What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2021-09-10 18:05:03 | Microsoft Zero-Day-of-the-Month Club (lien direct) |
 When it comes to zero day attacks against Microsoft products, I often feel like Bill Murray's character in the movie Groundhog Day. It seems like I keep waking up to the same scenario over and over and over, with attackers repeatedly exploiting zero-day vulnerabilities against Microsoft products.
When it comes to zero day attacks against Microsoft products, I often feel like Bill Murray's character in the movie Groundhog Day. It seems like I keep waking up to the same scenario over and over and over, with attackers repeatedly exploiting zero-day vulnerabilities against Microsoft products. |
||||
| 2021-09-10 16:00:00 | THREAT ALERT: Microsoft MSHTML Remote Code Execution Vulnerability (lien direct) |
 The Cybereason Global Security Operations Center (SOC) issues Cybereason Threat Alerts to inform customers of emerging impacting threats. The Alerts summarize these threats and provide practical recommendations for protecting against them.
The Cybereason Global Security Operations Center (SOC) issues Cybereason Threat Alerts to inform customers of emerging impacting threats. The Alerts summarize these threats and provide practical recommendations for protecting against them. |
Vulnerability Threat | |||
| 2021-09-09 19:56:50 | UN Breach Highlights Escalation of Cyber Threats (lien direct) |
 Hackers have been inside the United Nations network for months. According to a report from Bloomberg, stolen credentials of a UN employee were sold on the Dark Web for as little as $1,000. The report claims that Russian-speaking cybercriminals sold access to the UN systems for months-from April through August of 2021.
Hackers have been inside the United Nations network for months. According to a report from Bloomberg, stolen credentials of a UN employee were sold on the Dark Web for as little as $1,000. The report claims that Russian-speaking cybercriminals sold access to the UN systems for months-from April through August of 2021. |
||||
| 2021-09-09 12:46:23 | CISO Stories Podcast: The Unpatchable Vulnerability that is Human Nature (lien direct) |
 Rachel Tobac, CEO of SocialProof Security, delves into the inner-workings of social engineering exploits where she leverages her background in neuroscience and behavioral psychology to exploit the unpatchable vulnerability that is human nature - check it out...
Rachel Tobac, CEO of SocialProof Security, delves into the inner-workings of social engineering exploits where she leverages her background in neuroscience and behavioral psychology to exploit the unpatchable vulnerability that is human nature - check it out... |
Vulnerability | |||
| 2021-09-08 16:18:23 | Ransomware Attackers Don\'t Take Holidays (lien direct) |
 Not everyone took time off for Labor Day weekend. While millions of Americans enjoyed an extended weekend in honor of the holiday, cybercriminals were busy targeting Howard University with a ransomware attack.
Not everyone took time off for Labor Day weekend. While millions of Americans enjoyed an extended weekend in honor of the holiday, cybercriminals were busy targeting Howard University with a ransomware attack. |
Ransomware | |||
| 2021-09-08 13:30:00 | Cybereason\'s Lodrina Cherne Joins Panel on Building a More Inclusive Future in Cybersecurity (lien direct) |
 Cybereason's Lodrina Cherne, Principal Security Advocate in the Office of the CSO and Aspen Tech Policy Hub Fellow, will join other cyber experts in a discussion on inclusiveness sponsored by the Aspen Tech Policy Hub and Aspen Digital.
Cybereason's Lodrina Cherne, Principal Security Advocate in the Office of the CSO and Aspen Tech Policy Hub Fellow, will join other cyber experts in a discussion on inclusiveness sponsored by the Aspen Tech Policy Hub and Aspen Digital. |
||||
| 2021-09-08 13:00:00 | Cybereason and Smarttech247 Partner to Deliver Managed Detection and Response (lien direct) |
 Businesses today face a constant barrage of cyber threats, including destructive ransomware attacks and other malicious activity. That's why Cybereason is joining forces with Smarttech247, a multi-award-winning MDR company, to defend joint customers through managed detection and response services that block cyber attacks on endpoints anywhere on their networks.
Businesses today face a constant barrage of cyber threats, including destructive ransomware attacks and other malicious activity. That's why Cybereason is joining forces with Smarttech247, a multi-award-winning MDR company, to defend joint customers through managed detection and response services that block cyber attacks on endpoints anywhere on their networks. |
Ransomware | |||
| 2021-09-08 12:36:01 | Busted: Taking Down Ransomware Attackers (lien direct) |
 Ransomware has been big news this year. In March, the REvil/Sodinokibi ransomware gang infected Acer and demanded $50 million-the highest ransom demand from any ransomware group up to that point. That same gang then turned around a month later and demanded the same ransom from Apple after it failed to coerce Quanta Computer, one of the tech giant's business partners, into paying up.
