What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-11-08 19:27:00 | WhatsApp présente une nouvelle fonctionnalité de confidentialité pour protéger l'adresse IP dans les appels WhatsApp Introduces New Privacy Feature to Protect IP Address in Calls (lien direct) |
WhatsApp méta-constitué déploie officiellement une nouvelle fonctionnalité de confidentialité dans son service de messagerie appelé "Protect Adresse IP dans les appels" qui masque les utilisateurs \\ 'IP d'adresses à d'autres parties en relayant les appels via ses serveurs.
"Les appels sont cryptés de bout en bout, donc même si un appel est relayé via des serveurs WhatsApp, WhatsApp ne peut pas écouter vos appels", a déclaré la société dans un communiqué partagé avec le
Meta-owned WhatsApp is officially rolling out a new privacy feature in its messaging service called "Protect IP Address in Calls" that masks users\' IP addresses to other parties by relaying the calls through its servers. "Calls are end-to-end encrypted, so even if a call is relayed through WhatsApp servers, WhatsApp cannot listen to your calls," the company said in a statement shared with The |
Tool | ★★★ | ||
| 2023-11-08 18:59:39 | Predator AI | ChatGPT-Powered Infostealer Takes Aim at Cloud Platforms (lien direct) | #### Description
Sentinellabs a identifié un nouvel infosteller basé sur Python et hacktool appelé \\ 'Predator Ai \' conçu pour cibler les services cloud.
Predator AI est annoncé via des canaux télégrammes liés au piratage.L'objectif principal de Predator est de faciliter les attaques d'applications Web contre diverses technologies couramment utilisées, y compris les systèmes de gestion de contenu (CMS) comme WordPress, ainsi que les services de messagerie cloud comme AWS SES.Cependant, Predator est un outil polyvalent, un peu comme les outils de spam de cloud Alienfox et Legion.Ces ensembles d'outils partagent un chevauchement considérable dans le code accessible au public qui réutilise chaque utilisation de leur marque, y compris l'utilisation des modules AndroxGH0st et Greenbot.
Le développeur AI Predator a implémenté une classe axée sur le chatppt dans le script Python, qui est conçue pour rendre l'outil plus facile à utiliser et pour servir d'interface de texte unique entre les fonctionnalités disparates.Il y avait plusieurs projets comme Blackmamba qui étaient finalement plus hype que l'outil ne pouvait livrer.L'IA prédateur est un petit pas en avant dans cet espace: l'acteur travaille activement à la fabrication d'un outil qui peut utiliser l'IA.
#### URL de référence (s)
1. https://www.sentinelone.com/labs/predator-ai-chatgpt-powered-infostealer-takes-aim-at-cloud-platforms/
#### Date de publication
7 novembre 2023
#### Auteurs)
Alex Delamotte
#### Description SentinelLabs has identified a new Python-based infostealer and hacktool called \'Predator AI\' that is designed to target cloud services. Predator AI is advertised through Telegram channels related to hacking. The main purpose of Predator is to facilitate web application attacks against various commonly used technologies, including content management systems (CMS) like WordPress, as well as cloud email services like AWS SES. However, Predator is a multi-purpose tool, much like the AlienFox and Legion cloud spamming toolsets. These toolsets share considerable overlap in publicly available code that each repurposes for their brand\'s own use, including the use of Androxgh0st and Greenbot modules. The Predator AI developer implemented a ChatGPT-driven class into the Python script, which is designed to make the tool easier to use and to serve as a single text-driven interface between disparate features. There were several projects like BlackMamba that ultimately were more hype than the tool could deliver. Predator AI is a small step forward in this space: the actor is actively working on making a tool that can utilize AI. #### Reference URL(s) 1. https://www.sentinelone.com/labs/predator-ai-chatgpt-powered-infostealer-takes-aim-at-cloud-platforms/ #### Publication Date November 7, 2023 #### Author(s) Alex Delamotte |
Tool Cloud | ChatGPT | ★★ | |
| 2023-11-08 18:27:00 | Méfiez-vous, développeurs: logiciels malveillants BlazesEaler découverts dans Python Packages sur PYPI Beware, Developers: BlazeStealer Malware Discovered in Python Packages on PyPI (lien direct) |
Un nouvel ensemble de packages Python malveillants a glissé son chemin vers le référentiel Python Package Index (PYPI) dans le but ultime de voler des informations sensibles à des systèmes de développeurs compromis.
Les forfaits se masquent comme des outils d'obscurcissement apparemment inoffensifs, mais abritent un logiciel malveillant appelé BlazesEaler, a déclaré Checkmarx dans un rapport partagé avec le Hacker News.
"[BLAZESTEALER]
A new set of malicious Python packages has slithered their way to the Python Package Index (PyPI) repository with the ultimate aim of stealing sensitive information from compromised developer systems. The packages masquerade as seemingly innocuous obfuscation tools, but harbor a piece of malware called BlazeStealer, Checkmarx said in a report shared with The Hacker News. "[BlazeStealer] |
Malware Tool | ★★ | ||
| 2023-11-08 16:30:00 | Guide: comment VCISOS, MSPS et MSSP peuvent protéger leurs clients des risques Gen AI Guide: How vCISOs, MSPs and MSSPs Can Keep their Customers Safe from Gen AI Risks (lien direct) |
Téléchargez le guide gratuit, "C'est un monde d'IA génératif: comment VCISO, MSPS et MSSPS peuvent protéger leurs clients des risques Gen Gen AI."
Chatgpt se vante désormais de 1,5 à 2 milliards de visites par mois.D'innombrables ventes, marketing, RH, exécutif informatique, soutien technique, opérations, finances et autres fonctions alimentent les invites de données et les requêtes dans les moteurs d'IA génératifs.Ils utilisent ces outils pour écrire
Download the free guide, "It\'s a Generative AI World: How vCISOs, MSPs and MSSPs Can Keep their Customers Safe from Gen AI Risks." ChatGPT now boasts anywhere from 1.5 to 2 billion visits per month. Countless sales, marketing, HR, IT executive, technical support, operations, finance and other functions are feeding data prompts and queries into generative AI engines. They use these tools to write |
Tool Technical | ChatGPT | ★★ | |
| 2023-11-08 11:44:35 | FBI: Ransomware Gangs Hack Casinos via des vendeurs de jeux tiers FBI: Ransomware gangs hack casinos via 3rd party gaming vendors (lien direct) |
Le Federal Bureau of Investigation avertit que les acteurs des menaces de ransomware ciblent les serveurs de casino et utilisent des outils de gestion des systèmes légitimes pour augmenter leurs autorisations sur le réseau.[...]
