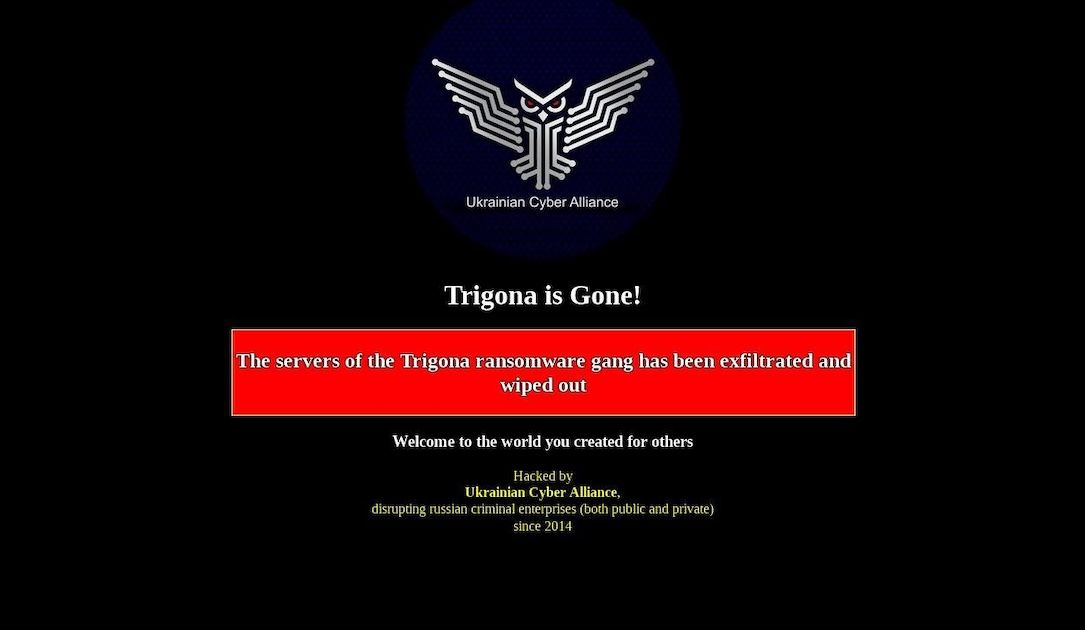 Un groupe de hacktivistes pro-ukraine connus sous le nom de Cyber Alliance ukrainien dit qu'il a fermé le site de fuite géré par le groupe Ransomware Trigona.Selon le porte-parole de l'alliance, qui passe par l'alias en ligne "Herm1t", les hacktivistes ont anéanti 10 des serveurs de Trigona Gang \\, ont défait son site Web et les données exfiltrées
Un groupe de hacktivistes pro-ukraine connus sous le nom de Cyber Alliance ukrainien dit qu'il a fermé le site de fuite géré par le groupe Ransomware Trigona.Selon le porte-parole de l'alliance, qui passe par l'alias en ligne "Herm1t", les hacktivistes ont anéanti 10 des serveurs de Trigona Gang \\, ont défait son site Web et les données exfiltrées
 A group of pro-Ukraine hacktivists known as the Ukrainian Cyber Alliance says it has shut down the leak site run by the Trigona ransomware group. According to the spokesperson for the alliance, who goes by the online alias "herm1t," the hacktivists wiped out 10 of the Trigona gang\'s servers, defaced its website and exfiltrated data
A group of pro-Ukraine hacktivists known as the Ukrainian Cyber Alliance says it has shut down the leak site run by the Trigona ransomware group. According to the spokesperson for the alliance, who goes by the online alias "herm1t," the hacktivists wiped out 10 of the Trigona gang\'s servers, defaced its website and exfiltrated data |
Ransomware | ★★ | ||
| 2023-10-18 12:00:00 | Obtenez le rapport AT & amp; T Cybersecurity Insights Rapport: Focus sur la vente au détail Get the AT&T Cybersecurity Insights Report: Focus on Retail (lien direct) |
We’re pleased to announce the availability of the 2023 AT&T Cybersecurity Insights Report: Focus on Retail. The report examines the edge ecosystem, surveying retail IT leaders from around the world, and provides benchmarks for assessing your edge computing plans. This is the 12th edition of our vendor-neutral and forward-looking report. Last year’s focus on retail report documented how we secure the data, applications, and endpoints that rely on edge computing (get the 2022 report). Get the complimentary 2023 report. The robust quantitative field survey reached 1,418 security, IT, application development, and line of business professionals worldwide. The qualitative research tapped subject matter experts across the cybersecurity industry. Retail-specific respondents equal 201. At the onset of our research, we established the following hypotheses. Momentum edge computing has in the market. Approaches to connecting and securing the edge ecosystem – including the role of trusted advisors to achieve edge goals. Perceived risk and perceived benefit of the common use cases in each industry surveyed. The results focus on common edge use cases in seven vertical industries – healthcare, retail, finance, manufacturing, energy and utilities, transportation, and U.S. SLED- delivering actionable advice for securing and connecting an edge ecosystem, including external trusted advisors. Finally, it examines cybersecurity and the broader edge ecosystem of networking, service providers, and top use cases. The role of IT is shifting, embracing stakeholders at the ideation phase of development. Edge computing is a transformative technology that brings together various stakeholders and aligns their interests to drive integrated business outcomes. The emergence of edge computing has been fueled by a generation of visionaries who grew up in the era of smartphones and limitless possibilities. Look at the infographic below for a topline summary of key findings in the retail industry. In this paradigm, the role of IT has shifted from being the sole leader to a collaborative partner in delivering innovative edge computing solutions. In addition, we found that retail leaders are budgeting differently for edge use cases. These two things, along with an expanded approach to securing edge computing, were prioritized by our respondents in the 2023 AT&T Cybersecurity Insights Report: Edge Ecosystem. One of the most promising aspects of edge computing is its potential to effectively use near-real-time data for tighter control of variable operations such as inventory and supply chain management that deliver improved operational