What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2017-06-13 01:26:00 | More notes on US-CERTs IOCs (lien direct) | Yet another Russian attack against the power grid, and yet more bad IOCs from the DHS US-CERT.IOCs are "indicators of compromise", things you can look for in order to order to see if you, too, have been hacked by the same perpetrators. There are several types of IOCs, ranging from the highly specific to the uselessly generic.A uselessly generic IOC would be like trying to identify bank robbers by the fact that their getaway car was "white" in color. It's worth documenting, so that if the police ever show up in a suspected cabin in the woods, they can note that there's a "white" car parked in front.But if you work bank security, that doesn't mean you should be on the lookout for "white" cars. That would be silly.This is what happens with US-CERT's IOCs. They list some potentially useful things, but they also list a lot of junk that waste's people's times, with little ability to distinguish between the useful and the useless.An example: a few months ago was the GRIZZLEYBEAR report published by US-CERT. Among other things, it listed IP addresses used by hackers. There was no description which would be useful IP addresses to watch for, and which would be useless.Some of these IP addresses were useful, pointing to servers the group has been using a long time as command-and-control servers. Other IP addresses are more dubious, such as Tor exit nodes. You aren't concerned about any specific Tor exit IP address, because it changes randomly, so has no relationship to the attackers. Instead, if you cared about those Tor IP addresses, what you should be looking for is a dynamically updated list of Tor nodes updated daily.And finally, they listed IP addresses of Yahoo, because attackers passed data through Yahoo servers. No, it wasn't because those Yahoo servers had been compromised, it's just that everyone passes things though them, like email.A Vermont power-plant blindly dumped all those IP addresses into their sensors. As a consequence, the next morning when an employee checked their Yahoo email, the sensors triggered. This resulted in national headlines about the Russians hacking the Vermont power grid.Today, the US-CERT made similar mistakes with CRASHOVERRIDE. They took a report from Dragos Security, then mutilated it. Dragos's own IOCs focused on things like hostile strings and file hashes of the hostile files. They also included filenames, but similar to the reason you'd noticed a white car -- because it happened, not because you should be on the lookout for it. In context, there's nothing wrong with noting the file name.But the US-CERT pulled the filenames out of context. One of those filenames was, humorously, "svchost.exe". It's the name of an essential Windows service. Every Windows computer is running multiple copies of "svchost.exe". It's like saying "be on the lookout for Windows".Yes, it's true that viruses use the same filenames as essential Windows files like "svchost.exe". That's, generally, something you should be aware of. But that CRASHOVERRIDE did this is wholly meaningless.What Dragos Security was actually reporting was that a "svchost.exe" with the file hash of 79ca89711cdaedb16b0ccccfdcfbd6aa7e57120a was the virus -- it's the hash that's the important IOC. Pulling the filename out of context is just silly.Luckily, the DHS also provides some of the raw information provided by Dragos. But even then, there's problems: they provide it in formatted | Yahoo | |||
| 2017-05-12 02:51:43 | Some notes on Trump\'s cybersecurity Executive Order (lien direct) | President Trump has finally signed an executive order on "cybersecurity". The first draft during his first weeks in power were hilariously ignorant. The current draft, though, is pretty reasonable as such things go. I'm just reading the plain language of the draft as a cybersecurity expert, picking out the bits that interest me. In reality, there's probably all sorts of politics in the background that I'm missing, so I may be wildly off-base.Holding managers accountableThis is a great idea in theory. But government heads are rarely accountable for anything, so it's hard to see if they'll have the nerve to implement this in practice. When the next breech happens, we'll see if anybody gets fired."antiquated and difficult to defend Information Technology"The government uses laughably old computers sometimes. Forces in government wants to upgrade them. This won't work. Instead of replacing old computers, the budget will simply be used to add new computers. The old computers will still stick around."Legacy" is a problem that money can't solve. Programmers know how to build small things, but not big things. Everything starts out small, then becomes big gradually over time through constant small additions. What you have now is big legacy systems. Attempts to replace a big system with a built-from-scratch big system will fail, because engineers don't know how to build big systems. This will suck down any amount of budget you have with failed multi-million