The Federal Bureau of Investigation is warning that ransomware threat actors are targeting casino servers and use legitimate system management tools to increase their permissions on the network. [...] |
Ransomware Hack Tool Threat | ★★★ | ||
| 2023-11-08 11:00:00 | Atténuer les menaces profondes dans le monde de l'entreprise: une approche médico-légale Mitigating deepfake threats in the corporate world: A forensic approach (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. In an era where technology advances at breakneck speed, the corporate world finds itself facing an evolving and insidious threat: deepfakes. These synthetic media creations, powered by artificial intelligence (AI) algorithms, can convincingly manipulate audio, video, and even text - posing significant risks to businesses, their reputation, and their security. To safeguard against this emerging menace, a forensic approach is essential. Understanding deepfakes “Deepfake” is a term used to describe a type of synthetic media that is created or manipulated using artificial intelligence (AI) and deep learning algorithms. The term "deepfake" is a combination of "deep learning" and "fake." Deep learning is a subset of machine learning that involves training artificial neural networks to perform specific tasks, such as image or speech recognition. Deepfake technology is primarily associated with the manipulation of audio and video content, although it can also be applied to text. It allows for the creation of highly convincing and often indistinguishable fake content by superimposing one person\'s likeness and voice onto another person\'s image or video. Deepfake technology has been used in various real-world scenarios, raising concerns about its potential for misinformation and deception. For instance, a deepfake video of former President Barack Obama was manipulated to make it seem like he was delivering a speech using synthetic audio and video. In the entertainment industry, deepfake technology has been used to recreate deceased actors for film or commercial purposes. For example, a deepfake version of actor James Dean was used in a Vietnamese commercial. Deepfake content has been circulated on social media and news platforms, contributing to the spread of fake news and disinformation. This can include fabricated speeches, interviews, or events involving public figures. Deepfake technology has been exploited to create explicit content featuring individuals without their consent. This content is often used for harassment, revenge, or extortion. These examples illustrate the versatility of deepfake technology and the potential risks associated with its misuse. As a result, there is growing concern about the need for effective detection and countermeasures to address the potential negative consequences of deepfake manipulation in various contexts. Here are some key aspects of deepfake technology: Face swapping: Deepfake algorithms can replace the face of a person in a video with the face of another individual, making it appear as though the second person is speaking or acting in the video. Voice cloning: Deepfake technology can replicate a person\'s voice by analyzing their speech patterns and using AI to generate new audio recordings in that person\'s voice. Realistic visuals: Deepfake videos are known for their high degree of realism, with facial expressions, movements, and lip-syncing that closely resemble the original subject. Manipulated text: While less common, deepfake technology can also be used to generate fake text content that mimics an individual\'s writing style or produces fictional narratives. Misinformation and deception: Deepfakes have the potential to spread misinformation, deceive people, and create convincing fake content for various purposes, both benign and malicious. Implications for corporations Reputation damage: Corporations invest years in building their brand and reputation. Deepfake videos or audio recordings featuring corporate leaders making controversial statements can have devastating consequences. Financial fraud: Deepfakes can be used to impersonate executives, leading to fraudulent requests for funds, | Tool Vulnerability Threat Commercial | ★★ | ||
| 2023-11-08 07:00:00 | Une seule vitre peut-elle jamais être découverte pour la cybersécurité? Can a Single Pane of Glass Ever be Discovered for Cybersecurity? (lien direct) |
> Dans le paysage en constante évolution de la cybersécurité, le concept d'un «volet unique de verre» a longtemps été le Saint Graal pour de nombreuses organisations.L'idée est simple: consolider tous vos outils et données de cybersécurité sur un seul tableau de bord pour une visibilité et un contrôle améliorés. & # 160;Bien que ce concept contient du mérite, en particulier dans la main-d'œuvre hybride moderne, il \'s [& # 8230;]
>In the ever-evolving landscape of cybersecurity, the concept of a ”single pane of glass” has long been the Holy Grail for many organisations. The idea is simple: consolidate all your cybersecurity tools and data onto a single dashboard for improved visibility and control. While this concept holds merit, particularly in the modern hybrid workforce, it\'s […] |
Tool | ★★ | ||
| 2023-11-08 06:00:00 | Protéger vos chemins, partie 1: comment la gestion du chemin d'attaque peut arrêter les attaquants sur leurs traces Protecting Your Paths, Part 1: How Attack Path Management Can Stop Attackers in Their Tracks (lien direct) |
This blog is the first in a series where we explore attack path management. We\'ll explain what you need to know and give you the tools you need to help you better protect the middle of the attack chain. A big reason that successful cyberattacks are on the rise is that threat actors are shifting their tactics to identity-based attacks. Last year, 84% of businesses fell victim to an identity-related breach. When attackers land on a host, it is rarely their end target. Instead, they look to escalate privilege and move laterally across an environment. Their next step is to exploit more privileged credentials, and they often do this by using shadow admin vulnerabilities. It can be a challenge to stop them. To do so, you need to quickly discover, prioritize and remediate identity vulnerabilities. But first, you need to know what you\'re up against. In this blog post, we explore the multitude of identity vulnerability challenges, and we explain why an attack path management (APM) view is so important. We also specify which identity-centric attack vectors are likely to exist in your environment. Key terms Before we dive into this topic further, let\'s define some key terms that are central to this area of security: Attack path management. This refers to the process of identifying, analyzing, understanding and remediating attack paths within a business. Identities and other system resources are typically spread across multiple on-premises and cloud identity stores. These include Microsoft Active Directory (AD), Entra ID (formerly Azure AD), AWS and Okta. Attack path. Threat actors follow a sequence of steps as they compromise security, which is called an attack path. The typical end result is the compromise of a tier-zero asset (TZA)-or what is generally referred to as a bad breach. TZAs. Tier-zero assets are often referred to as the “crown jewels.” They are a company\'s most critical and sensitive assets. They can include systems, data or other resources (databases, web gateways) that are essential to its operation, reputation and overall resilience. In certain scenarios, AD domain controllers or authentication systems can be considered TZAs given the broad scope of damage that can arise with their breach. The risks of TZA compromise Compromising a tier-zero asset is a high-value objective for attackers because it allows them to achieve their financial or other malicious goals. Here are some common objectives: Data exfiltration TZAs may store or have access to critical and sensitive data or intellectual property. Or they might be critical system resources that, if compromised, could result in a service outage. Attackers aim to steal this information for financial gain, espionage or extortion. Data exfiltration clearly impacts the confidentiality part of the CIA triad. Data manipulation Attackers may alter or manipulate data within TZAs to achieve their goals. For instance, they could modify user account settings, insert malicious code or encrypt data as a step toward operational disruption. Data manipulation impacts the integrity part of the CIA triad. Denial of service (DoS) or disruption Attackers may use compromised tier-zero assets to launch DoS attacks against critical operational services in an enterprise. This can disrupt services and cause operational or financial harm to the business. This exposure category is about impacting the availability portion of the CIA triad. Ransomware Attackers may use their control over TZAs to deploy ransomware across a network. By encrypting critical systems and data, they can demand substantial ransom payments in exchange for the decryption keys. Ultimately ransomware attackers are focused on financial gain. One of their main tactics for extracting a ransom is threatening to directly impact system availability. (See this 2021 breach as an example.) Lateral movement to more TZAs Once attackers compromise a tier-zero asset, they can use it as a launch pad to move laterally to other TZAs. Figure 1. Tier-zero | Ransomware Tool Vulnerability Threat Cloud | ★★ | ||
| 2023-11-07 17:58:00 | La variante de logiciels malveillants de la nouvelle gootloader échappe à la détection et se propage rapidement New GootLoader Malware Variant Evades Detection and Spreads Rapidly (lien direct) |
Il a été constaté qu'une nouvelle variante du logiciel malveillant de gootloader appelé Gootbot facilite les mouvements latéraux sur des systèmes compromis et d'éviter la détection.
"L'introduction de leur propre bot personnalisé par le groupe de chèques dans les stades tardifs de leur chaîne d'attaque est une tentative d'éviter les détections lors de l'utilisation d'outils standard pour C2 tels que CobalTstrike ou RDP", chercheurs IBM X-ForceGolo m & uuml; hr et ole
A new variant of the GootLoader malware called GootBot has been found to facilitate lateral movement on compromised systems and evade detection. "The GootLoader group\'s introduction of their own custom bot into the late stages of their attack chain is an attempt to avoid detections when using off-the-shelf tools for C2 such as CobaltStrike or RDP," IBM X-Force researchers Golo Mühr and Ole |
Malware Tool | ★★★ | ||
| 2023-11-07 17:37:50 | Sécuriser les API: étapes pratiques pour protéger votre logiciel Securing APIs: Practical Steps to Protecting Your Software (lien direct) |
Dans le monde dynamique du développement de logiciels, les interfaces de programmation d'applications (API) servent de conduits essentiels, facilitant l'interaction transparente entre les composants logiciels.Cette interface intermédiaire rationalise non seulement le développement, mais permet également aux équipes logicielles de réutiliser le code.Cependant, la prévalence croissante des API dans les affaires modernes est accompagnée de défis de sécurité.C'est pourquoi nous avons créé ce billet de blog - pour vous fournir des étapes exploitables pour améliorer la sécurité de vos API aujourd'hui.
Comprendre la sécurité de l'API
La sécurité de l'API s'étend au-delà de la protection des services backend d'une application, y compris des éléments tels que des bases de données, des systèmes de gestion des utilisateurs et des composants interagissant avec les magasins de données.Il s'agit d'adopter divers outils et pratiques pour renforcer l'intégrité de votre pile technologique.Une forte stratégie de sécurité des API réduit le risque d'accès non autorisé et d'actions malveillantes, assurant la protection des informations sensibles.
Explorer les vulnérabilités API
Malgré la…
In the dynamic world of software development, Application Programming Interfaces (APIs) serve as essential conduits, facilitating seamless interaction between software components. This intermediary interface not only streamlines development but also empowers software teams to reuse code. However, the increasing prevalence of APIs in modern business comes with security challenges. That\'s why we\'ve created this blog post - to provide you with actionable steps to enhance the security of your APIs today. Understanding API Security API Security extends beyond protecting an application\'s backend services, including elements such as databases, user management systems, and components interacting with data stores. It involves adopting diverse tools and practices to strengthen the integrity of your tech stack. A strong API security strategy reduces the risk of unauthorized access and malicious actions, ensuring the protection of sensitive information. Exploring API Vulnerabilities Despite the… |
Tool Guideline | ★★ | ||
| 2023-11-07 16:30:00 | L'implant de chèvre augmentait le risque de ransomware post-infection GootBot Implant Heightens Risk of Post-Infection Ransomware (lien direct) |
IBM a trouvé un groupe de chèvre-chargeur optant pour des outils de gluant sur le mouvement latéral pour le mouvement latéral
IBM found Gootloader group opting for GootBot over off-the-shelf tools for lateral movement |
Ransomware Tool | ★★ | ||
| 2023-11-07 16:00:00 | Visual Studio Code Security: Deep Dive dans votre éditeur préféré (1/3) Visual Studio Code Security: Deep Dive into Your Favorite Editor (1/3) (lien direct) |
Nous avons examiné la sécurité de l'éditeur de code le plus populaire, Visual Studio Code!Ce billet de blog couvre les risques communs et les surfaces d'attaque afin que vous sachiez à quoi vous attendre lorsque vous l'utilisez.