efficiency. Adding new endpoints is essential for collecting the data, but how they’re connected can make them vulnerable to cyberattacks. Successful cyberattacks can disrupt services, highlighting the need for robust cybersecurity measures. Edge computing brings the data closer to where decisions are made. With edge computing, the intelligence required to make decisions, the networks used to capture and transmit data, and the use case management are distributed. Distributed means things work faster because nothing is backhauled to a central processing area such as a data center and delivers the near-real-time experience. With this level of complexity, it’s common to re-evaluate decisions regarding security, data storage, or networking. The report shares emerging trends as retail continues exploring edge computing use cases. One area that’s examined is expense allocation, and what we found may | Ransomware Studies | ★★★ | ||
| 2023-10-18 09:15:08 | Les escrocs malveillants trouvent une mise à jour de fausses navigateurs, au cas où les vrais ne seraient pas assez mauvais Malware crooks find an in with fake browser updates, in case real ones weren\\'t bad enough (lien direct) |
Les chercheurs disent que le ransomware pourrait être à l'horizon si le succès se poursuit Une augmentation des cybercriminels masquant les téléchargements malveillants car de fausses mises à jour du navigateur sont repérées par des chercheurs en sécurité.…
Researchers say ransomware could be on the horizon if success continues An uptick in cybercriminals masking malicious downloads as fake browser updates is being spotted by security researchers.… |
Ransomware Malware | ★★ | ||
| 2023-10-17 20:15:00 | Le gouvernement chilien met en garde contre les attaques de ransomwares noirs de Basta après incident de douane Chilean government warns of Black Basta ransomware attacks after customs incident (lien direct) |
 Le gouvernement du Chili a mis en garde contre les attaques de ransomwares par une gang notoire de pirates après que son service des douanes ait traité mardi un incident.Les responsables du Chili \'s Servicio Nacional de Aduanas de Chili & # 8211;le ministère du gouvernement en charge du commerce extérieur, des importations et plus & # 8211;a déclaré mardi après-midi qu'ils ont pu
Le gouvernement du Chili a mis en garde contre les attaques de ransomwares par une gang notoire de pirates après que son service des douanes ait traité mardi un incident.Les responsables du Chili \'s Servicio Nacional de Aduanas de Chili & # 8211;le ministère du gouvernement en charge du commerce extérieur, des importations et plus & # 8211;a déclaré mardi après-midi qu'ils ont pu
 The government of Chile warned of ransomware attacks by a notorious gang of hackers after its customs department dealt with an incident on Tuesday. Officials from Chile\'s Servicio Nacional de Aduanas de Chile – the government department in charge of foreign trade, imports and more – said on Tuesday afternoon that they were able to
The government of Chile warned of ransomware attacks by a notorious gang of hackers after its customs department dealt with an incident on Tuesday. Officials from Chile\'s Servicio Nacional de Aduanas de Chile – the government department in charge of foreign trade, imports and more – said on Tuesday afternoon that they were able to |
Ransomware | ★★ | ||
| 2023-10-17 18:40:56 | Les cyber-assureurs notent que les revendications de ransomware ont augmenté de manière significative au premier semestre de 2023 Cyber Insurers Notes Ransomware Claims Rose Significantly in the First Half of 2023 (lien direct) |

|
Ransomware | ★★ | ||
| 2023-10-17 13:30:00 | Géant des ventes de publicité télévisée affectée par l'attaque des ransomwares TV advertising sales giant affected by ransomware attack (lien direct) |
 Une entreprise de vente et de technologie de publicité télévisée appartenant aux trois plus grands opérateurs de câblodistribution américaine a été frappée par une attaque de ransomware ces dernières semaines qui a affecté les opérations.AmperSand - appartenant à Comcast Corporation, Charter Communications et Cox Communications - fournit des données d'audience aux annonceurs d'environ 85 millions de ménages et existe depuis 1981.