Ransomware has been big news this year. In March, the REvil/Sodinokibi ransomware gang infected Acer and demanded $50 million-the highest ransom demand from any ransomware group up to that point. That same gang then turned around a month later and demanded the same ransom from Apple after it failed to coerce Quanta Computer, one of the tech giant's business partners, into paying up. |
Ransomware | |||
| 2021-09-07 12:15:05 | Malicious Life Podcast: Understanding China\'s Cyber Culture (lien direct) |
 Lt. Colonel (Ret.) Bill Hagestad examines how China's culture and troubled history of western colonialism influenced its government views and actions regarding the global internet and its interactions with western technology companies such as Google and Nortel - check it out...
Lt. Colonel (Ret.) Bill Hagestad examines how China's culture and troubled history of western colonialism influenced its government views and actions regarding the global internet and its interactions with western technology companies such as Google and Nortel - check it out... |
||||
| 2021-09-02 21:22:38 | Microsoft Vulnerability Exposes Thousands to Risk…Again (lien direct) |
 I can't deny that Microsoft competes with Cybereason, but the truth is, I owe a lot of the success of Cybereason to Microsoft. After all, the lion's share of what we do as defenders is protect against exploits targeting vulnerable Microsoft platforms and applications.
I can't deny that Microsoft competes with Cybereason, but the truth is, I owe a lot of the success of Cybereason to Microsoft. After all, the lion's share of what we do as defenders is protect against exploits targeting vulnerable Microsoft platforms and applications. |
Vulnerability | |||
| 2021-09-02 20:46:00 | Cybersecurity Is National Security (lien direct) |
 President Biden convened a meeting at the White House last week to focus on cybersecurity. After months of escalating cyber attacks that have affected critical infrastructure providers, the food supply chain, and even disrupted distribution of COVID-19 vaccines and hospitals at capacity struggling to treat COVID patients, it is time to draw a line in the sand. One thing that is increasingly evident as the lines have blurred for cyber attacks is that cybersecurity is national security.
President Biden convened a meeting at the White House last week to focus on cybersecurity. After months of escalating cyber attacks that have affected critical infrastructure providers, the food supply chain, and even disrupted distribution of COVID-19 vaccines and hospitals at capacity struggling to treat COVID patients, it is time to draw a line in the sand. One thing that is increasingly evident as the lines have blurred for cyber attacks is that cybersecurity is national security. |
||||
| 2021-09-02 13:04:13 | CISO Stories Podcast: Did You Ask For (and Get) Too Much Security Budget? (lien direct) |
 It seems CISOs are typically lamenting that the security budgets are insufficient. While this can represent a significant problem in achieving information security goals, what happens when you get the funding you asked for and are asked to spend it in less time than expected?
It seems CISOs are typically lamenting that the security budgets are insufficient. While this can represent a significant problem in achieving information security goals, what happens when you get the funding you asked for and are asked to spend it in less time than expected? |
||||
| 2021-09-01 13:02:03 | The Value Drivers for an XDR Investment (lien direct) |
 We have a pretty good idea by now of what Extended Detection and Response (XDR) is. As we noted in an earlier article, titled XDR: The Next Step in Threat Detection and Response, XDR is a security approach that builds on the successes of Endpoint Detection and Response (EDR).
We have a pretty good idea by now of what Extended Detection and Response (XDR) is. As we noted in an earlier article, titled XDR: The Next Step in Threat Detection and Response, XDR is a security approach that builds on the successes of Endpoint Detection and Response (EDR). |
Threat | |||
| 2021-08-31 13:35:38 | ESG Research Report: 2021 Trends in Endpoint Security (lien direct) |
 As security threats quickly continue to evolve, our approaches to security must evolve as well. Simple signature-based antivirus solutions are no longer enough to prevent the highly targeted attacks of today, making traditional solutions an inadequate defense.
As security threats quickly continue to evolve, our approaches to security must evolve as well. Simple signature-based antivirus solutions are no longer enough to prevent the highly targeted attacks of today, making traditional solutions an inadequate defense. |
||||
| 2021-08-31 12:01:26 | Evolving Ransomware Tactics Include Recruiting Insiders and DDoS Attacks (lien direct) |
 The attention generated by the DarkSide ransomware attack against Colonial Pipeline in May has helped to reshape the ransomware threat landscape. One of the most important modifications came when the digital crime forum XSS announced that members could no longer post about ransomware topics. The Exploit forum followed suit not long after, as reported by Bleeping Computer.
The attention generated by the DarkSide ransomware attack against Colonial Pipeline in May has helped to reshape the ransomware threat landscape. One of the most important modifications came when the digital crime forum XSS announced that members could no longer post about ransomware topics. The Exploit forum followed suit not long after, as reported by Bleeping Computer. |
Ransomware Threat | |||
| 2021-08-30 12:44:17 | Malicious Life Podcast: The Life and Times of John McAfee (lien direct) |
 What do you get when you take a gun-toting cybersecurity pioneer and add some drugs and a serious amount of money to the mix? You get a life so bizarre, so unbelievably extreme that people will tell your story long after you're long gone. It's all part of John McAfee's unbelievable life and times - check it out...