We took a look at the security of the most popular code editor, Visual Studio Code! This blog post covers common risks and attack surfaces so you know what to expect when using it. |
Tool Vulnerability | ★★★ | ||
| 2023-11-07 15:59:21 | Eaton lance une plateforme logicielle pour les exploitatants de Data Centers (lien direct) | Eaton lance une plateforme logicielle inédite pour accélérer la transformation digitale et favoriser la durabilité des exploitants de datacenters • Cette nouvelle plateforme rassemble des outils de gestion des équipements, de mesure de la qualité énergétique, de surveillance des appareils informatiques et des technologies opérationnelles (OT), ainsi que d'autres fonctionnalités uniques, réunies en une seule application native • Cet ensemble de solutions digitales permet d'améliorer la durabilité, la résilience et les performances des infrastructures critiques dans les datacenters et les services d'informatique distribuée - Produits | Tool | ★★ | ||
| 2023-11-07 15:51:00 | AI offensif et défensif: le chat (GPT) de \\ Offensive and Defensive AI: Let\\'s Chat(GPT) About It (lien direct) |
Chatgpt: outil de productivité, idéal pour écrire des poèmes et… un risque de sécurité ?!Dans cet article, nous montrons comment les acteurs de la menace peuvent exploiter Chatgpt, mais aussi comment les défenseurs peuvent l'utiliser pour niveler leur jeu.
Chatgpt est l'application de consommation la plus en pleine croissance à ce jour.Le chatbot AI génératif extrêmement populaire a la capacité de générer des réponses humaines, cohérentes et contextuellement pertinentes.
ChatGPT: Productivity tool, great for writing poems, and… a security risk?! In this article, we show how threat actors can exploit ChatGPT, but also how defenders can use it for leveling up their game. ChatGPT is the most swiftly growing consumer application to date. The extremely popular generative AI chatbot has the ability to generate human-like, coherent and contextually relevant responses. |
Tool Threat | ChatGPT | ★★★ | |
| 2023-11-07 15:26:00 | Le projet de loi bipartisan vise à avoir un impact large sur les efforts de surveillance fédérale Bipartisan bill aims to have wide impact on federal surveillance efforts (lien direct) |
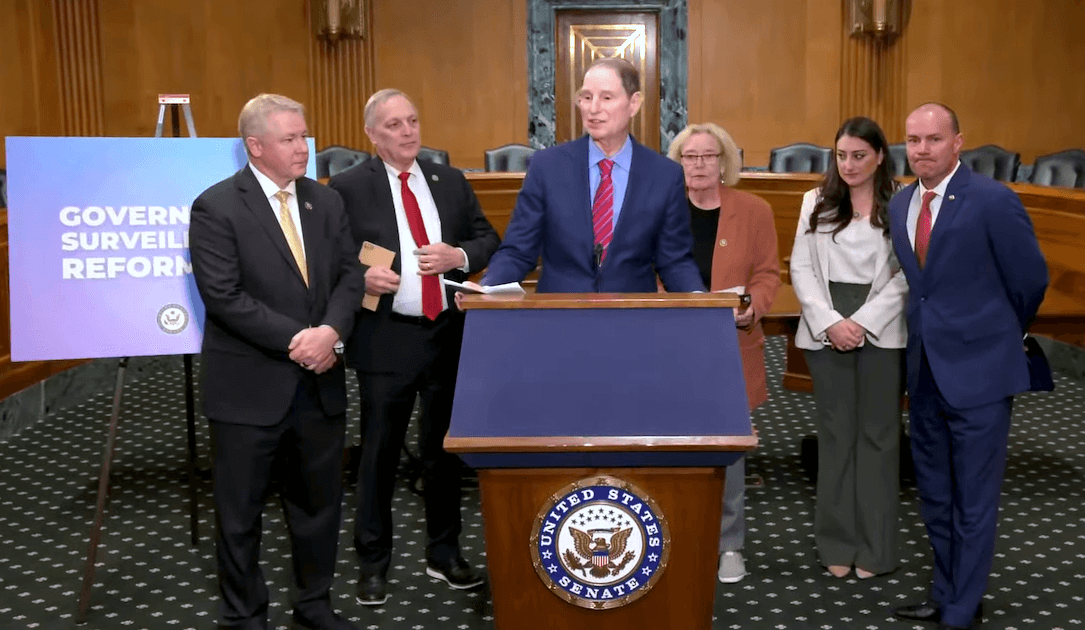 Cette année, la première législation majeure de \\ pour étendre les autorités de surveillance du gouvernement américain expirées est un effort bipartite qui comprendrait certaines des bordures les plus substantielles depuis des années sur ces outils et autres pouvoirs de renseignement.Un groupe de législateurs de la Chambre et du Sénat a introduit la mesure mardi pour renouveler l'article 702 de la Foreign Intelligence Act,
Cette année, la première législation majeure de \\ pour étendre les autorités de surveillance du gouvernement américain expirées est un effort bipartite qui comprendrait certaines des bordures les plus substantielles depuis des années sur ces outils et autres pouvoirs de renseignement.Un groupe de législateurs de la Chambre et du Sénat a introduit la mesure mardi pour renouveler l'article 702 de la Foreign Intelligence Act,
 This year\'s first major legislation to extend expiring U.S. government surveillance authorities is a bipartisan effort that would include some of the most substantial curbs in years on those tools and other intelligence powers. A group of House and Senate lawmakers introduced the measure on Tuesday to renew Section 702 of the Foreign Intelligence Act,
This year\'s first major legislation to extend expiring U.S. government surveillance authorities is a bipartisan effort that would include some of the most substantial curbs in years on those tools and other intelligence powers. A group of House and Senate lawmakers introduced the measure on Tuesday to renew Section 702 of the Foreign Intelligence Act, |
Tool Legislation | ★★ | ||
| 2023-11-07 08:00:00 | Boostez votre PC avec Windows Memory Cleaner ! (lien direct) | Windows Memory Cleaner est un nettoyeur de RAM gratuit et sans installation pour ordinateurs Windows. Il optimise la mémoire en utilisant des fonctionnalités natives et offre plusieurs options telles que l'optimisation automatique et le mode compact. L'outil est multilingue et permet aux utilisateurs de contribuer aux traductions. | Tool | ★★ | ||
| 2023-11-06 21:35:00 | Enlèvement virtuel: les outils d'IA permettent des escroqueries d'extorsion IRL Virtual Kidnapping: AI Tools Are Enabling IRL Extortion Scams (lien direct) |
Avec l'IA et les données accessibles au public, les cybercriminels ont les ressources dont ils ont besoin pour simuler un enlèvement réel et vous faire croire.
With AI and publicly available data, cybercriminals have the resources they need to fake a real-life kidnapping and make you believe it. |
Tool | ★★ | ||
| 2023-11-06 20:15:07 | CVE-2023-5719 (lien direct) | L'outil de configuration Windows Crimson 3.2 permet aux utilisateurs ayant un accès administratif pour définir de nouveaux mots de passe pour les utilisateurs et télécharger la configuration de sécurité résultante sur un appareil.Si un tel mot de passe contient le caractère en pourcentage (%), des valeurs non valides seront incluses, tronquant potentiellement la chaîne si un NUL est rencontré.Si le mot de passe simplifié n'est pas détecté par l'administrateur, l'appareil peut être laissé dans un état vulnérable en raison des informations d'identification plus bien compromises.Notez que les mots de passe entrés via le serveur Web Crimson System ne souffrent pas de cette vulnérabilité.
The Crimson 3.2 Windows-based configuration tool allows users with administrative access to define new passwords for users and to download the resulting security configuration to a device. If such a password contains the percent (%) character, invalid values will be included, potentially truncating the string if a NUL is encountered. If the simplified password is not detected by the administrator, the device might be left in a vulnerable state as a result of more-easily compromised credentials. Note that passwords entered via the Crimson system web server do not suffer from this vulnerability. |
Tool Vulnerability | |||
| 2023-11-06 19:56:48 | Le directeur de contre-terroriste a utilisé l'attaque du Hamas pour justifier le renouvellement du programme de surveillance de masse Counterterror Director Used Hamas Attack to Justify Mass Surveillance Program Renewal (lien direct) |
> La communauté du renseignement américain est confrontée à des appels pour réformer l'outil d'espionnage connu sous le nom de 702, qui devrait expirer à la fin de l'année.
>The U.S. intelligence community is facing calls to reform the spying tool known as 702, which is set to expire at the end of the year. |
Tool | ★★ | ||
| 2023-11-06 16:44:35 | AWS CodeWhisperer reconverti en expert MongoDB (lien direct) | En parallèle du chantier d'adaptation de CodeWhisperer aux codebases internes, AWS l'affine pour des outils spécifiques... dont MongoDB. | Tool | ★★ | ||
| 2023-11-06 13:55:00 | Google avertit comment les pirates pourraient abuser du service de calendrier en tant que canal C2 secret Google Warns How Hackers Could Abuse Calendar Service as a Covert C2 Channel (lien direct) |
Google met en garde contre les acteurs de menaces multiples partageant un exploit de preuve de concept public (POC) qui exploite son service de calendrier pour héberger une infrastructure de commandement et de contrôle (C2).
L'outil, appelé Google Calendar Rat (GCR), utilise des événements de calendrier Google pour C2 à l'aide d'un compte Gmail.Il a été publié pour la première fois sur Github en juin 2023.