dollar projects.It's not the antiquated systems that are usually the problem, but more modern systems. Antiquated systems can usually be protected by simply sticking a firewall or proxy in front of them."address immediate unmet budgetary needs necessary to manage risk"Nobody cares about cybersecurity. Instead, it's a thing people exploit in order to increase their budget. Instead of doing the best security with the budget they have, they insist they can't secure the network without more money.An alternate way to address gaps in cybersecurity is instead to do less. Reduce exposure to the web, provide fewer services, reduce functionality of desktop computers, and so on. Insisting that more money is the only way to address unmet needs is the strategy of the incompetent.Use the NIST frameworkProbably the biggest thing in the EO is that it forces everyone to use the NIST cybersecurity framework.The NIST Framework simply documents all the things that organizations commonly do to secure themselves, such run intrusion-detection systems or impose rules for good passwords.There are two problems with the NIST Framework. The first is that no organization does all the things listed. The second is that many organizations don't do the things well.Password rules are a good example. Organizations typically had bad rules, such as frequent changes and complexity standards. So the NIST Framework documented them. But cybersecurity experts have long opposed those complex rules, so have been fighting NIST on them.Another good example is intrusion-detection. These days, I scan the entire Internet, setting off everyone's intrusion-detection systems. I can see first hand that they are doing intrusion-detection wrong. But the NIST Framework recommends they do it, because many organizations do it, but the NIST Framework doesn't demand they do it well.When this EO forces everyone to follow the NIST Framework, then, it's likely just going to i | Guideline | Yahoo Tesla | ||
| 2017-03-06 06:50:36 | Journalists: How hacking details matter (lien direct) | When I write my definitive guide for journalists covering hacking, I'm going to point out how easy it is for journalists to misunderstand the details of a story -- especially when they change the details to fit the story they want to tell.For example, there is the notorious "CIA hacked Senate computers" scandal. In fact, the computers in question were owned by the CIA, located in a CIA facility, and managed/operated by CIA employees. You can't "hack" computers you own. Yes, the CIA overstepped the bounds of an informal agreement with the Senate committee overseeing them, but in no way did anything remotely like "hacking" occur.This detail matter. If the CIA had truly hacked the Senate committee, that would be a constitutional crisis. A small misstep breaking an informal agreement is not.A more recent example is this story, which mentions that AlfaBank-Trump connection, claiming the server was in Trump Tower [*]:What about the computer server at Trump Tower?Several news media outlets have reported that investigators last year were puzzled by data transmissions between a computer server at Trump Tower and a computer server associated with a Russian bank. Although Mr. Trump on Twitter talked about his “phones,†in theory a judge might determine that the computer address of the server in the tower was a facility being used by a foreign power, Russia, to communicate, and authorize surveillance of it.No, the server was not located in Trump Tower. It was located outside Philadelphia. It's owned and operated by a company called Listrak. There's no evidence anybody in the Trump Organization even knew about the server. It was some other company named Cendyn who decided to associate Trump's name with the server. There's no evidence of communication between the server and Alfa -- only evidence of communication about the server from Alfa.The details are important to the story, because it's trying to show how a judge "might determine that the computer ... in the tower was a facility being used by a foreign power". If it's not anywhere near or related to the Trump Tower, no such determination could be made.Then there was that disastrous story from the Washington Post about Russia hacking into a Vermont power plant [*], which still hasn't been retracted despite widespread condemnation. No such hacking occurred. Instead, the details of what happened is that an employee checked Yahoo mail from his laptop. The night before, the DHS had incorrectly configured its "Einstein" intrusion detection system to trigger on innocent traffic with Yahoo as an indicator of compromise from Russian hackers.You can see how journalists make these mistakes. If CIA is spying on computers used by Senate staffers, then the natural assumption is that the CIA hacked those computers. If there was a server associated with the Trump Organization, however tenuous, it's easy to assume a more concrete relationship, such as the server being located in Trump's offices. You can see how once the DHS claims there was a hack, and you've filled your stories with quotes from senators pontificating about the meaning of such hacks, it's very difficult to retract the story when the details emerge there was nothing remotely resembling a hack.I'm not trying to claim that journalists need to be smarter about hacking. I'm instead claiming that journalists need to be smarter about journalism. The flaws here all go one way -- toward the sensational. Instead of paying attention to the details and questioning whether such sensational | Yahoo | |||