Une entreprise de vente et de technologie de publicité télévisée appartenant aux trois plus grands opérateurs de câblodistribution américaine a été frappée par une attaque de ransomware ces dernières semaines qui a affecté les opérations.AmperSand - appartenant à Comcast Corporation, Charter Communications et Cox Communications - fournit des données d'audience aux annonceurs d'environ 85 millions de ménages et existe depuis 1981.
 A television advertising sales and technology company joinly owned by the three largest U.S. cable operators was hit with a ransomware attack in recent weeks that affected operations. Ampersand - owned by Comcast Corporation, Charter Communications and Cox Communications - provides viewership data to advertisers about 85 million households and has existed since 1981. Last
A television advertising sales and technology company joinly owned by the three largest U.S. cable operators was hit with a ransomware attack in recent weeks that affected operations. Ampersand - owned by Comcast Corporation, Charter Communications and Cox Communications - provides viewership data to advertisers about 85 million households and has existed since 1981. Last |
Ransomware | ★★ | ||
| 2023-10-16 15:30:00 | Ransomware cible les serveurs WS_FTP non corrigés Ransomware Targets Unpatched WS_FTP Servers (lien direct) |
Les acteurs de la menace ont tenté d'escalader les privilèges en utilisant l'outil open source Godpotato
The threat actors attempted to escalate privileges using the open-source GodPotato tool |
Ransomware Tool Threat | ★★ | ||
| 2023-10-16 14:04:05 | 16 octobre & # 8211;Rapport de renseignement sur les menaces 16th October – Threat Intelligence Report (lien direct) |
> Pour les dernières découvertes de cyber-recherche pour la semaine du 9 octobre, veuillez télécharger notre bulletin Threat_Intelligence.Les meilleurs attaques et violations Gang de ransomware de verrouillage ont revendiqué la responsabilité d'une prétendue attaque contre le revendeur de produits et services informatiques de plusieurs milliards de dollars CDW.Le gang a demandé une rançon de 80 millions de dollars et a menacé de publier des données volées, censées [& # 8230;]
>For the latest discoveries in cyber research for the week of 9th October, please download our Threat_Intelligence Bulletin. TOP ATTACKS AND BREACHES LockBit ransomware gang has claimed responsibility for an alleged attack on the multibillion-dollar IT products and services reseller CDW. The gang has demanded $80M ransom and threatened to release stolen data, said to […] |
Ransomware Threat | ★★ | ||
| 2023-10-16 11:30:00 | Le secteur des soins de santé a mis en garde contre le nouveau groupe de ransomwares Noescape Healthcare Sector Warned About New Ransomware Group NoEscape (lien direct) |
Le gouvernement américain a souligné les opérations du groupe Noescape, qui serait un changement de marque de l'acteur de menace russe Avaddon
The US government highlighted the operations of the NoEscape group, which is believed to be a rebrand of Russian threat actor Avaddon |
Ransomware Threat Medical | ★★ | ||
| 2023-10-16 07:29:59 | Navigation du cyber-risque: ce qu'il faut rechercher dans la couverture de la cyber-assurance Navigating Cyber Risk: What to Look for in Cyber Insurance Coverage (lien direct) |
Modern threats like phishing, ransomware and data breaches cast a dark cloud over businesses across sectors. For most bad actors, the goal of an attack is financial. As Proofpoint noted in the 2023 State of the Phish report, 30% of businesses that endured a successful attack experienced a direct monetary loss, such as a fraudulent invoice, wire transfer or payroll redirection. That is an increase of 76% year over year. A cyber insurance policy can protect you from the financial losses caused by cybersecurity incidents and data breaches. And when businesses pair cyber insurance with the prowess of Proofpoint solutions, they can build a formidable defense strategy. In this blog, we\'ll go over some best practices for choosing and managing you cyber insurance policy so you can protect yourself from risk. Actions that cyber criminals monetize Our research for the latest State of the Phish report shows that the three most common consequences of a cyber attack are: Data breach (44%) Ransomware infection (43%) Account compromise (36%) Notably, cyber criminals can monetize all these actions. Most common results of successful phishing attacks. (Source: 2023 State of the Phish report from Proofpoint.) Just one cybersecurity incident can cost tens of thousands of dollars. So, it\'s easy to understand why insurers see these incidents as too costly to cover in their general liability policies. But with cyber insurance, your business has a tool to help manage risk. Why cyber insurance can be a vital financial safety net While firewalls and endpoint protections remain vital, the truth is that a level of residual risk always exists. No matter how fortified your security is, breaches can happen due to ingenious adversaries, human error or just unfortunate circumstances. This is where cyber insurance comes to the rescue. It is the safety net that catches your business when your defenses fall short. It can help you cover costs like ransomware payments, legal fees, and costs associated with crisis management and revenue loss. In the graphic below, we can see how often cyber insurance covered losses from ransomware attacks among those surveyed for our 2023 State of the Phish report. Nearly three-quarters (73%) of businesses with cyber insurance policies said their insurers paid at least some of their ransomware-related losses. (Source: 2023 State of the Phish report from Proofpoint.) Cyber insurance best practices Now that we\'ve covered why cyber insurance can be a vital financial safety net, let\'s look at some essential best practices for cyber insurance. These measures can help your business become more effective at managing cybersecurity risks. Find an expert and ask for support and guidance. Specialized brokers are your allies in the intricate world of