What do you get when you take a gun-toting cybersecurity pioneer and add some drugs and a serious amount of money to the mix? You get a life so bizarre, so unbelievably extreme that people will tell your story long after you're long gone. It's all part of John McAfee's unbelievable life and times - check it out... |
||||
| 2021-08-26 20:21:25 | Afghanistan, the Taliban and National Security (lien direct) |
 The United States may have left classified or sensitive intelligence behind as US forces withdrew and evacuated from Afghanistan. That information might now be in the hands of the Taliban. There was also a report this week about an alleged cyber breach at the US State Department. These are both concerns with potential implications for national security, but there is no need to panic.
The United States may have left classified or sensitive intelligence behind as US forces withdrew and evacuated from Afghanistan. That information might now be in the hands of the Taliban. There was also a report this week about an alleged cyber breach at the US State Department. These are both concerns with potential implications for national security, but there is no need to panic. |
||||
| 2021-08-26 12:42:47 | CISO Stories Podcast: Practical Considerations for Managing Your MSSP (lien direct) |
 For many organizations, large and small, it would be impractical to “skill up” to manage all aspects of cybersecurity. Managed Security Service Providers (MSSPs) provide many different services.
For many organizations, large and small, it would be impractical to “skill up” to manage all aspects of cybersecurity. Managed Security Service Providers (MSSPs) provide many different services. |
||||
| 2021-08-25 13:09:12 | How XDR Delivers on SOAR\'s Unfulfilled Promises (lien direct) |
 Security Orchestration, Automation, and Response (SOAR) is on the rise. According to MarketsandMarkets, the SOAR market is expected to increase from $868 million in 2019 to $1.791 million by 2024. Such growth would occur at a CAGR of 15.6% in that period - but are organizations getting the value out of SOAR they anticipated?
Security Orchestration, Automation, and Response (SOAR) is on the rise. According to MarketsandMarkets, the SOAR market is expected to increase from $868 million in 2019 to $1.791 million by 2024. Such growth would occur at a CAGR of 15.6% in that period - but are organizations getting the value out of SOAR they anticipated?
|
||||
| 2021-08-24 19:43:41 | Implications of the Alleged State Department Breach (lien direct) |
 The US State Department was reportedly hit by another cyber attack, although it has not been officially confirmed. Whether or not the attack occurred, it is a simple fact that government agencies and private organizations are under constant siege, and that the security professionals tasked with protecting against attacks need to remain vigilant.
The US State Department was reportedly hit by another cyber attack, although it has not been officially confirmed. Whether or not the attack occurred, it is a simple fact that government agencies and private organizations are under constant siege, and that the security professionals tasked with protecting against attacks need to remain vigilant. |
||||
| 2021-08-24 11:55:10 | Cybereason vs. LockBit2.0 Ransomware (lien direct) |
 The Cybereason Nocturnus team has been tracking the LockBit ransomware since it first emerged in September 2019 as a ransomware-as-a-service (RaaS). Following the rise of the new LockBit2.0 and the latest events, including the attack against the global IT company Accenture, we wanted to provide more information about the attack and show how the Cybereason Defense Platform protects customers from this threat.
The Cybereason Nocturnus team has been tracking the LockBit ransomware since it first emerged in September 2019 as a ransomware-as-a-service (RaaS). Following the rise of the new LockBit2.0 and the latest events, including the attack against the global IT company Accenture, we wanted to provide more information about the attack and show how the Cybereason Defense Platform protects customers from this threat. |
Ransomware | |||
| 2021-08-23 16:23:21 | Webinar: Extended Detection and Response (XDR) - Past, Present and Future (lien direct) |
 If you've been feeling critical about your company's ability to identify and defeat modern attacks, you're not alone. Our world is one where IT infrastructure, attacker trends, and workspace norms continue to shift, so it's an increasingly difficult challenge to build a resilient infosec program backed by tested best practices.
If you've been feeling critical about your company's ability to identify and defeat modern attacks, you're not alone. Our world is one where IT infrastructure, attacker trends, and workspace norms continue to shift, so it's an increasingly difficult challenge to build a resilient infosec program backed by tested best practices. |
||||
| 2021-08-23 12:01:58 | (Déjà vu) Malicious Life Podcast: Ten Years On - Are We Doing Security Right? (lien direct) |
 The company's leadership knew they had been breached in a sophisticated APT-style attack, but it was unknown whether the attackers had gained access to the cryptographic keys needed to decrypt sensitive client data. It was March of 2011, and security vendor RSA was the target of an attack that compromised sensitive data related to the company's flagship SecurID product.
The company's leadership knew they had been breached in a sophisticated APT-style attack, but it was unknown whether the attackers had gained access to the cryptographic keys needed to decrypt sensitive client data. It was March of 2011, and security vendor RSA was the target of an attack that compromised sensitive data related to the company's flagship SecurID product. |
Guideline | |||
| 2021-08-19 19:20:13 | T-Mobile and BlackBerry: More Lessons Learned the Hard Way (lien direct) |
 We learned this week that T-Mobile was the victim of a data breach that exposed data from tens of millions of customers, and then we found out that there is a flaw in BlackBerry's QNX operating system that puts hundreds of millions of devices at risk. These events don't impact everyone, but there are still lessons to be learned.