| 2017-01-09 23:13:24 | No, Yahoo! isn\'t changing its name (lien direct) | Trending on social media is how Yahoo is changing it's name to "Altaba" and CEO Marissa Mayer is stepping down. This is false.What is happening instead is that everything we know of as "Yahoo" (including the brand name) is being sold to Verizon. The bits that are left are a skeleton company that holds stock in Alibaba and a few other companies. Since the brand was sold to Verizon, that investment company could no longer use it, so chose "Altaba". Since 83% of its investment is in Alibabi, "Altaba" makes sense. It's not like this new brand name means anything -- the skeleton investment company will be wound down in the next year, either as a special dividend to investors, sold off to Alibaba, or both.Marissa Mayer is an operations CEO. Verizon didn't want her to run their newly acquired operations, since the entire point of buying them was to take the web operations in a new direction (though apparently she'll still work a bit with them through the transition). And of course she's not an appropriate CEO for an investment company. So she had no job left -- she made her own job disappear.What happened today is an obvious consequence of Alibaba going IPO in September 2014. It meant that Yahoo's stake of 16% in Alibaba was now liquid. All told, the investment arm of Yahoo was worth $36-billion while the web operations (Mail, Fantasy, Tumblr, etc.) was worth only $5-billion.In other words, Yahoo became a Wall Street mutual fund who inexplicably also offered web mail and cat videos.Such a thing cannot exist. If Yahoo didn't act, shareholders would start suing the company to get their money back.That $36-billion in investments doesn't belong to Yahoo, it belongs to its shareholders. Thus, the moment the Alibaba IPO closed, Yahoo started planning on how to separate the investment arm from the web operations.Yahoo had basically three choices.The first choice is simply give the Alibaba (and other investment) shares as a one time dividend to Yahoo shareholders. A second choice is simply split the company in two, one of which has the investments, and the other the web operations. The third choice is to sell off the web operations to some chump like Verizon.Obviously, Marissa Mayer took the third choice. Without a slushfund (the investment arm) to keep it solvent, Yahoo didn't feel it could run its operations profitably without integration with some other company. That meant it either had to buy a large company to integrate with Yahoo, or sell the Yahoo portion to some other large company.Every company, especially Internet ones, have a legacy value. It's the amount of money you'll get from firing everyone, stop investing in the future, and just raking in year after year a stream of declining revenue. It's the fate of early Internet companies like Earthlink and Slashdot. It's like how I documented with Earthlink [*], which continues to offer email to subscribers, but spends only enough to keep the lights on, not even upgrading to the simplest of things like SSL.Presumably, Verizon will try to make something of a few of the properties. Apparently, Yahoo's Fantasy sports stuff is popular, and will probably be rebranded as some new Verizon thing. Tumblr is already it's own brand name, independent of Yahoo, and thus will probably continue to exist as its own business unit.One of the weird things is Yahoo Mail. It permanently bound to the "yahoo.com" domain, so you can't do much with the "Yahoo" brand without bringing Mail along with it. Though at this point, the "Yahoo" brand is pretty tarnished. There's not much new you can put under that brand anyway. I can't see how Verizon would want to invest in that brand at all -- just milk it for what it can over the coming years.The investment company cannot long exist on its own. Investors want their | Yahoo | |||