cyber insurance. Insurers vary in risk appetite, claim acceptance rates and expertise. Brokers have an in-depth grasp of this landscape, and they will assess your options meticulously. They will help ensure that the policy you choose is the right fit for your industry, size, risk profile and more. Be prepared for a rigorous assessment. Today, insurers want more insight into your company\'s security protocols and controls before they issue a cyber insurance policy. So preparedness is key. Be ready to provide evidence, like external audits, penetration test results and compliance certifications to insurers. If you implement access controls that insurers deem vital, such as multifactor authentication (MFA) and privileged access management (PAM), it may help to reduce your premiums. Closely examine coverage scope. Coverage specifics vary globally. But you will find that most cyber insurance policies cover a portion of losses from ransomware attacks and expenses linked to crisis responses. You need to have a thorough understanding of the breach scenarios your policy does or does not cover. Take note of any exclusions. Also, be sure to scrutinize services like breach investigation support, legal | Ransomware Tool Threat Guideline Cloud | ★★★ | ||
| 2023-10-16 04:00:00 | Les tribunaux du Kansas ont fermé, les systèmes électroniques ont baissé après une prétendue attaque de ransomware Kansas courts closed, electronic systems down after alleged ransomware attack (lien direct) |
 Les tribunaux du Kansas sont confrontés à une variété de problèmes à la suite d'une prétendue attaque de ransomware la semaine dernière.La ville de Topeka a annoncé dimanche que ses divisions de la Cour municipale et de sa probation et de ses poursuites seront fermées au public lundi, tandis que la Cour suprême du Kansas utilise exclusivement des dossiers papier pour opérer.Juge Philip Journey, de
Les tribunaux du Kansas sont confrontés à une variété de problèmes à la suite d'une prétendue attaque de ransomware la semaine dernière.La ville de Topeka a annoncé dimanche que ses divisions de la Cour municipale et de sa probation et de ses poursuites seront fermées au public lundi, tandis que la Cour suprême du Kansas utilise exclusivement des dossiers papier pour opérer.Juge Philip Journey, de
 Courts across Kansas are facing a variety of issues following an alleged ransomware attack last week. The city of Topeka announced Sunday that its municipal court and probation and prosecution divisions will be closed to the public on Monday, while the Kansas Supreme Court is exclusively using paper records to operate. Judge Philip Journey, of
Courts across Kansas are facing a variety of issues following an alleged ransomware attack last week. The city of Topeka announced Sunday that its municipal court and probation and prosecution divisions will be closed to the public on Monday, while the Kansas Supreme Court is exclusively using paper records to operate. Judge Philip Journey, of |
Ransomware | ★★★ | ||
| 2023-10-16 02:58:14 | Le régulateur, les assureurs et les clients viennent tous pour les progrès après la violation de Moveit Regulator, insurers and customers all coming for Progress after MOVEit breach (lien direct) |
De plus, CISA catalogage de nouveaux points de données de ransomware, des sites WP 17K détournés par malware en septembre, et des vulns plus critiques infosec en bref les retombées de l'exploitation des boguesIn Progress Software \'s Moveit File Transfer Software se poursuit, la Commission américaine des Securities and Exchange (SEC) enquête désormais sur l'affaire et de nombreuses parties touchées à la rémunération.…
Also, CISA cataloging new ransomware data points, 17k WP sites hijacked by malware in Sept., and more critical vulns Infosec in brief The fallout from the exploitation of bugs in Progress Software\'s MOVEit file transfer software continues, with the US Securities and Exchange Commission (SEC) now investigating the matter, and lots of affected parties seeking compensation. … |
Ransomware Malware | ★★★ | ||
| 2023-10-15 21:45:00 | Colonial Pipeline attribue les prétentions des ransomwares à \\ 'non liée à la violation de données tierces Colonial Pipeline attributes ransomware claims to \\'unrelated\\' third-party data breach (lien direct) |
 Colonial Pipeline a déclaré qu'il n'y avait pas eu de perturbation des opérations de pipeline ou de leurs systèmes après qu'un gang de ransomware a fait plusieurs menaces vendredi après-midi.La société & # 8211;qui gère le plus grand système de pipeline pour les produits à l'huile raffinés aux États-Unis & # 8211;adressé les affirmations faites par le gang rancéd.vc que les données avaient été volées à leur
Colonial Pipeline a déclaré qu'il n'y avait pas eu de perturbation des opérations de pipeline ou de leurs systèmes après qu'un gang de ransomware a fait plusieurs menaces vendredi après-midi.La société & # 8211;qui gère le plus grand système de pipeline pour les produits à l'huile raffinés aux États-Unis & # 8211;adressé les affirmations faites par le gang rancéd.vc que les données avaient été volées à leur
 Colonial Pipeline said there has been no disruption to pipeline operations or their systems after a ransomware gang made several threats on Friday afternoon. The company – which runs the largest pipeline system for refined oil products in the U.S. – addressed claims made by the Ransomed.vc gang that data had been stolen from their
Colonial Pipeline said there has been no disruption to pipeline operations or their systems after a ransomware gang made several threats on Friday afternoon. The company – which runs the largest pipeline system for refined oil products in the U.S. – addressed claims made by the Ransomed.vc gang that data had been stolen from their |
Ransomware Data Breach | ★★★ | ||
| 2023-10-14 01:43:36 | Colonial Pipeline nie la violation de RansomEdVC Ransomware Group Colonial Pipeline Denies Breach by RANSOMEDVC Ransomware Group (lien direct) |
> Par waqas
violation de données tierce suspectée dans les fichiers en ligne liés au pipeline colonial.