We learned this week that T-Mobile was the victim of a data breach that exposed data from tens of millions of customers, and then we found out that there is a flaw in BlackBerry's QNX operating system that puts hundreds of millions of devices at risk. These events don't impact everyone, but there are still lessons to be learned. |
||||
| 2021-08-19 13:00:27 | CISO Stories Podcast: Achieving Security Buy-In - Change Approach Not Culture (lien direct) |
 We need the organization to support the cybersecurity initiatives and thus we try to influence the organization to support these goals for the protection of the organizational assets. If we are failing, is it that the organization did not 'get it' or was it our approach?
David Nolan, Vice President of Information Security at Aaron's, joins this podcast to discuss how to achieve that consensus - check it out...
We need the organization to support the cybersecurity initiatives and thus we try to influence the organization to support these goals for the protection of the organizational assets. If we are failing, is it that the organization did not 'get it' or was it our approach?
David Nolan, Vice President of Information Security at Aaron's, joins this podcast to discuss how to achieve that consensus - check it out... |
||||
| 2021-08-18 16:43:59 | BlackBerry QNX Vulnerability Highlights Lurking Issues with IOT Security (lien direct) |
 BlackBerry revealed that its QNX operating system is vulnerable to the BadAlloc flaw revealed earlier this year. QNX is an embedded systems operating system that can be found in hundreds of millions of cars, as well as everything from critical infrastructure, to hospital devices, to equipment on the International Space Station. The disclosure highlights a lurking issue illustrating the much larger challenge we face when it comes to securing internet-of-things (IoT) and embedded systems like QNX.
BlackBerry revealed that its QNX operating system is vulnerable to the BadAlloc flaw revealed earlier this year. QNX is an embedded systems operating system that can be found in hundreds of millions of cars, as well as everything from critical infrastructure, to hospital devices, to equipment on the International Space Station. The disclosure highlights a lurking issue illustrating the much larger challenge we face when it comes to securing internet-of-things (IoT) and embedded systems like QNX. |
Vulnerability | |||
| 2021-08-18 13:23:46 | Three Reasons Why You Should Never Pay Ransomware Attackers (lien direct) |
 After falling prey to a ransomware attack, most organizations are faced with the decision of whether they're going to pay the ransom demand. We'll save you some time: it's not worth it, and here are three of the many reasons why it does not pay to pay.
After falling prey to a ransomware attack, most organizations are faced with the decision of whether they're going to pay the ransom demand. We'll save you some time: it's not worth it, and here are three of the many reasons why it does not pay to pay. |
Ransomware | |||
| 2021-08-17 19:07:26 | Analyst Report: How to Prepare for Ransomware Attacks (lien direct) |
 Ransomware operations have evolved dramatically in recent months and years, and now leverage advanced tactics to infiltrate an organization. Security and risk management leaders need to look beyond just the endpoints to help protect the organization from ransomware. Fine-tuning incident response processes to specifically deal with ransomware is a key component for successful mitigation of these multi-stage attacks.
Ransomware operations have evolved dramatically in recent months and years, and now leverage advanced tactics to infiltrate an organization. Security and risk management leaders need to look beyond just the endpoints to help protect the organization from ransomware. Fine-tuning incident response processes to specifically deal with ransomware is a key component for successful mitigation of these multi-stage attacks. |
Ransomware Guideline | |||
| 2021-08-17 17:51:52 | T-Mobile Data Breach Amplifies Larger Cybersecurity Challenge (lien direct) |
 Reports came out this week that T-Mobile had suffered a data breach. T-Mobile claims that the leak has been sealed. They deserve credit for responding quickly, but for some the damage may already be done. The data itself may not pose a direct risk to anyone, but the more information cybercriminals can obtain and correlate, the more effective future attacks will be.
Reports came out this week that T-Mobile had suffered a data breach. T-Mobile claims that the leak has been sealed. They deserve credit for responding quickly, but for some the damage may already be done. The data itself may not pose a direct risk to anyone, but the more information cybercriminals can obtain and correlate, the more effective future attacks will be. |
Data Breach | |||
| 2021-08-17 12:51:03 | XDR: The Key to Solving SIEM Shortcomings (lien direct) |
 One of the mainstays of organizations' digital security postures is a Security Information and Event Management (SIEM) platform. According to CSO Online, SIEMs augment threat monitoring and incident response with log analysis.