"Le script crée une chaîne \\ 'Covert \' en exploitant l'événement
Google is warning of multiple threat actors sharing a public proof-of-concept (PoC) exploit that leverages its Calendar service to host command-and-control (C2) infrastructure. The tool, called Google Calendar RAT (GCR), employs Google Calendar Events for C2 using a Gmail account. It was first published to GitHub in June 2023. "The script creates a \'Covert Channel\' by exploiting the event |
Tool Threat | ★★★★ | ||
| 2023-11-06 11:00:00 | Appliquer une approche basée sur l'intelligence à la cybersécurité;SIEM et Dark Web Survering Applying an intelligence-based approach to Cybersecurity; SIEM and dark web monitoring (lien direct) |
“History repeatedly has demonstrated that inferior forces can win when leaders are armed with accurate intelligence.” – Central Intelligence Agency; Intelligence in War In the ever-changing landscape of global cybersecurity, the boundaries between traditional military intelligence and cybersecurity are increasingly blurred. At the heart of this convergence lies the science of intelligence analysis—a process fundamental to both realms. Equally important is the recognition of target indicators, which serve as harbingers of impending activities, whether on a battlefield or within the complex circuits of cyberspace. For the modern organization, Security Information and Event Management (SIEM) systems serve as the nexus where the ancient art of intelligence gathering meets the contemporary needs of cybersecurity. This fusion is further enriched by dark web monitoring, a relatively new frontier in information gathering that equips analysts with a fuller understanding of the threat landscape in the darker recesses of the Internet where cybercriminals do their bidding. Traditionally, military intelligence has been the linchpin of strategic and tactical decision-making. It involves complex processes for data collection, analysis, and interpretation. In short, it turns ubiquitous data into actionable intelligence. The types of data used in intelligence analysis range from intercepted radio communications, satellite images, and even information gathered from troops on the ground. Analysts and applications sift through this plethora of information to extract actionable insights, scrutinizing for target indicators—clues that signal the enemy\'s intent or location. For instance, an unusual accumulation of vehicles in a remote area could indicate the staging of troops, thereby serving as a target indicator. Recognizing such cues is crucial for informed decision-making. Likewise, in cybersecurity, intelligence analysis serves as the backbone of protective strategies. Here, data collection is continuous and automated, thanks to SIEM systems and security correlation engines. These systems aggregate logs from various network endpoints, generating alerts based on defined rules that flag anomalies or known indicators of compromise. Just as military analysts look for signs like troop movement or weapons stockpiling, cybersecurity analysts review SIEM logs for target indicators such as repeated failed login attempts or abnormal data transfers, which might indicate a cyber-attack. The enrichment of SIEM data sets through dark web monitoring brings a novel depth to cybersecurity. For the uninitiated, the dark web serves as a haven for cybercriminals, offering a marketplace for anything from hacking tools to stolen data. This space is often the first point of compromise, where stolen data may appear for sale or where impending cyber-attacks might be discussed. Dark web monitoring involves the tracking of these criminal forums and marketplaces for specific keywords, threats, or data sets related to an organization. Information gleaned from the dark web provides that extra layer of intelligence, allowing for a more proactive cybersecurity posture. For example, a company might discover on the dark web that its stolen user credentials or company client lists are being sold. This type of information is a specific target indication that a company has experienced a data breach at some level. The parallels between military intelligence and cybersecurity are not merely conceptual; they have practical implications. Military operations often employ real-ti | Data Breach Tool Threat | ★★ | ||
| 2023-11-06 07:20:56 | 3 erreurs courantes que vous faites avec votre programme de sensibilisation à la sécurité 3 Common Mistakes You\\'re Making with Your Security Awareness Program (lien direct) |
Despite the vast budget and resources invested in cybersecurity, breaches are still commonplace and increasingly impactful. When these incidents are analyzed, there is a common factor-the controlling technology is undermined by human action. This can include staff handing out credentials, facilitating unauthorized requests, falling for spoof emails and running malware at the behest of an attacker. When the World Economic Forum states that 95% of security breaches occur because of human action, it is clear that security awareness throughout your organization is imperative. Yet despite years of activity, more still needs to be done. Here are some things you may be doing that will hinder your security program-and, more importantly, the steps you can take to fix them. Mistake 1: You have named your security program incorrectly As simple as it sounds, you may have chosen a poor name for your security program. We all focus on security awareness and build “security awareness programs” for our businesses, but that isn\'t what we really want. Our true aim is more than just to improve awareness-it is to change behavior. Calling our program “security awareness” encourages us to focus on the wrong outcome. After all, if our real aim is to stop people smoking, we wouldn\'t call our initiative the “be aware of the risks of smoking campaign.” This has an easy fix: Change the name of your program. Decide on the outcome you want and name your program appropriately-such as \'Security Behavior Change Program\' or \'Build Security Culture Program.\' You will be amazed by the difference such a small change can make because the new title will be a constant reminder of what you are actually trying to achieve. Mistake 2: Thinking that \'lots of awareness\' leads to culture The second mistake is related to the first. All too often, programs decide they can change the culture of the organization by increasing the amount of awareness training that staff undertake. That won\'t happen. Culture is not the same as “lots of awareness.” There is an “ABC” maturity model that I use, which stands for awareness, behavior, culture. Each is a step that builds on the previous one. Critically, there is a pivot at each step-a change of focus that\'s required to transition from one level to the next. Let\'s assume we already do awareness. To pivot to behavior, you need to focus on making sure that your staff members understand the consequences of cybersecurity, both personally and professionally. Once they have awareness and motivation, they are much more likely to display the correct behavior. (There is science behind this simplified approach, and I recommend you check out Professor BJ Fogg\'s behavior model.) Once behavior is on the road to achievement, then culture becomes your goal. The pivot for the culture step is the creation of a wide-ranging perception that everyone around the business cares about security. Note that I use the word “perception.” It doesn\'t have to be true initially, as this is a real case of “fake it \'til you make it.” Create that perception by tuning your communications plan to ensure that security messages arrive from across your organization-from executives, from receptionists, and especially from middle and line managers. Indeed, these messages should come from almost everyone except the chief information security officer (CISO). This will build a perception in each staff member that everyone around them cares about security, and that will create peer pressure for them to act in similar ways. This is the crucible of culture. Mistake 3: Using negative consequences as a primary motivator The key step to mature to the behavior level mentioned above is to create a motivation to change behavior. Motivation can be encouraged in various ways. One approach is to create a fear of punishment or embarrassment if staff make an error or fail a security test. Many security professionals have strong opinions on this matter. Some believe that negative c | Malware Tool Vulnerability | ★★ | ||
| 2023-11-05 17:45:05 | Alors, avez-vous entendu parler de Havoc, le nouvel outil du cyber arsenal? So, have you heard about Havoc, the new tool in the cyber arsenal? (lien direct) |
Permettez-moi de vous donner la baisse de ce que le brassage dans le métro numérique avec ce nouveau logiciel appelé Havoc.Maintenant, vous pourriez être [Plus ...]
Let me give you the lowdown on what’s brewing in the digital underground with this fresh piece of software called Havoc. Now, you might be [more...] |
Tool Tool Technical | ★★★★ | ||
| 2023-11-05 14:40:37 | Outils d'étagère supérieurs: les huit meilleurs de Kali Linux Top Shelf Tools: The Best Eight of Kali Linux (lien direct) |
Vous avez soif pour briser les choses en toute sécurité?Soit les tests de stylo de parler et Kali Linux qu'est-ce que ce buzz ce que je continue à entendre?Vous êtes tombé sur [plus ...]
Got a Thirst for Breaking Things Securely? Let’s Talk Pen Testing and Kali Linux What’s this Pen Testing Buzz I Keep Hearing? You’ve stumbled across [more...] |
Tool | ★★★ | ||
| 2023-11-05 13:01:30 | Meilleurs outils logiciels de cybersécurité pour 2024 Best CyberSecurity Software Tools For 2024 (lien direct) |
En 2024, vous souhaitez être équipé des meilleurs outils de cybersécurité.Nous avons créé cette liste d'outils de cybersécurité qui contiennent une collection massive [plus ...]
In 2024, you want to be equipped with the best cybersecurity tools. We have created this list of cybersecurity tools that contain a massive collection [more...] |
Tool | ★★ | ||
| 2023-11-04 17:33:50 | Le partage de données transparente est-il la clé de l'amélioration de la collaboration en cybersécurité? Is Seamless Data Sharing the Key to Enhanced Cybersecurity Collaboration? (lien direct) |
Dans le labyrinthe de la cybersécurité, le partage de l'intelligence rapidement et en toute sécurité entre les outils et les équipes n'est pas critique.Pourquoi?Parce que la vitesse à [plus...]
In the labyrinth of cybersecurity, the sharing of intelligence swiftly and securely among tools and teams isn’t just beneficial-it’s critical. Why? Because the speed at [more...] |
Tool | ★★ | ||
| 2023-11-03 14:17:30 | Intégration de Thor dans Velociraptor: suralimentation en médecine légale numérique et réponse aux incidents Integration of THOR in Velociraptor: Supercharging Digital Forensics and Incident Response (lien direct) |
Dans le labyrinthe de la cybersécurité, le partage de l'intelligence rapidement et en toute sécurité entre les outils et les équipes n'est pas critique.Pourquoi?Parce que la vitesse à [plus...]