| 2017-01-03 21:33:01 | Dear Obama, From Infosec (lien direct) | Dear President Obama:We are more than willing to believe Russia was responsible for the hacked emails/records that influenced our election. We believe Russian hackers were involved. Even if these hackers weren't under the direct command of Putin, we know he could put a stop to such hacking if he chose. It's like harassment of journalists and diplomats. Putin encourages a culture of thuggery that attacks opposition, without his personal direction, but with his tacit approval.Your lame attempts to convince us of what we already agree with has irretrievably damaged your message.Instead of communicating with the America people, you worked through your typical system of propaganda, such as stories in the New York Times quoting unnamed "senior government officials". We don't want "unnamed" officials -- we want named officials (namely you) who we can pin down and question. When you work through this system of official leaks, we believe you have something to hide, that the evidence won't stand on its own.We still don't believe the CIA's conclusions because we don't know, precisely, what those conclusions are. Are they derived purely from companies like FireEye and CloudStrike based on digital forensics? Or do you have spies in Russian hacker communities that give better information? This is such an important issue that it's worth degrading sources of information in order to tell us, the American public, the truth.You had the DHS and US-CERT issue the "GRIZZLY-STEPPE" report "attributing those compromises to Russian malicious cyber activity". It does nothing of the sort. It's full of garbage. It contains signatures of viruses that are publicly available, used by hackers around the world, not just Russia. It contains a long list of IP addresses from perfectly normal services, like Tor, Google, Dropbox, Yahoo, and so forth.Yes, hackers use Yahoo for phishing and malvertising. It doesn't mean every access of Yahoo is an "Indicator of Compromise".For example, I checked my web browser [chrome://net-internals/#dns] and found that last year on November 20th, it accessed two IP addresses that are on the Grizzley-Steppe list: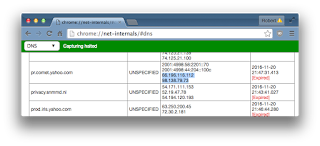 No, this doesn't mean I've been hacked. It means I just had a normal interaction with Yahoo. It means the Grizzley-Steppe IoCs are garbage.If your intent was to show technical information to experts to confirm Russia's involvement, you've done the precise opposite. Grizzley-Steppe proves such enormous incompetence that we doubt all the technical details you might have. I mean, it's possible that you classified the important details and de-classified the junk, but even then, that junk isn't worth publishing. There's no excuse for those Yahoo addresses to be in there, or the numerous other problems.Among the consequences is that Washington Post story claiming Russians hacked into the Vermont power grid. What really happened is that somebody just checked their Yahoo email, thereby accessing one of the same IP addresses I did. How they get from the facts (one person accessed Yahoo email) to the story (Russians hacked power grid) is your responsibility. This misinformation is your fault.You announced sanctions for the Russian hacking [*]. At the same time, you announced sanctions for Russian harassment of diplomati No, this doesn't mean I've been hacked. It means I just had a normal interaction with Yahoo. It means the Grizzley-Steppe IoCs are garbage.If your intent was to show technical information to experts to confirm Russia's involvement, you've done the precise opposite. Grizzley-Steppe proves such enormous incompetence that we doubt all the technical details you might have. I mean, it's possible that you classified the important details and de-classified the junk, but even then, that junk isn't worth publishing. There's no excuse for those Yahoo addresses to be in there, or the numerous other problems.Among the consequences is that Washington Post story claiming Russians hacked into the Vermont power grid. What really happened is that somebody just checked their Yahoo email, thereby accessing one of the same IP addresses I did. How they get from the facts (one person accessed Yahoo email) to the story (Russians hacked power grid) is your responsibility. This misinformation is your fault.You announced sanctions for the Russian hacking [*]. At the same time, you announced sanctions for Russian harassment of diplomati |
Yahoo APT 29 APT 28 | |||
| 2016-10-12 15:21:46 | WTF Yahoo/FISA search in kernel? (lien direct) | A surprising detail in the Yahoo/FISA email search scandal is that they do it with a kernel module. I thought I'd write up some (rambling) notes.What the government was searching forAs described in the previoius blog post, we'll assume the government is searching for the following string, and possibly other strings like it within emails:### Begin ASRAR El Mojahedeen v2.0 Encrypted Message ###I point this out because it's simple search identifying things. It's not natural language processing. It's not searching for phrases like “bomb presidentâ€.Also, it's not AV/spam/childporn processing. Those look at different things. For example, filtering message containing childporn involves calculating a SHA2 hash of email attachments and looking up the hashes in a table of known bad content. This is quite different from searching.The Kernel vs. User SpaceOperating systems have two parts, the kernel and user space. The kernel is the operating system proper (e.g. the “Linux kernelâ€). The software we run is in user space, such as browsers, word processors, games, web servers, databases, GNU utilities [sic], and so on.The kernel has raw access to the machine, memory, network devices, graphics cards, and so on. User space has virtual access to these things. The