One of the mainstays of organizations' digital security postures is a Security Information and Event Management (SIEM) platform. According to CSO Online, SIEMs augment threat monitoring and incident response with log analysis. |
Threat | |||
| 2021-08-16 12:04:08 | (Déjà vu) Malicious Life Podcast: DeadRinger - Exposing Chinese APTs Targeting Major Telcos (lien direct) |
 Cybereason recently discovered several previously unidentified attack campaigns targeting the telecoms industry across Southeast Asia that are assessed to be the work of multiple Chinese APT groups. The attacks are detailed in the threat intelligence report titled DeadRinger: Exposing Chinese Threat Actors Targeting Major Telcos.
Cybereason recently discovered several previously unidentified attack campaigns targeting the telecoms industry across Southeast Asia that are assessed to be the work of multiple Chinese APT groups. The attacks are detailed in the threat intelligence report titled DeadRinger: Exposing Chinese Threat Actors Targeting Major Telcos. |
Threat | |||
| 2021-08-12 17:03:00 | LockBit Ransomware Wants to Hire Your Employees (lien direct) |
 If I offer you a million dollars right now, would you betray your company and help me compromise their data? What if I told you that there is a ransomware group out there that is doing just that? Would you take the bait? Are you sure that others in your company won't be motivated to take that deal?
If I offer you a million dollars right now, would you betray your company and help me compromise their data? What if I told you that there is a ransomware group out there that is doing just that? Would you take the bait? Are you sure that others in your company won't be motivated to take that deal? |
Ransomware | |||
| 2021-08-12 14:02:11 | Accenture Responds Following LockBit Ransomware Attack (lien direct) |
 Global IT consultancy company Accenture announced that it has fully restored its systems after experiencing a LockBit ransomware attack. On August 11, Accenture shared details about an incident involving some of their IT assets.
Global IT consultancy company Accenture announced that it has fully restored its systems after experiencing a LockBit ransomware attack. On August 11, Accenture shared details about an incident involving some of their IT assets. |
Ransomware | |||
| 2021-08-11 14:45:48 | The Rising Threat from LockBit Ransomware (lien direct) |
 LockBit ransomware is the latest threat posing an increased risk for organizations. The ransomware gang has been making headlines recently. LockBit has also reportedly compromised Accenture.
The group reportedly revealed the attack on their site on the DarkWeb, noting, “these people are beyond privacy and security. Hope their services are better than what I have seen inside. If you are interested in purchasing data sets, contact us.”
LockBit ransomware is the latest threat posing an increased risk for organizations. The ransomware gang has been making headlines recently. LockBit has also reportedly compromised Accenture.
The group reportedly revealed the attack on their site on the DarkWeb, noting, “these people are beyond privacy and security. Hope their services are better than what I have seen inside. If you are interested in purchasing data sets, contact us.” |
Ransomware Threat | |||
| 2021-08-11 12:47:11 | CISO Stories Podcast: Hacking Your Way Into Cybersecurity (lien direct) |
 Kerissa Varma is Group Chief Information Security Officer of Old Mutual Limited, one of the largest financial services organizations on the African continent. Kerissa joins the show to discuss the cybersecurity skills shortage and her initiative to recruit brilliant minds from across an array of fields who have skill sets applicable to cybersecurity, but they might not even know it - check it out...
Kerissa Varma is Group Chief Information Security Officer of Old Mutual Limited, one of the largest financial services organizations on the African continent. Kerissa joins the show to discuss the cybersecurity skills shortage and her initiative to recruit brilliant minds from across an array of fields who have skill sets applicable to cybersecurity, but they might not even know it - check it out... |
||||
| 2021-08-10 18:17:00 | Webinar: REvil Ransomware - Pick Your Path (lien direct) |
 Today's ransomware actors are operating to devastating effect as evidenced by the Colonial Pipeline and JBS attacks, showing that a successful attack can disrupt any business.
Today's ransomware actors are operating to devastating effect as evidenced by the Colonial Pipeline and JBS attacks, showing that a successful attack can disrupt any business. |
Ransomware | |||
| 2021-08-10 12:56:59 | Who Are the Main Targets of Ransomware Attacks? (lien direct) |
 In our ransomware report, titled Ransomware: The True Cost to Business, 81% of respondents indicated that they are highly or very concerned about the risk of ransomware attacks. That's not a surprise given the growing ransomware threat.
In our ransomware report, titled Ransomware: The True Cost to Business, 81% of respondents indicated that they are highly or very concerned about the risk of ransomware attacks. That's not a surprise given the growing ransomware threat. |
Ransomware | |||
| 2021-08-09 12:18:15 | XDR: The Next Step in Threat Detection and Response (lien direct) |
 The global EDR market (Endpoint Detection and Response) is growing rapidly. The Transparency Market Research team predicted that this market will increase at a CAGR of about 21% in the next decade, reported Help Net Security. If it happens, this growth will help the global EDR market surpass a valuation of $13.8 billion by 2030.