In the labyrinth of cybersecurity, the sharing of intelligence swiftly and securely among tools and teams isn’t just beneficial-it’s critical. Why? Because the speed at [more...] |
Tool | ★★★ | ||
| 2023-11-03 12:35:00 | \\ 'Campagne sociale en plusieurs étapes \\' Campagne contre Israël lié au groupe basé en Iran \\'Multi-stage social engineering\\' campaign against Israel tied to Iran-based group (lien direct) |
 Un groupe de longue date lié au gouvernement iranien a ciblé au moins deux entités israéliennes avec une campagne de piratage au cours du dernier mois, ont déclaré des chercheurs.Dans un effort continu détecté fin octobre, le groupe connu sous le nom de Muddywater a utilisé des tactiques familières avec de légers modifications à ses outils précédents, selon un Rapport par l'entreprise de cybersécurité
Un groupe de longue date lié au gouvernement iranien a ciblé au moins deux entités israéliennes avec une campagne de piratage au cours du dernier mois, ont déclaré des chercheurs.Dans un effort continu détecté fin octobre, le groupe connu sous le nom de Muddywater a utilisé des tactiques familières avec de légers modifications à ses outils précédents, selon un Rapport par l'entreprise de cybersécurité
 A long-running group connected to the Iranian government targeted at least two Israeli entities with a hacking campaign in the last month, researchers said. In an ongoing effort detected in late October, the group known as MuddyWater used familiar tactics with slight changes to its previous tools, according to a report by the cybersecurity firm
A long-running group connected to the Iranian government targeted at least two Israeli entities with a hacking campaign in the last month, researchers said. In an ongoing effort detected in late October, the group known as MuddyWater used familiar tactics with slight changes to its previous tools, according to a report by the cybersecurity firm |
Tool | ★★ | ||
| 2023-11-03 10:04:59 | Premier combiné avec MTE sur le marché First handset with MTE on the market (lien direct) |
By Mark Brand, Google Project ZeroIntroduction It\'s finally time for me to fulfill a long-standing promise. Since I first heard about ARM\'s Memory Tagging Extensions, I\'ve said (to far too many people at this point to be able to back out…) that I\'d immediately switch to the first available device that supported this feature. It\'s been a long wait (since late 2017) but with the release of the new Pixel 8 / Pixel 8 Pro handsets, there\'s finally a production handset that allows you to enable MTE! The ability of MTE to detect memory corruption exploitation at the first dangerous access is a significant improvement in diagnostic and potential security effectiveness. The availability of MTE on a production handset for the first time is a big step forward, and I think there\'s real potential to use this technology to make 0-day harder. I\'ve been running my Pixel 8 with MTE enabled since release day, and so far I haven\'t found any issues with any of the applications I use on a daily basis1, or any noticeable performance issues. Currently, MTE is only available on the Pixel as a developer option, intended for app developers to test their apps using MTE, but we can configure it to default to synchronous mode for all2 apps and native user mode binaries. This can be done on a stock image, without bootloader unlocking or rooting required - just a couple of debugger commands. We\'ll do that now, but first:Disclaimer This is absolutely not a supported device configuration; and it\'s highly likely that you\'ll encounter issues with at least some applications crashing or failing to run correctly with MTE if you set your device up in this way. This is how I\'ve configured my personal Pixel 8, and so far I\'ve not experienced any issues, but this was somewhat of a surprise to me, and I\'m still waiting to see what the first app that simply won\'t work at all will be...Enabling MTE on Pixel 8/Pixel 8 Pro | Tool Mobile | ★★ | ||
| 2023-11-03 08:15:07 | CVE-2023-42670 (lien direct) | Une faille a été trouvée en samba.Il est sensible à une vulnérabilité où plusieurs auditeurs de RPC incompatibles peuvent être initiés, provoquant des perturbations dans le service AD DC.Lorsque le serveur RPC de Samba \\ connaît une charge élevée ou une non-réponse, les serveurs destinés à des fins de courant continu non AD (par exemple, l'émulation NT4-émulation "DCS") peuvent démarrer et rivaliser à tort pour les mêmes prises de domaine Unix.Ce problème conduit à des réponses de requête partielles de l'AD DC, provoquant des problèmes tels que "le numéro de procédure est hors de portée" lors de l'utilisation d'outils comme les utilisateurs Active Directory.Ce défaut permet à un attaquant de perturber les services AD DC.
A flaw was found in Samba. It is susceptible to a vulnerability where multiple incompatible RPC listeners can be initiated, causing disruptions in the AD DC service. When Samba\'s RPC server experiences a high load or unresponsiveness, servers intended for non-AD DC purposes (for example, NT4-emulation "classic DCs") can erroneously start and compete for the same unix domain sockets. This issue leads to partial query responses from the AD DC, causing issues such as "The procedure number is out of range" when using tools like Active Directory Users. This flaw allows an attacker to disrupt AD DC services. |
Tool Vulnerability | |||
| 2023-11-03 01:00:48 | Top 10 des outils de développement Web Top 10 web development tools (lien direct) |
Commencez-vous simplement votre voyage en tant que développeur Web et recherchez des outils pour rationaliser votre processus de développement?Eh bien, vous & # 8217; Re dans la chance!Ici & # 8217; s a [plus ...]
Are you just beginning your journey as a web developer and hunting for tools to streamline your development process? Well, you’re in luck! Here’s a [more...] |
Tool | ★★ | ||
| 2023-11-02 20:07:38 | Dévoiler le côté obscur: une plongée profonde dans les familles de ransomwares actifs Unveiling the Dark Side: A Deep Dive into Active Ransomware Families (lien direct) |
#### Description
Dans le paysage en constante évolution de la cybersécurité, une tendance constante observée ces dernières années est l'augmentation troublante des attaques de ransomwares.Le groupe NCC partage TTP \\ déployé par quatre familles de ransomwares récemment observées lors des engagements de réponse aux incidents du NCC Group \\.Les familles de ransomwares qui seront explorées sont:
- Blackcat & # 8211;Il est également connu sous le nom d'ALPHV, observé pour la première fois en 2021, un ransomware en tant que service (RAAS) utilisant souvent la méthode d'extorsion à double extorsion pour le gain monétaire.
- Donut & # 8211; Le groupe d'extorsion D0nut a été signalé pour la première fois en août 2022 pour avoir violé les réseaux et exigeant des rançons en échange de ne pas fuiser des données volées.Quelques mois plus tard, les rapports du groupe utilisant le cryptage ainsi que l'exfiltration de données ont été publiés avec des spéculations selon lesquelles le ransomware déployé par le groupe a été lié à des ransomwares Helloxd.Il existe également des liens soupçonnés entre les affiliés D0nut et les opérations de ransomware de casier Hive et Ragnar.
- Medusa & # 8211;À ne pas confondre avec Medusalocker, Medusa a été observée pour la première fois en 2021, est un ransomware en tant que service (RAAS) utilisant souvent la méthode d'extorsion à double extorsion pour le gain monétaire.En 2023, l'activité des groupes \\ 'a augmenté avec le lancement du blog \' Medusa \\ '.Cette plate-forme sert d'outil pour divulguer des données appartenant aux victimes.
- NoEscape & # 8211;Fin mai 2023, un Ransomware nouvellement émergé en tant que service (RAAS) a été observé sur un forum de cybercriminalité nommé NoeScape.
#### URL de référence (s)
1. https://research.nccgroup.com/2023/10/31/unveiling-the-dark-side-a-plongée profonde-inactive-ransomware-families /
#### Date de publication
31 octobre 2023
#### Auteurs)
Alex Jessop
@Thissisfinechief
Molly Dewis
#### Description In the ever-evolving cybersecurity landscape, one consistent trend witnessed in recent years is the unsettling rise in ransomware attacks. NCC Group shares TTP\'s deployed by four ransomware families recently observed during NCC Group\'s incident response engagements. The ransomware families that will be explored are: - BlackCat – Also known as ALPHV, first observed in 2021, is a Ransomware-as-a-Service (Raas) often using the double extortion method for monetary gain. - Donut –The D0nut extortion group was first reported in August 2022 for breaching networks and demanding ransoms in return for not leaking stolen data. A few months later, reports of the group utilizing encryption as well as data exfiltration were released with speculation that the ransomware deployed by the group was linked to HelloXD ransomware. There is also suspected links between D0nut affiliates and both Hive and Ragnar Locker ransomware operations. - Medusa – Not to be confused with MedusaLocker, Medusa was first observed in 2021, is a Ransomware-as-a-Service (RaaS) often using the double extortion method for monetary gain. In 2023 the groups\' activity increased with the launch of the \'Medusa Blog\'. This platform serves as a tool for leaking data belonging to victims. - NoEscape – At the end of May 2023, a newly emerged Ransomware-as-a-Service (RaaS) was observed on a cybercrime forum named NoEscape. #### Reference URL(s) 1. https://research.nccgroup.com/2023/10/31/unveiling-the-dark-side-a-deep-dive-into-active-ransomware-families/ #### Publication Date October 31, 2023 #### Author(s) Alex Jessop @ThisIsFineChief Molly Dewis |
Ransomware Tool Prediction | ★★ | ||
| 2023-11-02 14:54:00 | La sécurité SaaS est désormais accessible et abordable à tous SaaS Security is Now Accessible and Affordable to All (lien direct) |
Ce nouveau produit propose l'évaluation de la découverte et des risques SaaS couplée à une revue gratuite d'accès aux utilisateurs dans un modèle «freemium» unique
La sécurisation des employés \\ 'SaaS devient de plus en plus cruciale pour la plupart des organisations basées sur le cloud.Bien que de nombreux outils soient disponibles pour répondre à ce besoin, ils utilisent souvent différentes approches et technologies, conduisant à une confusion et une complexité inutiles.Entrer
This new product offers SaaS discovery and risk assessment coupled with a free user access review in a unique “freemium” model Securing employees\' SaaS usage is becoming increasingly crucial for most cloud-based organizations. While numerous tools are available to address this need, they often employ different approaches and technologies, leading to unnecessary confusion and complexity. Enter |
Tool Cloud | ★★ | ||
| 2023-11-02 14:51:00 | Muddywater iran Iran\\'s MuddyWater Targets Israel in New Spear-Phishing Cyber Campaign (lien direct) |
L'acteur iranien de l'État-nation connu sous le nom de Muddywater a été lié à une nouvelle campagne de phishing de lance ciblant deux entités israéliennes pour déployer finalement un outil d'administration à distance légitime de Nable appelé agent de surveillance avancée.