user space is the original “virtual machinesâ€, before kernels got so bloated that we needed a third layer to virtualize them too.This separation between kernel and user has two main benefits. The first is security, controlling which bit of software has access to what. It means, for example, that one user on the machine can't access another's files. The second benefit is stability: if one program crashes, the others continue to run unaffected.Downside of a Kernel ModuleWriting a search program as a kernel module (instead of a user space module) defeats the benefits of user space programs, making the machine less stable and less secure.Moreover, the sort of thing this module does (parsing emails) has a history of big gapping security flaws. Parsing stuff in the kernel makes cybersecurity experts run away screaming in terror.On the other hand, people have been doing security stuff (SSL implementations and anti-virus scanning) in the kernel in other situations, so it's not unprecedented. I mean, it's still wrong, but it's been done before.Upside of a Kernel ModuleIf doing this is as a kernel module (instead of in user space) is so bad, then why does Yahoo do it? It's probably due to the widely held, but false, belief that putting stuff in the kernel makes it faster.Everybody knows that kernels are faster, for two reasons. First is that as a program runs, making a system call switches context, from running in user space to running in kernel space. This step is expensive/slow. Kernel modules don't incur this expense, because code just jumps from one location in the kernel to another. The second performance issue is virtual memory, where reading memory requires an extra step in user space, to translate the virtual memory address to a physical one. Kernel modules access physical memory directly, without this extra step.But everyone is wrong. Using features like hugepages gets rid of the cost of virtual memory translation cost. There are ways to mitigate the cost of user/kernel transitions, such as moving data in bulk instead of a little bit at a time. Also, CPUs have improved in recent years, dramatically reducing the cost of a kernel/user transition.The problem we face, though, is inertia. Everyone knows moving modules into the kernel makes things faster. It's hard getting them to un-learn what they've been taught.Also, following this logic, Yahoo may already hav | Yahoo | |||
| 2016-10-06 02:47:52 | What the Yahoo NSA might\'ve looked for (lien direct) | The vague story about Yahoo searching emails for the NSA was cleared up today with various stories from other outlets [1]. It seems clear a FISA court order was used to compel Yahoo to search all their customer's email for a pattern (or patterns). But there's an important detail still missing: what specifically were they searching for? In this post, I give an example.The NYTimes article explains the search thusly:Investigators had learned that agents of the foreign terrorist organization were communicating using Yahoo's email service and with a method that involved a “highly unique†identifier or signature, but the investigators did not know which specific email accounts those agents were using, the officials said.What they are likely referring it is software like "Mujahideen Secrets", which terrorists have been using for about a decade to encrypt messages. It includes a unique fingerprint/signature that can easily be searched for, as shown below.In the screenshot below, I use this software to type in a secret message: I then hit the "encrypt" button, and get the following, a chunk of random looking text: I then hit the "encrypt" button, and get the following, a chunk of random looking text: This software encrypts, but does not send/receive messages. You have to do that manually yourself. It's intended that terrorists will copy/paste this text into emails. They may also paste the messages into forum posts. Encryption is so good that nobody, not even the NSA, can crack properly encrypted messages, so it's okay to post them to public forums, and still maintain secrecy.In my case, I copy/pasted this encrypted message into an email message from one of my accounts and sent to to one of my Yahoo! email accounts. I received the message shown below: This software encrypts, but does not send/receive messages. You have to do that manually yourself. It's intended that terrorists will copy/paste this text into emails. They may also paste the messages into forum posts. Encryption is so good that nobody, not even the NSA, can crack properly encrypted messages, so it's okay to post them to public forums, and still maintain secrecy.In my case, I copy/pasted this encrypted message into an email message from one of my accounts and sent to to one of my Yahoo! email accounts. I received the message shown below: The obvious "highly unique signature" the FBI should be looking for, to catch this software, is the string:### Begin ASRAR El Mojahedeen v2.0 Encrypted Message ###Indeed, if this is the program the NSA/FBI was looking for, they've now caught this message in their dragnet of incoming