The global EDR market (Endpoint Detection and Response) is growing rapidly. The Transparency Market Research team predicted that this market will increase at a CAGR of about 21% in the next decade, reported Help Net Security. If it happens, this growth will help the global EDR market surpass a valuation of $13.8 billion by 2030. |
Threat | |||
| 2021-08-09 12:04:26 | Malicious Life Podcast: The Jester - Hacktivist for Good (lien direct) |
 The Jester is a patriotic, pro-American Hacktivist that since 2010 has waged a personal cyberwar against an array of targets he considers to be “the bad guys.” But detractors have insinuated that some of the Jester's operations were little more than internet sleight-of-hand. So, who is The Jester and what can we make of his reported exploits? Check it out…
The Jester is a patriotic, pro-American Hacktivist that since 2010 has waged a personal cyberwar against an array of targets he considers to be “the bad guys.” But detractors have insinuated that some of the Jester's operations were little more than internet sleight-of-hand. So, who is The Jester and what can we make of his reported exploits? Check it out… |
||||
| 2021-08-06 16:32:00 | \'DeadRinger\' Reveals Pervasive Cyber Espionage Campaign (lien direct) |
 In the summer of 2019, our researchers discovered a massive malicious campaign against telecommunications providers that we dubbed Operation Soft Cell. This week, our researchers revealed details of more pervasive attacks against telecommunications providers. The DeadRinger report reveals a cyber espionage campaign out of China targeting providers in Southeast Asia.
In the summer of 2019, our researchers discovered a massive malicious campaign against telecommunications providers that we dubbed Operation Soft Cell. This week, our researchers revealed details of more pervasive attacks against telecommunications providers. The DeadRinger report reveals a cyber espionage campaign out of China targeting providers in Southeast Asia. |
||||
| 2021-08-05 12:55:48 | CISO Stories Podcast: Managing the Security Product Salesperson (lien direct) |
 CISOs are approached frequently by salespersons seeking to sell products that are supposed to reduce risk. How should a CISO manage these relationships? Kevin Morrison, CISO at Alaska Air Group, joins the podcast to discuss strategies for dealing with salespeople and selecting the best products for the organization - check it out...
CISOs are approached frequently by salespersons seeking to sell products that are supposed to reduce risk. How should a CISO manage these relationships? Kevin Morrison, CISO at Alaska Air Group, joins the podcast to discuss strategies for dealing with salespeople and selecting the best products for the organization - check it out... |
||||
| 2021-08-04 12:37:12 | Partners in Crime: How Ransomware Gangs Are Working Together (lien direct) |
 By now, it's clear that paying the ransom won't necessarily help ransomware victims to recover their data. Paying up also doesn't guarantee that victims will be safe from secondary attacks. According to our ransomware report, 80% of organizations that opted to pay a ransom demand ended up suffering another attack. Nearly half (46%) of those victims said they believed that the same attackers had infected them again, while 34% felt that it might have been someone else.
By now, it's clear that paying the ransom won't necessarily help ransomware victims to recover their data. Paying up also doesn't guarantee that victims will be safe from secondary attacks. According to our ransomware report, 80% of organizations that opted to pay a ransom demand ended up suffering another attack. Nearly half (46%) of those victims said they believed that the same attackers had infected them again, while 34% felt that it might have been someone else. |
Ransomware | |||
| 2021-08-03 04:03:00 | DeadRinger: Exposing Chinese Threat Actors Targeting Major Telcos (lien direct) |
 Following the discovery of Hafnium attacks targeting Microsoft Exchange vulnerabilities, the Cybereason Nocturnus and Incident Response teams proactively hunted for various threat actors trying to leverage similar techniques in-the-wild. In the beginning of 2021, the Cybereason Nocturnus Team investigated clusters of intrusions detected targeting the telecommunications industry across Southeast Asia. During the investigation, three clusters of activity were identified and showed significant connections to known threat actors, all suspected to be operating on behalf of Chinese state interests.
The report comes on the heels of the Biden administration's public rebuke of China's Ministry of State Security for the recent HAFNIUM attacks that exploited vulnerabilities in unpatched Microsoft Exchange Servers and put thousands of organizations worldwide at risk. Exploitation of these same vulnerabilities were central to the success of the attacks detailed in this research.
Following the discovery of Hafnium attacks targeting Microsoft Exchange vulnerabilities, the Cybereason Nocturnus and Incident Response teams proactively hunted for various threat actors trying to leverage similar techniques in-the-wild. In the beginning of 2021, the Cybereason Nocturnus Team investigated clusters of intrusions detected targeting the telecommunications industry across Southeast Asia. During the investigation, three clusters of activity were identified and showed significant connections to known threat actors, all suspected to be operating on behalf of Chinese state interests.