La société de cybersécurité Deep Instinct, qui a divulgué les détails des attaques, a déclaré que la campagne "expose les TTP à jour à l'activité de Muddywater précédemment signalée".
The Iranian nation-state actor known as MuddyWater has been linked to a new spear-phishing campaign targeting two Israeli entities to ultimately deploy a legitimate remote administration tool from N-able called Advanced Monitoring Agent. Cybersecurity firm Deep Instinct, which disclosed details of the attacks, said the campaign "exhibits updated TTPs to previously reported MuddyWater activity," |
Tool | ★★★ | ||
| 2023-11-02 13:45:06 | SAST vs. DAST for Security Testing: Unveiling the Differences (lien direct) | Les tests de sécurité des applications (AST) comprennent divers outils, processus et approches pour scanner des applications pour découvrir des problèmes de sécurité potentiels.Les tests de sécurité des applications statiques (SAST) et les tests de sécurité des applications dynamiques (DAST) sont des approches de test de sécurité populairement utilisées qui suivent différentes méthodologies de codes d'application de numérisation à différentes étapes d'un cycle de vie de développement logiciel.
Sast suit une approche de test de boîte blanche pour analyser le code source, le code d'octets et les binaires pour identifier les vulnérabilités exploitables et les erreurs de codage.D'un autre côté, DAST met en œuvre une méthode de test de la boîte noire, où les ingénieurs de sécurité analysent les charges utiles simulées d'attaque via le frontal de l'application sans exposer des informations internes sur la construction interne de l'application \\.
Dans ce blog, nous discuterons des approches de tests de Sast et de Dast, comment ils aident à détecter les vulnérabilités et les défaillances des applications, leurs différences et les meilleurs cas d'utilisation.
Application statique…
Application Security Testing (AST) encompasses various tools, processes, and approaches to scanning applications to uncover potential security issues. Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) are popularly used security testing approaches that follow different methodologies of scanning application codes across different stages of a software development lifecycle. SAST follows a white-box testing approach to analyze the source code, byte code, and binaries to identify exploitable vulnerabilities and coding errors. On the other hand, DAST implements a black-box testing method, where security engineers parse simulated attack payloads through the application\'s front end without exposing internal information on the application\'s internal construct. In this blog, we will discuss SAST and DAST testing approaches, how they help detect vulnerabilities and application failures, their differences, and best use cases. Static Application… |
Tool Vulnerability | ★★ | ||
| 2023-11-02 12:00:24 | Plus de moyens pour les utilisateurs d'identifier les applications testées sur la sécurité indépendante sur Google Play More ways for users to identify independently security tested apps on Google Play (lien direct) |
Posted by Nataliya Stanetsky, Android Security and Privacy Team
Keeping Google Play safe for users and developers remains a top priority for Google. As users increasingly prioritize their digital privacy and security, we continue to invest in our Data Safety section and transparency labeling efforts to help users make more informed choices about the apps they use.
Research shows that transparent security labeling plays a crucial role in consumer risk perception, building trust, and influencing product purchasing decisions. We believe the same principles apply for labeling and badging in the Google Play store. The transparency of an app\'s data security and privacy play a key role in a user\'s decision to download, trust, and use an app.
Highlighting Independently Security Tested VPN Apps
Last year, App Defense Alliance (ADA) introduced MASA (Mobile App Security Assessment), which allows developers to have their apps independently validated against a global security standard. This signals to users that an independent third-party has validated that the developers designed their apps to meet these industry mobile security and privacy minimum best practices and the developers are going the extra mile to identify and mitigate vulnerabilities. This, in turn, makes it harder for attackers to reach users\' devices and improves app quality across the ecosystem. Upon completion of the successful validation, Google Play gives developers the option to declare an “Independent security review” badge in its Data Safety section, as shown in the image below. While certification to baseline security standards does not imply that a product is free of vulnerabilities, the badge associated with these validated apps helps users see at-a-glance that a developer has prioritized security and privacy practices and committed to user safety.
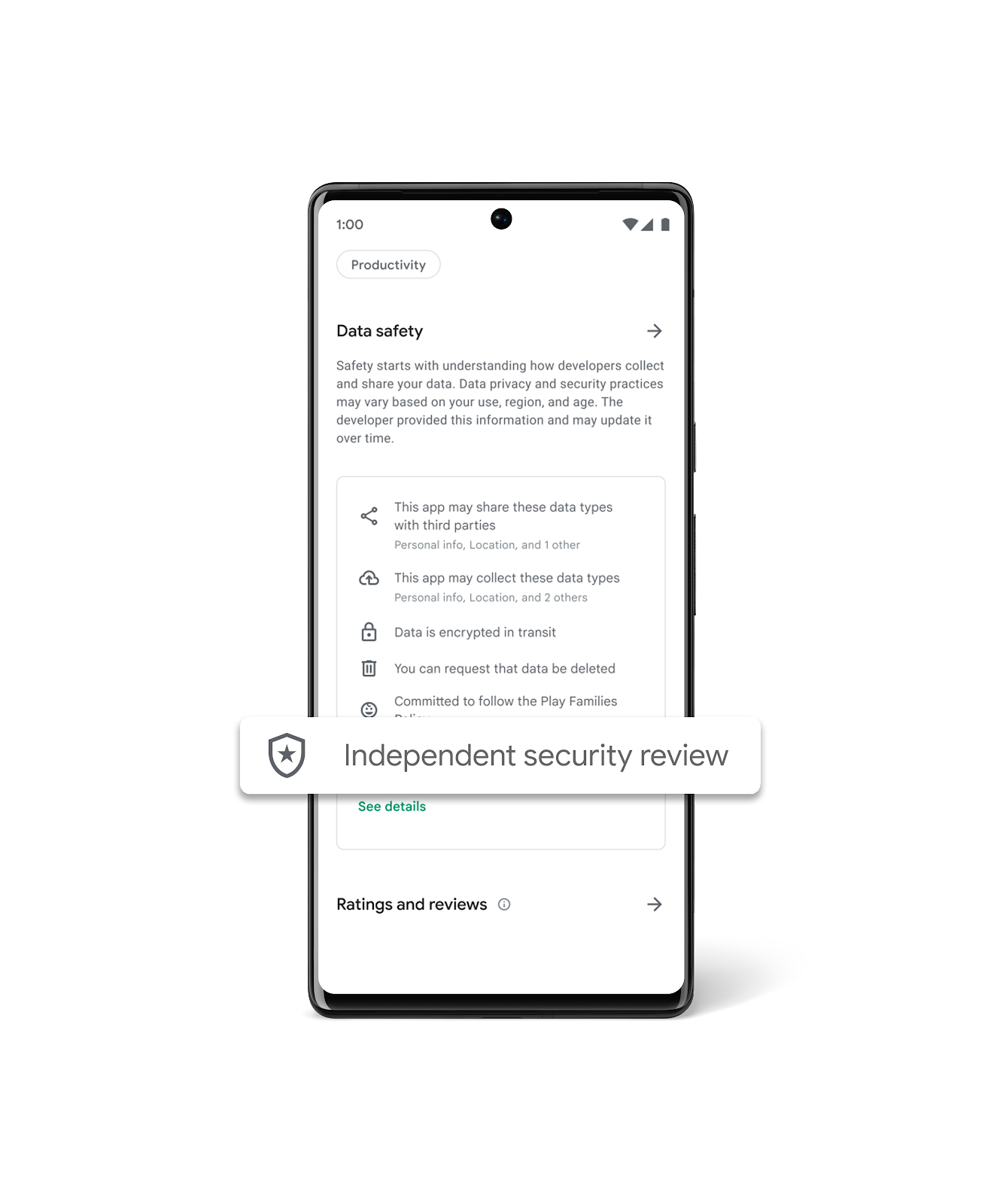 To help give users a simplified view of which apps have undergone an independent security validation, we\'re introducing a new Google Play store banner for specific app types, starting with VPN apps. We\'ve launched this banner beginning with VPN apps due to the sensitive and significant amount of user data these apps handle. When a user searches for VPN apps, they will now see a banner at the top of Google Play that educates them about the “Independent security review” badge in the Data Safety Section. Users also have the ability to “Learn More”, which redirects them to the App Validation Directory, a centralized place to view all VPN apps that have been independently security reviewed. Users can also discover additional technical assessment details in the App Validation Directory, helping them to make more informed decisions about what VPN apps to download, use, and trust with their data.