Ceci est un article de HackRead.com Lire le post original: pipeline colonialRefuse la violation de Ransomedvc Ransomware Group
>By Waqas Third-Party Data Breach Suspected in Online Files Linked to Colonial Pipeline. This is a post from HackRead.com Read the original post: Colonial Pipeline Denies Breach by RANSOMEDVC Ransomware Group |
Ransomware Data Breach | ★★ | ||
| 2023-10-13 20:25:58 | Feds: Méfiez-vous des attaques du ransomware Avoslocker contre l'infrastructure critique Feds: Beware AvosLocker Ransomware Attacks on Critical Infrastructure (lien direct) |
La CISA et le FBI avertissent que les affiliés du fournisseur RAAS frappaient des industries critiques, avec plus d'attaques qui devraient provenir de groupes de ransomware supplémentaires dans les mois à venir.
CISA and FBI warn the RaaS provider\'s affiliates are striking critical industries, with more attacks expected to come from additional ransomware groups in the months ahead. |
Ransomware | ★★ | ||
| 2023-10-13 18:26:21 | La semaine en ransomware - 13 octobre 2023 - Attaques croissantes The Week in Ransomware - October 13th 2023 - Increasing Attacks (lien direct) |
Les gangs de ransomware continuent de caresser l'entreprise, les attaques causant une perturbation dans les opérations commerciales et entraînant des violations de données si une rançon n'est pas payée.[...]
Ransomware gangs continue to pummel the enterprise, with attacks causing disruption in business operations and resulting in data breaches if a ransom is not paid. [...] |
Ransomware | ★★ | ||
| 2023-10-13 16:37:00 | Les attaques de ransomware ont doublé d'année en année.Les organisations sont-elles équipées pour gérer l'évolution des ransomwares en 2023? Ransomware attacks doubled year on year. Are organizations equipped to handle the evolution of Ransomware in 2023? (lien direct) |
Les attaques de ransomwares n'ont augmenté que dans la sophistication et les capacités au cours de la dernière année.Des nouvelles techniques d'évasion et d'anti-analyse aux variantes furtives codées dans de nouvelles langues, les groupes de ransomwares ont adapté leurs tactiques pour contourner efficacement les stratégies de défense communes.
Cet article couvrira uniquement ces nouveaux développements au troisième trimestre et donnera des prédictions sur les trimestres
Ransomware attacks have only increased in sophistication and capabilities over the past year. From new evasion and anti-analysis techniques to stealthier variants coded in new languages, ransomware groups have adapted their tactics to bypass common defense strategies effectively. This article will cover just some of those new developments in Q3-2023 as well as give predictions on quarters to |
Ransomware | ★★★ | ||
| 2023-10-13 15:55:00 | FBI, CISA met en garde contre l'augmentation des attaques de ransomware Avoslocker contre l'infrastructure critique FBI, CISA Warn of Rising AvosLocker Ransomware Attacks Against Critical Infrastructure (lien direct) |
Le gang de ransomware Avoslocker a été lié à des attaques contre les secteurs critiques des infrastructures aux États-Unis, certains d'entre eux ont été détectés aussi récemment que mai 2023.