Yahoo! mail. This is a bit creepy, which is why I added a plea to the message, in unencrypted form, asking them not to rendition or drone strike me. Since the NSA can use such signatures to search traffic from websites, as well as email traffic, there's a good change you've been added to their "list" simply for reading this blog post. For fun, send this blogpost to family or friends you don't particularly like, in order to get them on the watch list as well. The obvious "highly unique signature" the FBI should be looking for, to catch this software, is the string:### Begin ASRAR El Mojahedeen v2.0 Encrypted Message ###Indeed, if this is the program the NSA/FBI was looking for, they've now caught this message in their dragnet of incoming Yahoo! mail. This is a bit creepy, which is why I added a plea to the message, in unencrypted form, asking them not to rendition or drone strike me. Since the NSA can use such signatures to search traffic from websites, as well as email traffic, there's a good change you've been added to their "list" simply for reading this blog post. For fun, send this blogpost to family or friends you don't particularly like, in order to get them on the watch list as well. |
Yahoo | |||
| 2016-10-04 19:58:59 | The Yahoo-email-search story is garbage (lien direct) | Joseph Menn (Reuters) is reporting that Yahoo! searched emails for the NSA. The details of the story are so mangled that it's impossible to say what's actually going on.The first paragraph says this:Yahoo Inc last year secretly built a custom software program to search all of its customers' incoming emailsThe second paragraph says this:The company complied with a classified U.S. government demand, scanning hundreds of millions of Yahoo Mail accountsWell? Which is it? Did they "search incoming emails" or did they "scan mail accounts"? Whether we are dealing with emails in transmit, or stored on the servers, is a BFD (Big Fucking Detail) that you can't gloss over and confuse in a story like this. Whether searches are done indiscriminately across all emails, or only for specific accounts, is another BFD.The third paragraph seems to resolve this, but it doesn't:Some surveillance experts said this represents the first case to surface of a U.S. Internet company agreeing to an intelligence agency's request by searching all arriving messages, as opposed to examining stored messages or scanning a small number of accounts in real time.Who are these "some surveillance experts"? Why is the story keeping their identities secret? Are they some whistleblowers afraid for their jobs? If so, then that should be mentioned. In reality, they are unlikely to be real surveillance experts, but just some random person that knows slightly more about the subject than Joseph Menn, and their identities are being kept secret in order to prevent us from challenging these experts -- which is a violation of journalistic ethics.And, are they analyzing the raw information the author sent them? Or are they opining on the garbled version of events that we see in the first two paragraphs.It is not known what information intelligence officials were looking for, only that they wanted Yahoo to search for a set of characters. That could mean a phrase in an email or an attachment, said the sources, who did not want to be identified.What the fuck is a "set of characters"??? Is this an exact quote for somewhere? Or something the author of the story made up? The clarification of what this "could mean" doesn't clear this up, because if that's what it "actually means", then why not say this to begin with?What outsiders know about the NSA/FBI's ability to ask for strong selectors (email addresses). What what we don't know about is their ability to search all emails, regardless of account, for arbitrary keywords/phases. If that's what's going on, then this would be a huge story. But the story doesn't make it clear that this is actually what's going on -- just strongly implies it.There are many other ways to interpret this story. For example, the government may simply be demanding that when Yahoo satisfies demands for emails (based on email addresses), that it does so from the raw incoming stream, before it hits spam/malware filters. Or, they may be demanding that Yahoo satisfies their demands with more secrecy, so that the entire company doesn't learn of the email addresses that a FISA order demands. Or, the government may be demanding that the normal collection happen in real time, in the seconds that emails arrive, instead of minutes later.Or maybe this isn't an NSA/FISA story at all. Maybe the DHS has a cybersecurity information sharing program that distributes IoCs (indicators of compromise) to companies under NDA. Because it's a separate program under NDA, Yahoo would need to setup a email malware scanning system separate from their existing malware system in order to use those IoCs.My point is this: the story is full of mangled details that really tell us nothing. I can come up with multiple, unrelated s | Yahoo |
1
We have: 8 articles.
We have: 8 articles.
To see everything:
Our RSS (filtrered)