To help give users a simplified view of which apps have undergone an independent security validation, we\'re introducing a new Google Play store banner for specific app types, starting with VPN apps. We\'ve launched this banner beginning with VPN apps due to the sensitive and significant amount of user data these apps handle. When a user searches for VPN apps, they will now see a banner at the top of Google Play that educates them about the “Independent security review” badge in the Data Safety Section. Users also have the ability to “Learn More”, which redirects them to the App Validation Directory, a centralized place to view all VPN apps that have been independently security reviewed. Users can also discover additional technical assessment details in the App Validation Directory, helping them to make more informed decisions about what VPN apps to download, use, and trust with their data.
|
Tool Vulnerability Mobile Technical | ★★ | ||
| 2023-11-02 11:30:00 | Bugy octets # 216 & # 8211;Injections SQL, Android XSS et rédaction de rapports de qualité Bug Bytes #216 – SQL injections, Android XSS and Writing Quality Reports (lien direct) |
> Bug Bytes est une newsletter hebdomadaire organisée par les membres de la communauté Bug Bounty.La deuxième série est organisée par InsiderPhd.Chaque semaine, elle nous tient à jour avec une liste complète des articles, des outils, des tutoriels et des ressources.Ce numéro couvre la semaine du 23 octobre au 29 octobre Intigriti News de mon cahier
>Bug Bytes is a weekly newsletter curated by members of the bug bounty community. The second series is curated by InsiderPhD. Every week, she keeps us up to date with a comprehensive list of write-ups, tools, tutorials and resources. This issue covers the week from October 23rd to October 29th Intigriti News From my notebook |
Tool Mobile Technical | ★★★ | ||
| 2023-11-02 10:00:00 | Un guide de l'acquisition de données numériques en médecine légale avec l'imageur FTK A guide to digital forensics data acquisition with FTK Imager (lien direct) |
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. In the field of Digital Forensics and Incident Response (DFIR), acquiring a forensic copy of a suspect\'s storage device is a critical first step. This process involves either disk imaging or disk cloning, each with its own distinct purposes and methodologies. In this blog, we\'ll delve into the differences between disk imaging and disk cloning, when to use each method, and provide step-by-step guidance on how to create a forensic disk image using FTK Imager. Disk imaging vs. disk cloning Disk imaging Disk imaging is the process of creating a bit-for-bit copy or snapshot of an entire storage device or a specific partition. In forensic imaging, the goal is to create an exact, bit-for-bit copy of the source disk without making any changes to the original data. The key characteristics of disk imaging include: Non-destructive: Disk imaging is a non-destructive process that doesn\'t alter the original data on the source device. It preserves the integrity of the evidence. File-level access: After imaging, forensic examiners can access and analyze the files and folders within the image using specialized forensic software. This allows for targeted analysis and data recovery. Metadata preservation: Disk imaging retains critical metadata such as file timestamps, permissions, and attributes, which can be crucial in investigations. Flexible storage: Disk images can be stored in various formats (e.g., E01, DD, AFF) and on different media, such as external hard drives or network storage. Disk cloning Disk cloning, on the other hand, involves creating an exact duplicate of the source storage device, including all partitions and unallocated space. Unlike file copying, disk cloning also duplicates the filesystems, partitions, drive meta data and slack space on the drive. The characteristics of disk cloning include: Exact copy: Disk cloning produces an identical copy of the source device. It replicates everything, including empty space and hidden partitions. Quick duplication: Cloning is typically faster than imaging because it doesn\'t involve the creation of a separate image file. It\'s essentially a sector-by-sector copy. Cloning is like making an exact photocopy of a book, smudges and all. It copies everything, even the empty pages. So, if we\'re dealing with a whole computer, it copies the operating system, software, and every file, whether it\'s useful or not. Creating a forensic disk image with FTK Imager FTK Imager is a widely used and trusted tool for creating forensic disk images. Here are the steps to create a disk image using FTK Imager: Download and Install FTK Imager, make sure to use latest stable version available as well mention the version and vendor details in case notes. This is a good practice in digital forensics and incident response (DFIR) as it ensures that you are using the most up-to-date and secure version of the software, and it provides important documentation about the tools and their configurations used in your investigations. Keeping software updated is essential for maintaining the integrity and reliability of your forensic processes. Download and Install FTK Imager on your forensic workstation. It can be downloaded from here. You’ll need to provide some information like name, business email etc., and after you fill in the form the download will start automatically. You can use privacy centric services while filling out the information. Begin the installation. | Tool Tool | ★★★ | ||
| 2023-11-01 20:30:00 | Le Département du commerce promet des garanties pour empêcher les ventes de technologies de surveillance à l'étranger Commerce Department promises safeguards to prevent surveillance tech sales abroad (lien direct) |
 Le Département du commerce a mis en œuvre de nouvelles politiques pour arrêter la promotion des technologies de surveillance aux gouvernements étrangers.Dans un lettre au sénateur Ron (D-or) Wyden, qui a exprimé la préoccupation de l'agence sur le spreadParmi les outils en mai, le Département du commerce a fixé les mesures que son Administration du commerce international (ITA) a prises pour freiner
Le Département du commerce a mis en œuvre de nouvelles politiques pour arrêter la promotion des technologies de surveillance aux gouvernements étrangers.Dans un lettre au sénateur Ron (D-or) Wyden, qui a exprimé la préoccupation de l'agence sur le spreadParmi les outils en mai, le Département du commerce a fixé les mesures que son Administration du commerce international (ITA) a prises pour freiner
 The Commerce Department has implemented new policies to stop the promotion of surveillance technologies to foreign governments. In a letter to Senator Ron (D-OR) Wyden, who expressed concern to the agency about the spread of the tools in May, the Commerce Department laid out the steps its International Trade Administration (ITA) has taken to curb
The Commerce Department has implemented new policies to stop the promotion of surveillance technologies to foreign governments. In a letter to Senator Ron (D-OR) Wyden, who expressed concern to the agency about the spread of the tools in May, the Commerce Department laid out the steps its International Trade Administration (ITA) has taken to curb |
Tool | ★★ | ||
| 2023-11-01 18:08:00 | Une campagne d'informations sur le voleur cible désormais les utilisateurs de Facebook avec des photos révélatrices An info-stealer campaign is now targeting Facebook users with revealing photos (lien direct) |
 Les cybercriminels utilisent des publicités Facebook pour distribuer des logiciels malveillants et des utilisateurs de détournement de logiciels \\ ', des chercheurs ont révélé des chercheurs.Dans la campagne dite de malvertising, les pirates exploitent des outils légitimes pour la distribution d'annonces en ligne et insérer des liens infectés vers des publicités typiques.Pour inciter les utilisateurs à cliquer, la campagne propose des «attracatifs» - dans ce cas, des images obscènes de jeunes
Les cybercriminels utilisent des publicités Facebook pour distribuer des logiciels malveillants et des utilisateurs de détournement de logiciels \\ ', des chercheurs ont révélé des chercheurs.Dans la campagne dite de malvertising, les pirates exploitent des outils légitimes pour la distribution d'annonces en ligne et insérer des liens infectés vers des publicités typiques.Pour inciter les utilisateurs à cliquer, la campagne propose des «attracatifs» - dans ce cas, des images obscènes de jeunes
 Cybercriminals are using Facebook ads to distribute malware and hijack users\' social media accounts, researchers have found. In the so-called malvertising campaign, hackers exploit legitimate tools for online ad distribution and insert infected links into typical advertisements. To entice users into clicking, the campaign offers “provocative enticements” - in this case, lewd images of young
Cybercriminals are using Facebook ads to distribute malware and hijack users\' social media accounts, researchers have found. In the so-called malvertising campaign, hackers exploit legitimate tools for online ad distribution and insert infected links into typical advertisements. To entice users into clicking, the campaign offers “provocative enticements” - in this case, lewd images of young |
Malware Tool Threat | ★★★ | ||
| 2023-11-01 16:45:53 | Docontrol lance l'extension de l'intégration Salesforce DoControl Launches Salesforce Integration Extending (lien direct) |
Docontrol lance l'intégration Salesforce étendant sa plate-forme de sécurité SaaS complète à tous les écosystèmes SaaS de premier plan
Les utilisateurs Salesforce bénéficieront désormais d'une solution consolidée de Docontrol, leur fournissant un éventail complet d'outils pour sauvegarder contre une vaste gamme de menaces
-
revues de produits
DoControl Launches Salesforce Integration Extending Its Comprehensive SaaS Security Platform To All Prominent SaaS Ecosystems Salesforce users will now benefit from DoControl\'s consolidated solution, providing them with a comprehensive array of tools to safeguard against an extensive range of threats - Product Reviews |
Tool Cloud | ★★ | ||
| 2023-11-01 15:10:26 | Outils de premier plan, efficaces et puissants pour identifier les visiteurs du site Leading, effective, and powerful tools for identifying site visitors (lien direct) |
> Par owais sultan
Savoir qui visite votre site Web vous donne des données précieuses que votre équipe de vente peut utiliser ce précieux marketing & # 8230;
Ceci est un article de HackRead.com Lire le post original: Outils de premier plan, efficaces et puissants pour identifier les visiteurs du site
>By Owais Sultan Knowing who visits your website gives you valuable data that your sales team can use this valuable marketing… This is a post from HackRead.com Read the original post: Leading, effective, and powerful tools for identifying site visitors |
Tool | ★★ | ||
| 2023-10-31 19:45:32 | From Albania to the Middle East: The Scarred Manticore is Listening (lien direct) | #### Description
Check Point Research (RCR) surveille une campagne d'espionnage iranienne en cours par Scarred Manticore, un acteur affilié au ministère du renseignement et de la sécurité (MOIS).Les attaques reposent sur Liontail, un cadre de logiciel malveillant passif avancé installé sur les serveurs Windows.À des fins de furtivité, les implants liionnal utilisent les appels directs vers Windows HTTP Stack Driver Http.SYS pour charger les charges utiles des résidents de mémoire.