Selon un nouveau conseil conjoint de cybersécurité publié par l'Agence américaine de sécurité de la cybersécurité et de l'infrastructure (CISA) et le Federal Bureau of Investigation (FBI) détaillant le Ransomware-as-a-Service (RAAS) Operation \'s \'s
The AvosLocker ransomware gang has been linked to attacks against critical infrastructure sectors in the U.S., with some of them detected as recently as May 2023. That\'s according to a new joint cybersecurity advisory released by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) detailing the ransomware-as-a-service (RaaS) operation\'s |
Ransomware | ★★ | ||
| 2023-10-13 15:00:00 | CDW enquête sur les allégations de gangs de ransomware de vol de données CDW investigating ransomware gang claims of data theft (lien direct) |
 La société de services technologiques de plusieurs milliards de dollars CDW a déclaré qu'elle enquêtait sur les réclamations faites par un gang de ransomware que des données avaient été volées lors d'une cyberattaque.Un porte-parole de la société & # 8211;qui a déclaré que les revenus de plus de 23 milliards de dollars en 2022 & # 8211;a déclaré qu'ils «abordent actuellement une question de sécurité informatique isolée associée aux données sur quelques serveurs
La société de services technologiques de plusieurs milliards de dollars CDW a déclaré qu'elle enquêtait sur les réclamations faites par un gang de ransomware que des données avaient été volées lors d'une cyberattaque.Un porte-parole de la société & # 8211;qui a déclaré que les revenus de plus de 23 milliards de dollars en 2022 & # 8211;a déclaré qu'ils «abordent actuellement une question de sécurité informatique isolée associée aux données sur quelques serveurs
 The multibillion-dollar technology services firm CDW said it is investigating claims made by a ransomware gang that data was stolen during a cyberattack. A spokesperson for the company – which reported revenues over $23 billion in 2022 – said they are currently “addressing an isolated IT security matter associated with data on a few servers
The multibillion-dollar technology services firm CDW said it is investigating claims made by a ransomware gang that data was stolen during a cyberattack. A spokesperson for the company – which reported revenues over $23 billion in 2022 – said they are currently “addressing an isolated IT security matter associated with data on a few servers |
Ransomware | ★★ | ||
| 2023-10-13 13:45:00 | La CISA prévoit de partager plus d'informations sur les acteurs du ransomware dans ses alertes de vulnérabilité exploitées CISA plans to share more information on ransomware actors in its exploited vulnerability alerts (lien direct) |
 La principale agence de cybersécurité des États-Unis a déclaré qu'elle prévoyait d'ajouter une section dédiée aux gangs de ransomware à sa liste de vulnérabilités exploitées par des pirates.Les responsables de la Cybersecurity and Infrastructure Security Agency (CISA) ont déclaré jeudi que toutes les organisations auront désormais accès à des informations sur les vulnérabilités généralement associées aux attaques de ransomware via son
La principale agence de cybersécurité des États-Unis a déclaré qu'elle prévoyait d'ajouter une section dédiée aux gangs de ransomware à sa liste de vulnérabilités exploitées par des pirates.Les responsables de la Cybersecurity and Infrastructure Security Agency (CISA) ont déclaré jeudi que toutes les organisations auront désormais accès à des informations sur les vulnérabilités généralement associées aux attaques de ransomware via son
 The U.S.\'s top cybersecurity agency said it plans to add a section dedicated to ransomware gangs to its list of vulnerabilities being exploited by hackers. Cybersecurity and Infrastructure Security Agency (CISA) officials said on Thursday that all organizations will now have access to information about which vulnerabilities are commonly associated with ransomware attacks through its
The U.S.\'s top cybersecurity agency said it plans to add a section dedicated to ransomware gangs to its list of vulnerabilities being exploited by hackers. Cybersecurity and Infrastructure Security Agency (CISA) officials said on Thursday that all organizations will now have access to information about which vulnerabilities are commonly associated with ransomware attacks through its |
Ransomware Vulnerability | ★★★ | ||
| 2023-10-13 13:33:20 | La CISA lance de nouvelles ressources pour lutter contre les vulnérabilités et les faiblesses exploitées par des groupes de ransomwares CISA Launches New Resources to Help Combat Vulnerabilities and Weaknesses Exploited by Ransomware Groups (lien direct) |
Dans le paysage en constante évolution de la cybersécurité, l'importance de rester en avance sur les menaces ne peut être ...
In the ever-evolving landscape of cybersecurity, the importance of staying ahead of threats cannot be... |
Ransomware Vulnerability | ★★★ | ||
| 2023-10-13 13:00:47 | Tendance du ransomware la plus récente: les attaquants se déplacent plus rapidement avec un chiffrement partiel Newest Ransomware Trend: Attackers Move Faster with Partial Encryption (lien direct) |
> Le mercredi matin 3 mai 2023, le personnel de sécurité avec la ville de Dallas a été horrifié lorsque leur logiciel de sécurité les a alertés qu'ils étaient probablement devenus la cible d'une attaque de ransomware.Plusieurs serveurs dans une gamme de départements ont été touchés: les répartiteurs du 911, les tribunaux et les services de police ne pouvaient pas utiliser leurs ordinateurs pendant des jours.Il est apparu plus tard que des données sensibles avaient été volées [1] -800 000 dossiers contenant des noms complets, des adresses domestiques, des numéros de sécurité sociale, des dates de naissance et les données de santé et d'assurance d'au moins 30 000 employés de la ville et d'autres personnes.Deux semaines plus tard, le Royal Ransomware Group, qui a pris la responsabilité de [& # 8230;]
>On Wednesday morning, May 3, 2023, security personnel with the City of Dallas were horrified when their security software alerted them that they had likely become the target of a ransomware attack. Multiple servers across a range of departments were affected: 911 dispatchers, courts, and police services couldn\'t use their computers for days. It later emerged that sensitive data had been stolen[1]-800,000 files containing full names, home addresses, Social Security numbers, dates of birth, and the health and insurance data of at least 30,000 city employees and other individuals. Two weeks later, the Royal ransomware group, which took responsibility for […] |
Ransomware | ★★ | ||
| 2023-10-13 00:00:00 | Le vide Rabisu cible les dirigeants politiques féminines avec une nouvelle variante ROMCOM maximale Void Rabisu Targets Female Political Leaders with New Slimmed-Down ROMCOM Variant (lien direct) |
Près d'un an après que le vide Rabisu a déplacé son ciblage des attaques de ransomwares opportunistes en mettant l'accent sur le cyberespionnage, l'acteur de menace développe toujours son malware principal, la porte dérobée ROMCOM.