The report comes on the heels of the Biden administration's public rebuke of China's Ministry of State Security for the recent HAFNIUM attacks that exploited vulnerabilities in unpatched Microsoft Exchange Servers and put thousands of organizations worldwide at risk. Exploitation of these same vulnerabilities were central to the success of the attacks detailed in this research. |
Threat | |||
| 2021-08-03 04:00:17 | Webinar: DeadRinger - Exposing Chinese Threat Actors Targeting Major Telcos (lien direct) |
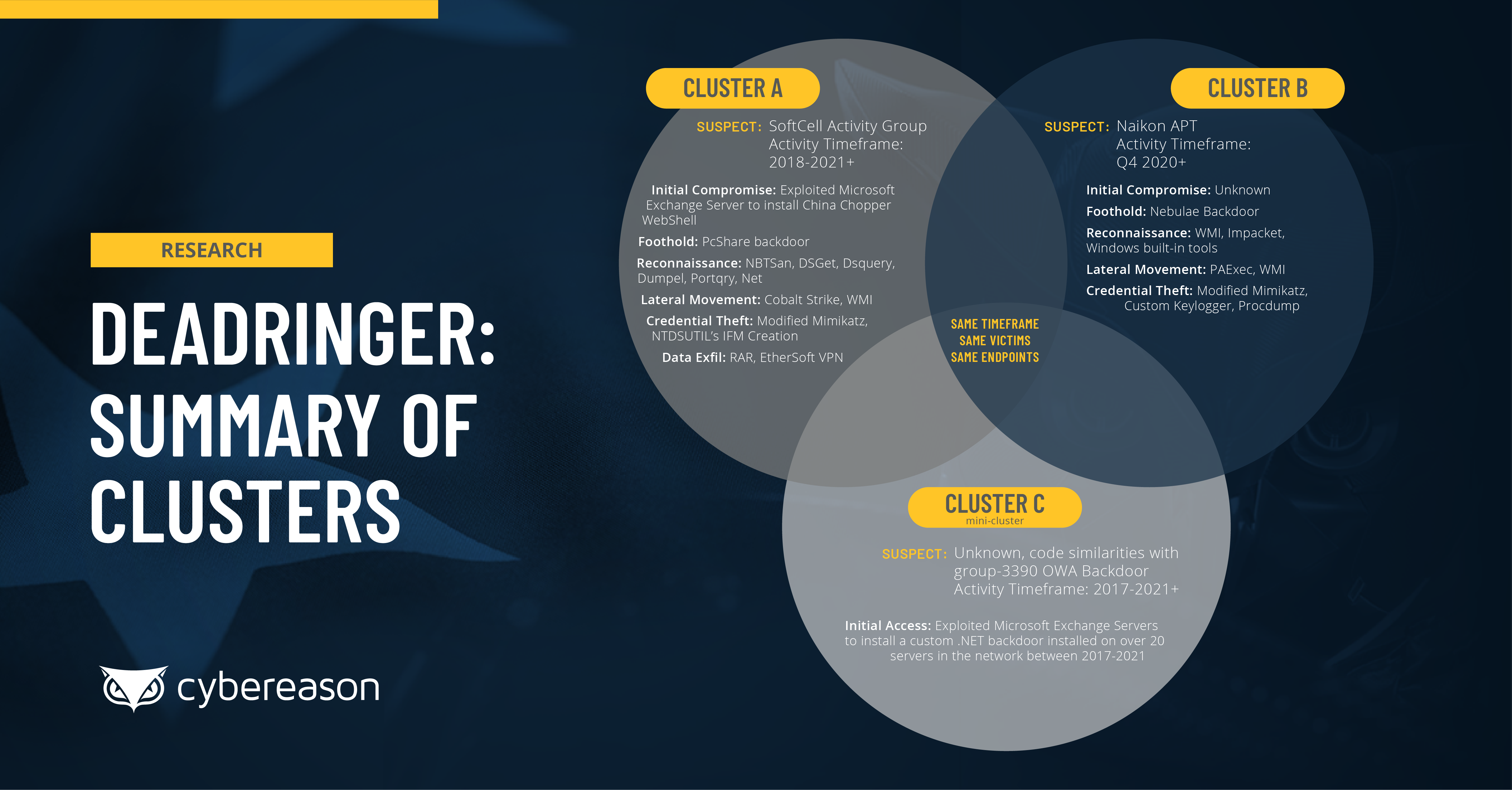 The Cybereason Nocturnus Research Team recently released a major threat intelligence research report titled DeadRinger: Exposing Chinese Threat Actors Targeting Major Telcos, which details the discovery of several previously unidentified attack campaigns targeting the telecommunications industry across Southeast Asia, where several clusters of attack activity were identified and assessed to be the work of several prominent APT groups who are known to conduct operations aligned with the interests of the Chinese government.
The Cybereason Nocturnus Research Team recently released a major threat intelligence research report titled DeadRinger: Exposing Chinese Threat Actors Targeting Major Telcos, which details the discovery of several previously unidentified attack campaigns targeting the telecommunications industry across Southeast Asia, where several clusters of attack activity were identified and assessed to be the work of several prominent APT groups who are known to conduct operations aligned with the interests of the Chinese government. |
Threat | |||
| 2021-08-02 12:07:17 | (Déjà vu) What the Growing Costs of a Data Breach Means for the Business (lien direct) |
 A recent global research report conducted by Cybereason, titled Ransomware: The True Cost to Business, revealed that the vast majority of organizations that have suffered a ransomware attack have experienced significant impact to the business, including loss of revenue, damage to the organization's brand, unplanned workforce reductions, and little in the way of relief from cyber insurance policies.