La campagne actuelle a culminé à la mi-2023, passant sous le radar pendant au moins un an.La campagne cible les organisations de haut niveau au Moyen-Orient en mettant l'accent sur les secteurs du gouvernement, des militaires et des télécommunications, en plus des fournisseurs de services informatiques, des organisations financières et des ONG.Scarred Manticore poursuit des objectifs de grande valeur depuis des années, utilisant une variété de déambulations basées sur l'IIS pour attaquer les serveurs Windows.Ceux-ci incluent une variété de shells Web personnalisés, de bornes de dos de DLL personnalisées et d'implants basés sur le pilote.Bien que la principale motivation derrière l'opération de Manticore \\ ne soit que l'espionnage, certains des outils décrits dans ce rapport ont été associés à l'attaque destructrice parrainée par MOIS contre l'infrastructure du gouvernement albanais (appelé Dev-0861).
#### URL de référence (s)
1. https://research.checkpoint.com/2023/from-albania-to-the-middle-East-the-scarred-Manticore-is-Listening/
#### Date de publication
31 octobre 2023
#### Auteurs)
Recherche de point de contrôle
#### Description Check Point Research (CPR) is monitoring an ongoing Iranian espionage campaign by Scarred Manticore, an actor affiliated with the Ministry of Intelligence and Security (MOIS). The attacks rely on LIONTAIL, an advanced passive malware framework installed on Windows servers. For stealth purposes, LIONTIAL implants utilize direct calls to Windows HTTP stack driver HTTP.sys to load memory-residents payloads. The current campaign peaked in mid-2023, going under the radar for at least a year. The campaign targets high-profile organizations in the Middle East with a focus on government, military, and telecommunications sectors, in addition to IT service providers, financial organizations and NGOs. Scarred Manticore has been pursuing high-value targets for years, utilizing a variety of IIS-based backdoors to attack Windows servers. These include a variety of custom web shells, custom DLL backdoors, and driver-based implants. While the main motivation behind Scarred Manticore\'s operation is espionage, some of the tools described in this report have been associated with the MOIS-sponsored destructive attack against Albanian government infrastructure (referred to as DEV-0861). #### Reference URL(s) 1. https://research.checkpoint.com/2023/from-albania-to-the-middle-east-the-scarred-manticore-is-listening/ #### Publication Date October 31, 2023 #### Author(s) Check Point Research |
Malware Tool | APT 34 APT 34 | ★★ | |
| 2023-10-31 19:25:00 | Les États-Unis mènent une alliance de 40 pays pour couper les paiements des ransomwares US Leads 40-Country Alliance to Cut Off Ransomware Payments (lien direct) |
Les parties de l'initiative internationale contre les ransomwares ont l'intention d'utiliser des outils de partage d'informations et une IA pour atteindre leurs objectifs de coupe des ressources financières des acteurs de la menace.
The parties within the International Counter Ransomware Initiative intend to use information-sharing tools and AI to achieve their goals of cutting off the financial resources of threat actors. |
Ransomware Tool Threat | ★★ | ||
| 2023-10-31 18:55:37 | Google prévoit RISC-V Android Tools en 2024, veut que les développeurs «soient prêts» Google plans RISC-V Android tools in 2024, wants developers to “be ready” (lien direct) |
Nous avons un support RISC-V OS, des puces entrantes et bientôt, un écosystème d'applications.
We\'ve got RISC-V OS support, incoming chips, and soon, an app ecosystem. |
Tool | ★★ | ||
| 2023-10-31 10:56:45 | Déstaurer la saga Manticore marquée: une épopée fascinante d'espionnage à enjeux élevés qui se déroule au cœur du Moyen-Orient Unraveling the Scarred Manticore Saga: A Riveting Epic of High-Stakes Espionage Unfolding in the Heart of the Middle East (lien direct) |
> Faits saillants: 1. Intrudeurs silencieux: Manticore marqué, un groupe de cyber-menaces iranien lié à Mois (Ministère des renseignements & # 38; Security), gère tranquillement une opération d'espionnage sophistiquée furtive au Moyen-Orient.En utilisant leur dernier cadre d'outils de logiciels malveillants, Liontail, ils volent sous le radar depuis plus d'un an.2. Secteurs ciblés: La campagne se concentre sur les grands joueurs-gouvernement, militaire, télécommunications, informatique, finance et ONG au Moyen-Orient.Manticore marqué est une question de données systématiquement en train de saisir des données, montrant leur engagement envers les cibles de grande valeur.3. Évolution des tactiques: le livre de jeu de Manticore Scarre est passé des attaques de base de shell sur les serveurs Windows à [& # 8230;]
>Highlights: 1. Silent Intruders: Scarred Manticore, an Iranian cyber threat group linked to MOIS (Ministry of Intelligence & Security), is quietly running a stealthy sophisticated spying operation in the Middle East. Using their latest malware tools framework, LIONTAIL, they have been flying under the radar for over a year. 2. Targeted Sectors: The campaign focuses on big players-government, military, telecom, IT, finance, and NGOs in the Middle East. Scarred Manticore is all about systematically nabbing data, showing their commitment to high-value targets. 3. Evolution of Tactics: Scarred Manticore’s playbook has evolved from basic web shell attacks on Windows Servers to […] |
Malware Tool Threat | APT 34 | ★★ | |
| 2023-10-31 10:37:38 | CISA dévoile la journalisation facilitée: la solution à guichet unique pour les systèmes basés sur Windows CISA Unveils Logging Made Easy: The One-Stop Solution for Windows-Based Systems (lien direct) |
L'Agence de sécurité de la cybersécurité et de l'infrastructure (CISA) a publié la journalisation Made Easy (LME), un outil de gestion de journaux robuste et gratuit conçu pour renforcer les mesures de cybersécurité pour [plus ...]
The Cybersecurity and Infrastructure Security Agency (CISA) has released Logging Made Easy (LME), a robust, cost-free log management tool designed to reinforce cybersecurity measures for [more...] |
Tool | ★★ | ||
| 2023-10-31 08:00:27 | Turbolehe – Un peu d\'OSINT pour trouver des emails cachés (lien direct) | Turbolehe, un outil puissant pour les enquêtes OSINT, facilite la génération et la validation d'adresses e-mail à partir d'un nom et prénom. Basé sur Python, il teste les combinaisons possibles et vérifie leur existence, permettant un gain de temps considérable. Turbolehe offre également des fonctionnalités supplémentaires, telles que le filtrage par domaine, et prévoit des améliorations futures pour optimiser son efficacité. | Tool | ★★★★ | ||
| 2023-10-30 18:30:00 | L'outil de piratage russe inonde les réseaux sociaux avec des robots, disent les chercheurs Russian hacking tool floods social networks with bots, researchers say (lien direct) |
 Les cybercriminels à faible teneur en compétence utilisent un nouvel outil pour créer des centaines de faux comptes de médias sociaux en quelques secondes, ont découvert des chercheurs.Appelé Kopeechka («Penny» en russe), le service aide à contourner deux «obstacles» principaux pour quelqu'un qui essaie de créer un faux compte - une vérification par e-mail et par téléphone.Les cybercriminels pourraient utiliser Kopeechka pour transporter
Les cybercriminels à faible teneur en compétence utilisent un nouvel outil pour créer des centaines de faux comptes de médias sociaux en quelques secondes, ont découvert des chercheurs.Appelé Kopeechka («Penny» en russe), le service aide à contourner deux «obstacles» principaux pour quelqu'un qui essaie de créer un faux compte - une vérification par e-mail et par téléphone.Les cybercriminels pourraient utiliser Kopeechka pour transporter
 Low-skill cybercriminals are using a new tool to create hundreds of fake social media accounts in just a few seconds, researchers have discovered. Called Kopeechka (“penny” in Russian), the service helps to bypass two main “hurdles” for someone trying to create a fake account - email and phone verification. Cybercriminals could use Kopeechka to carry
Low-skill cybercriminals are using a new tool to create hundreds of fake social media accounts in just a few seconds, researchers have discovered. Called Kopeechka (“penny” in Russian), the service helps to bypass two main “hurdles” for someone trying to create a fake account - email and phone verification. Cybercriminals could use Kopeechka to carry |
Tool | ★★★ |