Almost a year after Void Rabisu shifted its targeting from opportunistic ransomware attacks with an emphasis on cyberespionage, the threat actor is still developing its main malware, the ROMCOM backdoor. |
Ransomware Threat | ★★ | ||
| 2023-10-12 16:39:44 | SEC enquêter sur les logiciels de progrès sur Moveit Hack SEC Investigating Progress Software Over MOVEit Hack (lien direct) |
> Progress Software confirme que la SEC a lancé sa propre enquête sur le ransomware coûteux zéro-jours dans le logiciel de transfert de fichiers Moveit.
>Progress Software confirms the SEC has launched its own investigation into costly ransomware zero-days in the MOVEit file transfer software. |
Ransomware Hack | ★★ | ||
| 2023-10-12 15:59:00 | Microsoft Defender contrecarte à grande échelle Akira Ransomware Attack Microsoft Defender Thwarts Large-Scale Akira Ransomware Attack (lien direct) |
Microsoft a déclaré mercredi qu'une fonctionnalité de confinement des utilisateurs dans Microsoft Defender pour Endpoint a aidé à contrecarrer une "tentative de cryptage à grande échelle" effectuée par des acteurs de ransomware Akira ciblant une organisation industrielle inconnue début juin 2023.
L'équipe de renseignement sur les menaces du géant de la technologie suit l'opérateur en tant que Storm-1567.
Les dispositifs à levier d'attaque qui n'étaient pas à bord à Microsoft
Microsoft on Wednesday said that a user containment feature in Microsoft Defender for Endpoint helped thwart a "large-scale remote encryption attempt" made by Akira ransomware actors targeting an unknown industrial organization in early June 2023. The tech giant\'s threat intelligence team is tracking the operator as Storm-1567. The attack leveraged devices that were not onboarded to Microsoft |
Ransomware Threat Industrial | ★★★ | ||
| 2023-10-12 15:00:00 | Ransomware Roundup - Akira (lien direct) | Akira est un ransomware multi-OS relativement nouveau qui crypte et exfiltre les fichiers et les fichiers victimes et exigent une rançon pour le décryptage des fichiers.Apprendre encore plus.
Akira is a relatively new multi-OS ransomware that encrypts and exfiltrates victims\' files and demands ransom for file decryption. Learn more. |
Ransomware | ★★ | ||
| 2023-10-12 12:02:06 | Les attaques des ransomwares «exploitées par l'homme» sont doubles au cours de la dernière année “Human-Operated” Ransomware Attacks Double in the Last Year (lien direct) |

|
Ransomware | ★★ | ||
| 2023-10-12 10:00:00 | L'évolution des attaques de phishing The evolution of phishing attacks (lien direct) |
A practical guide to phishing and best practices to avoid falling victim. Introduction Over the past several years, remote and hybrid work has quickly gained popularity amongst those seeking a to reduce the amount of time on the road or an improved work/life balance. To accomplish this, users are often working from multiple devices, some of which may be company issued, but others may be privately owned. Cyberattackers have leveraged this trend to bypass traditional security controls using social engineering, with phishing attacks being a favored tactic. In fact, the FBI Internet Crime Report issued in 2022 reported phishing as the top reported internet crime for the past 5 years. Its ability to persuade individuals to divulge sensitive information to seemingly familiar contacts and companies over email and/or SMS text messages has resulted in significant data breaches, both personal and financial, across all industries. Mobile phishing, in particular, is quickly becoming a preferred attack vector among hackers seeking to use them as a jump point to gain access to proprietary data within a company’s network. This article provides an overview of the origins of phishing, its impact on businesses, the types of mobile phishing attacks hackers employ, and ways in which companies can best defend themselves against such attacks. The origins of phishing The belief among many in the cybersecurity industry is that phishing attacks first emerged in the mid-90s when dial-up was the only means of gaining access to the internet. Hackers posing as ISP administrators used fake screen names to establish credibility with the user, enabling them to “phish” for personal log-in data. Once successful, they were able to exploit the victim’s account by sending out phishing emails to other users in their contact list, with the goal of scoring free internet access or other financial gain. Awareness of phishing was still limited until May 2000 when Love Bug entered the picture. Love Bug, a highly effective and contagious virus designed to take advantage of the user’s psyche was unleashed in the Philippines, impacting an estimated 45 million Window PCs globally. Love Bug was sent via email with the subject line reading “ILOVEYOU”. The body of the message simply read “Kindly check the attached LOVELETTER coming from me”. Users who couldn’t resist opening the message unleashed a worm virus infecting and overwriting user’s files with copies of the virus. When the user opened the file, they would reinfect the system. Lovebug elevated phishing to a new level as it demonstrated the ability to target a user’s email mailing list for the purpose of spamming acquaintances thereby incentivizing the reader to