An esteemed panel of subject matter experts will examine the research findings and discuss how organizations can better prepare to defend against and respond to a ransomware attack, and the full on-demand webinar can be found here.
Recently, IBM came out with its Cost of a Data Breach Report 2021. This publication synthesizes the Ponemon Institute's research of 537 breaches that affected 17 different industries and that occurred across 17 countries and regions. It also draws on nearly 3,500 interviews to understand how much those breaches cost organizations and what decision makers are doing to better defend against security incidents going forward.
A recent global research report conducted by Cybereason, titled Ransomware: The True Cost to Business, revealed that the vast majority of organizations that have suffered a ransomware attack have experienced significant impact to the business, including loss of revenue, damage to the organization's brand, unplanned workforce reductions, and little in the way of relief from cyber insurance policies.
An esteemed panel of subject matter experts will examine the research findings and discuss how organizations can better prepare to defend against and respond to a ransomware attack, and the full on-demand webinar can be found here.
Recently, IBM came out with its Cost of a Data Breach Report 2021. This publication synthesizes the Ponemon Institute's research of 537 breaches that affected 17 different industries and that occurred across 17 countries and regions. It also draws on nearly 3,500 interviews to understand how much those breaches cost organizations and what decision makers are doing to better defend against security incidents going forward. |
Ransomware Data Breach | |||
| 2021-08-02 12:04:49 | Malicious Life Podcast: The State of Credit Card Security (lien direct) |
 In 2005, when Albert Gonzalez was hacking his way into the networks of many retail chains in the US (listen to Part 1, Part 2 and Part 3), credit cards were still very insecure: magnetic stripes and signed receipts did little to stop smart hackers such as Gonzalez and his crew.
In 2005, when Albert Gonzalez was hacking his way into the networks of many retail chains in the US (listen to Part 1, Part 2 and Part 3), credit cards were still very insecure: magnetic stripes and signed receipts did little to stop smart hackers such as Gonzalez and his crew. |
||||
| 2021-07-30 20:20:45 | (Déjà vu) CISO Stories Podcast: Ransomware Attacks and the True Cost to Business (lien direct) |
 A recent global research report conducted by Cybereason, titled Ransomware: The True Cost to Business, revealed that the vast majority of organizations that have suffered a ransomware attack have experienced significant impact to the business, including loss of revenue, damage to the organization's brand, unplanned workforce reductions, and little in the way of relief from cyber insurance policies.
A recent global research report conducted by Cybereason, titled Ransomware: The True Cost to Business, revealed that the vast majority of organizations that have suffered a ransomware attack have experienced significant impact to the business, including loss of revenue, damage to the organization's brand, unplanned workforce reductions, and little in the way of relief from cyber insurance policies. |
Ransomware | |||
| 2021-07-29 13:45:07 | Cybereason Offers Comprehensive Visibility and Protection for Diverse Systems (lien direct) |
 As enterprise technical infrastructures become more complex, managing them grows increasingly difficult. Protection against the growing problem of cybercrime also remains a key aspect for anyone involved in IT management. Cybersecurity considerations are especially critical for organizations involved in Customer Experience Automation and CRM, such as my company ActiveCampaign.
As enterprise technical infrastructures become more complex, managing them grows increasingly difficult. Protection against the growing problem of cybercrime also remains a key aspect for anyone involved in IT management. Cybersecurity considerations are especially critical for organizations involved in Customer Experience Automation and CRM, such as my company ActiveCampaign. |
||||
| 2021-07-28 12:33:28 | CISO Stories Podcast: Developing Secure Agile Code Quickly is Very Achievable (lien direct) |
 Speed to market is the mantra of software development today. This does not mean that a process is not followed, it means that an iterative approach to software development produces code changes and usable code much faster.
Speed to market is the mantra of software development today. This does not mean that a process is not followed, it means that an iterative approach to software development produces code changes and usable code much faster. |
||||
| 2021-07-27 12:56:20 | The XDR Advantage: Eliminate Dwell Time and Gain Visibility (lien direct) |
 The average cost of a data breach in 2020 was $3.86 million, according to IBM. It was even more expensive for certain entities. Indeed, that cost rose to $8.64 million when attackers succeeded in breaching an organization located in the United States. It was the same story in the healthcare industry, with the cost of data breaches climbing to $7.13 million for affected entities.
The average cost of a data breach in 2020 was $3.86 million, according to IBM. It was even more expensive for certain entities. Indeed, that cost rose to $8.64 million when attackers succeeded in breaching an organization located in the United States. It was the same story in the healthcare industry, with the cost of data breaches climbing to $7.13 million for affected entities.
|
Data Breach |
To see everything:
Our RSS (filtrered)