open his/her email. This enabled the lovebug worm to infect computer systems and steal other user’s passwords providing the hacker the opportunity to log-in to other user accounts providing unlimited internet access. Since Love Bug, the basic concept and primary goal of phishing tactics has remained consistent, but the tactics and vectors have evolved. The window of opportunity has increased significantly for hackers with the increased use of social media (e.g., Linkedin, Twitter, Facebook). This provides more personal data to the hackers enabling them to exploit their targets with more sophisticated phishing tactics while avoiding detection. Phishing’s impact in the marketplace today Phishing attacks present a significant threat for organizations as their ability to capture proprietary business and financial data are both costly and time consuming for IT organizations to detect and remediate. Based on a | Ransomware Malware Tool Threat Prediction | ★★★ | ||
| 2023-10-12 09:27:20 | J'ai été frappé par les ransomwares-temps quoi?Étapes pour gérer les conséquences I\\'ve Been Hit by Ransomware-Now What? Steps for Dealing with the Aftermath (lien direct) |
The following is an excerpt from the Ransomware Survival Guide, our free handbook on preventing, managing and recovering from ransomware threats at every stage of the attack chain. This blog post provides general tips-it is not a substitute for professional cybersecurity and incident response services. The best ransomware strategy is to avoid it in the first place. But increasingly advanced attacks against the software supply chain and end users have shown that even the best-prepared companies can be caught out. Ransomware may not even be the first malware payload to infect your system, because many ransomware gangs now prefer to buy access to targets already infected with Trojans or loader malware. During an attack, you have short-term problems to resolve, like getting computers, phones and networks back online and dealing with ransom demands. But a panicked response won\'t help-and may make things worse. Here are some general steps you can take to contain the threat and start on the road to recovery. Questions to answer during a ransomware attack Before you react to an attack, it\'s important to take a step back and ask questions that will inform your response. Your answers should help network administrators scope the problem, devise an action plan and possibly curtail the spread. Who in your environment is compromised? How widespread are the infections? Is a threat actor actively scouting your environment, exfiltrating data or ready to drop ransomware on other devices? What network permissions do compromised accounts or devices have? Ransomware may have been installed only after attackers had already moved laterally within the network or stolen credentials and other data. What type of attack is it? Is this attack a secondary infection? Did it come from downloaders, remote access Trojans (RATs) or other malware installed on the infected machine or others on the network? Keep in mind that ransomware spreads quickly and is often a byproduct of other threats. If you see one infection, there are probably others that you don\'t see. Proactively look for other issues within your environment. Now as you take action, there are three general step to follow: Step 1: Isolate infected systems The second employees see the ransomware demand or notice something\'s odd-such as suddenly losing access to their own files-they should disconnect from the network and take the infected machine to the IT department. To prepare for this scenario, we recommend that you keep valuable data and systems separated so that a security issue on one system doesn\'t affect other systems. For example, your sensitive research or business data should not reside on the same server and network segment as your email environment. We advise against having employees reboot their system. Only the IT security team should attempt a reboot, and even that will work only in the event that it is “scareware,” or fake ransomware. "Scareware" is malware that appears to be ransomware but isn\'t. It may lock the user\'s screen with a ransom demand and payment instructions, but the data is not actually encrypted. In those scenarios, standard anti-malware tools can help. Knowing the difference isn\'t always easy. Determine the scope of the problem using threat intelligence and external incident responders or forensic analysts when necessary. While all ransomware is bad, some attacks are worse than others. Your response-including whether to pay the ransom-hinges on several factors. Step 2: Call law enforcement Ransomware-like other forms of theft and extortion-is a crime. Nobody has the right to seize devices, networks or data-let alone demand a ransom in exchange for it. Notifying the proper authorities is a necessary first step. Contact local or federal law enforcement right away. Special departments exist specifically to aid cyber crime victims, so do not be afraid to pick up your phone and call them. They are there to help you and may have access to decryption keys or information on payment recovery after | Ransomware Malware Tool Threat | ★★★ |
To see everything:
Our RSS (filtrered)
